A Short Guide to Malware
Malware stands for malicious software, and it's any piece of code that does something harmful to a computer system.

Malware stands for 'malicious software' and it's any piece of code that does something harmful to a computer system, an example is a computer virus. Most people call all malware viruses, but viruses are actually only one of the things that your computer can be infected with, in this article we will look at all kinds of cyber nasties.
There are several different classifications of malware and they are different by how they spread, how they replicate themselves and how they evade detection. Here I’ll be giving a breakdown of some of the common types of malware and explain what hackers are trying to accomplish when they infect your computer with malware.
Classifications of Malware
Virus
This is what most media outlets and people will call every type of malware, but in actuality it only represents one small portion of the malware that exists. A virus is any type of malware that spreads by infecting other computer programs, it inserts its own code into that program. Most viruses target Windows but as of recently, started increasing in popularity on Mac Operating Systems.
Worm
A worm is a self-replicating malware program that tries to infect other computers by duplicating itself and travelling over a computer network. A worm doesn’t need other computer programs to replicate itself. Usually the worm will be programmed to exploit a certain security vulnerability, so once it infects one computer it will search for other computers with that same vulnerability, infect them and then continue that cycle until it gets all the computers on that network infected.
Trojan
A trojan is any malware program that tricks users into downloading or running it by pretending to be a legitimate program. It got its name from the Greek story of the trojan horse that led to the fall of the city of Troy.
Rogue Security Software/Scareware
This is a subset of a trojan but I’m putting it into its own category because of how common it is and how many variations there are. Rogue security software is a malware program that tries to scare you into downloading a malware program. A common way they do this is to present you with a pop-up message claiming that they found viruses on your computer and then tell you if you download their product, it will clean up your computer. It’s a straight scare tactic, avoid downloading any antivirus solution that you aren’t sure of.
Malvertising
This stands for malware advertising, this is the use of legitimate ads to spread malware to users that visit a webpage. It involves someone injecting malware into a legitimate ad block and then whenever someone clicks on that link they are redirected to a fake webpage to have their information stolen or they download a piece of malware directly. Additionally, some malvertising does something called a drive-by-download, where just by visiting the page hosting the malvertising will cause your computer to download the malware, whether or not you click on the ad.
Fileless Malware (Memory Malware)
Fileless malware is any malware that doesn’t need to infect another program in order to spread. It exists solely as a computer memory-based artifact, such as in the computer’s RAM. For those not familiar, when you download and save a file to your computer it is saved to that computer’s hard drive. But for anything a computer only uses temporarily it is kept in the computer’s memory, which is where this type of malware exists. This means that this type of malware doesn’t need to go through the trouble of being downloaded and saved to the computer like other types of malware. The positive side is since it only exists in memory, restarting the computer will remove it. This is because computer memory is volatile, meaning that it is lost once the computer loses power, even if only for a short period of time. However, this also means that this type of malware doesn’t leave a forensic trail because all evidence of its existence on the computer is lost once the computer is shut off.
Rootkit
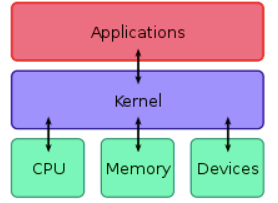
This is one of the worst types of malware, they are designed to allow the attacker to access and steal user’s information with being detected by antivirus or other security software for long periods of time. What makes rootkits very difficult to detect or remove is that they install themselves deeper into the computer than the application software, where the antivirus and security systems are found. For example there are kernel level rootkits. The kernel is the computer system at the core of an operating system and compromising that gives the attacker complete control over the computer. There are bootkits, which are rootkits that infect the software that launches and runs the computer before you get to your login screen.
File Macros
This is a type of malware that takes advantage of Macros found in Microsoft Excel and Microsoft Word documents. Malware can be created and attached to these files, then once someone opens it and enables macros, it will run and infect that system.
Polymorphic
A polymorphic malware, is malware that constantly changes its identifiable features in order to avoid detection. This can be changing its code, changing the filenames it creates, changing the size of the malware etc. The reason this works is that many anti-malware software create signatures or profiles for each piece of malware based on it’s characteristics or behaviour. When the anti-malware software finds another program that meets one of the profiles, the anti-malware solution will quarantine that program from the rest of the computer. By creating a malicious program that can change its features, it allows for the malware to avoid detection and infect multiple machines without getting blocked. About 97% of malware uses some type of polymorphic technique.
Types of Malware
This section focuses on the different types of malware, they are unique based on their features. This section highlights what malware will do once it has gotten onto your computer. Any of the classifications of malware explained in the previous section can have features of one or multiple of these types.
Adware
This is a relatively harmless type of malware. After being installed adware shows users advertisements that are meant to make profit for the hacker. Much of the software that is installed for legitimate applications is technically adware. Outside of being an annoyance it doesn’t do any harm to your computer except use up some of it’s resources.
Ransomware
This is one of the most popular and profitable types of malware. It encrypts all of the information on the infected systems and demands payment from the owner to have the files restored to normal. It is consistently used against businesses and generates a large amount of revenue every year.
Spyware
This type of malware sits on your computer, collects information and sends that information back to the attacker. This can include the websites you visited, your location on mobile phones, turning on your camera to see the person or take pictures etc.
Backdoor
A backdoor is a piece of malware that allows an attacker to connect to your computer at any time. Once a hacker gets into your computer system one of the first things they do is set up a backdoor. This is important so they don’t have to spend all the time hacking into your computer system again in the event that you fix the vulnerability that let them in, change your password or otherwise improve the security of your system.
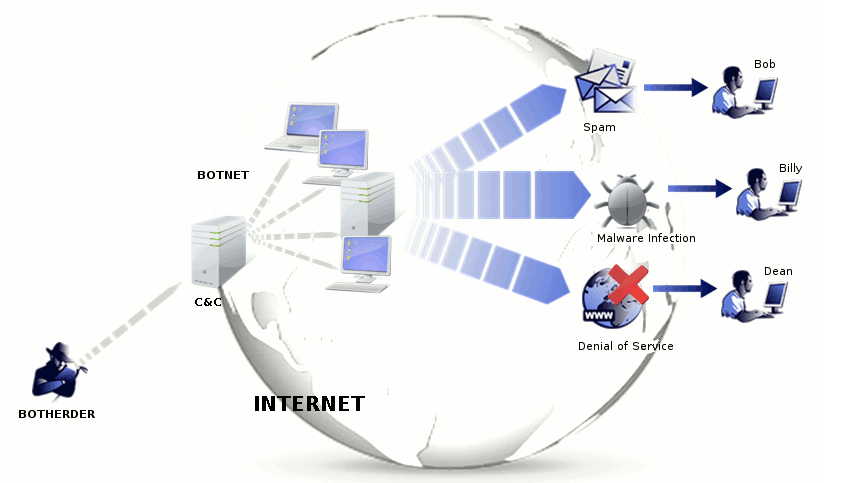
Bots/Botnet
Bot malware are pieces of software that lie dormant on a computer until the hacker gives it a command using a Command & Control server (C&C). At that point the bot malware will become active and take control of the computer to perform a certain task, assigned to it by the hacker. One controlled computer is called a bot and a collection of controlled computers are known as a botnet.
Cryptojacker
This is a type of malware that uses your computer's processing power to mine cryptocurrency and generate profit for the hacker. Usually they target hundreds or thousands of computers so they can mine cryptocurrency very quickly and for a large profit.
KeyLogger
This malware records keystrokes on a computer and sends that information back to the attacker. Generally, this information is used to discover people’s usernames, passwords, PINs and other login information. It can also be used to obtain other personal information but that is less common.
RAM scraper
RAM stands for remote access memory, it’s a type of temporary storage location on a computer. A RAM scraper collects information from the RAM on a computer and sends that back to the hacker. This is very profitable for point-of-sale(POS) systems like a cash register because for a brief period they store credit card numbers unencrypted so by collecting that information a hacker gets access to credit card payment information that can be reused or sold to other people for profit.
Browser Hijacking
Browser Hijacking is when malware alters the way your web browser works to either redirect you to a website that the hacker wants you to visit or to steal your information from the cookies that your web browser stores about your online activity. A cookie is a small piece of data that your web browser generates as you browse the internet. That’s how websites are able to remember that you are logged in, save your shopping carts, recommend products to you based on your search history etc.

