How An API Misconfiguration Can Lead To Your Internal Company Data
How An API Misconfiguration Can Lead To Your Internal Company Data

I came across this last year while doing reconnaissance for a bug bounty program, I assumed it was just another API which was meant to be public, but after digging deeper I found that a particular program was using the admin API key instead of the public search key, this led me to finding a large amount of internal documents for security policies, business operations and even slack messages.
After finding the same misconfiguration on a few sites I bought a dataset that contained 20k+ hosts which were using algolia, where i kept finding the same misconfiguration & sensitive information being leaked through the API.
What is Algolia
Algolia is a search API that powers the search function of over 50,000 sites, the Algolia API lets you set custom search suggestions where it uses a company defined index that is filled with content to be searched through. If the API is misconfigured and has the “listIndexes” permission this allows you to view all indexes that are available, sometimes this has included sensitive internal company documents, such as security policies and how to connect to VPN & internal systems.
I also found documents relating to company business operations and personnel policies. There are other permissions which can also be damaging, the “editSettings” permission allows you to define javascript which is ran when search is used, as you can imagine this can be quite dangerous for a large site with a lot of traffic.
How To Use
The API is a simple REST API and the applicationID and key are within the source code - as they are meant to be public (but only with the search permission), the keys can also be found within mobile applications, sometimes you might find a higher privileged key in the mobile app.
You can view the permissions that a key has by capturing the search request or looking for “applicationID” in the source then sending a GET request to
https://APPID-dsn.algolia.net/1/keys/APIKEY?x-algolia-application-id=APPID&x-algolia-api-key=APIKEY
This will return the permissions the key has in a json format. If the API is configured correctly it should only return the “search” permission or the key will be base64 encoded which means that its a "Secure Key" and you are unable to list permissions.
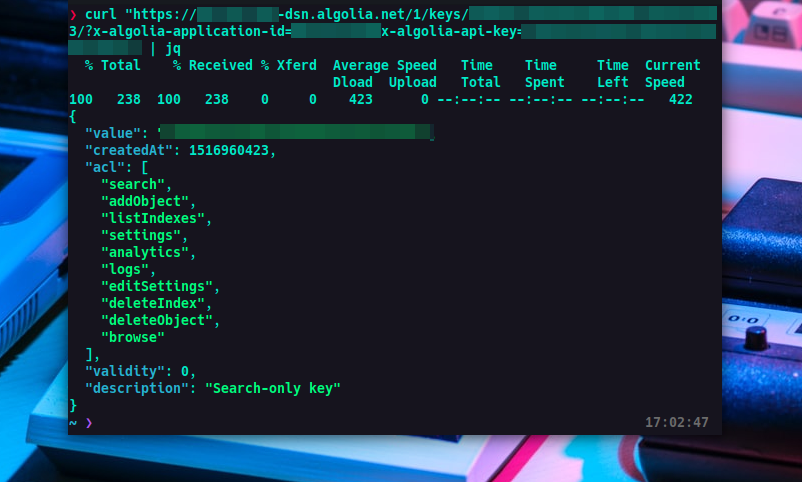
A list of permissions and other endpoints can be found on https://www.algolia.com/doc/api-reference/api-methods/get-api-key/
The most damaging permissions are
-
addObject: Allows adding/updating an object in the index. (Copying/moving indices are also allowed with this permission.)
-
deleteObject: Allows deleting an existing object.
-
deleteIndex: Allows deleting an index (will break search completely)
-
editSettings: Allows changing index settings. - this also allows you to run javascript when the search is used.
-
listIndexes: Allows listing all accessible indices.
-
logs: this will allow you to view the search logs, which can include IP Addresses and sensitive cookies.
Impact
After identifying other sites which were using Algolia I discovered many of them shared the same misconfiguration and the most dangerous permission is the "editSettings" permission which allows you to set the JavaScript which is run when the search feature on the site is used.
For a large site with hundreds of thousands of daily visitors, this would've allowed an attacker to inject their own malicious code for stealing credentials, card information etc. I've also found companies who are using the search only API key in their site but are using the admin API key in their mobile apps.
XSS can be achieved with this request - if the key has the "editSettings" permission.
curl --request PUT \
--url https://<application-id>-1.algolianet.com/1/indexes/<example-index>/settings \
--header 'content-type: application/json' \
--header 'x-algolia-api-key: <example-key>' \
--header 'x-algolia-application-id: <example-application-id>' \
--data '{"highlightPreTag": "<script>alert(1);</script>"}'
I was curious as to what was causing so many developers to make this mistake as by default Algolia generates a search only API key for you to put in your sites. Then i saw this while i was browsing the documentation
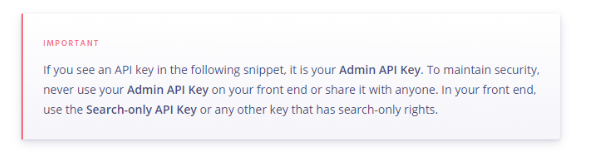
That's right, it’ll handily include your admin API key for you, in example code snippets, so you can copy and paste directly to your site, how thoughtful.
I’ve reported this to around 100 companies so far, including a large social platform, a large server hosting company & multiple large clothing stores. Sadly I can't disclose names yet as these were private programs.
How to Fix?
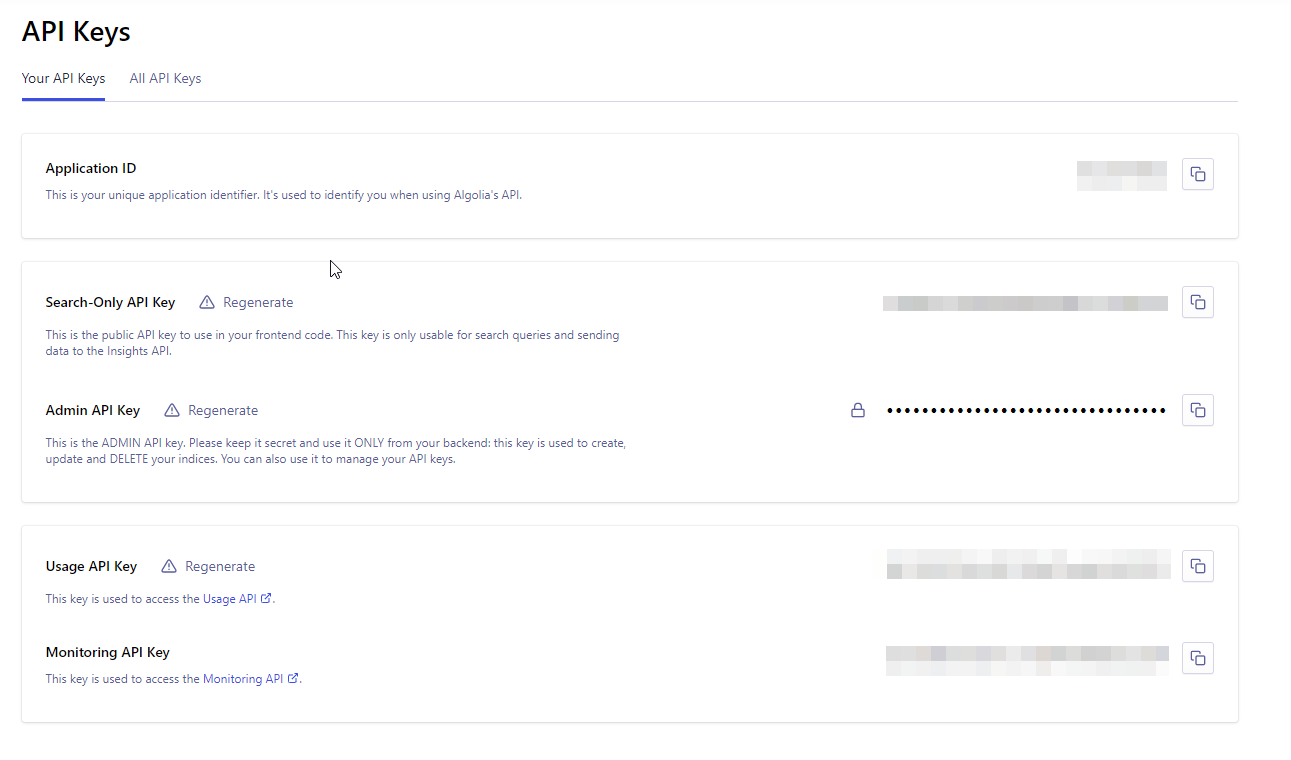
In the Algolia dashboard make sure your search only key is a search only key by checking it only has the “search” permission, if not revoke the key and generate a new search only key. Algolia also has a feature to generate "Secure Keys" which may be worth exploring.
Mentions

