Armor Up Where It Counts
Secure your organization where it counts the most by leveraging a World War 2 statistical analysis model.

During World War 2, statisticians and analysts studied the planes that returned from battles. While some experts wanted to reinforce the areas that were shot up, others - who won the argument - wanted to reinforce particular areas that weren't shot. The conclusion was that the bullet holes of the planes that returned meant that those areas could be shot and still allow the plane to return, while the evidence demonstrated that certain spots missing the holes were the areas that, when shot, caused planes to go down.
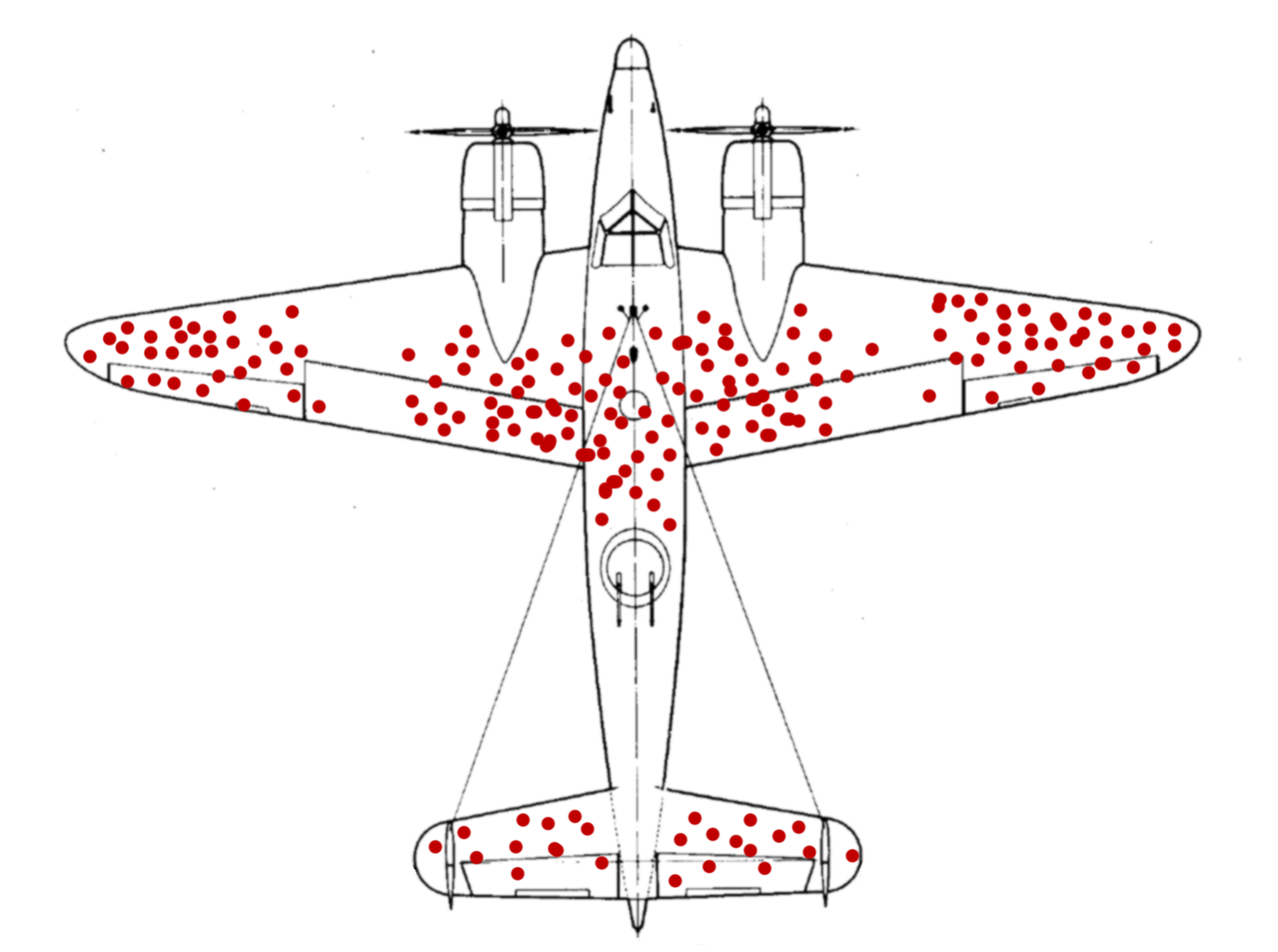
It's called Survival Bias - studying survivors, instead of focusing on why others don't survive. This same idea can be applied to infosec - focus on the reasons that companies were breached, rather than focusing on those who haven't been compromised.
A few years ago, I gave a presentation in which I summarized several of the largest breaches. One thing almost all of them had in common - the victims lacked security oversight in at least one of the foundational security areas. They lacked protection in the areas of 2FA, vendor management, updated server patching, phishing/social engineering, password protections, insecure S3 buckets, and SQLi - all foundational security concepts. Some of the attacks were by nation-state attackers (e.g., Sony), but even the Sony breach was assisted by the then-CEO's password being Sonyml3.
Very recently is the example of the February 5, 2021 hack of the Olsdmar water treatment facility in Florida. What were some factors in the breach? 1) Windows 7 2) one shared password for Teamviewer, and 3) no firewall. While it could have been the work of a nation-state, it could just as easily be a friend of one of the workers who shared the password, and also had a Shodan account.
With the informal analysis of my past presentation plus an informal review of recent breaches, I'm presenting an informal list of areas where organizations might want to focus on shoring up their security efforts. I don't discount the need for orgs to continue to study complex issues like the recent Solarwinds breach, nor do I hint that orgs should refuse to prepare in some way (e.g., Incident Response Plan, Risk Analysis) for serious and complex attacks such as APTs.
Rather, my intention is that the less complex security issues are ones that will certainly be attack vectors for all orgs. This is because it's much easier for an inexperienced attacker to compromise credentials, or to trick someone to install ransomware, than it is for someone to fund a nation-state attack. Before focusing on protecting against North Korea, or SMS cloning, or 2FA hijacking, I recommend ensuring that these aforementioned threats being addressed seriously in your organization.
For further consideration: according to the 2020 Verizon Data Breach Investigations Report (DBIR), 5 of the top 7 data breach threat sources are: phishing, password security, malware, data handling, and privilege abuse.
You can download the DBIR here, after providing basic contact info: https://enterprise.verizon.com/resources/reports/2020/2020-data-breach-investigations-report.pdf
Here's the list of foundational concepts, and some things to think about in addressing the problems.
Easy password - Use a scheme, use a password manager, get ideas online. Whatever you choose, make it a really tough password and put it in a place where it's secure and backed up. We have the technology!
Default username and password - To the uninitiated, this seems a really easy one to address. But with the rapid proliferation of technology, there are a tremendous number of places where this needs to be managed. And when that new tech comes in, there's often a rush just to get it set up, and that plan to change the password and write it down later gets forgotten. The recent Solarwinds finding that some update servers used "password123" is a perfect example. I'm not laying blame on any particular party there (which brings up the bigger question of "who's responsible?"), but it remains that simple password has caused an unbelievable amount of harm and introduced a herculean task to address worldwide.
Lack of Least Privilege - Eliminating this is technically fairly easy to achieve, but it's one of the hardest to deploy. This is because A) taking away privileges is a pain to pull off, and B) when it's not planned well, there's a whole lot of people calling you to install things that should have been allowed already.
- Weigh the risks of your network, how your computers are connected (e.g., are they all just connecting to Google Docs? Or are they on a connected LAN?), and other connections, such as WiFi. Imagine a scenario where one computer gets a virus. If your computers can talk to each other, and can connect to your servers, and they all are able to install with their credentials, then there could be a heap of trouble awaiting from that one infection.
Lack of 2FA - 2FA/MFA can be expensive, finnicky to maintain, and upsetting to users. This protection has great leverage due to its balance of setup and usefulness, but it can cause a great culture change in a company and cause administrative headaches if not done properly.
These previous four (4) make it relatively easy for a criminal to perform lateral movement and privilege escalation.
Phishing/Social Engineering/Ransomware
- Phishing - we all know it. On the non-destructive side, can inconvenience a computer by riddling it with spyware. On a more serious note, it can cause someone to send everybody's W-2. On the critical side, when it's a sysadmin who gets phished, and credentials are given, then the keys to the kingdom have been bequeathed to an unknown malefactor, and it's Game Over - "All your base are belong to us." Train employees on phishing, especially with ongoing phishing tests. There are free phishing tools available, so if you have no budget, see what you can do to get at least one pilot phishing test performed.
- I've placed these 3 categories together because they all pretty much stem from an employee getting tricked and clicking on something that they shouldn't.
Non-https
- Just get that SSL (technically TLS) cert.
- If you're looking to better position your certificate's trust factor, here are 4 CAs that can provide that higher level of trust that may be useful in garnering business with large companies:
- Entrust
- Digicert
- GlobalSign
- QuoVadis
Lack of monitoring and alerting
- Whether it's built-in, automated, requiring an upgrade to achieve it, manual review, or whatever you use - start with something and then improve. An imperfect something is better than a perfect nothing.
Open database/S3 bucket
- It's easy to go through the news to find out how many times we see "a third-party developer left the database open to the internet." And many times it's an S3 bucket. This is no dig at all against Amazon. S3 is an amazing service, and is a great resource for developers. But the danger is that the great development skill might not include secure systems administration. The high number of breach reports due to this precise lack of due diligence and due care is evidence that it is still a problem.
- Check to see if it's part of your contract to do some level of approved pentesting against the service to confirm the state of the service(s).
Vendor Management
- This is related to the previous security layer. Institute some sort of formal review of your vendors and suppliers so that your company has done some prudent research of those who provide critical services.
SQL Injection (SQLi)
- Use Burp Suite, use a third-party, use nmap - use something to test if those fields allow SQL commands, and if the data input is sanitized.
Updated Tech
- Even getting the update on your project list, with a project management and implementation plan, can go a long way to getting this accomplished.
- Use some form of calculation to determine what the cost of a breach vs. the cost of mitigation of the breach.
- E.g., "It will cost $10,000 to update and secure this tech, vs. the $10 million in GDPR fines that will be leveled against us when we get breached."
There are undoubtedly factors I've missed, and some intentionally not noted, such as DDoS. There are so many services that have built-in DDoS prevention that it doesn't show up much often. While it's a threat that needs to be guarded against, it is very often auto-mitigated by the services we purchase.
And this is not meant to be exhaustive and conclusive. Rather, it's intended to focus on foundational aspects of security. In the search to protect against the exciting and marvelous attacks, don't neglect the areas in the armor that are known to be weaknesses.