Bug Bounty Insider
RyanDeveloping takes us on a journey of discovery into the wonderful world of Bug Bounty Programs. Where we learn about the history, best platforms, and how you can get started. Ryan also interviews members of the community about their views.

Bug bounty projects have been around since 1983 and are viewed as a route for common way white hats to reveal vulnerabilities to organizations. Seeker and Ready started the first bug bounty program ever in 1983 for their Versatile Real-Time Executive working framework. The greater part of the vulnerabilities that are introduced are being sent through email to an organization in which the organization will at that point approve the data.
There are a couple of bug bounty platforms going nowadays known as HackerOne or Bugcrowd. Bug bounty is for everybody who is trying to procure benefit off of cautioning organizations of their security blemishes and anybody can learn with fundamental information of how to break a whole framework. In this article I will meet a digital security research gathering referred to as 0Rapture as I have a bunch of inquiries to pose about present day security.
Who are 0Rapture and what do they do?
0Rapture is a private cyber security research group composed of four to five members currently seeking web security asylum for companies who may have left a few bugs laying around. The current members are: Overpwn, PromeDNS, Deathwish, Nostalgic, and Citadel. The mentor of the group being Overpwn he makes sure all of his team members learn from their mistakes and earn some sort of potential profit bug bounty offers. 0Rapture being invite only new members must go through a series of questions and maybe a possible test before joining. Overpwn says
Depending on what they already know and what career path they wish to go down some people will find Network Pentesting boring, but it all depends on the person. But this can range from the basics of networking all the way up to exploitation of pre-made setup machines & labs for beginners to test on.
The 0Rapture team has disclosed vulnerabilities from Shopify, a very popular fast food chain, a popular CMS, and the official portal of the Dutch government website. 0Rapture is a white hat group focusing on teaching any studies that happen to join the group. You can often see groups like these all over social media, but 0Rapture is a bit more private with their work. The individuals impart through Discord, however individuals who need to join or submit an inquiry can contact the gathering by email at the present after e-mail address: 0[email protected]. You could say this team is somewhat similar to the privately owned & publicly distributed SynackRedTeam.
A more detailed view on the founder of the 0Rapture team being that he is an 18 year old security researcher from the United Kingdom. He developed most of his skills in Network Security and Web Application Penetration Testing. He’s found the biggest bugs in WordPress and Shopify and in his spare time he likes to participate in Capture the Flags (CTFs). He enjoys helping companies, clients, and anyone with security flaws improve their security. He started building computers at a young age back in 2009. Back in 2010 he started learned Python and now he knows more languages such as Python2 & 3, PHP, C++, C#, and obviously HTML, CSS, and Javascript.
Citadel of the group is second in command of 0Rapture and has put in the most work as far as bug bounty research and disclosing vulnerabilities. Citadel is the person whom contacts individuals that would like to join and is also the individual who submits information to Bug Bounty companies. He is as of now 19 from the United States of America and is only a cool person to stay nearby and gain from when all is said in done.
Other Bug Bounty Communities & Groups
Another bug bounty company & platform catching people’s eye is HackerOne. HackerOne has over 100,000 people registered on it’s bug bounty website and of those members registered there are over 3,000 pentesters and vulnerability hunters. HackerOne gained more user interaction and traction after partnering with Twitter to form a bug bounty for Twitter allowing users to submit vulnerabilities through HackerOne and have Twitter correct and fix the errors. The CEO of HackerOne is recognized as Mårten Mickos. The number one most noticed security researcher on the HackerOne platform is Santiago Lopez. Santiago has made himself a millionaire off of finding vulnerabilities company left laying around. After reporting them to HackerOne he would receive some sort of payout after HackerOne has contacted the company themselves. Santiago has made history and a video has been published about his life displayed on YouTube.
The second bug bounty platform would be Bugcrowd which is likewise outstanding and has a large number of clients enrolled on its site domain. Most occasions when presenting a vulnerability to Bugcrowd they should obviously approve the weakness before unveiling it to their rundown of the open set vulnerabilities payout list. Bug Crowd was established by Ashish Gupta who is as outstanding, yet has footing on SEO and Google adwork. Relatively few individuals know this yet Bugcrowd has a Discord server accessible for anybody and everybody to join into. I'd state BugCrowd is the second best positioned bug bug bounty platform despite the fact that they have a one of a kind and conveniently changed method for announcing security vulnerabilities.
Thirdly, one of the most known bug bounty communities in the world is the Synack Red Team. Synack are composed of a community of only a couple thousand researchers. The group is invite only, even though you you can still sign up and register on their website. Synack was a community and platform built by hackers for hackers. What I mean by this is people with prior skill have decided to fabricate a new community & platform for future legal hackers. Synack has a blog where they post most of their updates, events, and guides and anyone is allowed to take a look, but not all will be able to join the actual team.
The last not all that perceived bug bounty platform would be HackenProof. HackenProof is to some degree known around the Bug Bounty Community, however isn't as global as what it is intended to be. Would it be able to be that the organizations are contending or might it be able to be that they simply haven't promoted to such an extent? We will genuinely never know until they begin to do both of those two things. Back regarding the matter of HackenProof; HackenProof has more than 1,000 bug bounty scientists and every one of them are amazingly talented. They report vulnerabilities day by day and ensure everybody gets a payout. The thing diverse that isolates HackenProof from different stages is that they really offer a demo for organizations to present a pentesting structure. HackenProof will at that point connect with the organization and addition experts to test their administrations.
How to get involved
In the event that you are looking for assistance about how to turn out to be increasingly associated with bug bounty researcher you ought to likely ask somebody who is most experienced and waiting around on Twitter. In any case, if that doesn't help spots like HackerOne have a help group accessible and ready to help your inquiries. You would prefer not to stroll into the bounty world not recognizing what to do, else you will get off-track. In general, on the off chance that you are hoping to apply to this mystery gatherings or networks, it's straight forward! Simply adhere to their recommended and guided directions and have a go at it. I guarantee you won't get a handle on left since this network is brimming with comfortable faces and individuals with earlier information about doing security investigation.
What is the Outcome of Bug Bounty Research?
I figure the genuine result of security specialists doing bug bounty research is picking up a wellspring of benefit from the organizations that will acknowledge the bounties do play out a payout. Despite the fact that a portion of these payouts are low, if you somehow happened to like locate a Remote Code Execution on the server side you'd presumably be paid well over a thousand dollars. Not all programmers can profit on stage like these however. For the basic actuality a portion of the vulnerabilities have been faked, or the individual doesn't gain enough learning.
Security Questions and Responses
Question: What is the biggest vulnerability you have found and how did you deal with it?
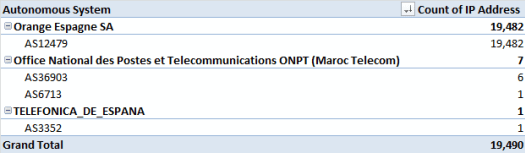
Answer: We detected opportunistic scanning activity attempting to steal the credentials from vulnerable ADSL modem/routers. Immediately we notified the service provider (Orange) and they corrected the issue within three days. This disclosure took place sometime over Christmas and there was a write-up done. It was great to see corrective action taken swiftly to protect users.
While Bad Packets currently isn't doing any type of bug bounty work they still provide cyber threat intelligence about IoT botnets and malicious malware over their social media profiles and website.
Association: Mr. Mursch is co-founder of Bad Packets and is a clever security analyst whom is revealing security vulnerabilities day by day.
Question: What does it take to be able to become the top researcher?
Answer: Becoming a top researcher on Bugcrowd takes dedication and hard work, all of that work can be done from home and completely remotely. Our ranking systems at Bugcrowd are based on your activity on our platform, particularly the accuracy and the severity of the bugs you submit. If you're often finding highly critical or large impact bugs, and you're accurate in that assessment, you will go far on Bugcrowd.
- Sam Houston - Senior Community Manager at Bugcrowd
Association: Mr. Houston helps to build, grow and maintain the Bugcrowd researcher community.
Question: Which bug bounties vulnerabilities pay the most and what is it like being a bug bounty hunter today?
Answer: Has its ups and downs really it can be fun and depressing when you don't get paid as much as you hoped or when and if Triage don't understand the issue. RCE's pay the most because I gotten like 25,000 from Snapchat before. I found an exposed Kubernetes cluster and had full control over it which it had network access to their internal systems.
In addition Random Robbie has disclosed 31 vulnerabilities to Bugcrowd and has a decent 91.18% accuracy rate on their website.
Conclusion
Doing bug bounty research has come a long way since 1983. Not all people are happy with their payouts, but if you were to find a vulnerability with a big company you'd receive a pretty beneficial payment. There are tons of public & private groups to join into. And all you have to do is enter a submission for the private ones. In this article I was looking to persuade multiple people to get into bug bounty and alert the people who knew less about the subject. In other words I hope you all find the correct path you are so dearly striving for & succeed in those courses.
The amazing image in this article is called Bobba Fett and is by Nicholas Roberts

