Cloudy With A Chance Of Downfall - A Look At Cloud Access Security Brokers
Cloud based applications bring with them a number of new risks. Is your security strategy taking them into account?

I used to be very "anti-cloud". When all the cloud based services first started popping up, my only thought was "why would you want to risk storing your data in someone else's data centre"? As a security guy who wanted control and visibility over everything, it just seemed like a really bad idea. Doesn't look like the rest of the world felt the same way though and cloud services took off in a big way!
Fast forward a few years and the way we all consume IT services has changed drastically. Most organisations use cloud based services in some way on a daily basis. Office365, Salesforce, Dropbox, Slack, Spark, Docusign - the list goes on. This may be because you've embraced them and authorised their use in your company, or because your end users have just decided to use them anyway - so called "Shadow IT".
You can no longer just ignore the use of cloud based applications - they are here to stay. And to be honest, why would you ignore them? Cloud based applications bring with them a huge number of benefits, not least increased flexibility, reduced management overheads and reduced costs.
I still feel strongly there are certain exceptions where data should not be sat in someone else's data centre, but on the whole cloud based applications have helped change IT in a really good way. Beware though, not all clouds have silver linings!
New Risks
Along with the increased flexibility come a number of new risks and attack vectors:
- Unauthorised access - Cloud based applications are typically accessed over the Internet and are not often locked down to specific source IPs. This means an attacker no longer has to be inside your network to potentially gain access to your data. This risk also extends to the company who is providing you the service - do their staff now have access to your data as well?
- Visibility - How do you track what your users are doing whilst using cloud applications? Are disgruntled employees downloading sensitive files before leaving your company? Are people uploading files they shouldn't be to cloud services?
- Unauthorised File Sharing - Lots of cloud based applications provide users with the ability to share files and resources with others. This can be great, however how do you know users aren't maliciously or inadvertently sharing data that they shouldn't be?
- Malicious or Risky Applications - There are numerous third-party applications out there that enhance functionality or add additional features and they often use an authorisation standard known as OAuth. However malicious applications can also levy OAuth in order to gain access to your data. Whether you realise it or not, you've likely come across OAuth before. Do any of the following look familiar to you?

How do you know which applications your users are authorising to gain access to your corporate data?
Traditional on-premise solutions such as firewalls, proxies and SIEM solutions aren't enough to deal with these new threats. Users are now often able to access corporate cloud resources from anywhere, so they become ineffective at protecting your data. That isn't to say they aren't still required for your corporate network, but they can't protect everything.
With these points in mind, if you aren't taking steps to secure cloud based applications then you are potentially leaving huge gaps in your security posture. A lot of cloud based applications already provide tools to address a number of these problems, but not necessarily all of them. And with so many different cloud based applications this can become cumbersome to manage. So what other options are there?
Cloud Access Security Brokers
Cloud Access Security Brokers (or CASB if you love an acronym!) are policy enforcement and monitoring solutions for cloud based applications. They help you to regain some visibility and control over your users activities and provide you with a single pane of glass for management.
CASB solutions can reside on-premise or in the cloud and broadly fall into one of two categories:
- Inline/proxy based
- API based
Both approaches have their own pro's and cons. Inline/proxy based solutions work as the name suggests - by funneling user traffic through on-premise or cloud based appliances. They provide much greater control of data flow between end users and cloud applications and allow you to enforce Data Loss Prevention (DLP) policies much more effectively than API based solutions. They do however require the user be behind on-premise device or have an agent installed on their endpoint.
That's all well and good for corporate devices, but it doesn't help address the problem of users accessing resources from personal unmanaged devices.
API based solutions behave very differently. User to application traffic continues to flow directly to the cloud service being accessed. That includes both corporate managed devices and personal unmanaged devices. API based CASBs don't rely on being in the data path, instead they query the cloud application directly using publicly available APIs.
This approach allows the solution to gather information on what has been going on without actually sitting in the middle. This is great for ease of deployment and for gaining more visibility, but doesn't provide as effective control over data. Sure, you can still implement DLP type controls, however these are (in most instances) going to be retrospective activities to delete files that shouldn't be there, rather than preventing them from getting there in the first place.
There are plenty of vendors providing CASB in the market now, some of the more prominent names include:
- Skyhigh networks (now part of McAfee)
- Cisco Cloudlock
- Netskope
- Symantec
Being that I work for a Cisco partner it is no surprise that I am most familiar with Cisco's Cloudlock solution. I don't want to turn this into a sales pitch nor do I want to go into loads of detail, but I do want to take a quick look at some of the useful information you can get from it.
Cisco Cloudlock
Cisco Cloudlock falls into the camp of being an API based CASB. It integrates with cloud based applications using their APIs and uses rule and behaviour based policies to identify and alert you to threats as they occur. Cloudlock can help you answer questions in a number of key areas, including:
- Users/Accounts - Have accounts been compromised? What are users doing in the cloud based service? Are any users downloading lots of data (data hoarding)?
- Data - What data do I have stored in the cloud application? Does any of the data violate corporate policies or regulations (e.g. credit card details, passwords).
- Applications - What applications are users granting access to our data? Are they risky applications? Are they authorised corporate applications?
Cloudlock comes with pre-defined policies that allow you to detect and respond automatically to a number of these, but also allows you to define your own granular custom policies.
Let's take a look at a few examples from each of these high-level categories.
Users and Accounts
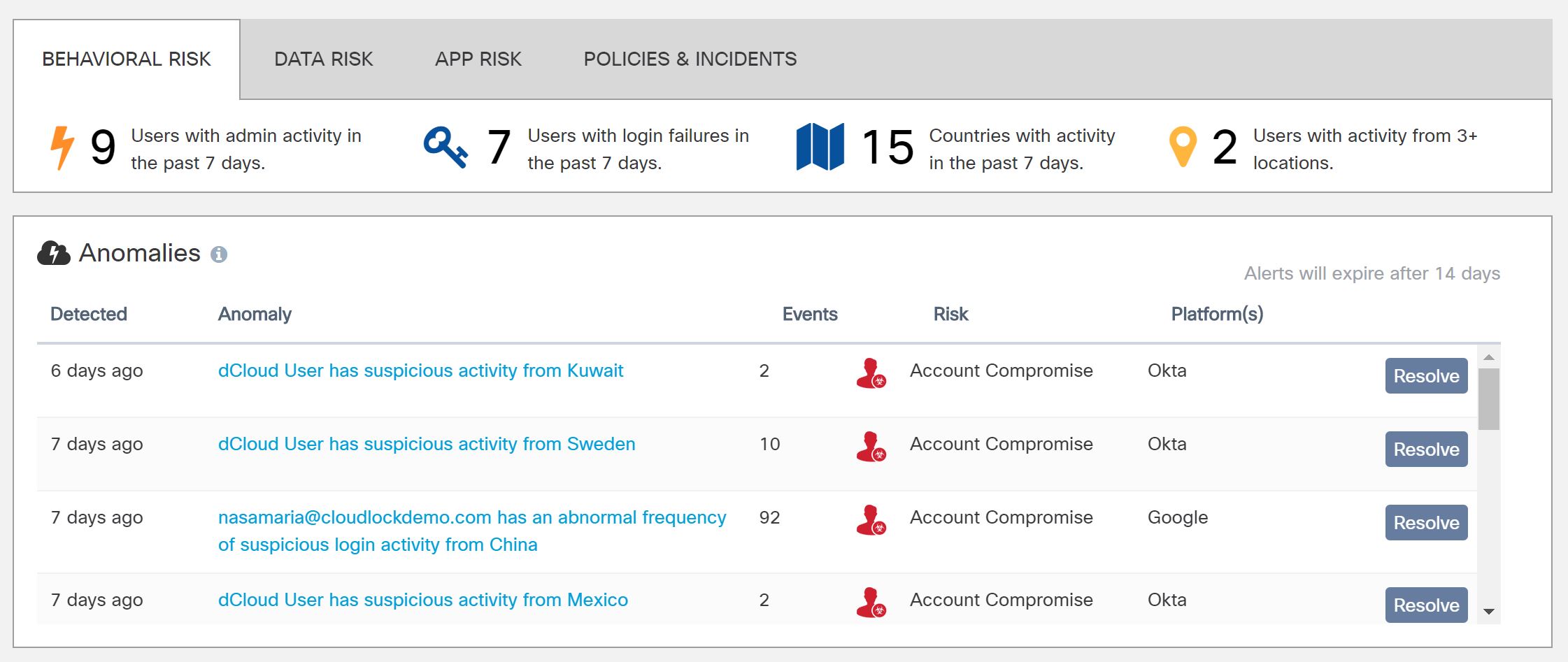
Suppose you have a user that always logs in to Microsoft Office365 between 8am and 6pm from your office in the UK. Then one day their login credentials are seen used in a different country, or perhaps the login occured at 11pm at night. These behaviours are significantly different from their normal behaviour and could be a sign of a compromised account. Granted, there may be valid reasons for the behaviour - but you can't check if you don't know about the incident in the first place! Cloudlock can flag up these type of anomalies for further review.
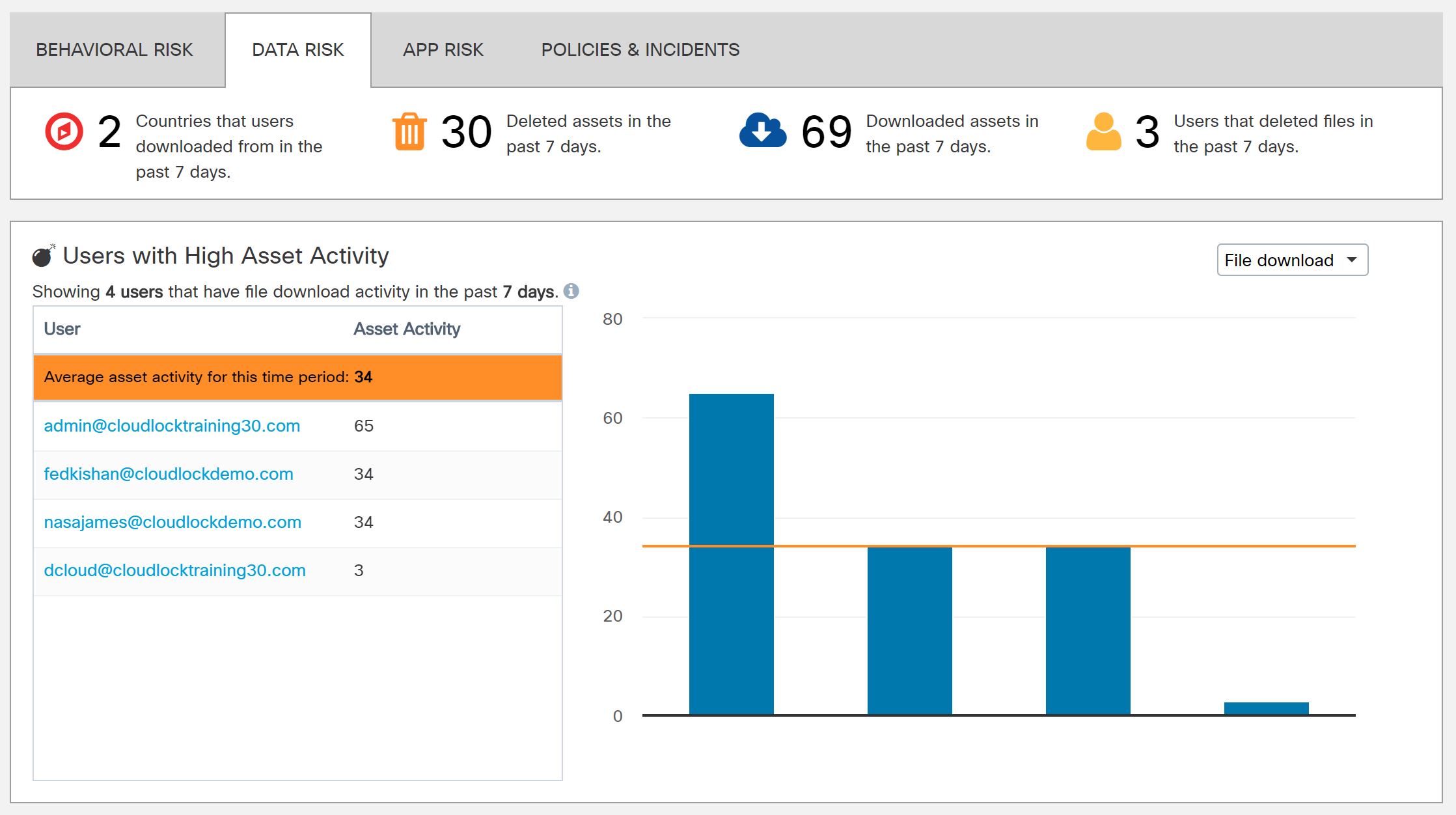
What about if you want to know if some of your users have been downloading or deleting large numbers of files (files are referred to as "assets" in Cloudlock). Again, this is something you can easily view.
Data
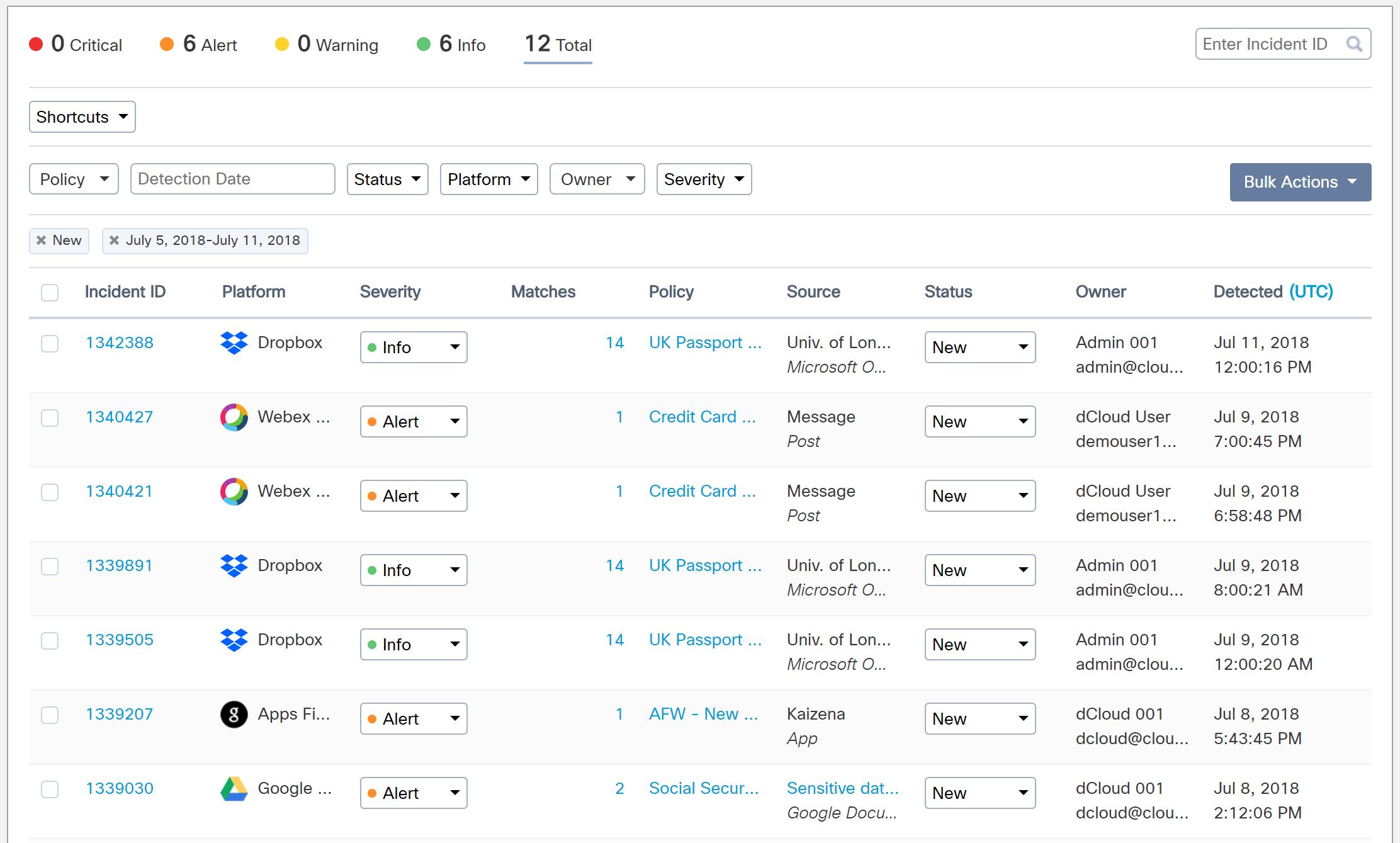
As touched on earlier - cloud applications can be great, but there are going to be certain types of data you aren't going to want to store there. One example of this could be sensitive information such as credit card data. This is something Cloudlock policies can alert you to. In the screenshot below you can see various different policies triggered (in relation to credit card numbers, passport numbers and social security numbers) as well as details of the "owner" (the user who uploaded the offending data) and platform it was found in.
Applications
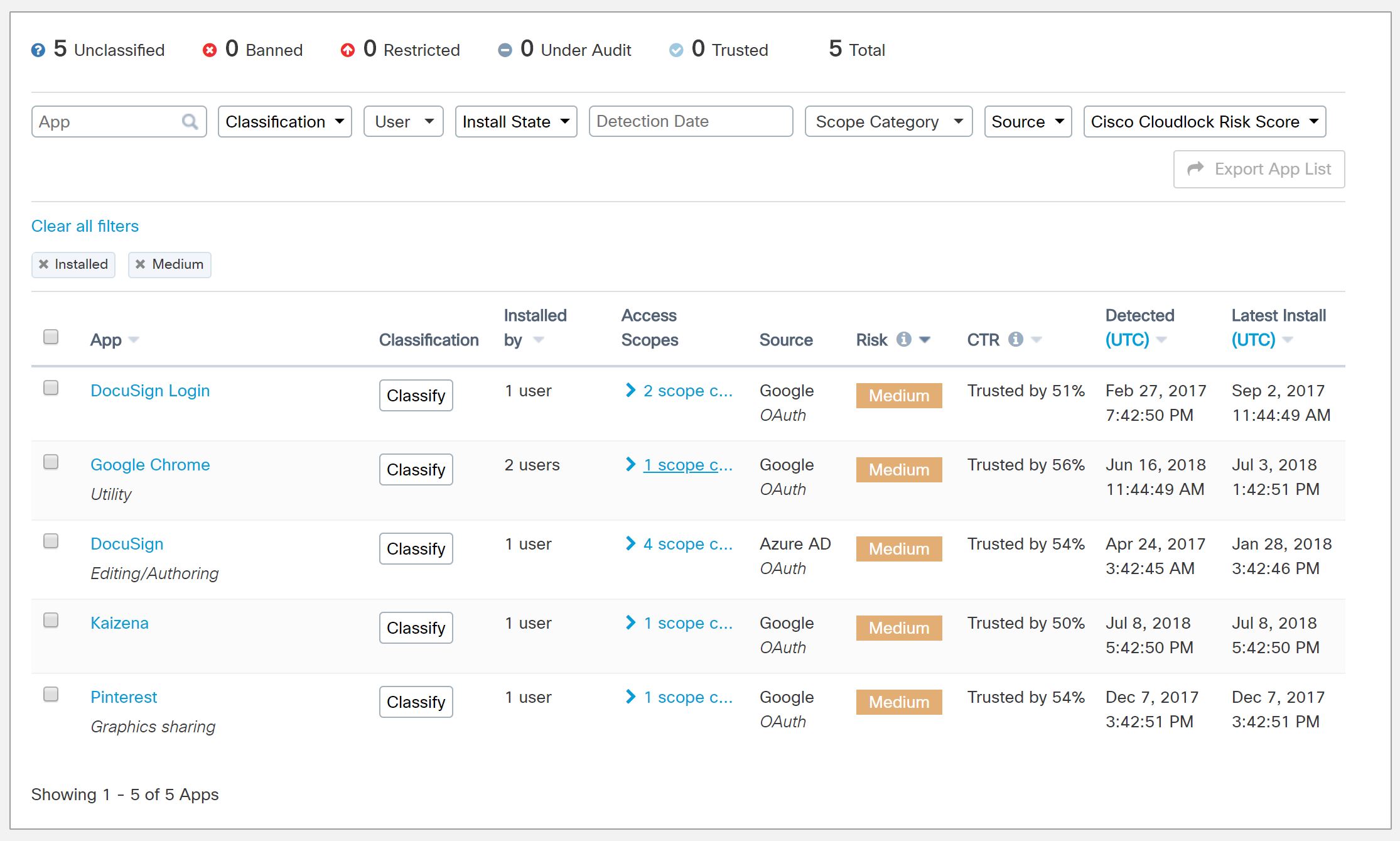
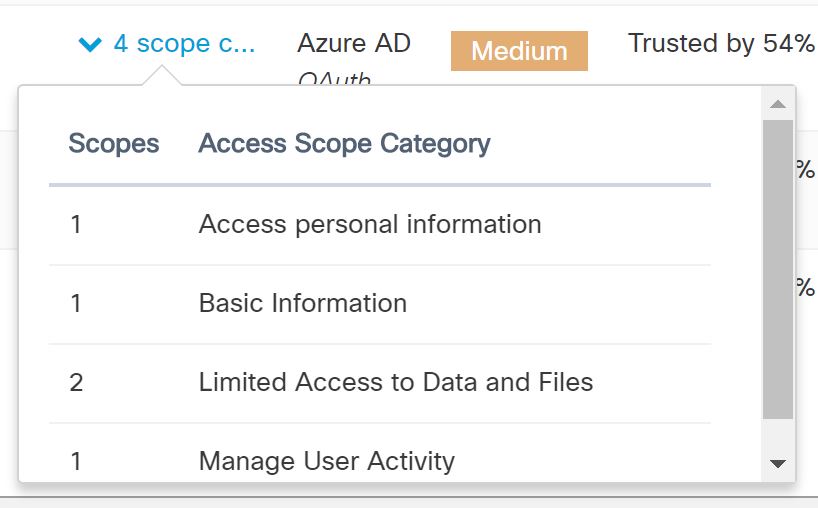
Cloudlock allows you to view which applications users have been granting access to your data. Applications are given a risk score by the Cloudlock team as well as a Community Trust Rating (CTR) by the Cloudlock user community. This allows you to review the applications that can access your data and decide if policy violations have occurred or not.
As you'll see in the screenshot below you can also drill down into the exact permissions the application requested. For example, if we take a look at DocuSign we can see the following.
Summary
There is a lot more that you can do with Cloudlock and CASBs in general. Hopefully this post has given you a bit of a taste of what is possible and the sort of information you can get out of the solutions.
Cloud based applications aren't going anywhere, neither are the additional risks that come with them. So if you're not already factoring these into your security policies then it is probably a good time to start thinking about it. There is no silver bullet and some risks are always going to be inevitable, but a good CASB solution can certainly help provide you much greater visibility and control.
Do you have any feedback, comments or tips on the solutions you use? Get in touch with my via my blog at https://mikeguy.co.uk or twitter @mike_sec_eng
Main Image Credit : The awesome piece of artwork used to head this article is called 'Bad Omens' and it was created by graphic designer Hurca.