Cybersecurity Yoga
Yoga is an ancient practice that helps achieve balance between mind, body, and soul. Learn how to leverage yoga to improve your cybersecurity defense.
Yoga or Yog, is an ancient Indian form of practices that helps in achieving a good balance between mind, body, and soul. Yoga gurus from India later introduced yoga to the West, through various forms such as "asanas" (meaning a specific posture of body). Yog, is now widely adapted as posture-based physical fitness, stress-relief and relaxation technique.
One such form of Yog is the "ashtang" Yog- meaning "Eight-Limbed Yoga", which features in the most recognized and ancient publication of - "Yoga Sutras of Patanjali". The benefits of practicing Yog and specifically the "ashtang" Yog are limitless and equally challenging.
With this background, through this article, we intend to outline the "ashtang" Yog for the Cyber-security world, the Essential Eight Maturity Model of the Australian Cyber Security Centre, which was recently revised with definitions of the maturity levels.
The Australian Signals Directorate’s Australian Cyber Security Centre (ACSC) has developed prioritized mitigation strategies, in the form of the Strategies to Mitigate Cyber Security Incidents, to help organisations mitigate cyber security incidents caused by various cyber threats. More details and source here.
The most effective of these mitigation strategies are known as the Essential Eight.
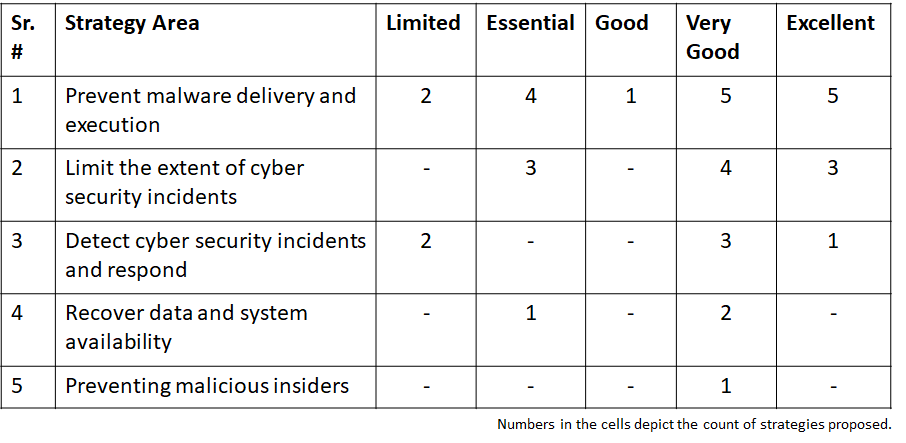
Prioritized mitigation strategies are classified into five areas as below:
- Mitigation strategy specific to preventing malicious insiders
- Mitigation strategies to recover data and system availability
- Mitigation strategies to detect cyber security incidents and respond
- Mitigation strategies to limit the extent of cyber security incidents
- Mitigation strategies to prevent malware delivery and execution
These five areas include proposed strategies/controls, and mapped against five levels of - Limited, Essential, Good, Very Good, and Excellent.
Now, let's look at what the "Essential Eight" strategies are:
- Application white-listing - One of the keys to secure the endpoints is to restrict executables to run. This can be achieved by implementing an application white-listing solution - on all workstation and servers. This includes executables, software libraries, scripts and installers from an approved set.
- Patch applications - This is one of the most painful, yet most important area for both IT and Security teams. Key considerations include 6.1) Security vulnerabilities are re-mediated within prescribed timelines 6.2) Outdated systems, applications are replaced with latest versions 6.3) Automated mechanisms are used to confirm and record the updates.
- Configure Microsoft Office macro settings - This area is often overlooked for business reasons, but is extremely critical for secure user experience. key considerations include - 3.1) Allow macros after seeking user approval and logging such actions appropriately 3.2) Allow signed macros 3.3) Block macros from Internet 3.4) Restrict users from changing settings 3.5) Allow macros to be run from trusted locations only
- User application hardening - This is a micro-focus area for all security teams, which often falls between the cracks. The framework specifically focuses on disabling the Flash content, web advertisements, Java, Object Linking and Embedding across web-browsers and productivity suite of applications.
- Restrict administrative privileges - Administrative privileges are one of the weak links in the cyber ecosystem. Restricting and monitoring these privileges should be a priority for any security team. Key considerations include - 5.1) Prevent privileged users from reading emails, browsing the Web and obtaining files via online services 5.2) Validate all requests for privileged access 5.3) Conduct frequent entitlement reviews for privileged user accounts 5.4) Implement the principles of least privileges and need-to-know.
- Patch operating systems - Pretty similar to Strategy #2
- Multi-factor authentication - They say, the only thing that lies between a user and an attacker is the "password", alternatively, the authentication information. In order to strengthen the authentication mechanisms, it is important to introduce multiple factors to authenticate users inclusive of standard users, business users, privileged users, remote users, etc. 7.1) Multi-factor authentication uses at least two of the following authentication factors: passwords with six or more characters, Universal 2nd Factor security keys, physical one-time password tokens, biometrics, smartcards, mobile app one-time password tokens, SMS messages, emails, voice calls or software certificates. 7.2) This authentication may further be extended to access critical systems and/or information.
- Daily backups - This is an important strategy area, but often overlooked by the security teams. Key considerations in this strategy include - 8.1) An inventory of important information, software and configuration settings 8.2) Medium for storing backups - non-rewritable and non-erasable manner 8.3)Retention time periods aligned to the organization, regulatory and legal requirements 8.4) Periodic full and partial restoration testing.
With these "Ashta" - eight essential strategies, security teams will be able to cover some of the latest attack vectors and reduce the exposure to cyber-attacks.