Playing In The Dark Corners Of Windows With Alternative Data Streams
In this article we look at the exploitation of ADS in the NTFS file system to conceal data secretly using the Stealth Alternative Data Stream, which cannot easily be detected.

In my previous article (https://www.secjuice.com/ntfs-steganography-hiding-in-plain-sight), we investigated data concealment technique inside Microsoft Windows NTFS file system by talking about how the ADS feature of NTFS file system can be exploited to conceal secret data stealthy inside it. In this article, we will continue our discussion of exploiting the ADS feature of NTFS file system to conceal data more secretly using modern type of ADS stream called Stealth Alternative Data Stream, which cannot be detected using any of the methods from my previous article.
Stealth Alternative Data Stream
Before saving any file or folder in the file system under Windows, the OS performs a check on the validity of the name using NT-style name rules. These rules, check for name and path length (255 characters’ maximum) in addition to checking if the pathname contains periods or any punctuation marks. In order to override the naming rule’s limitation we use the prefix \\?\ With file I/O, adding the \\?\ prefix to a path string instructs the Windows APIs to disable all string parsing and to send the string that follows it straight to the file system.
Windows already has a set of reserved names for its connected hardware devices that cannot be used to create any file or folder under Windows. These names are:
CON, PRN, AUX, NUL, COM1, COM2, COM3, COM4, COM5, COM6, COM7, COM8, COM9, LPT1, LPT2, LPT3, LPT4, LPT5, LPT6, LPT7, LPT8, and LPT9.
In order to create our Stealth ADS file, we will combine two techniques, the first one is forcing Windows to create a file with a reserved Windows name (See Figure 1) and then appending our secret ADS stream file to it (See Figure 2).
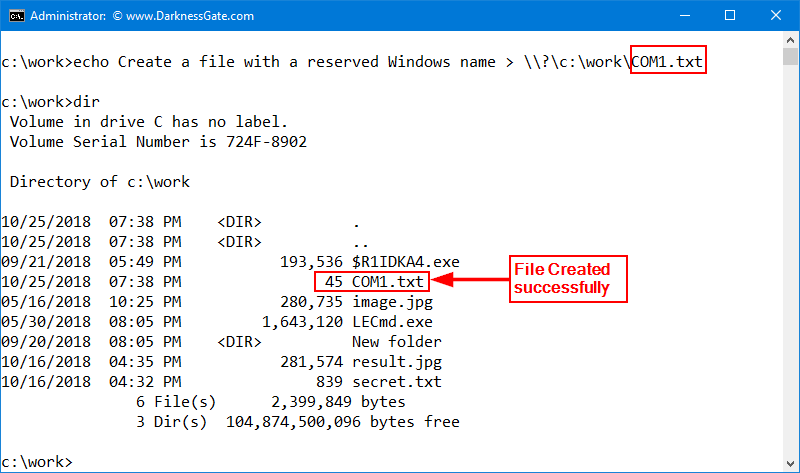
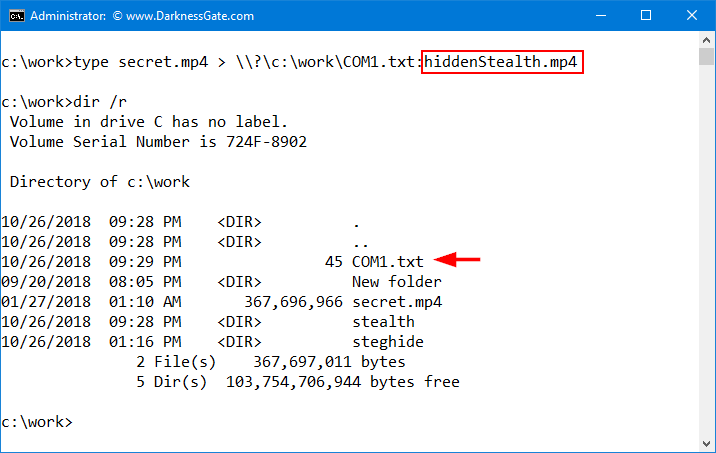
This approach allows users to create completely hidden ADS files that are very difficult to detect. Most ADS detection tools and DOS command (DIR /R) are not able to uncover streams appended to files with a reserved Windows name. The majority of personal antivirus software does not scan, stealth ADSs, which make them an ideal place to hide your confidential information. Malware can be concealed using this technique because it is difficult to detect.
How to detect Stealth ADS Files
The majority of ADS detection tools in addition to DOS commands such as (DIR) and (DIR /r) are not able to uncover stealth ADS files.
We test the following ADS detection tools; they were unable to detect Stealth ADS files:
1. Streams.exe (available from: https://docs.microsoft.com/en-us/sysinternals/downloads/streams
2. Ad spy (available from: http://www.bleepingcomputer.com/download/ads-spy/)
3. Stream Detector (available from: http://www.novirusthanks.org/products/stream-detector)
4. AlternateStreamView v1.55 (available from: https://www.nirsoft.net/utils/alternate_data_streams.html)
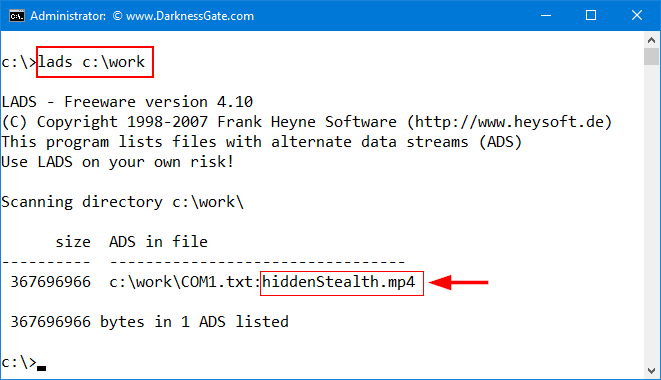
Only one tool was able to detect Stealth ADS files, LADS.exe (available from: http://www.heysoft.de/en/software/lads.php?lang=EN) please note its developer website is NO longer offer a download link for this tool, but you can still find it at the following location: https://github.com/codejanus/ToolSuite/blob/master/lads.exe(See Figure 3) for demonstration on LADS.exe ability to detect Stealth ADS files.
You can find more examples about concealing executable code in NTFS file system in the following locations:
- My awesome book on the subject Data Hiding Techniques in Windows OS: A Practical Approach to Investigation and Defense 1st Edition
- My awesome InfoSec portal with tutorials: http://www.darknessgate.com/security-tutorials/date-hiding/


