Funny Deadly Linux Strings Part 2
Security researcher Patrick Hoogeveen returns with part two of his series on deadly little Linux strings.

Hello folks, I'm back again with another post about funny deadly linux strings. If you remember my previous article (part one) on this subject, we covered how we can use escape chars to execute code that executes directly after decryption.
I noticed that on kali2021-3 payloads like the following could be used.
* e/c/h/o/ "id" | b/a/s/h/ $()
* /e/c/h/o "id" | b/a/s/h/ $() | e/c/h/o "ls -la" | b/a/s/h/ $()
* /e/c/h/o "rot47 payload"
So here we go again,
code execution directly
* e'c'h'o "id" | ""b""a""s""h"" $() & "e"c'h'o "ls -la" | ""b""a""s""h"" $()
* 'e'c'h'o "id" | ""b""a""s""h"" $() & "e"c'h'o "ls -la" | "b"a"s"h" $()
# rot47 decode code exec
* e'c'h"o" ":7 , QSt&xsQ ?6 _ . E96? 649@ Q!=62D6 CF? 2D C@@EQ
6I:E
7:" | \t\r '!-~' 'P-~!-O' | ""b""a""s""h"" $() & "e"c'h'o "ls -la" | ""b""a""s""h"" $()
Gunning For Root
Below in the first image we use a encrypted rot47 payload which pushes out of a bash check to run as root. Here we decrypt the rot47 payload and exec directly with a pipe and $() to exec it.
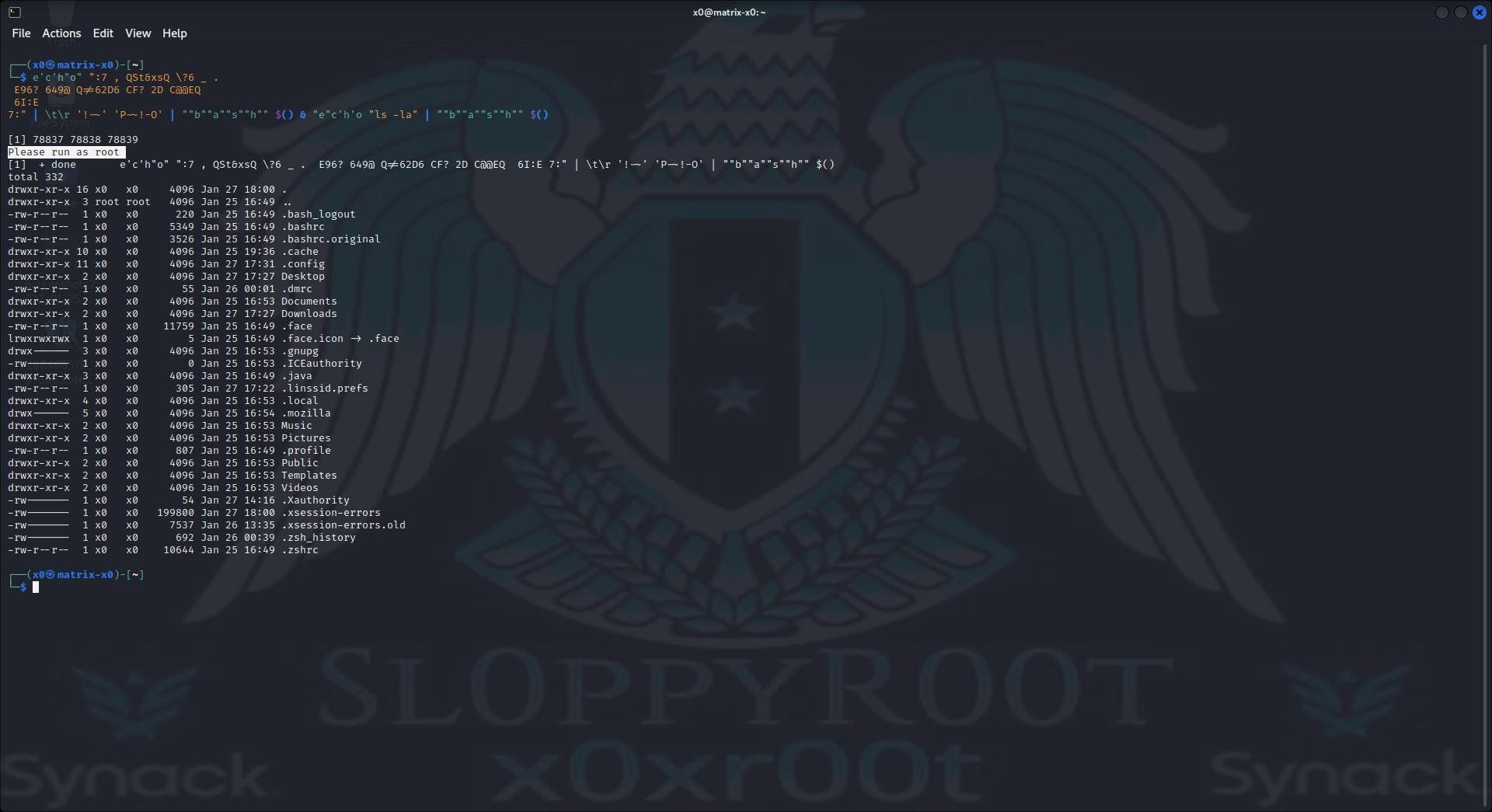
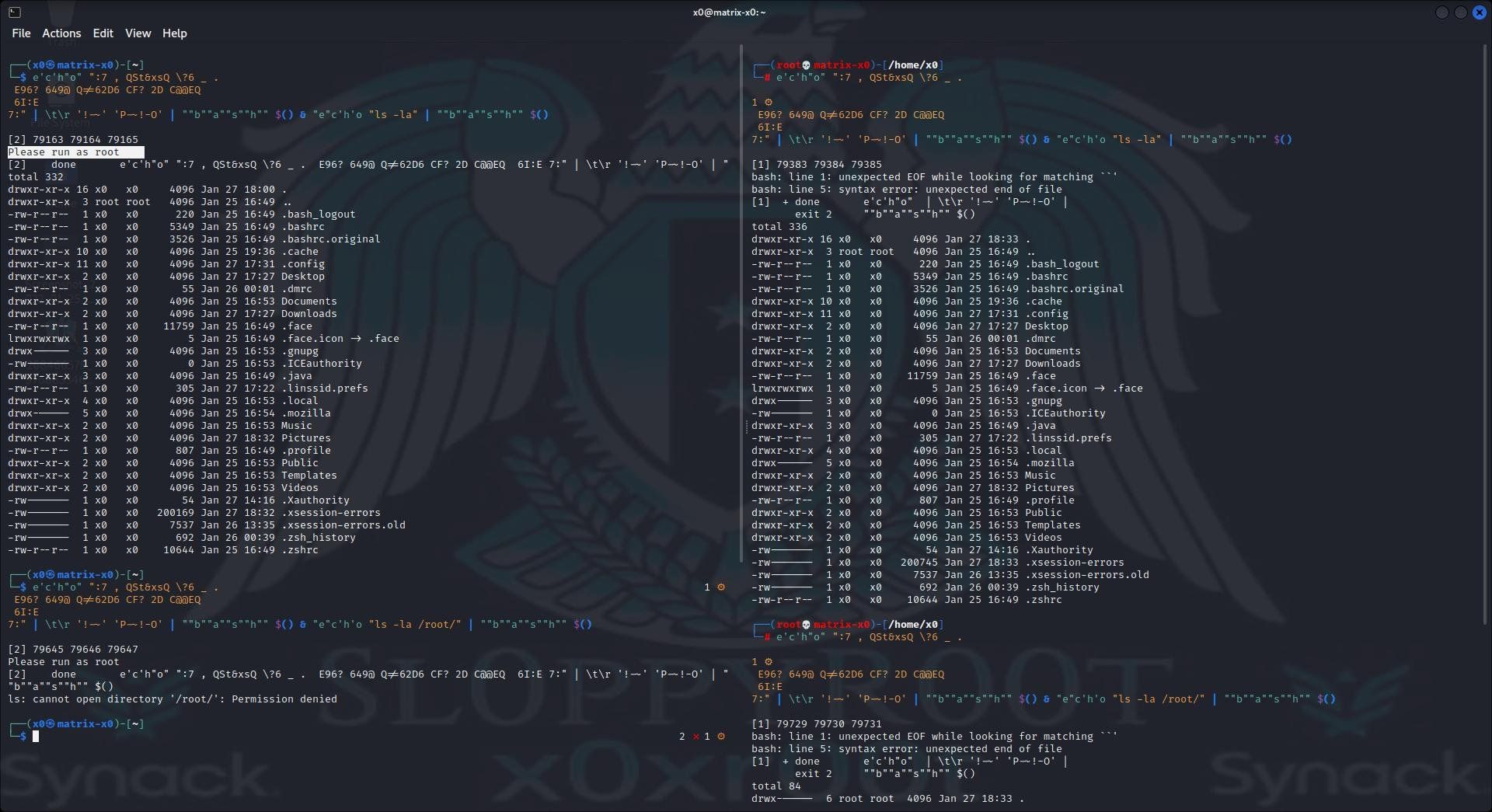
Below in the second image we use a encrypted rot47 payload which consist out of a bash check to run as root. Here we decrypt the rot47 payload and exec directly with a pipe and $() to exec it And we successfull do that in the top right slide as root user. :D
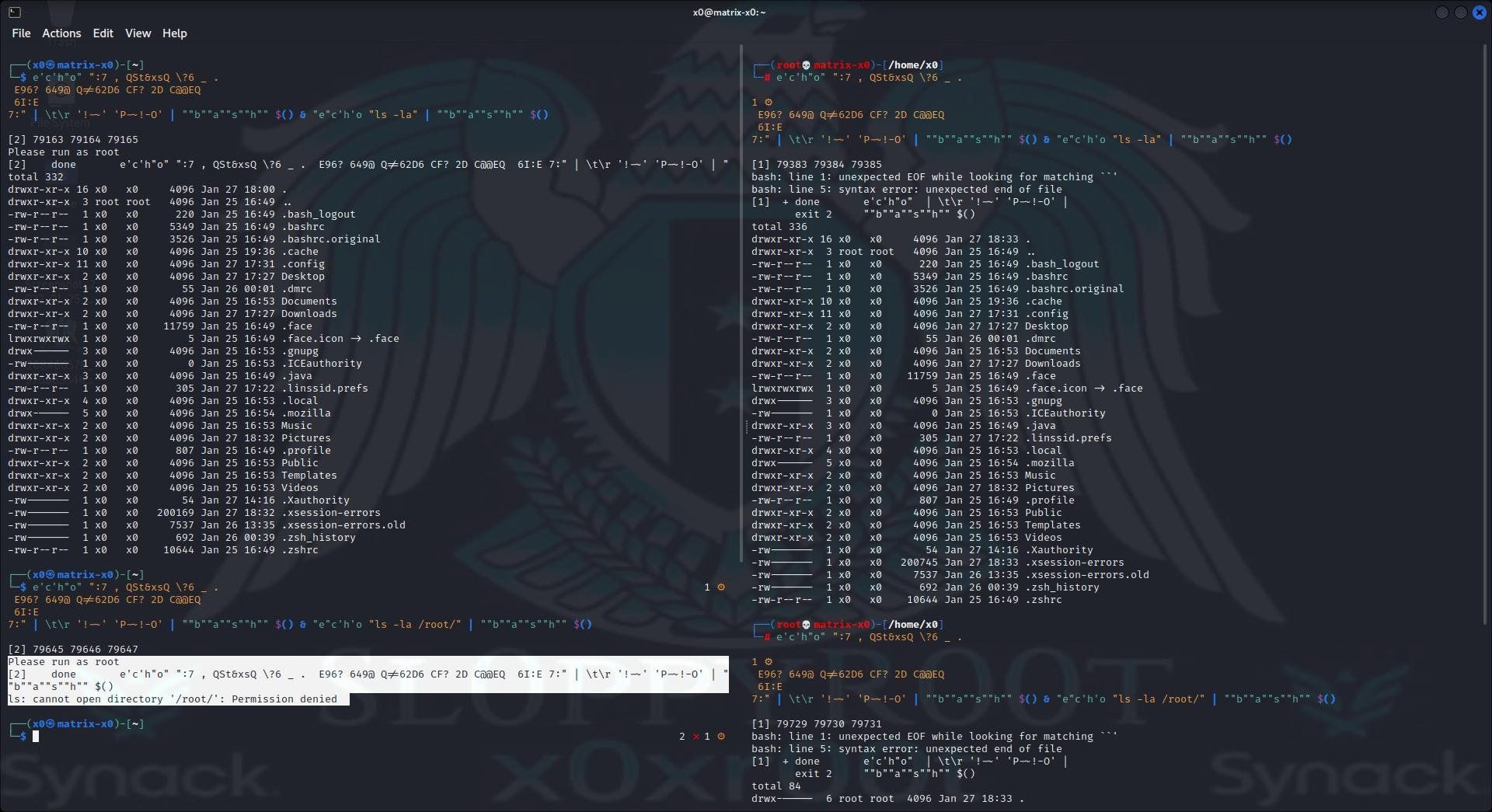
Below in the third image we use a encrypted rot47 payload which consist out of a bash check to run as root. Here we decrypt the rot47 payload and exec directly with a pipe and $() to exec it. And try to ls -la the root dir.
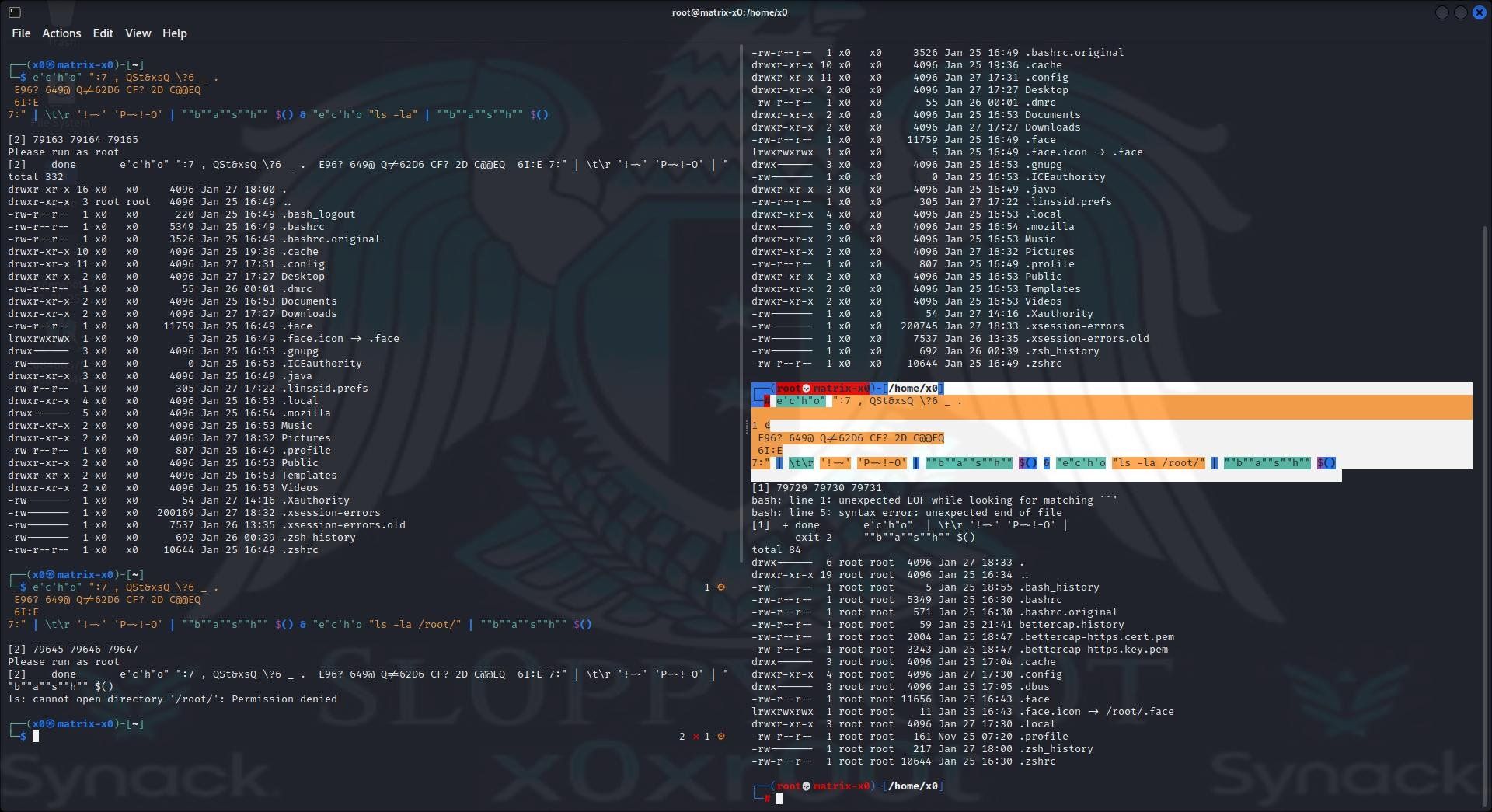
Below in image four we use a encrypted rot47 payload which consist out of a bash check to run as root. Here we decrypt the rot47 payload and exec directly with a pipe and $() to exec it. And try to ls -la the root dir and we are successfull as root user.
If one would use this to either obfuscate this method, or use it in dubble tripple encoding pipe to bash and $() to exec it, then on could make nifty payloads.
One could also use this to exec code with bash where one is limited of exec bash it self and use '' "" or combination of these in the command instruction.
like this ....
e'c'h"o"
"e"c'h'o
""b""a""s""h
And such
I hope u enjoyed this read.
Team sl0ppyr00t
~x0xr00t~


