How To Choose A Virtual Private Network (VPN) Provider
This article will help you cut through the VPN vendor marketing confusion and help you choose a provider who is serious about your privacy.

With so many different VPN providers on the market producing content and guest blog posts which often contain conflicting information about VPN's, it can be confusing and difficult to choose a reliable VPN provider. This article will help you cut through the confusion and choose a provider who is serious about your privacy.
What Is A VPN?
A VPN works to establish a secure tunnel between two or more devices, a website and your computer for example. Using a VPN helps you to add an extra layer of security and privacy to private and public networks such as Wi-Fi connections and the Internet. Enterprises use VPN services regularly to secure their sensitive and business-related traffic. However, its use by ordinary end users has become more popular of late because of the huge increase in digital communications along with the increase of cyber-attacks and online tracking, making more people aware of the security dangers when utilizing online services.
When using a VPN (see Figure 1), an organization/individual can secure private network traffic over an unsecured network such as the Internet. Thus, users feel safe connecting their personal devices to the Internet, ensuring their banking details, credit card numbers, passwords, and any other sensitive data is not intercepted by an unauthorized party. The VPN also gives the user an anonymous IP address, making them appear as if in another location so they can avoid censorship, share files with other people anonymously, and more. In today’s digital world, using a VPN service is no longer considered a security luxury.
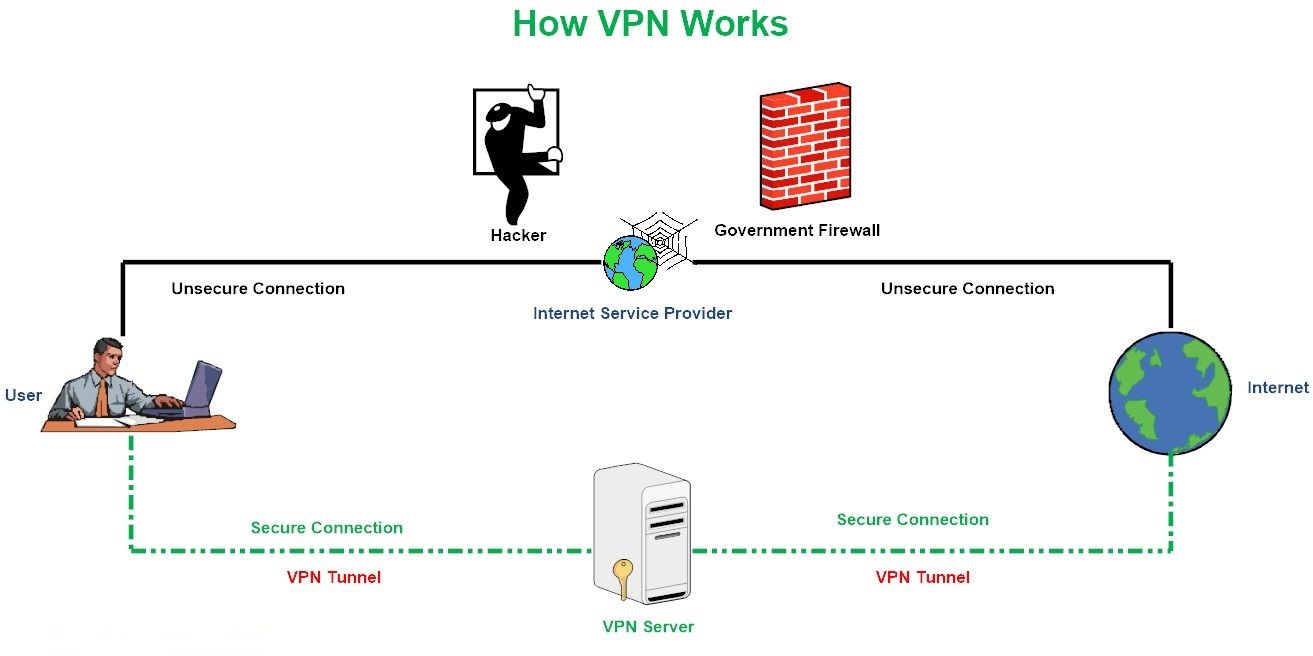
The ultimate aim of a VPN service is to provide security for data transmitted through the internet by encrypting it and concealing the real IP address of the sender, this will effectively make snooping on your online communications extremely difficult. However, there is still a big risk when using VPN services, for instance, a VPN provider has the ability to record anything pass through its channel, customers private information such as IP address, web browsing history in addition to online account credentials can all be recorded and linked to each customer account. The risk does not stop there, as some free VPN providers may sell their customers personal details to third party companies (e.g. Advertisement companies) for commercial gain, others may even go further and display malicious advertisements -also known as Malvertising- for their customer, leading to infecting customer machine with different types of malware such as ransomware or spyware.
What is Malvertising? Also known as "malicious advertising", Malvertising refers to the act of abusing legal advertisement channels -such as Google Adsense- to spread malware through injecting malicious code inside Ads and web pages to redirect the user to compromised websites hosting exploit kits to further infect his/her machine with types of malware.Although a VPN service can have negative privacy effects on its users when operated by a malicious actor or simply by known secure provider, however, this should not make us abandon using this enhanced security feature, actually, I advise you not to access the Internet at all (either from home or using public Wi-Fi hotspots) without a reliable VPN connection!
Criteria to Select the Best VPN
There are numerous VPN service providers worldwide. Many of them are reliable and offer distinct features. The prices usually are in the range of $5 to $10 for a monthly subscription (you can expect to get a discount for a yearly subscription). There are also many providers that offer free VPN services in exchange for showing advertisements during the browsing session. For most users, any paid VPN providers will provide an adequate service to protect their online communications. However, if you want to approach your online privacy correctly, then you need to select your VPN provider carefully because the provider can intercept all your online communications passing through its service if it so wanted.
In order to use any VPN service, you need to install its client software on your PC, installing a VPN client is generally easy and requires a set of easy steps, so we shift our focus on providing general advice to aid you when selecting your VPN provider.
The Criteria That Must Be Met To Ensure Privacy
- Do not subscribe to VPN service providers that are based on one of the following countries: The United States, United Kingdom, Australia, New Zealand, Canada, Denmark, France, Netherlands, Norway, Belgium, Germany, Italy, Spain, Israel, Sweden, and of course less free countries such as Russia, China, Iran, and all Arab states. These countries are either actively involved in mass surveillance programs or they have made partnership agreements with other countries to exchange intelligence information and have data retention laws (also known as disclosure laws) that force VPN providers to handle customer activity log to authorities upon request.
There are many countries involved in mass surveillance agreements, which among their activities is intercepting VPN traffic, the following are the countries involved in main global surveillance arrangements:
a) The Five Eyes (FVEY) alliance: It includes United States, United Kingdom, Canada, Australia, and New Zealand).
b) 9 Eyes: This includes the countries in FVEY plus Denmark, France, the Netherlands, and Norway.
c) 14 Eyes: This includes the countries in 9 Eyes, with the addition of Germany, Belgium, Italy, Spain, and Sweden.
The majority of information about mass surveillance programs remains top secret; however, the revelation of the Snowden documents casts light on the underground world of mass surveillance programs and their huge impact on each citizen’s privacy. It is wise to consider this when choosing a VPN.
2. The VPN provider must support the OpenVPN software; this is an open source program published under a GNU General Public License, that its source code can be audited by anyone independent security researchers to make sure it is clean and does not contain backdoors.
3. Select a well-funded VPN provider that has its own servers that reside in countries where their laws support user rights to privacy. For instance, most VPN companies providers are small companies that use other third-party provider’s IT infrastructure to operate (e.g. They use Infrastructure as a service (IaaS) & Software as a service (SaaS) service models), this put question marks on their ability to assure the privacy of their customer’s data communication efficiently, especially when renting servers in countries controlled by oppressive regimes or the one involved in global mass surveillance programs.
4. The VPN provider should support the newest and most secure encryption & protocols for connection, currently the OpenVPN protocol is still considered the most secure one.
5. The VPN provider must have its own private DNS servers to avoid leaking users’ DNS requests (web browsing history) to third-party observers. You can check if your VPN connection is leaking info about your connection by running this test.
6. The VPN provider should have integrated DNS leak protection technology built into their client VPN software.
7. The VPN provider must separate Internet traffic according to the protocol used. For example, it should separate web browsing from file sharing, meaning that each one has a dedicated server.
8. The VPN client software must support the ability to disconnect the Internet from your computer if the VPN fails for any reason (to avoid leaking your current activities to your ISP).
9. Your VPN provider should support multiple devices at the same time, so you can protect your tablet and smartphone data in addition to your laptop or PC.
10. Your VPN provider should accept anonymous payments such as bitcoin, gift cards, debit cards, and cash, if possible without showing any IDs.
11. Your VPN provider should not require many details to set up; a username and a password should be enough, in case you need to supply an email address for one time to activate the account, you can use a disposable email address to avoid using your real email address -and consequently risking of revealing your true identity. The Temp Mail Address (https://www.tempmailaddress.com) offers such a service.
12. Your VPN provider should not store any Personally Identifiable Information (PII) about you, his policy is also known as a zero-knowledge or no-logs policy.
13. The VPN provider should not use any third party provider to collect anonymous information about its user, for marketing and diagnosing purposes, for example, if a specific VPN provider use Google Analytical -or other similar analytical software- on its website to better understand its customers, this may lead to privacy violation by the company doing the analytics.
14. Read the VPN provider’s privacy policy and terms of service very well. These two documents contain company policies and state the amount of data they are going to be logging about you and for how long, it will also mention the jurisdiction where this company operate and adhere to its laws. The privacy policy also declares the circumstances under which your VPN provider may turn your data over to governments or law enforcement.
15. Do not use a free VPN service for mission-critical tasks online, usually, it is preferred not to use any type of free VPN services, because those providers will simply use your web browsing history log as a fee for their service.
16. If your ultimate purpose is anonymity and plausible deniability, use the Tor Browser instead of a VPN. VPN is not intended -by technical design- to make you completely anonymous online, if you want online anonymity, go and get the TOR Browser from here https://www.torproject.org/download
Built-in Opera VPN
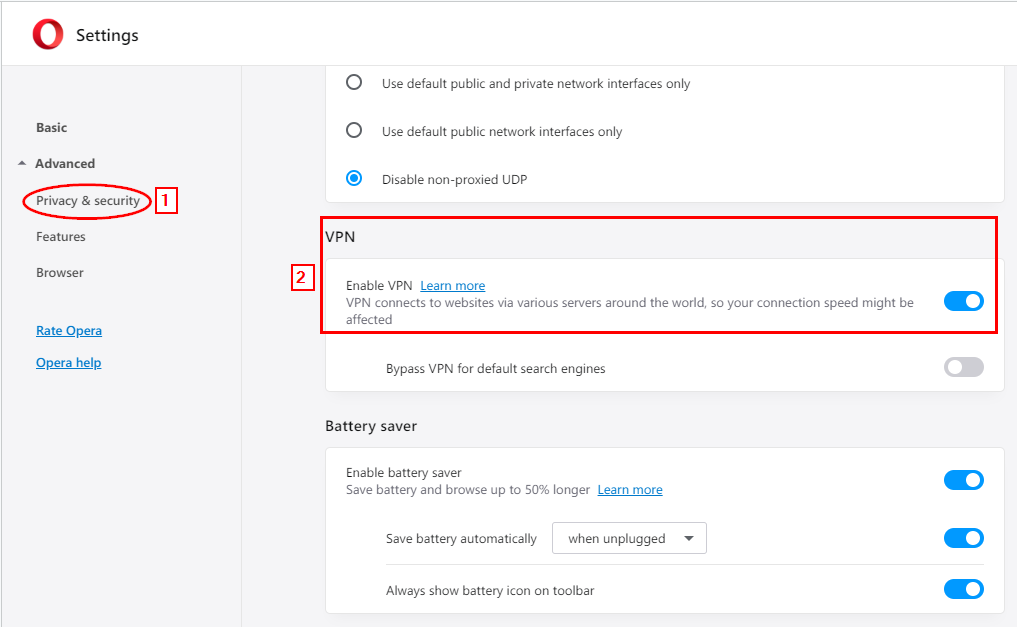
The Opera browser has a built-in VPN function. This feature is completely free and unlimited (in terms of monthly bandwidth usage). You can activate the built-in VPN in your Opera browser by going to the Opera menu and selecting Settings. Go to the Privacy & Security tab, find the VPN section, and select the Enable VPN check box (see Figure 2).
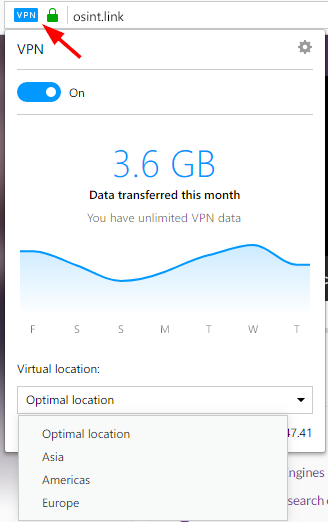
After successfully enabling VPN in the Opera browser, you will see a blue VPN icon in the Opera address bar. You can further configure Opera VPN settings by clicking this icon to select whether you want to enable/disable the VPN feature and select the server location you want to connect through (see Figure 3).
Opera VPN is suitable for users looking to bypass online censorship and restrictions of forbidden websites in their countries, however, you cannot use it for mission-critical communications, especially now that Opera is owned by a Chinese company!
Laws Concerning VPN Services
No matter how strong your VPN provider is in terms of technical security measures, legal jurisdiction where this VPN operate will still play a crucial role in determining its privacy suitability’s for end-users. For instance, different countries impose different legal agreements on VPN providers when using their land or using servers hosted on their land to conduct their business.
In China, VPN services are banned unless it has a legal permit from the government, the same applies to UAE where citizens are only allowed to connect to a list of approved VPN providers. Both China and UAE enforce data retention policy laws where VPN providers must maintain a log of their customer’s online activities!
VPN providers maintain two log types for their registered customers:
A. Connection log: Hold customer account info such as username, password, email and billing address. This log is mandatory for any VPN provider id they want to provide a service. As I already stated, the less the amount of personal information to open the account, the better for user privacy.
B. Activity log: The sum of online activities, the users browsing history.
GDPR & The EU - Now, we come to European Union’s General Data Protection Regulation Act (GDPR), the GDPR regulations stipulate the duties of companies operating in EU or dealing with customers from EU and wishing to collect, store and/or use their personal data to run the subject service.
VPN providers working in EU should comply with the GDPR, for instance, they should not record their customers “Activity Log”, for the “Connection Log” it should remain present to manage customers account to deliver the service properly. Although the GDPR impose real restrictions on VPN provider’s ability to record customer’s activity log, however, no one can guarantee the possibility of collecting such data using other -secret- methods, especially from state-sponsored agencies.
In the US - which is still leading the world in the intelligence arena- VPN providers should keep the activity log of their connected users as a part of the VPN provider work license agreement. Obviously, this makes USA based VPN providers untrusted choice for privacy-conscious people.
Other countries are usually using a mix of EU and USA cyber laws; you should always read the VPN provider “Terms of service” agreement -which states the jurisdiction that this provider is subject to its laws- before subscribing to its service.
Wrapping Up: The conclusion
VPN is developed to increase the security of data transmitted online, however, using the wrong provider will give its user a false sense of security, which is worse than the existence of no security at all. For instance, there are scores of VPN companies promoting their services worldwide, as a customer need to use a VPN service, you should read the terms and privacy policy of selected VPN provider very carefully, taking into account the issue raised during this article before subscribing to a particular service.
Swiss privacy laws are still the best in the world. In relation to VPN services, the Swiss cyber law does not require Swiss-based VPN providers to log anything about their users, including the real IP address used to access the VPN service. In addition to this Switzerland is not engaged in any intelligence sharing and surveillance agreements (e.g. Five 9 or 14 Eyes agreements), unlike other European countries.
For more information about the best methods to protect your online communications and assure your digital privacy online, check author book “Digital Privacy and Security Using Windows” published by Apress https://www.amazon.com/Digital-Privacy-Security-Using-Windows/dp/1484227980


