Why Does Google Insist On HTTPS & Penalize You For Not Having It?
What is the difference between HTTP and HTTPS? In this article security researcher Stephen Chapendama breaks it down and explains it for us.

It's no secret that for years now, Google has taken the stance that all HTTP sites are insecure. Chrome, one of the most popular browsers will identify any sites not using the HTTPS protocol as "not secure." But what does this mean for users? Well, in July 2018, Google will release Chrome (update 68) and they have changed the treatment of HTTP pages to:
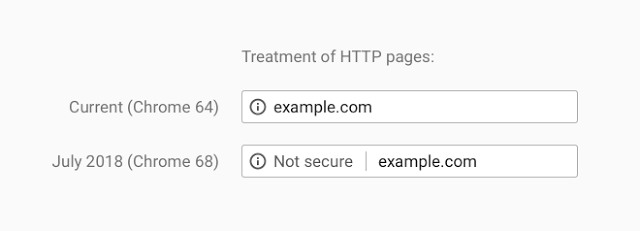
A question I get asked a lot is what's actually the difference, and should I fork out the extra £€$ to secure my site. The simple answer is yes, you should probably secure your site. Even if it's just a blog. The reason you are securing your site however will not be the reason Google is pushing for HTTPS. SEO is affected by your site not having HTTPS, and Google has made web admins aware of this. Since last year, websites not using the secure protocol are less favourable to search engines. This means when you search for what your brand/company is known for, Google most likely isn't helping you by putting you on page 13 because you aren't using HTTPS. In 2014 they announced that they would be using HTPPS as a ranking signal at Google I/O.
What is HTTP?
HTTP - Hyper Text Transfer Protocol is the underlying protocol of the World Wide Web. It defines how messages are formatted and transmitted and what actions browsers should take in response to commands. An example is when you enter a website URL into a browser, an HTTP command is sent to the webserver directing it to fetch and transmit the requested web page. HTTP also comes with status codes, such as the infamous 404 error code when a request is sent and it can't find what was requested. HTTP is known as an application protocol, and by default, HTTP uses Port 80 which is the port that a web server accepts requests from.
And HTTPS?
The Hyper Text Transfer Protocol Secure is the alternative to HTTP and uses port 443 for communication. The transmissions between the browser and website are encrypted by TLS (Transport Layer Security) or SSL (Secure Sockets Layer). Both are cryptographic protocols that "provide authentication and data encryption between servers and applications operating over a network." From a functional standpoint, SSL encrypts data before it's sent to another party and TSL encrypts data in transit and requires a "handshake" between two authorised clients before revealing anything.
Why use HTTPS?
Well if at any point during a user interacting with your site and sensitive data such as payment or login credentials are exchanged, you definitely need to be protected against man in the middle attacks.
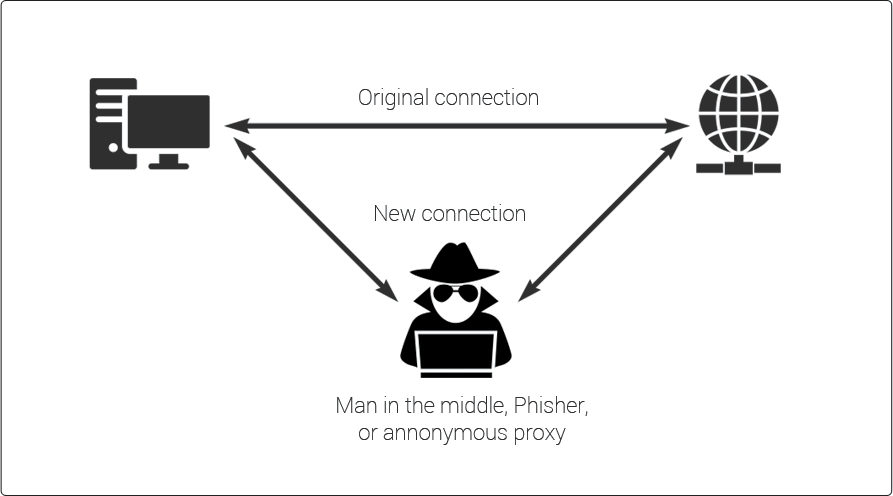
A MITM (Man-in-the-middle) attack happens when the authenticity and communication between two systems is altered/intercepted by a 3rd party. This can happen through hackers creating fake Wifi access points disguised as legitimate node to access and steal the data of anyone who connects. It is also possible for hackers to hijack sessions after you have logged into a website. A popular way to execute this attack is stealing your browsers cookies. Remember that old saying, "never log into your banking using coffee shop wifi," this is why!
The session hijacking attack can be executed via multiple methods:
Session sniffing - as the name suggests is about recon of a users session ID when they try authenticate or enter credentials. The application will try to identify the user based on his cookie value (this is where the session ID is stored) and if this information is captured by a malicious attacker, they can use the same login session to the application as the victim. If an application does not utilise SSL and transmits data in plain text, this creates a vulnerability where anyone on the same network can grab the cookie values by sniffing the traffic using tools like Wireshark.
Predicting session IDs - It is possible to analyse and predict session IDs. Let's say for example, the following session ID has been captured:
Set-Cookie: sessionid=ZGFuaWVsOmR1bWlsZTc4=
Looks random and difficult to crack right? Wrong! A simple Base64 decoder will reveal:
Base64 Decode [ZGFuaWVsOmR1bWlsZTc4=] = daniel:dumile78
This has just revealed the format in which a malicious attacker can now randomly generate and attempt to construct a valid cookie.
This is why HTTPS is important. But it is also possible to go one step further by implementing HSTS (HTTP Strict Transport Security) which can help prevent attacks such as session jacking. Implementing HSTS will force any web browser or application to connect to HTTPS and block any content that uses HTTP as it's protocol.
Web service providers should be implementing HTTPS as standard now, as often, customers who may be looking to cut costs will opt to not include HTTPS. This not only means, they are website isn't getting the search engine attention it deserves, it is leaving it wide open to attacks. Not everyone agrees however with the stance taken by Google. Should a search engine giant be policing the internet and enforcing on us what's safe and what isn't? It goes against what the internet is, but I believe the threat landscape has changed. With so many people now looking to monetise their web presence, security should be a priority.
Stephen Chapendama of BantuTech.com

