Squeeze Volume 5 - Christmas Trojans, Bluetooth Car Break-Ins & More!
Welcome to Squeeze, a curated selection of interesting infosec articles from the past week that you may have missed.

Welcome to the fifth edition of the Secjuice Squeeze, where we present a selection of last weeks interesting infosec articles curated for your reading enjoyment in case you missed them! This week's volume was created by Manmeet Singh Bhatia, Miguel Calles, and Chad Calease.
Microsoft releases patch updates for recent Windows zero-day
In November 2019, cybersecurity firm Kaspersky disclosed their finding of a zero-day vulnerability in the Google Chrome browser, which was actively being used in online attacks termed as Operation WizardOpium. In case you missed it, in this attack, the attackers injected a JavaScript tag in a Korean language news website subsequently taking over its control. The injected JavaScript tag would execute malicious scripts in the visitor's browser. This vulnerability was tagged as CVE-2019-13720 with a severity score of 8.8. Google fixed the problem in its latest update of the browser.
In the course of the investigation, Kaspersky revealed it discovered another zero-day exploit, this time in Windows, which worked in conjunction with the chrome vulnerability. Marked as CVE-2019-1458, this zero-day allowed to gain escalated privilege on the infected machine. Kaspersky technology explained, "During our investigation, we discovered that yet another 0-day exploit was used in those attacks. The exploit for Google Chrome embeds a 0-day EoP exploit (CVE-2019-1458) that is used to gain higher privileges on the infected machine as well as escaping the Chrome process sandbox."
Microsoft, in its December security updates, 2019, patches a total of 36 vulnerabilities and advises its users about the zero-day vulnerability. The latest developments as perceived by Kaspersky can be read on their latest blog post.
Windows 0-day exploit CVE-2019-1458 used in Operation WizardOpium
Windows 0-day exploit CVE-2019-1458 used in Operation WizardOpium
Merry Christmas from EMOTET Trojan Virus
It is a festive time of year and malicious actors are taking advantage. Before you open an email inviting you to a holiday party, stop and be cautious. You might get an email containing an attachments giving you details to a holiday party. The email is written calmy and suggestive toward downloading the attachment. If you open the attachment, it installs a trojan virus that starts sending emails to others and potentially installs a ransomware virus too.
Emotet Trojan is Inviting You To A Malicious Christmas Party
EMOTET Arrives via Spam, Greeting You a Merry Christmas
K-12 Cybersecurity Act of 2019
Senators introduced a new act to address cybersecurity in the K-12 school systems. They recognized the "K–12 educational institutions across the United States are facing cyber attacks." The education institutions store and maintain personally identifiable information, medical records, family records, and scholastics records (e.g., grades). This is valuable information to hackers. The act proposes the Department of Homeland Security to become more involved.
Senators introduce K-12 Cybersecurity Act
S.3033 - K-12 Cybersecurity Act of 2019
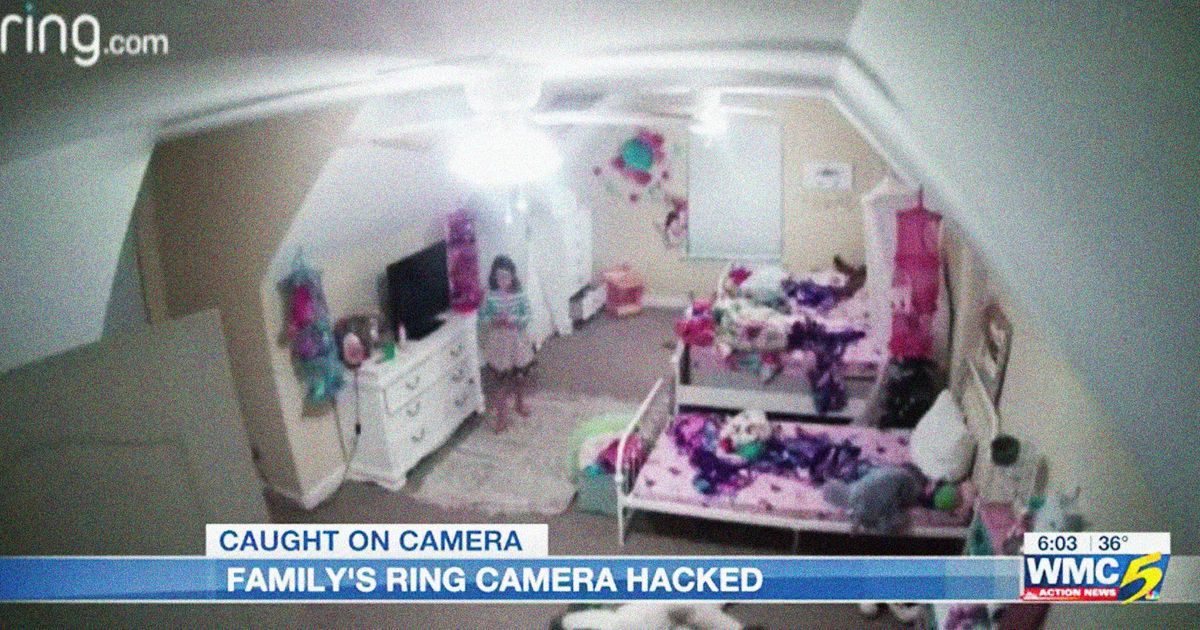
"Hacking Apocalypse!!!"
There's a media frenzy about Ring cameras getting broken into. It's not a "hacking apocalypse" so much as it's people using weak passwords, like 12345.
Terrifying Videos Show Men Hacking Into Home Security Cameras
Third Party Risk Providers
The Pentagon is developing a cybersecurity maturity model with five levels of compliance that correspond to the sensitivity of data being protected. Their vendors and contractors will have to step-up their own practices if they want to stay in the game.
Pentagon Wants Contractors to Meet Cybersecurity Requirements

Not Your Grampa's Break-In Tactics
Bluetooth scanners are the new hotness for thieves. They use them to identify valuable devices like laptops, phones, and tablets inside vehicles, making their target-selection more on-point. No more breaking into a nice car just because they "think" there might be something worth stealing inside.
Thieves Are Using Bluetooth to Target Vehicle Break-Ins






