Getting started with the MITRE ATT&CK Framework
MITRE ATT&CK is a knowledge base of adversary tactics and techniques based on real-world observations.

Remember the old Westerns, TV shows like The Lone Ranger and movies like The Magnificent Seven? In many of them – especially the TV shows - the good cowboy and sidekick catch the bad guy, they start walking away to get the sheriff, and invariably another bad guy who was hiding emerges, and then there’s a shootout. The audience, after seeing a couple of these, knows what’s going to happen and wonders why these cowboys don’t see it coming (while heroic, these mere mortals obviously didn’t watch enough movies about their own profession).
In music composition, ostinatos are repeated musical patterns, providing a good rhythmic or harmonic backdrop. They’re not always exciting but they are useful and sometimes necessary – and, yes, they can be magnificent and emotional. A lot of modern music is made almost solely of ostinatos. (Much more can be said about the value of ostinatos and movie score composition over the years, so here are a couple decent articles about it: https://howtowritefilmmusic.com/ostinatos-the-back-bone-of-epic-scoring/ and https://tedium.co/2022/11/09/the-death-of-the-key-change/ )
At minimum, ostinatos provide a necessary canvas for music.
Along the lines of Westerns, MITRE ATT&CK provides defenders the plans of the attackers, reducing the number of crooks hiding behind rocks and buildings. Along the lines of ostinatos, MITRE provides a consistent pattern that can be adapted as needed to fit the “scoring” of an organization’s threat intelligence needs.
What is MITRE ATT&CK?
Per the MITRE ATT&CK webpage, "MITRE ATT&CK is a globally accessible knowledge base of adversary tactics and techniques based on real-world Observations. The ATT&CK knowledge base provides a foundation for the development Of specific threat models and methodologies in the private sector, in government. and in the cybersecurity product service community. "
MITRE ATT&CK (short for Adversarial Tactics, Techniques, and Common Knowledge) is a framework consisting of adversarial tactics, techniques, and procedures (TTPs) used by threat actors. It’s a matrix-based model that provides a systematic way to understand, analyze, and describe the various tactics, techniques, and procedures that attackers may use at different stages of an attack
A simpler definition from one of MITRE’s other pages, “MITRE ATT&CK is a knowledge base that helps model cyber adversaries' tactics and techniques—and then shows how to detect or stop them.”
The MITRE ATT&CK framework (MAF) is useful for a variety of purposes, including:
Assessing an organization's cybersecurity posture: By mapping the TTPs used by attackers to the defenses in place within an organization, MAF can help identify potential vulnerabilities and areas for improvement.
Developing and testing cybersecurity controls: The framework can be used to identify and prioritize the most important controls to implement based on the tactics and techniques commonly used by attackers.
Detecting and responding to cyberattacks: The ATT&CK framework can help security teams understand the tactics, techniques, and procedures being used by attackers, enabling them to more effectively detect and respond to attacks.
Sharing knowledge and best practices: MAF provides a common language and understanding of cyber threats that can be used to facilitate communication and collaboration among information security professionals.
There are 14 tactics, under each tactic are well-known techniques, and many techniques have sub-techniques.
The following helpful image is from F5 Labs:
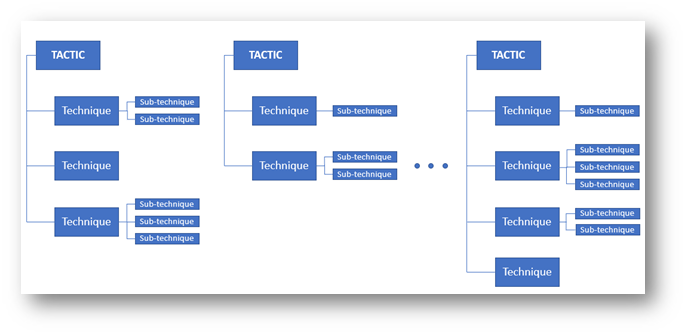
The 14 tactics (displayed in the matrix as headers) are:
- Reconnaissance: Acquiring information about the target group in order to organize future enemy operations.
- Resource Development: Creating infrastructure for command and control and resources to support activities
- Initial access: These are tactics that adversaries use to enter a network by exploiting vulns in public-facing systems. One example is spear-phishing.
- Execution: These tactics result in an adversary running code on a target system. For example, A malicious hacker running a PowerShell script to download other attacker tools and/or scan other systems is one example.
- Persistence: These allow adversaries to maintain access on a target system, even after restarts and credential changes. One example is an attacker who creates a scheduled task that runs code at a specific time.
- Privilege escalation: Adversaries gain higher-level privileges (e.g., root, local admin).
- Defense evasion: Evasion tactics include hiding malicious code within current processes or folders, encrypting adversary code, or disabling security software.
- Credential access: These tactics steal usernames and credentials for reuse.
- Discovery: Used to obtain information about systems and networks that they want to exploit or use for their tactical advantage.
- Lateral movement: Attackers can move from one system to another. Examples are pass-the-hash and abuse of RDP.
- Collection: Adversaries gather the information they targeted as part of their objectives.
- Command and control: Attackers communicate with a system under their control. For example, an attacker communicates with a system over an uncommon port to evade detection.
- Exfiltration: Moving data from a compromised network to a system that's under control by the attacker.
- Impact: These tactics are used by attackers to negatively affect the availability of systems, networks, and data. Methods include denial-of-service, disk-wiping, and data-wiping.
Why use MITRE?
Microsoft uses MAF in its Sentinel and Defender detections. VMWare uses it as one of the benchmarks for their security solutions. Red Teamers use it as a blueprint for attack surfaces. Red Canary includes it as a basis for their Atomic Red Team tests, Threat hunters use it to correlate attacker techniques with their own defenses. Security engineers evaluate their products’ effectiveness. It’s used in all sectors and industries.
For something so popular, it still seems complex and seems to need an expert to understand it. Is it only for Big Tech or experts? It’s for everyone, and I hope this article helps either demystify it or encourage you to look further into its usefulness.
Here are some possible ways to implement it:
You have on-prem servers that need protected
a. https://top-attack-techniques.mitre-engenuity.org/calculator
MITRE Engenuity uses MITRE ATT&CK to help IT & Security leaders calculate which Top Ten offensive techniques they need to watch out for.
Even if there’s not an initiative from corporate leadership, this can be a quick win by way of providing an industry-standard approach to mapping a course of control implementations.
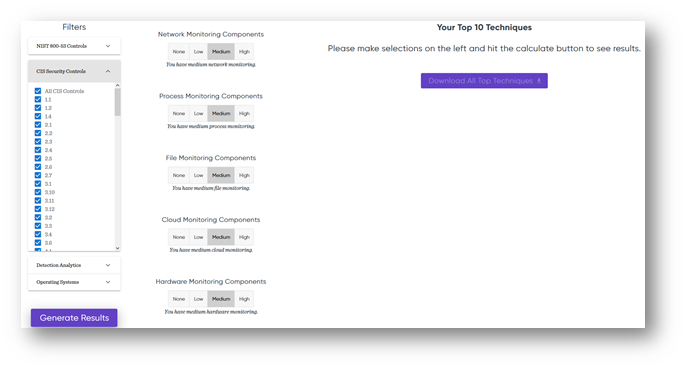
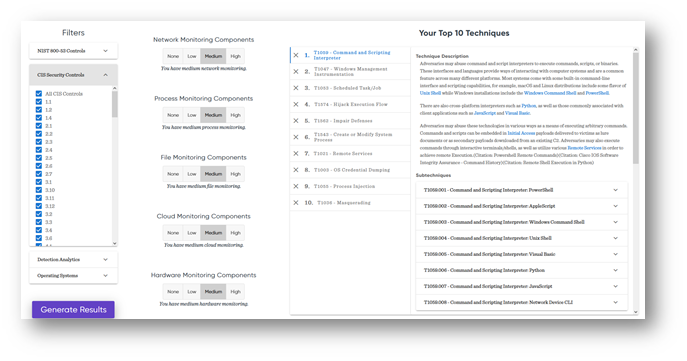
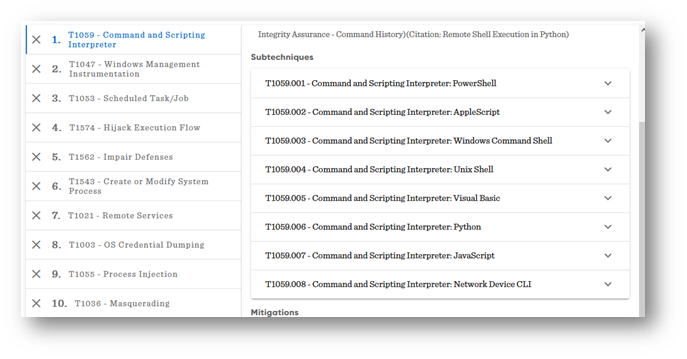
You have Azure and need Azure-specific action items.
You can see the specific Azure controls for yourself here: https://mitre-attack.github.io/attack-navigator/#layerURL=https://center-for-threat-informed-defense.github.io/security-stack-mappings/Azure/layers/platform.json
2. NOTE: If you get the following error when visiting the page, just click OK and you’ll be taken to the controls anyway – no need to update the layer version. You can update it if you like, but the underlying .json won’t be formatted properly and the results will probably look anemic.
Here’s what it looks like:

It can look intimidating, but it’s one of those things: once you grasp the layout,verbiage, and colors, it makes perfect sense.
Because Microsoft Sentinel includes ATT&CK queries, it’s easy to implement the framework and use the built-in hunting tools to quickly ramp up defenses.
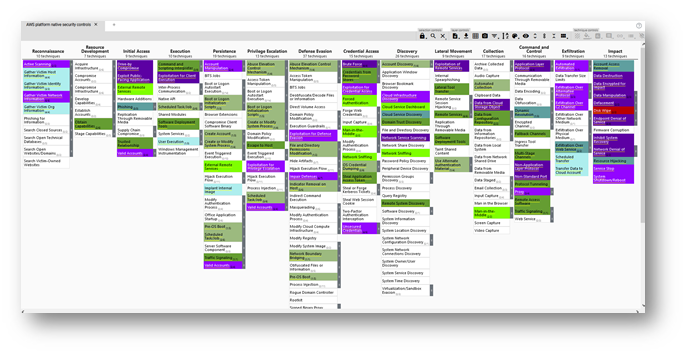
You have AWS and need AWS-specific action items
AWS-specific controls are here: https://center-for-threat-informed-defense.github.io/security-stack-mappings/AWS/README.html
And the .json is here:
Here's what it looks like:
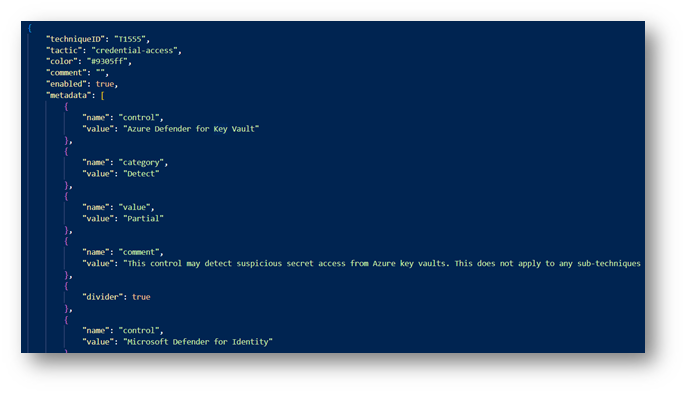
Changing the colors and view
I use Visual Studio Code (VSO), but whatever works for you to modify the JSON will do. You can make the colors whatever you like, and the JSON will show the descriptions that can be missed in all the jumble. There’s so much detail behind the matrix that it can be hard to see what all is going on.
Sample from VSO
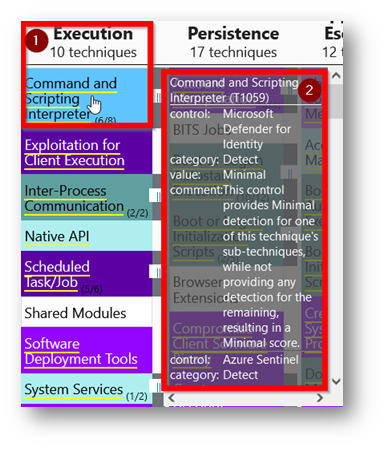
Here’s an example of the detail shown when mousing over the 1) Execution tactic and 2) Command and Scripting technique:
How to adapt it
1. Create a New empty layer (Enterprise, Mobile, ICS)
2. From left to right in the Tactics, click on just one item in each column, holding down the Ctrl key to select items one at a time and keep them selected.
3. Under “technique controls,” select the paint bucket and choose a color.
4. Voila! They’re all colored

This can be exported to JSON, SVG, or CSV. Change the colors, change the selections, redo the JSON so it’s to your liking, etc.
How it can be leveraged
The MAF is widely used across a variety of industries and sectors to help organizations assess and improve their cybersecurity defenses. Some examples of how the framework can be used include:
· Financial services: Financial institutions use the framework to identify and prioritize the most important controls to implement based on the tactics and techniques commonly used by attackers targeting the financial sector.
· Healthcare: Healthcare organizations use the framework to understand the tactics and techniques used by attackers targeting the healthcare industry, and to develop and test controls to defend against these threats.
· Critical infrastructure: Organizations in the critical infrastructure sector, such as utilities and transportation systems, use the framework to understand and defend against the tactics and techniques used by attackers targeting these types of systems.
· Government: Government agencies use the framework to assess and improve their cybersecurity defenses, and to understand the tactics and techniques used by attackers targeting the government sector.
· Retail: Retail organizations use the framework to understand and defend against the tactics and techniques used by attackers targeting the retail industry, including tactics such as point-of-sale attacks and data breaches.
Limitations and criticisms of the MITRE ATT&CK framework
There are a few potential limitations and criticisms of MAF:
1. Complexity: The framework is comprehensive and covers a wide range of tactics, techniques, and procedures. This can make it complex and challenging for organizations to fully understand and implement.
2. Limited coverage: While the framework covers a wide range of tactics, techniques, and procedures, it is not exhaustive and may not cover every potential threat. This can limit its usefulness as a comprehensive tool for assessing and improving cybersecurity defenses.
3. Bias towards certain tactics: Some critics have argued that the framework has a bias towards certain tactics, such as those related to advanced persistent threats (APTs), and may not adequately cover other types of threats.
4. Limited context: The framework does not provide context for the tactics, techniques, and procedures it covers, such as information about the specific threat actors or campaigns that have used them. This can make it difficult for organizations to fully understand the implications of the TTPs covered in the framework.
These are, however, what I’d consider minimal, or even typical, obstacles and limitations. To each point above: much of cybersecurity requires study, research, and experimenting to learn and understand; there’s not a single framework or tool or anything available that covers everything; any approach is limited in scope; and context can only be gained and attained by each individual company – no two companies are alike, so context is always pointedly individual.
More importantly, MITRE addresses these issues as they can, making the matrix and framework more and more useful and relevant to more organizations.
The difficulty in addressing these can be likened to “How do I write a melody for a song?” It depends on what song will be written. What’s the mood and ambience? What’s the story? What chords would be used? What rhythm and instrumentation are intended? It all depends. While there is an uncanny formula for many songs, that and other formulas have so many iterations that there are endless possibilities.
It’s the same with securing organizations – what’s the industry, budget, goal, technology, personnel, growth plan, etc.? Once those have been determined – or at least planned – then one can proceed with specific plans for securing things.
Conclusion
I hope that this introduction to the MITRE ATT&CK framework encourages you to dive in, learn something new, and see if it’s the right thing for you. At the very least, you’ve become familiar with a very popular and much-used attack and defense structure.
Festina Lente
Resources for more Information
https://attack.mitre.org/resources/attackcon/
https://center-for-threat-informed-defense.github.io/security-stack-mappings/Azure/README.html

