New Kids On The Block (Part I)
Shodan is considered to be the standard for mass internet OSINT, however in this article n0mad researches alternatives and provides insight to why these tools should be included in your toolset.

Intro
Many IT-Security professional will encounter a time, when they'll need OSINT-data[1] from technical systems. Maybe they want to investigate the external attack surface of a target, conduct passive reconnaissance, or may want to measure the overall threat level of an emerging attack vector. For example, the memcached-ddos-vector from last year that had an amplification-rate of 10,000 or more. A Shodan search on the day first reports came out showed roughly 17,000 vulnerable servers online; a number that could easily be blacklisted by a decent firewall.
For a long time, there was only shodan.io. While it was great and widely used, I realized a lot of filtering happening in the background. I remember around 2 or 3 years ago when a RCE against a Cisco-product came out – while there was a good amount of hits on one day, a week later the search-result was almost empty.
As OSINT has become more important, an analyst's toolkit has broadened. This is what this article explores: I will compare Shodan to two new services, Binaryedge and Zoomeye, that emerged over the last few years and seemed to be ready to gun for the crown of the OSINT tool of choice. In the remainder of this article I will compare both their features and result sets (although will leave out discussions on prices).
The focus for the services I compare are the following:
- Regular internet-wide scans on a regular basis
- Web interfaces for searching, filtering and downloading results
- Filtering options
- API to integrate results into 3rd-party-tools
Regarding my results, YMMV and everything in my honest opinion.
Shodan, the old bull
Shodan is known amongst almost anyone in the OSINT game. It became famous for its ability to tag and search for various kinds of different devices including webcams, industrial control systems and IoT-devices. During that "zOMG!! IOT ATTACKING! WE ALL GONNA DIE" hysteria it became the "The IoT search engine" of choice. Shodan set the industrial-standard of internet-wide OSINT-data. And it is certainly a tool you still can have fun with :D
Shodan pros:
- Developer-friendly path with APIs and lots of modules as well as language-integrations
- A lot of stuff to integrate into the community (tags, saved searches etc).
Shodan cons:
- The support for paying customers lacks manpower
- The result-filtering you see from time to time is annoying
- no option to filter for proto:tcp/udp in the interface; and there is one, it is not documented, at least I did find no information on that
BinaryEdge and ZoomEye entering the stage
BinaryEdge is a Swiss company, performing internet-wide scans and publishing a lot of results, findings and reports on their blog (that targets a mostly technical audience). BinaryEdge caught my attention with an analysis of open mongodb/redis/memcache-databases, that I have heavily cited. They made great steps in opening their platform as an OSINT-tool with extensive searching, filtering and downloading and seem to be able to now compete with Shodan.
BinaryEdge pros:
- the speed they adopt new features
- the technical blogs they publish
BinaryEdge cons:
- The price for API-calls, when they integrate their services into other solutions, for example the mass checking of IPs for open ports. Checking 50,000 IPs on a daily basis certainly isn't cheap, using BinaryEdge.
ZoomEye is created by the Chinese Knownsec 404-Team, who also run the excellent Seebug Blog with tonnes of good research. ZoomEye appeared on my radar two years ago, when I checked them as an alternative to Shodan. Back then their results weren't nearly as good as Shodan. However, when I checked back this winter, with all those juicy RCEs popping up, ZoomEye delivered quite solid results.
ZoomEye pros:
- They improve quickly and with huge leaps
- They seem to have good manpower behind the project.
ZoomEye cons:
- They require a mobile-number upon registration. I am waiting to grab another burner phone before setting up a full account.
Features
Basic features for pure OSINT-tasks:
| Feature | shodan | binaryedge | zoomeye |
|---|---|---|---|
| Free API | x | x | |
| Payed API | x | x | x |
| Free Webaccess w/out Account | x | x | |
| Free Account | x | x | x |
| Combined filtering | x | x | x |
| Download Searchresults | with delay | instant | x |
| freshness of results[2] | 3-4 days | weeks | ? |
| triggering scans | x | - | ? |
| ASN-Search | x | ||
| Vulnmapping | x | x | |
| support (A-F) | not so good | excellent | ? |
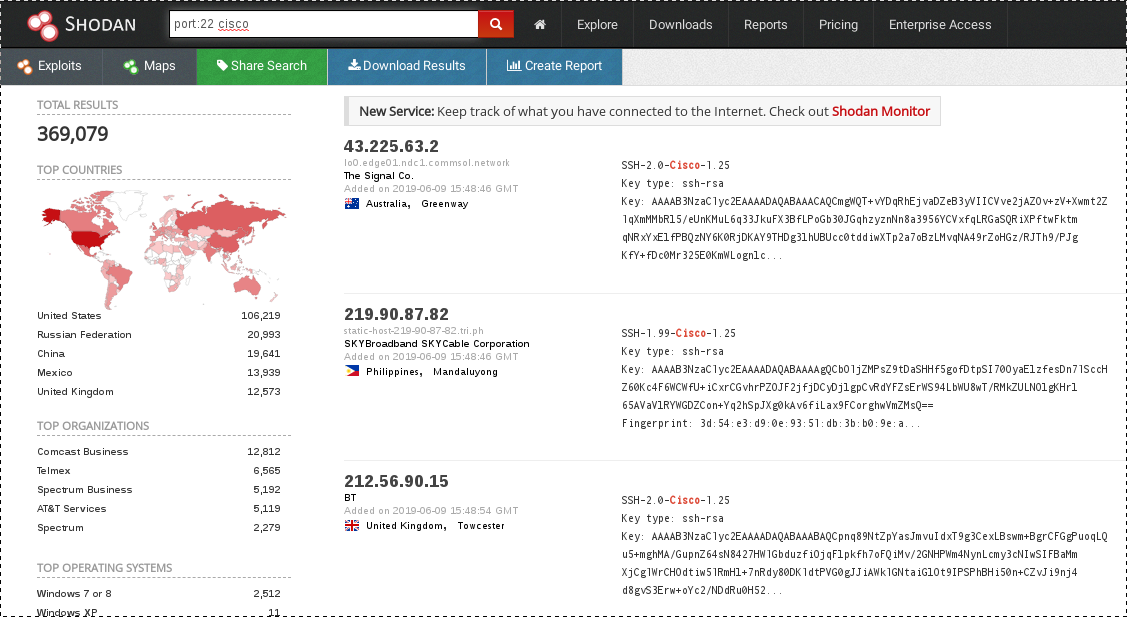
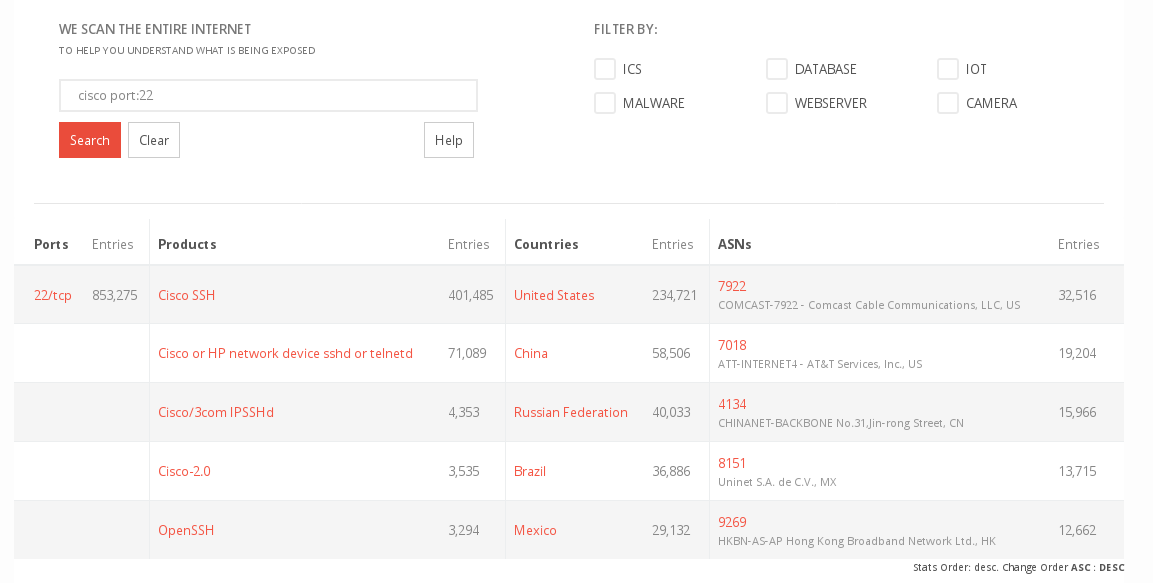
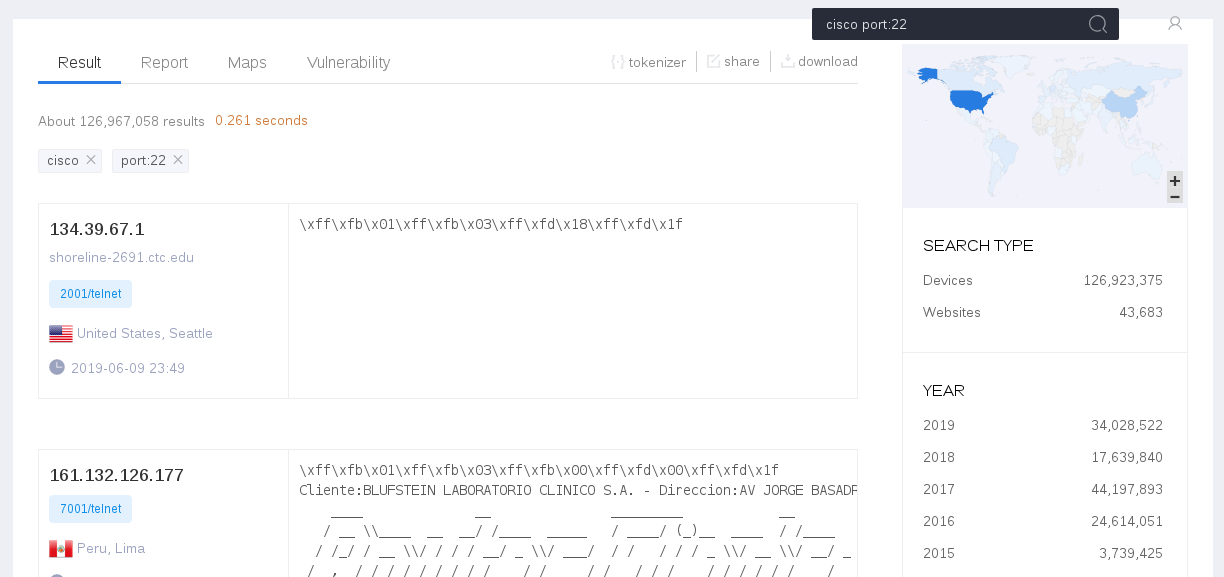
Some screenshots from the interfaces with search results:
Shodan:
BinaryEdge:
ZoomEye:
Advantages for each product:
All:
- The ability to search and filter with more than just IPs and ports
- Whole headers and informations, gathered while scanning are presented and searchable (e.g. cookies, serverheaders, versions)
- downloaded whole resultsets
Shodan:
- Clean interface, good drill down and aggregation, parts of header-info displayed
- Vulnerability mapping is nice
BinaryEdge:
- ASN-search is definitely a huge PLUS when doing large-scale-research
- Features like Image-Search (RDP anyone?), come in handy
ZoomEye:
- Historic results at your fingertips and searches can be limited to certain timeframes
- Vulnerability mapping is excellent
Once you get used to each of the interfaces, they all work very logical and developer-brain-friendly.
Resultsets
Now for the juicy parts: I checked resultsets from searches for various targets like vulnerable services and services/products in general.
Please Note:
- Numbers valid as of 2019-06-09
- ZoomEye results has been filtered to include only results from 2019-01-01 onwards
Vulnerable Services
I picked some nice RCEs from this year with quite a lot of discoverable servers. They are ordered by date ASC, link to an article with details and CVEs are given as well. When you click on the numbers for each service, you will be directed to the search-request I performed on each platform; a descriptive link to each vulnerability is added as well.
| Date | Vuln/CVE | shodan | binaryedge | zoomeye |
|---|---|---|---|---|
| 2019-03-20 | Confluence RCE CVE-2019-3396 |
19.000 | 53.000 | 34.000 |
| 2019-03-21 | Nexus Repository Manager RCE CVE-2019-7238 |
5.500 | 200 | 9.100 |
| 2019-04-04 | WebLogic RCE CVE-2019-2725 |
2.000 | 84.000 | 40.000 |
| 2019-05-09 | Typo3 RCE CVE-2019-11832 |
8.100 | 11.000 | 15.000 |
| 2019-05-14 | Windows RDP RCE CVE-2019-0708 |
2.600.000 [3] | 10.000.000 | 7.000.000 |
As a chart:
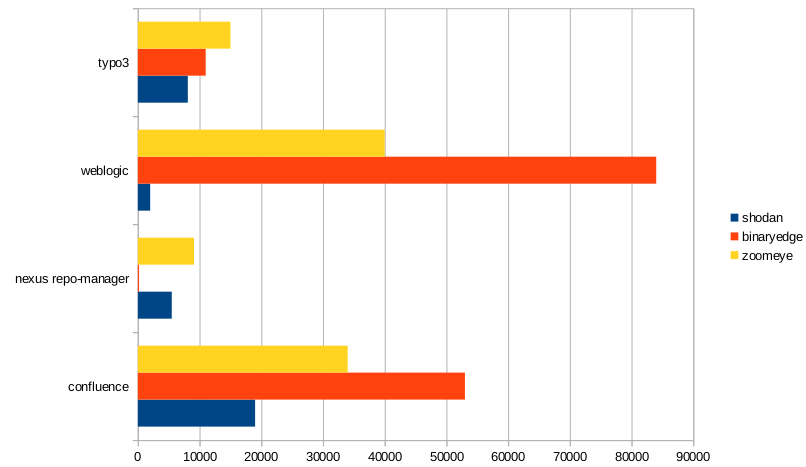
The result speaks for themselves.
Service-search in general
In a second step, I searched for some services and compared the numbers.
| Service | shodan | binaryedge | zoomeye |
|---|---|---|---|
| Memcached | 34.000 | 19.000 | 45.000 |
| MongoDB | 64.000 | 72.000 | 46.000 |
| SNMP | 2.100.000 | 0 | 2.200.000 |
| BGP | 700.000 | 0 | 700.000 |
| Citrix Netscaler | 26 | 72.000 | 48.000 |
| Cisco Port 22 | 370.000 | 430.000 | 580.000 |
As chart:
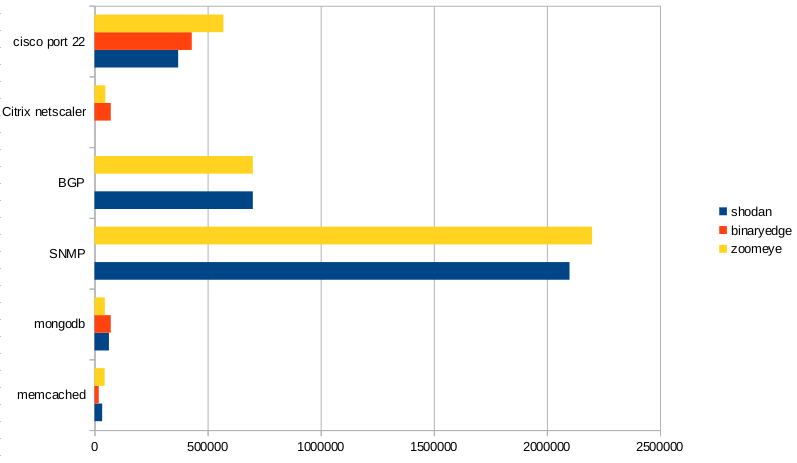
what you can see here:
- BinaryEdge is a little blind on the UDP-eye
- Compared by "raw" - results per port, Shodan still delivers good results
Conclusion
BinaryEdge and ZoomEye are totally comparable to Shodan. All three services differ by nuances and could be considered as a valuable addition into the arsenal. There is no clear winner and no clear loser. Every services has its pros and cons, but I like the fact that there is competition in the market.
What else is out there?
There are more than just these three. Let me list some of these services and explain why i didn't include them in the comparison:
- Censys.io - A good service, but the prices and limitations are ridiculous, nothing you would use when searching for, and downloading something with 300k results for an affordable price.
- Hackertarget.com and Securitytrails.com must be considered valuable tools when doing full-range-OSINT against a corporation; while they deliver results for certain IPs, you cannot use them for internet-wide researches
[1] - I speak mostly about data gathered by internet-wide scan
[2] - How old observed results might be (based on observation, not measurements)
[3] The resultset for shodan-RDP is somewhat hidden, the tag for Terminalserver/RDP-Server is missing in the products-section.
The awesome image in this article is called How to go Undercover and is by R A D I O

