The Daily Dose Of Malware OSINT Script For Hunting Fresh Malware Samples
Security researcher Wojciech created a brilliant OSINT script to help him harvest fresh malware samples that he calls the 'Daily Dose Of Malware'.

Looking for malware or command and control servers? I wrote a script I named 'Daily Dose Of Malware' which gathers information from OSINT (date, md5 and url) data related to malicious software. Supported platforms are Malcode, Malshare, Google, Cymon, Vx Vault and CyberCrime tracker among others.
Disclaimer
You are dealing with real malware, which may harm your computer. I’m not responsible for damages you do to yourself. Be careful and think.
Introduction
When I was learning how malware works and how it’s managed, I stumbled upon one pretty big obstacle, a place to source malware samples from. There are a lot of Github repos like The ZOO but mostly it contains very well known malware and it’s c&c servers are off. It’s great for analyzing still, but I wanted fresh samples.
For this purpose, most famous sites are malc0de.com and cybercrime-tracker.net, it’s updated when new malware appears. To make process of finding malicious software easier, I decided to build a model that allowed me to obtain malware samples that were not older than 3–4 days.
Daily Dose Of Malware
It’s hard to catch interesting malware in the wild because most of them are targeting specific group of people for various benefits. Then with rescue come open source platforms, which index malicious websites and payloads. And now, there is no need to visit each feed separately, DDoM connects it all and displays the newest info through OSINT sources.
Script allows you to download file directly from malevolent website or export information to text file for further analysis. Information are provided from mentioned feeds and only download option connects directly to malicious website, so if you want to use this option I suggest to get good VPN. It makes folder with samples, then you can transfer files to your sandbox and make a proper analysis.
Purpose
Researches who do not have access to private sources like for instance virus total or hybrid analysis also can follow malware campaigns. With provided data you can create small intelligence about popular campaigns used by crooks. Command and control servers allow you to get acquainted with different types of admin panels, used technologies, find interesting schemes or connection between variety of malware. You can also analyze files in order to dig deeper on particular case.
Additionally, it may be used as a defense against malicious software, for example by blocking C2 domains on your DNS or by adding md5 sum to your blacklist. What is interesting, sometimes you stumble upon unfinished malware, i.e. developer version or for testing purposes. It can give you insight how it’s evolving and what is the main target of the actor.
Usage
First, you need to specify source with -s flag, if you choose Cymon as a source then additionally option -cs must be passed as feed for Cymon. Last step is to precise if you want output to console ( — output option), export to text file ( — export) or download files ( — download). Screens are worth more than thousand words, so find usage below.
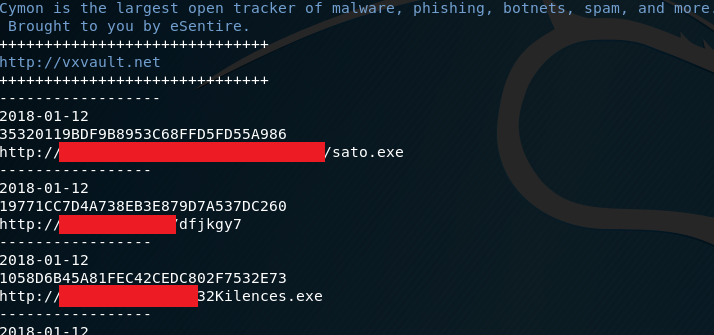
python ddom.py -s cymon -cs vxvault cct — output
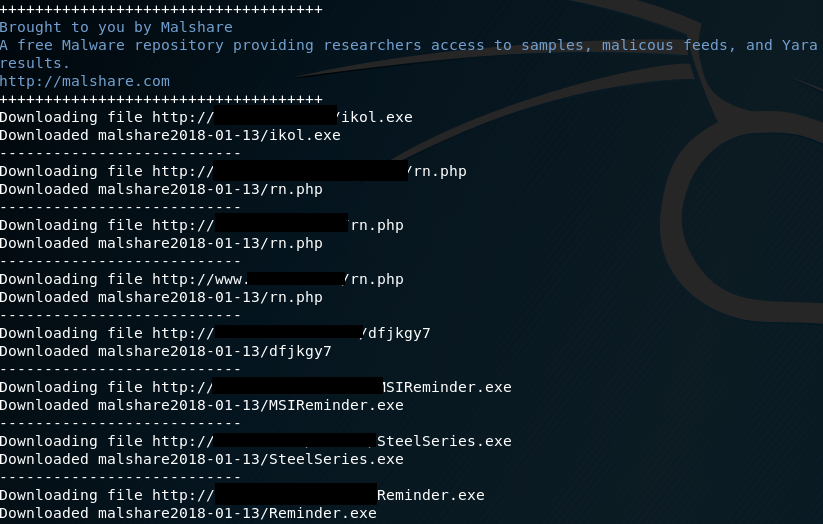
python ddom.py -s malshare — download
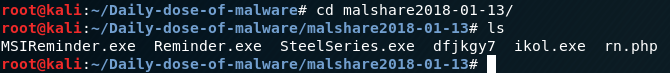
Downloaded malware from malshare
python ddom.py -s malcode malshare -e
Your export file will be named ‘source + timestamp’.txt and samples will be placed in directory with the same name.
Notes
- In case this script violates terms of use of any service used, I will delete it immediatelly if you let me know.
- Google can return false positives because of inaccuracy in dorks. Let me know if you have idea to extend this list.
- It consists of modules for every feed, so it can be easily expanded. If you know more public OSINT platforms for malware, let me know.
- More technical staff on Github.
You can find the script here.
Header Image : Cyber Creeper by Nate Perry
