OSINT Basics: Detecting and Enumerating Firewalls & Gateways
The following article will deal with basics and teach you how to detect and enumerate firewalls and gateways.
The following article will deal with basics from the Technical OSINT Manual and teach you how to detect and enumerate firewalls and gateways of all sorts (FW, VPN or Application-Gateways). This article is aimed towards beginners in the OSINT game.
Btw, I'm using my favourite tool binaryedge for showcasing screenshots.
Discovery by Hostname
Lets say, your task is to recon a company/domain, and you are able to perform a basic passivedns-recon against a domain, collecting as much hostnames in use as possible. All you have to do is to look for names like
- gw.example.com
- vpn.example.com
- secure.example.com
- fw.example.com
Below are some real-world-examples, taken from a recent scan.
here.com (vpn)
fra-a.ext.vpn.here.com (131.228.181.10)
fra-b-ext.vpn.here.com (131.228.181.11)
fra.vpn.here.com (131.228.181.12)
fra.vpn.here.com (131.228.181.9)
-----------------------------------------------
daimler.com (gw)
sagw.americas.daimler.com (141.113.144.21)
sagw.daimler.com (141.113.103.20)
-----------------------------------------------
various (secure)
secure.aov.de (193.28.21.10)
secure-bestsecret.noris.net (213.95.222.36)
secure-ccunirent-easyshare.noris.net (213.95.222.53)
secure.cinepostproduction.de (185.17.5.212)
secure-datev.noris.net (213.95.222.29)
secure-gw1-01.vocatus.de (213.155.79.108)
secure-nixdorf.noris.net (213.95.222.50)
secure.noris.net (213.95.222.6)
secure.qsc.de (195.158.160.6)
secure-vcenter.noris.net (213.95.222.13)
secure.vw-wecloud.de (213.95.222.42)
That method seems quite useful, but lets check, if there are gateways behind these IPs or not (you can always throw that IP into a OSINT-database of your choice though).
Discovery by Webinterface
So now you have some IPs/Hostnames, but you'd like to know if there is something to be found, and if so, what exactly.
Lets try this sagw.daimler.com and fire it up in a browser:
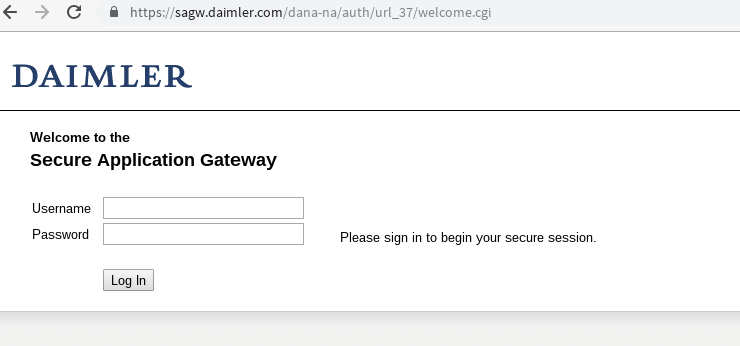
Et Voilá! There is something.
But what is it? Reading the sourcecode doesnt give a clue, but when i access the same source via IP, not hostname, it shows something different:
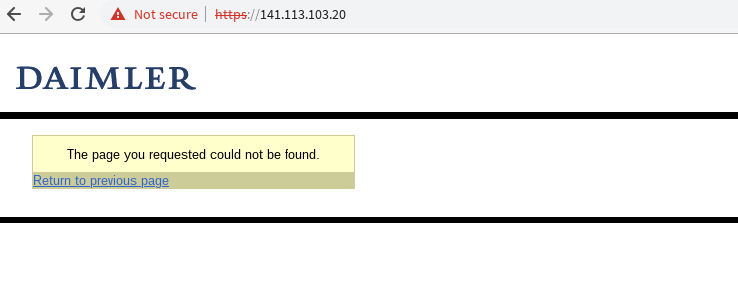
When i check the HTML-source i again, i get the info i wanted: a Pulse Secure VPN-Gateway
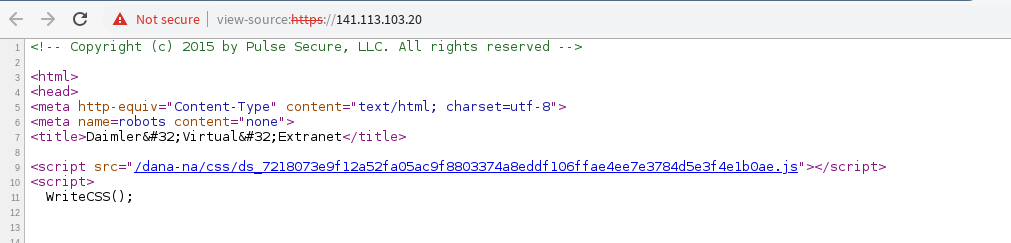
You'll recognize the "/dana-na/" - URL, and this information alone lets you search for all available Pulse-VPN-Gateways worldwide:
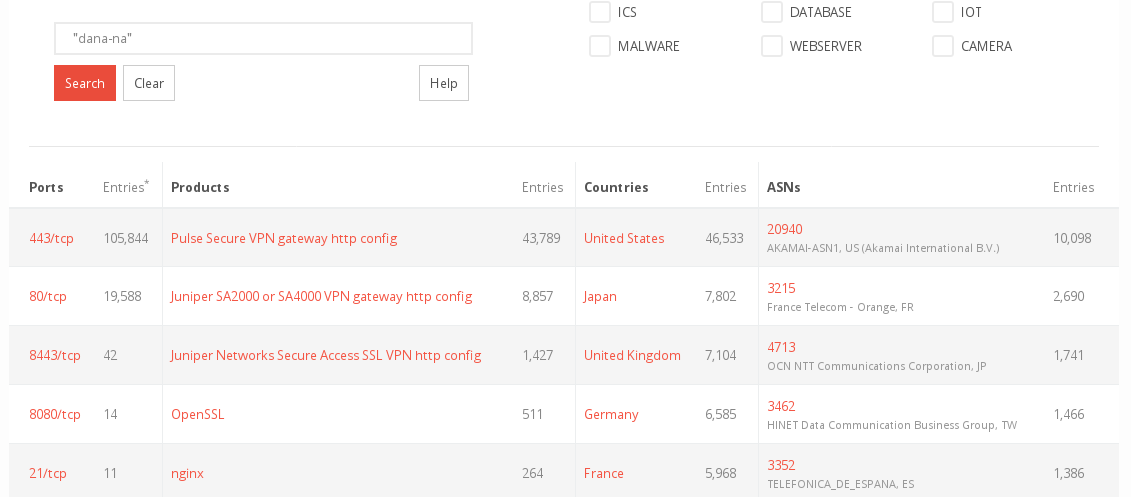
But Pulse is not alone with this, you can detect a lot of firewalls and gateways by their interfaces alone:
- Fortinet-VPN-Gateways tends to redirect to /remote/login
- Cisco-VPN redirects to /+CSCOE+/logon.html
- Netscaler redirects to /vpn/index.html
- ... you get the clou.
Discovery by Ports/Services
There are vendors, that really have an open heart for us OSINT-people.
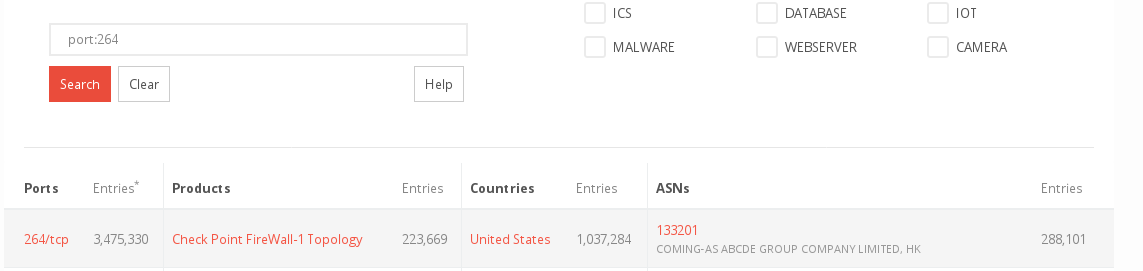
- Checkpoint for instance let us detect their firewalls by a custom port, 264 (sometimes 18264), even if no interface is exposed to the outside.
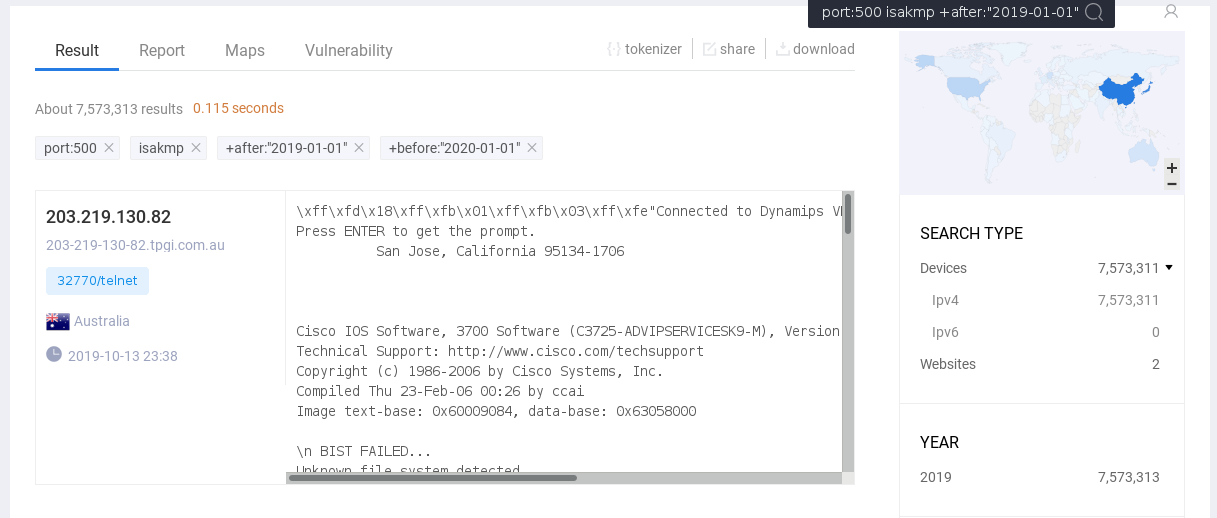
- Cisco-VPN (IPSEC iirc) is often found to have Port 500/udp open, as the following search on zoomeye shows:
Discovery by Banners/Headers
Sometimes we can use service-headers/banners to detect various devices, and again cisco is very helpful here (many devices are not firewalls, but router/switches though):
- Cisco-SSH advertises its own banner
debug1: Local version string SSH-3.14-OpenSSH_7.7-p42
debug1: Remote protocol version 2.0, remote software version Cisco-1.25
debug1: match: Cisco-1.25 pat Cisco-1.* compat 0x60000000
- Cisco IOS and telnet is very common
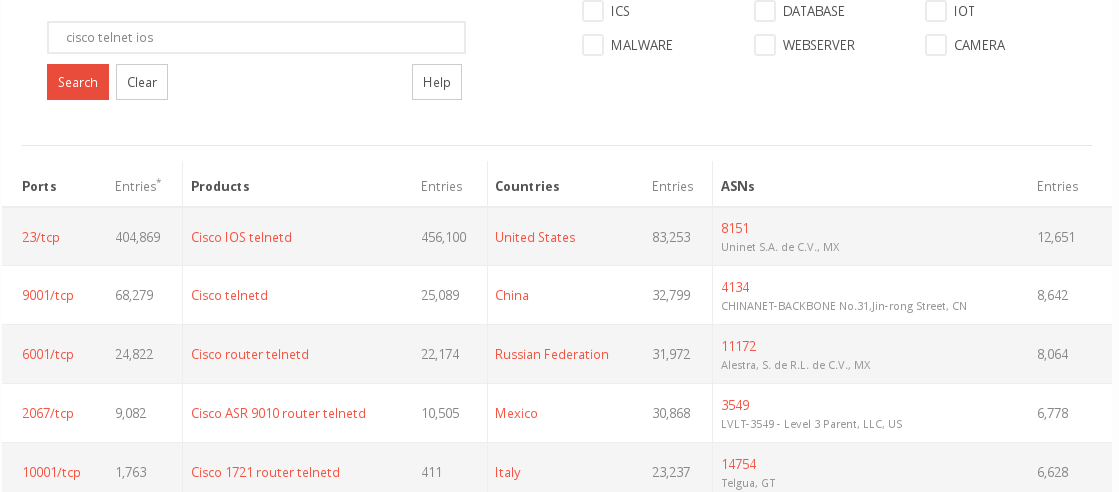
- Fortigate again helps us by using the Standard-Server-Header "xxxxxxxx-xxxxx", allowing us to find all servers with that header
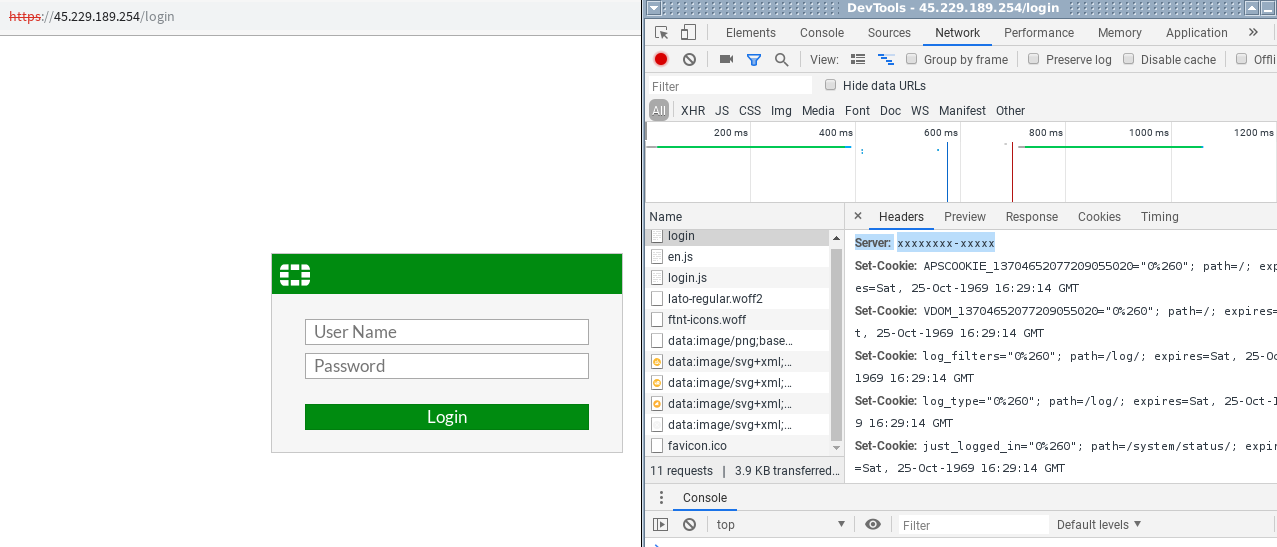
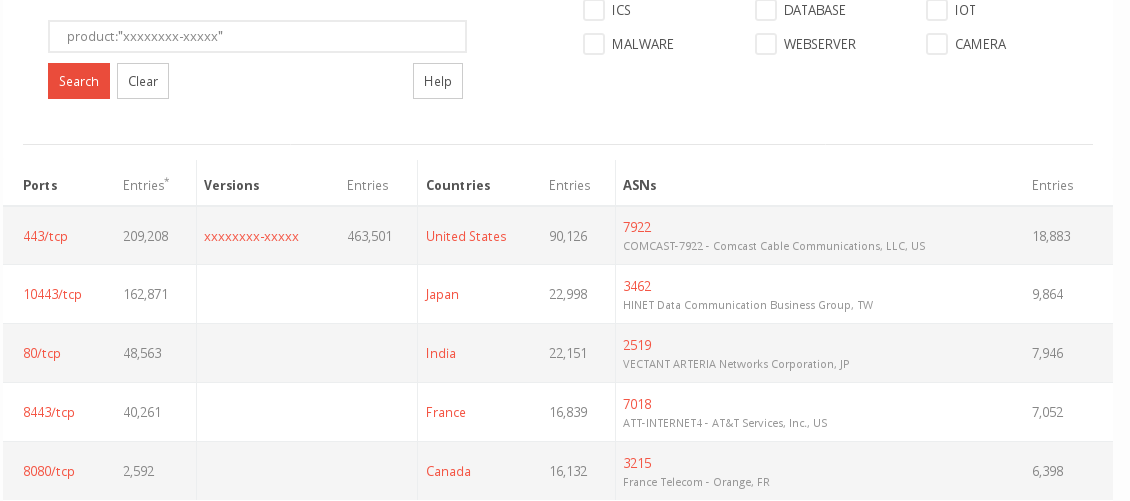
Discovery by TLS-Certs
During installation/setup, most firewalls and gateways, if available via TLS in any case, will setup a selfsigned certifcate. Since this process is automated for easier use, the most devices will have the name of its vendor written into the certifictae-information (Issuer Common Name / Issuer Organization)
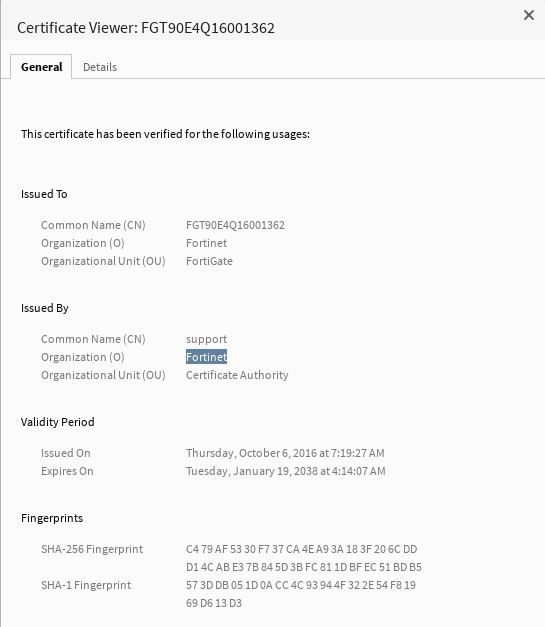
And since Binaryedge lets us search TLS-Certs as well ... lets do it!
- SonicWall: 450k hits
- Fortinet: 480k hits
- Cisco: 120k hits
- ... you get it.
Conclusion
You'll notice, some vendors are not mentioned here, and those are the ones who make it harder to recon their stuff and who will not show up in the average OSINT-databases like shodan, binarydge or zoomeye.
All the other examples above (without being complete), are helping an attacker with good OSINT-skills to enumerate the device, service and version, which can come in handy, if the device itself is not updated regularly and exploits exists.
Another problem should be mentioned: if you are a blue-teamer use a product that is easily detected, it WILL be indexed. If something like the latest PulseVPN/Fortigate Mayhem happens again, you'd better not have your company-access exploited.
Reduce your attack surface!
And last but not least, if i know which device is used by your company as firewall or gateway, i, as a red-teamer, can probably shoot some rubberbands on your firewall, allowing me to put you offline for 5$.
snippet!
And while OSINTing through the world, i found a Cisco-router/gateway with an open telnet; just wanted to share this little session with you.
$ telnet 123.45.67.89 1337
Connected to 123.45.67.89
Escape character is '^]'.
Connected to Dynamips VM "ISP" (ID 2, type c3725) - Console port
Press ENTER to get the prompt.
ash (Read/Write)
131072K bytes of ATA Slot0 CompactFlash (Read/Write)
Installed image archive
Press RETURN to get started!
*Mar 1 00:00:02.835: AAA is disabled
*Mar 1 00:00:03.291: %LINEPROTO-5-UPDOWN: Line protocol on Interface VoIP-Null0, changed state to up
*Mar 1 00:00:03.295: %LINEPROTO-5-UPDOWN: Line protocol on Interface IPv6-mpls, changed state to up
*Mar 1 00:00:03.651: %SYS-5-CONFIG_I: Configured from memory by console
*Mar 1 00:00:03.775: %LINK-3-UPDOWN: Interface FastEthernet0/0, changed state to up
*Mar 1 00:00:03.779: %LINK-5-CHANGED: Interface FastEthernet0/1, changed state to administratively down
*Mar 1 00:00:03.779: %LINK-5-CHANGED: Interface FastEthernet1/0, changed state to administratively down
*Mar 1 00:00:03.779: %LINK-5-CHANGED: Interface FastEthernet2/0, changed state to administratively down
*Mar 1 00:00:03.967: %SYS-5-RESTART: System restarted --
Cisco IOS Software, 3700 Software (C3725-ADVIPSERVICESK9-M), Version 12.4(6)T, RELEASE SOFTWARE (fc1)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2006 by Cisco Systems, Inc.
Compiled Thu 23-Feb-06 00:26 by ccai
*Mar 1 00:00:03.975: %SNMP-5-COLDSTART: SNMP agent on host ISP is undergoing a cold start
*Mar 1 00:00:04.019: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is OFF
*Mar 1 00:00:04.439: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback0, changed state to up
*Mar 1 00:00:04.491: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback1, changed state to up
*Mar 1 00:00:04.495: %LINEPROTO-5-UPDOWN: Line protocol on Interface Loopback2, changed state to up
*Mar 1 00:00:04.771: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/0, changed state to up
*Mar 1 00:00:04.779: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/1, changed state to down
*Mar 1 00:00:04.779: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet1/0, changed state to down
*Mar 1 00:00:04.779: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet2/0, changed state to down
*Mar 1 00:00:48.727: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.2.3 on FastEthernet0/0 from LOADING to FULL, Loading Done
*Mar 1 00:00:53.583: %OSPF-5-ADJCHG: Process 1, Nbr 192.168.2.2 on FastEthernet0/0 from LOADING to FULL, Loading Done
ISP>show ?
aaa Show AAA values
aal2 Show commands for AAL2
alarm-interface Display information about a specific Alarm Interface
Card
appfw Application Firewall information
auto Show Automation Template
backup Backup status
bcm560x BCM560x HW Table
bgp BGP information
call Show call
caller Display information about dialup connections
cca CCA information
ccm-manager Call Manager Application information
cdapi CDAPI information
cef Cisco Express Forwarding
cem cem channel information
class-map Show QoS Class Map
clock Display the system clock
cns CNS agents
compress Show compression statistics
connection Show Connection
context Show context information about recent crash(s)
control-plane Control Plane information
ISP>show bgp
% BGP not active
ISP>show controllers
Interface FastEthernet0/0
Hardware is GT96K FE ADDR: 665F2FCC, FASTSEND: 606E8924, MCI_INDEX: 0
DIST ROUTE ENABLED: 0Route Cache Flag: 11
GPIO 2 CONF= 0 GPIO 2 IO= 0 CIU arbit = 80000000
PHY add register = 0x0 PHY data register = 0x8000000
Port Conf Reg= 0x80 ENABLE HT8K HMOD0
Port Conf Ex Reg= 0x4CD00
TX1:1 RXPRI=DE(00) ~FLCNTL ~FLNKP MFL64KB FE
Port Com Reg= 0x0
Port Status Reg= 0xF 100MB FDPX FCTL DIS LNK UP ~PAUSED TX oFF
Serial Param Reg= 0x0 Hash table pointer= 0xF5A5B60
Source ADDR L= 0x0 Source ADDR H= 0x0
SDMA conf reg= 0x223C RETX 15 RX BE TX BE FRINT BSIZE 4
SDMA com reg= 0x30080 STP TXL STP TXH EN RX
IMASK= 0x90003DCD ICause= 0x0
Serial 0 mask 30000F3Serial 0 cause 0
IpDiffservP0L= 0x0 IpDiffservP0H= 0x0 IpDiffservP1L= 0x0 IpDiffservP1H= 0x0
IP VLAN TAG PRI= 0x0 IP VLAN TAG PRI= 0x0
First rxd Q0= 0xF5E5C20 Curr rxd Q0= 0xF5E5C20
First rxd Q1= 0xF5E6040 Curr rxd Q1= 0xF5E6040
First rxd Q2= 0xF5E64A0 Curr rxd Q2= 0xF5E64A0
First rxd Q3= 0xF5E6900 Curr rxd Q3= 0xF5E6900
First txd Q0= 0xF5E6E20 First txd Q1= 0xF5E75A0
gt96kfe_instance=0x665F40AC, registers=0xB4084800
RxRing entries=64, tx ring entries=128
RxR0=0x F5E5BE0, RxR1=0x F5E6040, RxR2=0x F5E64A0, RxR3=0x F5E6900
Malloc RxR0=0x F5E5BE0, RxR1=0x F5E6040, RxR2=0x F5E64A0, RxR3=0x F5E6900
SDOW RxR0=0x665F46A4, RxR1=0x665F47D8, RxR2=0x665F490C, RxR3=0x665F4A40
HEAD RxR0=0x4, RxR1=0x0, RxR2=0x0, RxR3=0x0
TAIL RxR0=0x0, RxR1=0x0, RxR2=0x0, RxR30x0
...
ISP>show appfw ?
configuration Application Firewall Policy configuration
dns DNS Name Management
name Appfw name
ISP>show control-plane counters
Feature Path Packets processed/dropped/errors
Aggregate 504953/0/0
Host 0/0/0
Transit 365512/0/0
Cef-exception 139441/0/0
ISP>show control-plane host open-ports
Active internet connections (servers and established)
Prot Local Address Foreign Address Service State
tcp *:23 *:0 Telnet LISTEN
tcp *:80 *:0 HTTP CORE LISTEN
tcp *:1720 *:0 H.225 LISTEN
tcp *:5060 *:0 SIP LISTEN
udp *:67 *:0 DHCPD Receive LISTEN
udp *:2887 *:0 DDP LISTEN
udp *:5060 *:0 SIP LISTEN
udp *:2517 *:0 CCH323_CT LISTEN
ISP>
ISP>show ip arp
Protocol Address Age (min) Hardware Addr Type Interface
Internet 192.168.2.2 52 c204.604d.0010 ARPA FastEthernet0/0
Internet 192.168.2.3 52 c203.61d4.0010 ARPA FastEthernet0/0
Internet 192.168.2.1 51 c201.6508.0010 ARPA FastEthernet0/0
Internet 192.168.2.254 - c202.6371.0000 ARPA FastEthernet0/0
ISP>exit
Happy Hunting!