Reconnaissance for Beginners (2)
A beginners guide to reconnaissance and how to investigate a target.

In my first article on cybersecurity for beginners, I gave an overview on the different phases of attack, in this article we will focus on reconnaissance and how to go about investigating your target.
Reconnaissance
As I mentioned, reconnaissance is an investigation activity, one where we investigate the system to be attacked. To make things easier I have divided investigations into three categories: networking, system and organization/individual.
For networking you have to try to identify methods of access to the system or network that is your target, authentication methods, name of domains within the network or set up into the specific system, IP addresses available within the Network, communication protocols, systems and services available and all other things that can be related to networking systems.
When it comes to reconnaissance on the system, you try to find passwords, routing tables, architectures, users, groups and so on.
When you perform reconnaissance on an organization or individual (depending on the type of target to which you approach, an organization in case of a company, then an entire corporate network... or an individual in the event of a system such as a personal computer), we are investigating information regarding the people who interact with the attached systems.
Some of this information is addresses and phone numbers, the background of the people, a company's management, detailed information about employees of the company or the individual himself. Above all, you have to consider the social networks used by those who have access to the system. I would like to stay a little longer on this aspect, which is poor by the technical point of view, but also the place where, in most cases, you'll obtain most of the information on the object of attack.
Especially the social aspect, on the main battlefield the psychological aspects mean more than technical ones. What I mean is that a psychologist probably has more chance of success in working our a users password than a hacker who knows all the exploits contained on exploit-db for a specific system. To make you understand what I mean, just think that the information of everyone you meet on the street, are almost all contained (and public) on his Facebook profile (or LinkedIn, Twitter).
Recently I watched a show where they showed how, by stopping someone in the street, it was possible to know a huge amount of information on them just by surfing their social profiles. Let me give you a clear example, your email is probably posted somewhere on one of your social profiles, an attacker who wants to try to access your email, browse the portal of your provider, once in front of the access form will do simply enable the password reset process (it is a procedure that is mandatory on many systems). At this point, the provider will make sure who you are saying to be, will ask you to answer the security question that you have set during the registration process to the site, such as "what's the name of my pet?".
So don't share the name of your pet on a social network if you can help it. You have never posted a photo of your cat with a tag "my sweet friend Felix!!!". No, certainly not, the questions have become more complex now, like "what was the name of my favorite teacher in junior high school?". You probably do not give out information like this on your profile, but you probably have given information about the schools you've attended and maybe you have not published even your date of birth, but there are online algorithms that evaluate the hypothetical age of a person from a photo and countless OSINT ways to find your age.
So your school, the time when you atended more or less... do you think that it is not possible to find the list of teachers for specific school years for a specific school?
Now we have also a nice list not too wide, all that remains to do is to fix it and try a good brute-forcing on the portal. How much of this has a technical aspect? Only the brute-forcing activity, the rest is the result of more or less deep research on what you have shared with the whole world (of course, because your profile is public). Fortunately, social and portals are adopting a bit more "complex and secure reset/recovery password systems", but do not let your guard down, normally it's only a matter of time, a secure system today will not be secure forever.
Before going ahead, I report below a photo of a successful attack that the intrinsic nature of the exploit is really... "striking". It is an interview with a journalist from a French TV and passwords are clearly visible on the screen behind him!
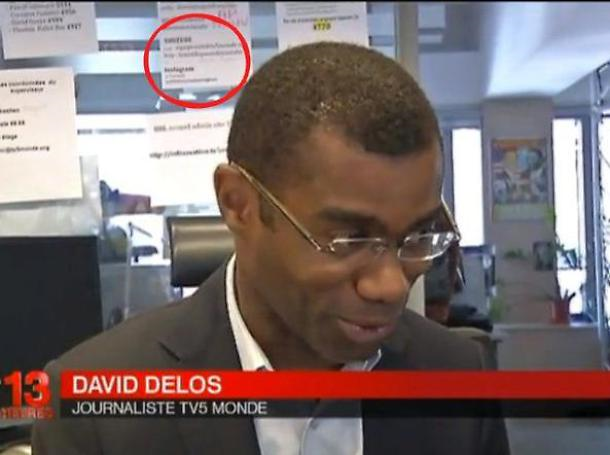
Just to conclude, the activities described above are called "passive search", that is, the information is retrieved from sources not strictly relevant to the target system (the company server or the personal pc).
Returning to the reconnaissance argument, probably what most interests us "vulnerability researchers", is a technical aspect, so networking and system. The identification work that takes place at this stage is instead called for "active search", where we try to retrieve information directly from the target system.
Normally we start with a question of the particular system that gives us an access point to the same, whatever it might be an IP address, a URL or an entire corporate network. Based on the specific information you have and the result of a first look, you can proceed for a way instead of another. There are different modes of attack, as we have said, unfortunately, list them all is almost impossible because there are different ways to get the final result.
Server and Device
Start with one of the most common reconnaissance methods, one oriented towards the discovery of a single machine. Obviously, in this case, you should have its a single IP or a network, the process is more or less similar, in the second case you'll identify a list of IP within the network and then considering one at a time, the way to proceed will be like the first case. You can also proceed with more machines in parallel, but it is often better to focus on a single instance, to not wander and get lost in the maze of many machines that you can find on the network, at best, we collect information that will be, after, the specific object of study. Anyway, in both cases you'll move in the same way; tools are the same. Well, our first tool is nmap:
nmap (or "Network Mapper") is a free and open-source utility for network discovery and security auditing.
This tool is used both in the cases of a network or a single machine. In the first case, we proceed with the nmap command to identify the active computers on the network:
nmap -sn 192.168.1.1/24The -sn option, allows to carry out only the scan via ping, basically, simply verifies the response of a computer to a possible ping, avoiding also to carry out scanning of the ports. As I said, if you have a hurry and have no time to lose, you may carry, in addition to searching for computers, also directly scanning the doors, to better identify the computers... "most interesting". The number of IP addresses to be scanned can be specified in several ways:
- space-separated list: 192.168.1.1 192.168.1.5 192.168.1.9 (in this case three addresses of the same network that ending for 1, 5 and 9)
- range: 192.168.1.1-10 (the first ten IP addresses on the same network)
- the entire LAN: 192.168.1.* (from 1 to 255)
- by subnet mask: This is a bit more complex, but you can specify a more complex set of addresses; to understand, in the example above, the result is the same of the previous point, but I'm specifying the subnet mask 255.255.255.0 on the addresses 192.168.1.* (the 32-bit data of the entire address, I am considering as fixed the first 24 bit, then 8 + 8 + 8 + 0 = 24)
PS: if you are not comfortable with the command shell, in many distributions mentioned above, or at least easy to install, a GUI tool called zenmap is available, allowing you to select and set via selections and drop down, the same options that you have on the command line. Even Armitage has integration with the nmap tool and records the machines on which you perform the audit in a graphical interface keeping the output of the scanned machines.
Once you identify the addresses of your interest (let us consider only one, to take the second of our cases), we proceed to retrieve specific information of the machine, ie, in this case, each "port" open that it may be a possible vulnerability. Each open port identifies a service running on the machine. Usually, you do an activity that nmap identifies as an "intense scan all TCP port". Following a series of commands that you can perform to get the information searched, with its description:
# scanning the specific port 80 of the machine with the address 192.168.0.1
nmap -p 192.168.0.1 80
# enables the identification of the operating system, could be possible that the identification fails
nmap -A 192.168.1.254
nmap -O 192.168.1.1
# seeks to identify the services and the version running on each port
nmap -sV 192.168.1.1
# standard command for port scanning, with an output verbose and a long execution time
nmap -v -A -sS -T4 192.168.2.5These commands will provide you information more or less important, similar to the one below:
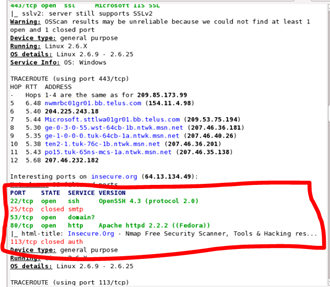
What interests us, is the part of the open ports and the description of the service running on that. Near you should also have the details of the operating system (if the tool can recover, otherwise you will have to try to understand it using the services running on ports).
Knowing the Operating System is one of the critical points to proceed with the recognition; the two basic streams are divided between Linux and Windows machines and tools to use are different in both cases.
Windows machines
If we found windows machines what often you can read in the forum is "enumerate." It might seem useless tips, but in this case, the "enumeration" is an essential step for windows machines.
The designated tool for this activity is called enum4linux.
Enum4linux is a tool for enumerating information from Windows and Samba systems. It is written in Perl and is a wrapper around the Samba smbclient tools, rpclient, net and nmblookup.
The command syntax is simple:
enum4linux [options] IPThe options are many, with the enum4linux -h command it is possible to have a comprehensive online help that describes in detail all the options available, to have in any case already a complete scan of the Windows machine, simply runs the command without options with only the IP address to query.
The entire package of information that you can retrieve is really wide: the list of the local users’ machine, the available groups and the membership association between them. The usefulness of such information, like to know the users of the machine, the groups of each one and the policies for the creation of the password is definitely like having the keys of an apartment.
Here some syntax and features activated by the specific command:
# performs a complete scan of all that you can enumerate
enum4linux -a 192.168.X.XX
# retrieves a list of usernames
enum4linux -U 192.168.X.XX
# retrieves the local machine groups
enum4linux -G 192.168.X.XX
such as nmap command, enum4linux can try to recover the OS information, of course, you already know that it is a windows system, but know the specific version could be an added value
enum4linux.pl -o 192.168.X.XXOk, but beware, because the enumeration is not always possible, you may run into windows machines that were still protected from this type of activity; you might be lucky if you have a credential enabled to query that information, in this case, you could use the same command, specifying credentials in your own:
enum4linux -u <username> -p <password> -U 192.168.X.XXThe enum4linux is a very useful complete tool, but, let me submit also another tool.
This tool is the smbclient. I mention it because later we will see him also as an "intrusion tool".
The functionality that at this stage of reconnaissance interests us is the enumeration of the shares of the Windows machine, ie services and shared folders with the outside (who coming from the Microsoft world, probably already know this share, some of this are made available by default from the OS, such as C$, IPC$ and a few others, of course, to access you need credentials with administrative rights).
To enumerate the share, the command to run is the follows:
smbclient -L 192.168.X.XXThe enumeration maybe allows only to specific authorization, in this case (if you have), you can specify the user with which to execute the scan, of course, you will be prompted to enter the password:
smbclient -U <domain>\\<username> -L 192.168.X.XXThe command will be back later as I said about the "intrusion". For completeness of information, however, the same operation is possible to perform it via the enum4linux command with the following syntax:
enum4linux -S 192.168.X.XXLinux Machine
For Linux, the scenario is a bit different. A similar command to use in the same way like the enum4linux, but towards Linux systems is finger. The finger command enumerates users of the machine, but normally is not a default service active after a normal installation of linux machine, so, it has to be activated on purpose. Metasploit has a scanner for this service, which attempts a brute-force of the users, using standard users or a dictionary.
Anyway, the reconnaissance activities, continue, focusing on services and open ports on the target machine.
Before the next phase
We could talk again about reconnaissance, but what I want that you understand is that doesn’t exist a checklist to tick for the success of a cyber attack, it isn’t like to go to the grocery store with a list of stuff to buy, each scenario is different from the other one and know-how that you will take from an attack will be your background to increase your ways of thinking and to approach to a new environment. You are going to reuse some of that knowledge on the new targets that are going to attack, but in part, you will have to identify new penetration mode. The systems are evolving and each time exploits are fixed in the new version.
The few indications that I stated just above, is a common starting point, the only actions that maybe are accomplished "always" (be careful, in this case, we are talking about an attack on a server, the goal is to penetrate a machine/device by exploiting vulnerabilities, different attacks may have different initial actions, see for example generic phishing). I try to make one last example to explain how an attack progresses; if we compare the possibility of evolution of an attack, this can be represented by a tree diagram, where the branches expand and duplicate quickly...
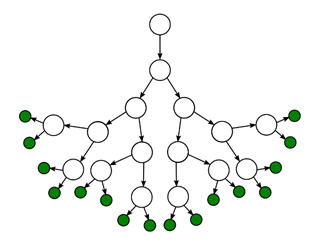
...and more services will you identify, more you’ll have ramifications; a bit as, surely you know, the tree diagram of the Linux distributions!

