How The Air Gap Got Its Groove Back
The idea of using an air gap for cybersecurity is an old idea, it harks back to the good old days when we weren’t paranoid about being hacked through the air.

The idea of using an air gap for cybersecurity is an old idea, it harks back to the good old days when we weren’t so paranoid about being hacked through the air. In those days, if you walked into a high security environment you would quite often see workers with two computers on their desks, each connected to different networks, each computer physically isolated from the other. An air gap in between them.
The vast majority of cyberattacks infiltrate networks from the open internet and in this context air gapping a computer containing sensitive information is a good idea.
It made a lot of sense in the old days, shut down the infiltration points on the networks by shutting off the internet. For those who did need access to the internet, you simply gave them an extra computer connected to a physically isolated network, confident in the knowledge that hackers could not magically jump through thin air.
Air gapping was frequently used in military and government networks, but you also tended to see air gapped networks in industrial control systems (SCADA), financial systems (stock exchanges), or on mission critical systems like nuclear power plant control systems or the avionic and the control systems on an aircraft.
Fast forward to today and the air gap is not quite as sexy as it used to be, air gap isolation as a tool of cybersecurity has been discredited for a number of perfectly decent reasons. Lets take a closer look at them before we continue.
An Air Gap Can Be Breached
Those of you who are into covert channel attacks can point out half a dozen instances where air gapped computers were successfully hacked. Some actors have developed special hardware specifically designed to penetrate air gapped networks and you can even use smartphones to penetrate an air gapped network if you can penetrate the area its located in. Here is a decent thesis outlining the ‘out-of-band covert channels’ (OOB-CCs) used to breach air gapped networks using acoustic, light, seismic, magnetic, thermal, and radio-frequency based techniques.
An Air Gap Can Cost You Money
Isolating your internal network from the outside world is a bad idea for modern business. Modern businesses operate in competitive global markets and modern networks need all kinds of live data to operate, they need production data, software integrations, automation data, engineering data, social network data and software updates. For most businesses, connecting your internal network to external networks is a defacto requirement of leveraging modern IT infrastructure.
In the face of these completely reasonable arguments, the air gap as a tool of isolation cybersecurity fell out of fashion, no executive would reasonably consider shutting off their internal networks from the outside world and I don’t know anyone who would consider physically disconnecting themselves from the internet in order to protect themselves from malware (I actually do, this is a lie).
Over time, almost everywhere, the poor old air gap fell out of fashion as it outlived its usefulness in a modern connected world, there were just too many compelling reasons not to air gap your IT infrastructure for most organizations to ignore.
Forget That Noise
None of this matters when it comes to web browsing. Think about the air gap as a way of isolating your web browser and the air gap model starts to look sexy again.
According to Gartner browser isolation is a top ten security technology, because when you think about where all the malware, viruses and cyber attacks actually originate from, air gapping web browsers makes a lot of sense. The internet browser is the primary attack vector for malware, ransomware and cyber attacks, simply because we expose our computers to external networks (the outside internet).
Browser isolation is a simple idea and an evolution of the old air gap cybersecurity model. When we talk about browser isolation in technical terms, we are really talking about physically isolating your browser from the rest of your machine, your networks and the rest of your organizations IT infrastructure.
With remote browsing, you are physically isolating your web browser away from the rest of your IT infrastructure, separating the most vulnerable part of your IT (the part most likely to be affected by malware, ransomware or cyber attacks) from the valuable part of your IT (databases, accounting systems, R&D).
Browser isolation is a smart way to shut down 95% of the hatches that hackers use to infiltrate your business and free up valuable technical resources to focus on other vulnerabilities in your IT infrastructure, browsers are no longer a concern.
This browser isolation model of cybersecurity has been embraced by the US federal government because it is highly effective in the real world. I was one of the co-developers of the Safeweb browser isolation model, a model that I developed in collaboration with Lawrence Livermore National Laboratory, we pioneered the remote browser model with more than five thousand users and it worked brilliantly.
The legacy technology we used at the time was virtualization based, specifically non persistent VDI, with a centralized architecture, built upon isolated cloud servers
Air gap browser isolation today is widely used by government institutions and big business, both of whom have valuable IP to protect. The reason the air gap got its groove back is because the risk of your organizations air-gapped browsers being breached on a large scale using out-of-band covert channels is very low.
Some hackers can breach that air gap if they really, really want to, but your average cybercriminal simply doesn’t have the time to hack lots of internet users in this way. Browser isolation as a tool of cybersecurity works at scale because its just not realistic to hack more than a few people at once using out-of-band covert channels.
Unless your attackers are seriously motivated, highly skilled, well funded and have a specific interest in hacking you, a remote browser will protect most of your users from most of the cyber attacks, most of the time.
Don’t Connect Browsers To Every Other Part Of Your Business
The vast majority of businesses do not really need their browsers to be connected to anything else, the browser is a standalone piece of software used for a specific purpose and you can easily physically isolate it away from the rest of your business.
The browser is just a window we look at the outside world with, one that can easily be isolated away from the rest of your IT without causing pain to your financial bottom line or annoying your users. In my view browser isolation is the future of end user cybersecurity and while there are different providers of browser isolation platforms, they are all trying to achieve the same goal, isolate cyber risk away from your business.
We no longer call it an air gap though, we call it a WEBGAP. The word has become the worlds favorite way of thinking about a gap between you and the internet.
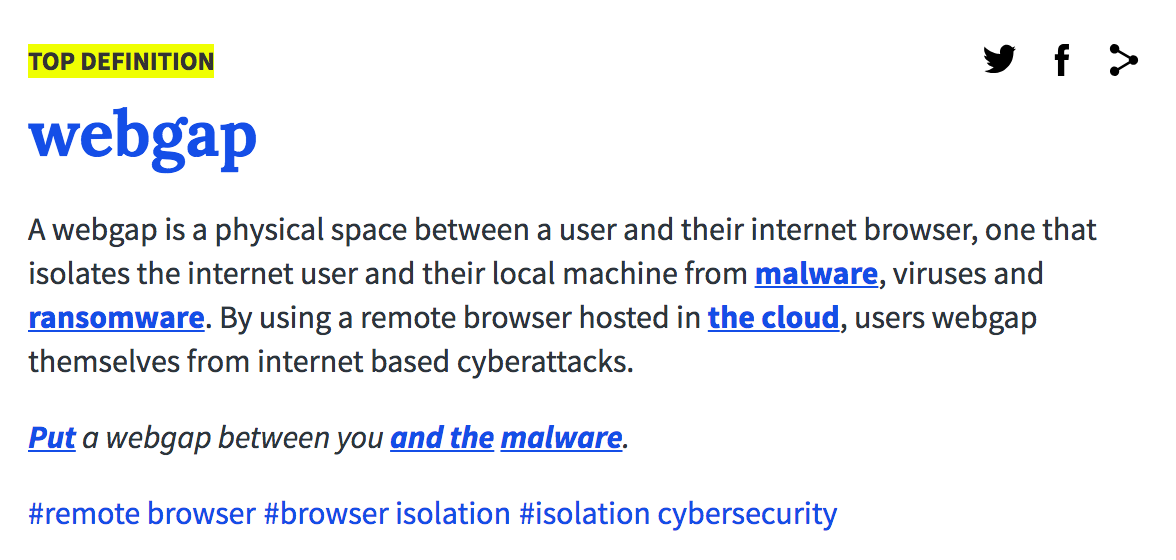
The air gap has gotten a bad rap over the last decade, but thanks to remote browser isolation and a rebrand to WEBGAP, the air gap finally got its groove back.


