How OSINT Is Used In SIM Swap Scams
Learn how scammers leverage OSINT when running SIM swap scams, and some of their common techniques.

SIM swap fraud is an increasingly widespread means for hackers to steal access to your phone number and then your identity. This kind of fraud is so successful because it is designed specifically to target the widespread default security measures that are supposed to protect you. In this article, we will explain how a hacker can SIM swap almost any phone number and how you can keep safe.
Why Your Phone is the Gateway to Your Identity
Your phone number is often the gateway to stealing access to your money and your identity. After the hacker takes your phone number, they can log into your email account without using your password.
Instead, the hacker clicks on the “Forgot My Password” option and usually, the default security measure is for the email provider to send a text message to your phone with a unique code number that is needed to log in. Because the hacker SIM-swapped your phone, the security text will go to the hacker’s phone instead of yours. After logging in, the hacker can reset your password so you are locked out of your account.
Unfortunately, this is only the beginning. The “Forgot My Password” option on the rest of your accounts (think of your credit cards, social media, bank, etc.) is usually set by default to send a link or code to your email or phone. After taking over your email, the hacker can gain access to your other accounts and lock you out.
When you contact your bank to regain access, you will have to go through a long and arduous process of proving to them that you are the true account owner, as opposed to the other person claiming to be you, who has the password, email, and phone that the bank has on file for your account. By the time you prove you are you, the hacker will probably have done whatever they planned for your accounts.
If you are a manager or a business-owner, the threat is not just against you personally. If your employees are targeted, a hacker could use an employee’s account to potentially gain access to your business network.

What is a SIM-Swap
Your smart phone likely has a SIM (Subscriber Information Module) card in it, which is basically a piece of plastic with a chip in it that holds the phone number and some account data. Normally, if you take your SIM card out of your phone and put it in a new one that will transfer the phone number to a new phone. But in a SIM-swap the hacker takes your phone number from your SIM card.
Hackers SIM-swap people by calling their phone service providers (also known as carriers), impersonating their victims, and claiming that their phone was lost or stolen. If your phone is lost or stolen, service providers can transfer your phone number to a new phone, and SIM, of your choice. Hackers take advantage of this system by buying a cheap phone and then calling your service provider and requesting to have your number’s service rerouted to it.
The main factor in a SIM-swap is for the hacker to convince the victim’s service provider that they are the true account owner. The default and most common security practice used by service providers is for the providers’ representative to ask the caller (who claims to be the phone’s true owner) a number of security questions. These questions are intended to “prove” that the caller is the actual owner of the phone number. To cheat this security practice, the hacker needs to know some personal information about their victim so that they can answer those questions.
How They Do It
Usually, a hacker does not need to know much about their victim and can even start off by knowing nothing other than the victim’s phone number. Consider a hypothetical hacker targeting you. Even if you never post any information about yourself on the internet, a hacker is still able to find enough relevant information about you to pull off a successful SIM-swap while relying only on using publicly available sources.
To start with, the hacker needs to know which service provider to call. They can use websites like Free Carrier Lookup, that will identify any phone number’s service provider for free.
The next step is to find out enough information about you to pass the security questions.
A January 2020 study from Princeton University investigated the default security screening for five major carriers (T-Mobile, AT&T, Verizon, Tracfone, and U.S. Mobile). The study documented service providers’ security screening parameters in response to people calling and claiming they are the account owner and needed to transfer their phone number to a new phone.
The study’s results showed that there were certain kinds of information that covered one or more of all five major carriers’ security questions. This included personal information and usage details such as the account owner’s current or former addresses, age / year of birth, email address, and/or phone numbers that the phone might have recently called. This information is available online for any phone number.
The study found that the customer service representative asking the security questions might ask for other kinds of information instead. However, callers in the study that did not know the answers, or even those that gave the wrong answers, were allowed to move on to other questions to try again until they landed on a question that they could answer correctly. This suggests that as long as the caller had the personal and usage information referenced above, they were likely to pass the screening.
How They Find Your Personal Information
Many people believe that they are safe from these kinds of scams if they do not use social media or at least do not post personal information. In truth, a hacker does not need to use your social media to find your information.
There are several people-searching websites (truepeoplesearch.com, fastpeoplesearch.com, thatsthem.com, freepeoplesearch.com) that can lookup information about any phone number’s user. These databases use a combination of marketing data, phone registration, public records, and other data sources.
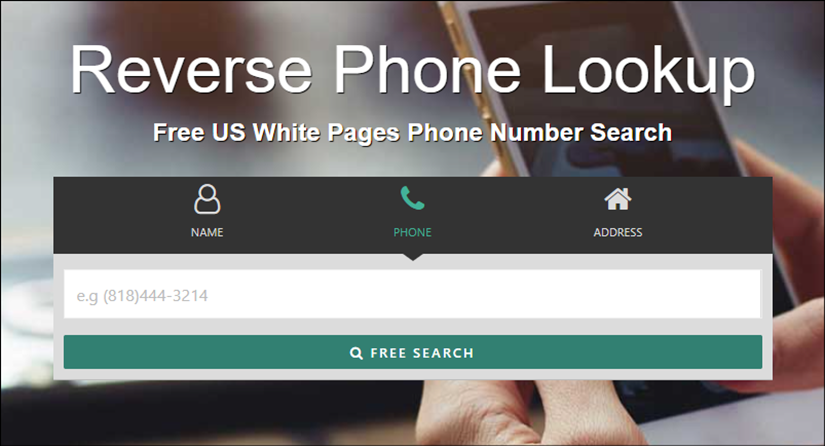
The result is that you can search any phone number and find the names and addresses associated with it. Note in the screenshot above that this site, like the others, will also let you search for information based on someone’s name or address. So a hacker can just walk past your house, see your address, and then decide to find your name and phone number.
In order to showcase how this works, I chose a random phone number to research as an example. Below you see the initial results revealing the user’s name, month and year of birth, and address.
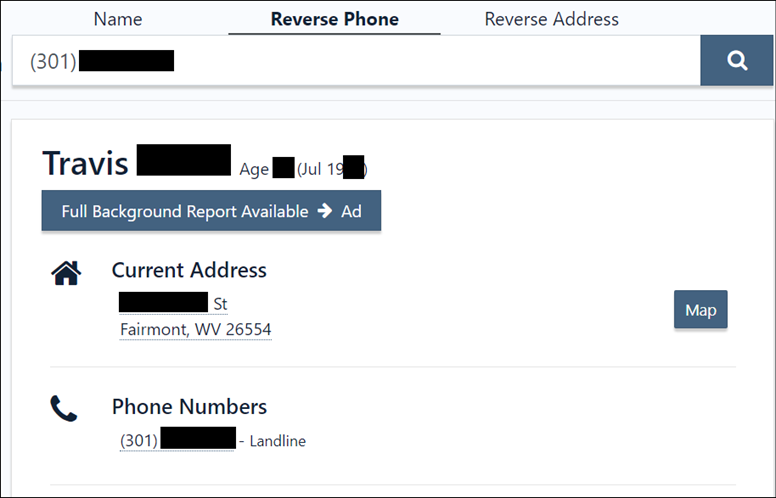
If we scroll down we see the user’s email address, the name of an “associate”, as well as former addresses and approximate dates when they lived there. If we click on the name of the “associate” we will see that this person lived at the same addresses at the same time as the phone’s user. This is almost certainly the user’s spouse. If we click on any of these data points (names, phones, addresses, email) the site will show all other data points associated with it.
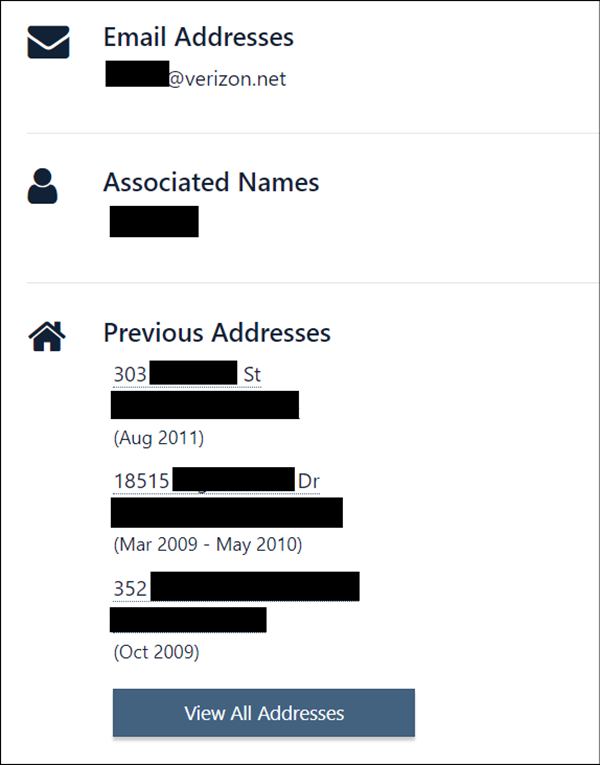
Finally, the site identifies “possible relatives” and “possible associates”. The “possible relatives” are identified be based on whether these people were registered to the same phone or address during the user’s childhood years (ages 1 through 18). The “possible associates” are often former neighbors or roommates.

You can click on the names to look further into the data. For example, if one name is approximately 20 or more years older than the owner, has the same last name, and lived at the same address during the owner’s childhood years, you can conclude that is a parent. Likewise you can identify probable siblings that were children at the same address with the same last name. You can use the same process to figure out who are the owner’s children.
These sites all likely have access to the same data, but some will provide different forms of the same information. For example, in the screenshot below you see how fastpeoplesearch.com will explain why it identified a second person as the owner’s spouse.
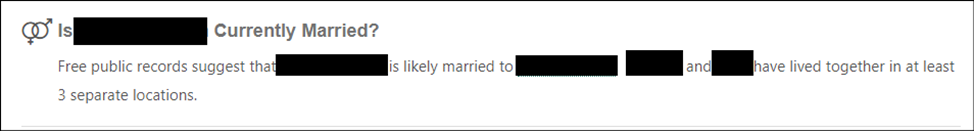
Some of the information that the hacker needs to pass your carrier’s security questions are directly provided in these results, such as when you were born, where you live, what is your email, and where you used to live. But some of the information that is not specifically identified can nonetheless be discovered by the hacker with a little bit of work. For example, when asked for the owner’s recent phone contacts, the hacker can assume that your recent calls might include your spouse/significant other/roommate, parents, siblings, or children.
Other Tools
There are other websites out there that a hacker can use for discovering different kinds of information about you. WAtools.io can look up if a phone number uses WhatsApp and download the owner’s profile photo. Truecaller.com can find out how people identify you in their contact books, like “John the IT guy”. There is also a Python script named Ignorant.py that can look up if a phone number uses Instagram, Snapchat, or Amazon. Data breach websites like HaveIBeenPwned.com will look up if any given phone number has been included in the data stolen by hackers and posted on the dark web. Data breach sites can identify personal information about the owner such as where they shop, play video games, or even what kind of car they own.
eSIMs
It is worth addressing the effect of eSIMs on this widespread threat. eSIMs are basically SIM cards that are embedded and hardwired into the phone for the sake of practical and security-related purposes. A consumer guide by the FCC (the Federal Communications Commission) notes some of the advantages of eSIMs.
That said, many articles have been written and experts have weighed in on whether eSIMs will make our phones more or less safe. The consensus among experts is that eSIMs are not expected to have a major impact on the threat of SIM-swapping. Malicious actors can still call up your carrier and request to transfer your SIM to a new phone.
How to Stay Secure?
Now that the threat of SIM-swapping is clear, we will address how you can stay safe.
The following steps are proven effective and listed in order of priority.
1 – Most phone service providers will let you set up a password to use in case your phone is lost or stolen. If you choose to use this method, consider getting a password manager (such as Bitwarden, NordPass, or Dashlane) where you can save your password long term.
2 – Start using an authenticator as your two factor authentication instead of text messages. Authenticators are a great way to make sure that you are the only one logging into your accounts. If you have an authenticator app, it will stay on your physical phone even if your phone number is stolen and transferred to another phone. If your physical phone is stolen, you can reset the authenticator on a new phone by using a pre-set password intended for this situation. The need for this password is one more reason to get a password manager.
3 – Sign up for a free account on a data breach website like HaveIBeenPwned.com that will notify you as soon as your phone number or other information appears in a data breach so that you know to change your password.
4 – Put a freeze on your credit score with the three main credit bureaus Equifax, Experian, and TransUnion. A freeze on your credit makes sure your credit wont be harmed if you are the victim of a hacker/scammer. Each of the three main credit bureaus offer this service (just google the name of the bureau and “credit freeze”).
5 - Remove your data from People-Search and Data Breach Websites. These websites all have an "opt out" option for you to remove your data. You can look up specific steps for how to remove your data for each website at the website JoinDeleteMe.com, which includes a section for opt out guides and other resources for removing data
These safety measures are straight-forward and convenient enough to ensure that you keep using them. The content of this article might be frightening from a security or privacy perspective, but you can stay safe with good security education and some simple measures.


