Spyse Geek Out
In this article I am going to geek out over Spyse, a new cybersecurity search engine I have started using.

In this article I am going to geek out over Spyse, a new cybersecurity search engine I have started using. It provides similar services to that of Shodan and has many similar functions from my personal perspective. I will be describing some of the things I found to be really good and some of the easier options in this service compared to others I have used in my bug bounty hunting career.
The homepage has a very nice UI and a tons of options for searching.
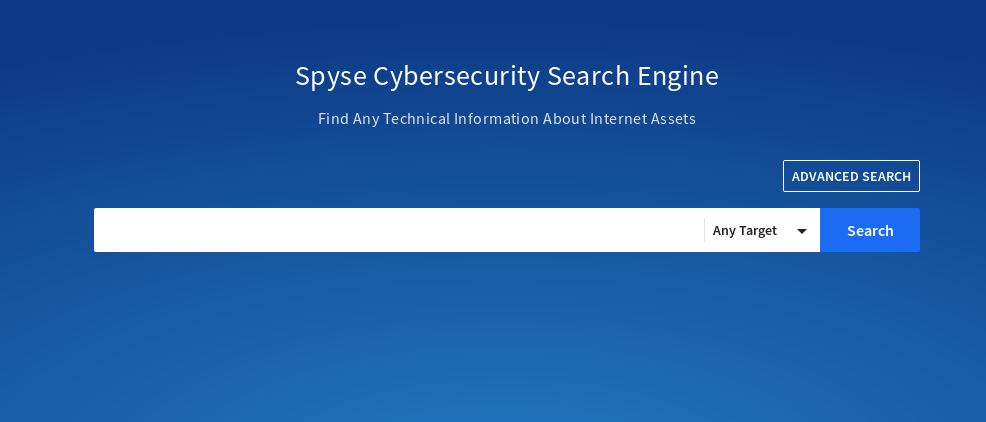
Some of the options that it lets you search using are :

I personally prefer to use Any Target mode, then search using domain name then make my way through the data/details it shows me in the resulting output. I am going to use Bugcrowd - a bugbounty platform as an example in this series.
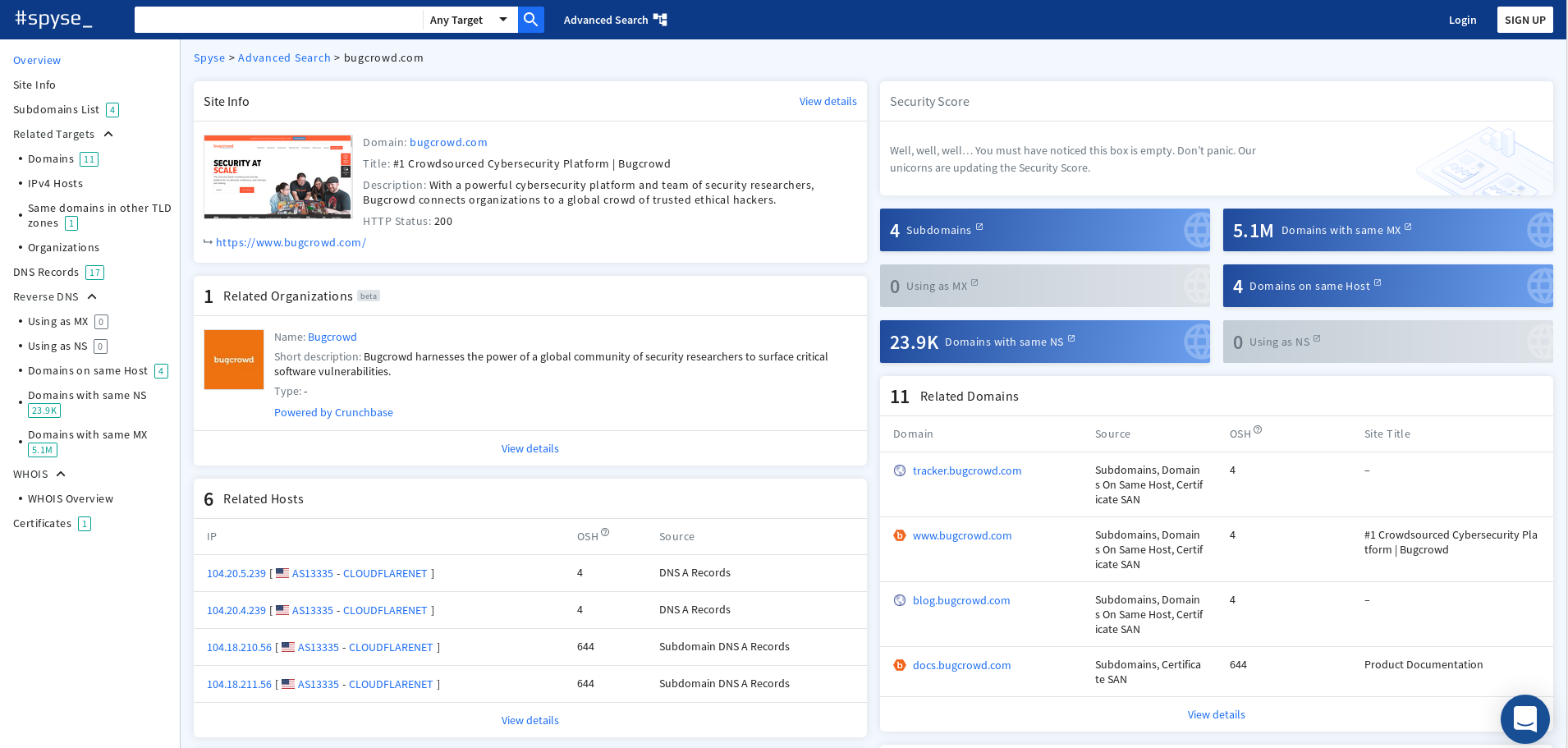
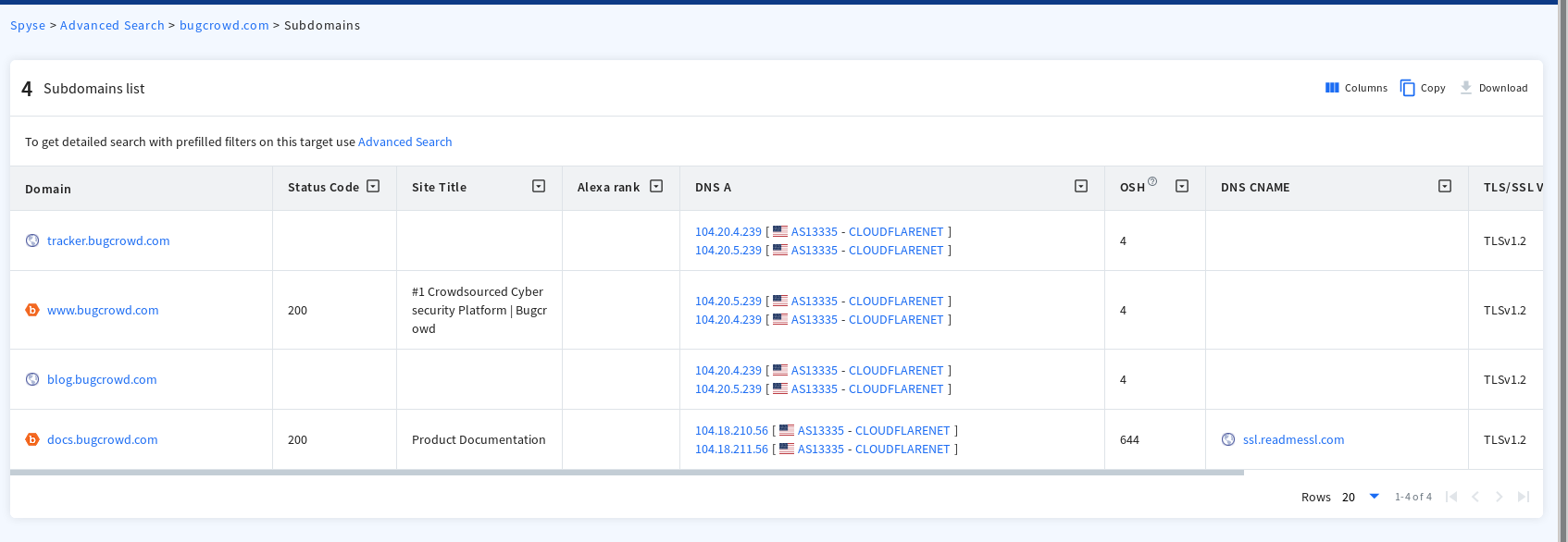
Similarly, when you are trying to enumerate the subdomains, there's a small window that shows the number of subdomains. If you click on it, you will be able to see the list of subdomains identified by Spyse alongwith some valuable information like DNS A record, DNS CNAME, TLS/SSL Version being used by that subdomain, Registrant's expiry date and few more.
Another neat feature that I identified and loved is that you can grab more details about the specific subdomain, find its TLS/SSL Certificate, related IP, etc and move around those details to do more deeper recon of your target.
Another simple yet powerful feature I started to use more and more is to find the assets based on the certificates identified. so when you click on "Find SSL/TLS Certificates" for a subdomain, you will then be shown a fingerprint of the certificate alongside its detail as below:
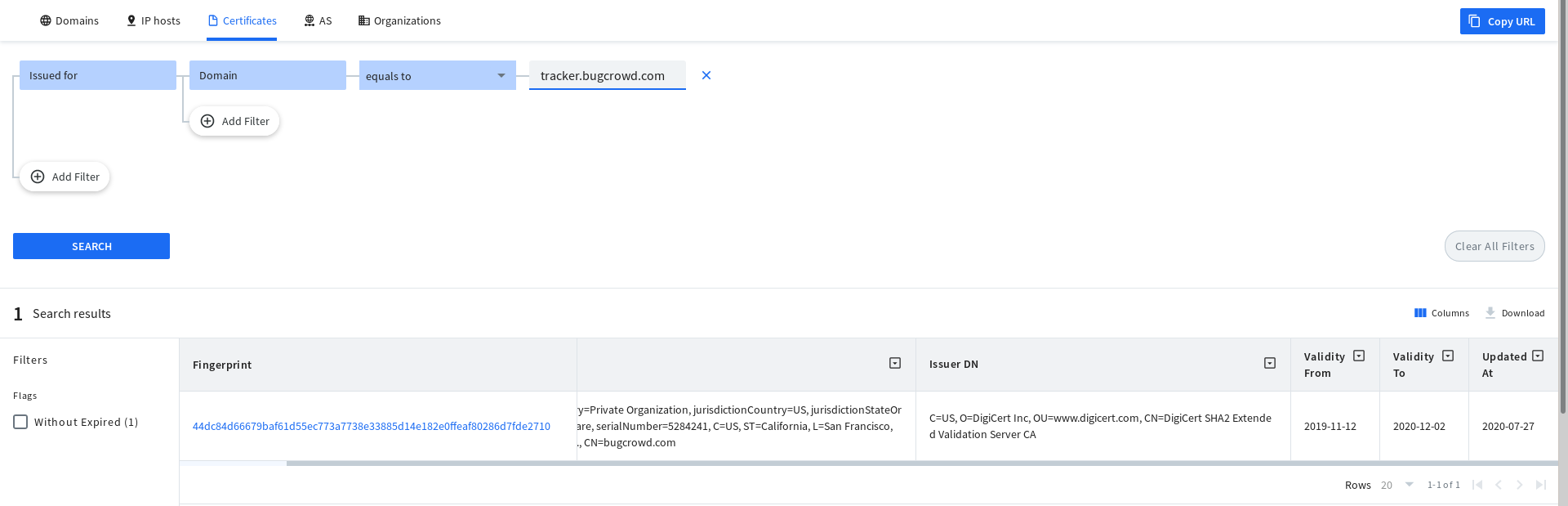
Clicking on the fingerprint, you can search for more domains related to that certificate and find more assets.
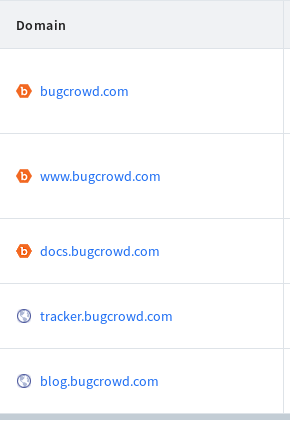
This is one of the easiest as well as fun method for me to utilise those information to find more and more assets for a bugbounty program that has wider scope. Beside this, what I loved is that you can use various filters and filter chain to focus on specific type of data to search. Moreover you would not need to remember all the different syntaxes which most of the other services requires in order to search. I found it as simple as searching for any simple data in popular search engines. All of these features were available in free version.
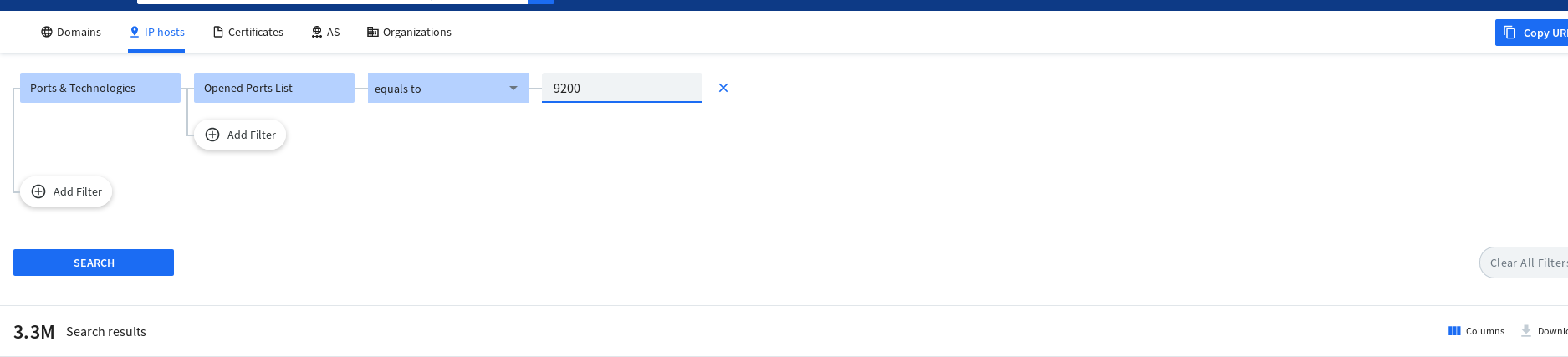
Another feature that I liked was its port-scanner. You can either scan for specific ports in the whole internet or search for open ports of a specific IP address.
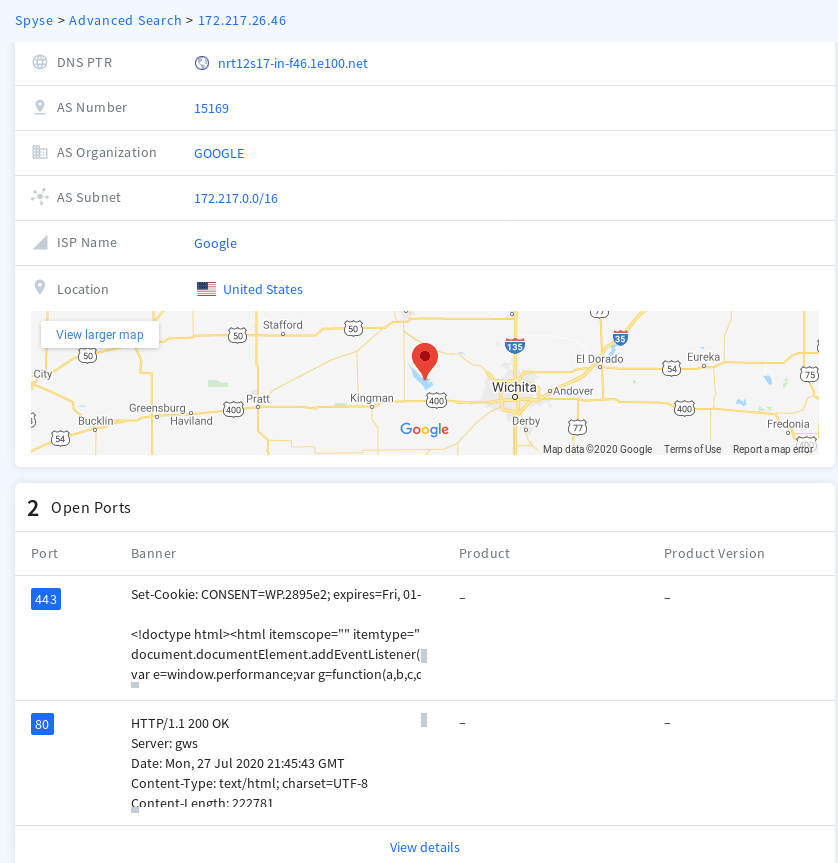
I searched for open port 9200 (for elastic search) and compared the response of Spyse and Shodan (another similar search engine) is that you need to be logged in to use filters in Shodan while it is not the case for Spyse. After logging into professional subscription account on Shodan and unauthenticated search via Spyse, Shodan yeilded 632,126 number of accessible assets that has port 9200 open while Spyse had 3.3 Millions.
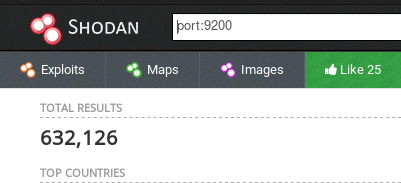
While searching via CVE is not possible without academic or Small Business subscription in Shodan, the pro subscription of Spyse do let you do that alongside more other functionalities which is great as not everyone could have academic emails to subscribe. The best similarity I found in both of them was that you can download the result in JSON and CSV format which is good for parsing and use with other tools. While shodan's download is limited to 10,000 result per export credit, Spyse lets you download the first 100,000 results which is promising if you are trying to download the data of a huge asset.
The thing that I liked more about Shodan than Spyse is the use of their API. Shodan lets you search unlimited times using API while Spyse only gives you 100,000 requests for a pro account. This limit still is enough but then some of the users could be automating the whole discovery phase using this and could easily run out of credits. Compared to Shodan, Spyse is bit expensive in their subscription model but definitely yields the results which can then be utilized to get return on investment sooner enough.
As of me, I would still be using the mix of Shodan and Spyse due to some of the features like unlimited API request, lower cost for account in Shodan and higher range of data and convenience to search in Spyse.
I would highly encourage readers to try out Spyse and Shodan then evaluate what is best suited for your needs and automation.


