How To Track A Facebook Page Owner
I was recently asked if there is a way to find out whereabouts of the person running the college's confession page on Facebook. In this article I discuss how I tracked them down.

I received a message from one of my juniors during the final year of my undergraduate degree. The message asked if there is a way to find out whereabouts of the person running the college's confession page on Facebook.
A bit on the background first:
When we were freshers in the college, someone created a confession page on Facebook. Anyone can submit a confession to the page anonymously using the google form link provided in the page. Devices inside the college create a private network. We had squid proxy servers for routing data in the public domain. The college has multiple dormitory buildings but only four buildings had the final year in them. Every building was a subnetwork, so I only need to worry about these four subnetworks.
My first thought, about deanonymizing the person, was that it is not possible! Afterall, it a Facebook page owner who don't want to advertise himself taking submissions via anonymous google forms. While in bed one night something struck me.
First things first, the IP Address
Like many other hacks, this one requires the IP address of the target. I thought if somehow I can create a malicious webpage and make him click on a link to acquire his IP address. After some pondering over this, I got an idea! The python's SimpleHTTPServer - Why not run the server and make him access it.
So, I wrote a tempting confession and added a link for the image (of my HTTP Server) that should be included with the post.
It took around five to six hour before an IP address pops up. I left the server running for a few more hours to see if any other IP address shows up - it didn't. Now I had the IP address of my target which fortunately belonged to my subnetwork.
After getting the IP address I mapped it to the MAC address of the machine. Something struck me so I decided to scan the whole subnetwork (python's nmap module were a great help for this) and map each IP address to a MAC address. I will explain shortly why I did this. I ran the script different times a day to make sure I have the record of almost all the systems running in the network.
Why record all the IP addresses and MAC addresses
There is a DHCP server running which allocates the IP addresses to the systems (We were also allowed to configure the IP addresses statically). Having both the IP address and MAC address of my target allowed me to cross-check that the IP address of my target doesn't get changed in the future whenever he reconnects. In case the DHCP server changes the IP address of my target, the record of all the systems in the subnetwork would have allowed me to track his new IP address.
There were around 250 students in the building and since I knew my target is from the final year I was able to eliminate around 150 students from the target space. It was necessary that I have the list of my target space. For this something from my third year helped me out. During the third year, one of my friends was working on a project for the college's Dean Student Welfare. He asked for my help with editing some files which had the list of all the students from my year. Now my goal was to keep reducing the search space until I have my target.
The Surveillance
My next step was to get as much information as I can to understand more about my target. So I implemented the passive man in the middle attack to capture his network activity. To understand and get the steps of my attack, read this post. This was during our mid-semester examinations when I intercepted his traffic which allowed me to find out his major. Also in our final year, we were supposed to select one elective from another major.
His normal traffic allowed me to guess either mechanical or electrical engineering as his major. Just a day before our elective exam I put extra care to understand the websites he is surfing. I cross reference the sites with all the elective subjects to find out the elective of my target. After having a good guess about his potential majors, I asked one of my juniors (from that major) to check (in the list) all the final years from my guessed two majors living in the hostel building. This narrowed down the search space to 23 students.
Analyzing his network activities just before the elective exam helped me to further narrow down the search space to 3 students. Now the road toward the destination was quite easy. I kept an eye on my target's activities to get more information. This includes websites he is surfing, his online timings, how often he opens his facebook, etc. In just 2 days I knew exactly who the target was. After all having lived for about four years with these people help you to get insights who among those these three he was.
Nerd Fact
Many people think that using HTTPS encrypts the URL part which makes it impossible for someone in the middle to find out which web server the client is getting connected to. Well this true, but only partially.
Imagine there is a server which is hosting multiple websites on port 80 for HTTP and 443 for HTTPS. Now, if the URL is encrypted how will the web server know to which website it should forward the packet. For this, the domain part of the URL is present in plain text in the ClientHello packet. RFC 3546 states that TLS does not provide a mechanism for a client to tell a server the name of the server is contacting.
It may be desirable for clients to provide this information to facilitate secure connections to servers that host multiple 'virtual' servers at a single underlying network address.
Conside the image of a wireshark capture below
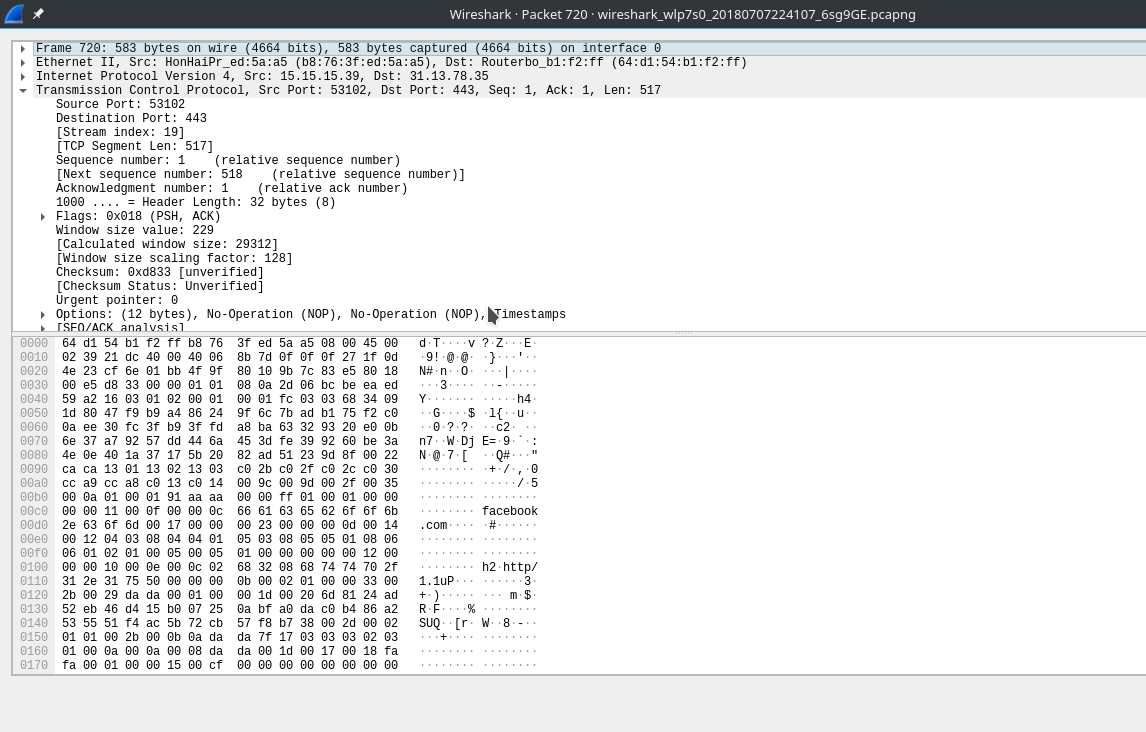
The above image shows the contents of ClientHello packet and it can be clearly seen that the client is connecting to facebook domain. Consider this stackoverflow question thread for more details.
What makes this hack my favorite is that it doesn't include using metasploit, burpsuite or any other software/application to initiate an attack. It doesn't rely on the vulnerability of a software, device, network protocol, etc. The attack was more artistic than scientific.
In both magic and hacking if you were to look in just the right spot, the trick would be obvious.
MAIN IMAGE CREDIT: Boba Fett by Justas Galaburda

